Provisioning Overview
Cisco IP Phones are intended for high-volume deployments by Voice-over-IP (VoIP) service providers to customers in home, business, or enterprise environments. Hence, provisioning the phone using remote management and configuration ensures the proper operation of the phone at the customer site.
Cisco supports the customized, ongoing feature configuration of the phone by using:
-
Reliable remote control of the phone.
-
Encryption of the communication that controls the phone.
-
Streamlined phone account binding.
Phones can be provisioned to download configuration profiles or updated firmware from a remote server. Downloads can happen when the phones are connected to a network, when they are powered up, and at set intervals. Provisioning is typically part of the high-volume, VoIP deployments common by service providers. Configuration profiles or updated firmware is transferred to the device using TFTP, HTTP, or HTTPS.
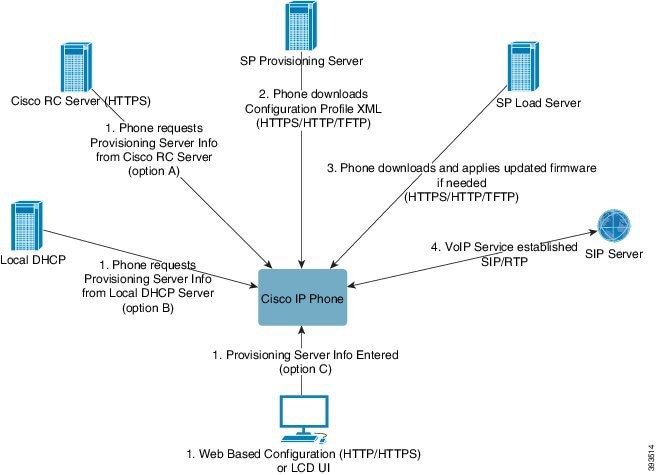
At a high level, the phone provisioning process is as follows:
-
If the phone is not configured, the provisioning server information is applied to the phone using one of the following options: -
A–Downloaded from the Cisco Enablement Data Orchestration System (EDOS) Remote Customization (RC) server using HTTPS, DNS SRV, GDS (Activation code onboarding), EDOS device activation.
-
B–Queried from a local DHCP server.
-
C–Entered manually using the Cisco phone web-based configuration utility or Phone UI.
-
-
The phone downloads the provisioning server information and applies the configuration XML using the HTTPS, HTTP, or TFTP protocol.
-
The phone downloads and applies the updated firmware, if needed, using HTTPS, HTTP, or TFTP.
-
The VoIP service is established using the specified configuration and firmware.
VoIP service providers intend to deploy many phones to residential and small business customers. In business or enterprise environments, phones can serve as terminal nodes. Providers widely distribute these devices across the Internet, which are connected through routers and firewalls at the customer premises.
The phone can be used as a remote extension of the service provider back-end equipment. Remote management and configuration ensure the proper operation of the phone at the customer premises.


 Feedback
Feedback