Device Sensor
Available Languages
Table Of Contents
How to Configure Device Sensor
Enabling Accounting Augmentation
Creating a Cisco Discovery Protocol Filter
Applying a Protocol Filter to Device Sensor Output
Verifying Device Sensor Configuration
Restrictions for Device Sensor
Configuration Examples for Device Sensor Feature
Feature Information for Device Sensor
device-sensor filter-list dhcp
device-sensor filter-list lldp
Obtaining Documentation and Submitting a Service Request
Device Sensor
Last Updated: June 26, 2012
Device Sensor feature is used to gather raw endpoint data from network devices using protocols such as Cisco Discovery Protocol (CDP), Link Layer Discovery Protocol (LLDP), and DHCP. The endpoint data is made available to registered clients in the context of an access session.
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the Feature Information Table at the end of this document.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Contents of this Guide
•
How to Configure Device Sensor
•
Restrictions for Device Sensor
About Device Sensor
Device Sensor introduces the device-sensor capability, which is used to gather raw endpoint data from network devices. The endpoint information aids in completing the profiling capability of switches. Profiling is the determination of the endpoint type based on information gleaned from various protocol packets from an endpoint during its connection to a network.
The profiling capability consists of two parts:
•
Collector--Gathers endpoint data from network devices.
•
Analyzer--Processes the data and determines the type of device.
Device Sensor represents the embedded collector functionality. The illustration below shows Device Sensor in the context of the profiling system and also features other possible clients of the sensor.
Figure 1
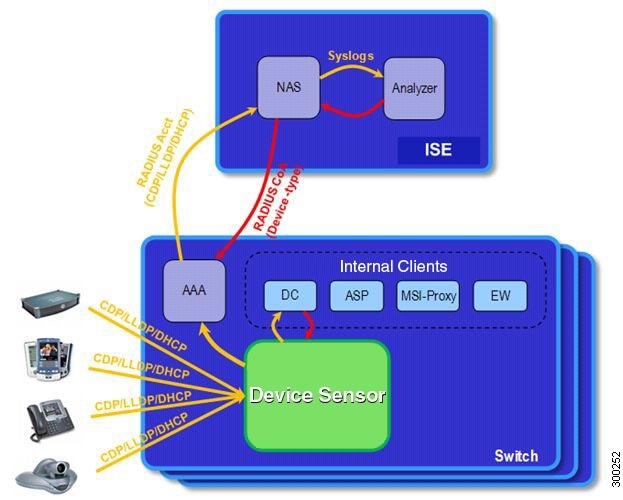
Device Sensor and Its Clients
A switch with sensor capability gathers endpoint information from network devices using protocols such as Cisco Discovery Protocol (CDP), LLDP, and DHCP, subject to statically configured filters, and makes this information available to its registered clients in the context of an access session. An access session represents an endpoint's connection to the network device.
Device Sensor has internal and external clients. The internal clients include components such as the embedded Device Classifier (local analyzer), ASP, MSI-Proxy, and EnergyWise (EW). The external client, that is the Identity Services Engine (ISE) analyzer, will use RADIUS accounting to receive additional endpoint data.
Client notifications and accounting messages containing profiling data along with the session events, and other session-related data, such as MAC address and ingress port are generated and sent to the internal and external clients (ISE). By default, for each supported peer protocol, client notifications and accounting events are only generated where an incoming packet includes a TLV that has not previously been received in the context of a given session. You can enable client notifications and accounting events for all TLV changes, where either a new TLV has been received or a previously received TLV has been received with a different value using CLI commands.
Device Sensor's port security protects the switch from consuming memory and crashing during deliberate or unintentional denial-of-service (DoS) type attack. The sensor limits the maximum device monitoring sessions to 32 per port (access ports and trunk ports). In case of lack of activity from hosts, the age session time is 12 hours.
How to Configure Device Sensor
Device Sensor is enabled by default. These tasks are applicable only if you want to configure the sensor based on your specific requirements.

Note
If you do not perform these configuration tasks, then the following TLVs are included by default:
•
Cisco Discovery Protocol filter--secondport-status-type and powernet-event-type (type 28 and 29)
•
LLDP filter--organizationally-specific (type 127)
•
DHCP filter--message-type (type 53)
•
Enabling Accounting Augmentation
•
Creating a Cisco Discovery Protocol Filter
•
Applying a Protocol Filter to Device Sensor Output
•
Verifying Device Sensor Configuration
Enabling Accounting Augmentation
For the sensor protocol data to be added to the accounting messages, you must enable session accounting by using the following standard Authentication, Authorization, and Accounting (AAA), and RADIUS configuration commands:
Switch(config)# aaa new-modelSwitch(config)# aaa accounting dot1x default start-stop group radiusSwitch(config)# radius-server host{hostname|ip-address}[auth-port port-number][acct-port port-number][timeout seconds][retransmit retries][key string]Switch(config)# radius-server vsa send accountingBeginning in privileged EXEC mode, follow these steps to add Device Sensor protocol data to accounting records.
Creating a Cisco Discovery Protocol Filter
Beginning in privileged EXEC mode, follow these steps to create a Cisco Discovery Protocol filter containing a list of TLVs that can be included or excluded in Device Sensor output.
Creating an LLDP Filter
Beginning in privileged EXEC mode, follow these steps to create an LLDP filter containing a list of TLVs that can be included or excluded in Device Sensor output.
Creating a DHCP Filter
Beginning in privileged EXEC mode, follow these steps to create a DHCP filter containing a list of options that can be included or excluded in Device Sensor output.
Applying a Protocol Filter to Device Sensor Output
Beginning in privileged EXEC mode, follow these steps to apply a CDP, LLDP, or DHCP filter to the sensor output. The output is session notifications to internal sensor clients and accounting requests.
Tracking TLV Changes
Beginning in privileged EXEC mode, follow these steps to enable client notifications and accounting events for all TLV changes. By default, for each supported peer protocol, client notifications and accounting events will only be generated where an incoming packet includes a TLV that has not previously been received in the context of a given session.
Verifying Device Sensor Configuration
Beginning in privileged EXEC mode, follow these steps to verify the sensor cache entries for all devices.
Here is an example for the show device-sensor cache mac mac-address privileged EXEC command.
Switch# show device-sensor cache mac 0024.14dc.df4dDevice: 0024.14dc.df4d on port GigabitEthernet1/0/24--------------------------------------------------Proto Type:Name Len Valuecdp 26:power-available-type 16 00 1A 00 10 00 00 00 01 00 00 00 00 FF FF FF FFcdp 22:mgmt-address-type 17 00 16 00 11 00 00 00 01 01 01 CC 00 04 09 1B 650Ecdp 11:duplex-type 5 00 0B 00 05 01cdp 9:vtp-mgmt-domain-type 4 00 09 00 04cdp 4:capabilities-type 8 00 04 00 08 00 00 00 28cdp 1:device-name 14 00 01 00 0E 73 75 70 70 6C 69 63 61 6E 74lldp 0:end-of-lldpdu 2 00 00lldp 8:management-address 14 10 0C 05 01 09 1B 65 0E 03 00 00 00 01 00lldp 7:system-capabilities 6 0E 04 00 14 00 04lldp 4:port-description 23 08 15 47 69 67 61 62 69 74 45 74 68 65 72 6E 6574 31 2F 30 2F 32 34lldp 5:system-name 12 0A 0A 73 75 70 70 6C 69 63 61 6E 74dhcp 82:relay-agent-info 20 52 12 01 06 00 04 00 18 01 18 02 08 00 06 00 2414 DC DF 80dhcp 12:host-name 12 0C 0A 73 75 70 70 6C 69 63 61 6E 74dhcp 61:client-identifier 32 3D 1E 00 63 69 73 63 6F 2D 30 30 32 34 2E 31 3464 63 2E 64 66 34 64 2D 47 69 31 2F 30 2F 32 34dhcp 57:max-message-size 4 39 02 04 80Here is an example for the show device-sensor cache all privileged EXEC command.
Switch# show device-sensor cache allDevice: 001c.0f74.8480 on port GigabitEthernet2/1--------------------------------------------------Proto Type:Name Len Valuedhcp 52:option-overload 3 34 01 03dhcp 60:class-identifier 11 3C 09 64 6F 63 73 69 73 31 2E 30dhcp 55:parameter-request-list 8 37 06 01 42 06 03 43 96dhcp 61:client-identifier 27 3D 19 00 63 69 73 63 6F 2D 30 30 31 63 2E 30 6637 34 2E 38 34 38 30 2D 56 6C 31dhcp 57:max-message-size 4 39 02 04 80Device: 000f.f7a7.234f on port GigabitEthernet2/1--------------------------------------------------Proto Type:Name Len Valuecdp 22:mgmt-address-type 8 00 16 00 08 00 00 00 00cdp 19:cos-type 5 00 13 00 05 00cdp 18:trust-type 5 00 12 00 05 00cdp 11:duplex-type 5 00 0B 00 05 01cdp 10:native-vlan-type 6 00 0A 00 06 00 01cdp 9:vtp-mgmt-domain-type 9 00 09 00 09 63 69 73 63 6FTroubleshooting Tips
The following commands can help troubleshoot Device Sensor.
•
debug device-sensor {errors | events}
•
debug authentication all
Restrictions for Device Sensor
•
Only CDP, LLDP, and DHCP protocols are supported.
•
The Session limit for profiling ports is 32.
•
The length of one TLV must not be more than 1024 and the total length of TLVs (combined length of TLVs) of all protocols must not be more than 4096.
•
The sensor profiles devices that are only one hop away.
Configuration Examples for Device Sensor Feature
The following example shows how to create a CDP filter containing a list of TLVs:
Switch> enableSwitch# configure terminalSwitch(config)# device-sensor filter-list cdp list cdp-listSwitch(config-sensor-cdplist)# tlv name address-typeSwitch(config-sensor-cdplist)# tlv name device-nameSwitch(config-sensor-cdplist)# tlv number 34Switch(config-sensor-cdplist)# endThe following example shows how to create an LLDP filter containing a list of TLVs:
Switch> enableSwitch# configure terminalSwitch(config)# device-sensor filter-list lldp list lldp-listSwitch(config-sensor-lldplist)# tlv name chassis-idSwitch(config-sensor-lldplist)# tlv name management-addressSwitch(config-sensor-lldplist)# tlv number 28Switch(config-sensor-lldplist)# endThe following example shows how to create a DHCP filter containing a list of options:
Switch> enableSwitch# configure terminalSwitch(config)# device-sensor filter-list dhcp list dhcp-listSwitch(config-sensor-lldplist)# option name domain-nameSwitch(config-sensor-lldplist)# option name host-nameSwitch(config-sensor-lldplist)# option number 50Switch(config-sensor-lldplist)# endThe following example shows how to apply a CDP TLV filter list to Device Sensor output:
Switch> enableSwitch# configure terminalSwitch(config)# device-sensor filter-spec cdp include cdp-list1The following example shows how to enable client notifications and accounting events for all TLV changes:
Switch> enableSwitch# configure terminalSwitch(config)# device-sensor notify all-changesAdditional References
Here are some additional references for Device Sensor feature.
Related Documents
Related Topic
Device Sensor with Cisco Identity Services Engine (ISE)
Cisco Identity Services Engine User Guide: Configuring Endpoint Profiling Policies
Cisco IOS Commands
Security Commands
•
Cisco IOS Security Command Reference: Commands A to C
•
Cisco IOS Security Command Reference: Commands D to L
•
Cisco IOS Security Command Reference: Commands M to R
Technical Assistance
Feature Information for Device Sensor
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Device Sensor Commands
This section contains the command references for Device Sensor feature.
•
device-sensor filter-list dhcp
•
device-sensor filter-list lldp
•
device-sensor filter-list cdp
device-sensor accounting
To add Device Sensor protocol data to accounting records and to generate additional accounting events when new sensor data is detected, use the device-sensor accounting command in global configuration mode. To disable adding Device Sensor protocol data to accounting records and to disable generating accounting events, use the no form of this command.
device-sensor accounting
no device-sensor accounting
Syntax Description
This command has no arguments or keywords.
Defaults
Device Sensor protocol data is added to the accounting records and additional accounting events are generated when new sensor data is detected.
Command Modes
Global configuration
Command History
Usage Guidelines
Device Sensor is used to glean endpoint information from Cisco Discovery Protocol (CDP), Link Layer Discovery Protocol (LLDP), and DHCP messages and make this information available to registered clients in the context of an access session. You can use the device-sensor accounting command to include the data gleaned by Device Sensor in RADIUS accounting messages.
For the sensor-protocol data to be added to the accounting messages, you must enable session accounting by using the following standard AAA and RADIUS configuration commands:
Switch(config)# aaa new-modelSwitch(config)# aaa accounting dot1x default start-stop group radiusSwitch(config)# radius-server host{hostname|ip-address}[auth-port port-number][acct-port port-number][timeout seconds][retransmit retries][key string]Switch(config)# radius-server vsa send accountingExamples
The following example shows how to add Device Sensor protocol data to the accounting records:
Switch> enableSwitch# configure terminalSwitch(config)# device-sensor accountingRelated Commands
debug device-sensor
Enables debugging for Device Sensor.
show device-sensor cache
Displays Device Sensor cache entries.
device-sensor filter-spec
To apply a specific protocol filter containing a list of Type-Length-Value (TLV) fields to Device Sensor output, use the device-sensor filter-spec command in global configuration mode. To remove the protocol filter list from Device Sensor output, use the no form of this command.
device-sensor filter-spec {cdp | dhcp | lldp} {exclude {all | list list-name} | include list list-name}
Syntax Description
Defaults
All TLVs are included in notifications and will trigger notifications.
Command Modes
Global configuration
Command History
Usage Guidelines
Use the device-sensor filter-spec command to specify the TLVs that must be included in all sensor outputs (session notifications sent to internal sensor clients and accounting requests).
Certain TLVs and message types such as DISCOVER, OFFER, REQUEST, ACK, and IP address are unconditionally excluded because they are used as transport for higher layer protocols and will change frequently without conveying any useful information about the endpoint.
OFFER messages will also be ignored as they may be received from multiple servers and will not convey any useful endpoint data.
Examples
The following example shows how to apply a Cisco Discovery Protocol TLV filter list to Device Sensor output:
Switch> enableSwitch# configure terminalSwitch(config)# device-sensor filter-spec cdp include cdp-list1Related Commands
device-sensor filter-list dhcp
To create a Dynamic Host Configuration Protocol (DHCP) filter containing a list of options that can be included or excluded in Device Sensor output, use the device-sensor filter-list dhcp command in global configuration mode. To remove the DHCP filter containing the list of options, use the no form of this command.
device-sensor filter-list dhcp list option-list-name
no device-sensor filter-list dhcp list option-list-name
Syntax Description
Defaults
DHCP options filter list is not available.
Command Modes
Global configuration
Command History
Usage Guidelines
Use the device-sensor filter-list dhcp list option-list-name command to configure the name of the DHCP options filter list and enter into DHCP sensor configuration mode. You can configure the list of options in DHCP sensor configuration mode using the option {name option-name | number option-number} command. Use the name option-name keyword-argument pair to specify the name of the TLV. Enter ? for querying the available TLV names. Use the number option-number keyword-argument pair to specify the TLV number to be added to the DHCP options filter list.
Use the no option {name option-name | number option-number} command to remove individual options from the DHCP options filter list.
Use the no device-sensor filter-list dhcp list option-list-name command to remove the entire TLV list containing all the TLVs.
Examples
The following example shows how to create a DHCP filter containing a list of options:
Switch> enableSwitch# configure terminalSwitch(config)# device-sensor filter-list dhcp list dhcp-listSwitch(config-sensor-dhcplist)# option name domain-nameSwitch(config-sensor-dhcplist)# option name host-nameSwitch(config-sensor-dhcplist)# option number 50Switch(config-sensor-dhcplist)# endRelated Commands
device-sensor filter-list lldp
To create a Link Layer Discovery Protocol (LLDP) filter containing a list of Type-Length-Value (TLV) fields that can be included or excluded in Device Sensor output, use the device-sensor filter-list lldp command in global configuration mode. To remove the LLDP filter containing the list of TLV fields, use the no form of this command.
device-sensor filter-list lldp list tlv-list-name
no device-sensor filter-list lldp list tlv-list-name
Syntax Description
Defaults
LLDP TLV filter list is not available.
Command Modes
Global configuration
Command History
Usage Guidelines
Use the device-sensor filter-list lldp list tlv-list-name command to configure the name of the LLDP TLV filter list and enter LLDP sensor configuration mode. You can configure the list of TLVs in LLDP sensor configuration mode using the tlv {name' tlv-name | number tlv-number} command. Use the name tlv-name keyword-argument pair to specify the name of the TLV. Enter ? for querying the available TLV names. Use the number tlv-name keyword-argument pair to specify the TLV number to be added to the LLDP TLV filter list.
Use the no tlv {name' tlv-name | number tlv-number} command to remove individual TLVs from the LLDP TLV filter list.
Use the no device-sensor filter-list lldp list tlv-list-name command to remove the entire TLV list containing all the TLVs.
Examples
The following example shows how to create an LLDP filter containing a list of TLVs:
Switch> enableSwitch# configure terminalSwitch(config)# device-sensor filter-list lldp list lldp-listSwitch(config-sensor-lldplist)# tlv name address-typeSwitch(config-sensor-lldplist)# tlv name device-nameSwitch(config-sensor-lldplist)# tlv number 34Switch(config-sensor-lldplist)# endRelated Commands
device-sensor notify
To enable client notifications and accounting events for Type-Length-Value (TLV) changes, use the device-sensor notify command in global configuration mode. To disable client notifications and accounting events for TLV changes, use the no form of this command.
device-sensor notify all-changes new-tlvs
no device-sensor notify all-changes new-tlvs
Syntax Description
all-changes
Enables client notifications and accounting events for all TLV changes.
new-tlvs
Enables client notifications and accounting events for only new TLV changes.
Defaults
Client notifications and accounting events are generated only for new TLVs.
Command Modes
Global configuration
Command History
Usage Guidelines
By default, for each supported peer protocol, client notifications and accounting events will only be generated when an incoming packet includes a TLV that has not been previously received in the context of a given session.
To enable client notifications and accounting events for all TLV changes, where either a new TLV has been received or a previously received TLV has been received with a different value, use the device-sensor notify all-changes command.
To return to the default behavior, use the device-sensor notify new-tlvs or the default device-sensor notify command.
Examples
The following example shows how to enable client notifications and accounting events for all TLV change:
Switch> enableSwitch# configure terminalSwitch(config)# device-sensor notify all-changesRelated Commands
device-sensor filter-list cdp
To create a Cisco Discovery Protocol filter containing a list of Type-Length-Value (TLV) fields that can be included or excluded in Device Sensor output, use the device-sensor filter-list cdp command in global configuration mode. To remove the Cisco Discovery Protocol filter containing the list of TLV fields, use the no form of this command.
device-sensor filter-list cdp list tlv-list-name
no device-sensor filter-list cdp list tlv-list-name
Syntax Description
list
Contains a Cisco Discovery Protocol TLV filter list.
tlv-list-name
Cisco Discovery Protocol TLV filter list name.
Defaults
Cisco Discovery Protocol TLV filter list is not available.
Command Modes
Global configuration
Command History
Usage Guidelines
Use the device-sensor filter-list cdp list tlv-list-name command to configure the name of the Cisco Discovery Protocol TLV filter list and enter Cisco Discovery Protocol sensor configuration mode. You can configure the list of TLVs in Cisco Discovery Protocol sensor configuration mode using the tlv {name tlv-name | number tlv-number} command. Use the name tlv-name keyword-argument pair to specify the name of the TLV. Enter ? for querying the available TLV names. Use the number tlv-number keyword-argument pair to specify the TLV number to be added to the Cisco Discovery Protocol TLV filter list.
Use the no tlv {name' tlv-name | number tlv-number} command to remove individual TLVs from the Cisco Discovery Protocol TLV filter list.
Use the no device-sensor filter-list cdp list tlv-list-name command to remove the entire TLV list containing all the TLVs.
Examples
The following example shows how to create a Cisco Discovery Protocol filter containing a list of TLVs:
Switch> enableSwitch# configure terminalSwitch(config)# device-sensor filter-list cdp list cdp-listSwitch(config-sensor-cdplist)# tlv name address-typeSwitch(config-sensor-cdplist)# tlv name device-nameSwitch(config-sensor-cdplist)# tlv number 34Switch(config-sensor-cdplist)# endRelated Commands
show device-sensor cache
To display Device Sensor cache entries, use the show device-sensor cache command in privileged EXEC mode.
show device-sensor cache { mac mac-address | all }
Syntax Description
mac mac-address
Specifies the MAC address of the device for which the sensor cache entries are to be displayed.
all
Displays sensor cache entries for all devices.
Defaults
There are no defaults for this command.
Command Modes
Privileged EXEC
Command History
Usage Guidelines
Use the show device-sensor cache command to display a list of Type-Length-Value (TLV) fields or options received from a particular device or from all devices.
Examples
The following is sample output from the show device-sensor cache mac mac-address command:
Router# show device-sensor cache mac 0024.14dc.df4dDevice: 0024.14dc.df4d on port GigabitEthernet1/0/24--------------------------------------------------Proto Type:Name Len Valuecdp 26:power-available-type 16 00 1A 00 10 00 00 00 01 00 00 00 00 FF FF FF FFcdp 22:mgmt-address-type 17 00 16 00 11 00 00 00 01 01 01 CC 00 04 09 1B 650Ecdp 11:duplex-type 5 00 0B 00 05 01cdp 9:vtp-mgmt-domain-type 4 00 09 00 04cdp 4:capabilities-type 8 00 04 00 08 00 00 00 28cdp 1:device-name 14 00 01 00 0E 73 75 70 70 6C 69 63 61 6E 74lldp 0:end-of-lldpdu 2 00 00lldp 8:management-address 14 10 0C 05 01 09 1B 65 0E 03 00 00 00 01 00lldp 7:system-capabilities 6 0E 04 00 14 00 04lldp 4:port-description 23 08 15 47 69 67 61 62 69 74 45 74 68 65 72 6E 6574 31 2F 30 2F 32 34lldp 5:system-name 12 0A 0A 73 75 70 70 6C 69 63 61 6E 74dhcp 82:relay-agent-info 20 52 12 01 06 00 04 00 18 01 18 02 08 00 06 00 2414 DC DF 80dhcp 12:host-name 12 0C 0A 73 75 70 70 6C 69 63 61 6E 74dhcp 61:client-identifier 32 3D 1E 00 63 69 73 63 6F 2D 30 30 32 34 2E 31 3464 63 2E 64 66 34 64 2D 47 69 31 2F 30 2F 32 34dhcp 57:max-message-size 4 39 02 04 80The following is sample output from the show device-sensor cache all command:
Router# show device-sensor cache allDevice: 001c.0f74.8480 on port GigabitEthernet2/1--------------------------------------------------Proto Type:Name Len Valuedhcp 52:option-overload 3 34 01 03dhcp 60:class-identifier 11 3C 09 64 6F 63 73 69 73 31 2E 30dhcp 55:parameter-request-list 8 37 06 01 42 06 03 43 96dhcp 61:client-identifier 27 3D 19 00 63 69 73 63 6F 2D 30 30 31 63 2E 30 6637 34 2E 38 34 38 30 2D 56 6C 31dhcp 57:max-message-size 4 39 02 04 80Device: 000f.f7a7.234f on port GigabitEthernet2/1--------------------------------------------------Proto Type:Name Len Valuecdp 22:mgmt-address-type 8 00 16 00 08 00 00 00 00cdp 19:cos-type 5 00 13 00 05 00cdp 18:trust-type 5 00 12 00 05 00cdp 11:duplex-type 5 00 0B 00 05 01cdp 10:native-vlan-type 6 00 0A 00 06 00 01cdp 9:vtp-mgmt-domain-type 9 00 09 00 09 63 69 73 63 6FThe following table describes the significant fields shown in the display.
Related Commands
debug device-sensor
To enable debugging for Device Sensor, use the debug device-sensor command in privileged EXEC mode.
debug device-sensor errors events
Syntax Description
errors
Displays Device Sensor error messages
events
Displays messages for events such as protocol packet arrivals, identity updates and release events sent to the session manager.
Defaults
There are no defaults for this command.
Command Modes
Privileged EXEC
Command History
Usage Guidelines
Use the debug device-sensor command in conjunction with the debug authentication all command to troubleshoot scenarios where device sensor cache entries are not being created for the connected devices
Examples
The following is sample output from the debug device-sensor events command. The debug output shows how Cisco Discovery Protocol packets and Type-Length-Values (TLVs) are received from the device connected to the GigabitEthernet 2/1 interface:
Switch# debug device-sensor eventsSwitch#*Nov 30 23:58:45.811: DSensor: Received cdp packet from GigabitEthernet2/1:00d0.2bdf.08a5*Nov 30 23:58:45.811: DSensor: SM returned no or invalid session label for GigabitEthernet2/1:00d0.2bdf.08a5*Nov 30 23:58:45.811: DSensor: Updating SM with identity attribute listcdp-tlv 0 00 01 00 0B 4A 41 45 30 37 34 31 31 50 53 32cdp-tlv 0 00 03 00 03 32 2F 38cdp-tlv 0 00 04 00 04 00 00 00 0Acdp-tlv 0 00 05 00 68 57 53 2D 43 32 39 34 38 20 53 6F 66 74 77 61 72 65 2C 20 56 65 72 73 69 6F 6E 20 4D 63 70 53 57 3A 20 36 2E 34 28 35 2E30 29 20 4E 6D 70 53 57 3A 20 36 2E 34 28 35 29 0A 43 6F 70 79 72 69 67 68 74 20 28 63 29 20 31 39 39 35 2D 32 30 30 33 20 62 79 20 43 69 73 63 6F 20 53 79 7374 65 6D 73 2C 20 49 6E 63 2E 0Acdp-tlv 0 00 06 00 08 57 53 2D 43 32 39 34 38cdp-tlv 0 00 09 00 00cdp-tlv 0 00 0A 00 02 00 21cdp-tlv 0 00 0B 00 01 01cdp-tlv 0 00 12 00 01 00cdp-tlv 0 00 13 00 01 00cdp-tlv 0 00 14 00 00cdp-tlv 0 00 15 00 0A 06 08 2B 06 01 04 01 09 05 2Acdp-tlv 0 00 16 00 16 00 00 00 02 01 01 CC 00 04 00 00 00 0001 01 CC 00 04 01 01 01 01cdp-tlv 0 00 17 00 01 00swidb 0 604702240 (0x240B0620)clid-mac-addr 0 00 D0 2B DF 08 A5*Nov 30 23:58:46.831: DSensor: Received cdp packet from GigabitEthernet2/1:00d0.2bdf.08a5exiSwitch#*Nov 30 23:58:51.171: %SYS-5-CONFIG_I: Configured from console by consoleRelated Commands
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, submitting a service request, and gathering additional information, see the monthly What's New in Cisco Product Documentation, which also lists all new and revised Cisco technical documentation:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.htmlSubscribe to the What's New in Cisco Product Documentation as a Really Simple Syndication (RSS) feed and set content to be delivered directly to your desktop using a reader application. The RSS feeds are a free service and Cisco currently supports RSS version 2.0.
This document is to be used in conjunction with the documents listed in the "Obtaining Documentation and Submitting a Service Request" section.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
© 2012 Cisco Systems, Inc. All rights reserved.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback