-
Cisco MDS 9000 Family Configuration Guide, Release 2.x
-
New and Changed Information
-
Index
-
Preface
- Part 1 - Getting Started
- Part 2 - Cisco MDS SAN-OS Installation and Switch Management
- Part 3 - Switch Configuration
-
Part 4 - Fabric Configuration
-
Configuring and Managing VSANs
-
Creating Dynamic VSANs
-
Configuring Inter-VSAN Routing
-
Configuring Zones
-
Distributing Device Alias Services
-
Configuring Fibre Channel Routing Services and Protocols
-
Managing FLOGI, Name Server, FDMI, and RSCN Databases
-
Discovering SCSI Targets
-
Configuring FICON
-
Advanced Features and Concepts
-
- Part 5 - Security
- Part 6 - IP Services
- Part 7 - Intelligent Storage Services
- Part 8 - Network and Switch Monitoring
- Part 9 - Traffic Management
- Part 10 - Troubleshooting
-
Table Of Contents
About the Cisco Fabric Analyzer
Configuring the Cisco Fabric Analyzer
Sending Captures to Remote IP Addresses
Clearing Configured fcanalyzer Information
The show tech-support brief Command
Troubleshooting Your Fabric
This chapter describes basic troubleshooting methods used to resolve issues with switches. This chapter includes the following sections:
•
Configuring a Fabric Analyzer
•
The show tech-support Command
The fctrace Feature
The fctrace feature allows you to:
•
Trace the route followed by data traffic.
•
Compute inter-switch (hop-to-hop) latency.
You can invoke fctrace by providing the FC ID, the N port, or the NL port WWN, or the device alias of the destination. The frames are routed normally as long as they are forwarded through TE ports.
Once the frame reaches the edge of the fabric (the F port or FL port connected to the end node with the given port WWN or the FC ID), the frame is looped back (swapping the source ID and the destination ID) to the originator.
If the destination cannot be reached, the path discovery starts, which traces the path up to the point of failure.
Note
The fctrace feature works only on TE ports. Make sure that only TE ports exist in the path to the destination. In case there is an E port in the path, the fctrace frame is dropped by that switch. Also, fctrace times out in the originator, and path discovery does not start.
Tip
You cannot use the fctrace feature in a locally configured VSAN interface (IPFC interface), but you can trace the route to a VSAN interface configured in other switches.
To perform a fctrace operation, follow this step:
The fcping Feature
The fcping feature verifies reachability of a node by checking its end-to-end connectivity. You can invoke the fcping feature by providing the FC ID, the destination port WWN, or the device alias information.
To perform a fcping operation, follow these steps:
Verifying Switch Connectivity
You can verify connectivity to a destination switch.
Note
The FC ID variable used in this procedure is the domain controller address; it is not a duplication of the domain ID.
To verify connectivity to a destination switch, follow these steps:
Configuring a Fabric Analyzer
Fibre Channel protocol analyzers capture, decode, and analyze frames and ordered sets on a link. Existing Fibre Channel analyzers can capture traffic at wire rate speed. They are expensive and support limited frame decoding. Also, to snoop traffic, the existing analyzers disrupt the traffic on the link while the analyzer is inserted into the link.
Cisco has brought protocol analysis within a storage network to a new level with the Cisco Fabric Analyzer. You can capture Fibre Channel control traffic from a switch and decode it without having to disrupt any connectivity, and without having to be local to the point of analysis.
The Cisco Fibre Channel protocol analyzer is based on two popular public-domain software applications:
•
libpcap—See http://www.tcpdump.org.
•
Ethereal—See http://www.ethereal.com.
Note
The Cisco Fabric Analyzer is useful in capturing and decoding control traffic, not data traffic. It is suitable for control path captures, and is not intended for high-speed data path captures.
About the Cisco Fabric Analyzer
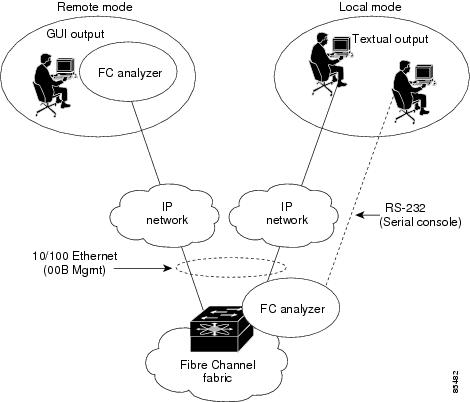
The Cisco Fabric Analyzer consists of two separate components (see Figure 49-1):
•
Software that runs on the Cisco MDS 9000 Family switch and supports two modes of capture:
–
A text-based analyzer that supports local capture and decodes captured frames
–
A daemon that supports remote capture
•
GUI-based client that runs on a host that supports libpcap such as Windows or Linux and communicates with the remote capture daemon in a Cisco MDS 9000 Family switch.
Figure 49-1 Cisco Fabric Analyzer Usage
Local Text-Based Capture
This component is a command-line driven text-based interface that captures traffic to and from the supervisor module in a Cisco MDS 9000 Family switch. It is a fully functional decoder that is useful for quick debug purposes or for use when the remote capture daemon is not enabled. Additionally, because this tool is accessed from within the Cisco MDS 9000 Family switch, it is protected by the roles-based policy that limits access in each switch.
See the "Capturing Frames Locally" section.
Remote Capture Daemon
This daemon is the server end of the remote capture component. The Ethereal analyzer running on a host is the client end. They communicate with each other using the Remote Capture Protocol (RPCAP). RPCAP uses two endpoints, a TCP-based control connection and a TCP or UDP-based data connection based on TCP (default) or UDP. The control connection is used to remotely control the captures (start or stop the capture, or specify capture filters). Remote capture can only be performed to explicitly configured hosts. This technique prevents an unauthorized machine in the network from snooping on the control traffic in the network.
RPCAP supports two setup connection modes based on firewall restrictions.
•
Passive mode (default)—The configured host initiates connection to the switch. Multiple hosts can be configured to be in passive mode and multiple hosts can be connected and receive remote captures at the same time.
•
Active mode—The switch initiates the connection to a configured host—one host at a time.
Using capture filters, you can limit the amount of traffic that is actually sent to the client. Capture filters are specified at the client end—on Ethereal, not on the switch.
See the "Sending Captures to Remote IP Addresses" section.
GUI-Based Client
The Ethereal software runs on a host, such as a PC or workstation, and communicates with the remote capture daemon. This software is available in the public domain from http://www.ethereal.com. The Ethereal GUI front-end supports a rich interface such as a colorized display, graphical assists in defining filters, and specific frame searches. These features are documented on Ethereal's website.
While remote capture through Ethereal supports capturing and decoding Fibre Channel frames from a Cisco MDS 9000 Family switch, the host running Ethereal does not require a Fibre Channel connection to the switch. The remote capture daemon running on the switch sends the captured frames over the out-of-band Ethernet management port. This capability allows you to capture and decode Fibre Channel frames from your desktop or laptop.
See the "Displaying Captured Frames" section.
Configuring the Cisco Fabric Analyzer
You can configure the Cisco Fabric Analyzer to perform one of two captures.
•
Local capture—The command setting to enable a local capture cannot be saved to persistent storage or synchronized to standby. Launches the textual version on the fabric analyzer directly on the console screen. The capture can also be saved on the local file system.
•
Remote capture—The command setting to enable a remote capture can be saved to persistent storage. It can be synchronized to the standby supervisor module and a stateless restart can be issued, if required.
To use the Cisco Fabric Analyzer feature, traffic should be flowing to or from the supervisor module.
Capturing Frames Locally
To capture frames locally, follow these steps:
Sending Captures to Remote IP Addresses
CautionYou must use the eth2 interface to capture control traffic on a supervisor module.
To capture frames remotely, follow these steps:
To capture remote traffic, use one of the following options:
•
The capture interface can be specified in Ethereal as the remote device:
rpcap://<ipaddress or switch hostname>/eth2For example:
rpcap://cp-16/eth2rpcap://17.2.1.1/eth2•
The capture interface can be specified either in the capture dialog box or by using the -i option at the command line when invoking Ethereal.
ethereal -i rpcap://<ipaddress|hostname>[:<port>]/<interface>For example:
ethereal -i rpcap://172.22.1.1/eth2or
ethereal -i rpcap://customer-switch.customer.com/eth2
Note
For example, in a Windows 2000 setup, click Start on your desktop and select Run. In the resulting Run window, type the required command line option in the Open field.
Clearing Configured fcanalyzer Information
Use the clear fcanalyzer command to clear the entire list of configured hosts. Note that the existing connections are not terminated.
Displaying Configured Hosts
Use the show fcanalyzer command to display the list of hosts configured for a remote capture. See Example 49-1.
Example 49-1 Displays Configured Hosts
switch# show fcanalyzerPassiveClient = 10.21.0.3PassiveClient = 10.21.0.3ActiveClient = 10.21.0.3, DEFAULT
Note
The DEFAULT in the ActiveClient line indicates that the default port is used.
Displaying Captured Frames
You can selectively view captured frames by using the display filters feature. For example, instead of viewing all the frames from a capture, you may only want to view Exchange Link Protocol (ELP) request frames. This feature only limits the captured view—it does not affect the captured or the saved frames. Procedures to specify, use, and save display filters are already documented in the Ethereal website (http://www.ethereal.com). Some examples of how you can use this feature are as follows:
•
To view all packets in a specified VSAN, use this expression:
mdshdr.vsan == 2•
To view all SW_ILS frames, use this expression:
fcswils•
To view class F frames, use this expression:
mdshdr.sof == SOFf•
To view all FSPF frames, use this expression:
swils.opcode == HLO || swils.opcode == LSU || swils.opcode == LSA•
To view all FLOGI frames, use this expression:
fcels.opcode == FLOGI•
To view all FLOGI frames in VSAN 1, use this expression:
fcels.opcode == FLOGI && mdshdr.vsan == 2•
To view all name server frames, use this expression:
dNSDefining Display Filters
Display filters limit the frames that can be displayed, but not what is captured (similar to any view command). The filters to be displayed can be defined in multiple ways in the GUI application:
•
Auto-definition
•
Manual definition
•
Assisted manual definition
•
Only manual definition in local capture
•
No assists
Regardless of the definition, each filter must be saved and identified with a name.
Note
This GUI-assisted feature is part of Ethereal and you can obtain more information from http://www.ethereal.com.
Displaying Filters Examples
Some examples of using display filters with the Fabric Analyzer local are provided in this section. The brief option is used in all examples to restrict the size of the output. See Example 49-2.
Example 49-2 Displays Only Fabric Login Server Traffic on VSAN 1
switch(config)# fcanalyzer local brief display-filter (mdshdr.vsan==0x01)&&((fc.d_id==\"ff.ff.fe\"\|\|fc.s_id==\"ff.ff.fe\"))Capturing on eth28.904145 00.00.00 -> ff.ff.fe FC ELS 1 0x28f8 0xffff 0x3 -> 0xf FLOGI8.918164 ff.ff.fe -> 79.03.00 FC ELS 1 0x28f8 0x12c6 0xff -> 0x0 ACC (FLOGI)You can trace all frames to and from a particular N port device. For example, to observe RSCNs from the Fabric Controller and registration and/or query requests to the name server. See Example 49-3.
Note
The filter requires prior knowledge of the FC ID that is assigned to the N port. Issue the show flogi database interface command before running fcanalyzer to obtain the FC ID. In this example, the N port FC ID is 79.03.00.
Example 49-3 Displays All Traffic for a Particular N Port on VSAN 1
switch(config)# fcanalyzer local brief display-filter(mdshdr.vsan==0x01)&&((fc.d_id==\"79.03.00\"\|\|fc.s_id==\"79.03.00\"))Capturing on eth2 8.699162 ff.ff.fe -> 79.03.00 FC ELS 1 0x35b8 0x148e 0xff -> 0x0 ACC (FLOGI) 8.699397 79.03.00 -> ff.ff.fc FC ELS 1 0x35d0 0xffff 0x3 -> 0xf PLOGI 8.699538 ff.ff.fc -> 79.03.00 FC ELS 1 0x35d0 0x148f 0xff -> 0x0 ACC (PLOGI) 8.699406 79.03.00 -> ff.ff.fd FC ELS 1 0x35e8 0xffff 0x3 -> 0xf SCR 8.700179 79.03.00 -> ff.ff.fc dNS 1 0x3600 0xffff 0x3 -> 0xf GNN_FT 8.702446 ff.ff.fd -> 79.03.00 FC ELS 1 0x35e8 0x1490 0xff -> 0x0 ACC (SCR) 8.704210 ff.ff.fc -> 79.03.00 dNS 1 0x3600 0x1491 0xff -> 0x0 ACC (GNN_FT) 8.704383 79.03.00 -> ff.ff.fc dNS 1 0x3618 0xffff 0x3 -> 0xf GPN_ID 8.707857 ff.ff.fc -> 79.03.00 dNS 1 0x3618 0x1496 0xff -> 0x0 ACC (GPN_ID)The VSAN ID is specified in hex. See Example 49-4.
Example 49-4 Displays All Traffic for a Specified VSAN
switch(config)# fcanalyzer local brief display-filter mdshdr.vsan==0x03e7 Capturing on eth2 12.762577 ff.ff.fd -> ff.ff.fd SW_ILS 999 0xb2c 0xffff 0x1 -> 0xf HLO 12.762639 ff.ff.fd -> ff.ff.fd FC 999 0xb2c 0xd32 0xff -> 0x0 Link Ctl, ACK1 13.509979 ff.ff.fd -> ff.ff.fd SW_ILS 999 0xd33 0xffff 0xff -> 0x0 HLO 13.510918 ff.ff.fd -> ff.ff.fd FC 999 0xd33 0xb2d 0x1 -> 0xf Link Ctl, ACK1 14.502391 ff.fc.64 -> ff.fc.70 SW_ILS 999 0xd34 0xffff 0xff -> 0x0 SW_RSCN 14.502545 ff.ff.fd -> 64.01.01 FC ELS 999 0xd35 0xffff 0xff -> 0x0 RSCN 14.502804 64.01.01 -> ff.ff.fd FC ELS 999 0xd35 0x215 0x0 -> 0xf ACC (RSCN) 14.503387 ff.fc.70 -> ff.fc.64 FC 999 0xd34 0xb2e 0x1 -> 0xf Link Ctl, ACK1 14.503976 ff.fc.70 -> ff.fc.64 SW_ILS 999 0xd34 0xb2e 0x1 -> 0xf SW_ACC (SW_RSCN) 14.504025 ff.fc.64 -> ff.fc.70 FC 999 0xd34 0xb2e 0xff -> 0x0 Link Ctl, ACK1By excluding FSPF hellos and ACK1, you can focus on the frames of interest. See Example 49-5.
Example 49-5 Displays All VSAN 1 Traffic Excluding FSPF Hellos and ACK1 Frames.
switch(config)# fcan lo bri dis (mdshdr.vsan==0x01)&¬((swils.opcode==0x14)or(fc.r_ctl==0xc0))Capturing on eth2 10.589934 ff.fc.79 -> ff.fc.7a FC-FCS 1 0x1b23 0xffff 0xff -> 0x0 GCAP 10.591253 ff.fc.7a -> ff.fc.79 FC-FCS 1 0x1b23 0x2f70 0x4 -> 0xf MSG_RJT (GCAP) 25.277981 ff.fc.79 -> ff.fc.7a SW_ILS 1 0x1b27 0xffff 0xff -> 0x0 SW_RSCN 25.278050 ff.fc.79 -> ff.fc.89 SW_ILS 1 0x1b28 0xffff 0xff -> 0x0 SW_RSCN 25.279232 ff.fc.89 -> ff.fc.79 SW_ILS 1 0x1b28 0xadd7 0x5 -> 0xf SW_ACC (SW_RSCN) 25.280023 ff.fc.7a -> ff.fc.79 Unzoned NS 1 0x3b2b 0xffff 0x5 -> 0xf GE_PT 25.280029 ff.fc.7a -> ff.fc.79 SW_ILS 1 0x1b27 0x2f71 0x4 -> 0xf SW_ACC (SW_RSCN) 25.282439 ff.fc.79 -> ff.fc.7a dNS 1 0x3b2b 0x1b29 0xff -> 0x0 RJT (GE_PT) 38.249966 00.00.00 -> ff.ff.fe FC ELS 1 0x36f0 0xffff 0x3 -> 0xf FLOGI 38.262622 ff.ff.fe -> 79.03.00 FC ELS 1 0x36f0 0x1b2b 0xff -> 0x0 ACC (FLOGI) 38.262844 79.03.00 -> ff.ff.fc FC ELS 1 0x3708 0xffff 0x3 -> 0xf PLOGI 38.262984 ff.ff.fc -> 79.03.00 FC ELS 1 0x3708 0x1b2c 0xff -> 0x0 ACC (PLOGI) 38.262851 79.03.00 -> ff.ff.fd FC ELS 1 0x3720 0xffff 0x3 -> 0xf SCR 38.263514 ff.fc.79 -> ff.fc.7a SW_ILS 1 0x1b2e 0xffff 0xff -> 0x0 SW_RSCN 38.263570 ff.fc.79 -> ff.fc.89 SW_ILS 1 0x1b2f 0xffff 0xff -> 0x0 SW_RSCN 38.263630 79.03.00 -> ff.ff.fc dNS 1 0x3738 0xffff 0x3 -> 0xf GNN_FT 38.263884 ff.ff.fd -> 79.03.00 FC ELS 1 0x3720 0x1b2d 0xff -> 0x0 ACC (SCR) 38.264066 ff.fc.89 -> ff.fc.79 SW_ILS 1 0x1b2f 0xaddf 0x5 -> 0xf SW_ACC (SW_RSCN) 38.264417 ff.fc.89 -> ff.fc.79 dNS 1 0xade0 0xffff 0x5 -> 0xf GE_ID 38.264585 ff.fc.79 -> ff.fc.89 dNS 1 0xade0 0x1b31 0xff -> 0x0 ACC (GE_ID) 38.265132 ff.ff.fc -> 79.03.00 dNS 1 0x3738 0x1b30 0xff -> 0x0 ACC (GNN_FT) 38.265210 ff.fc.7a -> ff.fc.79 Unzoned NS 1 0x3b2f 0xffff 0x5 -> 0xf GE_PT 38.265414 79.03.00 -> ff.ff.fc dNS 1 0x3750 0xffff 0x3 -> 0xf GPN_ID 38.265502 ff.fc.7a -> ff.fc.79 SW_ILS 1 0x1b2e 0x2f73 0x4 -> 0xf SW_ACC (SW_RSCN) 38.267196 ff.fc.79 -> ff.fc.7a dNS 1 0x3b2f 0x1b32 0xff -> 0x0 ACC (GE_PT)Use this command to focus on TE port initialization. This example allows two VSANs on the TE port and the port VSAN is 666. Hence the ELP, ESC, and EPP (0x71) go out on VSAN 666. Once the EPP negotiation is complete, we see EFP, DIA, RDI, MR, FSPF, and other updates flow for each allowed VSAN. See Example 49-6.
Example 49-6 Displays SW_ILS Traffic Between Fabric Controllers for all VSANs and Exclude FSPF Hellos and ACK1 Frames.
switch(config)# fcan lo bri dis fc.type==0x22&&((fc.d_id==\"ff.fc.ef\"\|\|fc.s_id==\"ff.fc.ef\"))Warning:Couldn't obtain netmask info (eth2:no IPv4 address assigned).Capturing on eth29.472181 ff.fc.ef -> ff.fc.61 0x5e0a 0xffff SW_ILS ACA9.472777 ff.fc.61 -> ff.fc.ef 0x5e0a 0x5e09 SW_ILS SW_ACC (ACA)9.474551 ff.fc.ef -> ff.fc.61 0x5e0b 0xffff SW_ILS SFC9.475706 ff.fc.61 -> ff.fc.ef 0x5e0b 0x5e0a SW_ILS SW_ACC (SFC)9.476694 ff.fc.ef -> ff.fc.61 0x5e0c 0xffff SW_ILS UFC9.483612 ff.fc.61 -> ff.fc.ef 0x5e0c 0x5e0b SW_ILS SW_ACC (UFC)9.488187 ff.fc.ef -> ff.fc.61 0x5e0d 0xffff SW_ILS RCA9.493703 ff.fc.61 -> ff.fc.ef 0x5e0d 0x5e0c SW_ILS SW_ACC (RCA)This example focuses on zone server changes. Prior knowledge of the domain controller ID is required. The switch domain ID where the fcanalyzer is run is x79, the domain controller is FF.FC.79. See Example 49-7.
Example 49-7 Display Switch Internal Link Services (SW_ILS) Traffic To and From Fabric Domain Controller ff.fc.79
switch(config)# fcan lo bri dis fc.type==0x22&&((fc.d_id==\ ff.fc.79\ \|\|fc.s_id==\"ff.fc.79\"))Capturing on eth264.053927 ff.fc.79 -> ff.fc.7a SW_ILS 0x1e15 0xffff 0xff -> 0x0 ACA64.053995 ff.fc.79 -> ff.fc.89 SW_ILS 0x1e16 0xffff 0xff -> 0x0 ACA64.054599 ff.fc.89 -> ff.fc.79 SW_ILS 0x1e16 0xb1e2 0x5 -> 0xf SW_ACC (ACA)64.054747 ff.fc.7a -> ff.fc.79 SW_ILS 0x1e15 0x3037 0x4 -> 0xf SW_ACC (ACA)64.057643 ff.fc.79 -> ff.fc.7a SW_ILS 0x1e17 0xffff 0xff -> 0x0 SFC64.057696 ff.fc.79 -> ff.fc.89 SW_ILS 0x1e18 0xffff 0xff -> 0x0 SFC64.058788 ff.fc.7a -> ff.fc.79 SW_ILS 0x1e17 0x3038 0x5 -> 0xf SW_ACC (SFC)64.059288 ff.fc.89 -> ff.fc.79 SW_ILS 0x1e18 0xb1e3 0x5 -> 0xf SW_ACC (SFC)64.062011 ff.fc.79 -> ff.fc.7a SW_ILS 0x1e19 0xffff 0xff -> 0x0 UFC64.062060 ff.fc.79 -> ff.fc.89 SW_ILS 0x1e1a 0xffff 0xff -> 0x0 UFC64.073513 ff.fc.7a -> ff.fc.79 SW_ILS 0x1e19 0x3039 0x5 -> 0xf SW_ACC (UFC)64.765306 ff.fc.89 -> ff.fc.79 SW_ILS 0x1e1a 0xb1e4 0x5 -> 0xf SW_ACC (UFC)64.765572 ff.fc.79 -> ff.fc.7a SW_ILS 0x1e1b 0xffff 0xff -> 0x0 RCA64.765626 ff.fc.79 -> ff.fc.89 SW_ILS 0x1e1c 0xffff 0xff -> 0x0 RCA64.766386 ff.fc.7a -> ff.fc.79 SW_ILS 0x1e1b 0x303a 0x4 -> 0xf SW_ACC (RCA)64.766392 ff.fc.89 -> ff.fc.79 SW_ILS 0x1e1c 0xb1e5 0x5 -> 0xf SW_ACC (RCA)
Note
You can find the Fabric Domain Controller address in the Mgmt-Id field in the show fcs ie vsan command output.
switch# show fcs ie vsan 999
IE List for VSAN:999
------------------------------------------------------------------------
IE-WWN IE-Type Mgmt-Id Mgmt-Addr
------------------------------------------------------------------------
23:e7:00:05:30:00:91:5f Switch (Remote) 0xfffc04 10.66.78.51
23:e7:00:05:30:00:9b:9f Switch (Adjacent) 0xfffc01 10.66.78.52
23:e7:00:0d:ec:00:93:81 Switch (Local) 0xfffc79 10.66.78.54
[Total 3 IEs in Fabric]
Capture Filters
You can limit what frames are captured by using the capture filters feature in a remote capture. This feature limits the frames that are captured and sent from the remote switch to the host. For example, you can capture only class F frames. Capture filters are useful in restricting the amount of bandwidth consumed by the remote capture.
Unlike display filters, capture filters restrict a capture to the specified frames. No other frames are visible until you specify a completely new capture.
The syntax for capture filter is different from the syntax for display filters. Capture filters use the Berkeley Packet Filter (BPF) library that is used in conjunction with the libpcap freeware. The list of all valid Fibre Channel capture filter fields are provided later in this section.
Procedures to configure capture filters are already documented in the Ethereal website (http://www.ethereal.com). Some examples of how you can use this feature as follows:
•
To capture frames only on a specified VSAN, use this expression:
vsan = 1•
To capture only class F frames, use this expression:
class_f•
To capture only class Fibre Channel ELS frames, use this expression:
els•
To capture only name server frames, use this expression:
dns•
To capture only SCSI command frames, use this expression:
fcp_cmd
Note
This feature is part of libpcap and you can obtain more information from http://www.tcpdump.org.
Permitted Capture Filters
This section lists the permitted capture filters.
o vsan o src_port_idx o dst_port_idx o sof o r_ctl o d_id o s_id o type o seq_id o seq_cnt o ox_id o rx_id o els o swils o fcp_cmd (FCP Command frames only) o fcp_data (FCP data frames only) o fcp_rsp (FCP response frames only) o class_f o bad_fc o els_cmd o swils_cmd o fcp_lun o fcp_task_mgmt o fcp_scsi_cmd o fcp_status o gs_type (Generic Services type) o gs_subtype (Generic Services subtype) o gs_cmd o gs_reason o gs_reason_expl o dns (name server) o udns (unzoned name server) o fcs (fabric configuration server) o zs (zone server) o fc (use as fc[x:y] where x is offset and y is length to compare) o els (use as els[x:y] similar to fc) o swils (use as swils[x:y] similar to fc) o fcp (use as fcp[x:y] similar to fc) o fcct (use as fcct[x:y] similar to fc)Loop Monitoring Initiation
By default, the loop monitoring is disabled in all switches in the Cisco MDS 9000 Family. When a disk is removed from a loop port, the loop stays active based on the bypass circuit. Thus the disk removal is not known until you try to communicate with the disk. To detect such removals, the disks can be polled periodically (every 20 seconds).
CautionChanges to the loop monitoring feature should be made by an administrator or individual who is completely familiar with switch operations.
Use the fcinterop loop-monitor command to enable loop polling for FL ports in a Cisco MDS 9000 Family switch.
To enable the loop monitoring feature, follow these steps:
The show tech-support Command
The show tech-support command is useful when collecting a large amount of information about your switch for troubleshooting purposes. The output of this command can be provided to technical support representatives when reporting a problem.
The show tech-support command displays the output of several show commands at once. The output from this command varies depending on your configuration. Use the show tech-support command in EXEC mode to display general information about the switch when reporting a problem.
You can choose to have detailed information for each command or even specify the output for a particular interface, module or VSAN. Each command output is separated by line and the command precedes the output.
Note
Explicitly set the terminal length command to 0 (zero) to disable auto-scrolling and enable manual scrolling. Use the show terminal command to view the configured the terminal size. After obtaining the output of this command, remember to reset you terminal length as required (see the "Setting the Terminal Length" section on page 2-18).
Tip
You can save the output of this command to a file by appending > filename to the show tech-support command (see the "Saving Command Output to a File" section on page 2-26). If you save this file, verify you have sufficient space to do so—each of these files may take about 1.8 MB. However, you can zip this file using the gzip filename command (see the "Compressing and Uncompressing Files" section on page 2-26). Copy the zipped file to the required location using the copy command and unzip the file using the gunzip command (see the "Copying Files" section on page 2-25).
The default output of the show tech-support command includes the output of the following commands:
•
show version
•
show environment
•
show module
•
show hardware
•
show running-config
•
show interface
•
show accounting log
•
show process
•
show process log
•
show processes log details
•
show flash
Each command is discussed in both the Cisco MDS 9000 Family Configuration Guide and the Cisco MDS 9000 Family Command Reference. Refer to the Cisco MDS 9000 Family Troubleshooting Guide to obtain debug processes, procedures, and examples.
The show tech-support brief Command
Use the show tech-support brief command to obtain a quick, condensed review of your switch configurations. This command provides a summary of the current running state of the switch.
The show tech-support brief command is useful when collecting information about your switch for troubleshooting purposes. The output of this command can be provided to technical support representatives when reporting a problem.
Tip
You can save the output of this command to a file by appending > filename to the show tech-support brief command (see the "Saving Command Output to a File" section on page 2-26).
Example 49-8 Displays the Condensed View of Switch Configurations
vegas01# show tech-support briefSwitch Name : vegas01Switch Type : DS-X9216-K9-SUPKickstart Image : 1.3(2) bootflash:///m9200-ek9-kickstart-mz.1.3.1.10.binSystem Image : 1.3(2) bootflash:///m9200-ek9-mz.1.3.1.10.binIP Address/Mask : 10.76.100.164/24Switch WWN : 20:00:00:05:30:00:84:9eNo of VSANs : 9Configured VSANs : 1-6,4091-4093VSAN 1: name:VSAN0001, state:active, interop mode:defaultdomain id:0x6d(109), WWN:20:01:00:05:30:00:84:9f [Principal]active-zone:VR, default-zone:denyVSAN 2: name:VSAN0002, state:active, interop mode:defaultdomain id:0x7d(125), WWN:20:02:00:05:30:00:84:9f [Principal]active-zone:<NONE>, default-zone:denyVSAN 3: name:VSAN0003, state:active, interop mode:defaultdomain id:0xbe(190), WWN:20:03:00:05:30:00:84:9f [Principal]active-zone:<NONE>, default-zone:denyVSAN 4: name:VSAN0004, state:active, interop mode:defaultdomain id:0x5a(90), WWN:20:04:00:05:30:00:84:9f [Principal]active-zone:<NONE>, default-zone:denyVSAN 5: name:VSAN0005, state:active, interop mode:defaultdomain id:0x13(19), WWN:20:05:00:05:30:00:84:9f [Principal]active-zone:<NONE>, default-zone:denyVSAN 6: name:VSAN0006, state:active, interop mode:defaultdomain id:0x1f(31), WWN:20:06:00:05:30:00:84:9f [Principal]active-zone:<NONE>, default-zone:denyVSAN 4091: name:VSAN4091, state:active, interop mode:defaultdomain id:0x08(8), WWN:2f:fb:00:05:30:00:84:9f [Principal]active-zone:<NONE>, default-zone:denyVSAN 4092: name:VSAN4092, state:active, interop mode:defaultdomain id:0x78(120), WWN:2f:fc:00:05:30:00:84:9f [Principal]active-zone:<NONE>, default-zone:denyVSAN 4093: name:VSAN4093, state:active, interop mode:defaultdomain id:0x77(119), WWN:2f:fd:00:05:30:00:84:9f [Principal]active-zone:<NONE>, default-zone:deny-------------------------------------------------------------------------------Interface Vsan Admin Admin Status FCOT Oper Oper PortMode Trunk Mode Speed ChannelMode (Gbps)-------------------------------------------------------------------------------fc1/1 1 auto on fcotAbsent -- -- --fc1/2 1 auto on fcotAbsent -- -- --fc1/3 1 auto on fcotAbsent -- -- --fc1/4 1 auto on fcotAbsent -- -- --fc1/5 1 auto on notConnected swl -- --fc1/6 1 auto on fcotAbsent -- -- --fc1/7 1 auto on fcotAbsent -- -- --fc1/8 1 auto on fcotAbsent -- -- --fc1/9 1 auto on fcotAbsent -- -- --fc1/10 1 auto on fcotAbsent -- -- --fc1/11 1 auto on fcotAbsent -- -- --fc1/12 1 auto on fcotAbsent -- -- --fc1/13 1 auto on fcotAbsent -- -- --fc1/14 1 auto on fcotAbsent -- -- --fc1/15 1 auto on fcotAbsent -- -- --fc1/16 1 auto on fcotAbsent -- -- ---------------------------------------------------------------------------------Interface Status Speed(Gbps)-------------------------------------------------------------------------------sup-fc0 up 1-------------------------------------------------------------------------------Interface Status IP Address Speed MTU-------------------------------------------------------------------------------mgmt0 up 10.76.100.164/24 100 Mbps 1500

 Feedback
Feedback