What are OT security best practices?
Because operational networks are based on IT technologies, OT security requires the same cybersecurity solutions as IT networks do, like perimeter security, endpoint protection, multifactor authentication (MFA), and team training. Specific measures must be enforced to support the particular nature of OT environments. Cisco Industrial Threat Defense, Cisco’s OT security solution, can help you strengthen your OT security posture.
Restrict communications between IT and OT domains
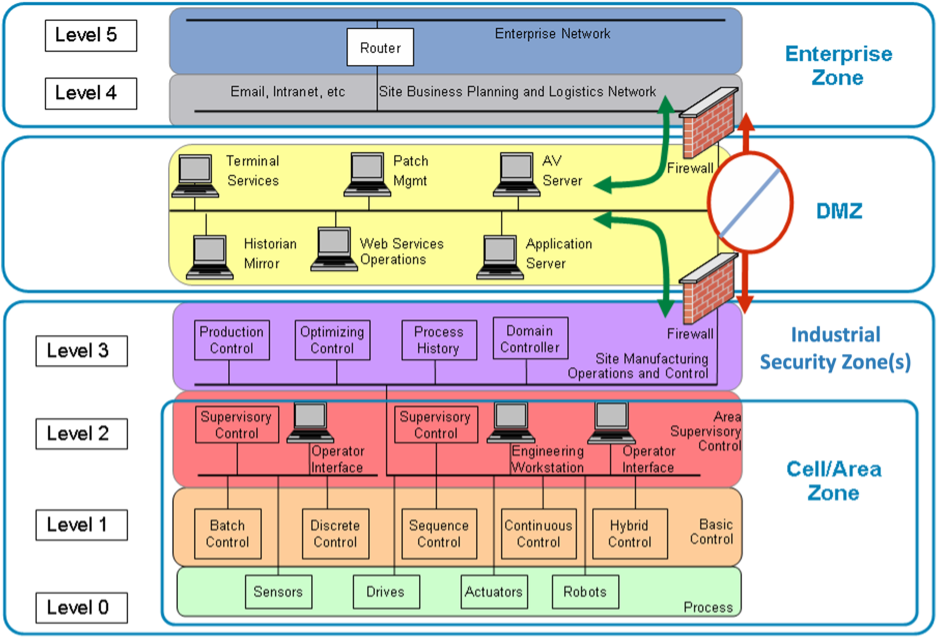
The first step in the journey to OT security is to restrict logical access to the OT network. A common setup method is an IDMZ network with firewalls that prevent network traffic from passing directly between the corporate and OT networks. The IDMZ firewall is the first line of defense that attackers meet when trying to breach the network and is the enforcement point for least-privilege access for legitimate services to cross the border in a secure way.
Explore Cisco Secure Firewall >
Maintain a detailed inventory of OT assets
You can’t secure what you don’t know. Maintaining a detailed inventory of operational technology assets is a prerequisite to an OT security program. Visibility into the OT environment helps in identifying risks like software vulnerabilities, unknown assets, IDMZ leaks, and unnecessary communications activities. It helps organizations to understand the difference between attacks and transient conditions or normal operations of the OT network.
Explore Cisco Cyber Vision >
Segment OT networks into smaller zones of trust
Many industrial networks have grown over the years to become large, flat, layer-2 networks. It’s now critical to restrict communications between assets to prevent attacks from spreading and disrupting the entire production infrastructure. The ISA/IEC-62443 security standards recommend that systems be separated into groups called "zones" that communicate with each other through channels called "conduits."
Using firewalls for zone segmentation requires deploying dedicated security appliances, changing network wiring, and maintaining firewall rules. Fortunately, you can use software segmentation to enforce security policies and create secure zones across the industrial network without having to deploy and maintain dedicated security appliances.
Explore Cisco Identity Services Engine (ISE) >
Enforce zero-trust remote access to OT assets
Remote access is key to managing and troubleshooting OT assets without time-consuming and costly site visits. In many organizations, machine builders, maintenance contractors, or the operations teams themselves have installed cellular gateways or remote access software that IT does not control. On the other hand, virtual private networks (VPNs) installed in the IDMZ require the maintenance of complex firewall rules and can’t access devices behind NAT boundaries.
Zero-trust network access (ZTNA) solutions are gaining increased attention to help organizations to reduce cyber risks. ZTNA is a secure remote access service that verifies users and grants access only to specific resources according to identity and context policies. It starts with a default deny posture and adaptively offers the appropriate trust required at the time. But in OT environments, ZTNA needs to be distributed to simplify deployment at scale and provide access to all assets.
Explore Cisco Secure Equipment Access (SEA) >
Give security teams a global vision across IT and OT
In addition to identifying and protecting OT assets, OT security needs to detect and respond to cybersecurity events. OT security is often managed in a silo, preventing security analysts from seeing the global threat landscape that the organization is facing. Security operations teams need solutions allowing them to easily investigate observables across the IT and OT domains, and launch remediation workflows to prevent a threat from crossing domains.
Explore Cisco XDR >
Be ready for the worst
The ideal cybersecurity response starts before an emergency does. Training employees in cybersecurity best practices should happen regularly in all organizations. Getting your OT security ready also means testing your defense, building playbooks, and running tabletop exercises.
Explore Cisco Talos Incident Response services >