Field Notice: FN74316 - Cisco Secure Firewalls: Microsoft Intune Managed Endpoints Might Be Unable to Communicate with the Intune Service After December 2, 2025 - Configuration Change Recommended
Available Languages
Notice
THIS FIELD NOTICE IS PROVIDED ON AN "AS IS" BASIS AND DOES NOT IMPLY ANY KIND OF GUARANTEE OR WARRANTY, INCLUDING THE WARRANTY OF MERCHANTABILITY. YOUR USE OF THE INFORMATION ON THE FIELD NOTICE OR MATERIALS LINKED FROM THE FIELD NOTICE IS AT YOUR OWN RISK. CISCO RESERVES THE RIGHT TO CHANGE OR UPDATE THIS FIELD NOTICE AT ANY TIME.
Products Affected
| Affected Software Product | Affected Release | Affected Release Number | Comments |
|---|---|---|---|
| FirePOWER Services Software for ASA | 6 | 6.4.0, 6.4.0.1, 6.4.0.10, 6.4.0.11, 6.4.0.12, 6.4.0.13, 6.4.0.14, 6.4.0.15, 6.4.0.16, 6.4.0.17, 6.4.0.18, 6.4.0.2, 6.4.0.3, 6.4.0.4, 6.4.0.5, 6.4.0.6, 6.4.0.7, 6.4.0.8, 6.4.0.9 | |
| FirePOWER Services Software for ASA | 7 | 7.0.0, 7.0.0.1, 7.0.1, 7.0.1.1, 7.0.2, 7.0.2.1, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.6.1, 7.0.6.2, 7.0.7, 7.0.8 | |
| Firepower Threat Defense (FTD) Software | 6 | 6.4.0, 6.4.0.1, 6.4.0.10, 6.4.0.11, 6.4.0.12, 6.4.0.13, 6.4.0.14, 6.4.0.15, 6.4.0.16, 6.4.0.17, 6.4.0.18, 6.4.0.2, 6.4.0.3, 6.4.0.4, 6.4.0.5, 6.4.0.6, 6.4.0.7, 6.4.0.8, 6.4.0.9 | |
| Firepower Threat Defense (FTD) Software | 7 | 7.0.0, 7.0.0.1, 7.0.1, 7.0.1.1, 7.0.2, 7.0.2.1, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.6.1, 7.0.6.2, 7.0.6.3, 7.0.7, 7.0.8, 7.1.0, 7.1.0.1, 7.1.0.2, 7.1.0.3, 7.2.0, 7.2.0.1, 7.2.1, 7.2.10, 7.2.2, 7.2.3, 7.2.4, 7.2.4.1, 7.2.5, 7.2.5.1, 7.2.5.2, 7.2.6, 7.2.7, 7.2.8, 7.2.8.1, 7.2.9, 7.3.0, 7.3.1, 7.3.1.1, 7.3.1.2, 7.4.0, 7.4.0.118, 7.4.1, 7.4.1.1, 7.4.2, 7.4.2.1, 7.4.2.2, 7.4.2.3, 7.6.0, 7.6.1, 7.6.2, 7.7.0, 7.7.10, 7.7.11 |
Defect Information
| Defect ID | Headline |
| CSCwr41995 | FN74316 Cisco Secure Firewalls: Microsoft Intune Managed Endpoints Might Be Unable to Communicate with the Intune Service After December 2, 2025 |
Problem Description
Endpoints behind Cisco Secure Firewalls that are managed by the Microsoft Intune service might be unable to communicate with the Intune service after December 2, 2025.
Microsoft is transitioning to new IP address ranges for the Intune service, and outbound Cisco Secure Firewall allowlists might prevent access to the new IP addresses.
Background
Microsoft has announced that, as part of its Secure Future Initiative (SFI), Intune device management endpoints will transition to new IP address ranges delivered through Azure Front Door. This change takes effect on or shortly after December 2, 2025, and might affect customers with outbound firewall allowlists that control traffic based on IP addresses for Azure service tags.
Cisco Secure Firewalls that are using Dynamic Attributes Connectors with the Azure service tags connector can automatically retrieve IP ranges published by Microsoft, including the AzureFrontDoor.MicrosoftSecurity object, and reference them in firewall policies. This allows policies to stay up to date without manual IP address updates.
For customers not using Cisco Secure Dynamic Attribute Connector or customers using Azure Government Cloud (because Cisco Secure Dynamic Attribute Connector is not available for Government Cloud environments), this change must be handled manually. The outbound firewall rules must be updated manually to include all published IPv4 and IPv6 subnets for the AzureFrontDoor.MicrosoftSecurity service tag from Microsoft. Without this update, endpoints behind Cisco Secure Firewalls that are managed by the Microsoft Intune service might fail to access required services on or shortly after December 2, 2025.
For customers subscribed to the Intune service, reference this Microsoft Service Bulletin that provides additional information related to the IP address range changes.
Problem Symptom
Endpoints behind Cisco Secure Firewalls that are managed by the Microsoft Intune service might be unable to communicate with the Intune service after December 2, 2025.
Additional problem symptoms might include:
- Device check-in failures
- Login failures for users
- Inability to access the Microsoft Intune company portal or applications protected by Intune app protection policies
Workaround/Solution
Cisco Secure Firewalls with Dynamic Attributes Connectors
For Cisco Secure Firewalls that are using Dynamic Attributes Connectors, Cisco recommends the following procedure.
Figure 1: Verify the presence of the AzureFrontDoor.MicrosoftSecurity object using Cisco Secure Firewall Management Center (FMC) or Cisco cloud-delivered Firewall Management Center (cdFMC).
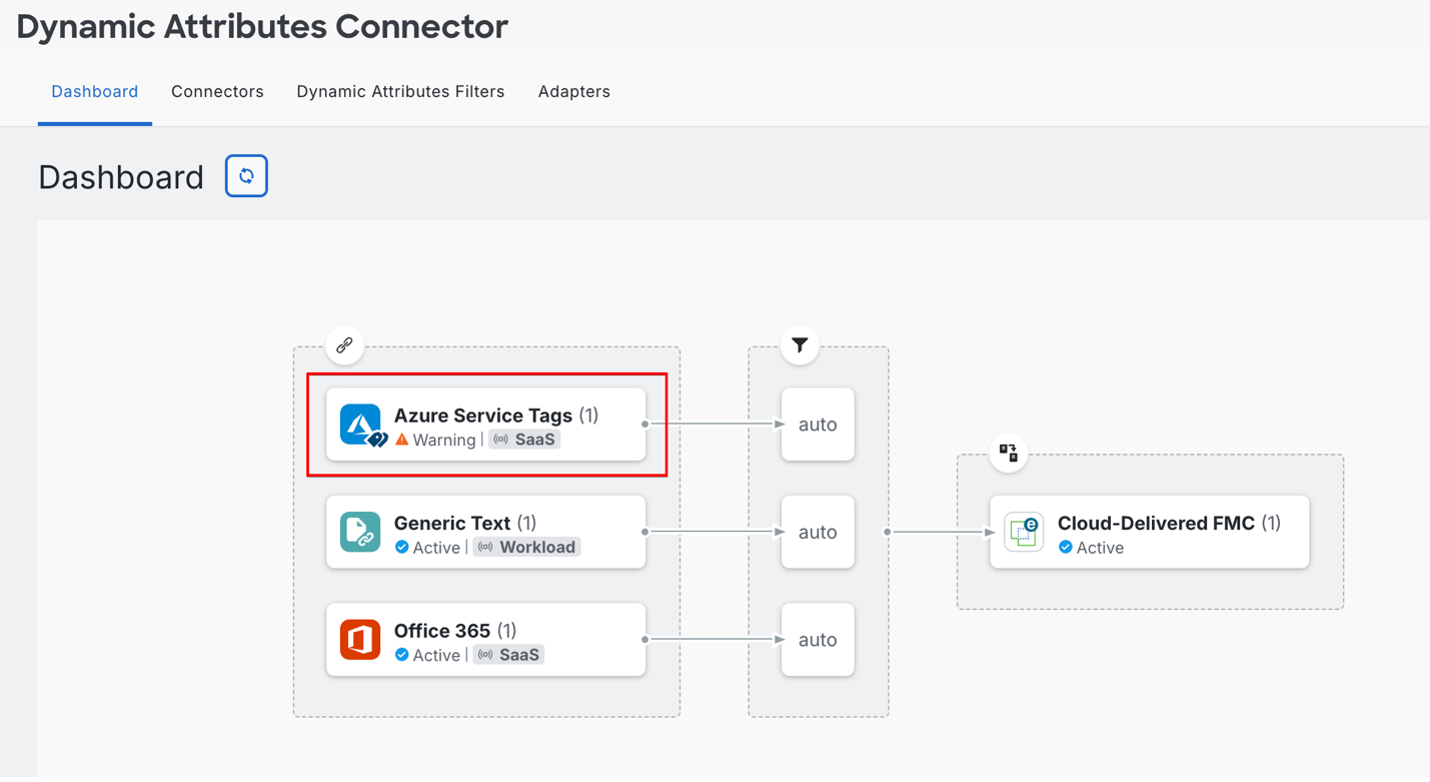
Figure 2: Confirm that AzureServiceTag_AzureFrontDoor_MicrosoftSecurity retrieves all IP address prefixes published by Microsoft, including both IPv4 and IPv6 ranges.
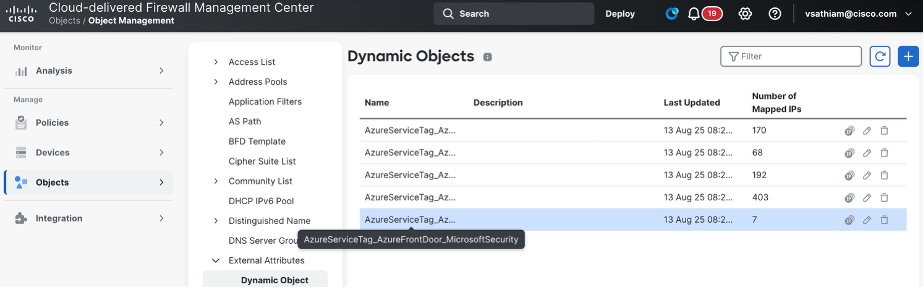
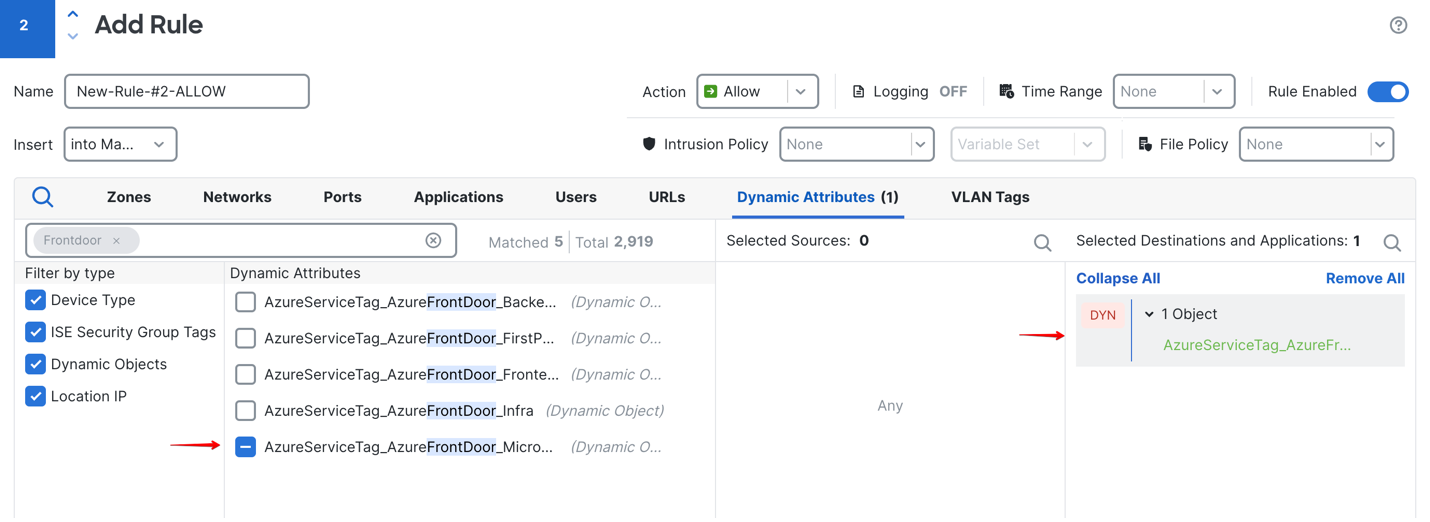
Figure 3: Verify that AzureServiceTag_AzureFrontDoor_MicrosoftSecurity is referenced in the firewall allow policies for outbound port 443 traffic to the Microsoft Intune service.
Cisco Secure Firewalls without Dynamic Attributes Connectors
For Cisco Secure Firewalls that are not using Dynamic Attributes Connectors, Cisco recommends manually updating the IP address ranges published by Microsoft for the Intune service.
Figure 4: Commercial applications - Azure IP address ranges and service tags. The most recent summary is available from Microsoft Intune at Network endpoints for Microsoft Intune.
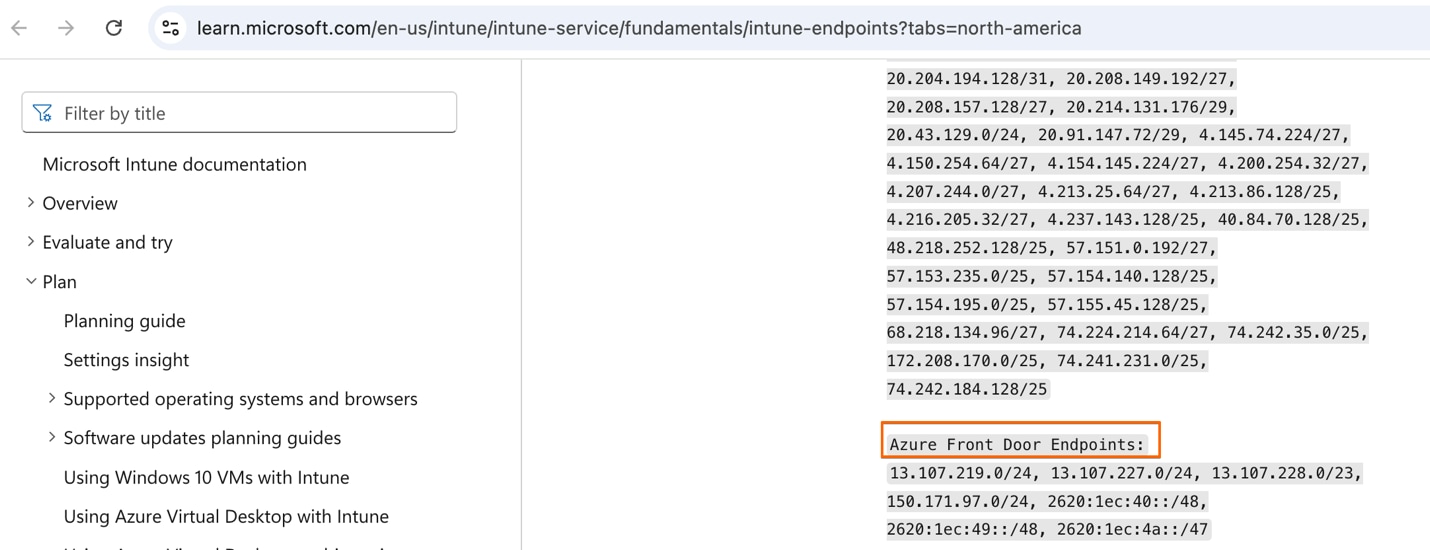
Note: The IP addresses for Azure Front Door endpoints shown in Figure 4 are for the U.S. region as of September 1, 2025.
Figure 5: U.S. government, U.S. Government Community Cloud (GCC) High, and Department of Defense (DoD) applications - Azure IP address ranges and service tags. The most recent summary is available from Microsoft Intune at US government endpoints for Microsoft Intune.
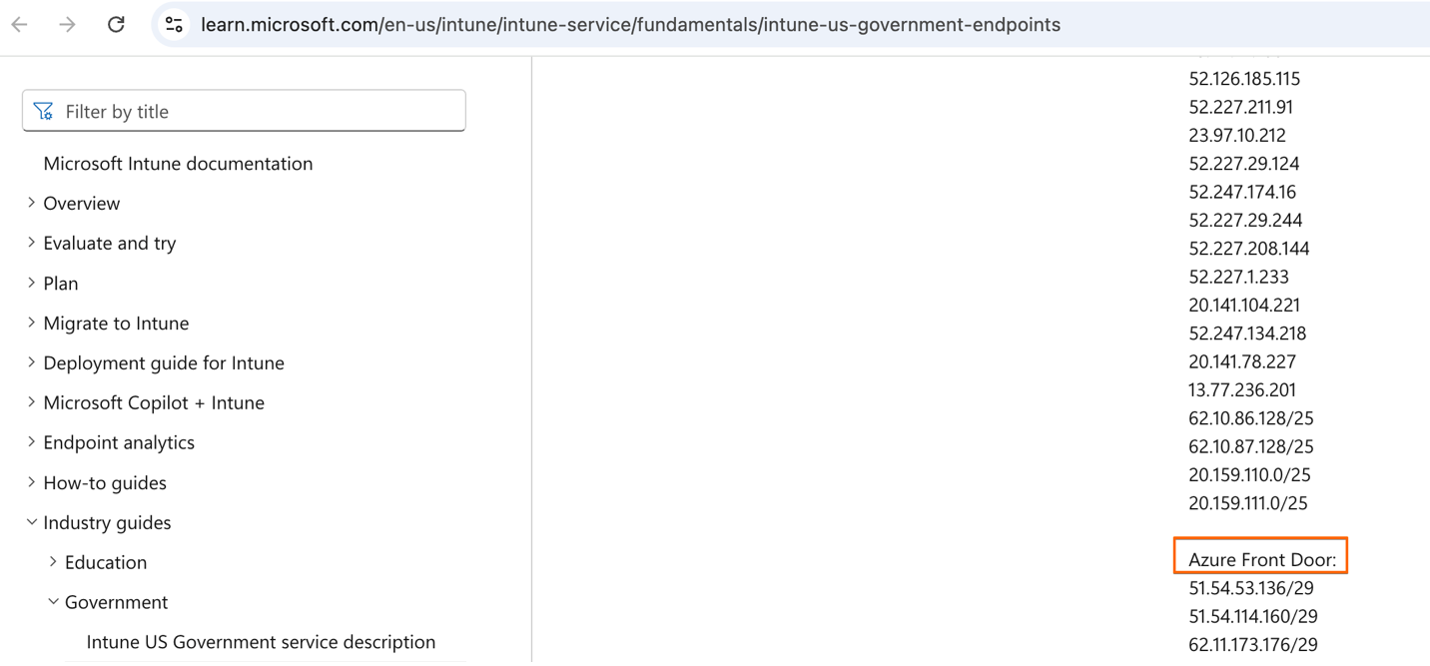
Note: The IP addresses for Azure Front Door shown in Figure 5 are for the U.S. government endpoints as of September 1, 2025.
Additional Information
Cisco offers a guided upgrade experience through the Cisco Secure Firewall upgrade program. This program will provide environment-specific software upgrade guidance, a customized procedure to follow, and a customized pre-upgrade checklist. For additional information and to register for the upgrade program, see Get access to Cisco Secure Firewall LevelUp.
Revision History
| Version | Description | Section | Date |
| 1.1 | Updating Impact Rating | — | 2025-OCT-01 |
| 1.0 | Initial Release | — | 2025-OCT-01 |
For More Information
For further assistance or for more information about this field notice, contact the Cisco Technical Assistance Center (TAC) using one of the following methods:
Receive Email Notification About New Field Notices
To receive email updates about Field Notices (reliability and safety issues), Security Advisories (network security issues), and end-of-life announcements for specific Cisco products, set up a profile in My Notifications.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
This Document Applies to These Products
Unleash the Power of TAC's Virtual Assistance
 Feedback
Feedback