802.1x Wired Authentication on a Catalyst 3550 Series Switch and an ACS Version 4.2 Configuration Example
Available Languages
Contents
Introduction
This document provides a basic IEEE 802.1x configuration example with Cisco Access Control Server (ACS) Version 4.2 and the Remote Access Dial In User Service (RADIUS) protocol for wired authentication.
Prerequisites
Requirements
Cisco recommends that you:
- Confirm IP reachability between ACS and the switch.
- Ensure that User Datagram Protocol (UDP) Ports 1645 and 1646 are open between ACS and the switch.
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Catalyst 3550 Series Switches
- Cisco Secure ACS Version 4.2
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Configure
Example Switch Configuration
- In order to define the RADIUS server and pre-shared key, enter this command:
Switch(config)# radius-server host 192.168.1.3 key cisco123
- In order to enable 802.1x functionality, enter this command:
Switch(config)# dot1x system-auth-control
- In order to globally-enable Authentication, Authorization, and Accounting (AAA) and RADIUS authentication and authorization, enter these commands:
Switch(config)# aaa new-model
Switch(config)# aaa authentication dot1x default group radius
awitch(Config)# aaa authorization network default group radius
Switch(Config)# aaa accounting dot1x default start-stop group radiusSwitch(config-if)# switchport mode acces
Switch(config-if)# switchport access vlan <vlan>
Switch(config-if)# authentication port-control auto (12.2.50 SE and later)
Switch(config-if)# dot1x port-control auto (12.2.50 SE and below)
Switch(config-if)# dot1x pae authenticator (version 12.2(25)SEE and below)
Switch(config-if)# dot1x timeout quiet-period <seconds to wait after failed attempt>
Switch(config-if)# dot1x timeout tx-period <time to resubmit request>
ACS Configuration
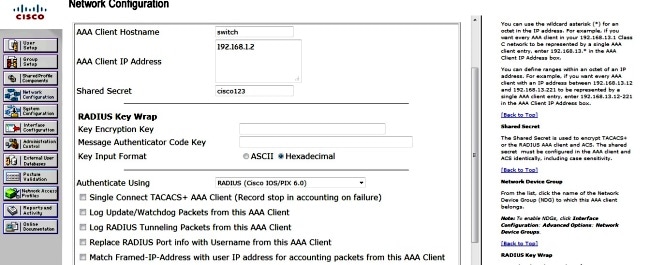
- In order to add the switch as an AAA client in ACS, navigate to Network Configuration > Add entry AAA client, and enter this information:
- IP Address: <IP>
- Shared secret: <key>
- Authenticate Using: Radius (Cisco IOS®/PIX 6.0)
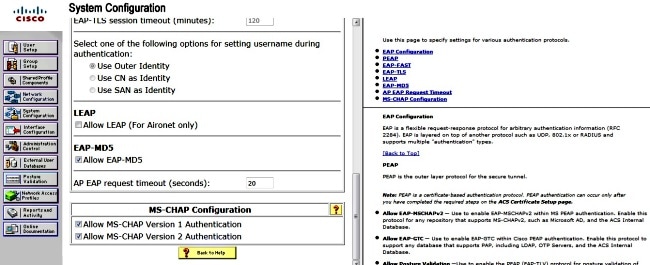
- In order to configure the authentication setup, navigate to System Configuration > Global Authentication Setup, and verify that the Allow MS-CHAP Version 2 Authentication check box is checked:
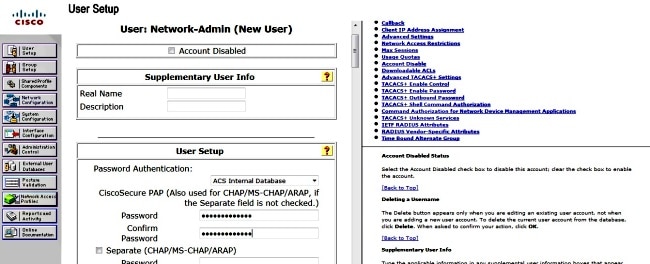
- In order to configure a user, click User Setup on the menu, and complete these steps:
- Enter the User information: Network-Admin <username>.
- Click Add/Edit.
- Enter the Real Name: Network-Admin <descriptive name>.
- Add a Description: <your choice>.
- Select the Password Authentication: ACS Internal Database.
- Enter the Password: ........ <password>.
- Confirm the Password: <password>.
- Click Submit.
Verify
The Output Interpreter Tool (registered customers only) supports certain show commands. Use the Output Interpreter Tool in order to view an analysis of show command output.
Enter these commands in order to confirm that your configuration works properly:
- show dot1x
- show dot1x summary
- show dot1x interface
- show authentication sessions interface <interface>
- show authentication interface <interface>
Switch(config)# show dot1x
_________________________________________________
Sysauthcontrol Enabled
Dot1x Protocol Version 3
_________________________________________________
Switch(config)# show dot1x summary
_________________________________________________
Interface PAE Client Status
_________________________________________________
Fa0/4 AUTH
_________________________________________________
Switch(config)# show dot1x interface fa0/4 detail
_________________________________________________
Dot1x Info for FastEthernet0/4
_________________________________________________
PAE = AUTHENTICATOR
PortControl = FORCE_AUTHORIZED
ControlDirection = Both
HostMode = SINGLE_HOST
QuietPeriod = 5
ServerTimeout = 0
SuppTimeout = 30
ReAuthMax = 2
MaxReq = 2
TxPeriod = 10
Troubleshoot
This section provides debug commands that you can use in order to troubleshoot your configuration.
- debug dot1x all
- debug authentication all
- debug radius (provides the information of radius at debug level)
- debug aaa authentication (debug for authentication)
- debug aaa authorization (debug for authorization)
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
09-Sep-2013 |
Initial Release |



 Feedback
Feedback