Cisco Nexus 5600 Series NX-OS Unicast Routing Configuration Guide, Release 7.x
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- March 12, 2014
Chapter: Configuring Layer 3 Virtualization
Configuring Layer 3 Virtualization
This chapter describes how to configure Layer 3 virtualization.
Layer 3 Virtualization
This section includes the following topics:
Overview of Layer 3 Virtualization
Cisco NX-OS supports virtual routing and forwarding instances (VRFs). Each VRF contains a separate address space with unicast and multicast route tables for IPv4 and IPv6 and makes routing decisions independent of any other VRF.
Each router has a default VRF and a management VRF. All Layer 3 interfaces and routing protocols exist in the default VRF until you assign them to another VRF. The mgmt0 interface exists in the management VRF. With the VRF-lite feature, the switch supports multiple VRFs in customer edge (CE) switches. VRF-lite allows a service provider to support two or more Virtual Private Networks (VPNs) with overlapping IP addresses using one interface.

Note![]() The switch does not use Multiprotocol Label Switching (MPLS) to support VPNs.
The switch does not use Multiprotocol Label Switching (MPLS) to support VPNs.
VRF and Routing
All unicast and multicast routing protocols support VRFs. When you configure a routing protocol in a VRF, you set routing parameters for the VRF that are independent of routing parameters in another VRF for the same routing protocol instance.
You can assign interfaces and route protocols to a VRF to create virtual Layer 3 networks. An interface exists in only one VRF. Figure 12-1 shows one physical network split into two virtual networks with two VRFs. Routers Z, A, and B exist in VRF Red and form one address domain. These routers share route updates that do not include router C because router C is configured in a different VRF.
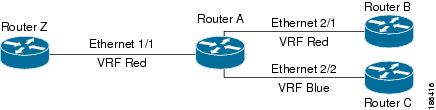
By default, Cisco NX-OS uses the VRF of the incoming interface to select which routing table to use for a route lookup. You can configure a route policy to modify this behavior and set the VRF that Cisco NX-OS uses for incoming packets.
Cisco NX-OS supports route leaking (import and export) between VRFs in a VRF lite scenario. The following are guidelines for the VRF route-leak feature:
- Supports route-leak between any two non-default VRFs and route-leak from the default VRF to any other VRF.
- Route-leak to the default VRF is not allowed as it is a global VRF.
- The route-leak feature is implemented using export and import route-targets under the VRF context.
- Leaking (exporting) a part of the prefixes is done by using export-map with the match ip address and set extcommunity rt commands. The regularly used route-target export command should not be used for this purpose.
- By default, the maximum prefix that can be leaked is 1000 routes. This is configurable.
- The route-leak feature must have an Enterprise license and the BGP feature enabled.
VRF-Lite
VRF-lite is a feature that enables a service provider to support two or more VPNs, where IP addresses can be overlapped among the VPNs. VRF-lite uses input interfaces to distinguish routes for different VPNs and forms virtual packet-forwarding tables by associating one or more Layer 3 interfaces with each VRF. Interfaces in a VRF can be either physical, such as Ethernet ports, or logical, such as VLAN SVIs, but a Layer 3 interface cannot belong to more than one VRF at any time.

Note![]() Multiprotocol Label Switching (MPLS) and MPLS control plane are not supported in the VRF-lite implementation.
Multiprotocol Label Switching (MPLS) and MPLS control plane are not supported in the VRF-lite implementation.

Note![]() VRF-lite interfaces must be Layer 3 interfaces.
VRF-lite interfaces must be Layer 3 interfaces.
VRF-Aware Services
A fundamental feature of the Cisco NX-OS architecture is that every IP-based feature is VRF aware.
The following VRF-aware servics can select a particular VRF to reach a remote server or to filter information based on the selected VRF:
- AAA—See the Cisco Nexus 6000 Series NX-OS Security Configuration Guide, Release 7.x, for more information.
- Call Home—See the Cisco Nexus 6000 Series NX-OS System Management Configuration Guide, Release 7.x, for more information.
- HSRP—See Chapter 17, “Configuring HSRP” for more information.
- HTTP—See the Cisco Nexus 6000 Series NX-OS Fundamentals Configuration Guide, Release 7.x, for more information.
- Licensing—See the Cisco NX-OS Licensing Guide for more information.
- NTP—See the Cisco Nexus 6000 Series NX-OS System Management Configuration Guide, Release 7.x, for more information.
- RADIUS—See the Cisco Nexus 6000 Series NX-OS Security Configuration Guide, Release 7.x, for more information.
- Ping and Traceroute —See the Cisco Nexus 6000 Series NX-OS Fundamentals Configuration Guide, Release 7.x, for more information.
- SSH—See the Cisco Nexus 6000 Series NX-OS Fundamentals Configuration Guide, Release 7.x, for more information.
- SNMP—See the Cisco Nexus 6000 Series NX-OS System Management Configuration Guide, Release 7.x, for more information.
- Syslog—See the Cisco Nexus 6000 Series NX-OS System Management Configuration Guide, Release 7.x, for more information.
- TACACS+—See the Cisco Nexus 6000 Series NX-OS Security Configuration Guide, Release 7.x, for more information.
- TFTP—See the Cisco Nexus 6000 Series NX-OS Fundamentals Configuration Guide, Release 7.x, for more information.
- VRRP—See Chapter 18, “Configuring VRRP” for more information.
See the appropriate configuration guide for each service for more information on configuring VRF support in that service.
Reachability
Reachability indicates which VRF contains the routing information necessary to get to the server providing the service. For example, you can configure an SNMP server that is reachable on the management VRF. When you configure that server address on the router, you also configure which VRF that Cisco NX-OS must use to reach the server.
Figure 12-2 shows an SNMP server that is reachable over the management VRF. You configure router A to use the management VRF for SNMP server host 192.0.2.1.
Figure 12-2 Service VRF Reachability
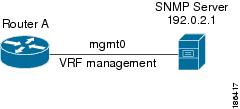
Filtering
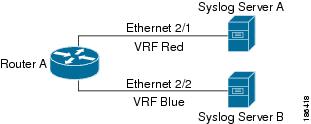
Filtering allows you to limit the type of information that goes to a VRF-aware service based on the VRF. For example, you can configure a syslog server to support a particular VRF. Figure 12-3 shows two syslog servers with each server supporting one VRF. syslog server A is configured in VRF Red, so Cisco NX-OS sends only system messages generated in VRF Red to syslog server A.
Figure 12-3 Service VRF Filtering
Combining Reachability and Filtering
You can combine reachability and filtering for VRF-aware services. You configure the VRF that Cisco NX-OS uses to connect to that service as well as the VRF that the service supports. If you configure a service in the default VRF, you can optionally configure the service to support all VRFs.
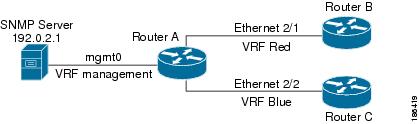
Figure 12-4 shows an SNMP server that is reachable on the management VRF. You can configure the SNMP server to support only the SNMP notifications from VRF Red, for example.
Figure 12-4 Service VRF Reachability Filtering
Licensing Requirements for VRFs
The following table shows the licensing requirements for this feature:
Guidelines and Limitations
VRFs have the following configuration guidelines and limitations:
- When you make an interface a member of an existing VRF, Cisco NX-OS removes all Layer 3 configuration. You should configure all Layer 3 parameters after adding an interface to a VRF.
- You should add the mgmt0 interface to the management VRF and configure the mgmt0 IP address and other parameters after you add it to the management VRF.
- If you configure an interface for a VRF before the VRF exists, the interface is operationally down until you create the VRF.
- Cisco NX-OS creates the default and management VRFs by default. You should make the mgmt0 interface a member of the management VRF.
- The write erase boot command does not remove the management VRF configuration. You must use the write erase command and then the write erase boot command.
VRF-lite has the following guidelines and limitations:
- A switch with VRF-lite has a separate IP routing table for each VRF, which is separate from the global routing table.
- Because VRF-lite uses different VRF tables, the same IP addresses can be reused. Overlapped IP addresses are allowed in different VPNs.
- VRF-lite does not support all MPLS-VRF functionality; it does not support label exchange, LDP adjacency, or labeled packets.
- Multiple virtual Layer 3 interfaces can be connected to a VRF-lite switch.
- The switch supports configuring a VRF by using physical ports, VLAN SVIs, or a combination of both. The SVIs can be connected through an access port or a trunk port.
- The Layer 3 TCAM resource is shared between all VRFs.
- A switch using VRF can support one global network and up to 64 VRFs. The total number of routes supported is limited by the size of the TCAM.
- VRF-lite supports BGP, RIP, static routing, EIGRP, EIGRPv6, OSPF, and OSPFv3.
- VRF-lite does not affect the packet switching rate.
Default Settings
Table 12-1 lists the default settings for VRF parameters.
|
|
|
|---|---|
Configuring VRFs
This section contains the following topics:
- Creating a VRF
- Assigning VRF Membership to an Interface
- Configuring VRF Parameters for a Routing Protocol
- Configuring a VRF-Aware Service
- Setting the VRF Scope

Note![]() If you are familiar with the Cisco IOS CLI, be aware that the Cisco NX-OS commands for this feature might differ from the Cisco IOS commands that you would use.
If you are familiar with the Cisco IOS CLI, be aware that the Cisco NX-OS commands for this feature might differ from the Cisco IOS commands that you would use.
Creating a VRF
SUMMARY STEPS
3.![]() ip route { ip-prefix | ip-addr ip-mask } {[ next-hop | nh-prefix ] | [ interface next-hop | nh-prefix ]} [ tag tag-value [ pref ]]
ip route { ip-prefix | ip-addr ip-mask } {[ next-hop | nh-prefix ] | [ interface next-hop | nh-prefix ]} [ tag tag-value [ pref ]]
DETAILED STEPS
Use the no vrf context command to delete the VRF and the associated configuration:
|
|
|
|---|---|
Any commands available in global configuration mode are also available in VRF configuration mode.
This example shows how to create a VRF and add a static route to the VRF:
Assigning VRF Membership to an Interface
BEFORE YOU BEGIN
Assign the IP address for an interface after you have configured the interface for a VRF.
SUMMARY STEPS
2.![]() interface interface-type slot/port
interface interface-type slot/port
5.![]() ip-address ip-prefix/length
ip-address ip-prefix/length
6.![]() (Optional) show vrf vrf-name interface interface-type number
(Optional) show vrf vrf-name interface interface-type number
DETAILED STEPS
This example shows how to add an interface to the VRF:
Configuring VRF Parameters for a Routing Protocol
You can associate a routing protocol with one or more VRFs. See the appropriate chapter for information on how to configure VRFs for the routing protocol. This section uses OSPFv2 as an example protocol for the detailed configuration steps.
SUMMARY STEPS
4.![]() (Optional) maximum-paths paths
(Optional) maximum-paths paths
5.![]() interface interface-type slot/port
interface interface-type slot/port
8.![]() ip address ip-prefix/length
ip address ip-prefix/length
DETAILED STEPS
This example shows how to create a VRF and add an interface to the VRF:
Configuring a VRF-Aware Service
You can configure a VRF-aware service for reachability and filtering. See the “VRF-Aware Services” section for links to the appropriate chapter or configuration guide for information on how to configure the service for VRFs. This section uses SNMP and IP domain lists as example services for the detailed configuration steps.
SUMMARY STEPS
2.![]() snmp-server host ip-address [ filter_vrf vrf-name ] [ use-vrf vrf-name ]
snmp-server host ip-address [ filter_vrf vrf-name ] [ use-vrf vrf-name ]
4.![]() ip domain-list domain-name [ all-vrfs ] [ use-vrf vrf-name ]
ip domain-list domain-name [ all-vrfs ] [ use-vrf vrf-name ]
DETAILED STEPS
This example shows how to send SNMP information for all VRFs to SNMP host 192.0.2.1, reachable on VRF Red:
This example shows how to Filter SNMP information for VRF Blue to SNMP host 192.0.2.12, reachable on VRF Red:
Setting the VRF Scope
You can set the VRF scope for all EXEC commands (for example, show commands). This automatically restricts the scope of the output of EXEC commands to the configured VRF. You can override this scope by using the VRF keywords available for some EXEC commands.
To set the VRF scope, use the following command in EXEC mode:
|
|
|
|---|---|
Sets the routing context for all EXEC commands. Default routing context is the default VRF. |
To return to the default VRF scope, use the following command in EXEC mode:
|
|
|
|---|---|
Verifying the VRF Configuration
To display the VRF configuration information, perform one of the following tasks:
|
|
|
|---|---|
Configuration Examples for VRF
This example shows how to configure VRF Red, add an SNMP server to that VRF, and add an instance of OSPF to VRF Red:
snmp-server host 192.0.2.12 use-vrf Red
This example shows how to configure VRF Red and Blue, add an instance of OSPF to each VRF, and create an SNMP context for each OSPF instance in each VRF.:
!Create the OSPF instances and associate them with each VRF
!Configure one interface to use ospf Lab on VRF Red
!Configure another interface to use ospf Production on VRF Blue
ip router ospf Production area 0
snmp-server user admin network-admin auth md5 nbv-12345
snmp-server community public ro
Related Topics
Additional References
For additional information related to implementing virtualization, see the following sections:
Related Documents
|
|
|
|---|---|
Cisco Nexus 6000 Series Command Reference, Cisco NX-OS Releases 7.x |
Standards
|
|
|
|---|---|
No new or modified standards are supported by this feature, and support for existing standards has not been modified by this feature. |
 Feedback
Feedback