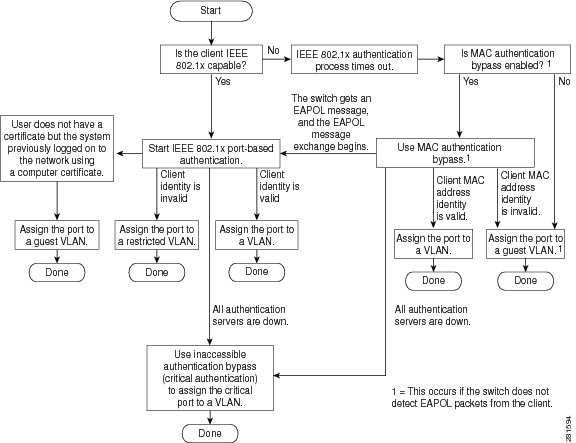
You can configure a guest
VLAN for each 802.1x port on the switch to provide limited services to clients,
such as downloading the 802.1x client. These clients might be upgrading their
system for 802.1x authentication, and some hosts, such as Windows 98 systems,
might not be IEEE 802.1x-capable.
When you enable a guest VLAN
on an 802.1x port, the switch assigns clients to a guest VLAN when the switch
does not receive a response to its EAP request/identity frame or when EAPOL
packets are not sent by the client.
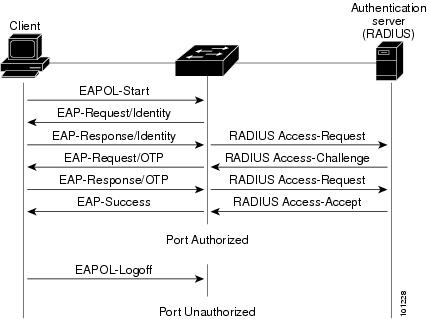
The switch maintains the
EAPOL packet history. If an EAPOL packet is detected on the interface during
the lifetime of the link, the switch determines that the device connected to
that interface is an IEEE 802.1x-capable supplicant, and the interface does not
change to the guest VLAN state. EAPOL history is cleared if the interface link
status goes down. If no EAPOL packet is detected on the interface, the
interface changes to the guest VLAN state.
If the switch is trying to
authorize an 802.1x-capable voice device and the AAA server is unavailable, the
authorization attempt fails, but the detection of the EAPOL packet is saved in
the EAPOL history. When the AAA server becomes available, the switch authorizes
the voice device. However, the switch no longer allows other devices access to
the guest VLAN. To prevent this situation, use one of these command sequences:
-
Enter the
authentication event no-response action authorize vlan
vlan-id
interface configuration command to allow access to the guest VLAN.
-
Enter the
shutdown interface configuration command followed
by the
no shutdown interface configuration command to
restart the port.
If devices send EAPOL packets
to the switch during the lifetime of the link, the switch no longer allows
clients that fail authentication access to the guest VLAN.

Note |
If an EAPOL packet is
detected after the interface has changed to the guest VLAN, the interface
reverts to an unauthorized state, and 802.1x authentication restarts.
|
Any number of
802.1x-incapable clients are allowed access when the switch port is moved to
the guest VLAN. If an 802.1x-capable client joins the same port on which the
guest VLAN is configured, the port is put into the unauthorized state in the
user-configured access VLAN, and authentication is restarted.
Guest VLANs are supported on
802.1x ports in single host, multiple host, multi-auth and multi-domain modes.
You can configure any active
VLAN except an RSPAN VLAN, a private VLAN, or a voice VLAN as an 802.1x guest
VLAN. The guest VLAN feature is not supported on internal VLANs (routed ports)
or trunk ports; it is supported only on access ports.
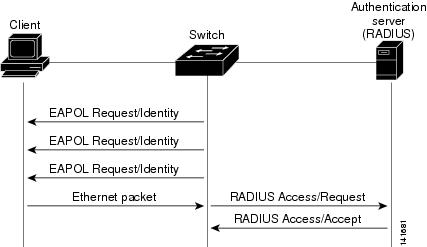
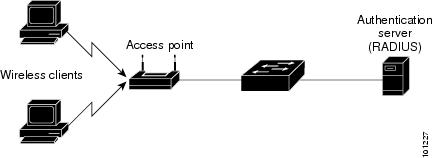
The switch supports
MAC authentication
bypass. When MAC authentication bypass is enabled on an 802.1x port, the
switch can authorize clients based on the client MAC address when IEEE 802.1x
authentication times out while waiting for an EAPOL message exchange. After
detecting a client on an 802.1x port, the switch waits for an Ethernet packet
from the client. The switch sends the authentication server a
RADIUS-access/request frame with a username and password based on the MAC
address. If authorization succeeds, the switch grants the client access to the
network. If authorization fails, the switch assigns the port to the guest VLAN
if one is specified.

 Feedback
Feedback