Cisco Unified Communications Manager Certificates
Two Cisco Unified Communications Manager certificates are significant for Mobile and Remote Access:
-
CallManager certificate
-
tomcat certificate
These certificates are automatically installed on the Cisco Unified Communications Manager and by default they are self-signed and have the same common name (CN).
We recommend using CA-signed certificates. However, if you do use self-signed certificates, the two certificates must have different common names. The Expressway does not allow two self-signed certificates with the same CN. So if the CallManager and tomcat self-signed certificates have the same CN in the Expressway's trusted CA list, the Expressway can only trust one of them. This means that either secure HTTP or secure SIP, between Expressway-C and Cisco Unified Communications Manager, will fail.
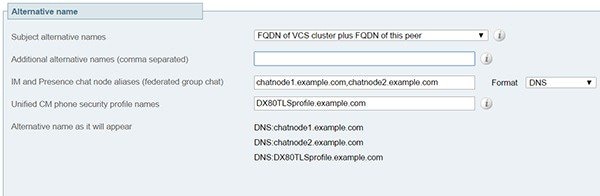
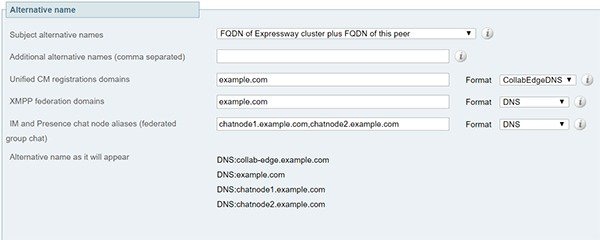
Also, when generating tomcat certificate signing requests for any products in the Cisco Collaboration Systems Release 10.5.2, you need to be aware of CSCus47235. You need to work around this issue to ensure that the FQDNs of the nodes are in the certificates as Subject Alternative Name (SAN) entries. The Expressway X8.5.3 Release Note on the Release Notes page has details of the workarounds.

 Feedback
Feedback