Restrictions for Configuring IPv4 Access Control Lists
General Network Security
The following are restrictions for configuring network security with ACLs:
-
Not all commands that accept a numbered ACL accept a named ACL. ACLs for packet filters and route filters on interfaces can use a name. VLAN maps also accept a name.
-
A standard ACL and an extended ACL cannot have the same name.
-
Though visible in the command-line help strings, appletalk is not supported as a matching condition for the deny and permit MAC access-list configuration mode commands.
-
ACL wildcard is not supported in downstream client policy.
-
Router ACL is enforced on all types of traffic, including CPU generated traffic.
-
ACL logging in the egress direction are not supported for packets that are generated from the control plane of the device.
-
If a downloadable ACL contains any type of duplicate entries, the entries are not auto merged. As a result, the 802.1X session authorization fails. Ensure that the downloadable ACL is optimized without any duplicate entries, for example port-based and name-based entries for the same port.
IPv4 ACL Network Interfaces
The following restrictions apply to IPv4 ACLs to network interfaces:
-
When controlling access to an interface, you can use a named or numbered ACL.
-
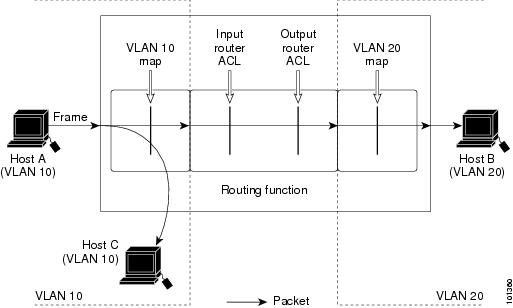
If you apply an ACL to a Layer 2 interface that is a member of a VLAN, the Layer 2 (port) ACL takes precedence over an input Layer 3 ACL applied to the VLAN interface or a VLAN map applied to the VLAN.
-
If you apply an ACL to a Layer 3 interface and routing is not enabled on the switch, the ACL only filters packets that are intended for the CPU, such as SNMP, Telnet, or web traffic.
-
If the preauth_ipv4_acl ACL is configured to filter packets, the ACL is removed after authentication.
-
You do not have to enable routing to apply ACLs to Layer 2 interfaces.
MAC ACLs on a Layer 2 Interface
After you create a MAC ACL, you can apply it to a Layer 2 interface to filter non-IP traffic coming in that interface. When you apply the MAC ACL, consider these guidelines:
-
You can apply no more than one IP access list and one MAC access list to the same Layer 2 interface. The IP access list filters only IP packets, and the MAC access list filters non-IP packets.
-
A Layer 2 interface can have only one MAC access list. If you apply a MAC access list to a Layer 2 interface that has a MAC ACL configured, the new ACL replaces the previously configured one.
 Note |
The mac access-group interface configuration command is only valid when applied to a physical Layer 2 interface. You cannot use the command on EtherChannel port channels. |
IP Access List Entry Sequence Numbering
- This feature does not support dynamic, reflexive, or firewall access lists.
 Feedback
Feedback