Expressway Configuration Summary
Procedure
| Step 1 |
Make sure that System host name and Domain name are specified for every Expressway and that each Expressway is synchronized to a reliable NTP service.The hostname can contain only letters, digits, hyphens, and underscores. The first character must be a letter, and the last character must be a letter or a digit. |
| Step 2 |
Enable SIP on the Expressway-E and Expressway-C. (SIP is disabled by default on new installs.) |
| Step 3 |
[Recommended] Disable automated intrusion protection on the Expressway-C and configure it on the Expressway-E. (From X8.9, this feature is enabled by default on new installations. See Expressway Automated Intrusion Protection) |
| Step 4 |
Set Unified Communications mode to Mobile and Remote Access. |
| Step 5 |
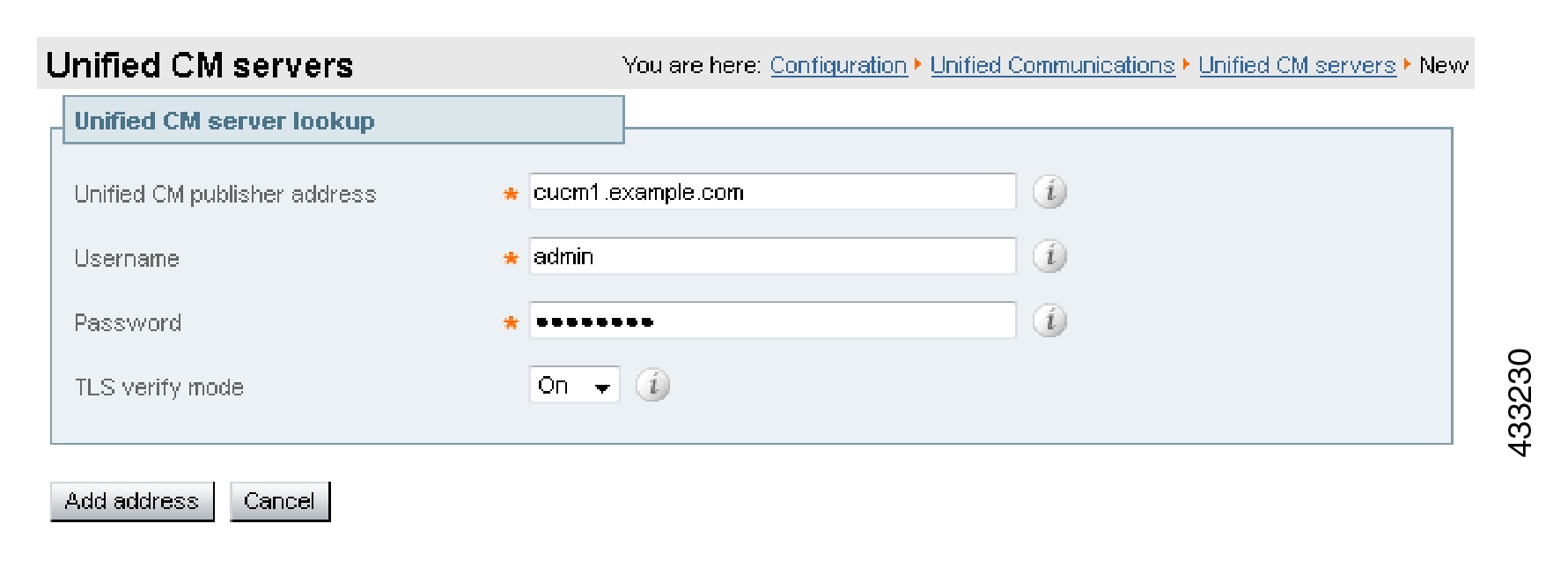
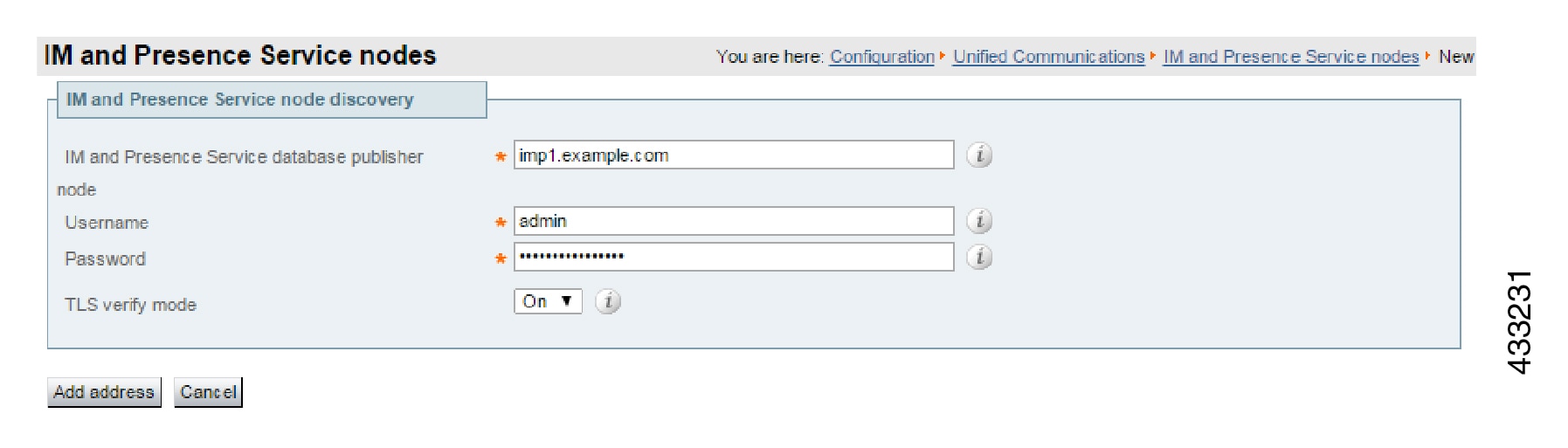
Configure the Unified CM, IM and Presence Service, and Cisco Unity Connection servers on the Expressway-C. |
| Step 6 |
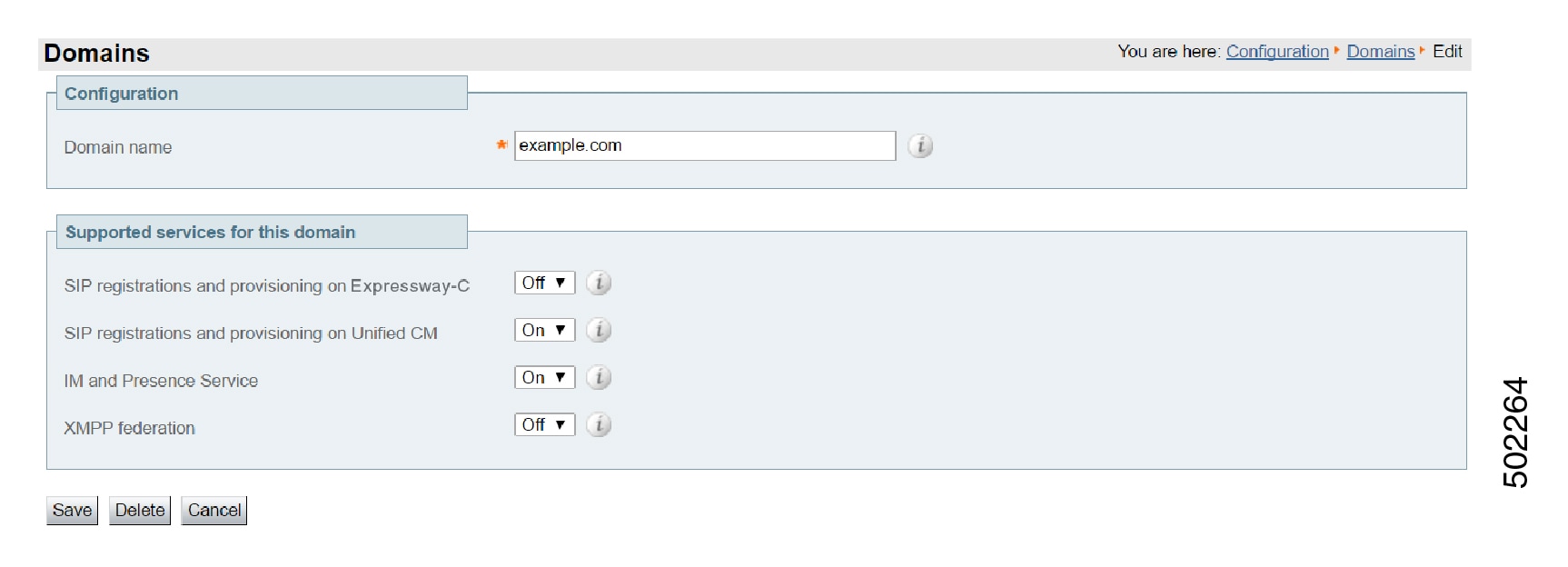
Configure the domains on the Expressway-C for which services are to be routed to Unified CM. |
| Step 7 |
[Optional] Create additional deployments and associate domains, and UC services with them. |
| Step 8 |
Install appropriate server certificates and trusted CA certificates. |
| Step 9 |
Configure a Unified Communications traversal zone connection between Expressway-E and Expressway-C. |
| Step 10 |
If required, configure the HTTP server allow list for any web services inside the enterprise that need to be accessed from remote Jabber clients. |
| Step 11 |
[Optional] Configure SSO over collaboration edge, to allow for common identity between external Jabber clients and the users' Unified CM profiles. Configuration changes on Expressway generally take immediate effect. A banner message or alarm will prompt you if a system restart or other action is required. |

 Feedback
Feedback