Cisco Crosswork Trust Insights At-a-Glance
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
System integrity is the foundation of trustworthiness
The network is critical infrastructure, hence its integrity and trustworthiness are paramount. A compromise in integrity, whether hardware or software, presents vulnerability to cyber attacks. A malicious actor can control network devices, steal or manipulate data, or deny specific traffic flows and spread to other parts of the network. Verifying device integrity and establishing device trust posture can be difficult without the critical system knowledge provided by the manufacturer.
Cisco Crosswork™ Trust Insights is a cloud-based SaaS solution that reports on the integrity of devices and provides forensics for assured inventory. It offers a cryptographically secured collection of trust and inventory data, intuitive visualization, meaningful analytics, and alerts to notify of changes that may affect device integrity. In addition, the service provides an independent and secure repository of collected evidence.
Cisco Crosswork Trust Insights uniquely leverages the trust technologies built into Cisco platforms. For example, it utilizes the cryptographic identity as part of a trust anchor to validate information collected from the device. Trust Insights also uses an automated feed of up-to-date fingerprints derived from software build processes to validate device integrity in the run time.
● Visualize and report on the trustworthiness of your network infrastructure
● Reduce Mean Time To Know (MTTK) using investigative workflows and analyzing system integrity changes
● Establish compliance and forensic readiness with independent and immutable storage of evidence
● Minimize operational complexity and costs while maintaining high service reliability using a scalable, cloud-based Software-as-a-Service (SaaS) offering
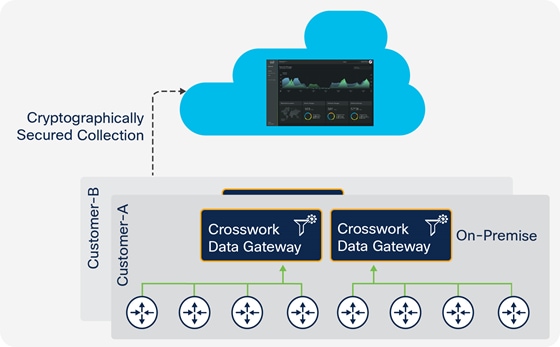
Crosswork Cloud Trust Insights leverages robust Cisco Crosswork Cloud infrastructure.
Cisco is committed to transparency and accountability and to acting as a trusted partner to our customers to address security challenges. Cisco Crosswork Trust Insights collects signed and cryptographically secured evidence from network devices and combines it with deep system knowledge from Cisco to provide a comprehensive view of device integrity and assured inventory forensics.
Contact your Cisco sales representative to learn more about how Cisco Crosswork Trust Insights can empower you with comprehensive visibility to affirm trustworthiness of your critical network infrastructure.
Analyze trustworthiness with verifiable evidence
Cisco Crosswork Trust Insights reports on inventory changes and system integrity information with comprehensive coverage across hardware and software. It utilizes Cisco Crosswork Data Gateway as a proxy deployed in your network to collect data from network devices using a cryptographically secured channel. It enables you to:
● Track and analyze system integrity changes utilizing intuitive dashboard and investigative workflows
● Maintain verifiable evidence as proof-of-change for compliance
● Analyze the history of changes for traceability and forensic analysis
● Maximize the benefits of the built-in trust technologies in the devices
Today, telemetry provided by networks is plentiful, but the existing toolsets are unable to comprehensively assess the device’s integrity. This assessment is required not only at the boot time, but also at runtime and retrospectively to preserve trustworthiness.