Networks are complicated to manage.
Multiple devices, apps, locations, and user policies have made the network very difficult to manage and have severely limited scalability.
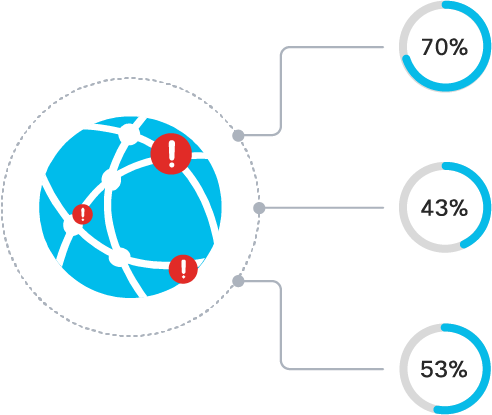
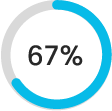
Over 70% of security breaches start on endpoints.2
Troubleshooting is difficult.
IT can’t troubleshoot problems if it can’t replicate them or see them in real time. That slows down resolution times.
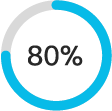
43% of IT’s time is spent troubleshooting the network.3
Security concerns are increasing.
Hackers evolve as network technology does, and the more complex the network is, the harder it is to secure it.
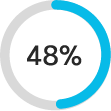
Over 53% of midmarket companies have experienced a security breach.4