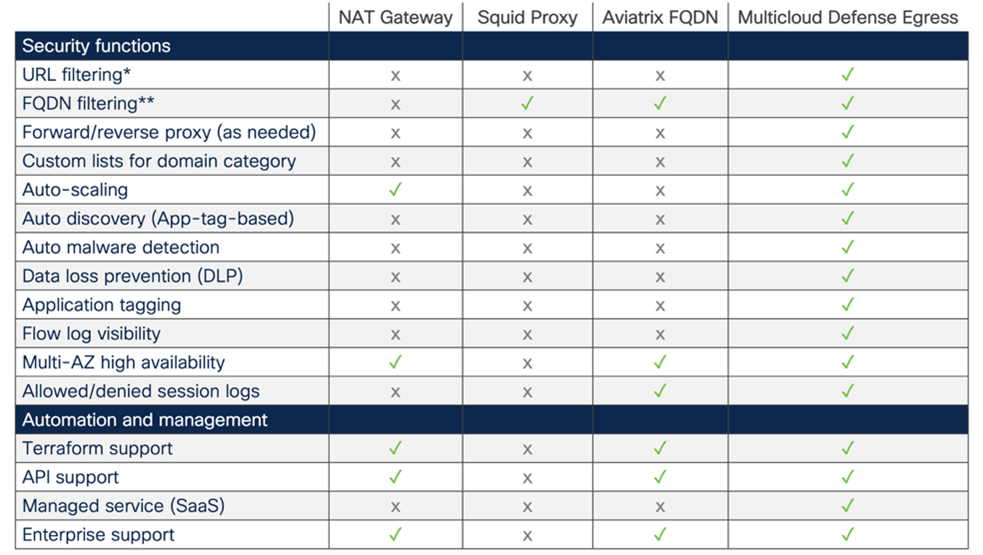
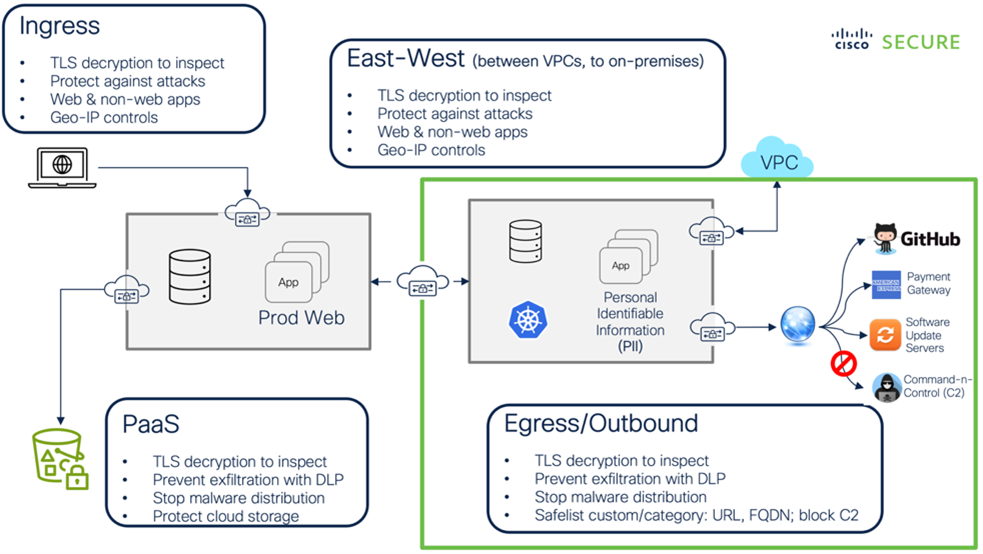
Cloud egress security and firewall
Deploying egress security with Multicloud Defense can be achieved in these three steps:
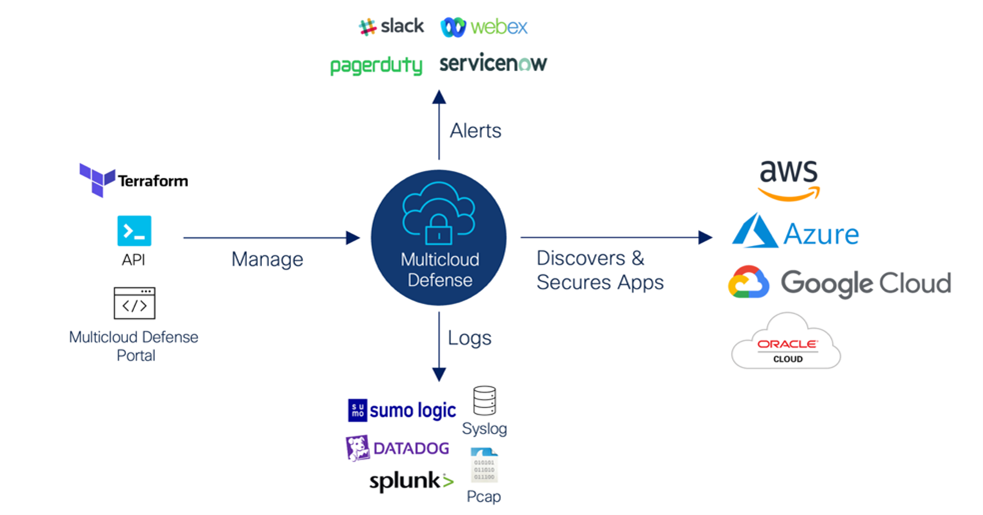
Initiate discovery: The discovery capability empowers an evergreen model of running cloud applications, auto-detecting changes, and providing the needed insights into security requirements. Coupling discovery with tag-based policy capabilities inside Multicloud Defense simplifies policy management, providing near real-time policy updates in constantly changing environments.
Deploy security: The deployment architecture is driven by the discovery. Auto-scaled, provisioned, and network-plumbed security (agent-less) with single-click deployment objectives. Support for AWS, Azure, and GCP cloud deployments and network pathing with infrastructure as code (IaC) automation (Terraform and API) without the need to build and manage a complex control plane.
Defend your networks: Write custom security policies to protect your applications as you determine their need, and that may include some, or all, of the following defense functions:
- URL plus fully qualified domain name (FQDN) filtering: Custom plus domain categories
- TLS decryption/re-encryption with single pass deep packet inspection (DPI)
- Advanced web application firewall (WAF)
- Network protection (IDS/IPS) plus malicious sources
- Egress security in public cloud