Prerequisites for IGMP Snooping
Observe these guidelines when configuring the IGMP snooping querier:
-
Configure the VLAN in global configuration mode.
-
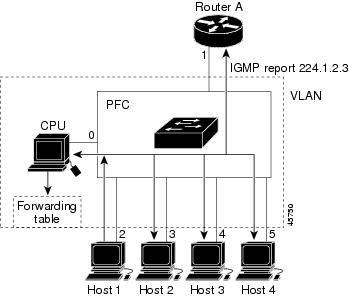
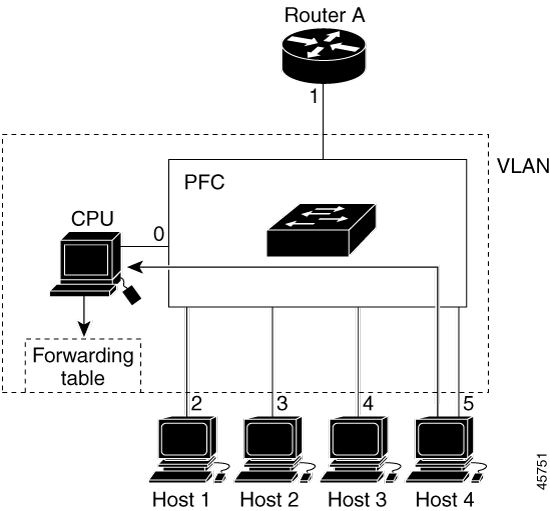
Configure an IP address on the VLAN interface. When enabled, the IGMP snooping querier uses the IP address as the query source address.
-
If there is no IP address configured on the VLAN interface, the IGMP snooping querier tries to use the configured global IP address for the IGMP querier. If there is no global IP address specified, the IGMP querier tries to use the VLAN switch virtual interface (SVI) IP address (if one exists). If there is no SVI IP address, the device uses the first available IP address configured on the device. The first IP address available appears in the output of the show ip interface privileged EXEC command. The IGMP snooping querier does not generate an IGMP general query if it cannot find an available IP address on the device.
-
The IGMP snooping querier supports IGMP Versions 1 and 2.
-
When administratively enabled, the IGMP snooping querier moves to the nonquerier state if it detects the presence of a multicast router in the network.
-
When it is administratively enabled, the IGMP snooping querier moves to the operationally disabled state if IGMP snooping is disabled in the VLAN.
-
Layer 3 multicast is not supported.
-
MAC based snooping is supported in hardware.

 Feedback
Feedback