-
Cisco MDS 9000 Family Configuration Guide, Release 2.x
-
New and Changed Information
-
Index
-
Preface
- Part 1 - Getting Started
- Part 2 - Cisco MDS SAN-OS Installation and Switch Management
- Part 3 - Switch Configuration
-
Part 4 - Fabric Configuration
-
Configuring and Managing VSANs
-
Creating Dynamic VSANs
-
Configuring Inter-VSAN Routing
-
Configuring Zones
-
Distributing Device Alias Services
-
Configuring Fibre Channel Routing Services and Protocols
-
Managing FLOGI, Name Server, FDMI, and RSCN Databases
-
Discovering SCSI Targets
-
Configuring FICON
-
Advanced Features and Concepts
-
- Part 5 - Security
- Part 6 - IP Services
- Part 7 - Intelligent Storage Services
- Part 8 - Network and Switch Monitoring
- Part 9 - Traffic Management
- Part 10 - Troubleshooting
-
Table Of Contents
Presenting Fibre Channel Targets as iSCSI Targets
iSCSI Virtual Target Configuration Examples
Presenting iSCSI Hosts as Virtual Fibre Channel Hosts
Example of VSAN membership for iSCSI devices
Advanced VSAN membership for iSCSI hosts
Fibre Channel Zoning Based Access Control
iSCSI ACL Based Access Control
Restricting iSCSI Initiator Authentication
iSCSI Immediate Data and Unsolicited Data Features
iSCSI Interface Advanced Features
Displaying Proxy Initiator Information
Displaying Global iSCSI Information
Displaying iSCSI Virtual Targets
Displaying iSCSI User Information
iSCSI High Availability with Host Running Multi-Path Software
iSCSI HA with Host Not Having Any Multi-Path Software
Storage Port Failover LUN Trespass
Multiple IPS Ports Connected to the Same IP Network
Ethernet PortChannel-Based High Availability
iSCSI Authentication Setup Guidelines and Scenarios
CHAP with Local Password Database
CHAP with External RADIUS Server
iSCSI Transparent Mode Initiator
Target Storage Device Requiring LUN Mapping
About iSCSI Storage Name Services
About iSNS Client Functionality
Creating an iSNS Client Profile
Verifying iSNS Client Configuration
About iSNS Server Functionality
iSCSI Configuration Distribution
Configuring the ESI Retry Count
iSNS Client Registration and Deregistration
Verifying the iSNS Server Configuration
Configuring iSCSI
Cisco MDS 9000 Family IP storage (IPS) services extend the reach of Fibre Channel SANs by using open-standard, IP-based technology. The switch allows IP hosts to access Fibre Channel storage using the iSCSI protocol.
Note
The iSCSI feature is specific to the IPS module and is available in Cisco MDS 9200 Switches or Cisco MDS 9500 Directors.
The Cisco MDS 9216I switch and the 14/2 Multiprotocol Services (MPS-14/2) module also allow you to use Fibre Channel, FCIP, and iSCSI features. The MPS-14/2 module is available for use in any switch in the Cisco MDS 9200 Series or Cisco MDS 9500 Series.
Note
For information on configuring Gigabit Ethernet interfaces, see the "Configuring Gigabit Ethernet Interfaces" section on page 37-4.
This chapter includes the following sections:
•
iSCSI Authentication Setup Guidelines and Scenarios
•
About iSCSI Storage Name Services
•
About iSNS Client Functionality
•
Creating an iSNS Client Profile
•
About iSNS Server Functionality
About iSCSI
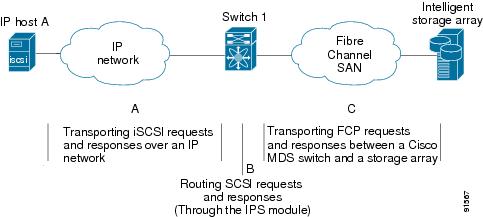
The iSCSI feature consists of routing iSCSI requests and responses between iSCSI hosts in an IP network and Fibre Channel storage devices in the Fibre Channel SAN that are accessible from any Fibre Channel interface of the Cisco MDS 9000 Family switch (see Figure 35-1).
Figure 35-1 Transporting iSCSI Requests and Responses for Transparent iSCSI Routing
Each iSCSI host that requires access to storage through the IPS module or MPS-14/2 module needs to have a compatible iSCSI driver installed. (The Cisco.com website at http://www.cisco.com/cgi-bin/tablebuild.pl/sn5420-scsi provides a list of compatible drivers). Using the iSCSI protocol, the iSCSI driver allows an iSCSI host to transport SCSI requests and responses over an IP network. From the host operating system perspective, the iSCSI driver appears to be a SCSI transport driver similar to a Fibre Channel driver in the host.
The IPS module or MPS-14/2 module provides transparent SCSI routing. IP hosts using the iSCSI protocol can transparently access targets on the Fibre Channel network. Figure 35-1 provides an example of a typical configuration of iSCSI hosts connected to an IPS module or MPS-14/2 module via the IP network access Fibre Channel storage on the Fibre Channel SAN.
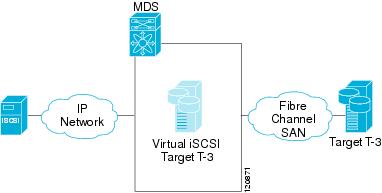
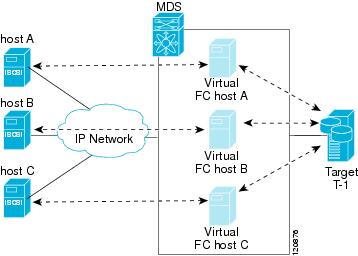
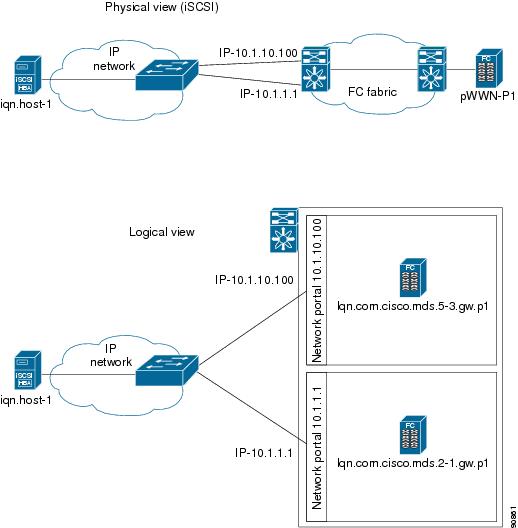
The IPS module or MPS-14/2 module create a separate iSCSI SAN view and Fibre Channel SAN view. For the iSCSI SAN view, the IPS module or MPS-14/2 module create iSCSI virtual targets and then maps them to physical Fibre Channel targets available in the Fibre Channel SAN. They present the Fibre Channel targets to IP hosts as if the physical iSCSI targets were attached to the IP network (see Figure 35-2).
Figure 35-2 iSCSI SAN View—iSCSI virtual targets
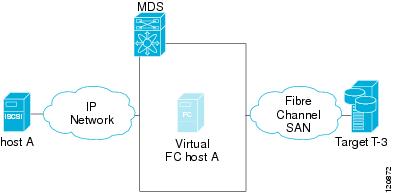
For the Fibre Channel SAN view, the IPS module or MPS-14/2 module presents iSCSI hosts as a virtual Fibre Channel host. The storage devices communicate with the virtual Fibre Channel host similar to communications performed with real Fibre Channel hosts (see Figure 35-3).
Figure 35-3 Fibre Channel SAN View—iSCSHI Host as an HBA
The IPS modules or MPS-14/2 modules transparently map the command between the iSCSI virtual target and the virtual Fibre Channel host (see Figure 35-4).
Figure 35-4 iSCSI to FCP (Fibre Channel) Routing
Routing SCSI from the IP host to the Fibre Channel storage device consists of the following main actions:
•
The iSCSI requests and responses are transported over an IP network between the hosts and the IPS module or MPS-14/2 module.
•
The SCSI requests and responses are routed between the hosts on an IP network and the Fibre Channel storage device (converting iSCSI to FCP and vice versa). The IPS module or MPS-14/2 module performs this conversion and routing.
•
The FCP requests or responses are transported between the IPS module or MPS-14/2 module and the Fibre Channel storage devices.
Note
FCP (the Fibre Channel equivalent of iSCSI) carries SCSI commands over a Fibre Channel SAN.
Refer to the IETF standards for IP storage at http://www.ietf.org for information on the iSCSI protocol.
Configuring iSCSI
This section describes how to configure iSCSI on the Cisco MDS 9000 Family switches.
This section includes the following topics:
•
Presenting Fibre Channel Targets as iSCSI Targets
•
Presenting iSCSI Hosts as Virtual Fibre Channel Hosts
•
iSCSI Immediate Data and Unsolicited Data Features
•
iSCSI Interface Advanced Features
Enabling iSCSI
To use the iSCSI feature, you must explicitly enable iSCSI on the required switches in the fabric. By default, this feature is disabled in all switches in the Cisco MDS 9000 Family.
To enable iSCSI on any participating switch, follow these steps:
CautionWhen you disable this feature, all related configurations are automatically discarded.
Creating iSCSI Interfaces
Each physical GigabitEthernet interface on an IPS module or MPS-14/2 module can be used to translate and route iSCSI requests to Fibre Channel targets and responses in the opposite direction. To enable this capability, the corresponding iSCSI interface must be in an enabled state.
To enable iSCSI interfaces, follow these steps:
Step 1
Enable the required Gigabit Ethernet interface.
switch# config terminalswitch(config)# interface gigabitethernet 2/1switch(config-if)# no shutdownStep 2
Create the required iSCSI interface and enable the interface.
switch(config-if)# exitswitch(config)# interface iscsi 2/1switch(config-if)# no shutdown
Presenting Fibre Channel Targets as iSCSI Targets
The IPS module or MPS-14/2 module presents physical Fibre Channel targets as iSCSI virtual targets allowing them to be accessed by iSCSI hosts. It does this in one of two ways:
•
Dynamic mapping—automatically maps all the Fibre Channel target devices/ports as iSCSI devices. Use this mapping to create automatic iSCSI target names.
•
Static mapping—Manually create iSCSI target devices and map them to the whole Fibre Channel target port or a subset of Fibre Channel LUNs. With this mapping, you must specify unique iSCSI target names.
Static mapping should be used when iSCSI hosts should be restricted to subsets of LUs in the Fibre Channel targets and/or iSCSI access control is needed (see the "iSCSI Access Control" section). Also, static mapping allows configuration of transparent failover if the LUs of the Fibre Channel targets are reachable by redundant Fibre Channel ports (see the "Transparent Target Failover" section).
Note
The IPS module or MPS-14/2 module does not import Fibre Channel targets to iSCSI by default. Either dynamic or static mapping must be configured before the IPS module or MPS-14/2 module makes Fibre Channel targets available to iSCSI initiators.
Dynamic Mapping
When you configure dynamic mapping the IPS module or MPS-14/2 module imports all Fibre Channel targets to the iSCSI domain and maps each physical Fibre Channel target port as one iSCSI target. That is, all LU accessible through the physical storage target port are available as iSCSI LUs with the same LU number (LUN) as in the physical Fibre Channel target port.
The iSCSI target node name is created automatically using the iSCSI qualified name (IQN) format. The iSCSI qualified name is restricted to a maximum name length of 223 alphanumeric characters and a minimum length of 16 characters.
The IPS module or MPS-14/2 module creates an IQN formatted iSCSI target node name using the following conventions because the name must be unique in the SAN:
•
IPS Gigabit Ethernet ports that are not part of a VRRP group or PortChannel use this format:
iqn.1987-05.com.cisco:05.<mgmt-ip-address>.<slot#>-<port#>-<sub-intf#>.<Target-pWWN>•
IPS ports that are part of a VRRP group use this format:
iqn.1987-05.com.cisco:05.vrrp-<vrrp-ID#>-<vrrp-IP-addr>.<Target-pWWN>•
Ports that are part of a PortChannel use this format:
iqn.1987-02.com.cisco:02.<mgmt-ip-address>.pc-<port-ch-sub-intf#>.<Target-pWWN>
Note
If you have configured a switch name, then the switch name is used instead of the management IP address. If you have not configured a switch name, the management IP address is used.
With this convention, each IPS port in a Cisco MDS 9000 Family switch creates a unique iSCSI target node name for the same Fibre Channel target port in the SAN.
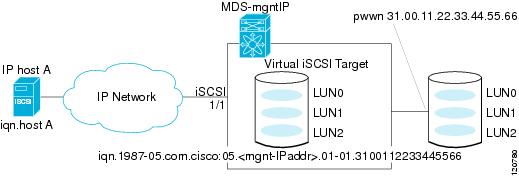
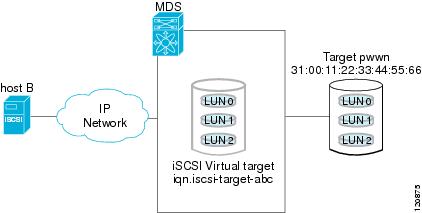
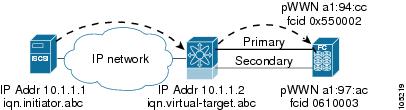
For example, if an iSCSI target was created for a Fibre Channel target port with pWWN 31:00:11:22:33:44:55:66 and that pWWN contains LUN 0, LUN 1, and LUN 2, those LUNs would become available to an IP host via the iSCSI target node name iqn.1987-05.com.cisco:05.<MDS_switch_management_IP_address>.01-01.3100112233445566 (see Figure 35-5).
Figure 35-5 Dynamic Target Mapping
Note
Each iSCSI initiator may not have access to all targets depending on the configured access control mechanisms (see "iSCSI Access Control" section).
To enable dynamic importing of Fibre Channel targets into iSCSI, follow these steps:
Static Mapping
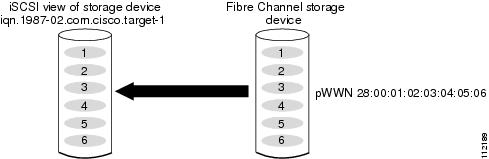
You can manually (statically) create an iSCSI target by assigning a user-defined unique iSCSI node name to it. The iSCSI qualified name is restricted to a minimum length of 16 characters and a maximum of 223 characters. A statically mapped iSCSI target can either map the whole Fibre Channel target port (all LUNs in the target port mapped to the iSCSI target), or it can contain one or more LUs from a Fibre Channel target port (see Figure 35-1).
Figure 35-6 Statically Mapped iSCSI Targets
To create a static iSCSI virtual target for the entire Fibre Channel target port, follow these steps:
Tip
An iSCSI target cannot contain more than one Fibre Channel target port. If you have already mapped the whole Fibre Channel target port, you cannot use the LUN mapping option.
Note
See the "iSCSI ACL Based Access Control" section for more information on controlling access to statically-mapped targets.
Advertising Static iSCSI Targets
You can limit the Gigabit Ethernet interfaces via which static iSCSI targets are advertised. By default iSCSI targets are advertised on all Gigabit Ethernet interfaces, subinterfaces, PortChannel interfaces, and PortChannel subinterfaces.
To configure a specific interface that should advertise the iSCSI virtual target, follow these steps:
iSCSI Virtual Target Configuration Examples
This section provides three examples of iSCSI virtual target configurations.
Example 1
This example assigns the whole Fibre Channel target as a iSCSI virtual target. All LUNs that are part of the Fibre Channel target are available as part of the iSCSI target (see Figure 35-7).
Figure 35-7 Assigning iSCSI Node Names
iscsi virtual-target name iqn.1987-02.com.cisco.target-1pWWN 28:00:01:02:03:04:05:06Example 2
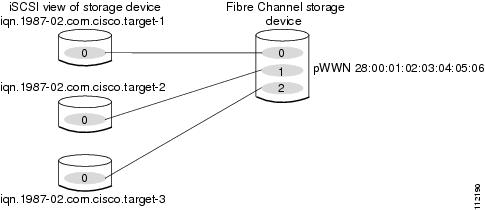
This example maps a subset of LUNs of a Fibre Channel target to three iSCSI virtual targets. Each iSCSI target only has one LUN (see Figure 35-8).
Figure 35-8 Mapping LUNs to a iSCSI Node Name
iscsi virtual-target name iqn.1987-02.com.cisco.target-1pWWN 28:00:01:02:03:04:05:06 fc-lun 0 iscsi-lun 0iscsi virtual-target name iqn.1987-02.com.cisco.target-2pWWN 28:00:01:02:03:04:05:06 fc-lun 1 iscsi-lun 0iscsi virtual-target name iqn.1987-02.com.cisco.target-3pWWN 28:00:01:02:03:04:05:06 fc-lun 2 iscsi-lun 0Example 3
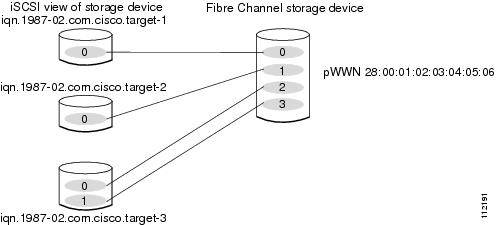
This example maps three subsets of Fibre Channel LUN targets to three iSCSI virtual targets. Two iSCSI targets have one LUN and the third iSCSI target has two LUNs (see Figure 35-8).
Figure 35-9 Mapping LUNs to Multiple iSCSI Node Names
iscsi virtual-target name iqn.1987-02.com.cisco.target-1pWWN 28:00:01:02:03:04:05:06 fc-lun 0 iscsi-lun 0iscsi virtual-target name iqn.1987-02.com.cisco.target-2pWWN 28:00:01:02:03:04:05:06 fc-lun 1 iscsi-lun 0iscsi virtual-target name iqn.1987-02.com.cisco.target-3pWWN 28:00:01:02:03:04:05:06 fc-lun 2 iscsi-lun 0pWWN 28:00:01:02:03:04:05:06 fc-lun 3 iscsi-lun 1Presenting iSCSI Hosts as Virtual Fibre Channel Hosts
The IPS module or MPS-14/2 module connects to the Fibre Channel storage devices on behalf of the iSCSI host to send commands and transfer data to and from the storage devices. These modules use a virtual Fibre Channel N port to access the Fibre Channel storage devices on behalf of the iSCSI host. iSCSI hosts are identified by either iSCSI qualified name (IQN) or IP address.
Initiator Identification
iSCSI hosts can be identified by the IPS module or MPS-14/2 module using the following:
•
iSCSI qualified name (IQN)
An iSCSI initiator is identified based on the iSCSI node name it provides in the iSCSI login. This mode can be useful if an iSCSI host has multiple IP address and you want to provide the same service independent of the IP address used by the host. An initiator with multiple IP addresses (multiple network interface cards—NICs) has one virtual N port on each IPS port to which it logs in.
•
IP address
An iSCSI initiator is identified based on the IP address of the iSCSI host. This mode is useful if an iSCSI host has multiple IP addresses and you want to provide different service based on the IP address used by the host. It is also easier to get the IP address of a host compared to getting the iSCSI node name. A virtual N port is created for each IP address it uses to log in to iSCSI targets. If the host using one IP address logs in to multiple IPS ports, each IPS port will create one virtual N port for that IP address.
You can configure the iSCSI initiator identification mode on each IPS port and all the iSCSI hosts terminating on the IPS port will be identified according to that configuration. The default mode is to identify the initiator by name.
To specify the initiator identification mode, follow these steps:
Initiator Presentation Modes
Two modes are available to present iSCSI hosts in the Fibre Channel fabric: transparent initiator mode and proxy initiator mode.
•
In transparent initiator mode, each iSCSI host is presented as one virtual Fibre Channel host. The benefit of transparent mode is it allows a finer-level of Fibre Channel access control configuration (similar to managing a "real" Fibre Channel host). Because of the one-to-one mapping from iSCSI to Fibre Channel, each host can have different zoning or LUN access control on the Fibre Channel storage device.
•
In proxy-initiator mode, there is only one virtual Fibre Channel host per one IPS port and all iSCSI hosts use that to access Fibre Channel targets. In a scenario where the Fibre Channel storage device requires explicit LUN access control for every host, the static configuration for each iSCSI initiator can be overwhelming. In such case, using the proxy-initiator mode simplifies the configuration.
The Cisco MDS switches support the following iSCSI session limits:
•
The maximum number of iSCSI sessions on a switch is 5000.
•
The maximum number of iSCSI sessions per IPS port in transparent initiator mode is 500.
•
The maximum number of iSCSI sessions per IPS port in proxy initiator mode is 250.
•
The maximum number of concurrent iSCSI sessions allowed per port is 10.
Note
If more than 10 iSCSI sessions try to come up simultaneously on a port, the initiator receives a temporary error and later retries to create a session.
Transparent Initiator Mode
Each iSCSI host is presented as one virtual Fibre Channel host (that is, one Fibre Channel N port). The benefit of transparent mode is it allows a finer-level of Fibre Channel access control configuration. Because of the one-to-one mapping from iSCSI to Fibre Channel, each host can have different zoning or LUN access control on the Fibre Channel storage device.
When an iSCSI host connects to the IPS module or MPS-14/2 module, a virtual host N port (HBA port) is created for the host (see Figure 35-9). Every Fibre Channel N port requires a unique Node WWN and Port WWN.
Figure 35-10 Virtual Host HBA Port
After the virtual N port is created with the WWNs, a Fabric Login (FLOGI) is done via the virtual iSCSI interface of the IPS port. After the FLOGI is completed, the virtual N port is on-line in the Fibre Channel SAN and virtual N port is registered in the Fibre Channel Name Server. The IPS module or MPS-14/2 module registers the following entries in the Fibre Channel Name Server:
•
IP address of the iSCSI host in the IP-address field on the Name Server
•
IQN of the iSCSI host in the symbolic-node-name field of the Name Server
•
SCSI_FCP in the FC-4 type field of the name server
•
Initiator flag in the FC-4 feature of the name server
•
Vendor-specific iSCSI GW flag in the FC-4 type field to identify the N-port device as a iSCSI gateway device in the NS.
When all the iSCSI sessions from the iSCSI host are terminated, the IPS modules or MPS-14/2 modules perform an explicit Fabric logout (FLOGO) to remove the virtual N-port device from the Fibre Channel SAN (this indirectly de-registers the device from the Fibre Channel Name Server).
For every iSCSI session from the host to the iSCSI virtual target there is a corresponding Fibre Channel session to the real Fibre Channel target. In Figure 35-10, there are three iSCSI hosts and all three of them connect to the same Fibre Channel target. There is one Fibre Channel session from each of the three virtual Fibre Channel hosts to the target.
iSCSI Initiator Idle Timeout
iSCSI initiator idle timeout specifies the time for which the virtual Fibre Channel N port is kept idle after the initiator logs out from its last iSCSI session. The default value for this timer is 300 seconds. This is useful to avoid N ports logging in to and logging off of the Fibre Channel SAN as transient failure occurs in the IP network. This helps reduce unnecessary RSCNs being generated in the Fibre Channel SAN.
To configure the initiator idle timeout, follow these steps
:
WWN Assignment for iSCSI Initiators
An iSCSI host is mapped to an N port's WWNs by one of the following mechanisms:
•
Dynamic mapping (default)
•
Static mapping
Dynamic Mapping
With dynamic mapping, an iSCSI host is mapped to a dynamically generated port WWN (pWWN) and node WWN (nWWN). Each time the iSCSI host connects it might be mapped to a different WWN. Use this option if no access control is required on Fibre Channel target device (because the target device access control is usually configured using the host WWN).
The WWNs are allocated from the MDS switch's WWN pool. The WWN mapping to the iSCSI host is maintained as long as the iSCSI host has at least one iSCSI session to the IPS port. When all iSCSI sessions from the host are terminated and the IPS module or MPS-14/2 module performs an FLOGO for the virtual N port of the host, the WWNs are released back to the switch's Fibre Channel WWN pool. These addresses are then available for assignment to other iSCSI hosts requiring access to the Fibre Channel Fabric.
Dynamic mapping is the default mode of operation.
Static Mapping
With static mapping, an iSCSI host is mapped to a specific pWWN and nWWN. This mapping is maintained in persistent storage and each time the iSCSI host connects, the same WWN mapping is used. This mode is required if you use access control on the target device.
You can implement static mapping in one of two ways:
•
User assignment—You can specify your own unique WWN by providing them during the configuration process.
•
System assignment—You can request that the switch should provide a WWN from the switch's Fibre Channel WWN pool and keep the mapping in its configuration.
Tip
We recommend using the system-assign option. If you manually assign a WWN, you must ensure its uniqueness (see the "Configuring World Wide Names" section on page 25-5). You should not use any previously-assigned WWNs.
To configure static mapping (using the name option) for an iSCSI initiator, follow these steps:
To configure static mapping (using the ip-address option) for an iSCSI initiator, follow these steps:
To assign the WWN for an iSCSI initiator, follow these steps:
Note
If the system-assign option is used to configure WWNs for an iSCSI initiator, when the configuration is saved to an ASCII file the system-assigned WWNs are also saved. Subsequently if you perform a write erase, you must manually delete the WWN configuration from the ASCII file. Failing to do so can cause duplicate WWN assignments if the ASCII configuration file is reapplied on the switch.
Making the Dynamic Initiator WWN Mapping Static
After a dynamic initiator has already logged in, you may decide to permanently keep the automatically assigned nWWN/pWWN mapping so this initiator uses the same mapping the next time it logs in.
To permanently keep the automatically assigned nWWN/pWWN mapping, follow these steps:
Checking for WWN Conflicts
Prior to Cisco MDS SAN-OS Release 2.1(2), WWNs assigned to static iSCSI initiators by the system can be inadvertently returned to the system when an upgrade fails or you downgrade the system software (manually booting up an older Cisco MDS SAN-OS release without using the install all command). In these instances, the system can later assign those WWNs to other iSCSI initiators (dynamic or static) and cause conflicts.
As of Cisco MDS SAN-OS Release 2.1(2), you can fix this problem by checking for and removing any configured WWNs that belong to the system whenever such scenarios occur.
To check for and remove WWN conflicts, follow these steps:
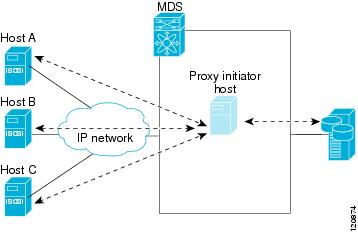
Proxy-Initiator Mode
In the event that the Fibre Channel storage device requires explicit LUN access control for every host using the transparent initiator mode (presenting one iSCSI host as one Fibre Channel host) means every iSCSI host has to be configured statically. This can mean several configuration tasks for each iSCSI host. In this case, using the proxy-initiator mode simplifies the configuration.
In this mode, only one virtual host N port (HBA port) is created per IPS port. All the iSCSI hosts connecting to that IPS port will be multiplexed using the same virtual host N port (see Figure 35-11). This mode simplifies the task of statically binding WWNs. LUN mapping and assignment on the Fibre Channel storage array must be configured to allow access from the proxy virtual N port's pWWN for all LUNs used by each iSCSI initiator which connects through this IPS port. The LUN is then assigned to each iSCSI initiator by configuring iSCSI virtual targets (see the "Static Mapping" section) with LUN mapping and iSCSI access control (see the "iSCSI Access Control" section).
Figure 35-11 Multiplexing IPS Ports
Proxy initiator mode can be configured on a per IPS port basis, in which case only iSCSI initiators terminating on that IPS port will be in this mode.
When a IPS port is configured in proxy-initiator mode, Fabric Login (FLOGI) is done via the virtual iSCSI interface of the IPS port. After the FLOGI is completed, the proxy-initiator virtual N port is on-line in the Fibre Channel Fabric and virtual N port is registered in the Fibre Channel Name Server. The IPS module or MPS-14/2 module registers the following entries in the Fibre Channel Name Server:
•
iSCSI interface name iSCSI slot /port is registered in the symbolic-node-name field Name Server
•
SCSI_FCP in the FC-4 type field of the name server
•
Initiator flag in the FC-4 feature of the name server
•
Vendor specific flag (iscsi-gw) in the FC-4 type field to identify the N-port device as a iSCSI gateway device in the name server
Similar to transparent initiator mode, user can provide a pWWN and nWWN or request a system assigned WWN for the proxy initiator N port.
To configure the proxy initiator, follow these steps:
Note
When an interface is in proxy initiator mode, you can only configure Fibre Channel access control (zoning) based on the iSCSI interface's proxy N port attributes—the WWN pairs or the FCID. You cannot configure zoning using iSCSI attributes such as IP address or IQN of the iSCSI initiator. To enforce initiator-based access control, use iSCSI based access control (see the "iSCSI Access Control" section).
VSAN Membership for iSCSI
Similar to Fibre Channel devices, iSCSI devices have two mechanisms by which VSAN membership can be defined.
•
iSCSI host—VSAN membership to iSCSI host (This method takes precedent over the iSCSI interface.)
•
iSCSI interface—VSAN membership to iSCSI interface (All iSCSI hosts connecting to this iSCSI interface inherit the interface VSAN membership if the host is not configured in any VSAN by the iSCSI host method.)
VSAN Membership for iSCSI Hosts
Individual iSCSI hosts can be configured to be in a specific VSAN (similar to the DPVM feature for Fibre Channel, see Chapter 17, "Creating Dynamic VSANs"). The specified VSAN overrides the iSCSI interface VSAN membership.
To assign VSAN membership for iSCSI hosts, follow these steps:
Note
When an initiator is configured in any other VSAN (other than VSAN 1), for example VSAN 2, the initiator is automatically removed from VSAN 1. If you also want it to be present in VSAN 1, you must explicitly configure the initiator in VSAN 1.
VSAN Membership for iSCSI Interfaces
VSAN membership can be configured for an iSCSI interface, called the port VSAN. All the iSCSI devices that connect to this interface automatically become members of this VSAN, if it is not explicitly configured in a VSAN. In other words, the port VSAN of an iSCSI interface is the default VSAN for all dynamic iSCSI initiators. The default port VSAN of an iSCSI interface is VSAN 1.
Tip
This feature was introduced in Cisco SAN-OS Release 1.3(1). If you downgrade to an earlier release, be sure to delete any assigned VSAN and to issue the no iscsi interface vsan-membership command before performing the downgrade procedure.
To change the default port VSAN, follow these steps:
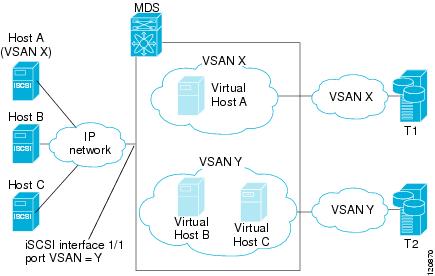
Example of VSAN membership for iSCSI devices
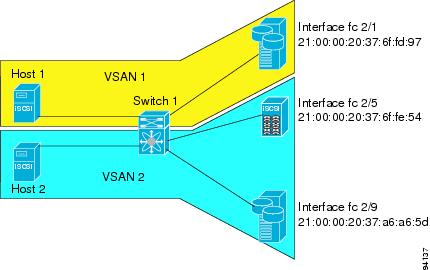
Figure 35-12 provides an example of VSAN membership for iSCSI devices:
•
iSCSI interface 1/1 is member of VSAN Y
•
iSCSI initiator host-A has explicit VSAN membership to VSAN X
•
Three iSCSI initiators host-A, host-B, Host-C connect to iSCSI interface 1/1
Figure 35-12 VSAN Membership for iSCSI Interfaces
Host A's virtual Fibre Channel N port will be added to VSAN X because of explicit membership for the initiator. The virtual host-B and host-C N ports do not have any explicit membership configuration so will inherit the iSCSI interface VSAN membership and be part of VSAN Y.
Advanced VSAN membership for iSCSI hosts
An iSCSI host can be a member of multiple VSANs. In this case multiple virtual Fibre Channel host are created, one in each VSAN in which the iSCSI host is a member. This configuration is useful when certain resources such as Fibre Channel tape devices need to be shared among different VSANs.
iSCSI Access Control
Two mechanisms of access control are available for iSCSI devices.
•
Fibre Channel based zoning access control
•
iSCSI ACL-based access control
Depending on the initiator mode used to present the iSCSI hosts in the Fibre Channel Fabric, either or both the access control mechanisms can be used.
Fibre Channel Zoning Based Access Control
SAN-OS VSAN and zoning concepts has been extended to cover both Fibre Channel devices and iSCSI devices. Zoning is the standard access control mechanism for Fibre Channel devices which is applied within the context of a VSAN. Fibre Channel zoning has been extended to support iSCSI devices and their extension has the advantage of having a uniform, flexible access control mechanism across the whole SAN.
Common mechanisms of identifying members in Fibre Channel Zone are the following (see Chapter 19, "Configuring and Managing Zones" for details of Fibre Channel Zoning):
•
Fibre Channel device pWWN
•
Interface and Switch WWN. Device connecting via that interface is within the zone:
In the case of iSCSI, behind an iSCSI interface multiple iSCSI devices may be connected. Interface based zoning may not be useful because all the iSCSI devices behind the interface will automatically be within the same zone.
In transparent initiator mode (where one Fibre Channel virtual N port is created for each iSCSI host as described in the "Transparent Initiator Mode" section) if an iSCSI host has static WWN mapping then the standard Fibre Channel deice pWWN-based zoning membership mechanism can be used.
Zoning membership mechanism has been enhanced to add iSCSI devices to zones based on the following:
•
IP address/mask (IP subnet)
•
Symbolic-node-name (IQN)
For iSCSI hosts that do not have a static WWN mapping, the feature allows the IP address or iSCSI node name to be specified as zone members. Note that iSCSI hosts that have static WWN mapping can also use these features. IP address based zone membership allows multiple devices to be specified in one command by providing the subnet mask.
Note
In proxy initiator mode, all iSCSI devices connecting to an IPS port gain access to the Fibre Channel fabric via a single virtual Fibre Channel N port. Thus, zoning based on the iSCSI node name or IP address will not have any effect. If zoning based on pWWN is used then all iSCSI devices connecting to that IPS port will be put in the same zone. To implement individual initiator access control in proxy initiator mode, configure a iSCSI ACL on the virtual target (see the "iSCSI ACL Based Access Control" section).
To add an iSCSI initiator to the zone database, follow these steps:
iSCSI ACL Based Access Control
iSCSI based access control is applicable only if static iSCSI virtual targets are created (see the "Static Mapping" section). For a static iSCSI target, you can configure a list of iSCSI initiators that are allowed to access the targets.
By default, static iSCSI virtual targets are not accessible to any iSCSI host. You must explicitly configure accessibility to allow a iSCSI virtual target to be accessed by all hosts. The initiator access list can contain one or more initiators. The iSCSI initiator can be identified by one of the following mechanisms:
•
iSCSI node name
•
IP address
•
IP subnet
Note
For transparent mode iSCSI initiator, if both Fibre Channel zoning and iSCSI ACLs are used, then for every static iSCSI target that is accessible to the iSCSI host, the initiator's virtual N port should be in the same Fibre Channel zone as the Fibre Channel target.
To configure access control in iSCSI, follow these steps:
Enforcing Access Control
IPS modules and MPS-14/2 modules use both iSCSI and Fibre Channel zoning-based access control lists to enforce access control. Access control is enforced both during the iSCSI discovery phase and the iSCSI session creation phase. Access control enforcement is not required during IO phase because the IPS module or MPS-14/2 module is responsible for the routing of iSCSI traffic to Fibre Channel.
•
iSCSI discovery phase—When an iSCSI host creates an iSCSI discovery session and queries for all iSCSI targets, the IPS module or MPS-14/2 module returns only the list of iSCSI targets this iSCSI host is allowed to access based on the access control policies discussed in the previous section. The IPS module or MPS-14/2 module does this by querying the Fibre Channel name server for all the devices in the same zone as the initiator in all VSANs. It then filters out the devices that are initiator by looking at the FC4-feature field of the FCNS entry. (If a device does not register as either initiator or target in the FC4-feature field, the IPS module or MPS-14/2 module will advertise it). It then responds to the iSCSI host with the list of targets. Each will have either a static iSCSI target name that you configure or a dynamic iSCSI target name that the IPS module or MPS-14/2 module creates for it (see the "Dynamic Mapping" section).
•
iSCSI session creation—When an IP host initiates an iSCSI session, the IPS module or MPS-14/2 module verifies if the specified iSCSI target (in the session login request) is allowed by both the access control mechanisms described in previous section.
If the iSCSI target is a static mapped target, the IPS module or MPS-14/2 module verifies if the iSCSI host is allowed within the access list of the iSCSI target. If the IP host does not have access, its login is rejected. If the iSCSI host is allowed, it validates if the virtual Fibre Channel N port used by the iSCSI host and the Fibre Channel target mapped to the static iSCSI virtual target are in the same Fibre Channel zone.
If the iSCSI target is an auto-generated iSCSI target, then the IPS module or MPS-14/2 module extracts the WWN of the Fibre Channel target from the iSCSI target name and verifies if the initiator and the Fibre Channel target is in the same Fibre Channel zone or not. If they are, then access is allowed.
The IPS module or MPS-14/2 module uses the Fibre Channel virtual N port of the iSCSI host and does a zone-enforced name server query for the Fibre Channel target WWN. If the FCID is returned by the name server, then the iSCSI session is accepted. Otherwise, the login request is rejected.
iSCSI Session Authentication
The IPS module or MPS-14/2 module supports iSCSI authentication mechanism to authenticate iSCSI hosts that request access to storage. By default, IPS module or MPS-14/2 modules allow CHAP or None authentication of iSCSI initiators. If authentication should always be used, you must configure the switch to allow only CHAP authentication.
For CHAP username or secret validation you can use any method supported and allowed by the Cisco MDS AAA infrastructure (see Chapter 28, "Configuring RADIUS and TACACS+"). AAA authentication supports RADIUS, TACACS+, or local authentication device.
The aaa authentication iscsi command enables aaa authentication for the iSCSI host and specifies the method to use.
To configure AAA authentication for an iSCSI user, follow these steps:
Authentication Mechanism
You can configure iSCSI CHAP or None authentication at both the global level and at each interface level.
The authentication for a Gigabit Ethernet interface or subinterface overrides the authentication method configured at the global level.
If CHAP authentication should always be used, issue the iscsi authentication chap command at either the global level or at a per-interface level. If authentication should not be used at all, issue the iscsi authentication none command.
To configure the authentication mechanism for iSCSI, follow these steps:
To configure the authentication mechanism for iSCSI sessions to a particular interface, follow these steps:
Local Authentication
See the "Configuring User Accounts" section on page 26-10 to create the local password database. To create new users in the local password database for the iSCSI initiator, the iSCSI keyword is mandatory.
To configure iSCSI users for local authentication, follow these steps:
Restricting iSCSI Initiator Authentication
By default, the iSCSI initiator can use any user name in RADIUS or local database in authenticating itself to the IPS module or MPS-14/2 module (the CHAP user name is independent of the iSCSI initiator name). The IPS module or MPS-14/2 module allows the initiator to login as long as it provides a correct response to the CHAP challenge sent by the switch. This can be a problem if one CHAP user name and password had been compromised.
To restrict an initiator to use a specific user name for CHAP authentication, follow these steps:
Mutual CHAP Authentication
In addition to the IPS module or MPS-14/2 module authentication of the iSCSI initiator, the IPS module or MPS-14/2 module also supports a mechanism for the iSCSI initiator to authenticate the Cisco MDS switch's iSCSI target during the iSCSI login phase. This authentication requires the user to configure a username and password for the switch to present to the iSCSI initiator. The provided password is used to calculate a CHAP response to a CHAP challenge sent to the IPS port by the initiator.
To configure a global iSCSI target username and password to be used by the switch to authenticate itself to an initiator, follow these steps:
To configure a per-initiator iSCSI target's user name and password used by the switch to authenticate itself to an initiator, follow these steps:
Use the show running-config and the show iscsi global (see Example 35-6) commands to display the global configuration Use the show running-config and the show iscsi initiator configured (see Example 35-14) commands to display the initiator specific configuration.
iSCSI Immediate Data and Unsolicited Data Features
Cisco MDS SAN-OS Release 2.1(1a), and later, supports the iSCSI immediate data and unsolicited data features if requested by the initiator during the login negotiation phase. Immediate data is iSCSI write data contained in the data segment of an iSCSI command protocol data unit (PDU), such as combining the write command and write data together in one PDU. Unsolicited data is iSCSI write data that an initiator sends to the iSCSI target, such as an MDS switch, in an iSCSI data-out PDU without having to receive an explicit ready to transfer (R2T) PDU from the target.
These two features help reduce I/O time for small write commands because it removes one round-trip between the initiator and the target for the R2T PDU. As an iSCSI target, the MDS switch allows up to 64 KB of unsolicited data per command. This is controlled by the FirstBurstLength parameter during iSCSI login negotiation phase.
If an iSCSI initiator supports immediate data and unsolicited data features, these features are automatically enabled on the MDS switch with no configuration required.
iSCSI Interface Advanced Features
Advanced configuration options are available for iSCSI interfaces on a per-IPS port basis. These configurations are similar to the advanced FCIP configurations and are already explained in that section (see the "Advanced FCIP Interface Configuration" section on page 33-12).
To access these commands from the iSCSI interface, follow these steps:
Step 1
switch# config t
switch(config)#
Enters configuration mode.
Step 2
switch(config)# interface iscsi 4/1
switch(config-if)#
Selects the iSCSI interface on the switch.
Cisco MDS switches support the following advanced features for iSCSI interfaces.
iSCSI Listener Port
You can configure the TCP port number for the iSCSI interface which listens for new TCP connections. The default port number is 3260. Once you change the TCP port number, the iSCSI port only accepts TCP connections on the newly configured port.
See the "Configuring TCP Listener Ports" section on page 33-7)
TCP Tuning Parameters
You can configure the following TCP parameters.
•
The minimum retransmit timeout, keepalive timeout, maximum retransmissions, path MTU, SACK (SACK is enabled by default for iSCSI TCP configurations), window management (The iSCSI defaults are max-bandwidth = 1G, min-available-bandwidth = 70 Mbps, and round-trip-time =1 ms.), buffer size (default send buffer size for iSCSI is 4096 KB), window congestion (enabled by default and the default burst size is 50 KB), and maximum delay jitter (enabled by default and the default time is 500 microseconds.).
See the "Minimum Retransmit Timeout" section on page 33-8, "Keepalive Timeout" section on page 33-8, "Maximum Retransmissions" section on page 33-9, "Path MTUs" section on page 33-9, "Monitoring Congestion" section on page 33-10 and "Estimating Maximum Jitter" section on page 33-11.
QoS
To set the QoS values, follow these steps:
iSCSI Routing Modes
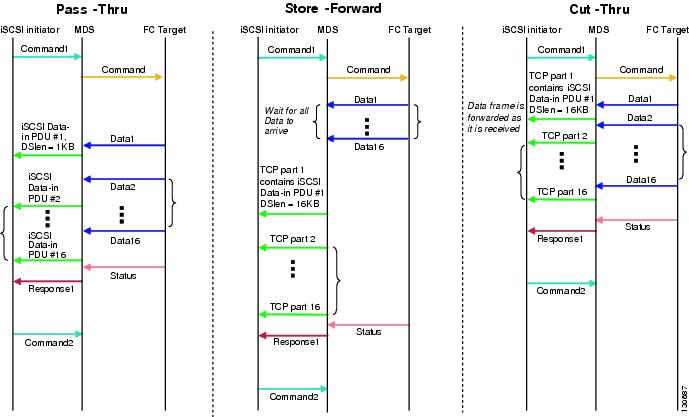
Cisco MDS 9000 Family switches support multiple iSCSI routing modes. Each mode negotiates different operational parameters, has different advantages and disadvantages, and is suitable for different usages.
•
Pass-thru mode
In pass-thru mode, the port on the IPS module or MPS 14/2 module converts and forwards read data frames from the Fibre Channel target to the iSCSI host frame-by-frame without buffering. This means that one data-in frame received is immediately sent out as one iSCSI data-in PDU.
In the opposite direction, the port on the IPS module or MPS 14/2 module limits the maximum size of iSCSI write data-out PDU that the iSCSI host can send to the maximum data size that the Fibre Channel target specifies that it can receive. The result is one iSCSI data-out PDU received sent out as one Fibre Channel data frame to the Fibre Channel target.
The absence of buffering in both directions leads to an advantage of lower forwarding latency. However, a small maximum data segment length usually results in lower data transfer performance from the host due to a higher processing overhead by the host system. Another benefit of this mode is iSCSI data digest can be enabled. This helps protect the integrity of iscsi data carried in the PDU over what TCP checksum offers.
•
Store-and-forward mode (default)
In store-and-forward mode, the port on the IPS module or MPS 14/2 module assembles all the Fibre Channel data frames of an exchange to build one large iSCSI data-in PDU before forwarding it to the iSCSI client.
In the opposite direction, the port on the IPS module or MPS 14/2 module does not impose a small data segment size on the host so the iSCSI host can send an iSCSI data-out PDU of any size (up to 256 KB). The port then waits until the whole iSCSI data-out PDU is received before it converts, or splits, the PDU, and forwards Fibre Channel frames to the Fibre Channel target.
The advantage of this mode is higher data transfer performance from the host. The disadvantages are higher transfer latency and that the iSCSI data digest (CRC) cannot be used.
Note
The store-and-forward mode is the default forwarding mode.
•
Cut-through mode
Cut-through mode improves the read operation performance over store-and-forward mode. The port on the IPS module or MPS 14/2 module achieves this by forwarding each Fibre Channel data-in frame to the iSCSI host as it is received without waiting for the whole exchange complete. There is no difference for write data-out operations from store-and-forward mode.
Figure 35-13 compares the messages exchanged by the iSCSI routing modes.
Figure 35-13 iSCSI Routing Modes
Table 35-1 compares the advantages and dissuasiveness of the different iSCSI routing modes.
To set the iSCSI routing mode, follow these steps:
Displaying iSCSI Information
Use the show iscsi command to obtain detailed informations about iSCSI configurations.
Displaying iSCSI Interfaces
Use the show iscsi interface command to view the summary, counter, description, and status of the iSCSI interface. Use the output to verify the administrative mode, the interface status, TCP parameters currently used, and brief statistics.
Example 35-1 Displays the iSCSI Interface Information
switch# show interface iscsi 4/1iscsi4/1 is upHardware is GigabitEthernetPort WWN is 20:cf:00:0c:85:90:3e:80Admin port mode is ISCSIPort mode is ISCSISpeed is 1 GbpsiSCSI initiator is identified by nameNumber of iSCSI session: 0 (discovery session: 0)Number of TCP connection: 0Configured TCP parametersLocal Port is 3260PMTU discover is enabled, reset timeout is 3600 secKeepalive-timeout is 60 secMinimum-retransmit-time is 300 msMax-retransmissions 4Sack is enabledQOS code point is 0Maximum allowed bandwidth is 1000000 kbpsMinimum available bandwidth is 70000 kbpsEstimated round trip time is 1000 usecSend buffer size is 4096 KBCongestion window monitoring is enabled, burst size is 50 KBConfigured maximum jitter is 500 usForwarding mode: store-and-forwardTMF Queueing Mode : disabledProxy Initiator Mode : disabled5 minutes input rate 0 bits/sec, 0 bytes/sec, 0 frames/sec5 minutes output rate 0 bits/sec, 0 bytes/sec, 0 frames/seciSCSI statisticsInput 0 packets, 0 bytesCommand 0 pdus, Data-out 0 pdus, 0 bytesOutput 0 packets, 0 bytesResponse 0 pdus (with sense 0), R2T 0 pdusData-in 0 pdus, 0 bytesDisplaying iSCSI Statistics
Use the show iscsi stats command to view brief or detailed iSCSI statistics per iSCSI interface. See Example 35-2 and Example 35-3.
Example 35-2 displays iSCSI throughput on an IPS port in both inbound and outbound directions. It also displays the number of different types of iSCSI PDU received and transmitted by this IPS port.
Example 35-2 Display brief iSCSI statistics for an iSCSI interface
switch# show iscsi stats iscsi 2/1iscsi2/15 minutes input rate 704 bits/sec, 88 bytes/sec, 1 frames/sec5 minutes output rate 704 bits/sec, 88 bytes/sec, 1 frames/seciSCSI statistics974756 packets input, 142671620 bytesCommand 2352 pdus, Data-out 44198 pdus, 92364800 bytes, 0 fragments, unsolicited 0 bytesoutput 1022920 packets, 143446248 bytesResponse 2352 pdus (with sense 266), R2T 1804 pdusData-in 90453 pdus, 92458248 bytesExample 35-3 displays detailed iSCSI statistics for an IPS port. Along with the traffic rate and the number of each iSCSI PDU types, it shows the number of FCP frames received and forwarded, the number of iSCSI login attempt, succeed, and failure. It also shows the number of different types of iSCSI PDUs sent and received that are noncritical or occur less frequently, such as NOP in and out (NOP-In and NOP-Out), text request and response (Text-REQ and Text-RESP), and task management request and response (TMF-REQ and TMF-RESP).
Various types of errors and PDU or frame drop occurrences are also counted and displayed. For example, Bad header digest shows the number of iSCSI PDUs received that have a header digest that fails CRC verification. The iSCSI Drop section shows the number of PDUs that were dropped due to reasons such as target down, LUN mapping fail, Data CRC error, or unexpected Immediate or Unsolicited data. These statistics are helpful for debugging purposes when the feature is not working as expected.
The last section, Buffer Stats, gives statistics of the internal IPS packet buffer operation. This section is for debugging purposes only.
Example 35-3 Displays Detailed iSCSI Statistics for the iSCSI Interface
switch# show iscsi stats iscsi 2/1 detailiscsi2/15 minutes input rate 704 bits/sec, 88 bytes/sec, 1 frames/sec5 minutes output rate 704 bits/sec, 88 bytes/sec, 1 frames/seciSCSI statistics974454 packets input, 142656516 bytesCommand 2352 pdus, Data-out 44198 pdus, 92364800 bytes, 0 fragments, unsolicited 0 bytesoutput 1022618 packets, 143431144 bytesResponse 2352 pdus (with sense 266), R2T 1804 pdusData-in 90453 pdus, 92458248 bytesiSCSI Forward:Command:2352 PDUs (Rcvd:2352)Data-Out (Write):16236 PDUs (Rcvd 44198), 0 fragments, 92364800 bytes, unsolicited 0 bytesFCP Forward:Xfer_rdy:1804 (Rcvd:1804)Data-In:90453 (Rcvd:90463), 92458248 bytesResponse:2352 (Rcvd:2362), with sense 266TMF Resp:0iSCSI Stats:Login:attempt:13039, succeed:110, fail:12918, authen fail:0Rcvd:NOP-Out:914582, Sent:NOP-In:914582NOP-In:0, Sent:NOP-Out:0TMF-REQ:0, Sent:TMF-RESP:0Text-REQ:18, Sent:Text-RESP:27SNACK:0Unrecognized Opcode:0, Bad header digest:0Command in window but not next:0, exceed wait queue limit:0Received PDU in wrong phase:0SCSI Busy responses:0Immediate data failure::Separation:0Unsolicited data failure::Separation:0, Segment:0Add header:0Sequence ID allocation failure:0FCP Stats:Total:Sent:47654Received:96625 (Error:0, Unknown:0)Sent:PLOGI:10, Rcvd:PLOGI_ACC:10, PLOGI_RJT:0PRLI:10, Rcvd:PRLI_ACC:10, PRLI_RJT:0, Error:0, From initiator:0LOGO:4, Rcvd:LOGO_ACC:0, LOGO_RJT:0PRLO:4, Rcvd:PRLO_ACC:0, PRLO_RJT:0ABTS:0, Rcvd:ABTS_ACC:0TMF REQ:0Self orig command:10, Rcvd:data:10, resp:10Rcvd:PLOGI:156, Sent:PLOGI_ACC:0, PLOGI_RJT:156LOGO:0, Sent:LOGO_ACC:0, LOGO_RJT:0PRLI:8, Sent:PRLI_ACC:8, PRLI_RJT:0PRLO:0, Sent:PRLO_ACC:0, PRLO_RJT:0ADISC:0, Sent:ADISC_ACC:0, ADISC_RJT:0ABTS:0iSCSI Drop:Command:Target down 0, Task in progress 0, LUN map fail 0CmdSeqNo not in window 0, No Exchange ID 0, Reject 0No task:0Data-Out:0, Data CRC Error:0TMF-Req:0, No task:0Unsolicited data:0, Immediate command PDU:0FCP Drop:Xfer_rdy:0, Data-In:0, Response:0Buffer Stats:Buffer less than header size:0, Partial:45231, Split:322Pullup give new buf:0, Out of contiguous buf:0, Unaligned m_data:0Displaying Proxy Initiator Information
If the proxy initiator feature is enabled in the iSCSI interface, use the show interface iscsi command to display configured proxy initiator information (see Example 35-4 and Example 35-5).
Example 35-4 Displays Proxy Initiator Information for the iSCSI Interface with System-Assigned WWNs
switch# show interface iscsi 4/1iscsi4/1 is upHardware is GigabitEthernetPort WWN is 20:c1:00:05:30:00:a7:9eAdmin port mode is ISCSIPort mode is ISCSISpeed is 1 GbpsiSCSI initiator is identified by nameNumber of iSCSI session: 0, Number of TCP connection: 0Configured TCP parametersLocal Port is 3260PMTU discover is enabled, reset timeout is 3600 secKeepalive-timeout is 60 secMinimum-retransmit-time is 300 msMax-retransmissions 4Sack is disabledQOS code point is 0Forwarding mode: pass-thruTMF Queueing Mode : disabledProxy Initiator Mode : enabled<----------------------------Proxy initiator is enablednWWN is 28:00:00:05:30:00:a7:a1 (system-assigned)<----System-assigned nWWNpWWN is 28:01:00:05:30:00:a7:a1 (system-assigned)<---- System-assigned pWWN5 minutes input rate 0 bits/sec, 0 bytes/sec, 0 frames/sec5 minutes output rate 0 bits/sec, 0 bytes/sec, 0 frames/seciSCSI statisticsInput 7 packets, 2912 bytesCommand 0 pdus, Data-out 0 pdus, 0 bytesOutput 7 packets, 336 bytesResponse 0 pdus (with sense 0), R2T 0 pdusData-in 0 pdus, 0 bytesExample 35-5 Displays Proxy Initiator Information for the iSCSI Interface with User-Assigned WWNs
switch# show interface iscsi 4/2iscsi4/2 is upHardware is GigabitEthernetPort WWN is 20:c1:00:05:30:00:a7:9eAdmin port mode is ISCSIPort mode is ISCSISpeed is 1 GbpsiSCSI initiator is identified by nameNumber of iSCSI session: 0, Number of TCP connection: 0Configured TCP parametersLocal Port is 3260PMTU discover is enabled, reset timeout is 3600 secKeepalive-timeout is 60 secMinimum-retransmit-time is 300 msMax-retransmissions 4Sack is disabledQOS code point is 0Forwarding mode: pass-thruTMF Queueing Mode : disabledProxy Initiator Mode : enablednWWN is 11:11:11:11:11:11:11:11 (manually-configured)<----User-assigned nWWNpWWN is 22:22:22:22:22:22:22:22 (manually-configured)<----User-assigned pWWN5 minutes input rate 0 bits/sec, 0 bytes/sec, 0 frames/sec5 minutes output rate 0 bits/sec, 0 bytes/sec, 0 frames/seciSCSI statisticsInput 7 packets, 2912 bytesCommand 0 pdus, Data-out 0 pdus, 0 bytesOutput 7 packets, 336 bytesResponse 0 pdus (with sense 0), R2T 0 pdusData-in 0 pdus, 0 bytesDisplaying Global iSCSI Information
Use the show iscsi global command to view the overall configuration and the iSCSI status. See Example 35-6.
Example 35-6 Displays the Current Global iSCSI Configuration and State
switch# show iscsi globaliSCSI Global informationAuthentication: CHAP, NONEImport FC Target: EnabledInitiator idle timeout: 300 secondsNumber of target node: 0Number of portals: 11Number of session: 0Failed session: 0, Last failed initiator name:Displaying iSCSI Sessions
Use the show iscsi session command to view details about the current iSCSI sessions in the switch. Without parameters, this command displays all sessions. The output can be filtered by specifying an initiator, a target, or both.
Example 35-7 displays one iSCSI initiator configured based on the IQN (iqn.1987-05.com.cisco:02.3021b0f2fda0.avanti12-w2k) and another based on its IP address (10.10.100.199).
Example 35-7 Displays Brief Information of All iSCSI Sessions
switch# show iscsi sessionInitiator iqn.1987-05.com.cisco:02.3021b0f2fda0.avanti12-w2kInitiator ip addr (s): 10.10.100.116Session #1Discovery session, ISID 00023d000043, Status activeSession #2Target VT1VSAN 1, ISID 00023d000046, Status active, no reservationSession #3Target VT2VSAN 1, ISID 00023d000048, Status active, no reservationInitiator 10.10.100.199Initiator name iqn.1987-05.com.cisco.01.7e3183ae458a94b1cd6bc168cba09d2eSession #1Target VT2VSAN 1, ISID 246700000000, Status active, no reservationSession #2Target VT1VSAN 1, ISID 246b00000000, Status active, no reservationSession #3Target iqn.1987-05.com.cisco:05.switch.04-01.2100002037a6be32VSAN 1, ISID 246e00000000, Status active, no reservationExample 35-8 and Example 35-9 display the iSCSI initiator configured based on its IP address (10.10.100.199).
Example 35-8 Displays Brief Information About the Specified iSCSI Session
switch# show iscsi session initiator 10.10.100.199 target VT1Initiator 10.10.100.199Initiator name iqn.1987-05.com.cisco.01.7e3183ae458a94b1cd6bc168cba09d2eSession #1Target VT1VSAN 1, ISID 246b00000000, Status active, no reservationExample 35-9 Displays Detailed Information About the Specified iSCSI Session
switch# show iscsi session initiator 10.10.100.199 target VT1 detailInitiator 10.10.100.199 (oasis-qa)Initiator name iqn.1987-05.com.cisco.01.7e3183ae458a94b1cd6bc168cba09d2eSession #1 (index 3)Target VT1VSAN 1, ISID 246b00000000, TSIH 384, Status active, no reservationType Normal, ExpCmdSN 39, MaxCmdSN 54, Barrier 0MaxBurstSize 0, MaxConn 0, DataPDUInOrder NoDataSeqInOrder No, InitialR2T Yes, ImmediateData NoRegistered LUN 0, Mapped LUN 0Stats:PDU: Command: 38, Response: 38Bytes: TX: 8712, RX: 0Number of connection: 1Connection #1Local IP address: 10.10.100.200, Peer IP address: 10.10.100.199CID 0, State: LOGGED_INStatSN 62, ExpStatSN 0MaxRecvDSLength 1024, our_MaxRecvDSLength 1392CSG 3, NSG 3, min_pdu_size 48 (w/ data 48)AuthMethod none, HeaderDigest None (len 0), DataDigest None (len 0)Version Min: 2, Max: 2FC target: Up, Reorder PDU: No, Marker send: No (int 0)Received MaxRecvDSLen key: NoDisplaying iSCSI Initiators
Use the show iscsi initiator command to display information about all initiators connected to an iSCSI interface in the switch. The information can be filtered to display only the desired iSCSI initiator by specifying the initiator name. Detailed output of the iscsi initiator can be obtained by specifying the detail option. The iscsi-session (and optionally detail) parameter displays only iSCSI session information. The fcp-session (and optionally detail) parameter displays only FCP session information. The output includes static and dynamic initiators. See Example 35-10 and Example 35-11.
Example 35-10 Displays Information About Connected iSCSI Initiators
switch# show iscsi initiatoriSCSI Node name is iqn.1987-05.com.cisco:02.3021b0f2fda0.avanti12-w2kInitiator ip addr (s): 10.10.100.116iSCSI alias name: AVANTI12-W2KNode WWN is 22:01:00:05:30:00:10:e1 (configured)Member of vsans: 1, 2, 10Number of Virtual n_ports: 1Virtual Port WWN is 22:04:00:05:30:00:10:e1 (configured)Interface iSCSI 4/1, Portal group tag: 0x180VSAN ID 1, FCID 0x6c0202VSAN ID 2, FCID 0x6e0000VSAN ID 10, FCID 0x790000iSCSI Node name is 10.10.100.199iSCSI Initiator name: iqn.1987-05.com.cisco.01.7e3183ae458a94b1cd6bc168cba09d2eiSCSI alias name: oasis-qaNode WWN is 22:03:00:05:30:00:10:e1 (configured)Member of vsans: 1, 5Number of Virtual n_ports: 1Virtual Port WWN is 22:00:00:05:30:00:10:e1 (configured)Interface iSCSI 4/1, Portal group tag: 0x180VSAN ID 5, FCID 0x640000VSAN ID 1, FCID 0x6c0203Example 35-11 Displays Detailed Information About the iSCSI Initiator
switch# show iscsi initiator iqn.1987-05.com.cisco:02.3021b0f2fda0.avanti12-w2k detailiSCSI Node name is iqn.1987-05.com.cisco:02.3021b0f2fda0.avanti12-w2kInitiator ip addr (s): 10.10.100.116iSCSI alias name: AVANTI12-W2KNode WWN is 22:01:00:05:30:00:10:e1 (configured)Member of vsans: 1, 2, 10Number of Virtual n_ports: 1Virtual Port WWN is 22:04:00:05:30:00:10:e1 (configured)Interface iSCSI 4/1, Portal group tag is 0x180VSAN ID 1, FCID 0x6c02021 FC sessions, 1 iSCSI sessionsiSCSI session details <-------------------iSCSI session detailsTarget: VT1Statistics:PDU: Command: 0, Response: 0Bytes: TX: 0, RX: 0Number of connection: 1TCP parametersLocal 10.10.100.200:3260, Remote 10.10.100.116:4190Path MTU: 1500 bytesRetransmission timeout: 310 msRound trip time: Smoothed 160 ms, Variance: 38Advertized window: Current: 61 KB, Maximum: 62 KB, Scale: 0Peer receive window: Current: 63 KB, Maximum: 63 KB, Scale: 0Congestion window: Current: 1 KBFCP Session details <-------------------FCP session detailsTarget FCID: 0x6c01e8 (S_ID of this session: 0x6c0202)pWWN: 21:00:00:20:37:62:c0:0c, nWWN: 20:00:00:20:37:62:c0:0cSession state: CLEANUP1 iSCSI sessions share this FC sessionTarget: VT1Negotiated parametersRcvDataFieldSize 1392 our_RcvDataFieldSize 1392MaxBurstSize 0, EMPD: FALSERandom Relative Offset: FALSE, Sequence-in-order: YesStatistics:PDU: Command: 0, Response: 0Use the show fcns database (and optionally detail) to display the Fibre Channel name server entry for the Fibre Channel N port created for iSCSI initiators in the SAN. See Example 35-12 and Example 35-13.
Example 35-12 Displays the FCNS Database Contents
switch# show fcns databaseVSAN 1:--------------------------------------------------------------------------FCID TYPE PWWN (VENDOR) FC4-TYPE:FEATURE--------------------------------------------------------------------------0x020101 N 22:04:00:05:30:00:35:e1 (Cisco) scsi-fcp:init isc..w <--iSCSI0x020102 N 22:02:00:05:30:00:35:e1 (Cisco) scsi-fcp:init isc..w initiator0x0205d4 NL 21:00:00:04:cf:da:fe:c6 (Seagate) scsi-fcp:target0x0205d5 NL 21:00:00:04:cf:e6:e4:4b (Seagate) scsi-fcp:target...Total number of entries = 10VSAN 2:--------------------------------------------------------------------------FCID TYPE PWWN (VENDOR) FC4-TYPE:FEATURE--------------------------------------------------------------------------0xef0001 N 22:02:00:05:30:00:35:e1 (Cisco) scsi-fcp:init isc..wTotal number of entries = 1VSAN 3:--------------------------------------------------------------------------FCID TYPE PWWN (VENDOR) FC4-TYPE:FEATURE--------------------------------------------------------------------------0xed0001 N 22:02:00:05:30:00:35:e1 (Cisco) scsi-fcp:init isc..wTotal number of entries = 1Example 35-13 Displays the FCNS Database in Detail
switch# show fcns database detail------------------------VSAN:1 FCID:0x020101------------------------port-wwn (vendor) :22:04:00:05:30:00:35:e1 (Cisco)node-wwn :22:03:00:05:30:00:35:e1class :2,3node-ip-addr :10.2.2.12 <--- iSCSI initiator's IP addressipa :ff ff ff ff ff ff ff fffc4-types:fc4_features:scsi-fcp:init iscsi-gwsymbolic-port-name :symbolic-node-name :iqn.1991-05.com.microsoft:oasis2-dell <--- iSCSI initiator's IQNport-type :Nport-ip-addr :0.0.0.0fabric-port-wwn :22:01:00:05:30:00:35:dehard-addr :0x000000------------------------VSAN:1 FCID:0x020102------------------------port-wwn (vendor) :22:02:00:05:30:00:35:e1 (Cisco)node-wwn :22:01:00:05:30:00:35:e1class :2,3node-ip-addr :10.2.2.11ipa :ff ff ff ff ff ff ff fffc4-types:fc4_features:scsi-fcp:init iscsi-gwsymbolic-port-name :symbolic-node-name :iqn.1987-05.com.cisco.01.14ac33ba567f986f174723b5f9f2377port-type :Nport-ip-addr :0.0.0.0fabric-port-wwn :22:01:00:05:30:00:35:dehard-addr :0x000000...Total number of entries = 10======================================================================------------------------VSAN:2 FCID:0xef0001------------------------port-wwn (vendor) :22:02:00:05:30:00:35:e1 (Cisco)node-wwn :22:01:00:05:30:00:35:e1class :2,3node-ip-addr :10.2.2.11ipa :ff ff ff ff ff ff ff fffc4-types:fc4_features:scsi-fcp:init iscsi-gwsymbolic-port-name :symbolic-node-name :iqn.1987-05.com.cisco.01.14ac33ba567f986f174723b5f9f2377port-type :Nport-ip-addr :0.0.0.0fabric-port-wwn :22:01:00:05:30:00:35:dehard-addr :0x000000Total number of entries = 1...Use the show iscsi initiator configured to display information about all the configured iSCSI initiators. Specifying the name shows information about the desired initiator. See Example 35-14.
Example 35-14 Display Information About Configured Initiators
switch# show iscsi initiator configurediSCSI Node name is iqn.1987-05.com.cisco:02.3021b0f2fda0.avanti12-w2kMember of vsans: 1, 2, 10Node WWN is 22:01:00:05:30:00:10:e1No. of PWWN: 5Port WWN is 22:04:00:05:30:00:10:e1Port WWN is 22:05:00:05:30:00:10:e1Port WWN is 22:06:00:05:30:00:10:e1Port WWN is 22:07:00:05:30:00:10:e1Port WWN is 22:08:00:05:30:00:10:e1iSCSI Node name is 10.10.100.199Member of vsans: 1, 5Node WWN is 22:03:00:05:30:00:10:e1No. of PWWN: 4Port WWN is 22:00:00:05:30:00:10:e1Port WWN is 22:09:00:05:30:00:10:e1Port WWN is 22:0a:00:05:30:00:10:e1Port WWN is 22:0b:00:05:30:00:10:e1User Name for Mutual CHAP: testuserDisplaying iSCSI Virtual Targets
Use the show iscsi virtual-target to display information about the Fibre Channel targets exported as iSCSI virtual targets to the iSCSI initiators. The output includes static as well as dynamic targets. See Example 35-15.
Example 35-15 Displays Exported Targets
switch# show iscsi virtual-targettarget: VT1* Port WWN 21:00:00:20:37:62:c0:0cConfigured nodeall initiator permit is enabledtarget: VT2Port WWN 21:00:00:04:cf:4c:52:c1Configured nodeall initiator permit is disabledtarget: iqn.1987-05.com.cisco:05.switch.04-01.2100002037a6be32Port WWN 21:00:00:20:37:a6:be:32 , VSAN 1Auto-created nodeDisplaying iSCSI User Information
The show user-account iscsi command displays all configured iSCSI user names. See Example 35-16.
Example 35-16 Displays iSCSI User Names
switch# show user-account iscsiusername:iscsiusersecret: dsfffsffsffasffsdffgusername:user2secret:cshadhdhsadadjajdjasiSCSI High Availability
The following high availability features are available for iSCSI configurations:
•
Multiple IPS Ports Connected to the Same IP Network
•
Ethernet PortChannel-Based High Availability
Transparent Target Failover
The following high availability configurations are available:
•
iSCSI high availability with host running multi-path software
•
iSCSI High availability with host not having multi-path software
iSCSI High Availability with Host Running Multi-Path Software
Figure 35-14 shows the physical and logical topology for iSCSI HA solution for hosts running multi-path software. In this scenario, the host will have 4 iSCSI sessions. Two iSCSI sessions from each host NIC to the two IPS port.
Figure 35-14 Host Running Multi-Path Software
Each IPS ports is exporting the same two Fibre Channel target ports of the storage but as different iSCSI target names (if you use dynamic iSCSI targets). So the two IPS ports are exporting a total of 4 iSCSI target devices. These four iSCSI targets map the same two ports of the Fibre Channel target.
The iSCSI host uses NIC-1 to connect to IPS port 1 and NIC-2 to connect to IPS port 2. Each IPS port exports two iSCSI targets, so the iSCSI host creates 4 iSCSI sessions.
If the iSCSI host NIC-1 fails (see Figure 35-14 for the physical view), then session 1 and 2 fail but we still have session 3 and 4.
If the IPS port -1 fails, iSCSI host cannot connect to the IPS port, then session 1 and 2 fail. But sessions 3/4 are still available.
If the Storage port P-1 fails, then the IPS ports will terminate session 1 and 3 (put iSCSI virtual target iqn.com.cisco.mds-5.1-2.p1 and iqn-com.cisco.mds-5.1-1.p1 in off-line state). But session 2/4 are still available.
In this topology, you have recovery from failure of any of the components. The host multi-path software takes care of load-balancing/fail-over across the different paths to access the storage.
iSCSI HA with Host Not Having Any Multi-Path Software
The above topology will not work if the host does not have multi-path software because the host has multiple sessions to the same storage. Without multi-path software the host does not have knowledge the multiple paths are to the same storage.
IP Storage has two additional features to provide HA solution in this scenario.
•
IPS ports support VRRP protocol (see the "Configuring VRRP for Gigabit Ethernet Interfaces" section on page 37-16) to provide failover for IPS ports.
•
IPS has transparent Fibre Channel target failover feature for iSCSI static virtual target.
Statically imported iSCSI targets have an additional option to provide a secondary pWWN for the Fibre Channel target. This can be used when the physical Fibre Channel target is configured to have an LU visible across redundant ports. When the active port fails, the secondary port becomes active and the iSCSI session switches to use the new active port (see Figure 35-15).
Figure 35-15 Static Target Importing Through Two Fibre Channel Ports
In Figure 35-15, you can create a iSCSI virtual target that is mapped to both pWWN1 and pWWN2 to provide redundant access to the Fibre Channel targets.
The failover to secondary port is done transparently by the IPS port without impacting the iSCSI session from the host. All outstanding I/O are terminated with a check condition status when the primary port fails. New I/O received while the failover has not completed will receive a busy status.
Tip
If you use LUN mapping, you can define a different secondary Fibre Channel LUN if the LU number is different.
Enable the optional revert-primary-port option to direct the IPS port to switch back to the primary port when the primary port is up again. If this option is disabled (default) and the primary port is up again after a switchover, the old sessions will remain with the secondary port and does not switch back to the primary port. However, any new session will use the primary port. This is the only situation when both the primary and secondary ports are used at the same time.
To create a static iSCSI virtual target, follow these steps:Storage Port Failover LUN Trespass
In addition to the high availability of statically imported iSCSI targets, the trespass feature is available to enable the move of LUs, on an active port failure, from the active to the passive port of a statically imported iSCSI target.
In physical Fibre Channel targets, which are configured to have LUs visible over two Fibre Channel N ports, when the active port fails, the passive port takes over. Some physical Fibre Channel targets require that the trespass feature be used to move the LUs from the active port to the passive port. A statically imported iSCSI target's secondary pWWN option and an additional option of enabling the trespass feature is available for a physical Fibre Channel target with redundant ports. When the active port fails, the passive port becomes active, and if the trespass feature is enabled, the Cisco MDS switch sends a request to the target to move the LUs on the new active port. The iSCSI session switches to use the new active port and the moved LUs are accessed over the new active port (see Figure 35-16).
Figure 35-16 Virtual Target with an Active Primary Port
To enable the trespass feature for a static iSCSI virtual target, follow these steps:
Use the show iscsi virtual-target command to verify.
switch# show iscsi virtual-target iqn.1987-02.com.cisco.initiatortarget: 1987-02.com.cisco.initiatorPort WWN 10:20:10:00:56:00:70:50Configured nodeall initiator permit is disabledtrespass support is enabledMultiple IPS Ports Connected to the Same IP Network
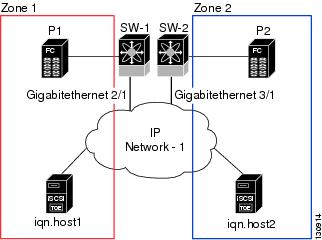
Figure 35-17 provides an example of a configuration with multiple Gigabit Ethernet interfaces in the same IP network.
Figure 35-17 Multiple Gigabit Ethernet Interfaces in the Same IP Network
In Figure 35-17, each iSCSI host discovers two iSCSI targets for every physical Fibre Channel target (with different names). The multi-pathing software on the host provides load-balancing over both paths. If one Gigabit Ethernet interface fails, the host multi-pathing software is not affected because it can use the second path.
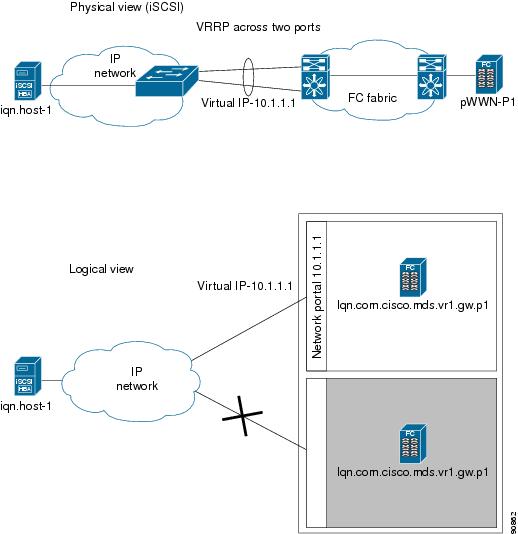
VRRP-Based High Availability
Figure 35-18 provides an example of a VRRP-based high availability iSCSI configuration.
Figure 35-18 VRRP-Based iSCSI High Availability
In Figure 35-18, each iSCSI host discovers one iSCSI target for every physical Fibre Channel target. When the Gigabit Ethernet interface of the VRRP master fails, the iSCSI session is terminated. The host then reconnects to the target and the session comes up because the second Gigabit Ethernet interface has taken over the virtual IP address as the new master.
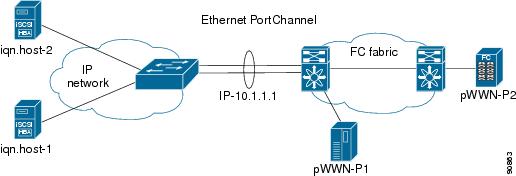
Ethernet PortChannel-Based High Availability
Note
All iSCSI data traffic for one iSCSI link is carried on one TCP connection. Consequently, the aggregated bandwidth is 1 Gbps for that iSCSI link.
Figure 35-19 provides a sample Ethernet PortChannel-based high availability iSCSI configuration.
Figure 35-19 Ethernet PortChannel-Based iSCSI High Availability
In Figure 35-19, each iSCSI host discovers one iSCSI target for every physical Fibre Channel target. The iSCSI session from the iSCSI host to the iSCSI virtual target (on the IPS port) uses one of the two physical interfaces (because an iSCSI session uses one TCP connection). When the Gigabit Ethernet interface fails, the IPS module and the Ethernet switch transparently forwards all the frames on to the second Gigabit Ethernet interface.
Note
If an Ethernet PortChannel is configured between the IPS module and an Ethernet switch, the load balancing policy on the Ethernet switch must be based on source/destination IP address only, not port numbers, for load balancing with VRRP to operate correctly.
iSCSI Authentication Setup Guidelines and Scenarios
This section provides guidelines on iSCSI authentication possibilities, setup requirements, and sample scenarios. It includes the following authentication setup guidelines:
•
CHAP with Local Password Database
•
CHAP with External RADIUS Server
Note
This section does not specify the steps to enter or exit EXEC mode, configuration mode, or any submode. Be sure to verify the prompt before issuing any command.
No Authentication
Set the iSCSI authentication method to none to configure a network with no authentication.
switch(config)# iscsi authentication noneCHAP with Local Password Database
To configure authentication using the CHAP option with the local password database, follow these steps:
Step 1
Set the AAA authentication to use the local password database for iSCSI protocol.
switch(config)# aaa authentication iscsi default localStep 2
Set the iSCSI authentication method to require CHAP for all iSCSI clients.
switch(config)# iscsi authentication chapStep 3
Configure the user names and passwords for iSCSI users.
switch(config)# username iscsi-user password abcd iscsi
Note
If you do not specify the iscsi option, the user name is assumed to be a Cisco MDS switch user instead of an iSCSI user.
Step 4
Verify the global iSCSI authentication setup.
switch# show iscsi globaliSCSI Global information Authentication: CHAP <----VerifyImport FC Target: Disabled...
CHAP with External RADIUS Server
To configure authentication using the CHAP option with an external RADIUS server, follow these steps:
Step 1
Configure the password for the Cisco MDS switch as RADIUS client to the RADIUS server.
switch(config)# radius-server key mds-1Step 2
Configure the RADIUS server IP address.
switch(config)# radius-server host 10.1.1.10Step 3
Configure a server group.
switch(config)# aaa group server radius iscsi-radius-groupswitch(config-radius)# server 10.1.1.1Step 4
Set up the authentication verification for the iSCSI protocol to go to the RADIUS server.
switch(config)# aaa authentication iscsi default group iscsi-radius-groupStep 5
Set up the iSCSI authentication method to require CHAP for all iSCSI clients.
switch(config)# iscsi authentication chapStep 6
Verify that the global iSCSI authentication set up is CHAP.
switch# show iscsi globaliSCSI Global informationAuthentication: CHAP <---------------- Verify CHAP....Step 7
Verify that the AAA authentication information for iSCSI.
switch# show aaa authenticationdefault: localconsole: localiscsi: group iscsi-radius-group <--------- Group namedhchap: localswitch# show radius-server groupstotal number of groups:2following RADIUS server groups are configured:group radius:server: all configured radius serversgroup iscsi-radius-group:server: 10.1.1.1 on auth-port 1812, acct-port 1813switch# show radius-serverGlobal RADIUS shared secret:mds-1 <-------- Verify secret....following RADIUS servers are configured:10.1.1.1: <----------- Verify the server IP addressavailable for authentication on port:1812available for accounting on port:1813To configure an iSCSI RADIUS server, follow these steps:
Step 1
Configure the RADIUS server to allow access from the Cisco MDS switch's management Ethernet IP address.
Step 2
Configure the shared secret for the RADIUS server to authenticate the Cisco MDS switch.
Step 3
Configure the iSCSI users and passwords on the RADIUS server.
iSCSI Transparent Mode Initiator
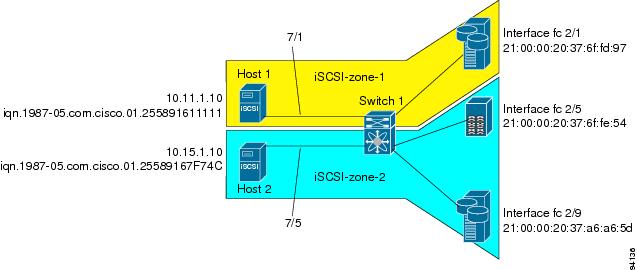
This scenario assumes the following configuration (see Figure 35-20):
•
No LUN mapping or LUN masking or any other access control for hosts on the target device
•
No iSCSI login authentication (that is, login authentication set to none)
Topology:
•
iSCSI interface 7/1 is configured to identify initiators by IP address
•
iSCSI interface 7/5 is configured to identify initiators by node name
•
iSCSI initiator host-1 with IP address 10.11.1.10 and name iqn.1987-05.com.cisco:01.255891611111 connects to IPS port 7/1 is identified using IP address (host 1 = 10.11.1.10).
•
The iSCSI initiator host-2 with IP address 10.15.1.10 and node name iqn.1987-05.com.cisco:01.25589167f74c connects to IPS port 7/5
Figure 35-20 iSCSI Scenario 1
To configure scenario 1 (see Figure 35-20), follow these steps:
Step 1
Configure null authentication for all iSCSI hosts in Cisco MDS switches.
switch(config)# iscsi authentication noneStep 2
Configure iSCSI to dynamically import all Fibre Channel targets into the iSCSI SAN using auto-generated iSCSI target names.
switch(config)# iscsi import target fcStep 3
Configure the Gigabit Ethernet interface in slot 7 port 1 with an IP address and enable the interface.
switch(config)# int gigabitethernet 7/1switch(config-if)# ip address 10.11.1.1 255.255.255.0switch(config-if)# no shut
Note
Host 2 is connected to this port.
Step 4
Configure the iSCSI interface in slot 7 port 1 to identify all dynamic iSCSI initiators by the IP address, and enable the interface.
switch(config)# int iscsi 7/1switch(config-if)# switchport initiator id ip-addressswitch(config-if)# no shutStep 5
Configure the Gigabit Ethernet interface in slot 7 port 5 with the IP address and enable the interface.
switch(config)# int gigabitethernet 7/5switch(config-if)# ip address 10.15.1.1 255.255.255.0switch(config-if)# no shutStep 6
Configure the iSCSI interface in slot 7 port 5 to identify all dynamic iSCSI initiators by node name and enable the interface.
switch(config)# int iscsi 7/5switch(config-if)# switchport initiator id nameswitch(config-if)# no shut
Note
Host 1 is connected to this port.
Step 7
Verify the available Fibre Channel targets (see Figure 35-20).
switch# show fcns databaseVSAN 1:--------------------------------------------------------------------------FCID TYPE PWWN (VENDOR) FC4-TYPE:FEATURE--------------------------------------------------------------------------0x6d0001 NL 21:00:00:20:37:6f:fd:97 (Seagate) scsi-fcp:target0x6d0101 NL 21:00:00:20:37:6f:fe:54 (Seagate) scsi-fcp:target0x6d0201 NL 21:00:00:20:37:a6:a6:5d (Seagate) scsi-fcp:targetTotal number of entries = 3Step 8
Create a zone named iscsi-zone-1 with host 1 and one Fibre Channel target in it.
Note
Use the IP address of the host in zone membership configuration because the iSCSI interface is configured to identify all hosts based on IP address.
switch(config)# zone name iscsi-zone-1 vsan 1switch(config-zone)# member pwwn 21:00:00:20:37:6f:fd:97switch(config-zone)# member ip-address 10.11.1.10Step 9
Create a zone named iscsi-zone-2 with host 2 and two Fibre Channel targets in it.
Note
Use the symbolic node name of the iSCSI host in zone membership configuration because the iSCSI interface is configured to identify all hosts based on node name.
switch(config)# zone name iscsi-zone-2 vsan 1switch(config-zone)# member pwwn 21:00:00:20:37:6f:fe:54switch(config-zone)# member pwwn 21:00:00:20:37:a6:a6:5dswitch(config-zone)# member symbolic-nodename iqn.1987-05.com.cisco:01.25589167f74cStep 10
Create a zone set and add the two zones as members.
switch(config)# zoneset name zoneset-iscsi vsan 1switch(config-zoneset)# member iscsi-zone-1switch(config-zoneset)# member iscsi-zone-2Step 11
Activate the zone set.
switch(config)# zoneset activate name zoneset-iscsi vsan 1Step 12
Display the active zone set.
Note
The iSCSI hosts has not connected so they do not have a FCID yet.
switch# show zoneset activezoneset name zoneset-iscsi vsan 1zone name iscsi-zone-1 vsan 1* fcid 0x6d0001 [pwwn 21:00:00:20:37:6f:fd:97] <-----------Targetsymbolic-nodename 10.11.1.10 <--------------------------------- iSCSI host (host 1, not online)zone name iscsi-zone-2 vsan 1* fcid 0x6d0101 [pwwn 21:00:00:20:37:6f:fe:54] <------------Target* fcid 0x6d0201 [pwwn 21:00:00:20:37:a6:a6:5d] <------------Targetsymbolic-nodename iqn.1987-05.com.cisco:01.25589167f74c <-iSCSI host (host 2, not online)Step 13
Bring up the iSCSI hosts (host 1 and host 2).
Step 14
Show all the iSCSI sessions (use the detail option for detailed information).
switch# show iscsi sessionInitiator iqn.1987-05.com.cisco:01.25589167f74c <-----Host 2Initiator ip addr (s): 10.15.1.11Session #1Target iqn.1987-05.com.cisco:05.172.22.92.166.07-05.21000020376ffe54
Note
The last part of the auto-created target name is the Fibre Channel target's pWWN.
VSAN 1, ISID 00023d000001, Status active, no reservationSession #2Target iqn.1987-05.com.cisco:05.172.22.92.166.07-05.2100002037a6a65dVSAN 1, ISID 00023d000001, Status active, no reservationInitiator 10.11.1.10 <-----------------------------------Host 1Initiator name iqn.1987-05.com.cisco:01.e41695d16b1aSession #1Target iqn.1987-05.com.cisco:05.172.22.92.166.07-01.21000020376ffd97VSAN 1, ISID 00023d000001, Status active, no reservationStep 15
Verify the details of the two iSCSI initiators.
Step 16
View the active zone set. The iSCSI initiators' FCIDs are resolved.
Step 17
The Fibre Channel name server shows the virtual N ports created for the iSCSI hosts.
switch# show fcns databaseVSAN 1:--------------------------------------------------------------------------FCID TYPE PWWN (VENDOR) FC4-TYPE:FEATURE--------------------------------------------------------------------------0x6d0001 NL 21:00:00:20:37:6f:fd:97 (Seagate) scsi-fcp:target0x6d0101 NL 21:00:00:20:37:6f:fe:54 (Seagate) scsi-fcp:target0x6d0201 NL 21:00:00:20:37:a6:a6:5d (Seagate) scsi-fcp:target0x6d0300 N 20:03:00:0b:fd:44:68:c2 (Cisco) scsi-fcp:init isc..w0x6d0301 N 20:05:00:0b:fd:44:68:c2 (Cisco) scsi-fcp:init isc..wStep 18
Verify the detailed output of the iSCSI initiator nodes in the Fibre Channel name server.
Target Storage Device Requiring LUN Mapping
Sample scenario 2 assumes the following configuration (see Figure 35-21):
•
Access control is based on Fibre Channel zoning.
•
There is target-based LUN mapping or LUN masking.
•
There is no iSCSI authentication (none).
•
The iSCSI initiator is assigned to different VSANs.
Figure 35-21 iSCSI Scenario 2
To configure scenario 2 (see Figure 35-21), follow these steps:
Step 1
Configure null authentication for all iSCSI hosts.
switch(config)# iscsi authentication noneStep 2
Configure iSCSI to dynamically import all Fibre Channel targets into the iSCSI SAN using auto-generated iSCSI target names.
switch(config)# iscsi import target fcStep 3
Configure the Gigabit Ethernet interface in slot 7 port 1 with an IP address and enable the interface.
switch(config)# int gigabitethernet 7/1switch(config-if)# ip address 10.11.1.1 255.255.255.0switch(config-if)# no shutStep 4
Configure the iSCSI interface in slot 7 port 1 to identify all dynamic iSCSI initiators by the IP address and enable the interface.
switch(config)# int iscsi 7/1switch(config-if)# switchport initiator id ip-addressswitch(config-if)# no shutStep 5
Configure the Gigabit Ethernet interface in slot 7 port 5 with the IP address and enable the interface.
switch(config)# int gigabitethernet 7/5switch(config-if)# ip address 10.15.1.1 255.255.255.0switch(config-if)# no shutStep 6
Configure the iSCSI interface in slot 7 port 5 to identify all dynamic iSCSI initiators by IP address and enable the interface.
switch(config)# int iscsi 7/5switch(config-if)# switchport initiator id nameswitch(config-if)# no shutStep 7
Add static configuration for each iSCSI initiator.
switch(config)# iscsi initiator name iqn.1987-05.com.cisco:01.e41695d16b1a <-----Host 2switch(config-iscsi-init)# static pWWN system-assign 1switch(config-iscsi-init)# static nWWN system-assignswitch(config)# iscsi initiator ip address 10.15.1.11 <-----------------------------------Host 1switch(config-iscsi-init)# static pwwn system-assigned 1switch(config-iscsi-init)# vsan 2
Note
Host 1 is configured in VSAN 2.
Step 8
View the configured WWNs.
Note
The WWNs are assigned by the system. The initiators are members of different VSANs.
switch# show iscsi initiator configurediSCSI Node name is iqn.1987-05.com.cisco:01.e41695d16b1aMember of vsans: 1Node WWN is 20:03:00:0b:fd:44:68:c2No. of PWWN: 1Port WWN is 20:02:00:0b:fd:44:68:c2iSCSI Node name is 10.15.1.11Member of vsans: 2No. of PWWN: 1Port WWN is 20:06:00:0b:fd:44:68:c2Step 9
Create a zone with host 1.
switch(config)# zone name iscsi-zone-1 vsan 1Step 10
Add three members to the zone named iscsi-zone-1.
Note
Fibre Channel storage for zone membership for the iSCSI initiator, either the iSCSI symbolic node name or the pWWN, can be used. In this case, the pWWN is persistent.
•
The following command is based on the symbolic node name.
switch(config-zone)# member symbolic-nodename iqn.1987-05.com.cisco:01.e41695d16b1a•
The following command is based on the persistent pWWN assigned to the initiator. You can obtain the pWWN from the show iscsi initiator output.
switch(config-zone)# member pwwn 20:02:00:0b:fd:44:68:c2Step 11
Create a zone with host 2 and two Fibre Channel targets.
Note
If the host is in VSAN 2, the Fibre Channel targets and zone must also be in VSAN 2.
switch(config)# zone name iscsi-zone-2 vsan 2Step 12
Activate the zone set in VSAN 2
switch(config)# zoneset activate name iscsi-zoneset-v2 vsan 2Zoneset activation initiated. check zone statusswitch# show zoneset active vsan 2zoneset name iscsi-zoneset-v2 vsan 2zone name iscsi-zone-2 vsan 2* fcid 0x750001 [pwwn 21:00:00:20:37:6f:fe:54]* fcid 0x750101 [pwwn 21:00:00:20:37:a6:a6:5d]pwwn 20:06:00:0b:fd:44:68:c2 <-----------------Host is not onlineStep 13
Start the iSCSI clients on both hosts and verify that sessions come up.
Step 14
Display the iSCSI sessions to verify the Fibre Channel target and the configured WWNs.
Step 15
Display the iSCSI initiator to verify the configured nWWN and pWWN.
Step 16
Check the Fibre Channel name server.
Step 17
Verify the details of the iSCSI initiator's FCID in the name server.
Step 18
Check the Fibre Channel name server
Step 19
Verify the details of the iSCSI initiator's FCID in the name server.
switch(config)# show fcns database fcid 0x680102 detail vsan 1------------------------VSAN:1 FCID:0x680102------------------------port-wwn (vendor) :20:02:00:0b:fd:44:68:c2 (Cisco)node-wwn :20:03:00:0b:fd:44:68:c2class :2,3node-ip-addr :10.11.1.10ipa :ff ff ff ff ff ff ff fffc4-types:fc4_features:scsi-fcp:init iscsi-gwsymbolic-port-name :symbolic-node-name :iqn.1987-05.com.cisco:01.e41695d16b1aport-type :Nport-ip-addr :0.0.0.0fabric-port-wwn :21:81:00:0b:fd:44:68:c0hard-addr :0x000000Step 20
Verify that zoning has resolved the FCID for the iSCSI client.
switch# show zoneset active vsan 1zoneset name iscsi-zoneset-v1 vsan 1zone name iscsi-zone-1 vsan 1* fcid 0x680001 [pwwn 21:00:00:20:37:6f:fd:97]* fcid 0x680102 [pwwn 20:02:00:0b:fd:44:68:c2]Step 21
Verify that the second initiator is connected to the two Fibre Channel targets in VSAN 2.
About iSCSI Storage Name Services
iSCSI Storage Name Services (iSNS) allow your existing TCP/IP network to function more effectively as a SAN by automating the discovery, management, and configuration of iSCSI devices. To facilitate these functions, the iSNS server and client function as follows:
•
The iSNS client registers iSCSI portals and all iSCSI devices accessible through them with an iSNS server.
•
The iSNS server provides the following services for iSNS client:
–
Device registration
–
State change notification
–
Remote domain discovery services
All iSCSI devices (both initiator and target), acting as iSNS clients, can register with an iSNS server. iSCSI initiators can then query the iSNS server for a list of targets. The iSNS server will respond with a list of targets that the querying client can access based on configured access control parameters.
A Cisco MDS 9000 Family switch can act as an iSNS client and register all available iSCSI targets with an external iSNS server. All switches in the Cisco MDS 9000 Family with IPS modules or MPS-14/2 modules installed support iSNS server functionality. This allows external iSNS clients, such as an iSCSI initiator, to register with the switch and discover all available iSCSI targets in the SAN.
About iSNS Client Functionality
The iSNS client functionality on each IPS interface (Gigabit Ethernet interface or subinterface or PortChannel) registers information with an iSNS server. You must specify an iSNS server's IP address by creating an iSNS profile, adding the server's IP address to it, then assign (or "tag") the profile to the interface. An iSNS profile can be tagged to one or more interfaces.
Once a profile is tagged to an interface, the switch opens a TCP connection to the iSNS server IP address (using the well-known iSNS port number 3205) in the profile and registers network entity and portal objects; a unique entity is associated with each IPS interface. The switch then searches the Fibre Channel name server (FCNS) database and switch configuration to find storage nodes to register with the iSNS server.
Statically mapped virtual targets are registered if the associated Fibre Channel pWWN is present in the FCNS database and no access control configuration prevents it. A dynamically mapped target is registered if dynamic target importing is enabled. See the "Presenting Fibre Channel Targets as iSCSI Targets" section for more details on how iSCSI imports Fibre Channel targets.
A storage node is deregistered from the iSNS server when it becomes unavailable when configuration changes (such as access control change or dynamic import disabling) or the Fibre Channel storage port goes off-line. It is registered again when the node comes back online.
When the iSNS client is unable to register or deregister objects with the iSNS server (for example, the client is unable to make a TCP connection to the iSNS server), it retries every minute to reregister all iSNS objects for the affected interfaces with the iSNS server. The iSNS client uses a registration interval value of 15 minutes. If the client fails to refresh the registration during this interval, the server will deregister the entries.
Untagging a profile also causes the network entity and portal to be deregistered from that interface.
Creating an iSNS Client Profile
To create an iSNS profile, follow these steps:
To remove an iSNS profile, follow these steps:
Step 1
switch# config t
switch(config)#
Enters configuration mode.
Step 2
switch(config)# no isns profile name OldIsns
Removes a configured iSNS profile called OldIsns.
To tag a profile to an interface, follow these steps:
To untag a profile from an interface, follow these steps:
Use the isns reregister command in EXEC mode to re-register associated iSNS objects with the iSNS server.
switch# isns reregister gigabitethernet 1/4switch# isns reregister port-channel 1Verifying iSNS Client Configuration
Use the show isns profile command to view configured iSNS profiles. Profile ABC has two portals registered with the iSNS server. Each portal corresponds to a particular interface. Profile XYZ has a specified iSNS server, but does not have any tagged interfaces configured (see Example 35-17 and Example 35-18).
Example 35-17 Displays Information for Configured iSNS Profiles
switch# show isns profileiSNS profile name ABCtagged interface GigabitEthernet2/3tagged interface GigabitEthernet2/2iSNS Server 10.10.100.204iSNS profile name XYZiSNS Server 10.10.100.211Example 35-18 Displays a Specified iSNS Profile
switch# show isns profile ABCiSNS profile name ABCtagged interface GigabitEthernet2/3tagged interface GigabitEthernet2/2iSNS Server 10.10.100.204Use the show isns profile counters command to view all configured profiles with the iSNS PDU statistics for each tagged interface (see Example 35-19 and Example 35-20).
Example 35-19 Displays Configured Profiles with iSNS Statistics
switch# show isns profile countersiSNS profile name ABCtagged interface port-channel 1iSNS statisticsInput 54 pdus (registration/deregistration pdus only)Reg pdus 37, Dereg pdus 17Output 54 pdus (registration/deregistration pdus only)Reg pdus 37, Dereg pdus 17iSNS Server 10.10.100.204iSNS profile name XYZtagged interface port-channel 2iSNS statisticsInput 30 pdus (registration/deregistration pdus only)Reg pdus 29, Dereg pdus 1Output 30 pdus (registration/deregistration pdus only)Reg pdus 29, Dereg pdus 1iSNS Server 10.1.4.218Example 35-20 Displays iSNS Statistics for a Specified Profile
switch# show isns profile ABC countersiSNS profile name ABCtagged interface port-channel 1iSNS statisticsInput 54 pdus (registration/deregistration pdus only)Reg pdus 37, Dereg pdus 17Output 54 pdus (registration/deregistration pdus only)Reg pdus 37, Dereg pdus 17iSNS Server 10.10.100.204Use the show isns command to view all objects registered on the iSNS server and specified in the given profile (see Example 35-21).
Example 35-21 Displays iSNS Queries
switch# show isns query ABC gigabitethernet 2/3iSNS server: 10.10.100.204Init: iqn.1991-05.com.w2kAlias: <MS SW iSCSI Initiator>Tgt : iqn.1987-05.com.cisco:05.172.22.94.22.02-03Tgt : iqn.1987-05.com.cisco:05.172.22.94.22.02-03.210000203762fa34nWWN: 200000203762fa34Use the show interface command to view the iSNS profile to which an interface is tagged (see Example 35-22).
Example 35-22 Displays Tagged iSNS Interfaces
switch# show interface gigabitethernet 2/3 GigabitEthernet2/3 is up Hardware is GigabitEthernet, address is 0005.3000.ae94Internet address is 10.10.100.201/24MTU 1500 bytesPort mode is IPSSpeed is 1 GbpsBeacon is turned offAuto-Negotiation is turned oniSNS profile ABC^^^^^^^^^^^^^^^^5 minutes input rate 112 bits/sec, 14 bytes/sec, 0 frames/sec5 minutes output rate 0 bits/sec, 0 bytes/sec, 0 frames/sec1935 packets input, 132567 bytes4 multicast frames, 0 compressed0 input errors, 0 frame, 0 overrun 0 fifo1 packets output, 42 bytes, 0 underruns0 output errors, 0 collisions, 0 fifo0 carrier errorsAbout iSNS Server Functionality
When enabled, the iSNS server on the Cisco 9000 Family MDS switch tracks all registered iSCSI devices. As a result, iSNS clients can locate other iSNS clients by querying the iSNS server. The iSNS server also provides the following functionalities:
•
Allows iSNS clients to register, deregister, and query other iSNS clients registered with the iSNS server.
•
Provides centralized management for enforcing access control to provide or deny access to targets from specific initiators.
•
Provides a notification mechanism for registered iSNS clients to receive change notifications on the status change of other iSNS clients.
•
Provides a single access control configuration for both Fibre Channel and iSCSI devices.
•
Discovers iSCSI targets that do not have direct IP connectivity to the iSCSI initiators.
Example Scenario
The iSNS server provides uniform access control across Fibre Channel and iSCSI devices by utilizing both Fibre Channel zoning information and iSCSI access control information and configuration. An iSCSI initiator acting as an iSNS client only discovers devices it is allowed to access based on both sets of access control information. Figure 35-22 provides an example of this scenario.
Figure 35-22 Using iSNS Servers in the Cisco MDS Environment
In Figure 35-22, iqn.host1 and iqn.host2 are iSCSI initiators. P1 and P2 are Fibre Channel targets. The two initiators are in different zones: Zone 1 consists of iqn.host1 and target P1, and Zone 2 consists of iqn.host2 and target P2. iSNS server functionality is enabled on both switches, SW-1 and SW-2. The registration process proceeds as follows:
1.
Initiator iqn.host1 registers with SW-1, port Gigabitethernet2/1.
2.
Initiator iqn.host2 registers with SW-2, port Gigabitethernet3/1.
3.
Initiator iqn.host1 issues an iSNS query to SW-1 to determine all accessible targets.
4.
The iSNS server in turn queries the Fibre Channel Name Server (FCNS) to obtain a list of devices that are accessible (that is, in the same zone) by the query originator. This query yields only P1.
5.
The iSNS server then queries its own database to convert the Fibre Channel devices to the corresponding iSCSI targets. This is based on the iSCSI configuration, such as virtual-target and its access control setting or whether the dynamic Fibre Channel target import feature is enabled or disabled.
6.
The iSNS server sends a response back to the query initiator. This response contains a list all iSCSI portals known to the iSNS server. This means iqn.host1 can choose to login to target P1 via either SW-1 (at Gigabitethernet 2/1) or SW-2 (at Gigabitethernet 3/1).
7.
If the initiator chooses to login to SW-1 and later that port becomes inaccessible (for example, Gigabitethernet 2/1 goes down), the initiator has the choice to move to connect to target P1 via port Gigabitethernet 3/1 on SW-2 instead.
8.
If the target either goes down or is removed from the zone, the iSNS server sends out an iSNS State Change Notification (SCN) message to the initiator so that the initiator can remove the session.
Configuring iSNS Servers
This section describe how to configure an iSNS server on a Cisco MDS 9000 Family switch.
Enabling the iSNS Server
Before iSNS server feature can be enabled, iSCSI must be enabled (see the "Enabling iSCSI" section). When you disable iSCSI, iSNS is automatically disabled. When the iSNS server is enabled on a switch, every IPS port whose corresponding iSCSI interface is up is capable of servicing iSNS registration and query requests from external iSNS clients.
To enable the iSNS server, follow these steps:
Note
If you are using VRRP IP addresses for discovering targets from iSNS clients, ensure that the IP address is created using the secondary option (see the "Virtual Router IP Address Addition" section on page 36-18).
iSCSI Configuration Distribution
You can use the CFS infrastructure to distribute the iSCSI initiator configuration to iSNS servers across fabric. This allows iSNS server running on any switch to provide to a querying iSNS client a list of iSCSI devices available anywhere on the fabric. For information on CFS, see the Chapter 5, "Using the CFS Infrastructure."
To enable configuration distribution, follow these steps:
Configuring the ESI Retry Count
The iSNS client registers information with its configured iSNS server using an iSNS profile. At registration, the client can indicate an entity status inquiry (ESI) interval of 60 seconds or more. If the client registers with an ESI interval set to zero (0), then the server does not monitor the client using ESI. In such cases, the client's registrations remain valid until explicitly deregistered or the iSNS server feature is disabled.
The ESI retry count is the number of times the iSNS server queries iSNS clients for their entity status. The default ESI retry count is 3. The client sends the server a response to indicate that it is still alive. If the client fails to respond after the configured number of retries, the client is deregistered from the server.
To configure the ESI retry count for an iSNS server, follow these steps:
iSNS Client Registration and Deregistration
An iSNS client cannot query the iSNS server until it has registered. You can use the show isns database command to display all registered iSNS clients and their associated configuration.
iSNS client deregistration can occur either explicitly or when the iSNS server detects that it can no longer reach the client (through ESI monitoring).
iSNS client registration and deregistration result in status change notifications (SCNs) being generated to all interested iSNS clients.
Target Discovery
iSCSI initiators discover targets by issuing queries to the iSNS server. The server supports DevGetNext requests to search the list of targets and DevAttrQuery to determine target and portal details, such as the IP address or port number to which to connect.
On receiving a query request from the iSCSI client, the iSNS server queries the Fibre Channel Name Server (FCNS) to obtain a list of Fibre Channel targets that are accessible by the querying initiator. The result of this query depends on zoning configuration currently active and current configuration(s) of the initiator. The iSNS server will subsequently use the iSCSI target configuration(s) (virtual target and dynamic import configuration) to translate the Fibre Channel target to an equivalent iSCSI target. At this stage it also applies any access control configured for the virtual target. A response message with the target details is then sent back to the query initiator.
The iSNS server sends a consolidated response containing all possible targets and portals to the querying initiator. For example, if a Fibre Channel target is exported as different iSCSI targets on different IPS interfaces, the iSNS server will respond with a list of all possible iSCSI targets and portals.
In order to keep the list of targets updated, the iSNS server sends state change notifications (SCN) to the client whenever an iSCSI target becomes reachable or unreachable. The client is then expected to rediscover its list of accessible targets by initiating another iSNS query. Reachability of iSCSI targets changes when any one of the following occurs:
1.
Target goes up or down
2.
Dynamic import of FC target configuration changes
3.
Zone set changes
4.
Default zone access control changes
5.
IPS interface state changes
6.
Initiator configuration that change make the target accessible or inaccessible.
Verifying the iSNS Server Configuration
Use the show isns config command to view the ESI interval and the summary information about the iSNS database contents (see Example 35-23).
Example 35-23 Displays the iSNS Server Configuration of ESI Interval and Database Contents
switch# show isns configServer Name: switch1(Cisco Systems) Up since: Fri Jul 30 04:08:16 2004Index: 1 Version: 1 TCP Port: 3205fabric distribute (remote sync): ONESINon Response Threshold: 5 Interval(seconds): 60Database contentsNumber of Entities: 2Number of Portals: 3Number of ISCSI devices: 4Number of Portal Groups: 0Use the show isns database command to view detailed information about the contents of the iSNS database (see Example 35-24 through Example 35-27). This command displays the full iSNS database giving all the entities, nodes, and portals registered in the database. This command without options only displays explicitly registered objects. The asterisk next to the VSAN ID indicates that the iSCSI node is in the default zone for that VSAN.
Example 35-24 Displays Explicitly Registered Objects
switch# show isns databaseEntity Id: dp-204Index: 2 Last accessed: Fri Jul 30 04:08:46 2004iSCSI Node Name: iqn.1991-05.comdp-2041Entity Index: 2Node Type: Initiator(2) Node Index: 0x1SCN Bitmap: OBJ_UPDATED|OBJ ADDED|OBJ REMOVED|TARGET&SELFNode Alias: <MS SW iSCSI Initiator>VSANS: 1(*), 5(*)Portal IP Address: 192.168.100.2 TCP Port: 4179Entity Index: 2 Portal Index: 1ESI Interval: 0 ESI Port: 4180 SCN Port: 4180Example 35-25 displays information about both virtual and registered iSCSI initiators/targets.
Example 35-25 Displays the Full Database With Both Registered and Configured Nodes and Portals
switch# show isns database fullEntity Id: isns.entity.mds9000Index: 1 Last accessed: Fri Jul 30 04:08:16 2004iSCSI Node Name: iqn.com.cisco.disk1Entity Index: 1Node Type: Target(1) Node Index: 0x80000001WWN(s):22:00:00:20:37:39:dc:45VSANS:iSCSI Node Name: iqn.isns-first-virtual-targetEntity Index: 1Node Type: Target(1) Node Index: 0x80000002VSANS:iSCSI Node Name: iqn.com.cisco.disk2Entity Index: 1Node Type: Target(1) Node Index: 0x80000003WWN(s):22:00:00:20:37:39:dc:45VSANS:Portal IP Address: 192.168.100.5 TCP Port: 3205Entity Index: 1 Portal Index: 3Portal IP Address: 192.168.100.6 TCP Port: 3205Entity Index: 1 Portal Index: 5Entity Id: dp-204Index: 2 Last accessed: Fri Jul 30 04:08:46 2004iSCSI Node Name: iqn.1991-05.com.microsoft:dp-2041Entity Index: 2Node Type: Initiator(2) Node Index: 0x1SCN Bitmap: OBJ_UPDATED|OBJ ADDED|OBJ REMOVED|TARGET&SELFNode Alias: <MS SW iSCSI Initiator>VSANS: 1(*), 5(*)Portal IP Address: 192.168.100.2 TCP Port: 4179Entity Index: 2 Portal Index: 1ESI Interval: 0 ESI Port: 4180 SCN Port: 4180Example 35-26 displays the virtual targets entries on the current switch.
Note
The local option is only available for virtual targets.
Example 35-26 Displays the Virtual Target Information in the Local Switch
switch# show isns database virtual-targets localEntity Id: isns.entity.mds9000Index: 1 Last accessed: Fri Jul 30 04:08:16 2004iSCSI Node Name: iqn.com.cisco.disk1Entity Index: 1Node Type: Target(1) Node Index: 0x80000001WWN(s):22:00:00:20:37:39:dc:45VSANS:iSCSI Node Name: iqn.isns-first-virtual-targetEntity Index: 1Node Type: Target(1) Node Index: 0x80000002VSANS:iSCSI Node Name: iqn.com.cisco.disk2Entity Index: 1Node Type: Target(1) Node Index: 0x80000003WWN(s):22:00:00:20:37:39:dc:45VSANS:Portal IP Address: 192.168.100.5 TCP Port: 3205Entity Index: 1 Portal Index: 3Portal IP Address: 192.168.100.6 TCP Port: 3205Entity Index: 1 Portal Index: 5Example 35-27 provides the virtual target information for a specific remote switch. The remote switch is specified using the switch ID (the WWN of the switch).
Example 35-27 Displays Virtual Target for a Specified Switch
switch# show isns database virtual-targets switch 20:00:00:0d:ec:01:04:40Entity Id: isns.entity.mds9000Index: 1 Last accessed: Fri Jul 30 04:08:16 2004iSCSI Node Name: iqn.com.cisco.disk1Entity Index: 1Node Type: Target(1) Node Index: 0x80000001WWN(s):22:00:00:20:37:39:dc:45VSANS:iSCSI Node Name: iqn.isns-first-virtual-targetEntity Index: 1Node Type: Target(1) Node Index: 0x80000002VSANS:iSCSI Node Name: iqn.com.cisco.disk2Entity Index: 1Node Type: Target(1) Node Index: 0x80000003WWN(s):22:00:00:20:37:39:dc:45VSANS:Portal IP Address: 192.168.100.5 TCP Port: 3205Entity Index: 1 Portal Index: 3Portal IP Address: 192.168.100.6 TCP Port: 3205Entity Index: 1 Portal Index: 5Use the show isns node command to display attributes of nodes registered with the iSNS server (see Example 35-28 through Example 35-30). If you do not specify any options the server displays the name and node type attribute in a compact format; one per line.
Example 35-28 Displays Explicitly Registered Objects
switch# show isns node all-------------------------------------------------------------------------------iSCSI Node Name Type-------------------------------------------------------------------------------iqn.1987-05.com.cisco:05.switch1.02-03.22000020375a6c8 Target...iqn.com.cisco.disk1 Targetiqn.com.cisco.ipdisk Targetiqn.isns-first-virtual-target Targetiqn.1991-05.cw22 Targetiqn.1991-05.cw53 TargetExample 35-29 Displays of the Specified Node
switch# show isns node name iqn.com.cisco.disk1iSCSI Node Name: iqn.com.cisco.disk1Entity Index: 1Node Type: Target(1) Node Index: 0x80000001WWN(s):22:00:00:20:37:39:dc:45VSANS: 1Example 35-30 Displays the Attribute Details for All Nodes
switch# show isns node all detailiSCSI Node Name: iqn.1987-05.com.cisco:05.switch1.02-03.22000020375a6c8fEntity Index: 1Node Type: Target(1) Node Index: 0x3000003Configured Switch WWN: 20:00:00:0d:ec:01:04:40WWN(s):22:00:00:20:37:5a:6c:8fVSANS: 1...iSCSI Node Name: iqn.com.cisco.disk1Entity Index: 1Node Type: Target(1) Node Index: 0x80000001Configured Switch WWN: 20:00:00:0d:ec:01:04:40WWN(s):22:00:00:20:37:39:dc:45VSANS: 1iSCSI Node Name: iqn.com.cisco.ipdiskEntity Index: 1Node Type: Target(1) Node Index: 0x80000002Configured Switch WWN: 20:00:00:0d:ec:01:04:40WWN(s):22:00:00:20:37:5a:70:1aVSANS: 1iSCSI Node Name: iqn.isns-first-virtual-targetEntity Index: 1Node Type: Target(1) Node Index: 0x80000003Configured Switch WWN: 20:00:00:0d:ec:01:04:40iSCSI Node Name: iqn.parna.121212Entity Index: 1Node Type: Target(1) Node Index: 0x80000004Configured Switch WWN: 20:00:00:0d:ec:01:04:40iSCSI Node Name: iqn.parna.121213Entity Index: 1Node Type: Target(1) Node Index: 0x80000005Configured Switch WWN: 20:00:00:0d:ec:01:04:40Use the show isns portal command to display the attributes of a portal along with its accessible nodes (see Example 35-31 through Example 35-35). You can specify portals by using the switch WWN-interface combination or the IP address-port number combination.
Example 35-31 Displays the Attribute Information for All Portals
switch# show isns portal all-------------------------------------------------------------------------------IPAddress TCP Port Index SCN Port ESI port-------------------------------------------------------------------------------192.168.100.5 3205 3 - -192.168.100.6 3205 5 - -Example 35-32 Displays Detailed Attribute Information for All Portals
switch# show isns portal all detailPortal IP Address: 192.168.100.5 TCP Port: 3205Entity Index: 1 Portal Index: 3Portal IP Address: 192.168.100.6 TCP Port: 3205Entity Index: 1 Portal Index: 5Example 35-33 Displays Virtual Portals
switch# show isns portal virtual-------------------------------------------------------------------------------IPAddress TCP Port Index SCN Port ESI port-------------------------------------------------------------------------------192.168.100.5 3205 3 - -192.168.100.6 3205 5 - -Example 35-34 Displays Virtual Portals for the Specified Switch
switch# show isns portal virtual switch 20:00:00:0d:ec:01:04:40-------------------------------------------------------------------------------IPAddress TCP Port Index SCN Port ESI port-------------------------------------------------------------------------------192.168.100.5 3205 3 - -192.168.100.6 3205 5 - -Example 35-35 Displays Detailed Information for the Virtual Portals in the Specified Switch
switch# show isns portal virtual switch 20:00:00:0d:ec:01:04:40 detailPortal IP Address: 192.168.100.5 TCP Port: 3205Entity Index: 1 Portal Index: 3Switch WWN: 20:00:00:0d:ec:01:04:40Interface: GigabitEthernet2/3Portal IP Address: 192.168.100.6 TCP Port: 3205Entity Index: 1 Portal Index: 5Switch WWN: 20:00:00:0d:ec:01:04:40Interface: GigabitEthernet2/5Use the show isns entity command to display the attributes of an entity along with the list of portals and nodes in that entity (see Example 35-36 through Example 35-40). If you do not specify any option, this command displays the entity ID and number of nodes or portals associated with the entity in a compact format; one per line.
Example 35-36 Displays All Registered Entries
switch1# show isns entity-------------------------------------------------------------------------------Entity ID Last Accessed-------------------------------------------------------------------------------dp-204 Tue Sep 7 23:15:42 2004Example 35-37 Displays All Entities in the Database
switch# show isns entity all-------------------------------------------------------------------------------Entity ID Last Accessed-------------------------------------------------------------------------------isns.entity.mds9000 Tue Sep 7 21:33:23 2004dp-204 Tue Sep 7 23:15:42 2004Example 35-38 Displays the Entity with the Specified ID
switch1# show isns entity id dp-204Entity Id: dp-204Index: 2 Last accessed: Tue Sep 7 23:15:42 2004Example 35-39 Displays Detailed Information for All Entities in the Database
switch1# show isns entity all detailEntity Id: isns.entity.mds9000Index: 1 Last accessed: Tue Sep 7 21:33:23 2004Entity Id: dp-204Index: 2 Last accessed: Tue Sep 7 23:16:34 2004Example 35-40 Displays Virtual Entities
switch# show isns entity virtualEntity Id: isns.entity.mds9000Index: 1 Last accessed: Thu Aug 5 00:58:50 2004Entity Id: dp-204Index: 2 Last accessed: Thu Aug 5 01:00:23 2004Use the show iscsi global config command to display information about import targets (see Example 35-41 and Example 35-42).
Example 35-41 Displays the Import Target Settings for the Specified Switch
switch# show isns iscsi global config switch 20:00:00:05:ec:01:04:00iSCSI Global configuration:Switch: 20:00:00:05:ec:01:04:00 iSCSI Auto Import: EnabledExample 35-42 Displays the Import Target Settings for All Switches
switch# show isns iscsi global config alliSCSI Global configuration:Switch: 20:00:44:0d:ec:01:02:40 iSCSI Auto Import: EnabledUse the show cfs peers command to display CFS peers switch information about the iSNS application (see Example 35-43).
Example 35-43 Displays the CFS Peer Switch Information for the iSNS Application
switch# show cfs peers name isnsScope : Physical--------------------------------------------------Switch WWN IP Address--------------------------------------------------20:00:00:00:ec:01:00:40 10.10.100.11 [Local]Total number of entries = 1Default Settings
Table 35-2 lists the default settings for iSCSI parameters.

 Feedback
Feedback