TLS Gateway
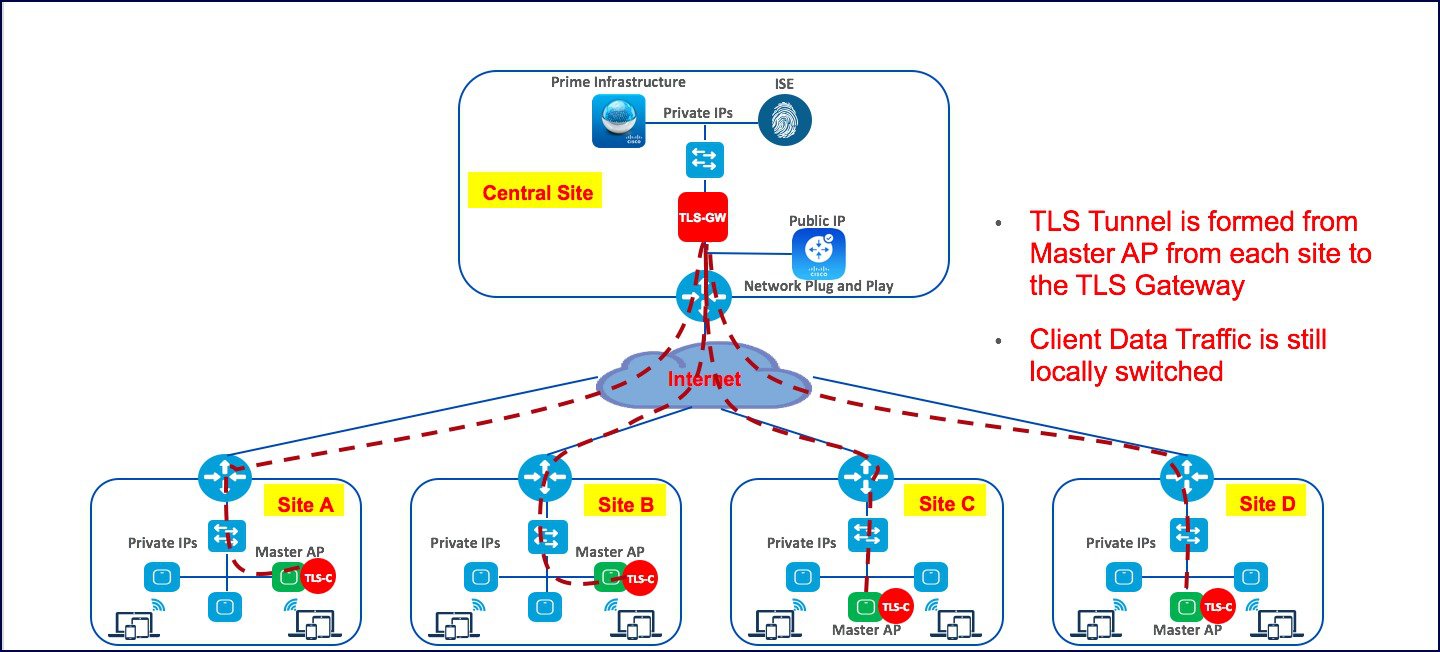
TLS Gateway is virtual machine and is deployed at the central site.
System Requirement for TLS Gateway
-
Hypervisor: VMware–ESXi 5.5.0/ESXI 6.0
-
VM Resources
-
4 vCPU
-
8GB RAM
-
100 GB Storage
-
2 NICs (One for Public network and one Private network)
-
-
IP routing requirements
-
Routing enabled from TLS-GW Private network towards Prime-infra(SNMP), ISE(Radius), DHCP servers, SSH, Monitoring system and vice-versa
-
-
TLS-GW public IP should be Reachable from Management IP of ME-AP
Deploying TLS Gateway
Please follow the steps below to deploy a TLS Gateway at the central site.
Procedure
| Step 1 |
Secure the TLS Gateway OVA File |
| Step 2 |
Navigate to File > Deploy OVF Template on the vSphere Client UI.  |
| Step 3 |
Browse to the TLS Gateway OVA file on your local machine. Click Next. 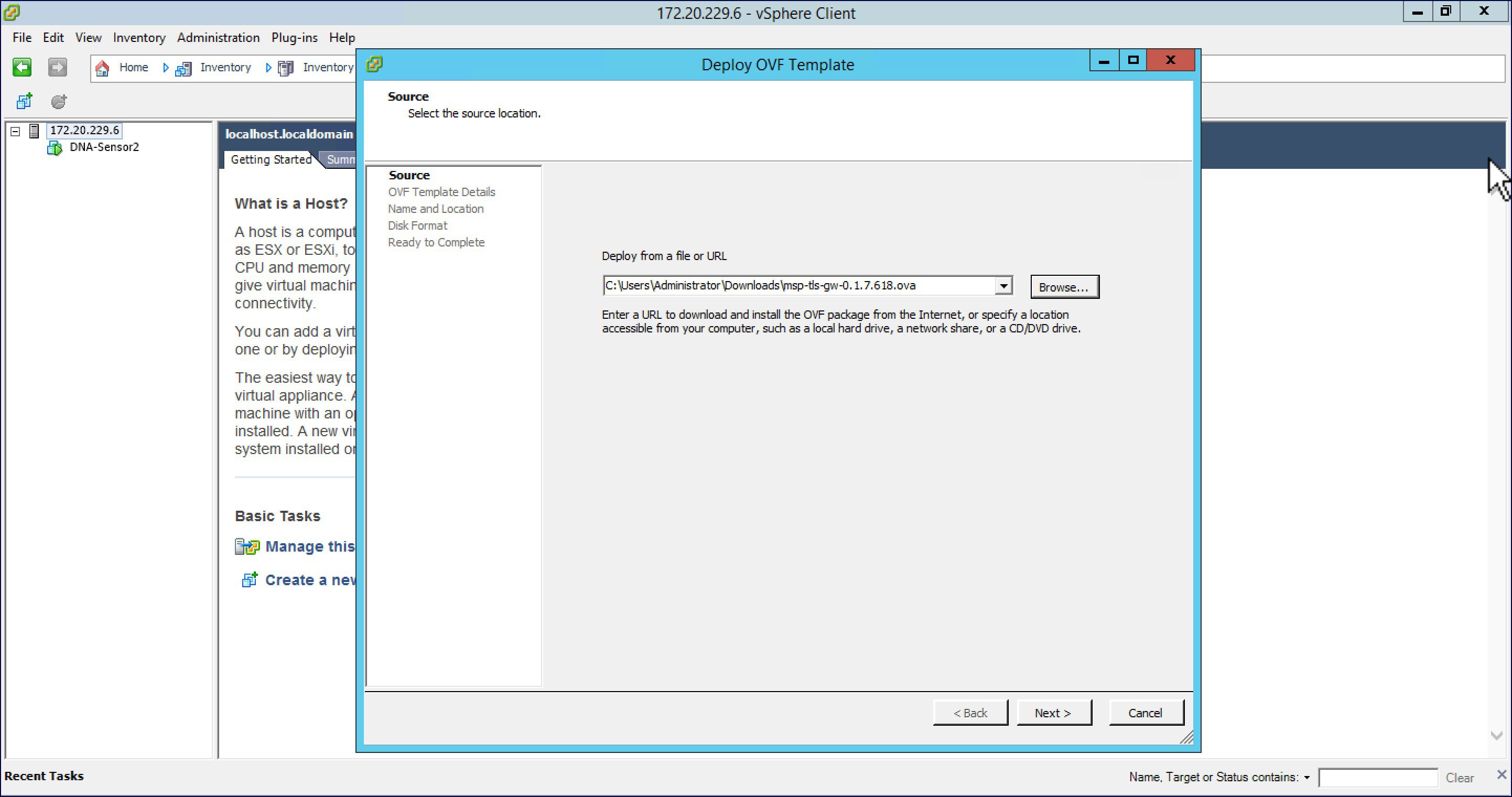 |
| Step 4 |
Check the OVF Template details and click Next. 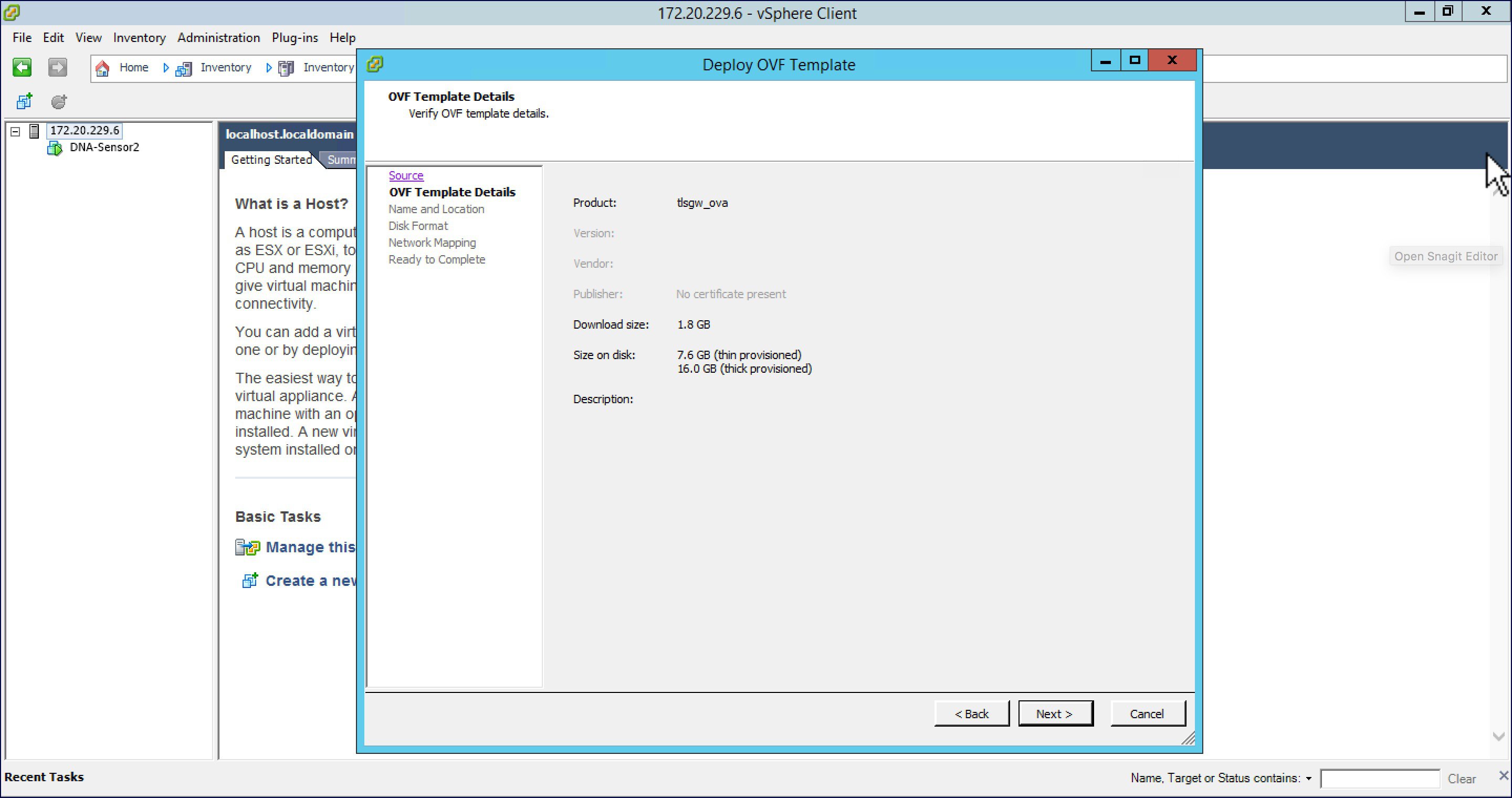 |
| Step 5 |
Specify the name for the TLS Gateway Virtual Machine. 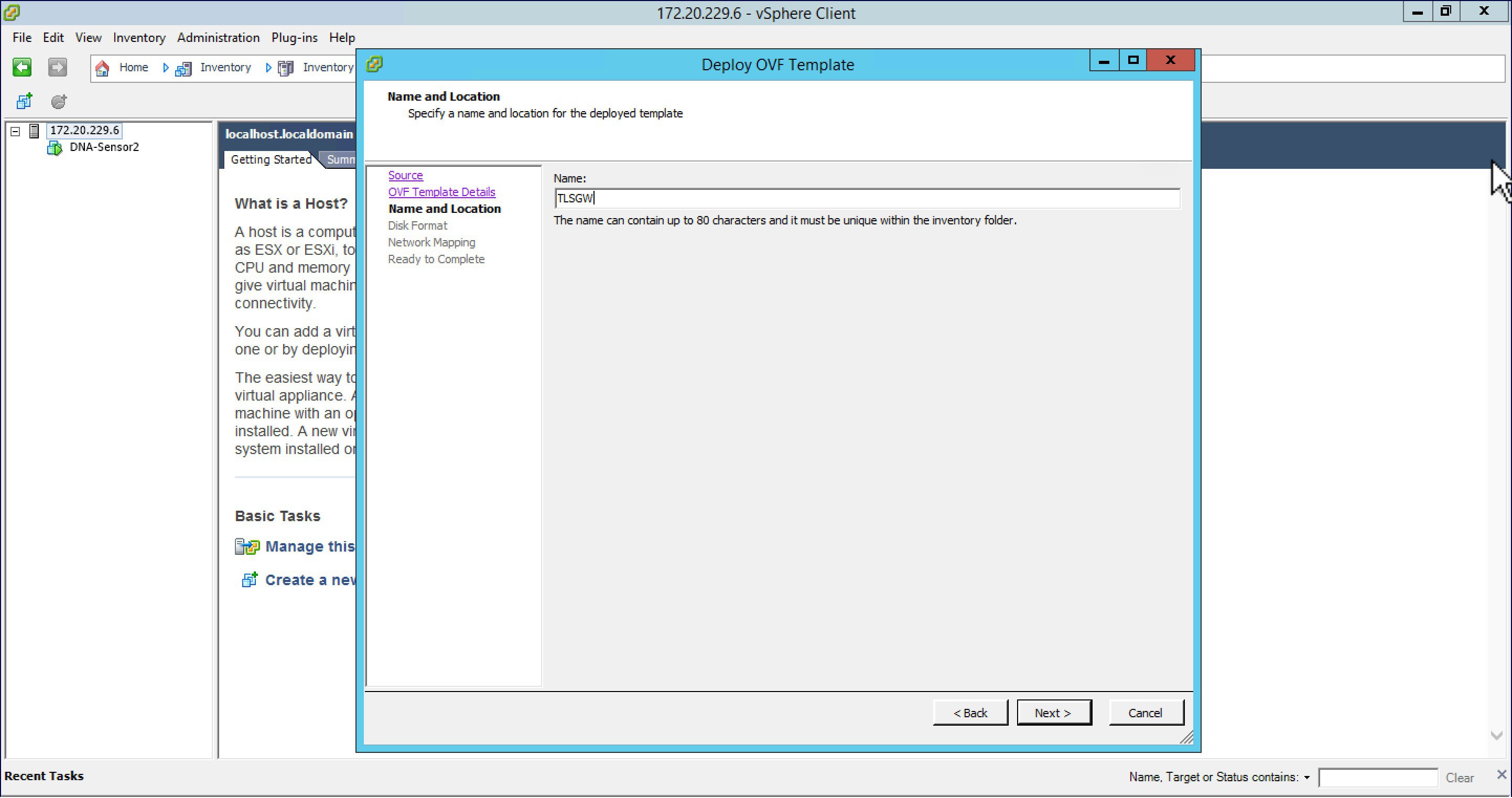 |
| Step 6 |
For Disk Format, stay with the default and click Next. 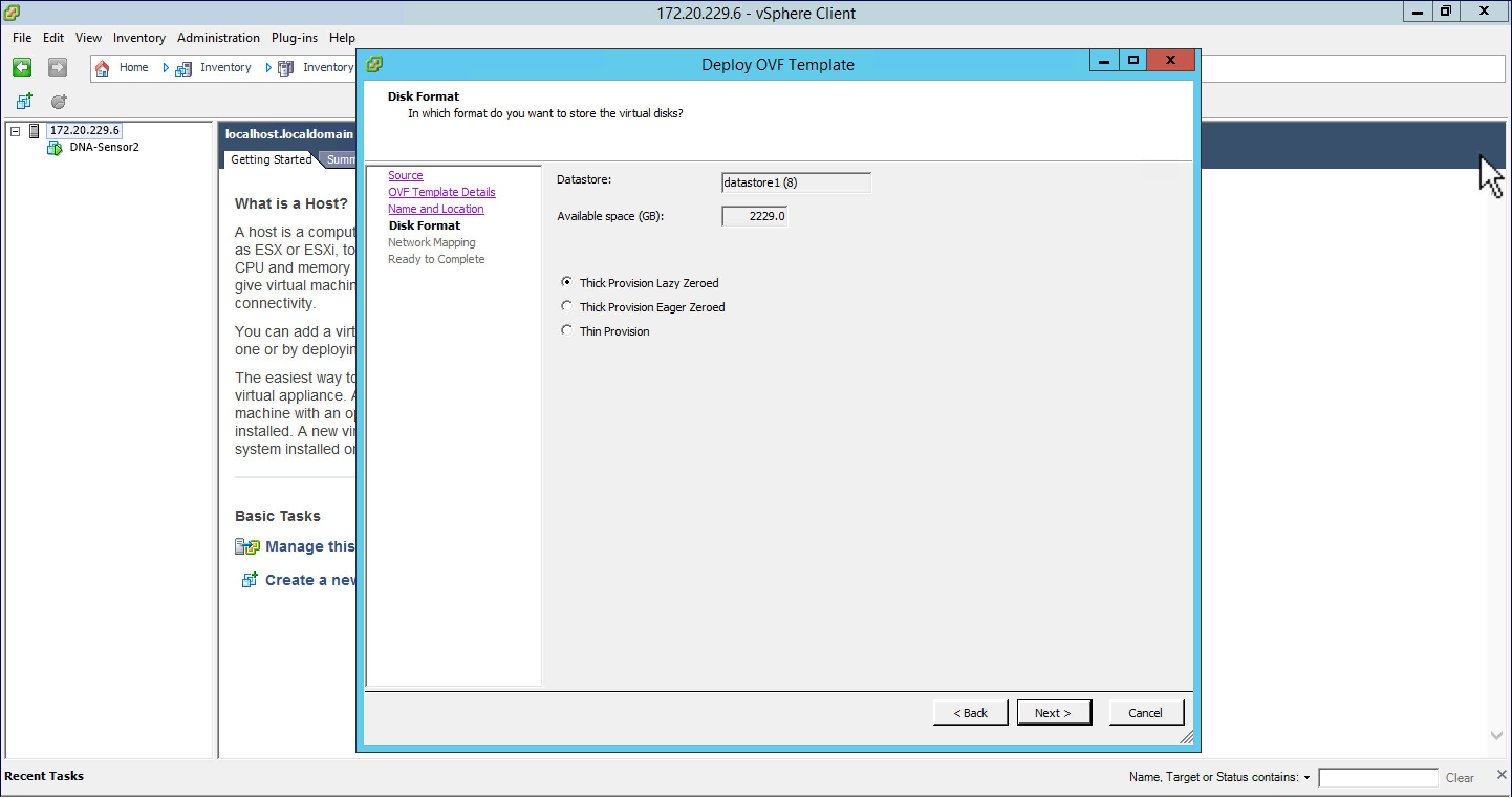 |
| Step 7 |
For Network Mapping, select the Destination Network for the Public Network interface. Click on Next. 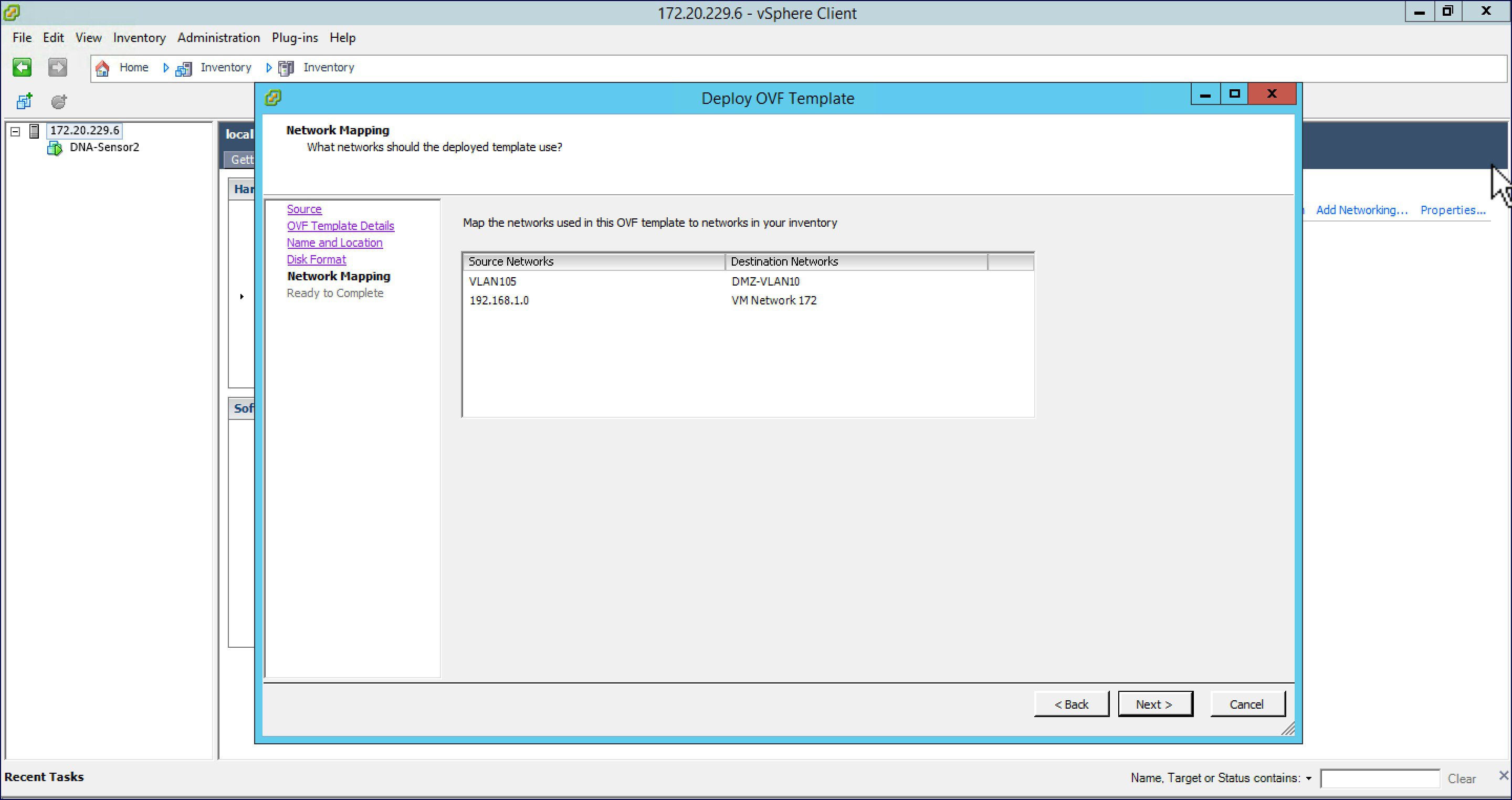 |
| Step 8 |
Verify the Deployment Settings. Enable the 'Power On after deployment' check box and click Finish. 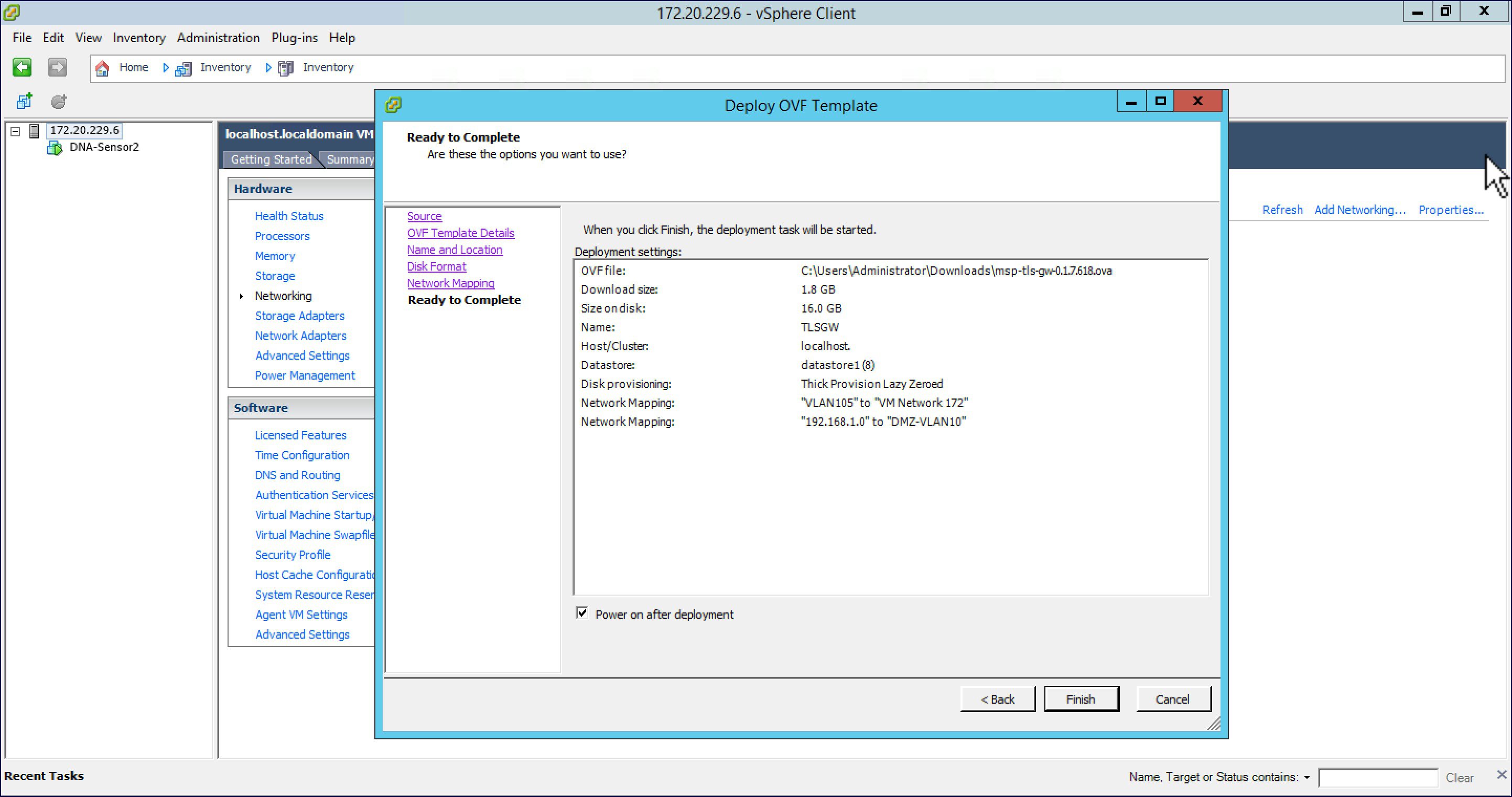 |
Configuring TLS Gateway
Configuring the TLS Gateway comprises of 3 things:
-
Configure the IP address for Public and Private network interfaces
-
Configure the TLS Gateway configuration file and start the service
-
Configuring the PSK ID-KEY Pair
After the OVA for TLS Gateway is deployed and powered up, follow the steps below to configure the TLS Gateway.
Configuring IP Address for Public and Private network interfaces
Procedure
| Step 1 |
Open a console session to the TLS Gateway VM and login using the following credentials: username: tlsgw password: tlsgw 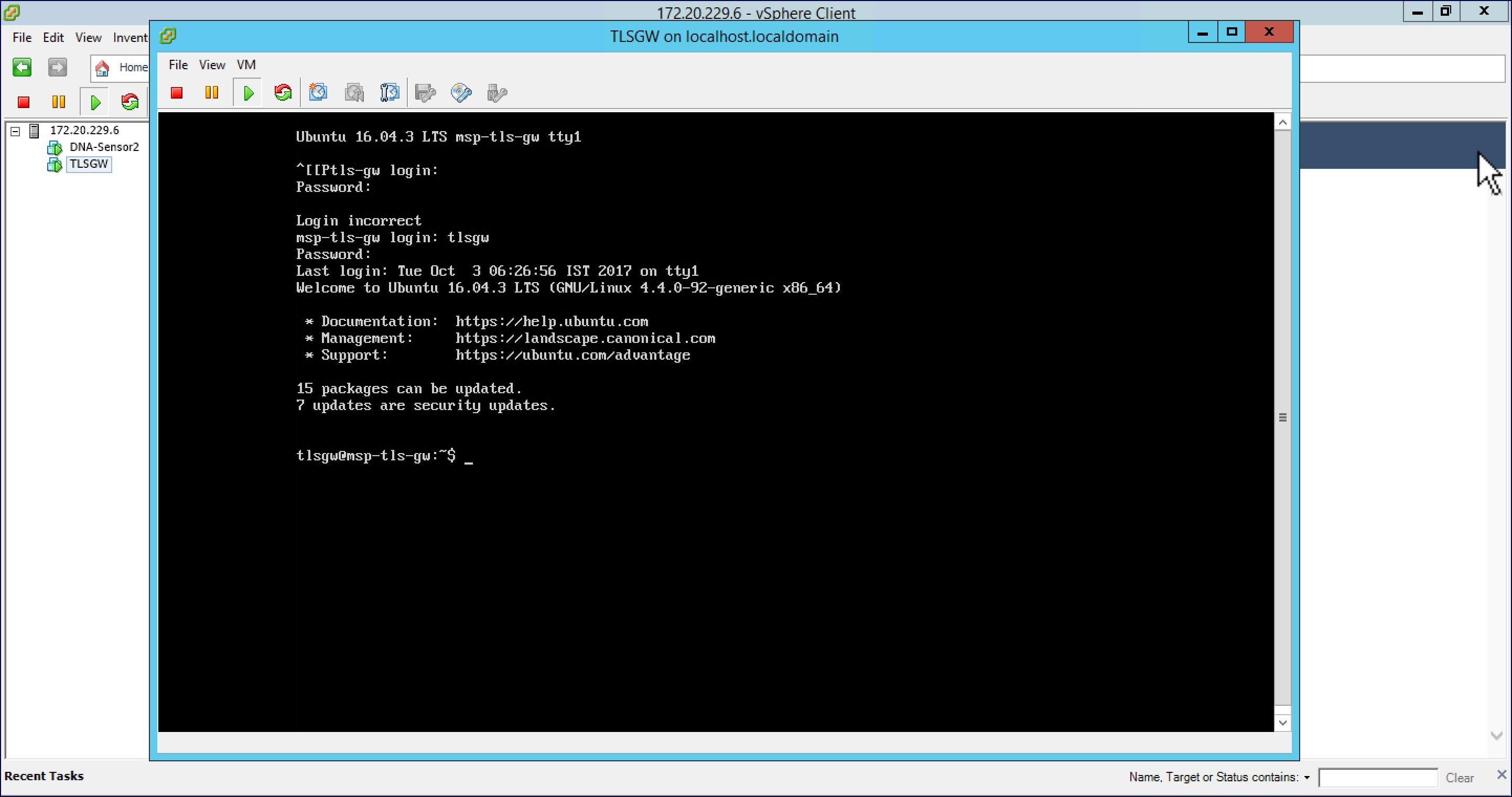 |
||
| Step 2 |
Type ifconfig to verify the IP address of the Public and Private interfaces as shown below. 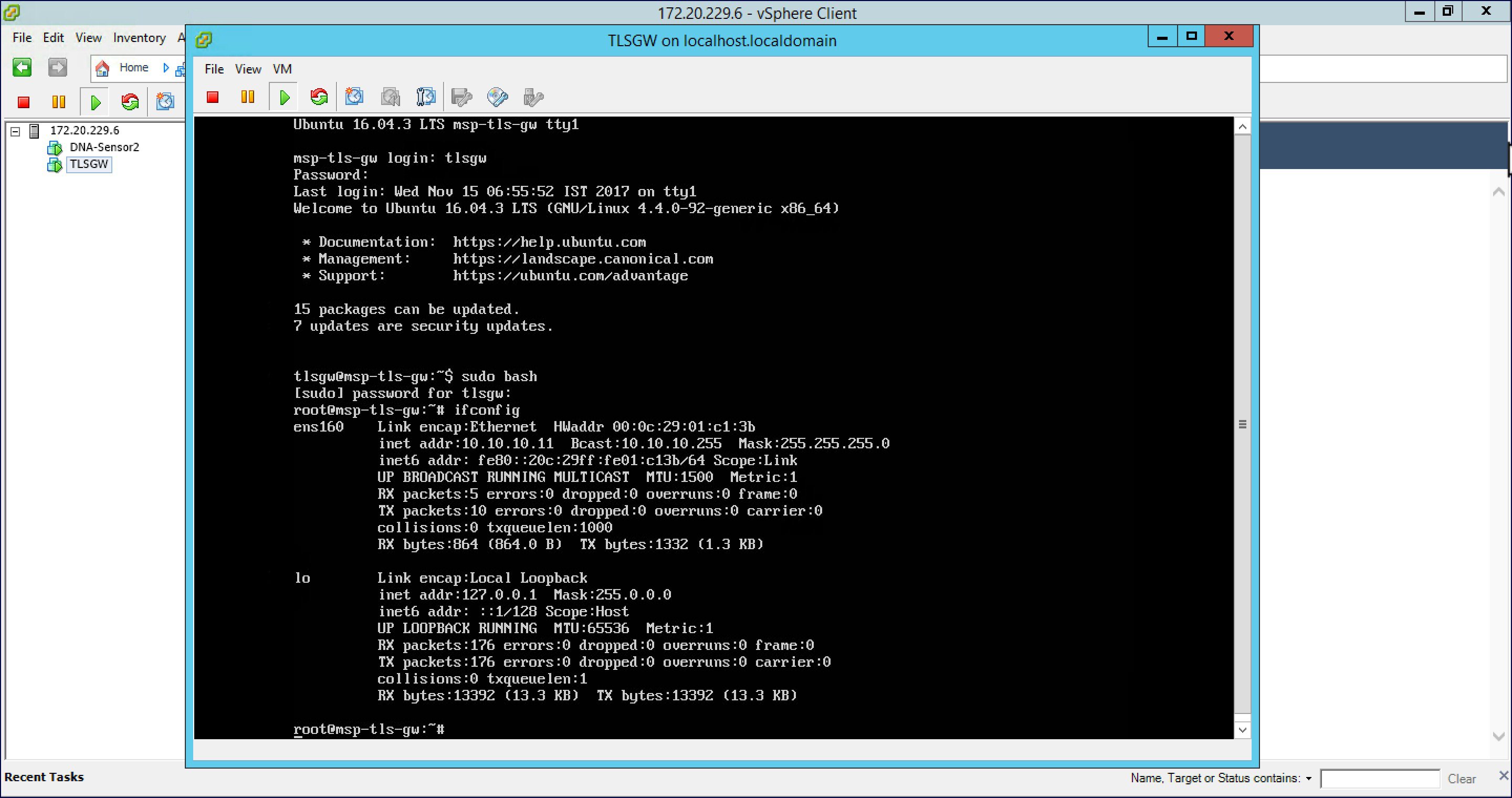
|
||
| Step 3 |
At the tlsgw@msp-tls-gw: prompt type sudo bash and enter tlsgw as the [sudo] password for tlsgw. |
||
| Step 4 |
To configure IP address for Public and Private network interface go to /etc/network directory by typing cd /etc/interfaces at the shell. |
||
| Step 5 |
Open the interfaces file using vi editor by typing vi interfaces at the shell. 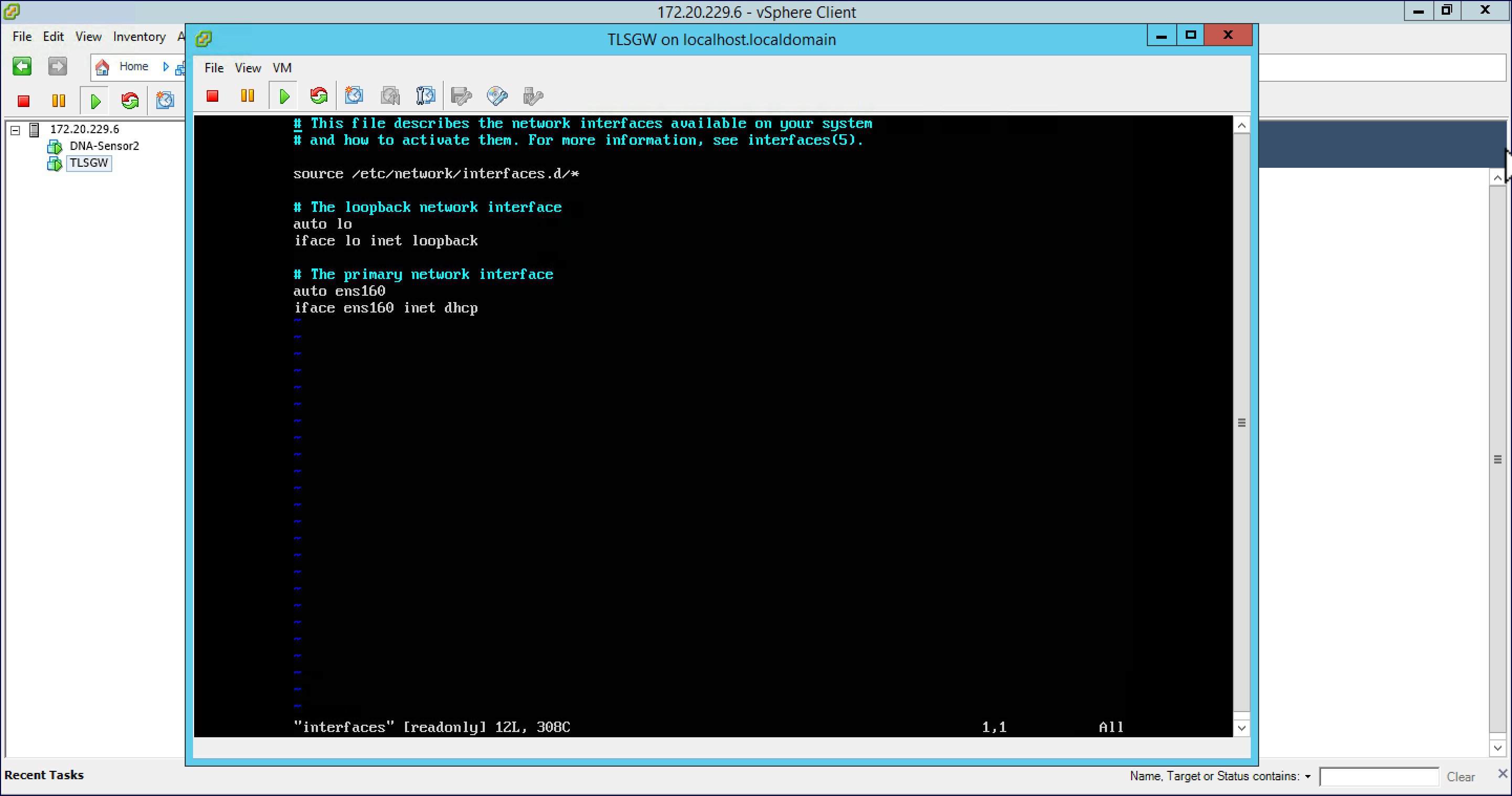
|
||
| Step 6 |
To configure the Private network interface IP address, add the following in the interfaces file as shown below and save the file. 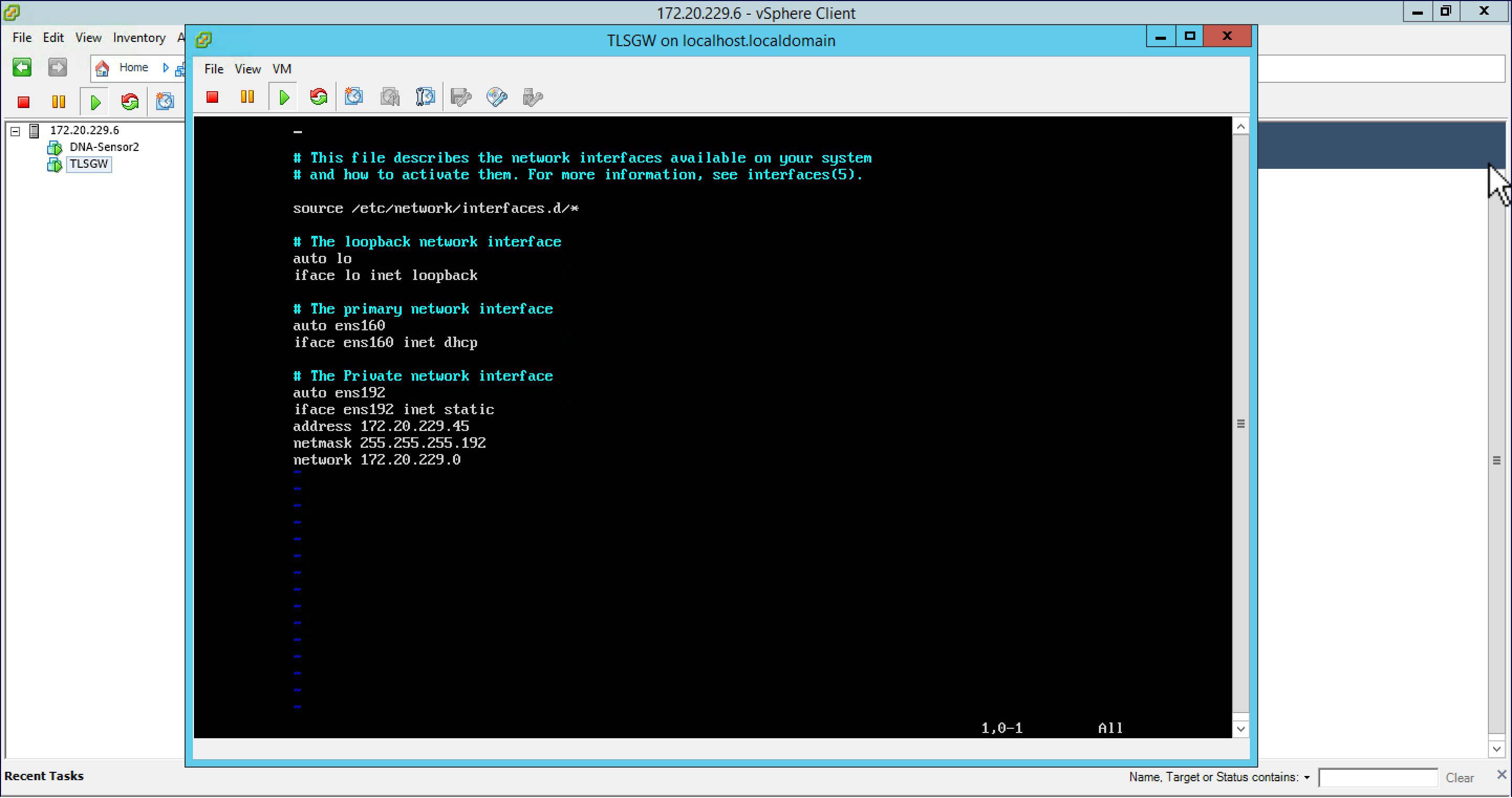 |
||
| Step 7 |
To restart the network service, go to /etc/init.d and type ./networking restart . Now, do a ifconfig and you should see both the Public interface IP address and Private interface IP address. Ping both Public and Private IP address to verify connectivity. 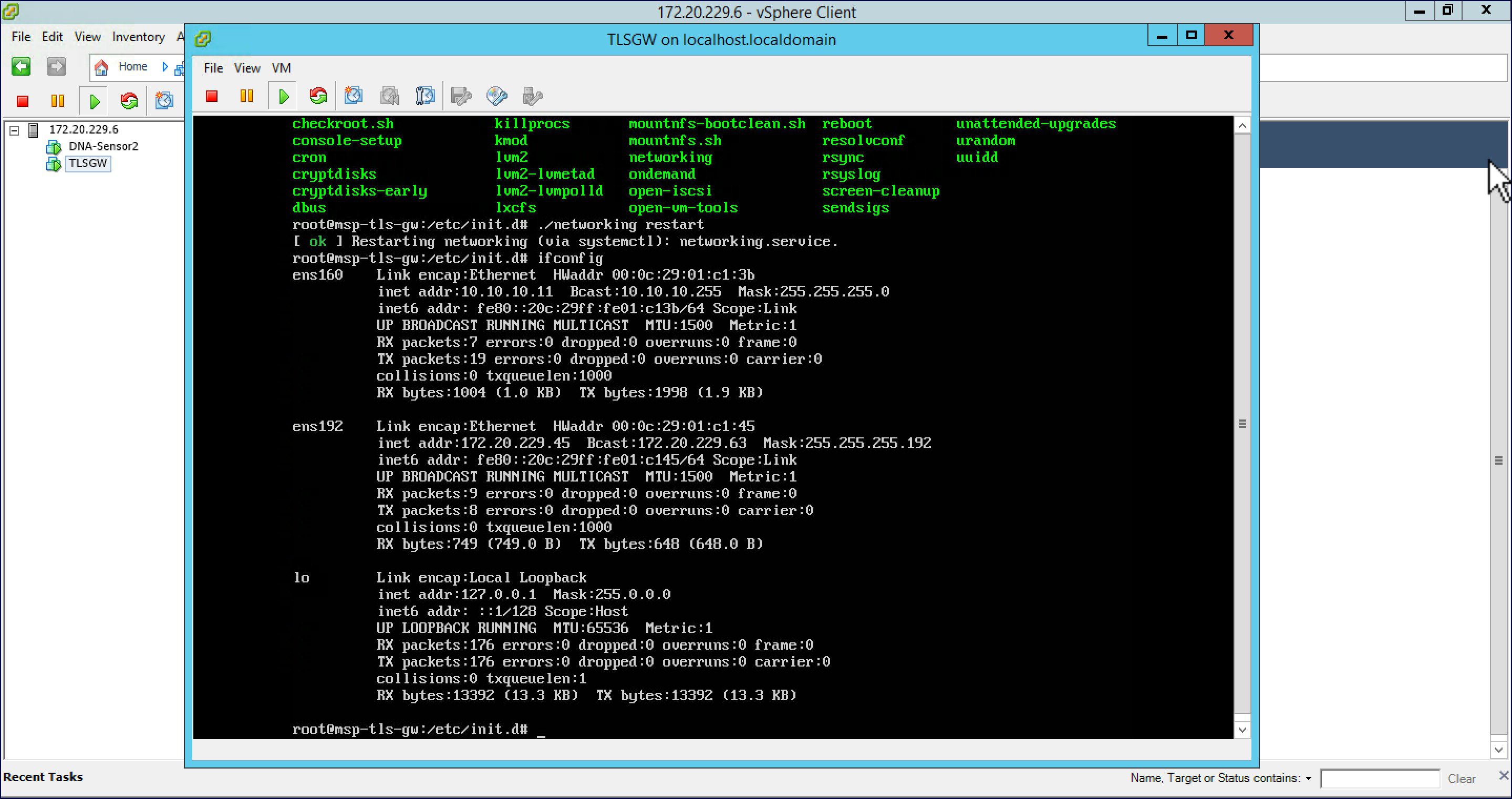 |
Configure the TLS Gateway configuration file and start the service
Procedure
| Step 1 |
: Go to /opt/cisco/msp-tls-gw/bin/ and edit the tlsgw_config.txt with the following:
|
||
| Step 2 |
Save the file. |
||
| Step 3 |
Go to /home/tlsgw and start the TLS Gateway service with script ./startSecureServer.sh |
||
| Step 4 |
To verify that the TLS Gateway service is running successfully, go to /opt/cisco/msp-tls-gw/bin/ and run ./tlsgw_cli as shown below. 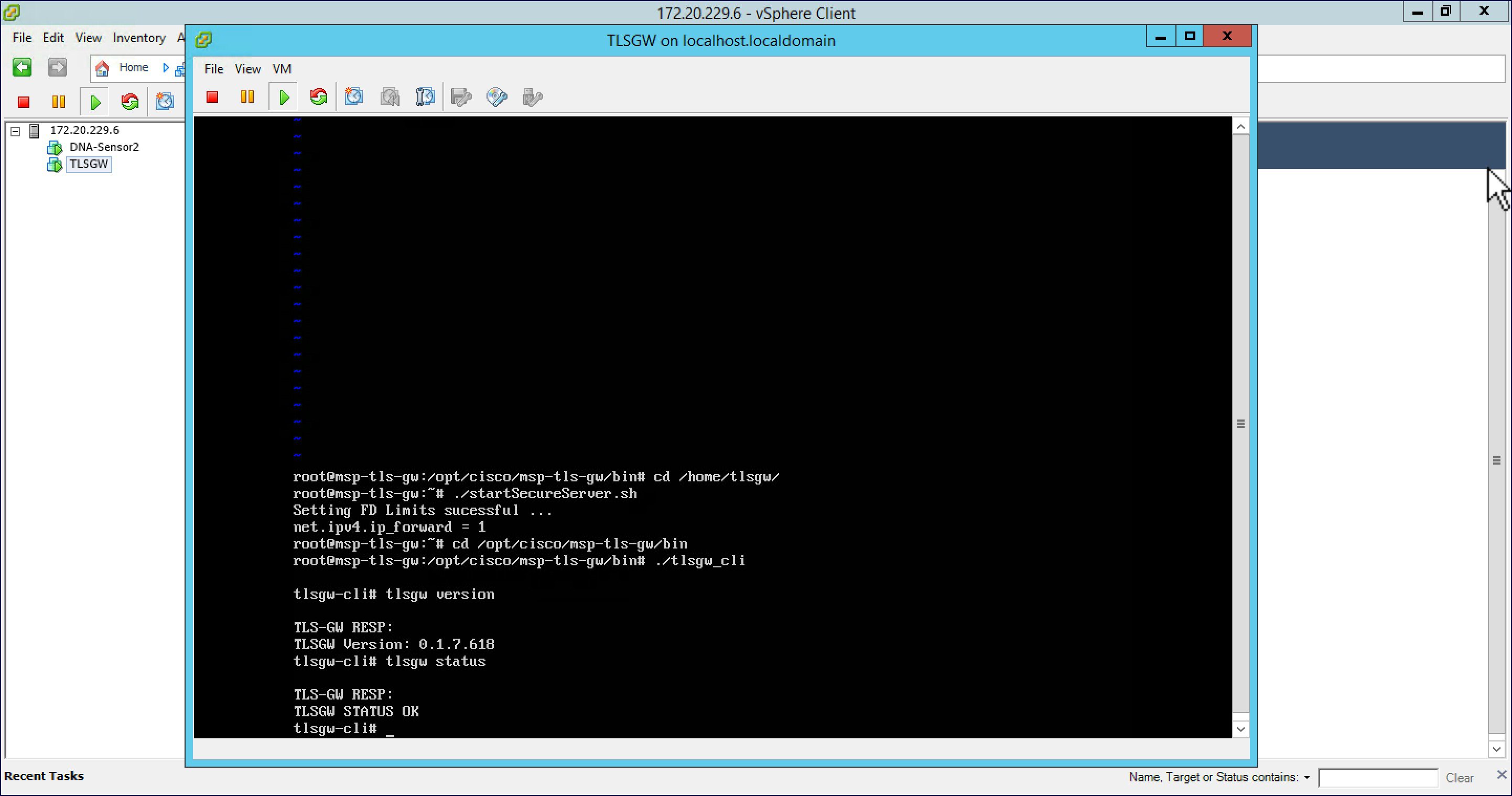 |
Configuring the PSK ID-KEY pair
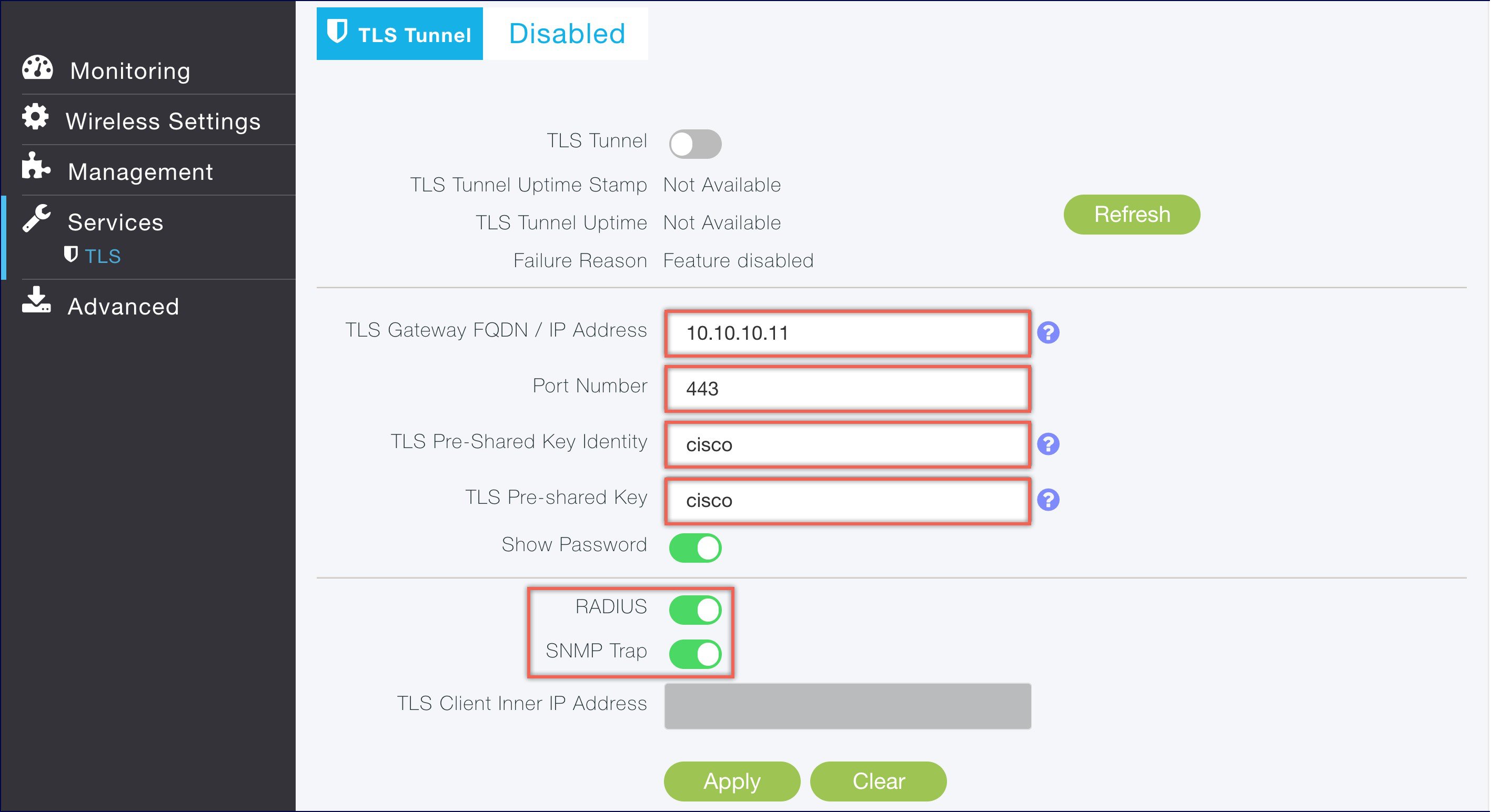
Configure the Pre Shared Key(PSK) on the TLS Gateway. This will be used by the TLS client on the Master AP to authenticate with the TLS Gateway.
 Note |
A maximum of 3 PSK ID-KEY pairs can be set for TLSGW. PSK-ID can be any character string of length (3-50), PSK password(or key) can be any character string of length (5-256) , Character ':' or 'space' or 'tab' are not allowed for both psk-id and psk-key. |
To configure, follow the steps below:
Procedure
| Step 1 |
: Go to /opt/cisco/msp-tls-gw/bin/ and run ./tlsgw_cli |
| Step 2 |
Configure the PSK using the following CLI: |
| Step 3 |
Verify that the PSK ID is configured using the following CLI: 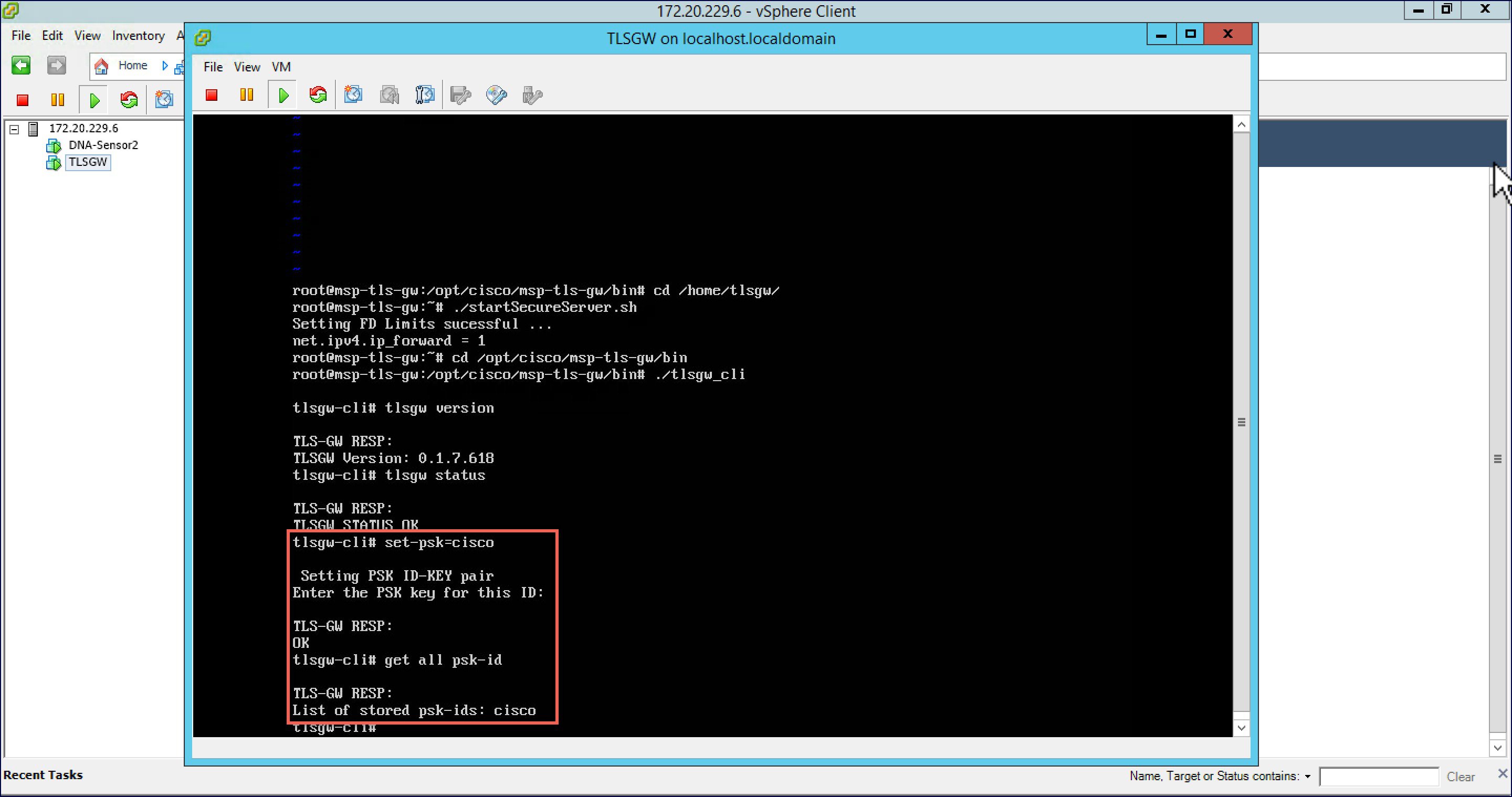 |
 Feedback
Feedback