Server Requirements
Cisco Product Requirements
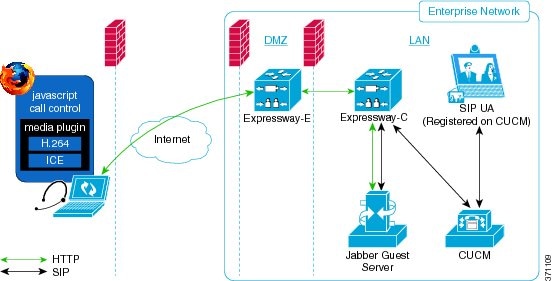
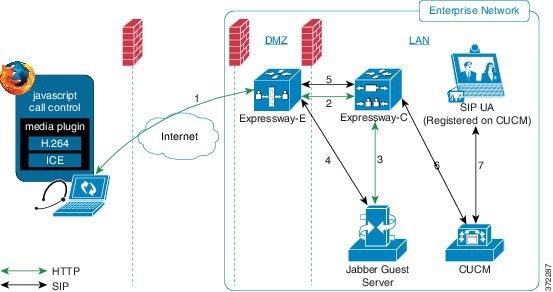
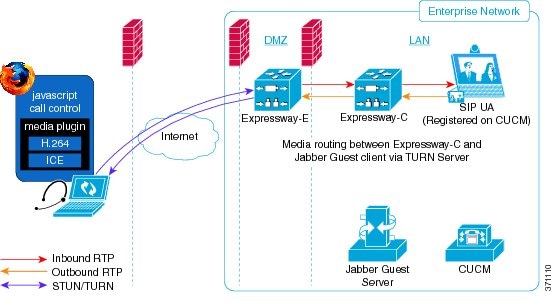
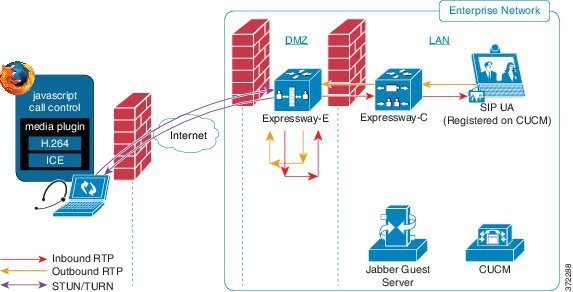
Deploy Cisco Jabber Guest with an existing Cisco Unified Communications Manager installation.
-
Cisco Unified Communications Manager 8.6.x or later
Cisco Jabber Guest requires that your Cisco Unified Communications Manager be configured to work with Cisco Expressway.
-
Cisco Jabber Guest Server
-
Cisco Expressway-C X8.2 or later
-
Cisco Expressway-E X8.2 or later

Important
-
Without Cisco Expressway-C and Cisco Expressway-E, you are limited to testing with clients that can directly access the network on which the Cisco Jabber Guest server is homed.
-
You cannot use the same Cisco Expressway-C and Cisco Expressway-E pair or cluster for both Cisco Jabber Guest and Expressway for Mobile and Remote Access.
-
For more information, download the Cisco Expressway Administrator Guide, deployment guides, and release notes or see the online help for complete information on configuring the options available on your Cisco Expressway.
Virtual Machine Requirements
Cisco Jabber Guest is deployed as a virtual server using the Open Virtualization Format (OVF) standard for packaging and distributing virtual appliances that run in a virtual environment. It requires VMware vSphere as the hypervisor. Cisco publishes the distribution as an OVF file with the file extension .OVA, which stands for Open Virtual Appliance. This file contains the OVF template for the application. The OVF template defines the virtual machine’s hardware and is preloaded with required software.
Hardware and System Requirements
-
A server platform that meets VMware’s Compatibility Guide for VMware vSphere 5.1 or later is required. The Cisco Jabber Guest virtual machine uses a 64-bit distribution of CentOS 6.10. Make sure that the server platform uses CPUs that are capable of 64-bit instructions.
-
Cisco Jabber Guest Server is supported on any Full UC Performance CPU, beginning with Intel Xeon Processor 5600 with a minimum physical core speed of 2.53 GHz or higher and any Restricted UC Performance CPU, beginning with Intel Xeon Processor E5 2609 v1 with a minimum physical core speed of 2.4 GHz or higher. For more information on Full UC performance CPUs and Restricted UC Performance CPUs, see the Processors/CPUs section in UC Virtualization Supported Hardware.
-
Cisco Jabber Guest is allowed on server models meeting required specifications, including Cisco Business Edition 6000 (BE6000), Cisco Business Edition 7000 (BE7000), and UC on UCS Tested Reference Configurations with a Full UC Performance CPU. BE6000M (M2) UCS C200 M2 TRC#1 is not supported. For more information, see Virtualization for Cisco Jabber Guest Server. Cisco Jabber Guest Server must follow the application co-residency and virtual-to-physical sizing rules in the Unified Communications Virtualization Sizing Guidelines.
-
Cisco Jabber Guest supports all virtualization software described in Purchasing/Sourcing Options for Required Virtualization Software.
-
If Cisco Jabber Guest Server is installed on a Cisco Business Edition 6000 server or Cisco Business Edition 7000 server, it must follow the additional co-residency rules in the Cisco Business Edition 6000 and Cisco Business Edition 7000 Co-residency Policy Requirements.
-
See the VMware developer documentation for additional configuration and hardware requirements. We highly recommend using the Cisco Unified Computing System (CUCS) to simplify and maximize performance.
Supported Storage Models
Virtual Machine Specifications
|
RAM |
CPU |
Storage |
Operating System |
CPU Resource Allocation |
Memory Resource Allocation |
|---|---|---|---|---|---|
|
4 GB |
2 logical CPUs with 1 core each |
100 GB |
CentOS 6.10 64-bit |
Default (not defined) |
Default (not defined) |
VMware vSphere Feature Support
-
VM OVA template deployment (using the Cisco-provided Cisco Jabber Guest OVA)
-
VMware vMotion
-
VMware vSphere Distributed Switch (vDS)
-
VMware Dynamic Resource Scheduler (DRS)
-
VMware Storage vMotion (Storage DRS)
-
VMware Virtual Machine Snapshots
You can restart Cisco Jabber Guest on a different VMware ESXi host and create or revert VMware Snapshots as long as the application was shut down without any issues before moving or taking a snapshot.
-
VMware Site Recovery Manager (SRM)
-
VMware Consolidated Backup (VCB)
-
VMware Data Recovery (VDR)
-
VMware Dynamic Power Management (Cisco Jabber Guest must be configured to run 24/7)
-
Long Distance vMotion (vMotion over a WAN)
-
VMware Fault Tolerance (FT)
-
VMware Hot Add
-
Copying a Cisco Jabber Guest virtual machine (must use OVA to deploy new server)
-
Configuring Cisco Jabber Guest with multiple virtual network interface controllers (vNICs)
-
Third-party Virtual to Physical (V2P) migration tools
-
Third-party deployment tools
Reverse Proxy Server Requirements
-
/call
-
/jabberc (used for HTTP/call control)
Configure the reverse proxy to redirect any HTTP requests to HTTPS.
 Feedback
Feedback