Network Settings
This section describes network services and settings related options that appear under the System menu of the web interface. These options enable you to configure the Expressway in relation to the network in which it is located, for example its IP settings, firewall rules, intrusion protection and the external services used by the Expressway (for example, DNS, NTP, and SNMP).
Ethernet Settings
 Note |
The speed settings on this page are for systems running on Cisco Expressway physical appliances only. They do not apply to virtual machine (VM)-based systems. The connection speed shown for VM systems is invalid, and always appears as 10000 Mb/s regardless of the actual speed of the underlying physical NIC(s). This is because VMs cannot retrieve the actual speed from the physical NIC. |
The Ethernet page ( ) displays the connection speeds between Expressway and the Ethernet networks to which it is connected. As the Expressway only supports auto-negotiation, the Speed is always Auto. The Expressway and the connected switch automatically negotiate the speed and the duplex mode for the connection.
Configuring IP Settings
The IP page ( ) is used to configure the IP protocols and network interface settings of the Expressway.
IP Protocol Configuration
You can configure whether the Expressway uses IPv4, IPv6, or both versions of the IP protocol suite. The default is Both.
-
IPv4 only: it only accepts registrations from endpoints using an IPv4 address, and only takes calls between two endpoints communicating via IPv4. It communicates with other systems via IPv4 only.
-
IPv6 only: it only accepts registrations from endpoints using an IPv6 address, and only takes calls between two endpoints communicating via IPv6. It communicates with other systems via IPv6 only.
-
Both: it accepts registrations from endpoints using either an IPv4 or IPv6 address, and takes calls using either protocol. If a call is between an IPv4-only and an IPv6-only endpoint, the Expressway acts as an IPv4 to IPv6 gateway. It communicates with other systems via either protocol.
Some endpoints support both IPv4 and IPv6, however an endpoint can use only one protocol when registering with the Expressway. Which protocol it uses is determined by the format used to specify the IP address of the Expressway on the endpoint. After the endpoint has registered using either IPv4 or IPv6, the Expressway only sends calls to it using this addressing scheme. Calls made to that endpoint from another device using the other addressing scheme are converted (gatewayed) by the Expressway.
All IPv6 addresses configured on the Expressway are treated as having a /64 network prefix length.
IPv4 to IPv6 Interworking
The Expressway can act as a gateway for calls between IPv4 and IPv6 devices. To enable this feature, select an IP protocol of Both. Calls for which the Expressway is acting as an IPv4 to IPv6 gateway are traversal calls and require a Rich Media Session license.
IP Gateways
You can set the default IPv4 gateway and IPv6 gateway used by the Expressway. These are the gateways to which IP requests are sent for IP addresses that do not fall within the Expressway’s local subnet.
-
The default IPv4 gateway is 127.0.0.1, which should be changed during the commissioning process.
-
The IPv6 gateway, if entered, must be a static global IPv6 address. It cannot be a link-local or a stateless auto-configuration (SLAAC) IPv6 address.
LAN Configuration
LAN 1 is the primary network port on the Expressway. You can configure the IPv4 address and subnet mask, the IPv6 address and the Maximum transmission unit (MTU) for this port. The Expressway is shipped with a default IP address of 192.168.0.100 (for both LAN ports). This lets you connect the Expressway to your network and access it via the default address so that you can configure it remotely.
The IPv6 address, if entered, must be a static global IPv6 address. It cannot be a link-local or stateless auto-configuration (SLAAC) address.
The Maximum transmission unit (MTU) defaults to 1500 bytes.
If you have Advanced Networking enabled, you can also configure these options for the LAN 2 port.
Dedicated Management Interface
If you want to enable the Expressway's DMI:
Procedure
| Step 1 |
Set Use Dedicated Management Interface to Yes. |
| Step 2 |
In the LAN3 - DMI section:
|
| Step 3 |
Restart the system. These changes require a restart to take effect. The DMI is now activated on LAN3 as an interface for management traffic. If you want the DMI to be the sole interface for management, go on to the next tasks. |
What to do next
Make DMI Sole Interface
(Optional) Make DMI Sole Interface - Server Management Traffic
Use this task to make management traffic use the DMI, where Expressway is the server.
-
You can do this for administration services (web user interface, REST API, and CLI) and/or for SNMP. Do either or both the following steps, depending on which services you want to configure for DMI only:
-
Go to the page and in the Configuration section set Use Dedicated Management Interface only to Yes.
-
Go to the page and in the Services section set Use Dedicated Management Interface only (for administration) to Yes.
-
-
You need to restart the system for the changes to take effect for the web user interface and the API, which remain accessible from LAN1 / LAN2 until you restart. Changes take immediate effect for the command line interface (SSH) and SNMP service, regardless of restart.
The specified management services can now be accessed only from the DMI / LAN3 port.
 Note |
Expressway will not let you disable the DMI while a management service is configured to use it as the only interface. |
(Optional) Make DMI Sole Interface - Client Management Traffic Outside Subnet
Depending on the Expressway software version, for management traffic where Expressway acts as the client, the traffic may only be directed to the DMI if the target server is in the same subnet as the DMI / LAN3 port. Check your release notes to see if this issue applies. If it does, and if it's not possible to deploy the server in the same subnet as LAN3, you can optionally force Expressway management traffic to use the DMI, by configuring static IP routes for LAN3 per service.
About Advanced Networking and Dual Network Interfaces
The Advanced Networking feature enables the LAN 2 Ethernet port on the Expressway-E, to allow a secondary IP address for the Expressway. It also includes support for deployments where the Expressway-E is located behind a static NAT device, allowing it to have separate public and private IP addresses.
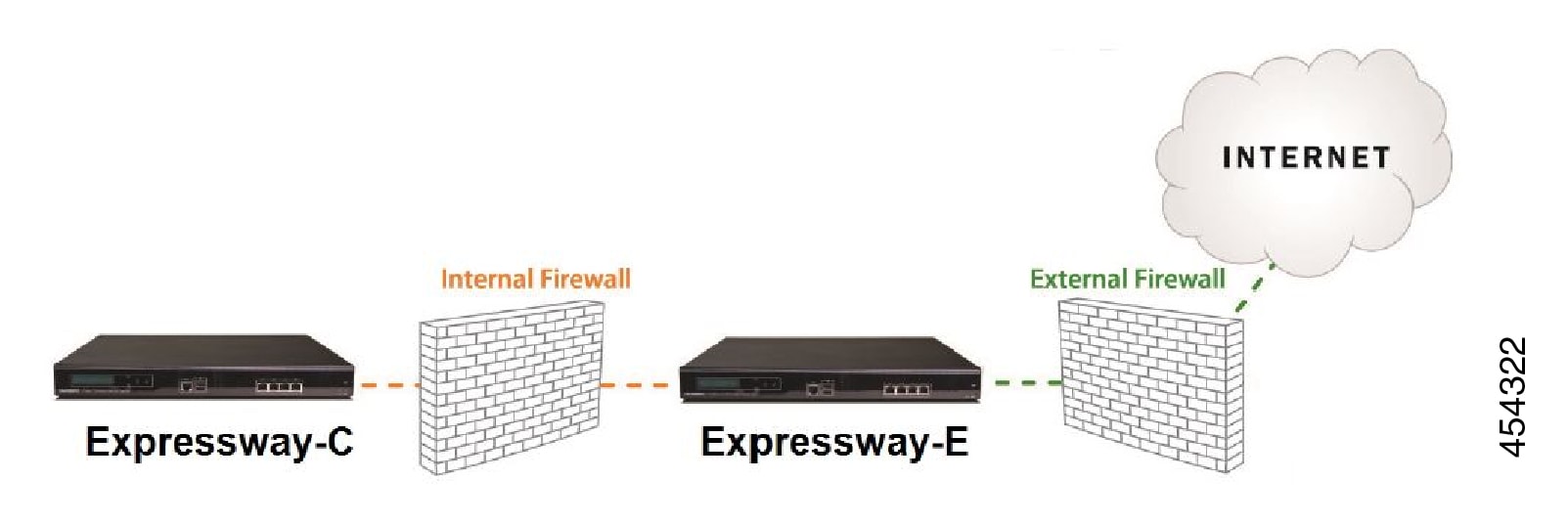
Configuring Dual Network Interfaces
Dual network interfaces are only supported on Expressway-E systems; you cannot deploy them on an Expressway-C.
Dual network interfaces are intended for deployments where the Expressway-E is located in a DMZ between two separate firewalls on separate network segments. In such deployments, routers prevent devices on the internal network from being able to route IP traffic to the public internet, and instead the traffic must pass through an application proxy such as the Expressway-E.
To enable dual network interfaces
Before you begin
-
Configure the LAN 1 port and restart the Expressway before you configure the LAN 2 port.
-
The LAN 1 and LAN 2 interfaces must be on different, non-overlapping subnets.
-
If the Expressway-E is in the DMZ, the outside IP address of the Expressway-E must be a public IP address, or if static NAT mode is enabled, the static NAT address must be publicly accessible.
-
The Expressway-E may also be used to traverse internal firewalls within an enterprise. In this case the "public" IP address may not be publicly accessible, but is an IP address accessible to other parts of the enterprise.
-
If you need to change the IP addresses on one or both interfaces, you can do it via the UI or the CLI. You can change both at the same time if required, and the new addresses take effect after a restart.
Procedure
| Step 1 |
Set Use dual network interfaces to Yes. |
| Step 2 |
Select LAN2 as the interface in the External LAN interface setting. You can now choose to enable static NAT on the external interface. This setting also determines which port allocates TURN server relays. Troubleshooting Tips: |
Configuring Static NAT
You can deploy the Expressway-E behind a static NAT device, allowing it to have separate public and private IP addresses. This feature is intended for use in deployments where the Expressway-E is located in a DMZ, and has the Advanced Networking feature enabled.
In these deployments, the externally-facing LAN port has static NAT enabled in order to use both a private and public IPv4 address. The internally facing LAN port does not have static NAT enabled and uses a single IP address. In such a deployment, traversal clients should be configured to use the internally-facing IP address of the Expressway-E.
To enable static NAT
Procedure
| Step 1 |
In the IPv4 address field, enter the private IP address of the port. |
| Step 2 |
Set IPv4 static NAT mode to On. |
| Step 3 |
In the IPv4 static NAT address field, enter the public IP address of the port - the IP address as it appears after translation (outside the NAT element). |
IPv6 Mode Features and Limitations
When you set the IP interfaces of the Expressway to IPv6 Only mode, those interfaces only use IPv6. They do not use IPv4 to communicate with other systems, and they do not interwork between IPv4 and IPv6 (Dual stack).
Explicit IPv6 Supported Features
-
Calls between Expressway-registered IPv6 endpoints.
-
DiffServ traffic class (TC) tagging.
-
TURN server (on Expressway-E).
-
Automated intrusion protection.
-
DNS lookups.
-
Port usage and status pages.
Supported RFCs
-
RFC 2460: Internet Protocol, Version 6 (IPv6) Specification (partially implemented: static global addresses only).
-
RFC 2464: Transmission of IPv6 Packets over Ethernet Networks.
-
RFC 3596: DNS Extensions to Support IP Version 6.
-
RFC 4213: Basic Transition Mechanisms for IPv6 Hosts and Routers.
-
RFC 4291: IP Version 6 Addressing Architecture.
-
RFC 4443: Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 (IPv6) Specification.
-
RFC 4861: Neighbor Discovery for IP version 6 (IPv6).
-
RFC 5095: Deprecation of Type 0 Routing Headers in IPv6.
-
RFC 6156: Traversal Using Relays around NAT (TURN) Extension for IPv6.
Known Limitations in IPv6 Mode
-
IPv6 addresses must be static; they cannot be link-local or SLAAC addresses.
-
You must restart the Expressway when you change its IP address or its gateway's IP address.
-
Mobile and Remote Access (MRA) is not tested or supported in IPv6 mode. For MRA, the primary call control agent is Unified CM which does not support IPv6.
-
Getting revocation status from distributed Certificate Revocation Lists is not supported in IPv6 mode.
Configuring DNS Settings
The DNS page ( ) is used to configure DNS servers and DNS settings on the Expressway.
Configuring the System Host Name and Domain Name
The System host name defines the DNS host name that this Expressway is known by.
-
It must be unique for each peer in a cluster.
-
It is used to identify the Expressway on a remote log server (a default name of "TANDBERG" is used if the System host name is not specified).
-
It must contain only letters, digits, hyphens, and underscore. The first character must be a letter, and the last character must be a letter or a digit.
The Domain name is used when attempting to resolve unqualified server addresses (for example, ldapserver). It's appended to the unqualified server address before the query is sent to the DNS server. If the server address is fully qualified (for example, ldapserver.mydomain.com) or is in the form of an IP address, the domain name is not appended to the server address before querying the DNS server. The domain name applies to the following Expressway configuration settings:
-
LDAP server
-
NTP server
-
External Manager server
-
Remote logging server
We recommend using an IP address or FQDN (Fully Qualified Domain Name) for all server addresses (The FQDN of the Expressway is the System host name plus the Domain name.)
Impact on SIP messaging
The System host name and Domain name are also used to identify references to this Expressway in SIP messaging, where an endpoint has configured the Expressway as its SIP proxy in the form of an FQDN (as opposed to an IP address, which is not recommended).
In this case the Expressway may, for example, reject an INVITE request if the FQDN configured on the endpoint does not match the System host name and Domain name configured on the Expressway.
 Note |
This check occurs because the SIP proxy FQDN is included in the route header of the SIP request sent by the endpoint to the Expressway. |
Custom domain searches
The Search domains setting is relevant for Edge deployments where the external hosts are in a different DNS domain from Expressway-C, and are configured with non-qualified hostnames. You can optionally use this setting to specify one or more DNS domains. The Expressway appends these domains one by one, to the unqualified hostname and queries DNS for the resultant FQDN. It repeats this process until DNS returns an IP address. This means that there's no need to enter FQDNs when configuring connections between hosts.
Use a space to separate multiple addresses.
DNS requests
By default, DNS requests use a random port from within the system's ephemeral port range. If required, you can specify a custom port range instead by setting DNS requests port range to Use a custom port range and then defining the DNS requests port range start and DNS requests port range end fields.
 Note |
Setting a small source port range will increase your vulnerability to DNS spoofing attacks. |
Configuring DNS Server Addresses
You must specify at least one DNS server to be queried for address resolution if you want to use the following:
-
FQDNs instead of IP addresses when specifying external addresses (for example, for LDAP and NTP servers, neighbor zones, and peers).
-
Features like URI Dialing or ENUM Dialing.
Default DNS servers
You can specify up to five default DNS servers. The Expressway only queries one server at a time. If that server is unavailable the Expressway tries another server from the list.
The order that the servers are specified is not significant. The Expressway favors servers that were last known to be available.
Per-domain DNS servers
As well as the five default DNS servers, you can specify up to five additional explicit DNS servers for specified domains. This can be useful in deployments where specific domain hierarchies need to be routed to their explicit authorities.
For each additional per-domain DNS server address you can specify up to two Domain names. Any DNS queries under those domains are forwarded to the specified DNS server instead of the default DNS servers.
To specify redundant per-domain servers, add an additional per-domain DNS server address and associate it with the same Domain names. DNS requests for those domains are sent in parallel to both DNS servers.
You can use the DNS lookup tool ( ) to check which domain name server (DNS server) is responding to a request for a particular hostname.
Transport protocols
The Expressway uses UDP and TCP to do DNS resolution, and DNS servers usually send both UDP and TCP responses. If the UDP response exceeds the UDP message size limit of 512 bytes, then the Expressway cannot process the UDP response. This is not usually a problem, because the Expressway can process the TCP response instead.
However, if you block TCP inbound on port 53, and if the UDP response is greater than 512 bytes, then the Expressway cannot process the response from the DNS. In this case you won't see the results using the DNS lookup tool, and any operations that need the requested addresses will fail.
Caching DNS Records
DNS lookups may be cached to improve performance. The cache is flushed automatically whenever the DNS configuration is changed, and you can optionally force a flush by clicking Flush DNS cache.
Configuring DSCP / Quality of Service Settings
About DSCP Marking
From X8.9, the Expressway supports improved DSCP (Differentiated Service Code Point) packet marking for traffic passing through the firewall, including Mobile and Remote Access. DSCP is a measure of the Quality of Service level of the packet. To provide more granular control of traffic prioritization, DSCP values are set (marked) for these individual traffic types:
|
Traffic type |
Supplied default value |
Web UI field |
|---|---|---|
|
Video |
34 |
QoS Video |
|
Audio |
46 |
QoS Audio |
|
XMPP |
24 |
QoS XMPP |
|
Signaling |
24 |
QoS Signaling |
Before X8.9 you had to apply DSCP values to all signaling and media traffic collectively.
You can optionally change the default DSCP values from the web UI page (or the CLI).
Notes:
-
DSCP value "0" specifies standard best-effort service.
-
DSCP marking is applied to SIP and H.323 traffic.
-
DSCP marking is applied to TURN media, providing the TURN traffic is actually handled by the Expressway.
-
Traffic type "Video" is assigned by default if the media type cannot be identified. (For example, if different media types are multiplexed on the same port.)
Existing QoS/DSCP Commands and API are Discontinued
 Note |
From X8.9 we no longer support the previous methods to specify QoS/DSCP values. The former Web UI settings QoS Mode and QoS
Value, CLI commands |
What if I currently use these commands?
When you upgrade the Expressway, any existing QoS value you have defined is automatically applied to the new fields and replaces the supplied defaults. For example, if you had a value of 20 defined, all four DSCP settings (QoS Audio, QoS Video, QoS XMPP, QoS Signaling) are set to 20 also.
We don't support downgrades. If you need to revert to your pre-upgrade software version, the QoS settings are reset to their original supplied defaults. So QoS Mode is set to None and QoS Value is set to 0. You will need to manually redefine the values you want to use.
Configuring DSCP Values
To optionally change the supplied DSCP default values, go to the Quality of Service page ( ) and specify the new values you want to use.
Static Routes
You can define static routes from the Expressway to an IPv4 or IPv6 address range. Go to .
On this page you can view, add, and delete static routes.
Static routes are sometimes required when using the Advanced Networking option and deploying the Expressway in a DMZ. They may also be required in other complex network deployments.
To add a static route:
Procedure
| Step 1 |
Enter the base destination address of the new static route from this Expressway. For example, enter 203.0.113.0 or 2001:db8:: |
||
| Step 2 |
Enter the prefix length that defines the range. Extending the example, you could enter 24 to define the IPv4 range 203.0.113.0 - 203.0.113.255, or 32 to define the IPv6 range 2001:db8:: to 2001:db8:ffff:ffff:ffff:ffff:ffff:ffff. The address range field shows the range calculated by the Expressway from the IP address and Prefix length. |
||
| Step 3 |
Enter the IP address of the gateway for your new route. |
||
| Step 4 |
Select an ethernet interface for your new route. This option is only available if the second ethernet interface is enabled. Select LAN 1 or LAN 2 to force the route via that interface, or select Auto to allow the Expressway to make this route on either interface. |
||
| Step 5 |
Click . The new static route is listed in the table. You can delete routes from this table if necessary.
|

 Feedback
Feedback