Information About ARP Spoofing and Flood Attack
Overview of ARP Anti-Spoofing
ARP provides IP communication within a broadcast domain by mapping an IP address to a MAC address. For example, host B wants to send information to host A but does not have the MAC address of host A in its ARP cache. In ARP terms, host B is the sender and host A is the target.
To get the MAC address of host A, host B generates a broadcast message for all hosts within the broadcast domain to obtain the MAC address associated with the IP address of host A. All hosts within the broadcast domain receive the ARP request, and host A responds with its MAC address.
ARP spoofing attacks occurs because ARP allows a reply from a host even if an ARP request was not received. After the attack, all traffic from the device under attack flows through the attacker’s computer and then to the router, switch, or host.
An ARP spoofing attack can affect hosts, switches, and routers connected to your network by sending false information to the ARP caches of the devices connected to the subnet. Sending false information to an ARP cache is known as ARP cache poisoning. Spoof attacks can also intercept traffic intended for other hosts on the subnet.
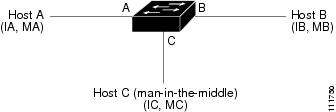
Hosts A, B, and C are connected to the device on interfaces A, B, and C, which are on the same subnet. Their IP and MAC addresses are shown in parentheses; for example, host A uses IP address IA and MAC address MA. When host A needs to send IP data to host B, it broadcasts an ARP request for the MAC address associated with IP address IB. When the device and host B receive the ARP request, they populate their ARP caches with an ARP binding for a host with the IP address IA and a MAC address MA; for example, IP address IA is bound to MAC address MA. When host B responds, the device and host A populate their ARP caches with a binding for a host with the IP address IB and the MAC address MB.
Host C can poison the ARP caches of the device, host A, and host B by broadcasting two forged ARP responses with bindings: one for a host with an IP address of IA and a MAC address of MC and another for a host with the IP address of IB and a MAC address of MC. Host B and the device then use the MAC address MC as the destination MAC address for traffic intended for IA, which means that host C intercepts that traffic. Likewise, host A and the device use the MAC address MC as the destination MAC address for traffic intended for IB.
Because host C knows the true MAC addresses associated with IA and IB, it can forward the intercepted traffic to those hosts by using the correct MAC address as the destination. This topology, in which host C has inserted itself into the traffic stream from host A to host B, is an example of a man-in-the middle attack.
To prevent spoofing, you can enable ARP anti-spoofing. If ARP anti-spoofing is enabled, all ARP packets will be redirected to CPU for a check. The ARP packets will be verified with the entries in the static ARP table or the IP source guard static binding table or the DHCP snooping table. All ARP packets that match the entries in any one of the table will be transmitted. All incomplete ARP packets, or packets that partially match with any one of the table entries, will be discarded. Unkown ARP packets, or packets that do not match with any table entries, can be configured to either be discarded or flooded to all ports. ARP anti-spoofing attack is disabled by default.
You can configure the host protection feature to bind the IP address or MAC address and the connected port of the host together. ARP packets transmitted from this port is accepted by all other connected ports. ARP packets with the same IP address or MAC address is discarded if transmitted from any other port.
You can configure the source MAC address consistency inspection feature to check whether the ethernet source MAC address in the ARP packet is the same as the source MAC address stored in the table. If the source MAC addresses do not match, the packet is discarded. This feature is disabled by default.
A layer-3 device can configured as the gateway for certain LAN devices. An attacker host can try to add the Layer 3 device to the blocked list by sending a gratuitous ARP identfying itself as the correct gateway. You can configure the gateway anti-spoofing feature to prevent this kind of attack. This feature is disabled by default.
By default, after an attack all ports are considered as not trustworthy. You can configure a port that does not require monitoring and is trustworthy as a trusted port.
Overview of ARP Flooding Attack
An ARP spoofing attack can affect hosts, switches, and routers connected to your network by flooding packets to the CPU of the devices connected to the subnet and thus affecting device performance. Flooding the CPU on the device is known as ARP flooding attack.
To prevent ARP flood attack, the following configurations are available.
-
You must enable ARP anti-flood attack to prevent ARP flood attack. The ARP packet is forwarded to the CPU. Each traffic flow is identified based on the source MAC address of the packet.
-
You can configure a rate threshold to monitor the ARP flow. If the rate threshold is exceeded, then it is considered as an attack. You configure a rate threshold globally or for an interface.
-
Once an attack occurs, you can configure whether to add the host's source MAC address to the blackhole address list and discard all packets, or discard only the ARP packets from the host.
-
To remove hosts from the blackhole address list, you can either define a recovery time interval or manually restore the host.
-
You can bind the dynamic MAC address to the static MAC address of a host in the blackhole address list. This prevents the host from transmitting any type of packets.
 Feedback
Feedback