Prerequisites for TACACS+
The following are the prerequisites for set up and configuration of switch access with TACACS+ (must be performed in the order presented):
-
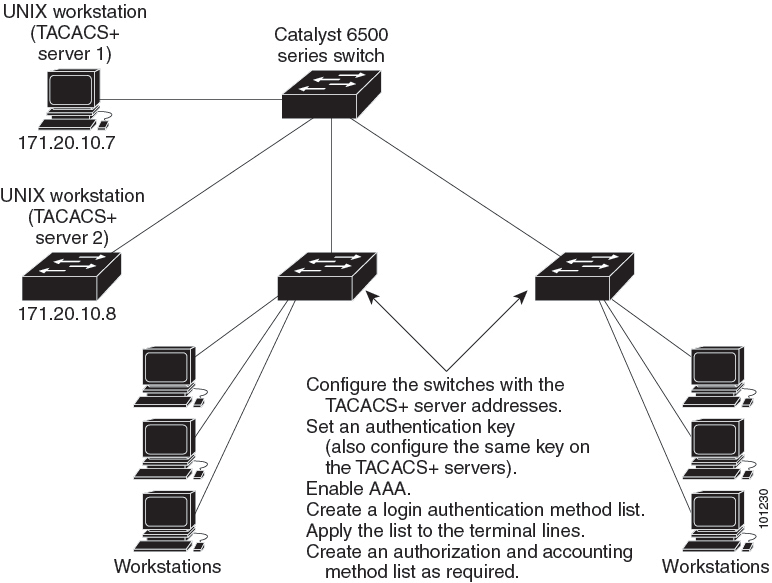
Configure the switches with the TACACS+ server addresses.
-
Set an authentication key.
-
Configure the key from Step 2 on the TACACS+ servers.
-
Enable authentication, authorization, and accounting (AAA).
-
Create a login authentication method list.
-
Apply the list to the terminal lines.
-
Create an authorization and accounting method list.
The following are the prerequisites for controlling switch access with TACACS+:
-
You must have access to a configured TACACS+ server to configure TACACS+ features on your switch. Also, you must have access to TACACS+ services maintained in a database on a TACACS+ daemon typically running on a LINUX or Windows workstation.
-
We recommend a redundant connection between a switch stack and the TACACS+ server. This is to help ensure that the TACACS+ server remains accessible in case one of the connected stack members is removed from the switch stack.
-
You need a system running the TACACS+ daemon software to use TACACS+ on your switch.
-
To use TACACS+, it must be enabled.
-
Authorization must be enabled on the switch to be used.
-
Users must first successfully complete TACACS+ authentication before proceeding to TACACS+ authorization.
-
To use any of the AAA commands listed in this section or elsewhere, you must first enable AAA with the aaa new-model command.
-
At a minimum, you must identify the host or hosts maintaining the TACACS+ daemon and define the method lists for TACACS+ authentication. You can optionally define method lists for TACACS+ authorization and accounting.
-
The method list defines the types of authentication to be performed and the sequence in which they are performed; it must be applied to a specific port before any of the defined authentication methods are performed. The only exception is the default method list (which, by coincidence, is named default ). The default method list is automatically applied to all ports except those that have a named method list explicitly defined. A defined method list overrides the default method list.
-
Use TACACS+ for privileged EXEC access authorization if authentication was performed by using TACACS+.
-
Use the local database if authentication was not performed by using TACACS+.

 Feedback
Feedback