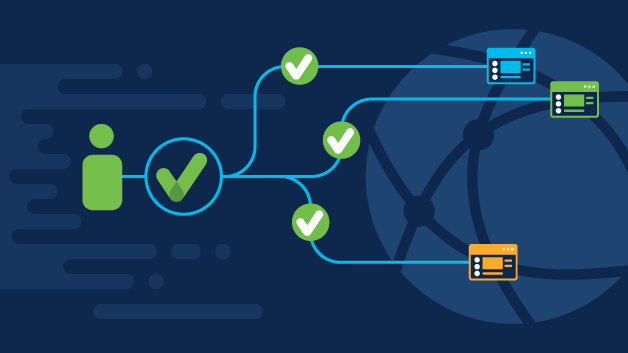
How does SSO work?
When a user signs into an SSO service, the service creates an authentication token that verifies the user's identity. This token is a piece of digital data stored in the user's web browser or on the SSO service's servers.
When a user attempts to access an application, the token checks with the SSO service, which passes the authentication token to the app. If the token is valid, the user is allowed to access the app. If the user has not yet signed in, they are prompted to do so through the SSO service.
Most SSO services verify user credentials against a separate identity management system, or identity provider (IdP). The SSO service acts as an intermediary between the user and the IdP. It checks the user's login credentials against the IdP's database, but it does not manage the database itself.
The ability to pass an authentication token to external apps and services is critical to the SSO process. This allows identity verification to take place separately from other cloud services, making SSO possible.
Authentication tokens have their own communication standards to help ensure that they are correct and legitimate. The most common standards are Secure Authentication Markup Language (SAML) 2.0 and OpenID Connect/OAuth 2.0. These standards are like common "languages" for authentication tokens.