Introduction
This document describes the configuration steps for VRF aware syslog on FTD.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Syslog
- Firepower Threat Defense (FTD)
Components Used
The information in this document is based on these software and hardware versions:
- Secure Firewall Management Center (FMCv) v7.4.2
- Secure Firewall Threat Defense Virtual (FTDv) v7.4.2
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Minimum Software and Hardware Platforms
- Application and Minimum version: Secure Firewall 7.4.1
- Supported Managed Platforms and version: All which support FTD 7.4.1
- Managers:
1) FMC on-perm + FMC REST API
2) cloud-delivered FMC
3) FDM + REST API
Snort3, Multi-Instance/Context and HA/Clustering Support

Note: Works with both IPv4 and IPv6 syslog servers. IPv6 is not supported yet in Syslog ftp server.
- Supported with Multi-instance.
- Supported with HA'd devices.
- Supported on Clustered Devices.
Configure
Network Diagram
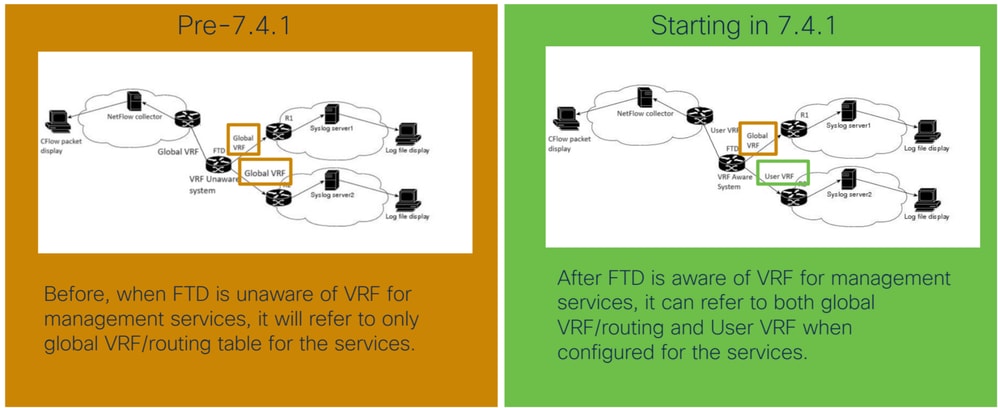 Network Diagram Comparison between Pre and Post 7.4.
Network Diagram Comparison between Pre and Post 7.4.
Configurations
Virtual Routing and Forwarding (VRF) is a technology used in networking to allow multiple instances of a routing table to coexist within the same router, providing network isolation between different virtual networks. Each VRF instance is independent of others, and traffic between them is kept separate. Multi-VRF is a feature that enables service providers to support multiple VPNs and services, even if their IP addresses overlap. It uses input interfaces to designate routes for various services and create virtual packet-forwarding tables by assigning Layer 3 interfaces to each VRF. Management services (Syslog, NetFlow) use Global VRF as default. Users want to use User VRF for Management services as well as the Global VRF because not all upload destinations are reachable via Global VRF.
In this document, Global + User VRF = Multi-VRF
Enable Syslog for User VRF.
- Syslog can use ftp service in a multi-VRF context.
How it Works
When interface is configured with User VRF, route lookup occurs in VRF routing domain, instead of default global routing domain.
- Two types of server configurations are supported:
- Send logging messages to Syslog servers to monitor and troubleshoot the network traffic.
- Send the log buffer content to an FTP server as a text file
- Syslog emits the logs to the respective UDP/TCP servers within that VRF.
- For buffer wrap syslogs, the logs are sent to configured FTP server within that VRF.

Note: Syslog server and FTP server can be part of different VRFs.
Configure Virtual Router
Step 1. Create a VRF
- Log in to FMC and navigate to Device > Device Management.
- Select the Device and click the Pencil icon to edit it.
- Navigate to Routing> Manage Virtual Router > Add Virtual Router.
- Enter the name in VRF Name.
- Select the interface and click Add and Save.
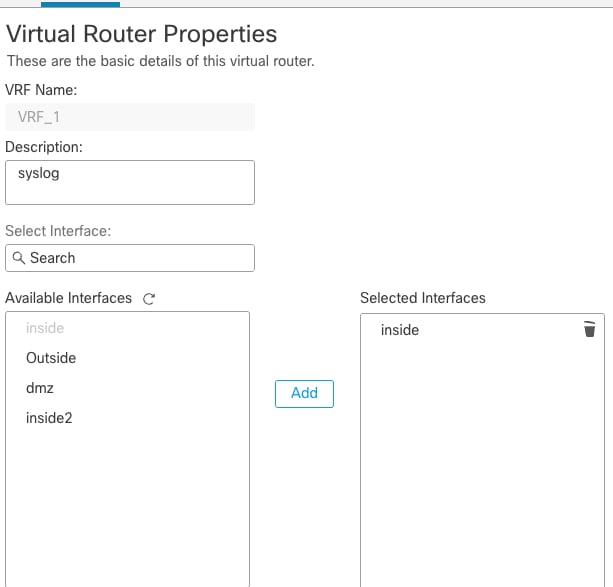 Adding Interface to VRF
Adding Interface to VRF
Step 2. Configure the logging set-up.
- Navigate to Devices > Platform Settings.
- Create a New Policy or edit the Pencil icon on existing policy.
 Creating the Platform Settings
Creating the Platform Settings
- Select Logging Setup and Enable logging.
 Enable Logging
Enable Logging
- Select Logging Destination and click Add.
- Set the Logging Destination as Syslog servers.
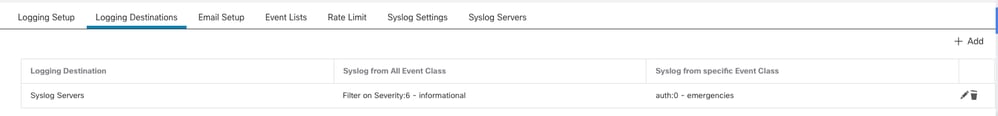 Logging Destination as Syslog Servers
Logging Destination as Syslog Servers
- Select Syslog Servers > Add.
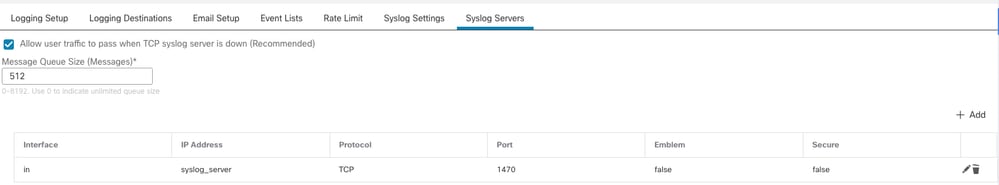 Adding Syslog Server with VRF Aware Interface
Adding Syslog Server with VRF Aware Interface

Note: Inside interface is part of Security-zone in.
- The interface configured in logging host command is now VRF aware.
- Click Save.
Prerequisites for FTP Server Configuration in FMC
- Use Interface Group Object.
- Interface Group Object can have both User and Global VRF.
Configuration
Step 1.
- Navigate to Object > Object Management > Interface > Add > Interface Group.
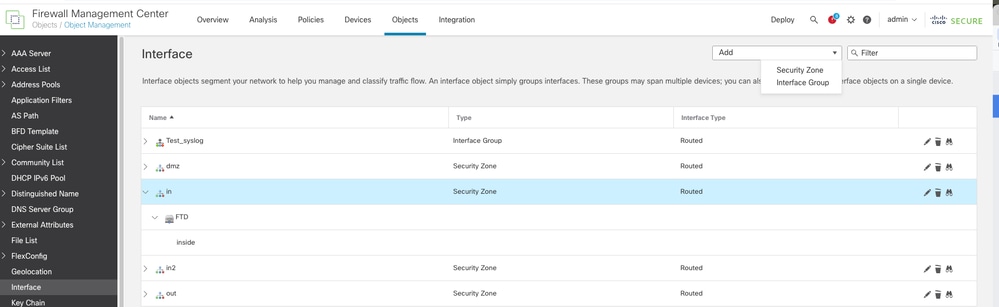 Adding Interface Group
Adding Interface Group
- Select the Device from drop down and Add the VRF Interface.
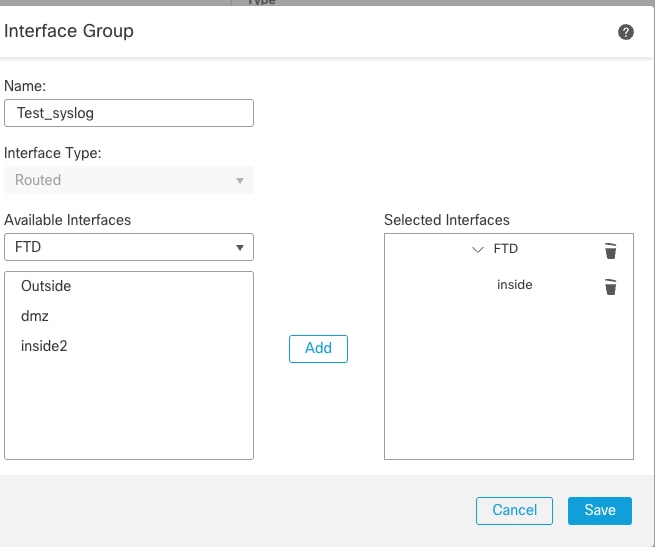 Adding VRF Aware Interface
Adding VRF Aware Interface
Step 2.
- Navigate to Devices > Platform Settings > Syslog > Logging Setup. Enable FTP server buffer wrap.
- Click Save.
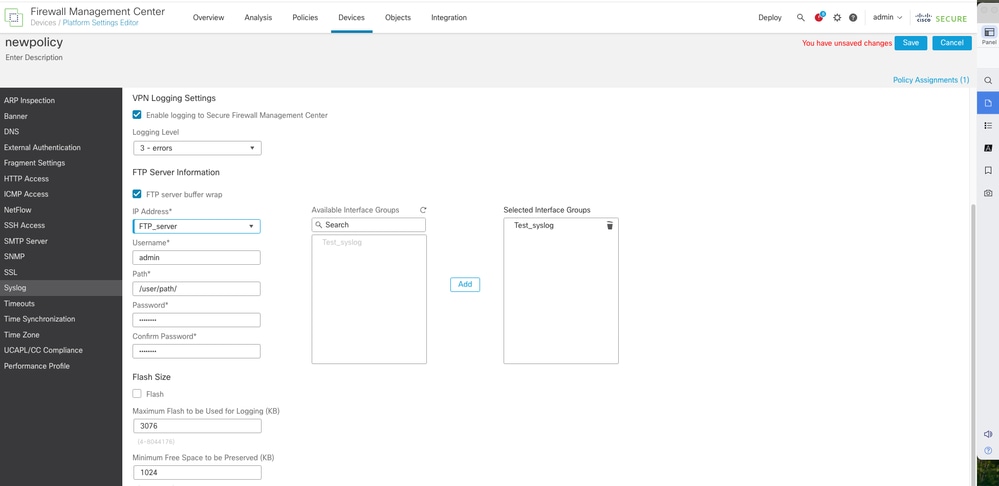 Enable FTP Server with VRF Aware Interface
Enable FTP Server with VRF Aware Interface
Verify
Pre 7.4.1
In this test, the FTD and FMC is 7.0.5.
FTD is configured with VRF and dmz interface has been assigned to VRF.
The dmz interface is configured with syslog server logging host.
Additionally inside interface is configured with syslog setting.
The inside interface is part of Global VRF.
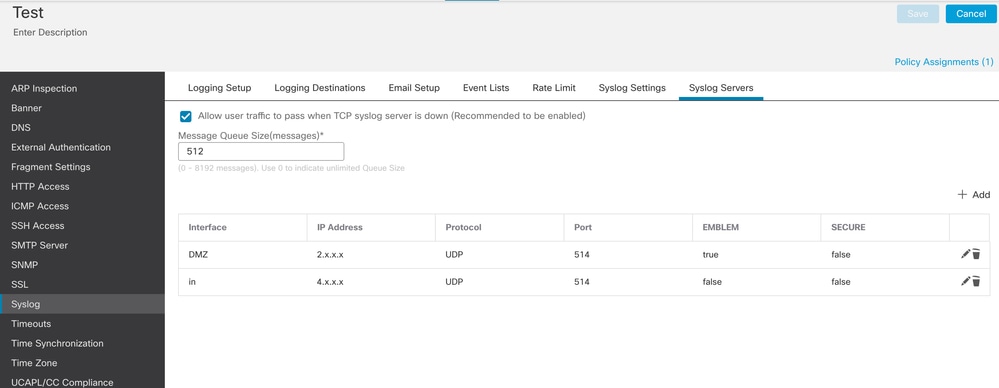 Syslog Server Setting on 7.0.5 FMC
Syslog Server Setting on 7.0.5 FMC
CLI Verification
> show logging
Syslog logging: enabled
Facility: 20
Timestamp logging: disabled
Hide Username logging: enabled
Standby logging: disabled
Debug-trace logging: disabled
Console logging: disabled
Monitor logging: disabled
Buffer logging: disabled
Trap logging: level informational, facility 20, 1193 messages logged
Logging to inside 4.x.x.x, UDP TX:52
Global TCP syslog stats::
NOT_PUTABLE: 0, ALL_CHANNEL_DOWN: 0
CHANNEL_FLAP_CNT: 0, SYSLOG_PKT_LOSS: 0
PARTIAL_REWRITE_CNT: 0
Permit-hostdown logging: enabled
History logging: disabled
Device ID: disabled
Mail logging: disabled
ASDM logging: disabled
FMC logging: list MANAGER_VPN_EVENT_LIST, 0 messages logged
> show vrf
Name VRF ID Description Interfaces
VRF-1 1 dmz

Note: Syslog server with destination 2.x.x.x is not available on logging setting for FTD CLI. This is part of User VRF.
Syslog server with destination 4.x.x.x is available on logging setting for FTD CLI. This is part of Global VRF.
Post 7.4.1
CLI Verification
ftd1# show vrf
Name VRF ID Description Interfaces
VRF_1 1 syslog inside
td1# show logging
Syslog logging: enabled
Facility: 20
Timestamp logging: disabled
Hide Username logging: enabled
Standby logging: disabled
Debug-trace logging: disabled
Console logging: disabled
Monitor logging: disabled
Buffer logging: disabled
Trap logging: level informational, class auth, facility 20, 19284 messages logged
Logging to inside 192.x.x.x tcp/1470 Not connected since Thu, 20 Mar 2025 01:53:17 UTC TX:0
TCP SYSLOG_PKT_LOSS:0
TCP [Channel Idx/Not Putable counts]: [0/0]
TCP [Channel Idx/Not Putable counts]: [1/0]
TCP [Channel Idx/Not Putable counts]: [2/0]
TCP [Channel Idx/Not Putable counts]: [3/0]
Global TCP syslog stats::
NOT_PUTABLE: 0, ALL_CHANNEL_DOWN: 1584
CHANNEL_FLAP_CNT: 1584, SYSLOG_PKT_LOSS: 0
PARTIAL_REWRITE_CNT: 0
Permit-hostdown logging: enabled
History logging: disabled
Device ID: disabled
Mail logging: disabled
ASDM logging: disabled
FMC logging: list MANAGER_VPN_EVENT_LIST, class auth, 0 messages logged

Note: Syslog server host 192.x.x.x is using the VRF aware inside interface.
FTP Server Verification
Pre 7.4.1
- On FMC, FTP server setting does not have the option to select Interface to use. Only IP address of the syslog server option is available.
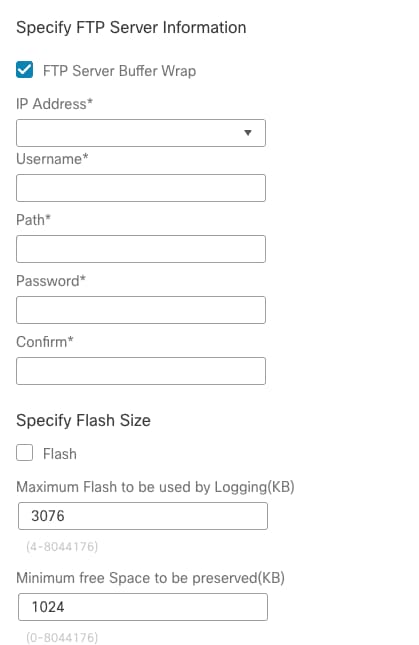 FTP Server Settings on FMC 7.0.5
FTP Server Settings on FMC 7.0.5
Post 7.4.1
- New Interface Option, which is configured with VRF in Syslog FTP server settings.
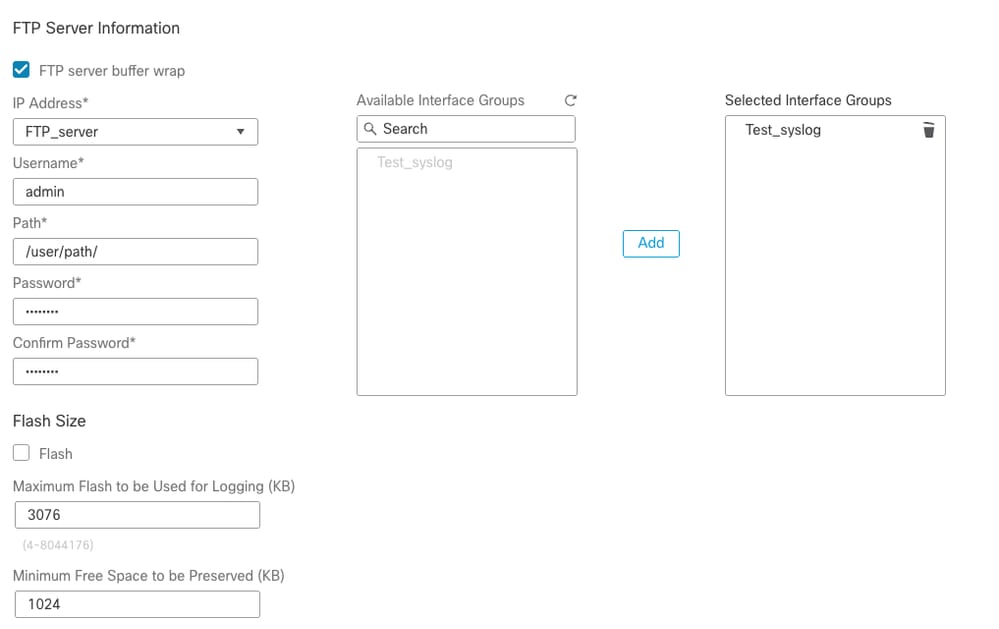 FTP Server Setting Port 7.4.1
FTP Server Setting Port 7.4.1
CLI verification
logging ftp-bufferwrap
logging ftp-server inside 55.x.x.x /user/path/ admin *****

Note: FTP server host is now using the VRF aware inside interface.














 Feedback
Feedback