Tunnel Management with Pre-Shared Key
A unique pre-shared key (PSK) solution is used for the tunnel management between FAR and HER, which significantly simplifies the authentication and authorization process in the headend infrastructure and allows the users to self-manage. The PSK is supported on all Cisco IOS and IOS-XE device types.
The table provides various scenarios where PSK can be used effectively in combination with either SUDI or a CA server in the greenfield deployment.
|
Deployment |
Scenario |
Recommendation |
||
|---|---|---|---|---|
|
Greenfield deployment |
Without CA server |
|
||
|
With CA server |
Choose one of the following combinations:
(or)
|
|||
|
||||
 Note |
For the brownfield deployment, IoT FND continues to support CA, RA, and AAA for the FAR communication with FND and HER. |
Configuring FND for Tunnel Management with PSK
Use the following steps to configure FND for managing tunnels with PSK.
Procedure
|
Step 1 |
Run the following script to configure FND with IPAM and PSK settings.  |
|
Step 2 |
On entering "y", you are provided with a new option to select PSK scheme for IPsec tunnel management. 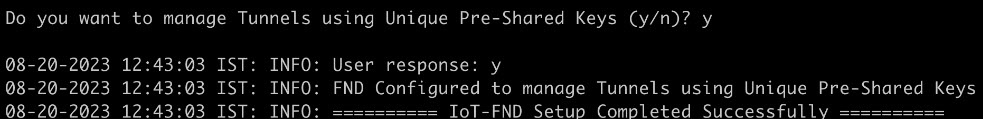 |
|
Step 3 |
On entering "y", FND is configured with PSK. FND updates the Preferences table by setting the property com.cisco.cgms.pnp.tunnelMgmtUsingPsk as True. By default, this property is False. |
Generating PSK
A unique pre-shared key is generated when you import a device through CSV or NB API. The pre-shared key is a 15-character alphanumeric string which is unique and generated randomly for each device. The generated key is encrypted and stored in the database for each router. For more information on tunnel management with PSK, see Workflow for Tunnel Management with PSK.
Default templates
Templates are used for pushing the configuration commands and data to devices from Cisco IoT FND. Templates help in configuring many devices simultaneously with a single file. Numerous templates are available for tunnel management based on different device configurations.
These default templates are available for tunnel management:
-
Router Tunnel Addition Template,
-
HER Tunnel Addition Template,
-
Router Bootstrap Configuration Template,
-
HER Tunnel FlexVPN Configuration Template.
| Release Information |
Feature Name |
Description |
|---|---|---|
|
Cisco IoT FND Release 4.11.0 |
Tunnel Management with pre-shared key (PSK) |
PSK is used during the tunnel provisioning to authenticate the communication between FAR and HER. This feature reduces the certificate dependency for tunnel formation. If PSK is enabled as part of Cisco IoT FND installation, then Cisco IoT FND generates a unique pre-shared key for each FAR in Cisco IoT FND. . |
|
Cisco IoT FND Release 5.1 |
Template Versioning |
Template versioning allows you to create new Cisco IoT FND templates with unique version numbers from both existing as well as newly created templates. You can create, edit, save or delete templates using template versioning in Cisco IoT FND. |
Template versioning in Cisco IoT FND
Starting from the Cisco IoT FND release 5.1.0, you can create new templates with unique version numbers from both existing as well as newly created templates. You can use the templates for pushing configuration commands from Cisco IoT FND to devices.
Template versioning lets you track and manage changes to your configuration templates. You can save the latest template as a new version or choose to select an existing template from the previously saved versions for configuring devices in Cisco IoT FND.
Consider these points before using template versioning in Cisco IoT FND:
-
The template's version number is assigned automatically by Cisco IoT FND itself in a sequential order.
-
The first template which already exists is referred to as the default template.
-
The latest template version is auto-selected and appears in the combo box with a text area, which you can use for editing configuration details of any device.
-
Whenever Cisco IoT FND is upgrade to 5.1.0 from the earlier versions, then the previous version template appears as the latest template version in Cisco IoT FND 5.1.0. Also, the default template version is created based on the device types.
-
For config groups prior to Cisco IoT FND release 5.1.0, the latest template version will be version-2 and in Cisco IoT FND release 5.1.0 the default template is version-1.
-
For tunnel provisioning groups, prior to Cisco IoT FND release 5.1.0, the latest template version will be version-1 and in Cisco IoT FND release 5.1.0 the default template is version-0.
-
Template versioning does not apply to individual devices and you need to consider this before using the Device Info > Push Configuration option.
Supported devices
Template versioning is enabled for these devices in Cisco IoT FND, which are running:
|
Software |
Routers |
|---|---|
|
Cisco IOS XE |
The supported routers running Cisco IOS XE:
|
|
Cisco IOS |
The supported running Cisco IOS:
|
Benefits of template versioning
The template versioning feature allows you to:
-
Easily identify and manage previously used templates with different version numbers.
-
Reuse or modify configuration details of devices by creating a new template with the latest version.
-
Easily track modifications and revert to previously saved template configurations.
-
Refer to template changes for troubleshooting purposes.
Configure template using device configuration
Use this task to save a template.
Before you begin
You need to consider the following points before configuring and saving new templates:
-
When you edit or make changes to any existing template then that template becomes the latest template.
-
You can only save the latest version of the template which can be used to generate the next version of the template later.
-
All previous versions of the templates except the latest version will appear as read only templates and you cannot edit or modify these versions.
-
There is no maximum limit set for the number of templates that you can create at any given time.
-
You can save a new version of the template even if Target Firmware Version is changed in the Router Bootstrap Configuration tab.
-
The default template version is version-1 in CONFIG > Device Configuration page.
Procedure
|
Step 1 |
From the Cisco IoT FND menubar, select CONFIG > Device Configuration. |
|
Step 2 |
Select the router from the router group. |
|
Step 3 |
Click Edit Configuration Template. |
|
Step 4 |
Edit the latest template using the text area which appears with the template. |
|
Step 5 |
Click Save. |
 Note |
If you click Save without modifying the latest template, then you will receive a message stating that there were no changes made in the template. In this case, edit the template and then try saving it again. |
What to do next
Configure template using tunnel provisioning page
Use this task to save a template.
Before you begin
You need to consider the following points before configuring and saving new templates:
-
When you edit any existing template or make changes to the existing template then that template becomes the latest template.
-
You can only save the latest version of the template which can be used to generate the next version of the template later.
-
All previous versions of the templates other than the latest version will appear as read only templates and you cannot edit or modify them.
-
There is no maximum limit set for the number of templates that you can create at any given time.
-
The default template version is version-0 in the CONFIG > Tunnel Provisioning page.
Procedure
|
Step 1 |
From the Cisco IoT FND menubar, select CONFIG > Tunnel Provisioning page. |
|
Step 2 |
Choose and click from the menu options as given:
|
|
Step 3 |
Select router from the router group. |
|
Step 4 |
Edit the latest template using the text area. |
|
Step 5 |
Click Save. |
 Note |
If you click Save without modifying the latest template, then you will receive a message indicating there were no changes made in the template. In this case you can try creating the template once again. |
What to do next
View template using device configuration
Use this task to view template using device configuration option.
Procedure
|
Step 1 |
From the Cisco IoT FND menubar, select CONFIG > Device Configuration. |
|
Step 2 |
Select router from the router group. |
|
Step 3 |
Select the template version you want to view from the Template Version drop-down list. |
You will see the template details displayed in the text area.
View template using tunnel provisioning
Use this task to view template using tunnel provisioning option.
Procedure
|
Step 1 |
From the Cisco IoT FND menubar, select CONFIG. |
|
Step 2 |
From CONFIG page, choose and click from the menu options as given:
|
|
Step 3 |
Select router from the router group. |
|
Step 4 |
Select the template version you want to view from the Template Version drop-down list. |
You will see the template details displayed in the text area.
Delete template
Use these steps to delete a template.
Before you begin
You cannot delete the latest template and the default template versions as the delete button is disabled for these versions.
You can access the template versioning combo box , by selecting one of these two navigation paths in Cisco IoT FND from the Cisco IoT FND menubar:
-
CONFIG > Device Configuration.
-
CONFIG >
-
Tunnel Provisioning > Router Tunnel Addition,
-
Tunnel Provisioning > HER Tunnel Addition,
-
Tunnel Provisioning > HER Tunnel Deletion,
-
Tunnel Provisioning > Router Bootstrap Configuration.
-
Procedure
|
Step 1 |
From the template versioning combo box select a template version. |
|
Step 2 |
Click Delete. |
The template is deleted.
Router tunnel addition template
There are two default router addition templates available for authentication. Based on the configuration settings in setupCgms.sh, the default template is selected to manage tunnels using PSK.
Configure router tunnel addition using template
Use this task to configure the router tunnel addition using template.
Before you begin
 Note |
By default, the peer name is set to her-tunnel in crypto ikev2 keyring FlexVPN_Keyring and Flexvpn_ikev2_profile. You can configure the peer name to match the name that is given in identity local key-id in the HER configuration. |
Procedure
|
Step 1 |
Edit the template as given in the example to configure router tunnel addition. Example: |
|
Step 2 |
Save the template. |
HER tunnel addition template
Similar to Router Tunnel Addition templates, there are two default HER tunnel addition templates available. Based on the configuration settings in setupCgms.sh, the default template is selected to manage tunnels using PSK or not.
Configure HER tunnel addition template
Use this task to configure HER tunnel addition using template.
Procedure
|
Step 1 |
Edit the template as given in the example to configure HER tunnel addition. Example: |
|
Step 2 |
Save the template. |
Router bootstrap configuration template
 Note |
For SUDI authentication, you must use cgna initiator profile as the tunnel profile. |
 Note |
Based on the device types, the following ports are used:
|
Configure router bootstrap using template
Use this task to configure router bootstrap using template.
Procedure
|
Step 1 |
Edit the template as given in the example to configure router bootstrap. Example: |
||
|
Step 2 |
Edit the template as given in the example to configure ACL optionally as an additional security step. Example:
|
||
|
Step 3 |
Save the template. |
HER tunnel FlexVPN configuration template
You can configure HER tunnel FlexVPN using a template.
Configure HER tunnel FlexVPN using template
Use this task to configure the HER tunnel FlexVPN using template.
Procedure
|
Step 1 |
Edit the template as given in the example to configure HER tunnel FlexVPN. Example: |
|
Step 2 |
Save the template. |
HER tunnel deletion template
 Note |
Ensure that the keyring name mentioned in "crypto ikev2 keyring FlexVPN_Keyring" and "FlexVPN_IKEv2_Profile" match the HER keyring name. |
Configure HER tunnel deletion using template
Use this task to configure HER tunnel deletion using template.
Procedure
|
Step 1 |
Edit the template as given in the example to configure HER tunnel deletion for HERs on Cisco IOS and Cisco IOS-XE. Example: |
|
Step 2 |
Save the template. |
IPv4/IPv6 host resolution during device upgrade to Cisco IOS XE Release 17.12 and later releases
This task enables you to reliably manage hostname resolution on Cisco IOS XE devices across upgrades and downgrades by explaining
the dual (split) versus single-line ip host behavior. This guidance helps you update templates, understand checkpoint/config file handling, and verify outcomes during
tunnel provisioning and config pushes, avoiding configuration loss after upgrades.
Here is a list of context for you to keep in mind:
-
Applies to Cisco IOS-XE devices only.
-
Cisco IOS-XE Release 17.12 and earlier releases behavior: Devices use split host entries per IP family (dual entries). For example: ip host fnd.iot.cisco.com 198.51.100.10 ip host fnd.iot.cisco.com 2001:db8:1000:10::10 -
Cisco IOS-XE Release 17.12 and later releases behavior: Devices expect a single host entry that combines IPv4 and IPv6 on the same line (single-line). For example: ip host fnd.iot.cisco.com 198.51.100.10 2001:db8:1000:10::10 -
When you upgrade a Cisco IOS XE device from 17.12 to later releases, the device continues to receive split host entries, the first entry is replaced by the second entry and it is used for resolution. Cisco IoT FND checks the device OS version; if it is greater than Cisco IOS XE Release 17.12, Cisco IoT FND normalizes host entries to a single line (IPv4 + IPv6) in checkpoint files.
Here are the checkpoint filenames:
express-setup-config,before-tunnel-config, andbefore-registration-config. -
When you downgrade, Cisco IoT FND splits entries back into separate IPv4 and IPv6 lines.
-
Templates continue to contain split entries, a config push or tunnel provisioning can override normalized lines on the device. Templates must be edited to align with the device version behavior. Here are the examples of templates: Default Router Bootstrap Configuration Template, Device-level Configuration Templates, and Router Tunnel Addition Template.
Before you begin
-
Use
show running-config | sec hoston the device to confirm the current host entry format. -
Confirm device versions and identify which devices are running Cisco IOS XE Release 17.12 and later releases.
Procedure
|
Step 1 |
Update the templates to match device behavior. Example:Example: |
|
Step 2 |
Initiate tunnel provisioning or device-level config pushes from Cisco IoT FND. Ensure that the templates already match the expected format; otherwise, a push may override normalization. |
Devices on Cisco IOS XE release 17.12 and later releases receive and retain single-line ip host entries, preserving both IPv4 and IPv6 resolution on one line.
Configuring ZTD Properties
The ZTD Properties section allows you to manage the device certificates with either SUDI or a CA server. On configuring FND with PSK for tunnel management, by default, the devices use SUDI certificate for the communication with FND. However, if you want to manage using a CA server, provide details in the SCEP URL and CA Fingerprint fields ().

Changes To TCL Script
This section explains about the two different versions of a TCL script used for configuring a trustpoint in a network device managed using Cisco IoT FND. The trustpoint is part of the device Public Key Infrastructure (PKI), which handles certificates and cryptographic keys.
TCL Script For Cisco IOS XE Release 17.4.x And Lower Releases
Here's the original TCL script version released in Cisco IOS XE Release 17.4.x and lower releases:
set clist [ list "config terminal" \
"crypto pki trustpoint $tp_name" \
"serial-number none" \
"ip-address none" \
"password" \
"no subject-name" \
"subject-name $subject_name" \
"enrollment retry count $ZTD_SCEP_enrollment_retry_count" \
"enrollment retry period $ZTD_SCEP_enrollment_retry_period" \
"crypto pki enroll $tp_name" \
"end"] Updated Script For Cisco IOS XE Release 17.9.x And Later Releases
Here's the updated TCL script starting from Cisco IOS XE Release 17.9.x and later releases:
set clist [ list "config terminal" \
"crypto pki trustpoint $tp_name" \
"serial-number none" \
"ip-address none" \
"no subject-name" \
"subject-name $subject_name" \
"enrollment retry count $ZTD_SCEP_enrollment_retry_count" \
"enrollment retry period $ZTD_SCEP_enrollment_retry_period" \
"end"]
Reason For The Changes
The script is modified to no longer use an empty password, aligning with the new PKI policy that recommends to migrate to strong type-6 encryption.
 Note |
Starting from Cisco IOS XE Release 17.9.x and later releases, the Subject Alternative Name (SAN) is included with the Certificate Signing Request (CSR). For more information see, CSCsk85992. |
Workflow for Tunnel Management with PSK
This section provides the workflow for tunnel management with PSK.
Staging
To stage the router with Cisco IoT FND TPS URL:
Procedure
|
Step 1 |
Configuring Cisco IoT FND for PSK-based tunnels differ for each deployment as given below. For VM deployment with Postgres DB, as the cgms service will already be running on OVA installation, the cgms service is restarted using the steps below while executing setupCgms.sh script. In this deployment, user creates a new Tunnel Provisioning group for PSK based tunnel management configuration. |
|
Step 2 |
Generate a public CA signed server certificate for TPS and Cisco IoT FND using the existing CSR generation workflow. |
|
Step 3 |
Configure FlexVPN on HER. For more information on the configuration, see HER tunnel FlexVPN configuration template. |
|
Step 4 |
Import the device to Cisco IoT FND through CSV or NB API.
Cisco IoT FND generates a unique pre-shared key for each device and adds the generated key to the device property while storing in the database. |
|
Step 5 |
Stage the router with Cisco IoT FND TPS URL using DHCP option 43 or PnP Install Trustpool / Cloud Redirection for PnP. |
What to do next
PnP Bootstrapping
To bootstrap a device:
Before you begin
Procedure
|
Step 1 |
Field area router (PnP agent) calls FND (through FND TPS). |
||
|
Step 2 |
FND pushes the Trust Anchor (root certificate) to the device. |
||
|
Step 3 |
To push the FAR PSK to the associated HER, a new state CONFIGURING_HEADEND is added in PnP.
|
||
|
Step 4 |
FND pushes the Bootstrap template to the device, which includes a tunnel creation profile and loopback IP configuration. For more information on the default templates, see Default templates. |
||
|
Step 5 |
On successful completion of PnP, the device status is marked as Bootstrapped in FND. |
What to do next
Tunnel Provisioning
To push the PSK configuration to the router:
Before you begin
Procedure
|
Step 1 |
Field area router calls FND (through FND TPS). Authentication based on mTLS:
|
|
Step 2 |
FND pushes the PSK along with other tunnel configurations present in the Router Tunnel Addition template to the router and activates the registration profile.
|
What to do next
Device Configuration
To push device configuration to the router:
Before you begin
Complete the following workflows:
Procedure
|
Step 1 |
Field area router calls FND (through IPsec). Authentication based on mTLS:
|
|
Step 2 |
FND pushes the device configuration present in the Configuration Template to the router. |
|
Step 3 |
On successful completion, the device is marked as UP in FND. |
Pushing PSK Configuration to HER Cluster
This section explains the steps that are required to push the PSK configuration to HER in the cluster.
Pushing PSK Configuration to Existing HERs in the Cluster
Use the following steps to push the PSK configuration to the existing HERs in the cluster, which are added to the cluster before the tunnel establishment.
Procedure
|
Step 1 |
Import all HERs in the cluster to FND and have them managed with the device status as UP. |
|
Step 2 |
For FND to be aware of the list of HERs in a cluster, add the list of HER eids separated by comma in the tunnelhereid property. |
|
Step 3 |
On receiving a PnP request from a FAR, the tunnelhereid property is checked to get the list of HERs in the cluster. |
|
Step 4 |
PSK configuration is pushed to each HER in the cluster.
|
Pushing PSK Configuration to New HER in the Cluster
Use the following steps to push the PSK configuration to a new HER, which is added to the cluster after the tunnel is established.
 Note |
The addition or removal of HERs from the tunnelHerEid list is added to a table named pending_tunnel_her_in_cluster in the DB. FND has a separate thread that runs every five minutes to pick up the entries from the table and based on the add_peer flag, it either pushes the PSK configuration or removes the PSK configuration to or from the HER. |
Procedure
|
Step 1 |
Import the new HER to FND and have it managed with the device status as UP. |
||
|
Step 2 |
Update the FAR using Change Device Properties to add the new HER to the tunnelhereid property list.
|
||
|
Step 3 |
The PSK configuration is pushed to the new HER added to the tunnelHerEid property list and an associated event (success or failure) is generated on the FAR. If any HER is removed from the tunnelHerEid property, then the PSK configuration of that HER is removed and an event is generated for successful configuration removal on the HER. |
Viewing Events
This section provides information on the events generated on FAR and HER when pushing and removing PSK tunnel configuration.
Viewing FAR Events
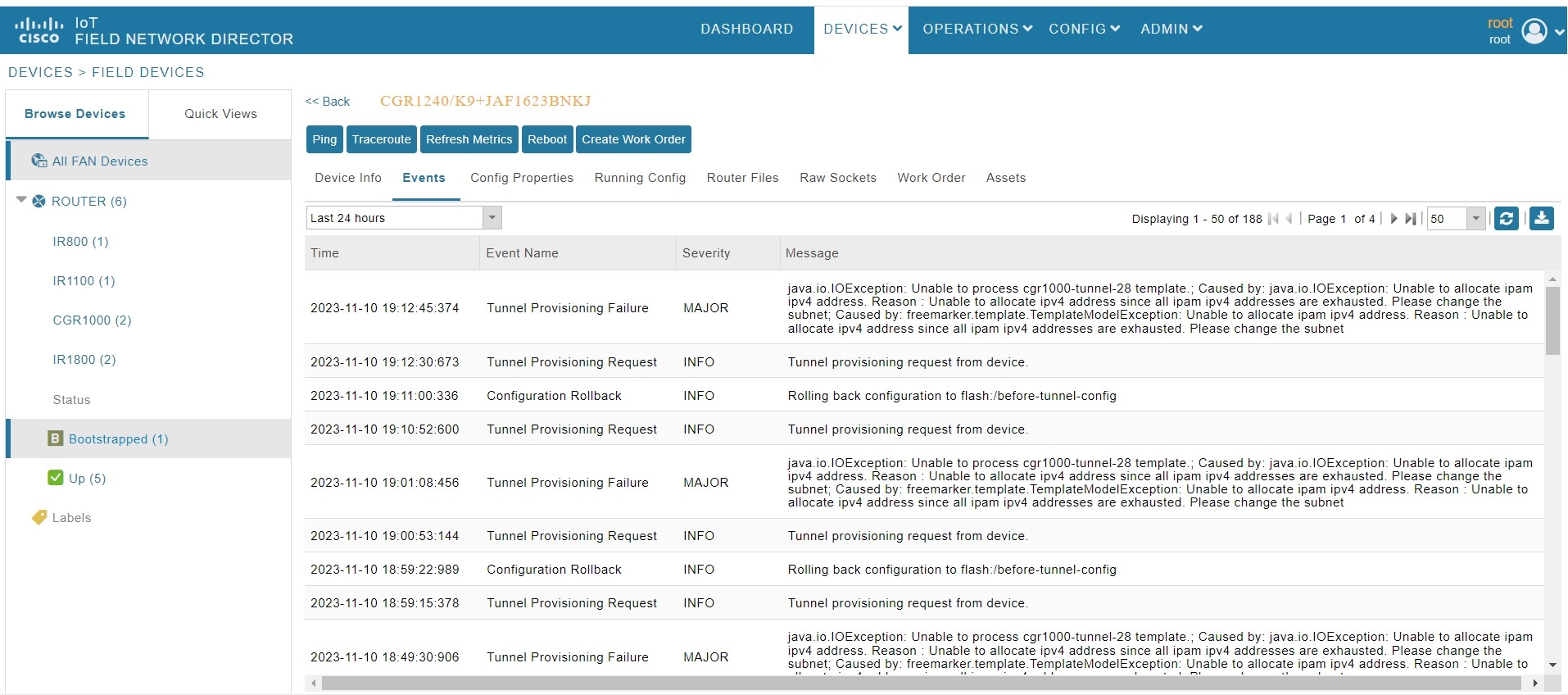
Use the following steps to view the events generated when pushing PSK tunnel configuration on HER during FAR onboarding.
-
Choose .
-
Select the device on the right pane. The Device Info page appears.
-
Click the Events tab to view the following events.
Event Name
Severity Level
Description
PSK Tunnel Configuration Pushed to HER
INFO
On successful completion of pushing PSK tunnel configuration on HER.
PSK Tunnel Configuration on HER Failed
Major
On failure to push the PSK tunnel configuration on HER.
Viewing HER Events
Use the following steps to view the events generated when removing the PSK tunnel configuration from HER and FAR during FAR decommissioning.
-
Choose .
-
Select the HER on the right pane. The Device Info page appears.
-
Click the Events tab to view the following events.
Event Name
Severity Level
Description
HER PSK Tunnel Configuration Removed for FAR
INFO
On successful removal of PSK configuration from HER.
HER PSK Tunnel Configuration Removal Failure for FAR
Major
On failure to remove the PSK configuration from HER.
Note
In this case, you should remove the PSK configuration from HER manually.
HER Mapping with FAR
Use the following steps to view the HERs associated with the FAR.
-
Choose .
-
Select the device on the left pane.
-
Click the HER Mapping tab on the right pane.
-
The HER associated with the device appears under the Tunnel HER EID column.
Use the filter option to search for HERs based on HER EID.
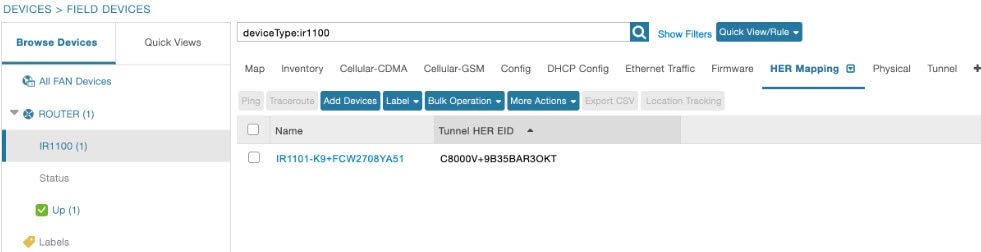
Decommissioning a Device
Whenever there is a device decommissioning, FND automatically removes the PSK configuration from HER using the HER deletion template which is available by default. If the HER is in a cluster, FND removes the PSK configuration from all HERs.
For information on HER deletion template, see HER tunnel deletion template.
For information on events generated during PSK configuration removal from HER, see Viewing HER Events.


 Feedback
Feedback