Cisco AVS Overview
The Cisco Application Virtual Switch (AVS) is a key part of the Cisco Application Centric Infrastructure (ACI). It is a distributed virtual switch that offers different forwarding and encapsulation options and extends across many virtualized hosts and data centers defined by the VMware vCenter Server.
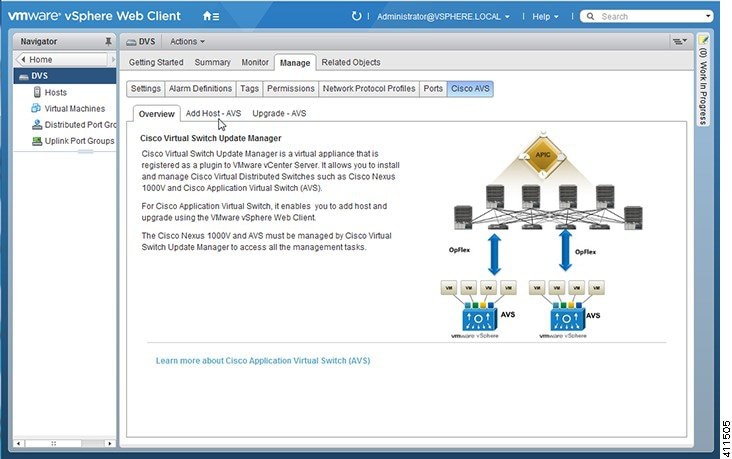
The Cisco AVS is integrated with the Cisco ACI architecture as a virtual leaf and is managed by the Cisco APIC. The Cisco AVS implements the OpFlex protocol for control plane communication.
This section provides an overview of the Cisco AVS.
The Cisco AVS supports two modes of traffic forwarding: Local Switching mode, formerly known as Fex disable mode; and No Local Switching mode, formerly known as Fex enable mode. You choose the forwarding mode during Cisco AVS installation.
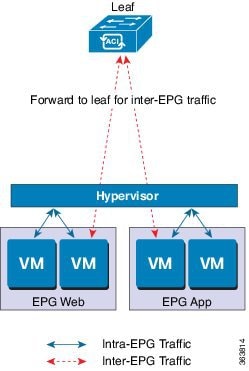
Local Switching Mode
In Local Switching mode, all intra-EPG traffic is locally forwarded by the Cisco AVS, without the involvement of the leaf. All inter-EPG traffic is forwarded through the leaf. In this mode, the Cisco AVS can use either VLAN or VXLAN encapsulation—or both—for forwarding traffic to the leaf and back. You choose the encapsulation type during Cisco AVS installation.
Beginning with Cisco AVS Release 5.2(1)SV3(2.5), you can configure a single VMM domain in Local Switching mode to use VLAN and VXLAN encapsulation. Previously, encapsulation was determined solely by the presence of VLAN or multicast pools, and you needed to have separate VMM domains for EPGs using VLAN and VXLAN encapsulation.
If you choose VLAN encapsulation, a range of VLANs must be available for use by the Cisco AVS. These VLANs have local scope in that they have significance only within the Layer 2 network between the Cisco AVS and the leaf. If you choose VXLAN encapsulation, only the infra-VLAN needs to be available between the Cisco AVS and the leaf. This results in a simplified configuration and is the recommended encapsulation type if there are one or more switches between the Cisco AVS and the physical leaf.
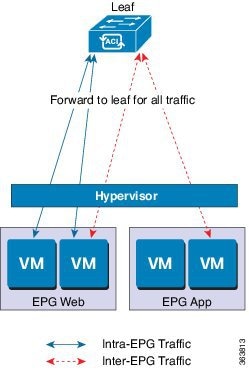
No Local Switching Mode
In No Local Switching mode, all traffic is forwarded by the leaf. In this mode, VXLAN is the only allowed encapsulation type.
Statistics Collection
Statistics collection is enabled on Cisco AVS by default. You may see Cisco AVS faults within the APIC GUI relating to VM resource use.
You should troubleshoot those faults in the VMware vCenter because the Cisco ACI only generates these faults based on information it receives from VMware vCenter.
About the Cisco AVS and the VMware vCenter
The Cisco Application Virtual Switch (AVS) is a distributed virtual switch that extends across many virtualized hosts. It manages a data center defined by the vCenter Server.
The Cisco AVS is compatible with any upstream physical access layer switch that complies with the Ethernet standard, including Cisco Nexus switches. The Cisco AVS is compatible with any server hardware listed in the VMware Hardware Compatibility List (HCL).
The Cisco AVS is a distributed virtual switch solution that is fully integrated within the VMware virtual infrastructure, including VMware vCenter for the virtualization administrator. This solution allows the network administrator to configure virtual switch and port groups in order to establish a consistent data center network policy.
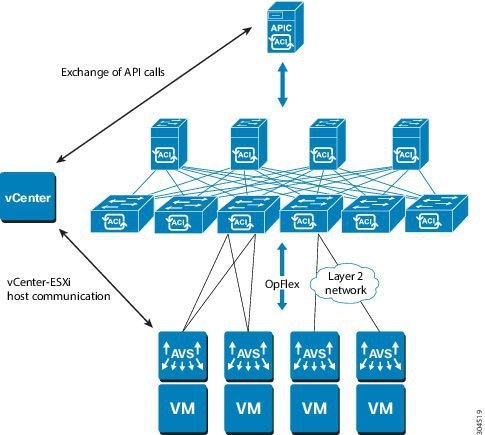
The following figure shows a topology that includes the Cisco AVS with the Cisco Application Policy Infrastructure Controller (APIC) and VMware vCenter.
 Note |
If there are multiple vCenters connected to a single Cisco ACI fabric, you should ensure that there are no overlapping MAC address allocation schema across the multiple vCenters while deploying the vCenters instead of the default OUI allocation. Overlaps can cause duplicate MAC address generation. For more information, see VMware documentation. |
Cisco AVS in a Multipod Environment
The Cisco AVS can be part of a multipod environment. Multipod environments use a single APIC cluster for all the pods; all the pods act as a single fabric.
Multipod environments enable a more fault tolerant fabric comprising multiple pods with isolated control plane protocols. They also provide greater flexibility in full mesh cabling between leaf and spine switches.
Cisco AVS does not require any additional configuration to operate in a multipod environment.
For detailed information about multipod environments, see the following documents on Cisco.com:
-
Cisco Application Centric Infrastructure Fundamentals
-
Cisco APIC Getting Started Guide
-
Cisco APIC NX-OS Style Command-Line Interface Configuration Guide
The following features are not supported for Cisco AVS with multipod in the Cisco APIC 2.0(1.x) release:
-
L3 Multicast
-
Storage vMotion with two separate NFS in two separate PODs
-
ERSPAN destination in different PODs
-
Distributed Firewall syslog server in different PODs
Required Software
The following table shows the versions of software you need to install for Cisco Application Virtual Switch (AVS) to work with the Cisco Application Policy Infrastructure Controller (APIC), VMware vCenter, and VMware ESXi hypervisor:
|
Component |
Description |
||
|---|---|---|---|
|
Cisco AVS software |
Cisco AVS is supported in Release 4.2(1)SV2(2.3) and later releases. However, Release 5.2(1)SV3(1.5) or later is required if you want to use Distributed Firewall and Microsegmentation with Cisco AVS. |
||
|
Cisco APIC |
See the Cisco AVS Release Notes for compatibility information. However, version 1.1(1j) or later is required with Cisco AVS 5.2(1)SV3(1.5) or later if you want to use Distributed Firewall and Microsegmentation with Cisco AVS. |
||
|
VMware vCenter |
Cisco AVS is compatible with release 5.5, 6.0, or 6.5 of VMware vCenter Server. |
||
|
VMware vSphere bare metal |
Cisco AVS is supported as a vLeaf for the Cisco APIC with release 5.5 and later releases of the VMware ESXi hypervisor.
|
||
|
Cisco Virtual Switch Update Manager (VSUM) |
Cisco AVS is supported in VSUM Release 1.0 and later releases. |
Cisco AVS Documentation
You can find documentation on the Cisco Application Virtual Switch page on Cisco.com.
-
Cisco Application Virtual Switch Release Notes
-
Cisco Application Virtual Switch Documentation Overview
-
Cisco Application Virtual Switch Installation Guide
-
Cisco Application Virtual Switch Download Instructions for VMware ESXi Deployments
-
Cisco Application Virtual Switch Configuration Guide
-
Cisco Application Virtual Switch Verified Scalability Guide
-
Cisco Application Virtual Switch Solution Guide
-
Cisco Application Virtual Switch Troubleshooting Guide
-
Cisco Virtual Switch Update Manager Getting Started Guide
-
Cisco Virtual Switch Update Manager Release Notes
-
Cisco Virtual Switch Update Manager Troubleshooting Guide




 Feedback
Feedback