Managed File Transfer
Managed file transfer (MFT) allows an IM and Presence Service client, such as Cisco Jabber, to transfer files to other users, ad hoc group chat rooms, and persistent chat rooms. The files are stored in a repository on an external file server and the transaction is logged to an external database.
This configuration is specific to file transfers and has no impact on the message archiver feature for regulatory compliance.
Supported Software
For detailed information on supported databases for Managed File Transfer, refer to the "External Database Requirements" chapter of the Database Seup Guide for the IM and Presence Service at https://www.cisco.com/c/en/us/support/unified-communications/unified-communications-manager-callmanager/products-installation-and-configuration-guides-list.html.
File Transfer Flow
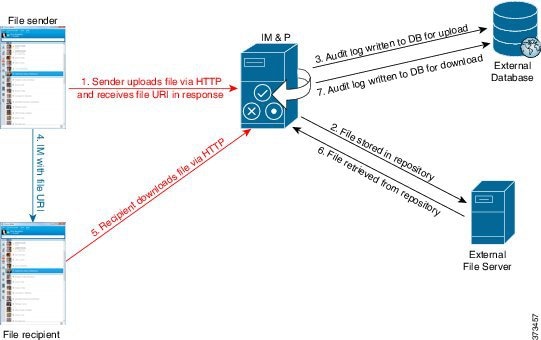
-
The sender's client uploads the file via HTTP, and the server responds with a URI for the file.
-
The file is stored in the repository on the file server.
-
An entry is written to the external database log table to record the upload.
-
The sender’s client sends an IM to the recipient; the IM includes the URI of the file.
-
The recipient’s client requests the file via HTTP. After reading the file from the repository (6) and recording the download in the log table (7), the file is downloaded to the recipient.
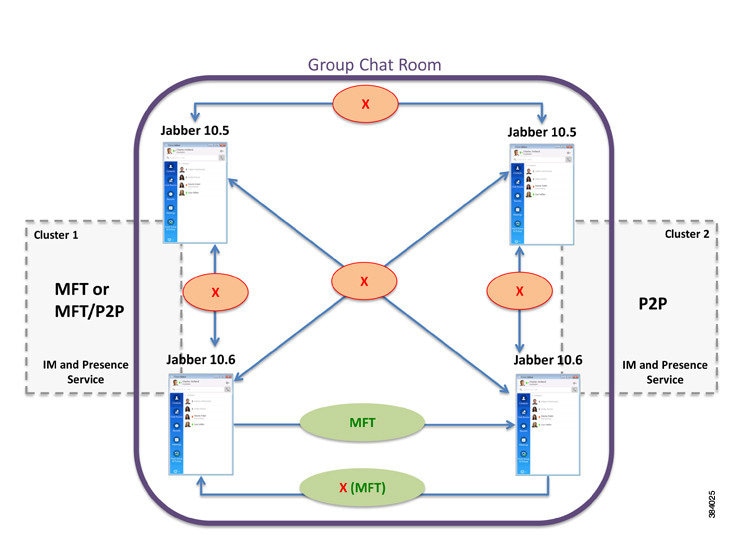
The flow for transferring a file to a group chat or persistent chat room is similar, except the sender sends the IM to the chat room, and each chat room participant sends a separate request to download the file.
 Note |
When a file upload occurs, the managed file transfer service is selected from all managed file transfer services available in the enterprise for the given domain. The file upload is logged to the external database and external file server associated with the node where this managed file transfer service is running. When a user downloads this file, the same managed file transfer service handles the request and logs it to the same external database and the same external file server, regardless of where this second user is homed. |
Important Notes
Before you enable managed file transfer on an IM and Presence Service node consider these points:
-
If you deploy any combination of the persistent group chat, message archiver, or managed file transfer features on an IM and Presence Service node, you can assign the same physical external database installation and external file server to all of these features. However, you should consider the potential IM traffic, the number of file transfers, and the file size when you determine the server capacity.
-
Ensure that all clients can resolve the full FQDN of the IM and Presence Service node to which they are assigned. For the managed file transfer feature to work, it is not enough for the clients to resolve the hostname; they must be able to resolve the FQDN.
-
The node public key is invalidated if the node's assignment is removed. If the node is reassigned, a new node public key is automatically generated and the key must be reconfigured on the external file server.
-
The Cisco XCP File Transfer Manager service must be active on each node where managed file transfer is enabled.
You can configure one of the following options on the File Transfer window:
-
Disabled—file transfer is disabled for the cluster.
-
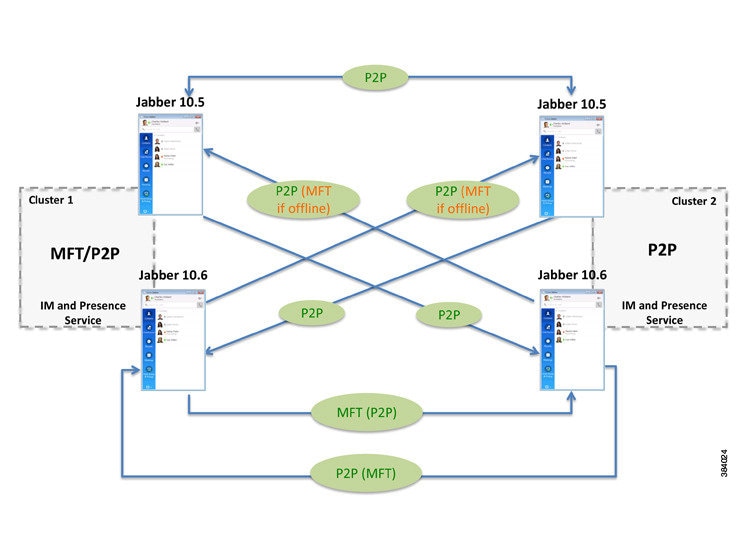
Peer-to-Peer—one-to-one file transfers are allowed, but files are not archived or stored on a server. Group chat file transfer is not supported.
-
Managed File Transfer—one-to-one and group file transfers are allowed. File transfers are logged to a database and the transferred files are stored on a server. The client must also support managed file transfer, otherwise no file transfers are allowed.
-
Managed and Peer-to-Peer File Transfer—one-to-one and group file transfers are allowed. File transfers are logged to a database and the transferred files are stored on a server only if the client supports managed file transfer. If the client does not support managed file transfer, this option is equivalent to the Peer-to-Peer option.
 Note |
If managed file transfer is configured on a node and you change the File Transfer Type to Disabled or Peer-to-Peer, be aware that the mapped settings to the external database and to the external file server for that node are deleted. The database and file server remain configured but you must reassign them if you re-enable managed file transfer for the node. |
Depending on your pre-upgrade setting, after an upgrade to IM and Presence Service Release 10.5(2) or later, either Disabled or Peer-to-Peer is selected.

 Feedback
Feedback