Cloud Campus Fabric Test
Available Languages
With digitization, software applications are evolving from simply supporting business processes to becoming, in some cases, the primary source of business revenue and competitive differentiation. Organizations are now constantly challenged by the need to scale their network capacity to react quickly to application demands and growth. Another important aspect is security; since the campus network is used by people with different levels of access (e.g. employees, contractors, third parties, guests, etc.) and their BYOD devices to access these applications, the wired and wireless LAN capabilities should be enhanced to support those changing needs and ensure security compliance at the same time.
One of these enhancements is Fabric technology, which provides wired and wireless campus networks with programmable overlays and easy-to-deploy network virtualization, permitting a physical network to host one or more logical networks to meet the design intent. In addition to network virtualization, fabric technology in the campus network enhances control of communications, providing software-defined segmentation and policy enforcement based on user identity and group membership. Software-defined segmentation is seamlessly integrated using Cisco TrustSec® and Adaptive Policy technology, providing micro-segmentation for groups within a virtual network using Scalable Group Tags (SGTs).
On the other hand, managing the Campus network in the cloud offers great benefits such as reducing the operational complexity which in turn improves efficiencies and achieves business outcomes with end-to-end security and high scalability.
This document is intended to provide a solution design and deployment guide for organizations that are transitioning to the cloud, either partially or fully and desire a Cloud-first operating model for their campus fabric while leveraging Cisco Catalyst hardware and programmable Fabric as the building blocks for their campus network.
The proposed campus network solution in this document leverages the Cisco Programmable Fabric VXLAN with BGP EBVPN technology and the Cloud Management and Monitoring for Catalyst aspects of the Meraki Dashboard as illustrated in the following conceptual diagram.
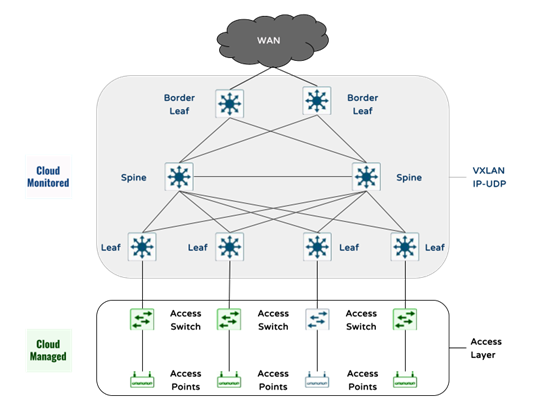
The proposed Cloud Campus Fabric is expected to deliver on the following outcomes:
● Control communications
● Segmentation
● Compliance
● Performance
● Cloud-first operating model
The following are the key requirements driving the evolution of existing campus networks.
Flexible campus for growth and scale (Test #1)
● Simplified deployment and automation (Wireless and Wired)—with single-pane of glass and provisioning APIs.
● Increased bandwidth needs—bandwidth aggregates using 10 Gbps Ethernet to 40 Gbps to 100 Gbps capacities over time.
● Increased capacity of wireless access points—WIFI 6 and WIFI 6E.
● Additional power requirements from Ethernet devices—The access layer design should have the ability to support Power over Ethernet (PoE) with 60W per port, offered with Cisco Universal Power Over Ethernet (UPOE), and as power demands continue to increase with new endpoints, IEEE 802.3bt and Cisco UPOE-Plus (UPOE+) can provide power up to 90W per port.
Integration Services and Security (unchanged)
● Consistent wired and wireless security capabilities—Security capabilities should be consistent whether a user is connecting to a wired Ethernet port or connecting over the wireless LAN.
● Network assurance and analytics—The deployment should proactively predict network-related and security-related risks by using telemetry to improve the performance of the network, devices, and applications.
● Identity services—Identifying users and devices connecting to the network provides the contextual information required to implement security policies for access control, network segmentation by using scalable group membership.
● Network virtualization—The capability to share a common infrastructure while supporting multiple VNs with isolated data and control planes enables different sets of users and applications to be isolated securely.
● Group-based policies—Creating access and application policies based on user group information provides a much easier and scalable way to deploy and manage security policies. Traditional access control lists (ACLs) can be difficult to implement, manage, and scale because they rely on network constructs such as IP addresses and subnets rather than group membership. Group membership is an IP-agnostic approach to policy creation which provides ease of operation for the network operator and a more scalable approach to ACLs.
● Software-defined segmentation—Scalable Group Tags assigned from group-based policies can be used to segment a network to achieve data plane isolation within physical and virtual networks.
Cisco Cloud Campus Fabric with BGP EVPN VXLAN Solution Components
The Cloud Campus Fabric solution is provided through a combination of Meraki Dashboard, the Cisco Identity Services Engine (ISE), and Catalyst wired platforms which have fabric functionality. As described later in this document, the Catalyst 9500 and 9300 platforms are utilized to create the elements of the Campus Fabric whilst the Catalyst 9300 and 9100 are utilized to create the elements of the Access Layer.
Cisco Meraki offers a comprehensive portfolio of cloud-managed IT solutions designed to work together to help deliver a modern network that is powerful, reliable, and easy to manage. This unique approach to IT aims to simplify powerful technology by reducing the overhead and costs associated with maintaining disparate solutions.
The Meraki cloud solution is a centralized management service that allows users to manage all their network devices via a single, simple and secure platform. Users can deploy, monitor, and configure their Meraki devices via the Meraki dashboard web interface or via APIs. The Meraki cloud is the backbone of the Meraki management solution. This "cloud" is a collection of highly reliable multi-tenant servers strategically distributed around the world at Meraki data centers. The servers at these data centers are powerful hosting computers comprised of many separate user accounts. They are called multi-tenant servers because the accounts share (equal) computing resources on their host (the server). Meraki ensures that customer information is kept secure by restricting organization access based on account authentication, as well as hashing authentication information such as user passwords or API keys.
The Meraki dashboard is a modern web browser-based tool used to configure Meraki devices and services. It is the visual alternative to the traditional command line, which is used to manage many routers, switches, security devices, and more. In addition to simplifying device management, the dashboard is also a platform for viewing network analytics, applying network permissions, and keeping track of users.
Here are some of the benefits of Meraki’s Cloud Managed IT:
Simplified network management
● Initial Configuration & Deployment allowing IT to benefit from a zero-touch deployment model.
● Management of the enterprise campus providing detailed insight into the health and performance of the network through a variety of unique features, tools, and proactive alerting.
● Support & Maintenance with logging, alerting, and debugging tools that are all built directly into each product, and are easily accessible via the Dashboard, or a variety of other services such as notifications or network summary reports including things such as anomalies.
End to end visibility
● Visibility and insight into the health of the services being delivered.
● Network trends and anomalies.
● Network Topology.
Streamline network operations
● Built-in operational tools for incident and problem management.
● Network sync and other configuration management tools such as templates.
● Native integrations with other Cisco platforms such as SSE, XDR, ISE, etc.
Enhanced security
● Meraki leverages technology such as secure boot, firmware image signing, and hardware trust anchors as part of the Cisco Secure Development lifecycle to maintain hardware and software integrity.
● Encrypted data between devices and the Cloud.
● Two factor authentication and Single Sign On, login history and change log.
Improved network reliability
● An expansive set of monitoring and logging tools, built directly into the Dashboard.
● Management data storage such as application usage, configuration changes, and event logs within the backend system.
● High Availability architecture in several ways to ensure serviceability with high bandwidth resilient connects, data center backups and resilient management servers.
Note: For additional information about the Meraki Cloud Architecture please refer to this article. Test #4
Cisco Identity Services Engine (ISE) is a secure network access platform enabling increased management awareness, control, and consistency for users and devices accessing an organization's network. ISE is an integral and mandatory component of campus for implementing network access control policy. ISE performs policy implementation, enabling dynamic mapping of users and devices to scalable groups, and simplifying end-to-end security policy enforcement. Within ISE, users and devices are shown in a simple and flexible interface. ISE integrates with the Meraki Dashboard by using ISE connector which is based on REST APIs (Representational State Transfer Application Programming Interfaces) for synchronization and automation of policy configurations.
The Cloud Campus Fabric solution integrates Cisco TrustSec and Adaptive Policy by supporting end-to-end group-based policy with Scalable Group Tags (SGTs). Scalable Group Tags are a metadata value that is transmitted in the header of fabric- encapsulated packets. While SGTs are administered by Cisco ISE through the tightly integrated REST APIs, Meraki Dashboard is used as the pane of glass to manage and create SGTs and define their policies. Policy management with identity services is enabled in Cloud Campus Fabric network using ISE integrated with Meraki Dashboard for dynamic mapping of users and devices to scalable groups. This simplifies end-to-end security policy management and enforcement at a greater scale than traditional network policy implementations relying on IP access-lists.
Note: For additional information about the ISE, please refer to the following ISE 3.2 documentation.
Cisco Catalyst 9k Platforms
Catalyst 9200
Cisco® Catalyst® 9200 Series switches extend the power of intent-based networking and Catalyst 9000 hardware and software innovation to a broader set of deployments. Catalyst 9200 Series switches provide security features that protect the integrity of the hardware as well as the software and all data that flows through the switch. It provides resiliency that keeps business up and running seamlessly. Combine that with open APIs of Cisco IOS XE® and programmability of the UADP ASIC technology, Catalyst 9200 Series ensures investment protection on future innovations.
With full PoE+ capability, power and fan redundancy, stacking bandwidth up to 160 Gbps, modular uplinks, Layer 3 feature support, and cold patching, Catalyst 9200 Series switches are the industry’s unparalleled solution with differentiated resiliency and progressive architecture for cost-effective branch-office access. Catalyst 9200 Series switches also provide operational choice of CLI, Cisco® Catalyst® Center (formerly Cisco DNA Center) on-premises management, or cloud monitoring for Catalyst on Meraki dashboard.
Catalyst 9300
Cisco® Catalyst® 9300 Series switches are Cisco’s lead stackable enterprise access switching platform and as part of the Catalyst 9000 family, are built to transform your network to handle a hybrid world where the workplace is anywhere, endpoints could be anything, and applications are hosted all over the place.
The Catalyst 9300 Series, including the new Catalyst 9300X models, continues to shape the future with continued innovation that helps you reimagine connections, reinforce security and redefine the experience for your hybrid workforce big and small. With Catalyst 9300 switches, you choose how you want to manage your network – on-premises, virtual or from the cloud.
Note: Catalyst 9300-M models are identical to 9300 series in hardware specifications. However, it ships with the Meraki persona (i.e. Meraki feature-set) preloaded for zero touch provisioning with the Meraki Dashboard. Please refer to documentation for further feature and software details. Test #1 wrapping
Catalyst 9500
The Cisco® Catalyst® 9500 Series switches including the Catalyst 9500X models, continues to shape the future with continued innovation that helps you reimagine connections, reinforce security and redefine the experience for your hybrid workforce big and small. Cisco® Catalyst® 9500 Series switches based on Cisco Unified Access Data Plane (UADP) Application-Specific Integrated Circuit (ASIC) are Cisco’s lead fixed enterprise core and aggregation switching platform and as part of the Catalyst 9000 family, are built to transform your network to handle a hybrid world where the workplace is anywhere, endpoints could be anything, and applications are hosted all over the place.
Cisco® Catalyst® 9500X switch based on Cisco Silicon One Q200 ASIC is purpose built for the next generation core with a programmable pipeline (P4) and is the first network silicon to offer switching capacity up to 12.8 Tbps full duplex in the enterprise. The Q200 ASIC offers high-performance along with full routing and switching capabilities without external memories. This is enabled by internal architecture that includes an on-chip High Bandwidth Memory (HBM). The Catalyst 9500X switch leverages a high- performance multiple core x86 CPU and is Cisco’s leading purpose-built fixed core and edge services enterprise switching platform, built for security, IoT, and cloud.
Cisco® Catalyst® 9500X switch is the industry’s first purpose-built fixed 10, 25, 50, 40, 100, 200 and 400 Gigabit Ethernet switch targeted for the enterprise campus. Catalyst 9500 Series switches provide operational choice of Cisco Catalyst Center, or Meraki cloud monitoring.
Catalyst Wireless 9100
Cisco® Catalyst® 9166/64/62 Wi-Fi 6E access points enable operation in the 6GHz band to produce a network that is more reliable and secure, with higher throughput, more capacity, and less device interference. Operational management is flexible because customers can change their network management whenever they want. If a network with Cisco Catalyst 9100 Series Access Points was originally an on-premises deployment, it can be changed to cloud-based management without the need to purchase and redistribute additional hardware, saving you money as you network your way.
With the industry’s leading on-premises network platform (Catalyst) joining the industry’s leading cloud IT platform (Meraki), these access points provide an unparalleled network experience. For organizations that need a wireless solution to deliver a reliable, flexible, and superior experience for your users, the Cisco® Catalyst® 9100 Series Access Points are the best choice.
Note: Catalyst 9100-M models are identical to 9100 series in hardware specifications. However, it ships with the Meraki persona (i.e. Meraki feature-set) preloaded for zero touch provisioning with the Meraki Dashboard. Please refer to documentation for further feature and software details.
Catalyst Wireless 9800
Cisco® Catalyst® 9800 Series Wireless Controllers are based on an open, programmable architecture with built-in security, streaming telemetry, and rich analytics. The controllers are always on, are secure, and can be deployed anywhere—three pillars of network excellence that strengthen the network by providing the best wireless experience without compromise, while saving time and money.
Always on
● High availability and seamless software updates, enabled by hot patching, keep your clients and services always on in planned and unplanned events.
● Bug fixes, access point deployment at multiple sites, network updates, and more can be handled without rebooting the controller or impacting the operation of the networks.
Secure
● Wireless infrastructure becomes the strongest first line of defense with Encrypted Traffic Analytics and Cisco Software-Defined Access.
● The controllers come with built-in security to secure the controller and the network: Secure Boot, runtime defenses, image signing, integrity verification, and hardware authenticity.
Flexible deployment
● Whether your deployment choice is an on-premises solution or a cloud deployment solution, the Cisco Catalyst 9800 Series Wireless Controllers allow for management and deployment of the controller anywhere
Whether your deployment choice is an on-premises solution or a cloud deployment solution, the Cisco Catalyst 9800 Series Wireless Controllers allow for management and deployment of the controller anywhere. The Cisco Catalyst 9800 Series Wireless Controllers support open and programmable APIs that enable flexible management and automation of your day-0 to day-N network operations. Model-driven streaming telemetry provides deep insights into your network and client health.
And when you manage your network with Cisco Catalyst Center, you can begin to take advantage of some truly cutting-edge Artificial Intelligence/Machine Learning features. Unfolding AI/ML over your wireless deployment, Cisco Catalyst Center provides your next step in terms of increased performance, better efficiency and greater cost savings. This allows for considerable network improvements in visibility, including troubleshooting and security. AI/ML turns data into intuition, resulting in time savings and greater efficiency.
Note: For additional information about Cisco Catalyst 9K series switches, please refer to the following datasheets: Catalyst 9200, Catalyst 9300, Catalyst 9300-M, Catalyst 9500, Catalyst Wireless 9162, 9164, 9166, Catalyst Wireless 9162-M, 9164-M, 9166-M and Catalyst Wireless 9800.
BGP EVPN VXLAN Fabric Architecture
For many years now, VLANs have been the de-facto method for providing network segmentation in campus networks. Standardized as IEEE 802.1Q, VLANs leverage traditional loop prevention techniques such as Spanning Tree Protocol which not only imposes restrictions on network design and resiliency, but it also results in an inefficient use of available network links due to the blocking of redundant paths, required to ensure a loop free network topology.
At its core, VXLAN provides benefits of elastic workload placement, higher scalability of Layer 2 segmentation, and connectivity extension across the Layer 3 network boundary. Multi-Protocol Border Gateway Protocol (MP-BGP) introduced new Network Layer Reachability Information (NLRI) to carry both Layer 2 MAC and Layer 3 IP information at the same time. By having the combined set of MAC and IP information available for forwarding decisions, optimized routing and switching within a network becomes feasible. The extension that allows BGP to transport Layer 2 MAC and Layer 3 IP information is called EVPN – Ethernet Virtual Private Network.
The advantages provided by BGP EVPN VXLAN are as follows:
Standard based
● Standard-based Overlay (VXLAN) with standard-based control plane (BGP)
Optimized Forwarding
● Layer 2 MAC and Layer 3 IP information distribution by control plane (BGP)
● Forwarding decision based on scalable control plane (minimizes flooding)
● Integrated Routing/Bridging (IRB) for Optimized Forwarding in the Overlay
Efficient Bandwidth Utilization
● Leverages Layer 3 ECMP – all links forwarding – in the underlay
Scalability
● Significantly larger namespace in the overlay (16M segments)
Roles and Terminology
A CLOS (a type of nonblocking, multistage switching network used today in large-scale switching fabrics) based Spine-Leaf architecture is used in the Programmable Fabric solution. The various components and their roles are described below:
Spine switch
● IP transport forwarder between Leaf switches (East-West).
● Potentially hosting Rendezvous-Point (RP) for the underlay.
● Potentially hosting BGP Route-Reflector (RR) for EVPN.
● Does not require the VTEP functionality.
● Interconnects leaf switches and border leaf switches.
Leaf switch (aka ToR or VTEP)
● VXLAN edge device to which end hosts are attached. The end hosts include virtual and physical/bare metal servers, FEX devices, 3rd party switches, UCS FI, controllers, and blade switches.
● Routes or bridges Classic Ethernet frames and encapsulates them into VXLAN.
● Requires the VTEP functionality.
Border Leaf/Spine switch
● VXLAN edge device for external connectivity.
● Routes and bridges Classical Ethernet frames from an outside network and encapsulate them into VXLAN (North-South).
● Decapsulate MPLS PE/LISP traffic from an outside network and re-encapsulates it into VXLAN (North-South).
● Speaks IGP/EGP routing protocols with the outside network (North-South).
● Requires the VTEP functionality.
● Interface options are physical routed ports, sub interfaces, and VLAN SVIs over trunk ports.
● IPv4/IPv6 route exchange with external neighbors.
Border Spine switch (additional functions unique to border spine)
● IP transport forwarder between Leaf switches (East-West).
● Potentially hosting Rendezvous-Point (RP) for the underlay.
● Potentially hosting BGP Route-Reflector (RR) for EVPN.
Note: Another role could potentially exist which is the Services Leaf switch – (This option does not need a dedicated pair of leaf switches and could be any combination of a leaf switch VTEP and a next-hop router) on which you can run the following services: Firewalls, Load balancers, Proxy services or IPS services.
IP Fabric Overlays (VXLAN)
An overlay network is a virtual network that is built over an existing Layer 2 or Layer 3 network by forming a static or dynamic tunnel that runs on top of the physical network infrastructure. The existing Layer 2 or Layer 3 network is what forms the underlay and is covered further below in this document.
When a data packet is sent through an overlay, the original packet or frame is packaged or encapsulated at a source edge device with an outer header and dispatched toward an appropriate destination edge device. The intermediate network devices forward the packet based on the outer header but are not aware of the data in the original packet. At the destination edge device, the packet is decapsulated by stripping off the overlay header and then forwarded based on the actual data within.
In the context of BGP EVPN VXLAN, VXLAN is used as the overlay technology to encapsulate the data packets and tunnel the traffic over a Layer 3 network. VXLAN creates a Layer 2 overlay network by using a MAC-in-UDP encapsulation. A VXLAN header is added to the original Layer 2 frame, and it is then placed within a UDP-IP packet. A VXLAN overlay network is also called as a VXLAN segment. Only host devices within the same VXLAN segment can communicate with each other.
Note: Each VXLAN segment is identified through a 24-bit segment ID, termed the VXLAN network identifier. This ensures that up to 16 million VXLAN segments can be present within the same administrative domain.
VXLAN is a MAC in IP/UDP overlay that allows layer 2 segments to be stretched across an IP core. All the benefits of layer 3 topologies are thereby available with VXLAN including the popular layer-3 ECMP feature for efficient traffic spread across multiple available paths. The encapsulation and decapsulation of VXLAN headers is handled by a functionality embedded in VXLAN Tunnel End Points (VTEPs).
VXLAN natively operates on a flood-n-learn mechanism where BU (Broadcast, Unknown Unicast) traffic in a given VXLAN network is sent over the IP core to every VTEP that has membership in that network. There are two ways to send such traffic: (1) Using IP multicast (2) Using Ingress Replication or Head-end Replication (HER). The receiving VTEPs will decapsulate the packet and based on the inner frame perform layer-2 MAC learning. The inner SMAC is learnt against the outer Source IP Address (SIP) corresponding to the source VTEP. In this way, reverse traffic can be unicasted toward the previously learnt end host. However, this poses a huge limitation since the broadcast domain spans a much larger boundary across an IP core where floods are translated to IP multicast (or HER). Consequently, the flood-n-learn based scheme presents serious scale challenges especially as the number of end hosts go up. This is addressed via learning using a control-plane for distribution of end host addresses. The control plane of choice is MP-BGP EVPN. Specifically, within BGP, the EVPN address family is employed to carry MAC and IP address information of the end hosts along with other information such as the network and tenant (aka VRF) to which they belong. This allows optimal forwarding of both layer-2 and layer-3 traffic within the fabric.
Fabric Control Plane (MP-BGP EVPN)
In a VXLAN-EVPN based fabric, MAC learning occurs via the control plane (MP-BGP) instead of the data plane. When a new end host is attached to a VTEP, the VTEP advertises the MAC and IP address of the end host to a route reflector which in turn advertises it to the other VTEPs through MP-BGP. Since MP-BGP enables isolation of groups of interacting agents, hosts that belong to the same tenant are logically isolated from other tenants.
There are many reasons and benefits for using MP-BGP EVPN as the control plane:
Reduce flooding
● Since the number of end hosts attached to VTEPs is huge, a mechanism is required to reduce flooding for discovery of end host location and resolution information. This is achieved via MAC/IP binding information distribution.
● MAC address distribution eliminates (or reduces) unknown unicast flooding because MAC addresses are prepopulated.
● MAC to IP binding information helps in local ARP suppression.
Distributed Anycast Gateway (DAG)
● For a given subnet, the same default gateway with the same IP and MAC address is realized simultaneously thereby ensuring the default gateway for the end hosts is always at its closest point aka its directly attached switch (in this case the leaf switch)
● This ensures that routed traffic is also optimally forwarded within the fabric without going through any hair-pinning.
Mobility support
● The control plane supports transparent mobility within and across BGP EVPN VXLAN fabrics, and quickly updates reachability information to avoid hair-pinning of east-west traffic.
● The distributed anycast gateway also aids in supporting transparent mobility since post its move, the ARP cache entry for the default gateway is still valid.
Secure VTEPs
● In a VXLAN-EVPN fabric, traffic is only accepted from VTEPs whose information is learnt via the BGP-EVPN control plane. Any VXLAN encapsulated traffic received from a VTEP that is not known via the control plane will be dropped. In this way, this presents a secure fabric where traffic will only be forwarded between VTEPs validated by the control plane. This is a major security hole in data-plane based VXLAN flood-n-learn environments where a rogue VTEP has the potential of bringing down the overlay network.
Note: An EVPN Instance (EVI) represents a Virtual Private Network (VPN) on a VTEP. It is the equivalent of IP VRF in Layer 3 VPN and is also known as a MAC VRF.
On the other hand, the benefits of using BGP as the routing protocol:
Increased flexibility
● EVPN address family carries both Layer-2 and Layer-3 reachability information. So, you can build bridged overlays or routed overlays. While bridged overlays are simpler to deploy, routed overlays are easier to scale out.
Increased security
● BGP authentication and security constructs provide more secure multi-tenancy.
Increased convergence time
● BGP being a hard-state protocol is inherently non-chatty and only provides updates when there is a change. This greatly improves convergence time when network failures occur.
BGP policies
● Rich BGP policy constructs provide policy-based export and import of reachability information. It is possible to constrain route updates where they are not needed thereby realizing a more scalable fabric.
Route reflectors
● Increases scalability and reduces the need for a full mesh (coverage) of BGP sessions.
● A route reflector in an MP-BGP EVPN control plane acts as a central point for BGP sessions between VTEPs. Instead of each VTEP peering with every other VTEP, the VTEPs peer with a spine device designated as a route reflector.
● For redundancy purposes, an additional route reflector is designated.
Unicast Underlay
The primary purpose of the underlay in the VXLAN EVPN fabric is to advertise the reachability of Virtual Tunnel End Points (VTEPs) and BGP peering addresses. The primary criterion for choosing an underlay protocol is fast convergence in the event of node failures.
From an underlay/overlay perspective, the packet flow from a host to another over the Virtual Extensible LAN (VXLAN) fabric comprises of these steps:
1) Host sends traffic to source VXLAN tunnel endpoint (VTEP)
Tech tip: Please note the difference between bridged and routed traffic; 1a) For bridged traffic in the same broadcast domain, the VTEP will have received the frame on the ingress port and look up the destination MAC. If the destination MAC is local to the VTEP, it will locally switch the frame as usual. If the destination MAC is connected to another VTEP, it derives the nexthop IP of that VTEP and the L2 VNI number. The far-end VTEP will use the L2 VNI number to determine which VLAN to bridge the frame in. 1b) For routed traffic sent to the default gateway, the VTEP will perform the routing lookup. If the destination host is local to the VTEP, it will route the frame as usual. If the destination host is connected to another VTEP, it derives the nexthop IP of that VTEP and the L3 VNI. The far end VTEP will use the L3 VNI number to determine which routing table to lookup the destination host in. (Far-end VRF) Test #1
2) The VTEP encapsulates the traffic (frames) into VXLAN packets (overlay function) and signals the underlay IP network
3) Based on the underlay routing protocol, the packet is sent from the source VTEP to destination VTEP through the IP network (underlay function)
4) The destination VTEP removes the VXLAN encapsulation (overlay function) and sends traffic to the intended destination.
The VTEPs are a part of the underlay network as well since VTEPs need to be reachable to each other to send VXLAN encapsulated traffic across the IP underlay network.
OSPF Underlay IP Network
An underlay network is the physical network over which the virtual overlay network is established. Once the overlay network is defined along with the data-plane encapsulation, a method of transport is required to move the data across the physical network underneath. This method of transport is typically an underlay transport network, or simply the underlay.
In BGP EVPN VXLAN, the underlay Layer 3 network transports the VXLAN-encapsulated packets between the source and destination VTEPs and provides reachability between them. The VXLAN overlay and the underlying IP network between the VTEPs are independent of each other.
There are several options for the Unicast routing and IP addressing options on the underlay network (e.g. OSPF, IS-IS, eBGP, etc.) OSPF is one of the most common options due to its simplicity and common use across different devices.
Planning and Preparation for Deployment
It is important to ensure proper network connectivity for all required services in this design (e.g. Meraki Management Tunnel) which might require attention to the configuration on the upstream and/or network edge devices. Micro-segmentation is achieved in this design by leveraging address-families in the MP-BGP protocol, ensuring that tenants in different segments are isolated in separate routing instances.
However, it is recommended to configure Scalable Group Tags (SGTs) and Security Group Tag Access lists (SGACLs) to manage the end-to-end network segmentation leveraging Cisco Identity Services Engine (ISE) and Adaptive Policy.
The following section explores the other main considerations for when planning for deployment.
Meraki Cloud Administration and Management
● If you don't have an account on the Meraki Dashboard, create one following these steps.
● An API Key will be required for onboarding Catalyst devices to your dashboard account. If you don’t have an API Key already, create one following these steps.
Note: API key must have full read/write access for the organization to which switches will be onboarded. Note indent Test #1
● Claim your order(s) or serial number(s) into your Meraki Dashboard account.
● Add your devices to existing networks or create new networks as required.
● Configure firmware upgrades for your network(s) with latest Stable or RC releases for each device type (Please check the firmware changelog for platform-specific details).
● Configure your network(s) with the correct time-zone from Network-wide > Configure > General (This is key for reporting and firmware upgrades).
● Configure your network(s) with the desired upgrade date and time.
● Ensure that only current administrators are added with the correct permissions on the Meraki dashboard (unless SAML is configured for Single Sign-on).
● If using Single sign-on integration with Meraki dashboard, please ensure that login to dashboard is scoped such that administrators have the correct level of access where applicable (e.g. Per network, Per switch port, etc.). For more information about dashboard access roles, please refer to the following article.
● In case of SAML SSO, it is still required to have one valid administrator account with full rights configured on the Meraki dashboard. However, it’s recommended to have at least two accounts to avoid being locked out from dashboard.
● Where applicable, ensure that the designated Management VLAN has access to DHCP (at least during initial bootup before assigning a static IP address) and also to the internet.
● Please ensure you have the required licenses (e.g. Advanced/Advantage for Adaptive Policy). For more information about license requirements, please refer to the following article.
Meraki Cloud Access
● Ensure that your Campus LAN has access to the internet for management purposes.
● Ensure that Meraki Cloud is accessible and that all required ports are opened where applicable (information can also be found in Dashboard under firewall info section).
● Ensure that there is sufficient bandwidth for firmware upgrades as they tend to be large in size.
Dashboard Administration for Wireless
● Ensure that your Campus LAN has access to the internet for management purposes.
● Configure the Wireless upgrade behavior as desired.
● By default, all management traffic is sourced by the Management IP address (Cloud, Radius/ISE, SNMP, Syslog) assigned to the access point. If there is a desire to configure an alternate Management Interfaces, please refer to this article and in this case ensure that this is reflected in your design (e.g. Cisco ISE).
Note: For further information about Dashboard administration for wireless, please refer to this MR – Wireless LAN section on Meraki Documentation.
Dashboard Administration for Switches
● Please note that all switches within the same network will use the same Management VLAN unless changed statically on a per switch bases.
● Ensure that the configured Management VLAN is applicable to all switches within the same dashboard network, otherwise change it per switch following these steps.
● By default, all management traffic is sourced by the Management IP address (Cloud, Radius, SNMP, Syslog) assigned to the switch. If there is a desire to configure an alternate Management Interfaces, please refer to this article and in this case ensure that this is reflected in your design (e.g. Cisco ISE).
Note: For further information about Dashboard administration for switches, please refer to this MS – Switches section on Meraki Documentation.
Cloud Monitoring for Catalyst Switches
● Please ensure that your Catalyst switch(es) is one of the supported platforms.
● Catalyst switch(es) must be running IOS XE 17.3 – 17.10.1 (Software can be downloaded from here, and please refer to this article for IOS XE image upgrade).
● All switches must be running a valid Cisco DNA Software subscription.
Note: Dashboard Client traffic analytics powered IOS XE AVC is available only with a Cisco DNA Advantage license. For more information about DNA Software license upgrade, please refer to this FAQ article.
● The management interface is not supported for onboarding Catalyst switches.
● At least one SVI needs to be configured with access to the internet on TCP port 443.
● A valid DNS server must be configured on your switch(es), and DNS lookup must be enabled.
● NTP must be enabled on your switch(es).
● AAA must be configured with aaa new-model
● SSH access must be enabled for the onboarding process. The account used must have privilege-15 level.
● Telnet is required for connectivity pre-checks.
● The switch(es) must have 4 unused consecutive VTY slots.
● If you are using the onboarding app, then please ensure that the environment used to run the app has access to the internet on TCP port 443.
● Make sure you backup your switch(es) configuration before onboarding them to Cloud Monitoring.
Note: For further information about onboarding Catalyst Switches for Cloud Monitoring, please refer to this article.
Cloud Monitoring for Catalyst Wireless
● Please ensure that Catalyst Wireless LAN Controller and Access Point(s) is one of the supported platforms.
● It is recommended to run IOS XE 17.15.1 or higher on the Wireless LAN Controller.
● AAA must be configured with aaa new-model
● The Wireless LAN Controller account used in Dashboard must have privilege-15 level.
● The Wireless LAN Controller must have 4 unused consecutive VTY slots.
● One of the supported SSH algorithms must be configured on the Wireless LAN Controller
● Access points require a Cisco DNA Essentials or Advantage license.
● Please pay attention to the restrictions for onboarding Catalyst Wireless (e.g. Mixing MR and un-managed CW access points in the same Dashboard network is not supported).
● Catalyst 9800 wireless controllers license level addon enabled for DNA Essentials or Advantage. Dashboard Client traffic analytics powered IOS XE AVC is available only with a Cisco DNA Advantage license.
Note: Dashboard Client traffic analytics powered IOS XE AVC is available only with a Cisco DNA Advantage license. For more information about DNA Software license upgrade, please refer to this FAQ article.
Note: Claiming Wireless LAN Controllers in Dashboard organizations running Per-Device licensing is not supported.
● Please ensure that Wireless LAN Controller is running up to the maximum number of supported access points for Cloud Monitoring.
● Please ensure that the Wireless LAN Controller has access to the Cloud. Please refer to this article for further information.
● It is recommended for Meraki Tunnel traffic to be exempt from TLS/SSL traffic inspection in order to avoid potential connectivity issues.
Note: For further information about onboarding Catalyst Wireless for Cloud Monitoring, please refer to this article.
Cloud Management for Catalyst Switches
● Several Catalyst 9300 platforms can be migrated to Meraki management mode.
● When migrating Catalyst 9300 platforms to Meraki management mode, please ensure you take a backup of all device files as they will be wiped during the migration process.
Note: Catalyst 9300-M, 9300L-M and 9300X-M platforms do not need to be migrated as they are pre-shipped with Meraki management mode.
Note: For further information about migrating Catalyst 9300 platforms for Cloud Management, please refer to this article.
Cisco Identity Services Engine (ISE)
● Cisco ISE and cloud-based Cisco Meraki are TrustSec-enabled systems that are policy administration points for TrustSec policies. If you use both Cisco and Meraki network devices, you can connect one or more Cisco Meraki dashboards to Cisco ISE to replicate TrustSec policies and elements from Cisco ISE to the Cisco Meraki networks belonging to each organization.
● The TrustSec Integration for Cisco Meraki is an on-premises service that runs on the primary PAN. If a failover occurs, the integration service continues to function on the newly promoted primary PAN.
● You can only choose the TrustSec policies that conform to the supported formats for Meraki Adaptive Policies.
● The TrustSec Integration for Cisco Meraki does not delete any policies or policy elements in Cisco Meraki. When you delete a policy or policy element in Cisco ISE, you must delete them in Cisco Meraki as well.
● If using an external Radius server (e.g. Cisco ISE), then ensure that the network segment where ISE is hosted can access the Management VLAN configured on your network devices (or the Alternate Management Interface on switches and/or access points if configured and where applicable).
● Ensure that all required ports are opened where applicable (e.g. 1812, 1813, etc.).
Note: For further information about deploying ISE, please refer to this Performance and Scalability guide, Installation guide and Deployment guide.
Note: When you connect Cisco ISE and a Cisco Meraki dashboard, if the two systems have different TrustSec policies that are configured for the same source and destination, the Cisco ISE TrustSec policy replaces the TrustSec policy in Cisco Meraki. Also please note that Cisco Meraki Policies can’t be transferred to Cisco ISE.
Note: For syncing policies from Cisco ISE to Dashboard, please ensure that you have the Cisco ISE Advantage license.
Underlay
● Running IGP (e.g. OSPF) for Unicast Routing between the VTEPs.
● Use interface type point-to-point with OSPF.
● When deploying Multicast, ensure that the protocol is consistent across all switches (PIM-SM vs PIM-Bidir).
● Spine switches can potentially host RP (Rendezvous Point) for the underlay with MSDP.
● To improve the convergence experience in the RP failure scenario, the recommendation is to deploy Anycast RP, which consists of using a common IP address on different devices to identify the RP.
● Simple static RP mapping configuration is then applied to each node in the Fabric to associate multicast groups to the RP, so that each source or receiver can then utilize the local RP that is the closest from a topological point of view.
● Configuring ARP suppression can remove the need to flood ARP requests across the Fabric, which usually represents the large majority of L2 broadcast traffic.
Overlay
● Spine switches should be stacked were applicable.
● Spine switches can potentially host RR (Route Reflector) for the EVPN.
● Rationalize the number of VRFs by collapsing them where applicable for easier troubleshooting.
● Each Leaf switch should be multi-homed (i.e. connected to each Spine switch).
● Border Leaf switches running EGP routing protocol (e.g. eBGP).
● For IP Transport devices, their OS software needs to support MP-BGP EVPN.
● For VTEP devices, the switch needs to support both the control-plane and data-plane functions.
Access Layer
● Stacking Cloud Managed Access Switches (where applicable) could be beneficial in many situations. Please ensure you follow the correct steps for bringing the stack online. Further details can be found here.
● In case of stacking Cloud Managed Access Switches, please ensure that same management IP address is configured on all stack members. This can be done in Dashboard or via the local status page.
Tech tip: If required, IP addressing can be changed to different settings (e.g. Static IP address or a different management VLAN) on all stack members after the stack has been properly configured and is showing online on dashboard. Again, it is recommended to configure the same IP address on all switches to ensure that traffic uses the same IP during failover scenarios. For best practices on changing Cloud Managed switches IP addresses, please refer to this article. Test #1 and #4
● Cloud Managed devices (e.g. Switches, Access Points) will by default search for a DHCP server in VLAN 1 unless changed.
Tech tip: Even if it is undesirable to use Native VLAN 1, it is recommended to use it for provisioning the switches for ZTP purposes. Once the switches/stacks are online on dashboard and running steady, you can then change the Management VLAN as required. Remember to change port settings downstream first to avoid losing access to switches. For more information about best practices, please refer to this article.
● In case of a layer-2 Access Layer, please ensure STP interoperability across all switches and STP domain.
Note: For further information about STP interoperability across Cisco switches (e.g. Cloud Managed and Cloud Monitored), please refer to the STP in Cloud Campus section in this article. It is recommended to run MST (802.1s) instance 0 / region 1 / revision 1 between Cloud Managed and Cloud Monitored Switches. Test #1 and #4
● All Cloud Managed Switch ports have the following default configuration: Trunk (802.1Q encapsulation, Native VLAN 1, MST enabled and will send management traffic to the cloud in VLAN 1 untagged)
Downlinks to Access Switches
● Leaf switch downlinks to access switches should be configured as Trunk.
● Allowing all VLANs on the Trunk port can simplify the design and will also simplify adding new services (e.g. VLANs) in the future. It is worth noting that sometimes it is required to prune un-used VLANs and only allow specific ranges on Trunk ports as this can be considered more secure. However, deploying Adaptive Policy eliminates this risk. Nonetheless, pruning VLANs on Trunk ports can also help reduce broadcast propagation.
● Configure a native VLAN where Cloud Managed devices (e.g. Switches, Access Points) can find a DHCP server.
● Please note that Cloud Managed devices (e.g. Switches, Access Points) will by default search for a DHCP server in VLAN 1 for zero touch provisioning purposes unless changed.
● For Cloud Managed Switches; If using an Alternate Management Interface, please ensure that this VLAN is enabled as well on the Trunk port.
● In a STP domain, downlinks to Access Switches must be configured with STP Root Guard.
● Where applicable, configure EtherChannels between Leaf switch and the access switch. Please ensure that the encapsulation is matched on both sides.
Note: Cloud Managed switches support LACP standard. For more information, please refer to this article.
Tech tip: In a Cloud Campus Fabric deployment, micro-segmentation is maintained using TrustSec and Adaptive Policy. As such, it eliminates the requirement to prune VLANs on the downlinks for security purposes. Allowing all VLANs (unless reserved) could facilitate adding new services in the future (e.g. new SSIDs)
Downlinks to Access Points
● Leaf switch downlinks to access points should be configured as Trunk.
● Access switch downlinks to access point should also be configured as Trunk.
● Allowing all VLANs on the Trunk port can simplify the design and will also simplify adding new services (e.g. SSIDs) in the future. It is worth noting that sometimes it is required to prune un-used VLANs and only allow specific ranges on Trunk ports as this can be considered more secure. However, deploying Adaptive Policy eliminates this risk. Nonetheless, pruning VLANs on Trunk ports can also help reduce broadcast propagation.
● For Cloud Managed Access Points; If using an Alternate Management Interface, please ensure that this VLAN is enabled as well on the Trunk port.
● Configure a native VLAN where Cloud Managed devices (e.g. Switches, Access Points) can find a DHCP server.
● Please note that Cloud Managed devices (e.g. Switches, Access Points) will by default search for a DHCP server in VLAN 1 for zero touch provisioning purposes.
Tech tip: Even if it is undesirable to use Native VLAN 1, it is recommended to use it for provisioning the switches for ZTP purposes. Once the switches/stacks are online on dashboard and running steady, you can then change the Management VLAN as required. Remember to change port settings downstream first to avoid losing access to switches. For more information about best practices, please refer to this article.
Cloud Campus Fabric with BGP EVPN VXLAN Design
Managing the enterprise campus in the Cloud offers several benefits to organizations that are looking for operational efficiency and speed of deployment. It helps organizations to streamline their network operations, improve the speed of deploying new services and enhance the network performance leveraging AI/ML in a scalable cloud-based platform. The proposed design and solution in this document is based on the Cloud Management and Monitoring for Catalyst aspects for Wired and Wireless LAN.
Note: For more information about Cloud Management and Monitoring for Catalyst, please refer to this article and this FAQ document.
The following sections highlights details related to the topology, hardware, software, and design selections that were made as part of the Cloud Campus Fabric with BGP EVPN VXLAN.
Use Cases
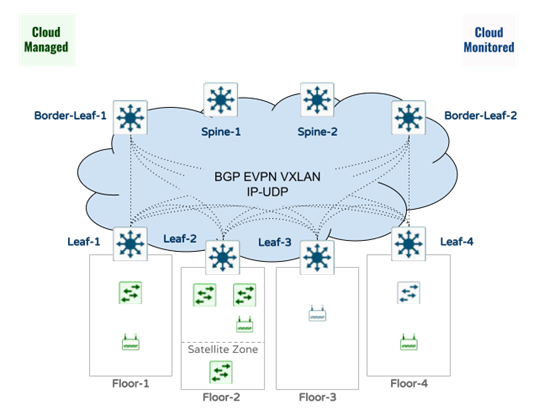
The proposed solution enables customers to run their Campus Fabric in the cloud in Management and monitoring modes. The access layer hanging off the leaf switches provides wired connectivity for the end users as well as connectivity to the wireless access points. To simplify the ongoing management of the fabric, the downlinks to the access layer will be configured as Trunk with all VLANs allowed. This will facilitate future expansions such as adding new SSIDs and/or VLANs. For the purposes of this document, the following use cases have been suggested. Please note that for illustration purposes, each floor is mapped to a unique use case.
Table 1. Network Segments and Design Use Cases
| Segment |
Requirements |
Use Case |
Management |
| Floor-1 |
● High performance wireless access
● Wired connectivity for user workstations
● Adequate PoE for WiFi6/6E applications
● Cloud Management
|
Cloud Managed Access |
Meraki Dashboard (Full Management) |
| Floor-2 |
● High performance wireless access
● Wired connectivity for user workstations
● Adequate PoE for WiFi6/6E and IoT applications
● Extension to remote services (e.g. IoT) – (1) See Note below
|
Cloud Managed Access with a remote/satellite zone (e.g. IoT applications) |
Meraki Dashboard (Full Management) |
| Floor-3 |
● High performance wireless access
● Direct attach to Fabric
● Cloud Monitoring
|
Cloud Monitored Access with Wireless LAN Controller(s) |
Meraki Dashboard (Monitor only) |
| Floor-4 |
● High performance wireless access
● Wired connectivity for user workstations
● Adequate PoE for WiFi6/6E applications
● Cloud Management
|
Cloud Managed Access |
Meraki Dashboard (Full Management) |
Note: (1) Shown as “Satellite Zone” in the below diagram
Please refer to the below for the VXLAN overlay and the design use cases.
Overlay and IP segments
The following diagram illustrates the mapping between IP segments and VRFs in the Overlay.
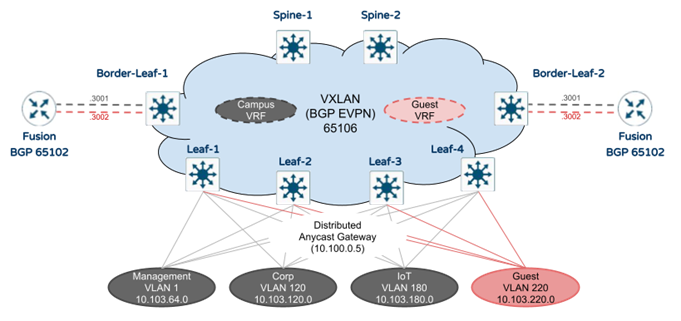
Note: In the above diagram, Overlay Handoffs are using BGP address-family IPv4 VRF to external routers (Fusion Routers) to maintain the segmentation between Campus and Guest. This is not necessarily part of the Campus Fabric design. Please design your Overlay Handoffs based on your own requirements.
Note: The Distributed Anycast Gateway shown in the above diagram will be created on the leaf switches on a per VLAN bases which is not shown in the above diagram.
The following table summarizes the VLANs and their VXLAN mappings used in this design.
Table 2. VLANs and L2/L3 VNI Mappings
| VLAN ID |
Name |
Subnet |
Default Anycast Gateway |
L2 VNI Mapping |
L3 VNI Mapping |
VRF |
| 1 |
Management |
10.103.64.0/24 |
MAC address = 0000.0000.0001 IP address = 10.103.64.1 Helper address = 10.100.0.5 |
200001 |
303001 |
Campus |
| 120 |
Corporate |
10.103.120.0/24 |
MAC address = 0000.0000.0120 IP address = 10.103.120.1 Helper address = 10.100.0.5 |
200120 |
303001 |
Campus |
| 180 |
IoT |
10.103.180.0/24 |
MAC address = 0000.0000.0180 IP address = 10.103.180.1 Helper address = 10.100.0.5 |
200180 |
303001 |
Campus |
| 220 |
Guest |
10.103.220.0/24 |
MAC address = 0000.0000.0220 IP address = 10.103.220.1 Helper address = 10.100.0.5 |
200220 |
303002 |
Guest |
Note: The Default Anycast Gateway (DAG) will be configured on leaf switches for the above mentioned VLANs with a helper address of 10.100.0.5 and option 82.
Schema and Numbering Conventions
It is vital to have consistency when configuring the Campus Fabric and avoid overlapping where possible. This will help simplify the implementation and improve the operational efficiency since troubleshooting can be much easier. The following table outlines the proposed scheme and numbering conventions for the designs proposed within this document.
Table 3. Schema and Numbering Conventions for Cloud Campus Fabric
| Item |
Structure |
Notes |
| LoopBack0 |
10.103.255.x |
.1 & .2 reserved for Spine Switches .3 & .4 reserved for Border Leaf Switches .11 onwards reserved for Leaf Switches |
| Underlay |
10.103.224.x |
/30 subnet for each interconnect |
| Sub-interfaces |
.x |
.10 for trunks .x for overlay |
| L2VNI |
20XXXX |
XXXX = VLAN Identifier |
| L3VNI |
30XXXX |
XXXX = VLAN Identifier |
| Route Distinguisher (RD) |
XXXXX:YY
OR
XXXXX:2YY |
XXXXX = BGP AS# YY = Last octet of Loopback0 (e.g. 65106:11 for Campus on Leaf-01)
XXXXX = BGP AS# YY = Last octet of Loopback0 (e.g. 65106:212 for Guest on Leaf-02) |
| Route Targets (RT) |
XXXX:Y |
XXXXX = BGP AS# Y = 1 for Campus, 2 for Guest |
| Hard Coded MAC address |
0000.0000.XXXX |
XXXX = VLAN Identifier |
Note: The schema and numbering conventions mentioned in the above table are for illustration purposes only and to ensure consistency. Please plan your schemas according to your own requirements.
EVPN Control Plane
iBGP is the most common routing protocol deployed for the EVPN control plane in VXLAN Fabrics. With iBGP, there is a requirement to have a full mesh between all iBGP speakers. To help scale and simplify the iBGP configuration, it is recommended to implement iBGP Route Reflectors (RR). The placement of the iBGP route reflectors is recommended to be implemented on the spines as they are central to all leaf switches. In this case, two of the spines will have BGP route reflector configured, and all leaf switches will be configured as the BGP route reflector clients. The route reflector will reflect EVPN routes for the VTEP leaf switches. Please refer to the following diagram for iBGP peering.
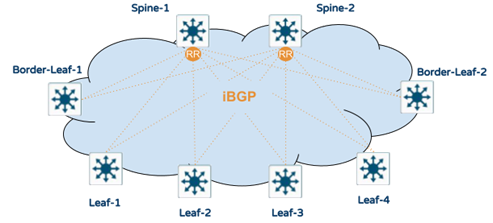
Note: Spines do not peer with each other.
Underlay
There are several options for the Unicast routing and IP addressing options on the underlay network (e.g. OSPF, IS-IS, eBGP, etc.) however for the purposes for this document, it will be referred to OSPF as the routing protocol on the underlay.
OSPF is a link-state routing protocol commonly used in enterprise environments. The OSPF default interface type used for Ethernet interfaces is “Broadcast,” which inherently results in a Designated Router (DR) and/or Backup Designated Router (BDR) election thus reducing routing update traffic. While this is fine in a Multi-Access network (such as a shared Ethernet segment), it is unnecessary in a point-to-point network. In a point-to-point network, the “Broadcast” interface type of OSPF adds a DR/BDR election process and an additional Type 2 Link State Advertisement (LSA). This results in unnecessary additional overhead, which can be avoided by changing the interface type to “point-to-point”. In this way, the DR/BDR election process can be avoided, reducing the amount of time to bring up the OSPF adjacency between the leaf and spine switches. In addition, with the point-to-point interface mode, the need for Type-2 LSAs is removed with only Type-1 LSA needed since there is no Multi-Access (or Broadcast) segment present. As a result, the OSPF LSA database remains lean.
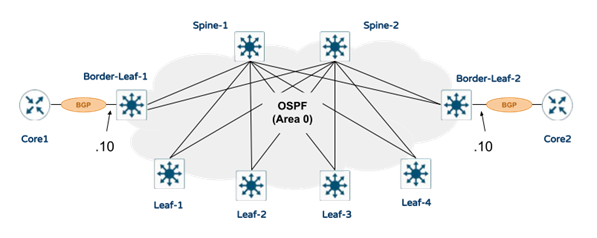
Note: In the above diagram, Underlay Handoffs are using BGP address-family ipv4 to external routers (Core Routers). This is not necessarily part of the Campus Fabric design. Please design your Underlay Handoffs based on your own requirements.
Topology and Design
The proposed topology and design incorporate the previously mentioned use cases and design concepts. As a reference to the below diagram (Cloud Campus with BGP EVPN VXLAN Topology) please refer to the following:
● Device list: Table 4
● Interface mapping: Table 5
● Device Interface and IP addressing: Table 6
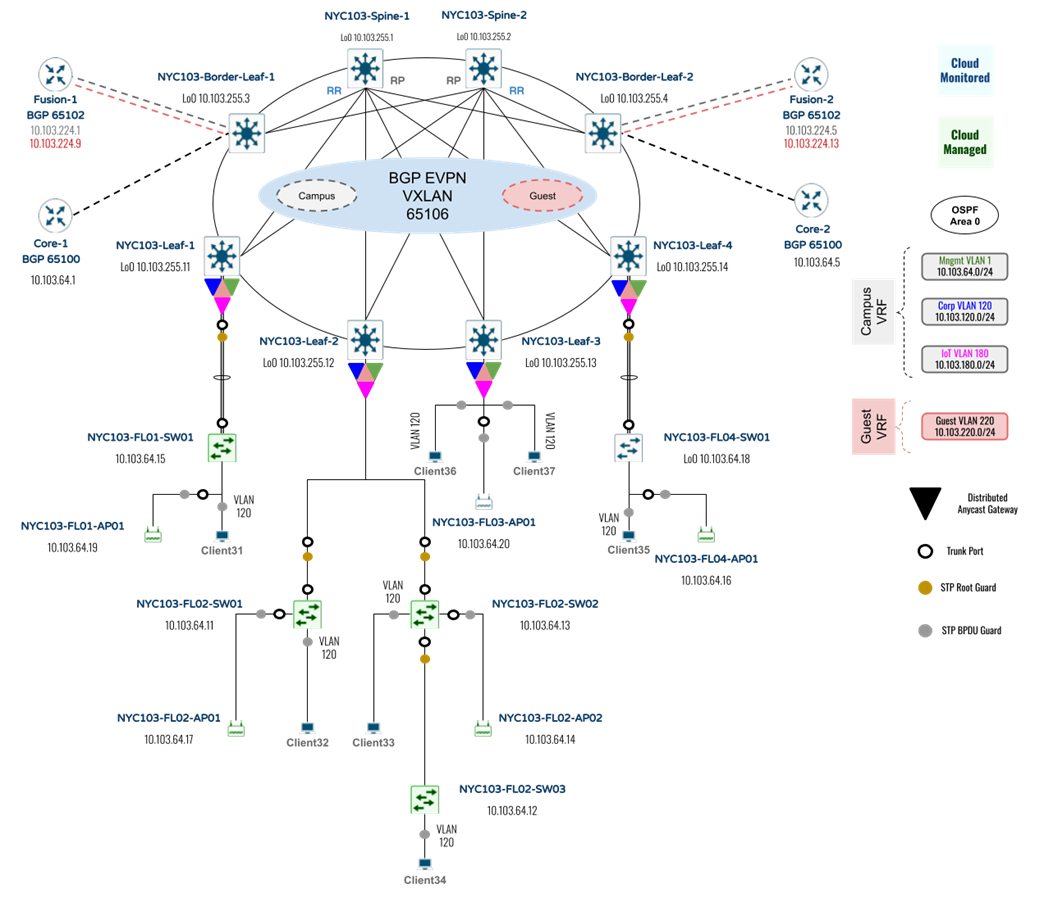
Table 4. List of Devices and Roles
| Role |
Requirements |
Hardware Platforms |
Management |
| Spine |
● Redundancy (Hardware, uplinks, downlinks)
● High-capacity connections (uplinks, downlinks)
● High-performance switching and processing power
● IP transport forwarder between Leaf switches (East-West)
● BGP Route-Reflector for the underlay
● Interconnects leaf switches and border leaf switches
|
C9500-24Y4C |
Meraki Dashboard (Monitor only) |
| Border Leaf |
● Redundancy (Hardware, uplinks, downlinks)
● High-capacity connections (uplinks, downlinks)
● Scalable tunnel endpoints
● Routing and bridging between external network and VXLAN (North-South)
● IGP/EGP with external network
● VXLAN tunnel endpoint (VTEP) functionality
|
9300-48P |
Meraki Dashboard (Monitor only) |
| Leaf |
● Develop UPS strategy considering the desired runtime for the various IT and OT PoE powered endpoints versus the cost, size, and weight of the battery backup solution
● VXLAN edge to access layer
● Routing or bridging between access layer and VXLAN
● VXLAN tunnel endpoint (VTEP) functionality
|
9300-48P |
Meraki Dashboard (Monitor only) |
| Access (Wired) |
● Physical stacking (desirable)
● High-capacity uplinks
● mGig access ports
● Adequate power over ethernet (PoE+, UPoE, UPoE+)
● Cloud management
|
9300-24P-M 9300-24UX-M |
Meraki Dashboard (Full Management) |
| Access (Wireless - 1) |
● High performance wireless (6, 6E)
● mGig uplink(s)
● Cloud management
|
9162-M 9164-M 9166-M |
Meraki Dashboard (Full Management) |
| Access (Wireless – 2) |
● High performance wireless (6, 6E)
● mGig uplink(s)
● Cloud monitoring
|
9166 |
Meraki Dashboard (Monitor only) |
| Other/Optional |
Cascaded access switch |
9300-24P-M |
Meraki Dashboard (Full Management) |
| Wireless LAN Controller (3) (Optional) |
C9800-L-C-K9 |
Meraki Dashboard (Monitor only) |
Note: (1) Cloud Managed Catalyst Wireless (2) Cloud Monitored Catalyst Wireless (3) WLC is not shown on the above topology
And please refer to the following table for the physical connectivity as a reference for this design.
Table 5. Device Interface Mapping
| Device |
Interface |
Remote Device |
Remove Interface |
| NYC103-Spine-1 |
Hu1/0/25 Hu1/0/26 Tw1/0/1 Tw1/0/2 Tw1/0/3 Tw1/0/4 Hu1/0/28 |
NYC103-Border-Leaf-1 NYC103-Border-Leaf-2 NYC103-Leaf-1 NYC103-Leaf-2 NYC103-Leaf-3 NYC103-Leaf-4 NYC103-Spine-2 |
Fo1/1/1 Fo1/1/1 Tw1/1/1 G1/0/1 G1/0/1 Tw1/1/1 Hu1/0/28 |
| NYC103-Spine-2 |
Hu1/0/25 Hu1/0/26 Tw1/0/1 Tw1/0/2 Tw1/0/3 Tw1/0/4 Hu1/0/28 |
NYC103-Border-Leaf-1 NYC103-Border-Leaf-2 NYC103-Leaf-1 NYC103-Leaf-2 NYC103-Leaf-3 NYC103-Leaf-4 NYC103-Spine-2 |
Fo1/1/2 Fo1/1/2 Tw1/1/2 G1/0/2 G1/0/2 Tw1/1/2 Hu1/0/28 |
| NYC103-Border-Leaf-1 |
Fo1/1/1 Fo1/1/2 G1/0/1 G1/0/2 |
NYC103-Spine-1 NYC103-Spine-2 Core-01 Fusion-01 |
Hu1/0/25 Hu1/0/25 Te1/0/14 Te1/0/4 |
| NYC103-Border-Leaf-2 |
Fo1/1/1 Fo1/1/2 G1/0/1 G1/0/2 |
NYC103-Spine-1 NYC103-Spine-2 Core-02 Fusion-02 |
Hu1/0/26 Hu1/0/26 Te1/0/14 Te1/0/4 |
| NYC103-Leaf-1 |
Tw1/1/1 Tw1/1/2 G1/0/47 & 48 (EtherChannel) |
NYC103-Spine-1 NYC103-Spine-2 NYC103-FL01-SW01 |
Tw1/0/1 Tw/1/0/1 G1/0/23 & 24 (EtherChannel) |
| NYC103-Leaf-2 |
G1/0/1 G1/0/2 G1/0/48 G1/0/47 |
NYC103-Spine-1 NYC103-Spine-2 NYC103-FL02-SW01 NYC103-FL02-SW02 |
Tw1/0/2 Tw/1/0/2 G1/0/24 G1/0/24 |
| NYC103-Leaf-3 |
G1/0/1 G1/0/2 G1/0/48 G1/0/12 G1/0/13 |
NYC103-Spine-1 NYC103-Spine-2 NYC103-FL03-AP01 Client36 Client37 |
Tw1/0/3 Tw/1/0/3 Uplink |
| NYC103-Leaf-4 |
Tw1/1/1 Tw1/1/2 G1/0/47 & 48 (EtherChannel) |
NYC103-Spine-1 NYC103-Spine-2 NYC103-FL04-SW01 |
Tw1/0/4 Tw/1/0/4 G1/0/23 & 24 (EtherChannel |
| NYC103-FL01-SW01 |
1 12 23 & 24 (EtherChannel) |
NYC103-FL02-AP01 Client31 NYC103-Leaf-1 |
Uplink
G1/0/47 & 48 (EtherChannel) |
| NYC103-FL02-SW01 |
1 12 24 |
NYC103-FL02-AP01 Client32 NYC103-Leaf-2 |
Uplink
G1/0/48 |
| NYC103-FL02-SW02 |
1 12 23 24 |
NYC103-FL02-AP02 Client33 NYC103-Leaf-2 NYC103-FL02-SW03 |
Uplink
G1/0/47 24 |
| NYC103-FL02-SW03 |
12 24 |
Client34 NYC103-FL02-SW02 |
24 |
| NYC103-FL04-SW01 |
1 12 23 & 24 (EtherChannel) |
NYC103-FL04-AP01 Client35 NYC103-Leaf-4 |
Uplink
G1/0/47 & 48 (EtherChannel) |
Note: The above physical connectivity and interface mapping is for illustration purposes only. Please design your physical layout and connectivity based on your requirements and use case(s).
And please refer to the following table for a list of IP addresses assigned to the devices.
Table 6. Device Interface and IP Addressing
| Device |
Interface |
IP Address |
Subnet Mask |
| NYC103-Spine-1 |
Loopback0 Loopback1 Loopback2 Hu1/0/25 Hu1/0/26 Tw1/0/1 Tw1/0/2 Tw1/0/3 Tw1/0/4 Hu1/0/28 |
10.103.255.1 10.103.254.1 10.103.255.255 10.103.224.9 10.103.224.21 10.103.224.29 10.103.224.37 10.103.224.45 10.103.224.53 10.103.224.17 |
255.255.255.255 255.255.255.255 255.255.255.255 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 |
| NYC103-Spine-2 |
Loopback0 Loopback1 Loopback2 Hu1/0/25 Hu1/0/26 Tw1/0/1 Tw1/0/2 Tw1/0/3 Tw1/0/4 Hu1/0/28 |
10.103.255.2 10.103.254.2 10.103.255.255 10.103.224.25 10.103.224.13 10.103.224.33 10.103.224.41 10.103.224.49 10.103.224.57 10.103.224.18 |
255.255.255.255 255.255.255.255 255.255.255.255 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 |
| NY103-Leaf-1 |
LoopBack0 Tw1/1/1 Tw1/1/2 |
10.103.255.11 10.103.224.30 10.103.224.34 |
255.255.255.255 255.255.255.252 255.255.255.252 |
| NYC103-Leaf2 |
LoopBack0 G1/0/1 G1/0/2 |
10.103.255.12 10.103.224.38 10.103.224.42 |
255.255.255.255 255.255.255.252 255.255.255.252 |
| NYC103-Leaf3 |
LoopBack0 G1/0/1 G1/0/2 |
10.103.255.13 10.103.224.46 10.103.224.50 |
255.255.255.255 255.255.255.252 255.255.255.252 |
| NYC103-Leaf4 |
LoopBack0 Tw1/1/1 Tw1/1/2 |
10.103.255.14 10.103.224.54 10.103.224.58 |
255.255.255.255 255.255.255.252 255.255.255.252 |
| NYC103-Border-Leaf-1 |
LoopBack0 Fo1/1/1 Fo1/1/2 G1/0/1.10 G1/0/2.3001 G1/0/2.3002 |
10.103.255.3 10.103.224.10 10.103.224.26 10.103.224.2 10.103.64.2 10.103.64.10 |
255.255.255.255 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 |
| NYC103-Border-Leaf-2 |
LoopBack0 Fo1/1/1 Fo1/1/2 G1/0/1.10 G1/0/2.3001 G1/0/2.3002 |
10.103.255.4 10.103.224.22 10.103.224.14 10.103.224.6 10.103.64.6 10.103.64.14 |
255.255.255.255 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 |
| NYC103-FL01-SW01 |
Port 23 & Port 24 |
10.103.64.15 |
255.255.255.0 |
| NYC103-FL02-SW01 |
Port 24 |
10.103.64.11 |
255.255.255.0 |
| NYC103-FL02-SW02 |
Port 23 |
10.103.64.13 |
255.255.255.0 |
| NYC103-FL02-SW03 |
Port 24 |
10.103.64.12 |
255.255.255.0 |
| Core-1 |
Te1/0/4.10 |
10.103.64.1 |
255.255.255.255 |
| Core-2 |
Te1/0/4.10 |
10.103.64.5 |
255.255.255.255 |
| Fusion-1 |
Te1/0/14.3001 Te1/0/14.3002 |
10.103.224.1 10.103.224.9 |
255.255.255.252 255.255.255.252 |
| Fusion-2 |
Te1/0/14.3001 Te1/0/14.3001 |
10.103.224.5 10.103.224.13 |
255.255.255.252 255.255.255.252 |
From a routing perspective, please refer to the following diagram for further details on the different routing domains on the underlay and overlay.
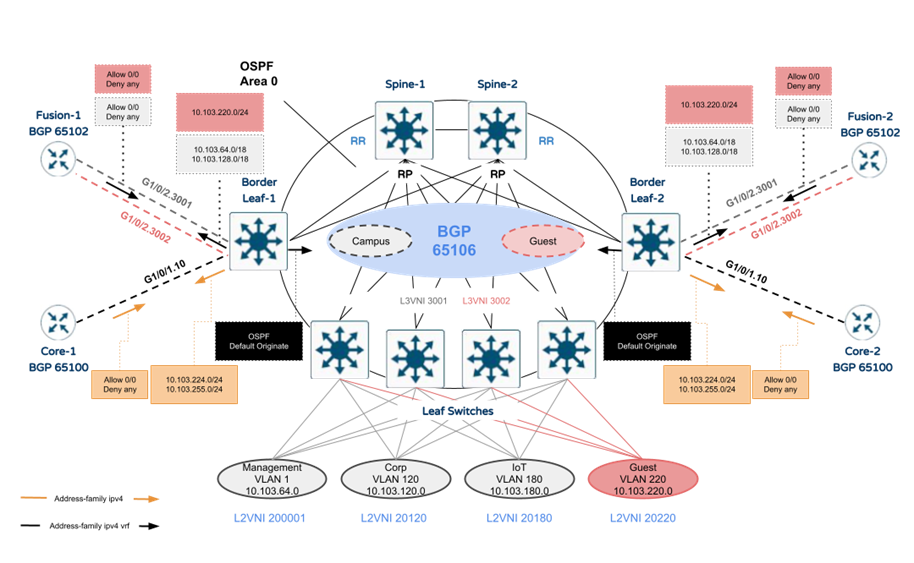
Note: In many situations, the external network roles (e.g. Fusion, Core) would be collapsed into a single device and in some occasions this could be handed over using static/default routes rather than BGP. Please design your Overlay/Underlay handoffs based on your own requirements.
Special considerations
● Border Leaf switches will only advertise a BGP aggregate for all interconnects (10.103.224.0/24) and Loopback0 (10.103.255.0/24) to external Core BGP neighbors.
● Border Leaf switches will only advertise a BGP aggregate for all Campus ranges (10.103.64.0/24, 10.103.120.0/24) and Guest ranges (10.103.220.0/24) to external Fusion BGP neighbors in separate IPv4 VRF address-families.
● Boarder Leaf switches will only receive a default route from external Fusion BGP neighbors received in separate IPv4 VRF address-families.
● Border Leaf switches will only inject a default route into OSPF which is redistributed from BGP 65100 (received in IPv4 address-family).
● All underlay interconnects are in OSPF area 0.
● All OSPF interfaces are configured as point-to-point.
Deploying Cloud Campus Fabric with BGP EVPN VXLAN
Prerequisites
It is important to ensure proper network connectivity for all required services in this design (e.g. Meraki Management Tunnel) which might require attention to the configuration on the upstream and/or network edge devices. Micro-segmentation is achieved in this design by leveraging address-families in the MP-BGP protocol, ensuring that tenants in different segments are isolated in separate routing instances.
Please ensure the following has been completed before proceeding with the deployment of Cloud Campus Fabric with BGP EVPN VXLAN:
● Meraki Dashboard Account and API Access (Full org access is required).
Note: Please ensure that the Dashboard Organization has API access before generating an API key for your profile in Dashboard.
● Network access for Meraki Cloud (Ensure these ports are open for all Cloud Managed devices).
● For Cloud Monitored Switches, please ensure connectivity to one of the TLS gateways on port TCP 443
● For Cloud Monitored Wireless, please ensure connectivity to one of the TLS gateways on port TCP 443.
● For Cloud Monitored Switches, please ensure you’re running IOS XE 17.3.1 – 17.9.4.
● For Cloud Monitored Wireless LAN Controllers, please ensure you’re running IOS XE 17.12.3 or 17.15.1 and later.
● Verify that Cloud Monitored Switches are a supported platform.
● Verify that Cloud Monitored Wireless devices are a supported platform.
Implementation Sequence
Please note that that there are several options such as manual CLI, CLI-macros, Ansible playbooks, Catalyst Center and other options for Fabric provisioning. However, only one option is outlined within this document which is manual CLI configuration. This does not exclude any of the other options as a viable option for Fabric provisioning. Please use the option that is suitable for your environment and requirements.
The following is an implementation sequence for this solution to simplify the deployment and troubleshooting process:
Step 1. Verify Logins to Meraki Dashboard
Step 2. Verify Meraki API Access (e.g. Using a tool such as Postman)
Step 3. Create Dashboard Networks as required (Please create a Combined type network)
Step 4. Configure Dashboard Network settings as desired (e.g. Firmware, Time-zone, etc.)
Step 5. Claim Managed Catalyst devices in Dashboard Inventory (e.g. 9300-M, 91XX-M, etc.)
Step 6. Add Managed Catalyst devices to a Dashboard Network
Note: It is recommended to have all Fabric switches (Monitor mode) and Access layer devices (Managed mode) in one Dashboard network to have a single topology view of the entire network.
Note: Please ensure that you have sufficient licenses in your Dashboard account otherwise your network(s) could go out of license compliance which may disrupt your network operations
Step 7. Configure Cloud Managed Access Switches and Access Points in Dashboard (Do not connect switch uplinks yet) Test #1
Step 8. Configure Adaptive Policy in Dashboard by creating Groups
Note: Adaptive Policy leverages SGTs for endpoint classification, identity propagation, and policy enforcement. Even though Adaptive Policy's actual policy lives and breathes in the dashboard, Cisco ISE can be utilized to dynamically assign SGTs to clients based on several conditions, such as device profile, posture, user, machine, and more. This is all done using RADIUS and the AV pair for security group tags. For further details, please refer to this article.
Step 9. Configure Cisco ISE for end user authentication, posturing and authorization.
Note: Configuring Cisco ISE is out of scope for this document. Please refer to Cisco ISE documentation for details. Also please note that Cisco ISE Meraki Connector is available with release 3.2 or higher.
Step 10. Configure your Spine Switch(es)
(1) Base configuration (including Loopback0 and main settings)
(2) Underlay links (excluding OSPF and Multicast)
(3) OSPF on Underlay links and Loopback0
(4) BGP address family for L2VPN EVPN
(5) Multicast; IP PIM Sparse mode with static RP and MSDP
Step 11. Configure your Border Leaf Switch(es)
(1) Base configuration (including Loopback0 and main settings)
(2) Underlay links (excluding OSPF and Multicast)
(3) OSPF on Underlay links and Loopback0
(4) BGP address family for L2VPN EVPN
(5) Multicast; IP PIM Sparse mode with static RP and MSDP
(6) OSPF to Core (Underlay)
(7) BGP to Core (Underlay)
(8) Add Campus VRF
(9) Add Campus Handoff to Core (Overlay)
(10) Add Campus BGP to Core (Overlay)
(11) L3 VNIs (Campus Routing on the Underlay)
(12) Add Guest VRF
(13) Add Guest Handoff to Core (Overlay)
(14) Add Guest BGP to Core (Overlay)
(15) VNIs (Guest Routing on the Underlay)
Step 12. Configure your Leaf Switch(es)
(1) Base configuration (including Loopback0 and main settings)
(2) Underlay links (excluding OSPF and Multicast)
(3) OSPF on Underlay links and Loopback0
(4) BGP address family for L2VPN EVPN
(5) Multicast; IP PIM Sparse mode with static RP and MSDP
(6) Add Campus VRF
(7) BGP for Campus IPv4 VRF
(8) Enable Management L2VPN EVPN and VXLAN Mapping
(9) Add NVE1 and VNI mapping for Management
(10) DAG and DHCP for Management VLAN
(11) Enable Corp L2VPN EVPN and VXLAN Mapping
(12) NVE1 to VNI mapping for Corp
(13) DAG and DHCP for Corp VLAN
(14) Enable IoT L2VPN EVPN and VXLAN Mapping
(15) NVE1 to VNI mapping for IoT
(16) DAG and DHCP for IoT VLAN
(17) L3 VNIs (Campus Routing on the Underlay)
(18) Add Guest VRF
(19) BGP for Guest IPv4 VRF
(20) Enable Guest L2VPN EVPN and VXLAN Mapping
(21) NVE1 to VNI mapping for Guest
(22) DAG and DHCP for Guest VLAN
(23) L3 VNIs (Guest Routing on the Underlay)
(24) Downlinks to Access Layer
(25) Inline Tagging
(26) Spanning Tree Protocol
Step 13. Onboard Fabric Switches for Cloud Monitoring (Spines, Border Leaf, Leaf)
Step 14. Onboard Access Switches for Cloud Monitoring (Where applicable)
Step 15. Onboard Wireless LAN Controllers for Cloud Monitoring (Where applicable)
Note: Onboarding Catalyst devices (Switches, APs, WLCs) is out of scope for this document. Please refer to documentation for steps required to onboard your devices.
Step 16. Connect Cloud Managed Access Switch Uplinks
Step 17. Wait for the Access Switch(es) and Access Points to come online and upgrade their firmware
Note: This will cause the Access Switches and Access Points to reboot several times. Please wait till they are online in dashboard and steady before proceeding.
Step 18. Configure EtherChannels on Leaf Switch(es) (Where applicable)
Step 19. Configure Cisco ISE for end user authentication, posturing and authorization
Step 20. Configure Adaptive Policy in Dashboard
Step 21. Testing and Verification
Deployment and Configuration Guide
Meraki Dashboard
Please use the following template to set your Meraki Dashboard account.
Note: Only the items mentioned in the below table need to be changed. All other items are the default settings which will remain unchanged unless required. Please set your Meraki Dashboard account based on your own requirements and use the below template for guidance.
Table 7. Meraki Dashboard Settings
| Item |
Configuration Details |
| Organization Name |
A name of your choice (e.g. Cloud Campus Fabric with BGP EVPN) |
| Network Name |
A name of your choice (e.g. SiteName-CityName-Country) |
| Network time zone |
Please choose the time zone for your city/region as this is going to reflect on all Dashboard reports (e.g. Traffic analytics, alerts, etc.) |
| Administration |
Please ensure that at least one user has full read-write access to the Dashboard organization, even if you have configured SAML for SSO |
Cloud Managed Access Switches
Please use the following template to configure your Cloud Managed Access Switches in Meraki Dashboard.
Note: Only the items mentioned in the below table need to be changed. All other items are the default settings which will remain unchanged unless required. Please setup the Meraki Dashboard based on your own requirements and use the below template for guidance.
Table 8. Cloud Managed Access Switches Configuration Template
| Item |
Configuration Details |
| Switch Settings |
● Management VLAN = 1
● Enable STP
● Bridge Priority = 32768
|
| Switch Name |
● Name (1) = SiteID-FLXX-SWXX
|
| Switch Tag |
● Tag (1) = Managed
|
| Access Policy (802.1x) |
● Name = Wired-802.1x
● Authentication method = my RADIUS server
● Radius Server: Host / Port / Secret
● Radius Attribute Specifying Group Policy Name = Filter-Id
● Host mode = Single-Host
● 802.1X Control Direction = both
● Failed Auth VLAN = 220 (Guest VLAN)
|
| Access Switch Uplinks to Leaf switch |
● Name (1) = To Leaf-XX Port XX
● Tag (1) = Uplink
● Trunk
● Native VLAN = 1
● Allowed VLANs (2) = 1-1000
● Peer SGT Capable = Enable
● Adaptive Policy Group = 2: Infrastructure
|
| Access Switch Downlinks to Access Points |
● Name (1) = To AP-XX Port XX
● Tag (1) = Wireless-AP
● Trunk
● Native VLAN = 1
● Allowed VLANs (2) = 1-1000
● Peer SGT Capable = Enable
● Adaptive Policy Group = 2: Infrastructure
|
| Access Switch Downlinks to Wired Clients |
● Name (1) = To ClientXX
● Tag (1) = Client
● Access
● Access Policy (3) = Wired-802.1x
● VLAN = 220 (4)
|
| EtherChannels for Access Switch Uplinks to Leaf Switch |
● Where applicable
|
Note: (1) Suggested. Please amend based on your requirements (2) Please note that -M switches support a maximum of 1000 VLANs (3) Access Policy must be configured first before assigning it to a switch port (4) Guest VLAN (VLAN 220) has been configured as ISE will be leveraged to return a VLAN identifier based on authentication and posture
The following section shows the configuration steps for Cloud Managed Access Switches based on the above template.
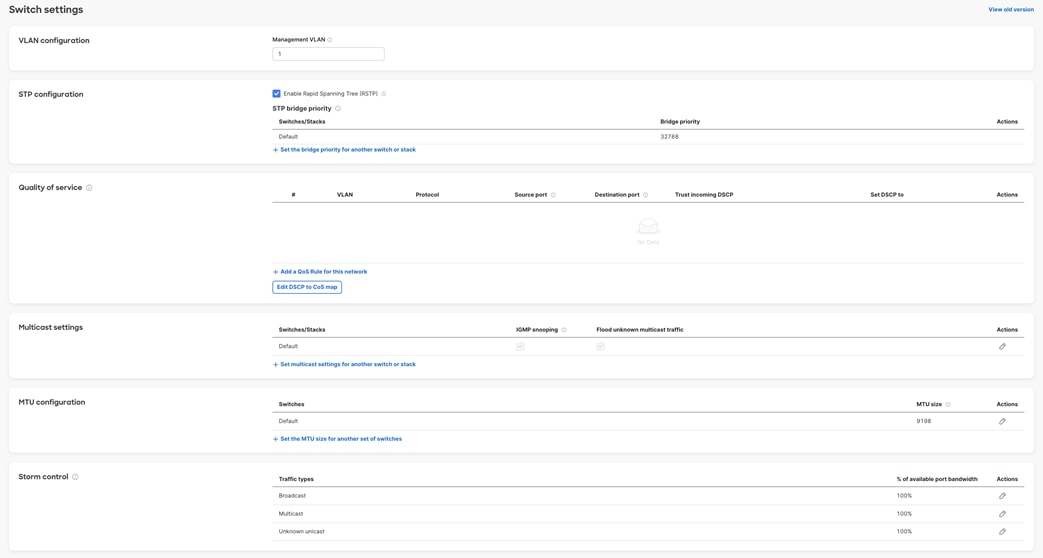
Switch Settings
In Dashboard, navigate to Switching > Switch Settings then change the settings accordingly. Click Save when you’re done.
Switch Name
In Dashboard, navigate to Switching > Switches then click on the desired switch which takes you to the Switch details page. Next, click on the edit button next to the switch name to specify the name then click on Save.
Switch Tag
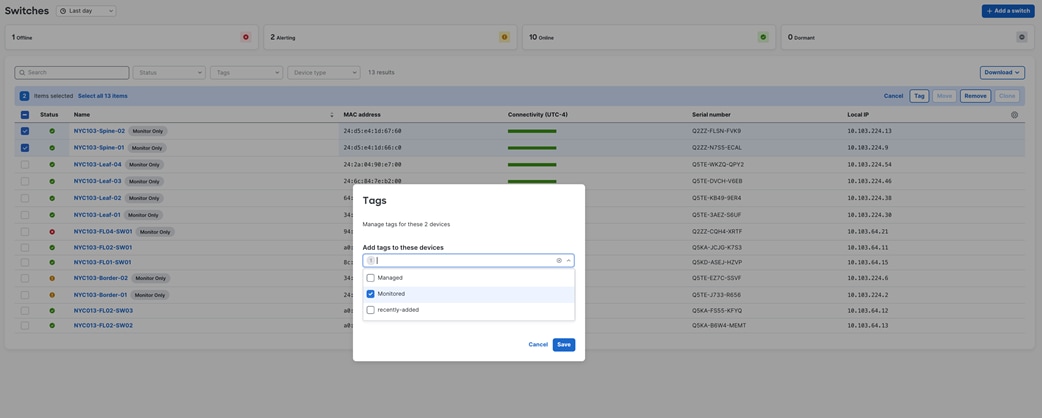
In Dashboard, navigate to Switching > Switches then select the desired switches and click on Tag. Then, choose the tags that you want to add or delete. Click Save when you’re done.
Access Policy
In Dashboard, navigate to Switching > Access policies then click on Add an access policy. Then choose the name and Authentication method as my RADIUS server. Then add the Radius server(s) with Host / Port / Secret. Enable Radius CoA and choose Filter-Id as the Radius Attribute. Choose the policy type, Host mode and 802.1X control direction and the Failed Auth VLAN. Click Save once you’re done.
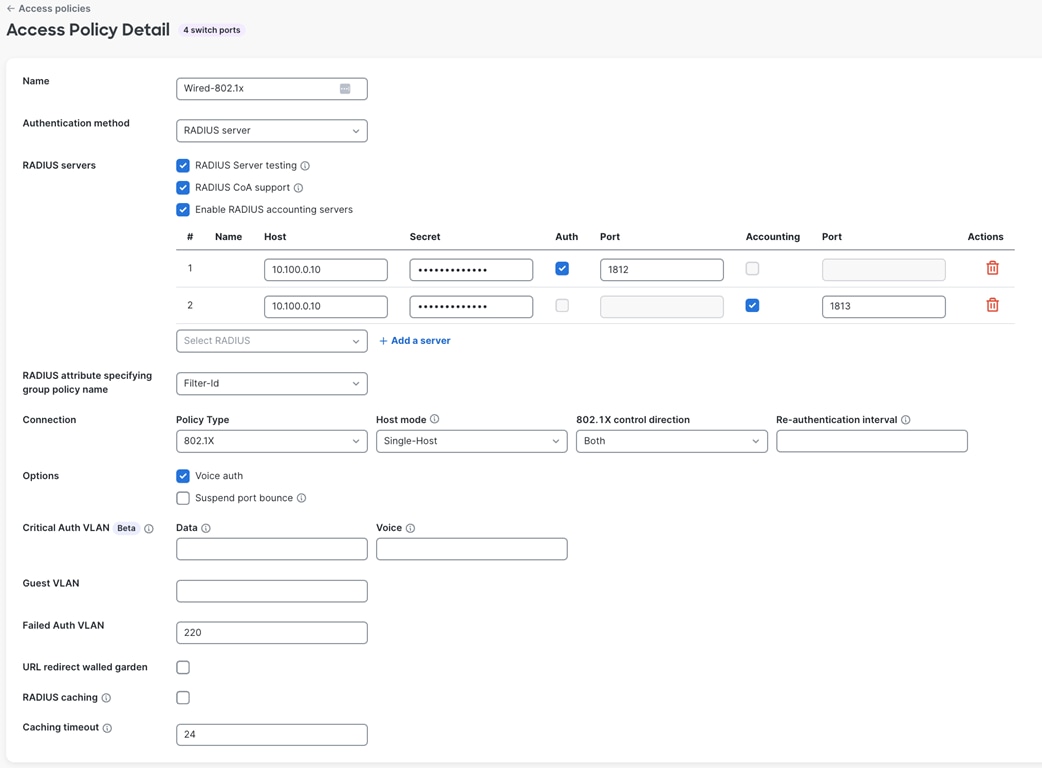
Cisco Identity Services Engine
The access policy configured in the previous section is set with Radius server as the authentication method. This is pointing to Cisco ISE as the Radius Server which in addition to authentication and authorization will also be configured to push VLANs, SGTs and TrustSec policies to Dashboard using the Meraki Connector which is available with Cisco ISE 3.2 and higher.
Note: Please note that the configuration of Cisco Identity Services Engine is out of scope for this document. The following sections will only illustrate the specific items related to adding Cloud Managed devices to Cisco ISE as well as the Cisco ISE integration with Dashboard for TrustSec integration.
The first step is to add the Cloud Managed devices as a network device in Cisco ISE. In Cisco ISE, navigate to Administration > Network devices then click on Add to create a new list for Cloud Managed devices (e.g. Switches, Access Points) that will be using Cisco ISE as a Radius server.
Note: Please note that you need to use the Management IP of the Cloud Managed devices (e.g. 10.103.64.0/24 in this design) as the IP address when adding to Cisco ISE.
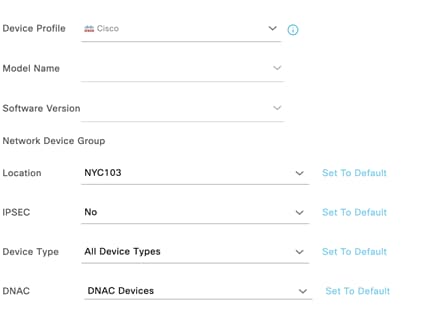
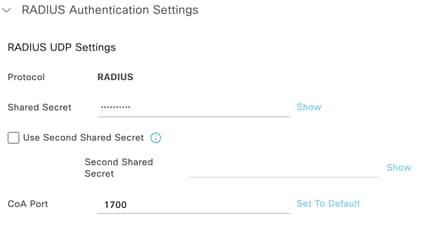
Note: Please note that the shared secret must match that configured on Dashboard (for both Cloud Managed switches and Cloud Managed access points).
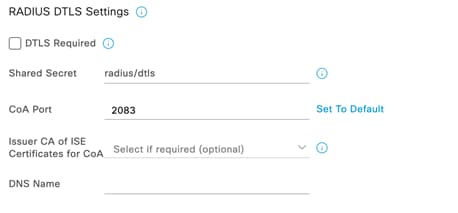
The second step is to integrate Cisco ISE with Dashboard. Navigate to Work Centers > Integrations then click on Connect Meraki and follow the steps on your screen. Remember that having a Dashboard API key is required for this step. Also remember that your Dashboard API key must have full access to the Dashboard organization you want connected with Cisco ISE. Next, select the sync interval settings (a value between 5 and 30mins, default value is 12). Then select the egress policies you want to sync with Dashboard by selected the corresponding check boxes. Finally, select SGACLs and SGTs that you want to sync with Dashboard.
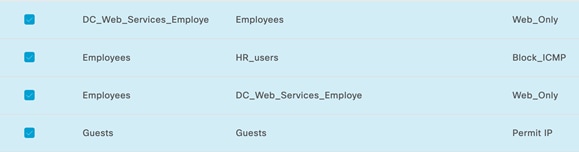
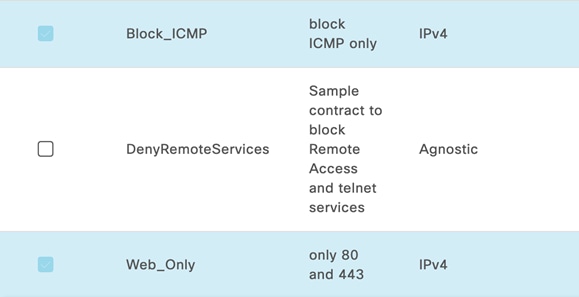
Note: The above Cisco ISE configuration is for illustration purposes only. Please configure your Cisco ISE settings according to your actual requirements.
Uplinks (Access-To-Leaf)
In Dashboard, navigate to Switching > Switch ports then select the uplink port(s) (You can also filter for them by port number for example) as shown below.
Then click on edit to edit all ports at once. Specify the tags then choose the port type Trunk. Specify the native VLAN and the allowed VLANs. Then ensure that peer SGT capable is enabled and then choose the Adaptive Policy Group for your uplinks. Please note that 2: Infrastructure is one of the default Adaptive Policy Groups in Dashboard. Click Update when you’re done.
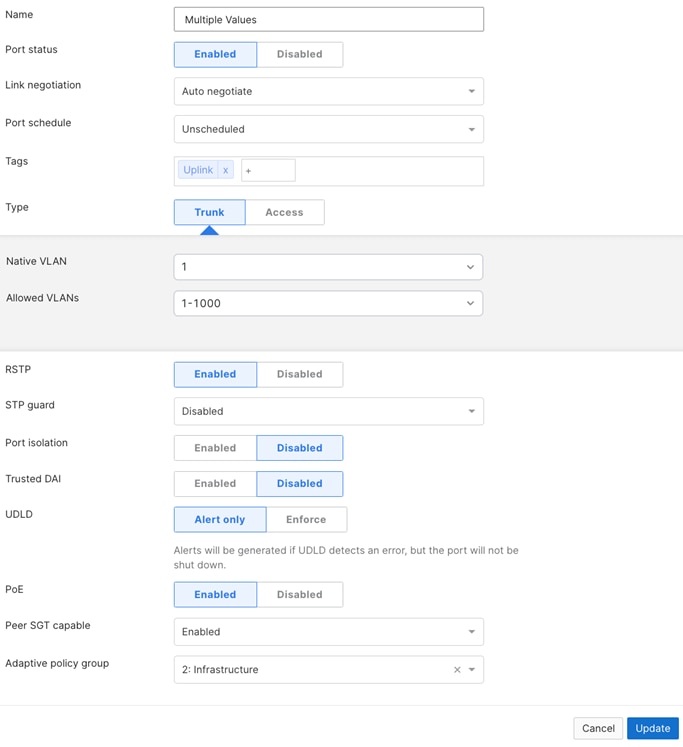
Note: Cloud Managed Switches (-M models) support a maximum of 1000 VLANs on a trunk port. It is recommended to configure the switch ports with the specific VLANs (or ranges) to stay within the 1000 VLAN count (e.g. 1-20, 100-300, 350, 900-1000, 1050-1250). Also, please note that the following VLAN ranges are reserved on -M models: 1002-1005, 4093-4094 and cannot be assigned or used on any port configuration.
Note: To modify each port’s name in Dashboard to a unique value, you will have to modify each port individually. As an alternative, you can edit all uplink ports and specify the common parameters (e.g. Trunk, Native VLAN, etc.) and then modify them individually to assign the unique values (e.g. Name)
The following figure shows the uplink ports after they have been setup for this topology and design:
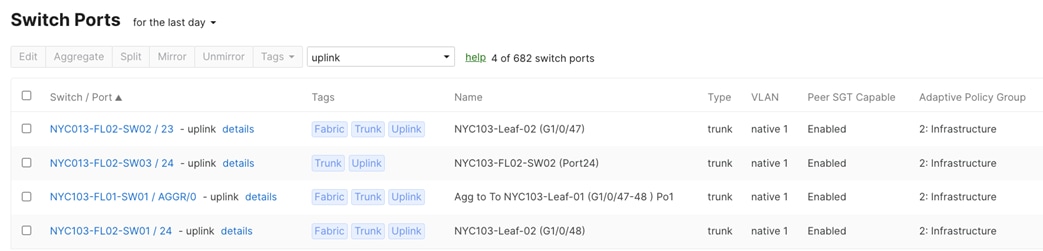
Tech tip: This view can be changed in Dashboard by clicking on the wrench sign. You can then customize the view by selecting or unselecting the table headers. You can also reorder the headers by dragging them to the desired location (e.g. Tags, Name, Type, VLAN, … instead of Tags, Sent Bytes, Received Bytes, …)
Downlinks (Switch-To-Access Point)
In Dashboard, navigate to Switching > Switch ports then select the downlink port(s) to Access Points (You can also filter for them by port number for example) then click on edit to edit all ports at once. Specify the tags then choose the port type Trunk. Specify the native VLAN and the allowed VLANs. Then ensure that peer SGT capable is enabled and then choose the Adaptive Policy Group for your downlinks. Please note that 2: Infrastructure is one of the default Adaptive Policy Groups in Dashboard. Click Update when you’re done.
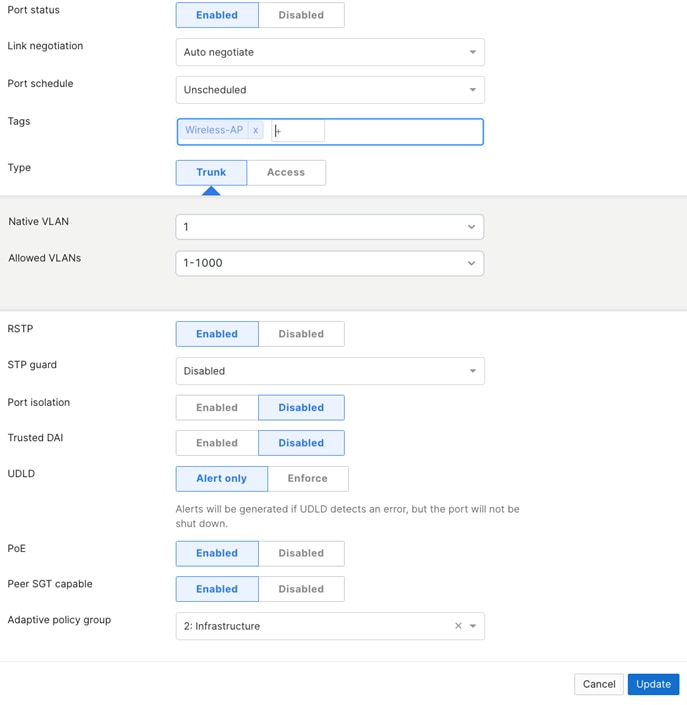
Similar to the previous step, you can change the port names individually. The following figure shows the downlink ports to Access Points after they have been setup for this topology and design:
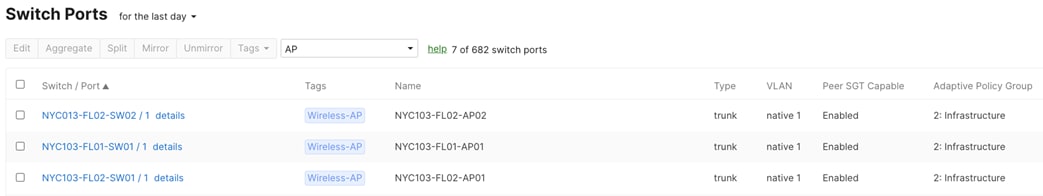
Downlinks (Switch-To-Clients)
In Dashboard, navigate to Switching > Switch ports then select the downlink port(s) to Client devices (You can also filter for them by port number for example) then click on edit to edit all ports at once. Specify the tags then choose the port type Access. Specify the Data VLAN. Then assign the Access Policy. Click Update when you’re done.
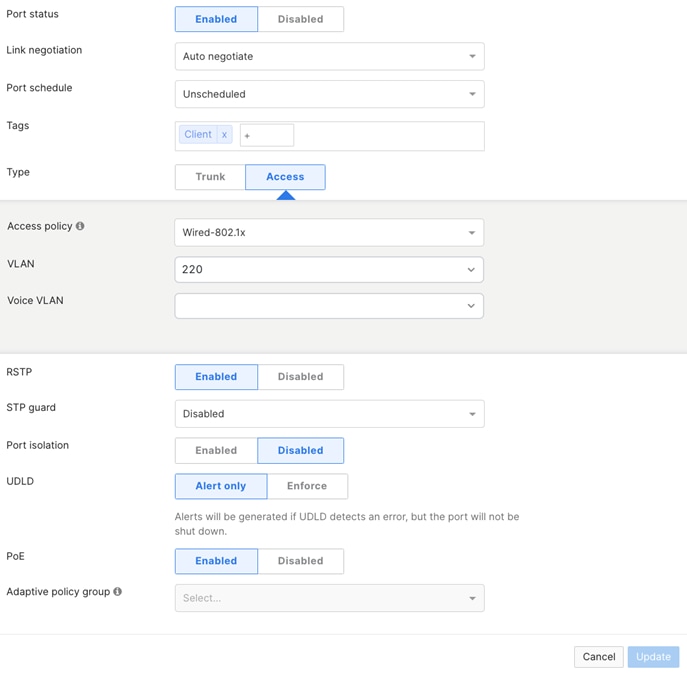
Similar to the previous step, you can change the port names individually. The following figure shows the downlink ports to Access Points after they have been setup for this topology and design:
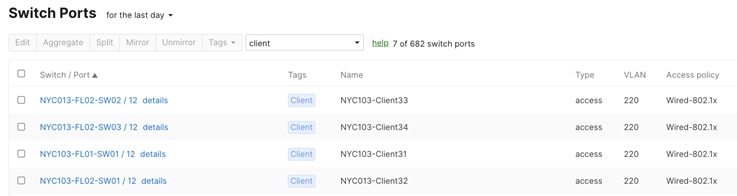
EtherChannels (Where Applicable)
In Dashboard, navigate to Switching > Switch ports then select the Uplink port(s) to Leaf Switches that need to be aggregated (You can also filter for them by port number for example) then click Aggregate.
Once aggregated, the two ports will be bundled together in the Switch ports view as shown below.
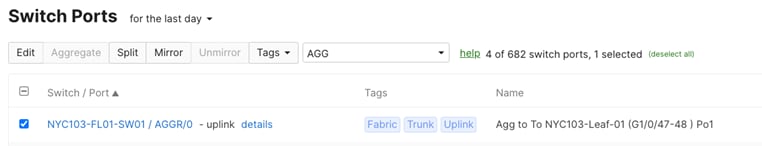
Note: You can specify the name of the Aggregate port after you have bonded the ports together by selecting the aggregate port and clicking on Edit.
Cloud Managed Access Points
Please use the following template to configure your Cloud Managed Access Points in Meraki Dashboard.
Note: Only the items mentioned in the below table need to be changed. All other items are the default settings which will remain unchanged unless required. Please configure the Meraki Dashboard based on your own requirements and use the below template for guidance.
Table 9. Cloud Managed Access Points Configuration Template
| Item |
Configuration Details |
| Access Point Name |
● Name (1) = SiteID-FLXX-APXX
|
| Access Point Tag |
● Tag (1) = Managed
|
| SSID1 |
● Name (1) = Campus
● Security = Enterprise with my RADIUS server
● Splash Page = None
● Radius Server: Host / Port / Secret
● Radius CoA Support = Enabled
● Client IP and LAN = Bridged
● Radius Override = Override VLAN tag
● VLAN Tagging = VLAN ID = 2202
● Adaptive Group Policy = 0: Unknown
|
| SSID2 |
● Name (1) = Guest
● Security = Password (xxxx)
● Splash Page = None
● Client IP and LAN = Bridged
● VLAN Tagging = VLAN ID = 220 (2)
● Adaptive Group Policy = 0: Unknown
|
Note: (1) Suggested. Please amend based on your requirements (2) Guest VLAN (VLAN 220) has been configured as ISE will be leveraged to return a VLAN identifier based on authentication and posture
The following section explains the configuration steps for Cloud Managed Access Points based on the above template.
Note: Other Access Point settings in Dashboard (e.g. Radio Profiles, SSID Availability, etc.) are out of this document’s scope. Please refer to Meraki Documentation for guidance on how to setup and operate your wireless network.
Access Point Name
In Dashboard, navigate to Wireless > Access points then click on the desired access point which takes you to the AP details page. Next, click on the edit button next to the AP name to specify the name then click on Save.
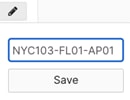
Access Point Tag
In Dashboard, navigate to Wireless > Access points then select the desired access points and click on Tag. Then, choose the tags that you want to add or delete. Click Save when you’re done.
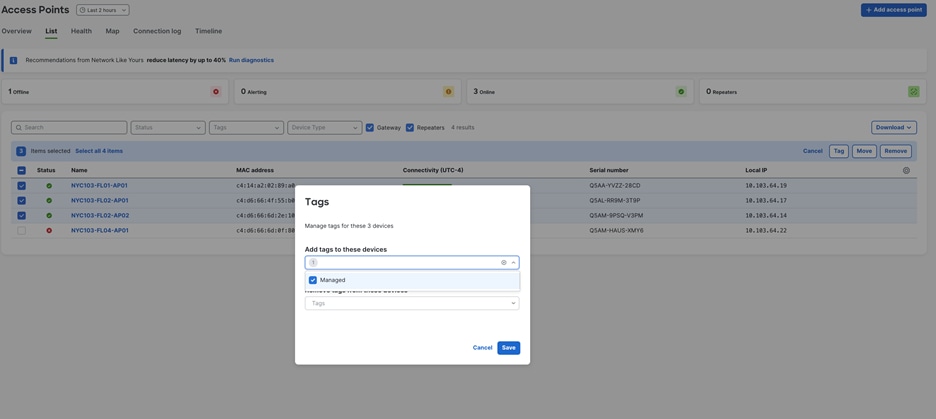
SSID Configuration (Campus)
In Dashboard, navigate to Wireless > SSIDs then click on rename then Save.
Next, click on edit settings and set this SSID as required. Finally, click on Save once you’re down. The following shows the configuration for the Campus SSID.
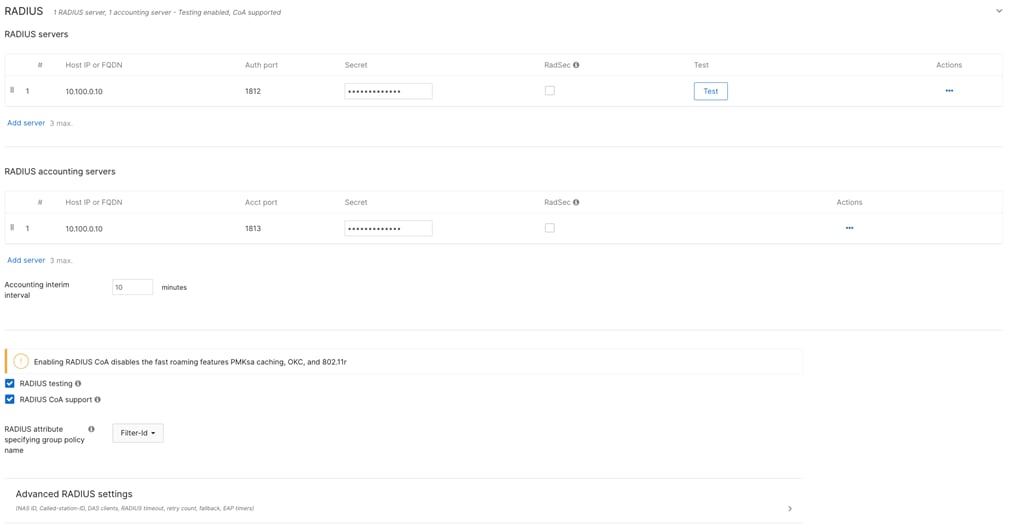
SSID Configuration (Guest)
In Dashboard, navigate to Wireless > SSIDs then click on rename then Save.
Next, click on edit settings and set this SSID as required. Finally, click on Save once you’re down. The following shows the configuration for the Guest SSID.
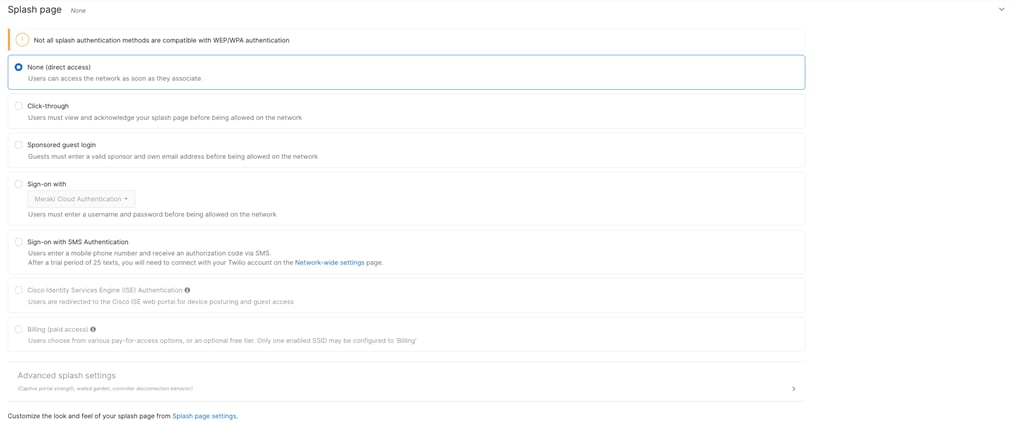
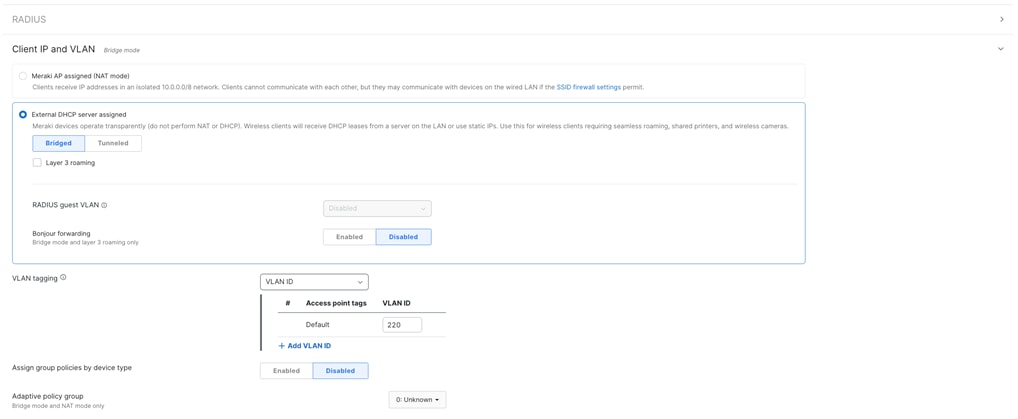
Adaptive Policy in Dashboard
Adaptive Policy Groups can either be created in Dashboard or in Cisco ISE which then can be synchronized. Policies can also be synchronized between Cisco ISE and Dashboard using Cisco ISE Meraki Connector which is available with Cisco ISE 3.2 or higher.
Note: The monitoring logs (meraki-connector.log and meraki-sync-service.log) for syncing TrustSec policies in Cisco ISE with Cisco Meraki Dashboards can be found in the debug logs maintained in the Meraki connector.
Creating Adaptive Policy Groups in Dashboard
If you are creating Adaptive Policy Groups in Dashboard, please navigate to Organization > Adaptive policy then click on Groups then click Add group. Once you’re done, click on Review changes then click on Submit. Please see the example provided below:
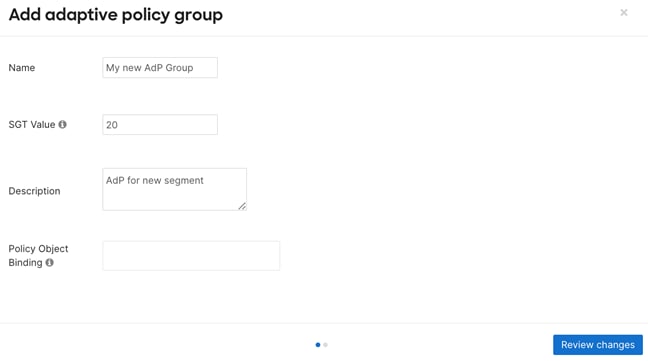
Note: Please make sure that Adaptive policy is enabled for your Dashboard network. Please refer to this article for the steps required.
You will need to create a group for each SGT value required. Please refer to the following figure for the Adaptive Policy Groups created for this solution:
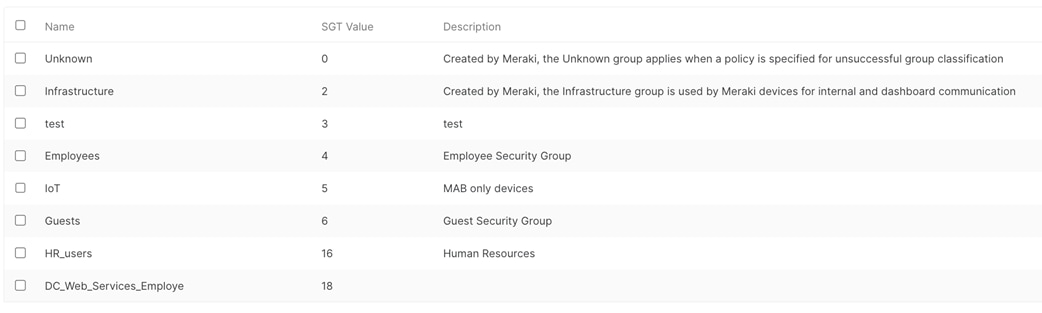
Note: If you are using Cisco ISE and wish to centralize your TrustSec configuration (Policies, SGACLs, SGTs) you do not need to create policies in Dashboard as these will be synched with the configuration on Cisco ISE. For further information, please refer to this article. The above configuration is provided as an example only.
Note: Please note that Cisco ISE will dynamically assign VLANs and SGTs to users that will be handed back to Dashboard in a Radius attribute.
Note: For more information on configuring Adaptive Policy with Cloud Managed Devices, please refer to Adaptive Policy for Cloud Managed Access Points and Adaptive Policy for Cloud Managed Switches.
Note: Please note that Adaptive Policy requires the Advanced/Advantage license on Cloud Managed Switches and Access Points. For more information about licensing requirements, please refer to the following article.
Spine Switches
Please use the following template to configure your Fabric Spine Switch(es)
Spine 1
Base Configuration for Spine 1
!
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
!
hostname NYC103-Spine-01
!
clock timezone EST -5 0
clock summer-time EDT recurring
!
ip routing
!
ip name-server 10.100.0.5 10.200.0.5
ip domain name ciscovalidated.com
!
license boot level network-advantage addon dna-advantage
!
system mtu 9198
!
errdisable recovery cause bpduguard
errdisable recovery interval 60
!
enable secret **masked**
!
username admin privilege 15 secret **masked**
!
no ip http server
no ip http secure-server
!
line con 0
exec-timeout 60 0
privilege level 15
logging synchronous
login local
!
line vty 0 31
exec-timeout 60 0
privilege level 15
logging synchronous
login local
transport input telnet ssh
!
aaa new-model
!
interface Loopback0
description Primary loopback
ip address 10.103.255.1 255.255.255.255
!
ntp source Loopback0
ntp server 10.100.0.5 prefer
!
Underlay Links (excluding OSPF and Multicast)
! Spine to Spine
!
interface HundredGigE1/0/28
description To NYC-Spine-02 HundredGigE1/0/28
no switchport
ip address 10.103.224.17 255.255.255.252
!
! Spine to Leaf
!
interface TwentyFiveGigE1/0/1
description To NYC013-Leaf-01 TwentyFiveGigE1/1/1
no switchport
ip address 10.103.224.29 255.255.255.252
!
interface TwentyFiveGigE1/0/2
description To NYC103-Leaf-02 GigabitEthernet1/0/1
no switchport
ip address 10.103.224.37 255.255.255.252
!
interface TwentyFiveGigE1/0/3
description To NYC103-Leaf-03 GigabitEthernet1/0/1
no switchport
ip address 10.103.224.45 255.255.255.252
!
interface TwentyFiveGigE1/0/4
description To NYC103-Leaf-04 TwentyFiveGigE1/1/1
no switchport
ip address 10.103.224.53 255.255.255.252
!
! Spine to Border
!
interface HundredGigE1/0/25
description To NYC103-Border-01 FortyGigabitEthernet1/1/1
no switchport
ip address 10.103.224.9 255.255.255.252
speed nonegotiate
speed 40000
!
interface HundredGigE1/0/26
description To NYC103-Border-02 FortyGigabitEthernet1/1/1
no switchport
ip address 10.103.224.21 255.255.255.252
speed nonegotiate
speed 40000
!
OSPF on Underlay links and Loopback0
!
router ospf 1
router-id 10.103.255.1
auto-cost reference-bandwidth 100000
default-information originate metric 1000 metric-type 1
bfd all-interfaces
!
interface Loopback0
ip ospf 1 area 0
!
interface HundredGigE1/0/28
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface TwentyFiveGigE1/0/1
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface TwentyFiveGigE1/0/2
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface TwentyFiveGigE1/0/3
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface TwentyFiveGigE1/0/4
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface HundredGigE1/0/25
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface HundredGigE1/0/26
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
BGP and Address Family for L2VPN EVPN
!
router bgp 65106
!
bgp router-id 10.103.255.1
bgp log-neighbor-changes
no bgp default ipv4-unicast
!
template peer-session leaf-ps
remote-as 65106
update-source Loopback0
fall-over bfd
exit-peer-session
!
neighbor 10.103.255.3 inherit peer-session leaf-ps
neighbor 10.103.255.4 inherit peer-session leaf-ps
neighbor 10.103.255.11 inherit peer-session leaf-ps
neighbor 10.103.255.12 inherit peer-session leaf-ps
neighbor 10.103.255.13 inherit peer-session leaf-ps
neighbor 10.103.255.14 inherit peer-session leaf-ps
!
template peer-policy leaf-pp
route-reflector-client
send-community both
exit-peer-policy
!
address-family l2vpn evpn
neighbor 10.103.255.3 activate
neighbor 10.103.255.3 inherit peer-policy leaf-pp
neighbor 10.103.255.4 activate
neighbor 10.103.255.4 inherit peer-policy leaf-pp
neighbor 10.103.255.11 activate
neighbor 10.103.255.11 inherit peer-policy leaf-pp
neighbor 10.103.255.12 activate
neighbor 10.103.255.12 inherit peer-policy leaf-pp
neighbor 10.103.255.13 activate
neighbor 10.103.255.13 inherit peer-policy leaf-pp
neighbor 10.103.255.14 activate
neighbor 10.103.255.14 inherit peer-policy leaf-pp
exit-address-family
!
Multicast; IP PIM Sparse Mode with Static RP and MSDP
!
ip multicast-routing
!
interface Loopback1
description MSDP specific loopback
ip address 10.103.254.1 255.255.255.255
ip pim sparse-mode
ip ospf 1 area 0
!
interface Loopback2
description PIM RP Anycast specific loopback
ip address 10.103.255.255 255.255.255.255
ip pim sparse-mode
ip ospf 1 area 0
!
ip msdp peer 10.103.254.2 connect-source Loopback1
ip msdp cache-sa-state
!
interface HundredGigE1/0/28
ip pim sparse-mode
!
interface TwentyFiveGigE1/0/1
ip pim sparse-mode
!
interface TwentyFiveGigE1/0/2
ip pim sparse-mode
!
interface TwentyFiveGigE1/0/3
ip pim sparse-mode
!
interface TwentyFiveGigE1/0/4
ip pim sparse-mode
!
interface HundredGigE1/0/25
ip pim sparse-mode
!
interface HundredGigE1/0/26
ip pim sparse-mode
!
ip pim rp-address 10.103.255.255
!
Spine 2
Base Configuration
!
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
!
hostname NYC103-Spine-02
!
clock timezone EST -5 0
clock summer-time EDT recurring
!
ip routing
!
ip name-server 10.100.0.5 10.200.0.5
ip domain name ciscovalidated.com
!
license boot level network-advantage addon dna-advantage
!
system mtu 9198
!
errdisable recovery cause bpduguard
errdisable recovery interval 60
!
enable secret **masked**
!
username admin privilege 15 secret **masked**
!
no ip http server
no ip http secure-server
!
line con 0
exec-timeout 60 0
privilege level 15
logging synchronous
login local
!
line vty 0 31
exec-timeout 60 0
privilege level 15
logging synchronous
login local
transport input telnet ssh
!
aaa new-model
!
interface Loopback0
description Primary loopback
ip address 10.103.255.2 255.255.255.255
!
ntp source Loopback0
ntp server 10.100.0.5 prefer
!
Underlay Links (excluding OSPF and Multicast)
!
! Spine to Spine
!
interface HundredGigE1/0/28
description To NYC-Spine-01 HundredGigE1/0/28
no switchport
ip address 10.103.224.18 255.255.255.252
!
! Spine to Leaf
!
interface TwentyFiveGigE1/0/1
description To NYC013-Leaf-01 TwentyFiveGigE1/1/2
no switchport
ip address 10.103.224.33 255.255.255.252
!
interface TwentyFiveGigE1/0/2
description To NYC103-Leaf-02 GigabitEthernet1/0/2
no switchport
ip address 10.103.224.41 255.255.255.252
!
interface TwentyFiveGigE1/0/3
description To NYC103-Leaf-03 GigabitEthernet1/0/2
no switchport
ip address 10.103.224.49 255.255.255.252
!
interface TwentyFiveGigE1/0/4
description To NYC103-Leaf-04 TwentyFiveGigE1/1/2
no switchport
ip address 10.103.224.57 255.255.255.252
!
! Spine to Border
!
interface HundredGigE1/0/25
description To NYC103-Border-01 FortyGigabitEthernet1/1/2
no switchport
ip address 10.103.224.25 255.255.255.252
speed nonegotiate
speed 40000
!
interface HundredGigE1/0/26
description To NYC103-Border-02 FortyGigabitEthernet1/1/2
no switchport
ip address 10.103.224.13 255.255.255.252
speed nonegotiate
speed 40000
!
OSPF on Underlay links and Loopback0
!
router ospf 1
router-id 10.103.255.2
auto-cost reference-bandwidth 100000
default-information originate metric 1000 metric-type 1
bfd all-interfaces
!
interface Loopback0
ip ospf 1 area 0
!
interface HundredGigE1/0/28
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface TwentyFiveGigE1/0/1
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface TwentyFiveGigE1/0/2
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface TwentyFiveGigE1/0/3
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface TwentyFiveGigE1/0/4
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface HundredGigE1/0/25
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface HundredGigE1/0/26
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
BGP and Address Family for L2VPN EVPN
!
router bgp 65106
!
bgp router-id 10.103.255.2
bgp log-neighbor-changes
no bgp default ipv4-unicast
!
template peer-session leaf-ps
remote-as 65106
update-source Loopback0
fall-over bfd
exit-peer-session
!
neighbor 10.103.255.3 inherit peer-session leaf-ps
neighbor 10.103.255.4 inherit peer-session leaf-ps
neighbor 10.103.255.11 inherit peer-session leaf-ps
neighbor 10.103.255.12 inherit peer-session leaf-ps
neighbor 10.103.255.13 inherit peer-session leaf-ps
neighbor 10.103.255.14 inherit peer-session leaf-ps
!
template peer-policy leaf-pp
route-reflector-client
send-community both
exit-peer-policy
!
address-family l2vpn evpn
neighbor 10.103.255.3 activate
neighbor 10.103.255.3 inherit peer-policy leaf-pp
neighbor 10.103.255.4 activate
neighbor 10.103.255.4 inherit peer-policy leaf-pp
neighbor 10.103.255.11 activate
neighbor 10.103.255.11 inherit peer-policy leaf-pp
neighbor 10.103.255.12 activate
neighbor 10.103.255.12 inherit peer-policy leaf-pp
neighbor 10.103.255.13 activate
neighbor 10.103.255.13 inherit peer-policy leaf-pp
neighbor 10.103.255.14 activate
neighbor 10.103.255.14 inherit peer-policy leaf-pp
exit-address-family
!
Multicast; IP PIM Sparse Mode with Static RP and MSDP
!
ip multicast-routing
!
interface Loopback1
description MSDP specific loopback
ip address 10.103.254.2 255.255.255.255
ip pim sparse-mode
ip ospf 1 area 0
!
interface Loopback2
description PIM RP Anycast specific loopback
ip address 10.103.255.255 255.255.255.255
ip pim sparse-mode
ip ospf 1 area 0
!
ip msdp peer 10.103.254.1 connect-source Loopback1
ip msdp cache-sa-state
!
interface HundredGigE1/0/28
ip pim sparse-mode
!
interface TwentyFiveGigE1/0/1
ip pim sparse-mode
!
interface TwentyFiveGigE1/0/2
ip pim sparse-mode
!
interface TwentyFiveGigE1/0/3
ip pim sparse-mode
!
interface TwentyFiveGigE1/0/4
ip pim sparse-mode
!
interface HundredGigE1/0/25
ip pim sparse-mode
!
interface HundredGigE1/0/26
ip pim sparse-mode
!
ip pim rp-address 10.103.255.255
!
Border Switches
Please use the following template to configure your Fabric Spine Switch(es)
Border Leaf 1
Base Configuration
!
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
!
hostname NYC103-Border-01
!
clock timezone EST -5 0
clock summer-time EDT recurring
!
ip routing
!
ip name-server 10.100.0.5 10.200.0.5
ip domain name ciscovalidated.com
!
license boot level network-advantage addon dna-advantage
!
system mtu 9198
!
errdisable recovery cause bpduguard
errdisable recovery interval 60
!
enable secret **masked**
!
username admin privilege 15 secret **masked**
!
no ip http server
no ip http secure-server
!
line con 0
exec-timeout 60 0
privilege level 15
logging synchronous
login local
!
line vty 0 31
exec-timeout 60 0
privilege level 15
logging synchronous
login local
transport input telnet ssh
!
aaa new-model
!
interface Loopback0
description Primary loopback
ip address 10.103.255.3 255.255.255.255
!
ntp source Loopback0
ntp server 10.100.0.5 prefer
!
Underlay Links (excluding OSPF and Multicast)
!
! Border to Spine
!
interface FortyGigabitEthernet1/1/1
description To NYC103-Spine-01 HundredGigE1/0/25
no switchport
ip address 10.103.224.10 255.255.255.252
speed nonegotiate
speed 40000
!
interface FortyGigabitEthernet1/1/2
description To NYC103-Spine-02 HundredGigE1/0/25
no switchport
ip address 10.103.224.26 255.255.255.252
speed nonegotiate
speed 40000
!
OSPF on Underlay links and Loopback0
!
router ospf 1
router-id 10.103.255.3
auto-cost reference-bandwidth 100000
default-information originate metric 1000 metric-type 1
bfd all-interfaces
!
interface Loopback0
ip ospf 1 area 0
!
interface FortyGigabitEthernet1/1/1
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface FortyGigabitEthernet1/1/2
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
BGP and Address Family for L2VPN EVPN
!
router bgp 65106
!
bgp router-id 10.103.255.3
bgp log-neighbor-changes
no bgp default ipv4-unicast
!
template peer-session spine-ps
remote-as 65106
update-source Loopback0
fall-over bfd
exit-peer-session
!
neighbor 10.103.255.1 inherit peer-session spine-ps
neighbor 10.103.255.2 inherit peer-session spine-ps
!
address-family l2vpn evpn
neighbor 10.103.255.1 activate
neighbor 10.103.255.1 send-community both
neighbor 10.103.255.2 activate
neighbor 10.103.255.2 send-community both
exit-address-family
!
Multicast; IP PIM Sparse Mode with Static RP and MSDP on Spine(s)
!
ip multicast-routing
!
interface FortyGigabitEthernet1/1/1
ip pim sparse-mode
!
interface FortyGigabitEthernet1/1/2
ip pim sparse-mode
!
ip pim rp-address 10.103.255.255
!
OSPF to Core (Underlay)
!
interface GigabitEthernet1/0/1
description Trunk to NYC-Core1 TenGigabitEthernet1/0/14
no switchport
no ip address
cts manual
policy static sgt 2 trusted
!
interface GigabitEthernet1/0/1.10
description To NYC-Core1 TenGigabitEthernet1/0/14.10 Underlay Handoff
encapsulation dot1Q 10
ip address 10.103.224.2 255.255.255.252
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
BGP to Core (Underlay)
!
bfd interval 100 min_rx 100 multiplier 3
!
! BGP for Underlay to Core
!
router bgp 65106
!
neighbor 10.103.224.1 remote-as 65100
neighbor 10.103.224.1 fall-over bfd
!
address-family ipv4
network 10.103.255.3 mask 255.255.255.255
network 10.103.224.3 mask 255.255.255.252
aggregate-address 10.103.255.0 255.255.255.0 summary-only
aggregate-address 10.103.224.0 255.255.255.0 summary-only
!
neighbor 10.103.224.1 activate
neighbor 10.103.224.1 route-map bgp-underlay-in-from-core in
neighbor 10.103.224.1 route-map bgp-underlay-out-to-core out
!
ip prefix-list bgp-underlay-in-from-core seq 5 permit 0.0.0.0/0
!
ip prefix-list bgp-underlay-out-to-core seq 5 permit 10.103.255.0/24
ip prefix-list bgp-underlay-out-to-core seq 10 permit 10.103.224.0/24
!
route-map bgp-underlay-out-to-core permit 10
match ip address prefix-list bgp-underlay-out-to-core
!
route-map bgp-underlay-in-from-core permit 10
match ip address prefix-list bgp-underlay-in-from-core
!
Note: In the above Border configuration, a prefix-list has been added to filter routes exchanged between the underlay and the core (external) network. Only a default route is allowed to the underlay from the core, and summary routes are allowed to the core from the underlay. Please adjust this based on your actual requirements if needed.
Add Campus VRF
!
vrf definition campus
rd 65106:3
!
address-family ipv4
route-target export 65106:1
route-target import 65106:1
route-target export 65106:1 stitching
route-target import 65106:1 stitching
exit-address-family
!
Add Campus Handoff to Core (Overlay)
!
interface GigabitEthernet1/0/2
description Trunk to NYC-DC-Handoff te1/0/4 for Overlays
no switchport
mtu 9000
no ip address
cts manual
policy static sgt 2 trusted
bfd interval 100 min_rx 100 multiplier 3
!
interface GigabitEthernet1/0/2.3001
description Campus Overlay Handoff
encapsulation dot1Q 3001
vrf forwarding campus
ip address 10.103.64.2 255.255.255.252
bfd interval 100 min_rx 100 multiplier 3
!
Add Campus BGP to Core (Overlay)
!
router bgp 65106
neighbor 10.103.64.1 remote-as 65102
neighbor 10.103.64.1 fall-over bfd
!
address-family ipv4 vrf campus
advertise l2vpn evpn
network 10.103.64.0 mask 255.255.255.252
aggregate-address 10.103.64.0 255.255.192.0 summary-only
aggregate-address 10.103.128.0 255.255.192.0 summary-only
!
neighbor 10.103.64.1 remote-as 65102
neighbor 10.103.64.1 fall-over bfd
neighbor 10.103.64.1 activate
neighbor 10.103.64.1 route-map bgp-campus-in-from-core in
neighbor 10.103.64.1 route-map bgp-campus-out-to-core out
!
ip prefix-list bgp-campus-in-from-core seq 5 permit 0.0.0.0/0
!
ip prefix-list bgp-campus-out-to-core seq 5 permit 10.103.64.0/18
ip prefix-list bgp-campus-out-to-core seq 10 permit 10.103.128.0/18
!
route-map bgp-campus-in-from-fusion permit 10
match ip address prefix-list bgp-campus-in-from-core
!
route-map bgp-campus-out-to-fusion permit 10
match ip address prefix-list bgp-campus-out-to-core
!
Setup L3 VNIs to allow Campus routing across the Underlay
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
VLAN 3001
name Campus-VRF-L3VNI
!
interface Vlan3001
vrf forwarding campus
ip unnumbered Loopback0
no autostate
!
vlan configuration 3001
member vni 303001
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 303001 vrf campus
!
Add Guest VRF
!
vrf definition guest
rd 65106:23
!
address-family ipv4
route-target export 65106:2
route-target import 65106:2
route-target export 65106:2 stitching
route-target import 65106:2 stitching
exit-address-family
!
Add Guest Handoff to Core (Overlay)
!
interface GigabitEthernet1/0/2.3002
description Guest Overlay Handoff
encapsulation dot1Q 3002
vrf forwarding guest
ip address 10.103.64.10 255.255.255.252
bfd interval 100 min_rx 100 multiplier 3
!
Add Guest BGP to Core (Overlay)
!
router bgp 65106
neighbor 10.103.64.9 remote-as 65102
neighbor 10.103.64.9 fall-over bfd
!
address-family ipv4 vrf guest
advertise l2vpn evpn
network 10.103.64.8 mask 255.255.255.252
!
neighbor 10.103.64.9 remote-as 65102
neighbor 10.103.64.9 fall-over bfd
neighbor 10.103.64.9 activate
neighbor 10.103.64.9 route-map bgp-campus-in-from-core in
neighbor 10.103.64.9 route-map bgp-campus-out-to-core out
!
ip prefix-list bgp-campus-in-from-core seq 5 permit 0.0.0.0/0
!
ip prefix-list bgp-campus-out-to-core seq 5 permit 10.103.220.0/24
!
route-map bgp-campus-in-from-core permit 10
match ip address prefix-list bgp-campus-in-from-core
!
route-map bgp-campus-out-to-core permit 10
match ip address prefix-list bgp-campus-out-to-core
!
Setup L3 VNIs to allow routing across the Underlay
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
VLAN 3002
name Guest-VRF-L3VNI
!
interface Vlan3002
vrf forwarding guest
ip unnumbered Loopback0
no autostate
!
vlan configuration 3002
member vni 303002
!
!
interface nve1
member vni 303002 vrf guest
!
Border Leaf 2
Base Configuration
!
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
!
hostname NYC103-Border-02
!
clock timezone EST -5 0
clock summer-time EDT recurring
!
ip routing
!
ip name-server 10.100.0.5 10.200.0.5
ip domain name ciscovalidated.com
!
license boot level network-advantage addon dna-advantage
!
system mtu 9198
!
errdisable recovery cause bpduguard
errdisable recovery interval 60
!
enable secret **masked**
!
username admin privilege 15 secret **masked**
!
no ip http server
no ip http secure-server
!
line con 0
exec-timeout 60 0
privilege level 15
logging synchronous
login local
!
line vty 0 31
exec-timeout 60 0
privilege level 15
logging synchronous
login local
transport input telnet ssh
!
aaa new-model
!
interface Loopback0
description Primary loopback
ip address 10.103.255.4 255.255.255.255
!
ntp source Loopback0
ntp server 10.100.0.5 prefer
!
Underlay Links (excluding OSPF and Multicast)
!
! Border to Spine
!
interface FortyGigabitEthernet1/1/1
description To NYC103-Spine-01 HundredGigE1/0/26
no switchport
ip address 10.103.224.22 255.255.255.252
speed nonegotiate
speed 40000
!
interface FortyGigabitEthernet1/1/2
description To NYC103-Spine-02 HundredGigE1/0/26
no switchport
ip address 10.103.224.14 255.255.255.252
speed nonegotiate
speed 40000
!
OSPF on Underlay links and Loopback0
!
router ospf 1
router-id 10.103.255.4
auto-cost reference-bandwidth 100000
default-information originate metric 1000 metric-type 1
bfd all-interfaces
!
interface Loopback0
ip ospf 1 area 0
!
interface FortyGigabitEthernet1/1/1
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface FortyGigabitEthernet1/1/2
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
BGP and Address Family for L2VPN EVPN
!
router bgp 65106
!
bgp router-id 10.103.255.4
bgp log-neighbor-changes
no bgp default ipv4-unicast
!
template peer-session spine-ps
remote-as 65106
update-source Loopback0
fall-over bfd
exit-peer-session
!
neighbor 10.103.255.1 inherit peer-session spine-ps
neighbor 10.103.255.2 inherit peer-session spine-ps
!
address-family l2vpn evpn
neighbor 10.103.255.1 activate
neighbor 10.103.255.1 send-community both
neighbor 10.103.255.2 activate
neighbor 10.103.255.2 send-community both
exit-address-family
!
Multicast; IP PIM Sparse Mode with Static RP and MSDP on Spine(s)
!
ip multicast-routing
!
interface FortyGigabitEthernet1/1/1
ip pim sparse-mode
!
interface FortyGigabitEthernet1/1/2
ip pim sparse-mode
!
ip pim rp-address 10.103.255.255
!
OSPF to Core (Underlay)
!
interface GigabitEthernet1/0/1
description Trunk to NYC-Core2 TenGigabitEthernet1/0/14
no switchport
no ip address
cts manual
policy static sgt 2 trusted
!
interface GigabitEthernet1/0/1.10
description To NYC-Core2 TenGigabitEthernet1/0/14.10 Underlay Handoff
encapsulation dot1Q 10
ip address 10.103.224.6 255.255.255.252
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
BGP to Core (Underlay)
!
bfd interval 100 min_rx 100 multiplier 3
!
! BGP for Underlay to Core
!
router bgp 65106
!
neighbor 10.103.224.5 remote-as 65100
neighbor 10.103.224.5 fall-over bfd
!
address-family ipv4
network 10.103.255.4 mask 255.255.255.255
network 10.103.224.4 mask 255.255.255.252
aggregate-address 10.103.255.0 255.255.255.0 summary-only
aggregate-address 10.103.224.0 255.255.255.0 summary-only
!
neighbor 10.103.224.5 activate
neighbor 10.103.224.5 route-map bgp-underlay-in-from-core in
neighbor 10.103.224.5 route-map bgp-underlay-out-to-core out
!
ip prefix-list bgp-underlay-in-from-core seq 5 permit 0.0.0.0/0
!
ip prefix-list bgp-underlay-out-to-core seq 5 permit 10.103.255.0/24
ip prefix-list bgp-underlay-out-to-core seq 10 permit 10.103.224.0/24
!
route-map bgp-underlay-out-to-core permit 10
match ip address prefix-list bgp-underlay-out-to-core
!
route-map bgp-underlay-in-from-core permit 10
match ip address prefix-list bgp-underlay-in-from-core
!
Note: In the above Border configuration, a prefix-list has been added to filter routes exchanged between the underlay and the core (external) network. Only a default route is allowed to the underlay from the core, and summary routes are allowed to the core from the underlay. Please adjust this based on your actual requirements if needed.
Add Campus VRF
!
vrf definition campus
rd 65106:4
!
address-family ipv4
route-target export 65106:1
route-target import 65106:1
route-target export 65106:1 stitching
route-target import 65106:1 stitching
exit-address-family
!
Add Campus Handoff to Core (Overlay)
!
interface GigabitEthernet1/0/2
description Trunk to NYC-DC-Handoff te1/0/5 for Overlays
no switchport
mtu 9000
no ip address
cts manual
policy static sgt 2 trusted
bfd interval 100 min_rx 100 multiplier 3
!
interface GigabitEthernet1/0/2.3001
description Campus Overlay Handoff
encapsulation dot1Q 3001
vrf forwarding campus
ip address 10.103.64.6 255.255.255.252
bfd interval 100 min_rx 100 multiplier 3
!
Add Campus BGP to Core (Overlay)
!
router bgp 65106
neighbor 10.103.64.5 remote-as 65102
neighbor 10.103.64.5 fall-over bfd
!
address-family ipv4 vrf campus
advertise l2vpn evpn
network 10.103.64.4 mask 255.255.255.252
aggregate-address 10.103.64.0 255.255.192.0 summary-only
aggregate-address 10.103.128.0 255.255.192.0 summary-only
!
neighbor 10.103.64.5 remote-as 65102
neighbor 10.103.64.5 fall-over bfd
neighbor 10.103.64.5 activate
neighbor 10.103.64.5 route-map bgp-campus-in-from-core in
neighbor 10.103.64.5 route-map bgp-campus-out-to-core out
!
ip prefix-list bgp-campus-in-from-core seq 5 permit 0.0.0.0/0
!
ip prefix-list bgp-campus-out-to-core seq 5 permit 10.103.64.0/18
ip prefix-list bgp-campus-out-to-core seq 10 permit 10.103.128.0/18
!
route-map bgp-campus-in-from-fusion permit 10
match ip address prefix-list bgp-campus-in-from-core
!
route-map bgp-campus-out-to-fusion permit 10
match ip address prefix-list bgp-campus-out-to-core
!
Setup L3 VNIs to allow Campus routing across the Underlay
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
VLAN 3001
name Campus-VRF-L3VNI
!
interface Vlan3001
vrf forwarding campus
ip unnumbered Loopback0
no autostate
!
vlan configuration 3001
member vni 303001
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 303001 vrf campus
!
Add Guest VRF
!
vrf definition guest
rd 65106:24
!
address-family ipv4
route-target export 65106:2
route-target import 65106:2
route-target export 65106:2 stitching
route-target import 65106:2 stitching
exit-address-family
!
Add Guest Handoff to Core (Overlay)
!
interface GigabitEthernet1/0/2.3002
description Guest Overlay Handoff
encapsulation dot1Q 3002
vrf forwarding guest
ip address 10.103.64.14 255.255.255.252
bfd interval 100 min_rx 100 multiplier 3
!
Add Guest BGP to Core (Overlay)
!
router bgp 65106
neighbor 10.103.64.13 remote-as 65102
neighbor 10.103.64.13 fall-over bfd
!
address-family ipv4 vrf guest
advertise l2vpn evpn
network 10.103.64.12 mask 255.255.255.252
!
neighbor 10.103.64.13 remote-as 65102
neighbor 10.103.64.13 fall-over bfd
neighbor 10.103.64.13 activate
neighbor 10.103.64.13 route-map bgp-campus-in-from-core in
neighbor 10.103.64.13 route-map bgp-campus-out-to-core out
!
ip prefix-list bgp-campus-in-from-core seq 5 permit 0.0.0.0/0
!
ip prefix-list bgp-campus-out-to-core seq 5 permit 10.103.220.0/24
!
route-map bgp-campus-in-from-core permit 10
match ip address prefix-list bgp-campus-in-from-core
!
route-map bgp-campus-out-to-core permit 10
match ip address prefix-list bgp-campus-out-to-core
!
Setup L3 VNIs to allow Guest routing across the Underlay
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
VLAN 3002
name Guest-VRF-L3VNI
!
interface Vlan3002
vrf forwarding guest
ip unnumbered Loopback0
no autostate
!
vlan configuration 3002
member vni 303002
!
interface nve1
member vni 303002 vrf guest
!
Leaf Switches
Please use the following template to configure your Fabric Leaf Switch(es)
Leaf 1
Base Configuration
!
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
!
hostname NYC103-Leaf-01
!
clock timezone EST -5 0
clock summer-time EDT recurring
!
ip routing
!
ip name-server 10.100.0.5 10.200.0.5
ip domain name ciscovalidated.com
!
license boot level network-advantage addon dna-advantage
!
system mtu 9198
!
errdisable recovery cause bpduguard
errdisable recovery interval 60
!
enable secret **masked**
!
username admin privilege 15 secret **masked**
!
no ip http server
no ip http secure-server
!
line con 0
exec-timeout 60 0
privilege level 15
logging synchronous
login local
!
line vty 0 31
exec-timeout 60 0
privilege level 15
logging synchronous
login local
transport input telnet ssh
!
aaa new-model
!
interface Loopback0
description Primary loopback
ip address 10.103.255.11 255.255.255.255
!
ntp source Loopback0
ntp server 10.100.0.5 prefer
!
lldp run
!
Underlay Links (excluding OSPF and Multicast)
! Leaf to Spine
!
interface TwentyFiveGigE1/1/1
description To NYC-Spine-01 TwentyFiveGigE1/0/1
no switchport
ip address 10.103.224.30 255.255.255.252
!
interface TwentyFiveGigE1/1/2
description To NYC-Spine-02 TwentyFiveGigE1/0/1
no switchport
ip address 10.103.224.34 255.255.255.252
!
OSPF on Underlay links and Loopback0
!
router ospf 1
router-id 10.103.255.11
auto-cost reference-bandwidth 100000
bfd all-interfaces
!
interface Loopback0
ip ospf 1 area 0
!
interface TwentyFiveGigE1/1/1
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface TwentyFiveGigE1/1/2
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
BGP and Address Family for L2VPN EVPN
!
router bgp 65106
!
bgp router-id 10.103.255.11
bgp log-neighbor-changes
no bgp default ipv4-unicast
!
template peer-session spine-ps
remote-as 65106
update-source Loopback0
fall-over bfd
exit-peer-session
!
neighbor 10.103.255.1 inherit peer-session spine-ps
neighbor 10.103.255.2 inherit peer-session spine-ps
!
address-family l2vpn evpn
neighbor 10.103.255.1 activate
neighbor 10.103.255.1 send-community both
neighbor 10.103.255.2 activate
neighbor 10.103.255.2 send-community both
exit-address-family
!
Multicast; IP PIM Sparse Mode with Static RP and MSDP
!
ip multicast-routing
!
interface TwentyFiveGigE1/1/1
ip pim sparse-mode
!
interface TwentyFiveGigE1/1/2
ip pim sparse-mode
!
ip pim rp-address 10.103.255.255
!
Add Campus VRF
!
vrf definition campus
rd 65106:11
!
address-family ipv4
route-target export 65106:1
route-target import 65106:1
route-target export 65106:1 stitching
route-target import 65106:1 stitching
exit-address-family
!
BGP for Campus IPV4 VRF
!
router bgp 65106
!
address-family ipv4 vrf campus
advertise l2vpn evpn
redistribute connected
exit-address-family
!
Enable Management L2VPN EVPN and VXLAN mapping
!
l2vpn evpn
replication-type static
router-id Loopback0
!
vlan 1
name Management
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration 1
member evpn-instance 1 vni 200001
!
Add NVE1 and VNI Mapping for Management
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 200001 mcast-group 225.0.0.1
!
DAG and DHCP settings via Underlay with Option 82 for Management
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration 1
member evpn-instance 1 vni 200001
!
interface Vlan1
description Meraki Mgt Distributed Anycast Gateway
mac-address 0000.0000.0001
vrf forwarding campus
ip address 10.103.64.1 255.255.255.0
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
Enable Corp L2VPN EVPN and VXLAN mapping
!
l2vpn evpn
replication-type static
router-id Loopback0
!
vlan 120
name Employee
!
l2vpn evpn instance 120 vlan-based
encapsulation vxlan
!
vlan configuration 120
member evpn-instance 120 vni 200120
!
NVE1 to VNI mapping for Corp
!
interface nve1
member vni 200120 mcast-group 225.0.0.120
!
DAG and DHCP settings via Underlay with Option 82 for Corp VLAN
!
interface Vlan120
description Employee Distributed Anycast Gateway
mac-address 0000.0000.0120
vrf forwarding campus
ip address 10.103.120.1 255.255.255.0
!
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
ip dhcp relay information option
ip dhcp relay information option vpn
!
Note: Please note that both ip dhcp relay information option and ip dhcp relay information option vpn are needed with IOS XE prior to 17.9.x. This is however not required with later IOS XE releases.
Enable IoT L2VPN EVPN and VXLAN mapping
!
vlan 180
name IoT
!
l2vpn evpn instance 180 vlan-based
encapsulation vxlan
!
vlan configuration 180
member evpn-instance 180 vni 200180
!
NVE1 to VNI mapping for IoT
!
interface nve1
member vni 200180 mcast-group 225.0.0.120
!
DAG and DHCP settings via Underlay with Option 82 for IoT VLAN
!
interface Vlan180
description IoT Distributed Anycast Gateway
mac-address 0000.0000.0180
vrf forwarding campus
ip address 10.103.180.1 255.255.255.0
!
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
ip dhcp relay information option
ip dhcp relay information option vpn
!
Note: Please note that both ip dhcp relay information option and ip dhcp relay information option vpn are needed with IOS XE prior to 17.9.x. This is however not required with later IOS XE releases.
Setup L3 VNIs to allow routing across the Underlay for Campus
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
!
VLAN 3001
name Campus-VRF-L3VNI
!
interface Vlan3001
vrf forwarding campus
ip unnumbered Loopback0
no autostate
!
vlan configuration 3001
member vni 303001
!
interface nve1
member vni 303001 vrf campus
!
Add Guest VRF
!
vrf definition guest
rd 65106:211
!
address-family ipv4
route-target export 65106:2
route-target import 65106:2
route-target export 65106:2 stitching
route-target import 65106:2 stitching
exit-address-family
!
BGP for Guest IPV4 VRF
!
router bgp 65106
!
address-family ipv4 vrf guest
advertise l2vpn evpn
redistribute connected
exit-address-family
!
Enable Guest L2VPN EVPN and VXLAN mapping
!
vlan 220
name Guest
!
l2vpn evpn instance 220 vlan-based
encapsulation vxlan
!
vlan configuration 220
member evpn-instance 220 vni 200220
!
NVE1 to VNI mapping for Guest
!
interface nve1
member vni 200220 mcast-group 225.0.0.120
!
DAG and DHCP settings via Underlay with Option 82 for Guest VLAN
!
interface Vlan220
description Guest Distributed Anycast Gateway
mac-address 0000.0000.0220
vrf forwarding guest
ip address 10.103.220.1 255.255.255.0
!
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
ip dhcp relay information option
ip dhcp relay information option vpn
!
Note: Please note that both ip dhcp relay information option and ip dhcp relay information option vpn are needed with IOS XE prior to 17.9.x. This is however not required with later IOS XE releases.
Setup L3 VNIs to allow routing across the Underlay for Guest
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
!
VLAN 3002
name Guest-VRF-L3VNI
!
interface Vlan3002
vrf forwarding guest
ip unnumbered Loopback0
no autostate
!
vlan configuration 3002
member vni 303002
!
interface nve1
member vni 303002 vrf guest
!
Downlinks to Access Layer
!
interface GigabitEthernet1/0/47
description Trunk to NYC103-FL01-SW01 port 23
switchport trunk allowed vlan 1-3000,3003-4096
switchport mode trunk
switchport nonegotiate
!
interface GigabitEthernet1/0/48
description Trunk to NYC103-FL01-SW01 port 24
switchport trunk allowed vlan 1-3000,3003-4096
switchport mode trunk
switchport nonegotiate
!
Tech tip: The above configuration for the Leaf downlinks to Access layer suggests allowing all supported VLANs to facilitate adding new services (e.g. new SSIDs) in the future. However, it is also possible to prune un-used VLANs if that’s a requirement.
Note: Cloud Managed Switches (-M models) supports a maximum of 1000 VLANs. The above downlink configuration has all non-reserved VLANs allowed on the Downlink Trunks such that if a new service is created (e.g. new SSID, new VLAN) on the downstream network it then needs to be added to the Cloud Managed Switch Uplink(s) without the need to adjust the Leaf switch.
Enable Inline Tagging
!
interface GigabitEthernet1/0/47
cts manual
policy static sgt 2 trusted
!
interface GigabitEthernet1/0/48
cts manual
policy static sgt 2 trusted
!
Enable Spanning-Tree with Bridge Priority and enable Root Guard
!
spanning-tree mst configuration
name region1
revision 1
exit
!
spanning-tree mst 0 priority 4096
!
interface GigabitEthernet1/0/47
spanning-tree guard root
!
interface GigabitEthernet1/0/48
spanning-tree guard root
!
Note: At this stage, you can plug the Access Switches and Access Points to Leaf 1 and wait for them to come online in Dashboard. Connect uplinks on the Access Points to Access switch and connect uplinks on Access switch to Leaf switch. Power on all devices and wait for them to come online in Dashboard.
Note: Please note that it might take a few minutes for the switches to download their configuration and firmware and reboot before they come steady online in Dashboard.
Configure Ether Channel for Access Switch (where applicable)
!
interface GigabitEthernet1/0/47
description Trunk to NYC103-FL01-SW01 port 23 in LACP Channel Group 1
channel-group 1 mode active
!
interface GigabitEthernet1/0/48
description Trunk to NYC103-FL01-SW01 port 24 in LACP Channel Group 1
channel-group 1 mode active
!
interface port-channel 1
description LACP Channel Group to NYC103-FL01-SW01 on ports 47-48
!
Leaf 2
Base Configuration
!
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
!
hostname NYC103-Leaf-02
!
clock timezone EST -5 0
clock summer-time EDT recurring
!
ip routing
!
ip name-server 10.100.0.5 10.200.0.5
ip domain name ciscovalidated.com
!
license boot level network-advantage addon dna-advantage
!
system mtu 9198
!
errdisable recovery cause bpduguard
errdisable recovery interval 60
!
enable secret **masked**
!
username admin privilege 15 secret **masked**
!
no ip http server
no ip http secure-server
!
line con 0
exec-timeout 60 0
privilege level 15
logging synchronous
login local
line vty 0 31
exec-timeout 60 0
privilege level 15
logging synchronous
login local
transport input telnet ssh
!
aaa new-model
!
interface Loopback0
description Primary loopback
ip address 10.103.255.12 255.255.255.255
!
ntp source Loopback0
ntp server 10.100.0.5 prefer
!
lldp run
!
Underlay Links (excluding OSPF and Multicast)
! Leaf to Spine
!
interface GigabitEthernet1/0/1
description To NYC103-Spine-01 TwentyFiveGigE1/0/2
no switchport
ip address 10.103.224.38 255.255.255.252
!
interface GigabitEthernet1/0/2
description To NYC103-Spine-02 TwentyFiveGigE1/0/2
no switchport
ip address 10.103.224.42 255.255.255.252
!
OSPF on Underlay links and Loopback0
!
router ospf 1
router-id 10.103.255.12
auto-cost reference-bandwidth 100000
bfd all-interfaces
!
interface Loopback0
ip ospf 1 area 0
!
interface GigabitEthernet1/0/1
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface GigabitEthernet1/0/2
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
BGP and Address Family for L2VPN EVPN
!
router bgp 65106
!
bgp router-id 10.103.255.12
bgp log-neighbor-changes
no bgp default ipv4-unicast
!
template peer-session spine-ps
remote-as 65106
update-source Loopback0
fall-over bfd
exit-peer-session
!
neighbor 10.103.255.1 inherit peer-session spine-ps
neighbor 10.103.255.2 inherit peer-session spine-ps
!
address-family l2vpn evpn
neighbor 10.103.255.1 activate
neighbor 10.103.255.1 send-community both
neighbor 10.103.255.2 activate
neighbor 10.103.255.2 send-community both
exit-address-family
!
Multicast; IP PIM Sparse Mode with Static RP and MSDP
!
ip multicast-routing
!
interface GigabitEthernet1/0/1
ip pim sparse-mode
!
interface GigabitEthernet1/0/2
ip pim sparse-mode
!
ip pim rp-address 10.103.255.255
!
Add Campus VRF
!
vrf definition campus
rd 65106:12
!
address-family ipv4
route-target export 65106:1
route-target import 65106:1
route-target export 65106:1 stitching
route-target import 65106:1 stitching
exit-address-family
!
BGP for Campus IPV4 VRF
!
router bgp 65106
!
address-family ipv4 vrf campus
advertise l2vpn evpn
redistribute connected
exit-address-family
!
Enable Management L2VPN EVPN and VXLAN mapping
!
l2vpn evpn
replication-type static
router-id Loopback0
!
vlan 1
name Management
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration 1
member evpn-instance 1 vni 200001
!
Add NVE1 and VNI Mapping for Management
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 200001 mcast-group 225.0.0.1
!
DAG and DHCP settings via Underlay with Option 82 for Management
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration 1
member evpn-instance 1 vni 200001
!
interface Vlan1
description Meraki Mgt Distributed Anycast Gateway
mac-address 0000.0000.0001
vrf forwarding campus
ip address 10.103.64.1 255.255.255.0
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
Enable Corp L2VPN EVPN and VXLAN mapping
!
l2vpn evpn
replication-type static
router-id Loopback0
!
vlan 120
name Employee
!
l2vpn evpn instance 120 vlan-based
encapsulation vxlan
!
vlan configuration 120
member evpn-instance 120 vni 200120
!
NVE1 to VNI mapping for Corp
!
interface nve1
member vni 200120 mcast-group 225.0.0.120
!
DAG and DHCP settings via Underlay with Option 82 for Corp VLAN
!
interface Vlan120
description Employee Distributed Anycast Gateway
mac-address 0000.0000.0120
vrf forwarding campus
ip address 10.103.120.1 255.255.255.0
!
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
ip dhcp relay information option
ip dhcp relay information option vpn
!
Enable IoT L2VPN EVPN and VXLAN mapping
!
vlan 180
name IoT
!
l2vpn evpn instance 180 vlan-based
encapsulation vxlan
!
vlan configuration 180
member evpn-instance 180 vni 200180
!
NVE1 to VNI mapping for IoT
!
interface nve1
member vni 200180 mcast-group 225.0.0.120
!
DAG and DHCP settings via Underlay with Option 82 for IoT VLAN
!
interface Vlan180
description IoT Distributed Anycast Gateway
mac-address 0000.0000.0180
vrf forwarding campus
ip address 10.103.180.1 255.255.255.0
!
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
ip dhcp relay information option
ip dhcp relay information option vpn
!
Setup L3 VNIs to allow routing across the Underlay for Campus
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
!
VLAN 3001
name Campus-VRF-L3VNI
!
interface Vlan3001
vrf forwarding campus
ip unnumbered Loopback0
no autostate
!
!
vlan configuration 3001
member vni 303001
!
!
interface nve1
member vni 303001 vrf campus
!
Add Guest VRF
!
vrf definition guest
rd 65106:212
!
address-family ipv4
route-target export 65106:2
route-target import 65106:2
route-target export 65106:2 stitching
route-target import 65106:2 stitching
exit-address-family
!
BGP for Guest IPV4 VRF
!
router bgp 65106
!
address-family ipv4 vrf guest
advertise l2vpn evpn
redistribute connected
exit-address-family
!
Enable Guest L2VPN EVPN and VXLAN mapping
!
vlan 220
name Guest
!
l2vpn evpn instance 220 vlan-based
encapsulation vxlan
!
vlan configuration 220
member evpn-instance 220 vni 200220
!
NVE1 to VNI mapping for Guest
!
interface nve1
member vni 200220 mcast-group 225.0.0.120
!
DAG and DHCP settings via Underlay with Option 82 for Guest VLAN
!
interface Vlan220
description Guest Distributed Anycast Gateway
mac-address 0000.0000.0220
vrf forwarding guest
ip address 10.103.220.1 255.255.255.0
!
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
ip dhcp relay information option
ip dhcp relay information option vpn
!
Setup L3 VNIs to allow routing across the Underlay for Guest
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
!
VLAN 3002
name Guest-VRF-L3VNI
!
interface Vlan3002
vrf forwarding guest
ip unnumbered Loopback0
no autostate
!
vlan configuration 3002
member vni 303002
!
interface nve1
member vni 303002 vrf guest
!
Downlinks to Access Layer
!
interface GigabitEthernet1/0/47
description Trunk to NYC103-FL02-SW02 port 23
switchport trunk allowed vlan 1-3000,3003-4096
switchport mode trunk
switchport nonegotiate
!
interface GigabitEthernet1/0/48
description Trunk to NYC103-FL02-SW01 port 24
switchport trunk allowed vlan 1-3000,3003-4096
switchport mode trunk
switchport nonegotiate
!
Enable Inline Tagging
!
interface GigabitEthernet1/0/47
cts manual
policy static sgt 2 trusted
!
interface GigabitEthernet1/0/48
cts manual
policy static sgt 2 trusted
!
Enable Spanning-Tree with Bridge Priority and enable Root Guard
!
spanning-tree mst configuration
name region1
revision 1
exit
!
spanning-tree mst 0 priority 4096
!
interface GigabitEthernet1/0/47
spanning-tree guard root
!
interface GigabitEthernet1/0/48
spanning-tree guard root
!
Note: At this stage, you can plug the Access Switches and Access Points to Leaf 2 and wait for them to come online in Dashboard. Connect uplinks on the Access Points to Access switch and connect uplinks on Access switch to Leaf switch. Power on all devices and wait for them to come online in Dashboard.
Note: Please note that it might take a few minutes for the switches to download their configuration and firmware and reboot before they come steady online in Dashboard.
Leaf 3
Base Configuration
!
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
!
hostname NYC103-Leaf-03
!
clock timezone EST -5 0
clock summer-time EDT recurring
!
ip routing
!
ip name-server 10.100.0.5 10.200.0.5
ip domain name ciscovalidated.com
!
license boot level network-advantage addon dna-advantage
!
system mtu 9198
!
errdisable recovery cause bpduguard
errdisable recovery interval 60
!
enable secret **masked**
!
username admin privilege 15 secret **masked**
!
no ip http server
no ip http secure-server
!
line con 0
exec-timeout 60 0
privilege level 15
logging synchronous
login local
!
line vty 0 31
exec-timeout 60 0
privilege level 15
logging synchronous
login local
transport input telnet ssh
!
aaa new-model
!
interface Loopback0
description Primary loopback
ip address 10.103.255.13 255.255.255.255
!
ntp source Loopback0
ntp server 10.100.0.5 prefer
!
lldp run
!
Underlay Links (excluding OSPF and Multicast)
! Leaf to Spine
!
interface GigabitEthernet1/0/1
description To NYC103-Spine-01 TwentyFiveGigE1/0/3
no switchport
ip address 10.103.224.46 255.255.255.252
!
interface GigabitEthernet1/0/2
description To NYC103-Spine-02 TwentyFiveGigE1/0/3
no switchport
ip address 10.103.224.50 255.255.255.252
!
OSPF on Underlay links and Loopback0
!
router ospf 1
router-id 10.103.255.13
auto-cost reference-bandwidth 100000
bfd all-interfaces
!
interface Loopback0
ip ospf 1 area 0
!
interface GigabitEthernet1/0/1
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface GigabitEthernet1/0/2
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
BGP and Address Family for L2VPN EVPN
!
router bgp 65106
!
bgp router-id 10.103.255.13
bgp log-neighbor-changes
no bgp default ipv4-unicast
!
template peer-session spine-ps
remote-as 65106
update-source Loopback0
fall-over bfd
exit-peer-session
!
neighbor 10.103.255.1 inherit peer-session spine-ps
neighbor 10.103.255.2 inherit peer-session spine-ps
!
address-family l2vpn evpn
neighbor 10.103.255.1 activate
neighbor 10.103.255.1 send-community both
neighbor 10.103.255.2 activate
neighbor 10.103.255.2 send-community both
exit-address-family
!
Multicast; IP PIM Sparse Mode with Static RP and MSDP
!
ip multicast-routing
!
interface GigabitEthernet1/0/1
ip pim sparse-mode
!
interface GigabitEthernet1/0/2
ip pim sparse-mode
!
ip pim rp-address 10.103.255.255
!
Add Campus VRF
!
vrf definition campus
rd 65106:13
!
address-family ipv4
route-target export 65106:1
route-target import 65106:1
route-target export 65106:1 stitching
route-target import 65106:1 stitching
exit-address-family
!
BGP for Campus IPV4 VRF
!
router bgp 65106
!
address-family ipv4 vrf campus
advertise l2vpn evpn
redistribute connected
exit-address-family
!
Enable Management L2VPN EVPN and VXLAN mapping
!
l2vpn evpn
replication-type static
router-id Loopback0
!
vlan 1
name Management
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration 1
member evpn-instance 1 vni 200001
!
Add NVE1 and VNI Mapping for Management
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 200001 mcast-group 225.0.0.1
!
DAG and DHCP settings via Underlay with Option 82 for Management
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration 1
member evpn-instance 1 vni 200001
!
interface Vlan1
description Meraki Mgt Distributed Anycast Gateway
mac-address 0000.0000.0001
vrf forwarding campus
ip address 10.103.64.1 255.255.255.0
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
Enable Corp L2VPN EVPN and VXLAN mapping
!
l2vpn evpn
replication-type static
router-id Loopback0
!
vlan 120
name Employee
!
l2vpn evpn instance 120 vlan-based
encapsulation vxlan
!
vlan configuration 120
member evpn-instance 120 vni 200120
!
NVE1 to VNI mapping for Corp
!
interface nve1
member vni 200120 mcast-group 225.0.0.120
!
DAG and DHCP settings via Underlay with Option 82 for Corp VLAN
!
interface Vlan120
description Employee Distributed Anycast Gateway
mac-address 0000.0000.0120
vrf forwarding campus
ip address 10.103.120.1 255.255.255.0
!
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
ip dhcp relay information option
ip dhcp relay information option vpn
!
Enable IoT L2VPN EVPN and VXLAN mapping
!
vlan 180
name IoT
!
l2vpn evpn instance 180 vlan-based
encapsulation vxlan
!
vlan configuration 180
member evpn-instance 180 vni 200180
!
NVE1 to VNI mapping for IoT
!
interface nve1
member vni 200180 mcast-group 225.0.0.120
!
DAG and DHCP settings via Underlay with Option 82 for IoT VLAN
!
interface Vlan180
description IoT Distributed Anycast Gateway
mac-address 0000.0000.0180
vrf forwarding campus
ip address 10.103.180.1 255.255.255.0
!
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
ip dhcp relay information option
ip dhcp relay information option vpn
!
Setup L3 VNIs to allow routing across the Underlay for Campus
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
!
VLAN 3001
name Campus-VRF-L3VNI
!
interface Vlan3001
vrf forwarding campus
ip unnumbered Loopback0
no autostate
!
!
vlan configuration 3001
member vni 303001
!
!
interface nve1
member vni 303001 vrf campus
!
Add Guest VRF
!
vrf definition guest
rd 65106:213
!
address-family ipv4
route-target export 65106:2
route-target import 65106:2
route-target export 65106:2 stitching
route-target import 65106:2 stitching
exit-address-family
!
BGP for Guest IPV4 VRF
!
router bgp 65106
!
address-family ipv4 vrf guest
advertise l2vpn evpn
redistribute connected
exit-address-family
!
Enable Guest L2VPN EVPN and VXLAN mapping
!
vlan 220
name Guest
!
l2vpn evpn instance 220 vlan-based
encapsulation vxlan
!
vlan configuration 220
member evpn-instance 220 vni 200220
!
NVE1 to VNI mapping for Guest
!
interface nve1
member vni 200220 mcast-group 225.0.0.120
!
DAG and DHCP settings via Underlay with Option 82 for Guest VLAN
!
interface Vlan220
description Guest Distributed Anycast Gateway
mac-address 0000.0000.0220
vrf forwarding guest
ip address 10.103.220.1 255.255.255.0
!
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
ip dhcp relay information option
ip dhcp relay information option vpn
!
Setup L3 VNIs to allow routing across the Underlay for Guest
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
!
VLAN 3002
name Guest-VRF-L3VNI
!
interface Vlan3002
vrf forwarding guest
ip unnumbered Loopback0
no autostate
!
vlan configuration 3002
member vni 303002
!
interface nve1
member vni 303002 vrf guest
!
Downlinks to Access Layer
!
interface GigabitEthernet1/0/12
description To NYC103-Client36 Dot1x Capable
switchport access vlan 120
switchport mode access
switchport nonegotiate
spanning-tree portfast
spanning-tree bpduguard enable
!
interface GigabitEthernet1/0/13
description To NYC103-Client37 Dot1x Capable
switchport access vlan 120
switchport mode access
switchport nonegotiate
spanning-tree portfast
spanning-tree bpduguard enable
!
interface GigabitEthernet1/0/48
description Trunk to NYC103-FL03-AP01
switchport trunk allowed vlan 1-3000,3003-4096
switchport mode trunk
switchport nonegotiate
!
Enable Inline Tagging
!
interface GigabitEthernet1/0/48
cts manual
policy static sgt 2 trusted
!
Enable Spanning-Tree with Bridge Priority and enable Root Guard
!
spanning-tree mst configuration
name region1
revision 1
exit
!
spanning-tree mst 0 priority 4096
!
interface GigabitEthernet1/0/47
spanning-tree guard root
!
interface GigabitEthernet1/0/48
spanning-tree guard root
!
Note: At this stage, you can plug the Access Switches and Access Points to Leaf 3 and wait for them to come online in Dashboard. Connect uplinks on the Access Points to Access switch and connect uplinks on Access switch to Leaf switch. Power on all devices and wait for them to come online in Dashboard.
Note: Please note that it might take a few minutes for the switches to download their configuration and firmware and reboot before they come steady online in Dashboard.
Leaf 4
Base Configuration
!
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
!
hostname NYC103-Leaf-03
!
clock timezone EST -5 0
clock summer-time EDT recurring
!
ip routing
!
ip name-server 10.100.0.5 10.200.0.5
ip domain name ciscovalidated.com
!
license boot level network-advantage addon dna-advantage
!
system mtu 9198
!
errdisable recovery cause bpduguard
errdisable recovery interval 60
!
enable secret **masked**
!
username admin privilege 15 secret **masked**
!
no ip http server
no ip http secure-server
!
line con 0
exec-timeout 60 0
privilege level 15
logging synchronous
login local
!
line vty 0 31
exec-timeout 60 0
privilege level 15
logging synchronous
login local
transport input telnet ssh
!
aaa new-model
!
interface Loopback0
description Primary loopback
ip address 10.103.255.14 255.255.255.255
!
ntp source Loopback0
ntp server 10.100.0.5 prefer
!
lldp run
!
Underlay Links (excluding OSPF and Multicast)
! Leaf to Spine
!
interface TwentyFiveGigE1/1/1
description To NYC103-Spine-01 TwentyFiveGigE1/0/4
no switchport
ip address 10.103.224.54 255.255.255.252
!
interface TwentyFiveGigE1/1/2
description To NYC103-Spine-02 TwentyFiveGigE1/0/4
no switchport
ip address 10.103.224.58 255.255.255.252
!
OSPF on Underlay links and Loopback0
!
router ospf 1
router-id 10.103.255.14
auto-cost reference-bandwidth 100000
bfd all-interfaces
!
interface Loopback0
ip ospf 1 area 0
!
interface TwentyFiveGigE1/1/1
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
interface TwentyFiveGigE1/1/2
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
BGP and Address Family for L2VPN EVPN
!
router bgp 65106
!
bgp router-id 10.103.255.14
bgp log-neighbor-changes
no bgp default ipv4-unicast
!
template peer-session spine-ps
remote-as 65106
update-source Loopback0
fall-over bfd
exit-peer-session
!
neighbor 10.103.255.1 inherit peer-session spine-ps
neighbor 10.103.255.2 inherit peer-session spine-ps
!
address-family l2vpn evpn
neighbor 10.103.255.1 activate
neighbor 10.103.255.1 send-community both
neighbor 10.103.255.2 activate
neighbor 10.103.255.2 send-community both
exit-address-family
!
Multicast; IP PIM Sparse Mode with Static RP and MSDP
!
ip multicast-routing
!
interface TwentyFiveGigE1/1/1
ip pim sparse-mode
!
interface TwentyFiveGigE1/1/2
ip pim sparse-mode
!
ip pim rp-address 10.103.255.255
!
Add Campus VRF
!
vrf definition campus
rd 65106:14
!
address-family ipv4
route-target export 65106:1
route-target import 65106:1
route-target export 65106:1 stitching
route-target import 65106:1 stitching
exit-address-family
!
BGP for Campus IPV4 VRF
!
router bgp 65106
!
address-family ipv4 vrf campus
advertise l2vpn evpn
redistribute connected
exit-address-family
!
Enable Management L2VPN EVPN and VXLAN mapping
!
l2vpn evpn
replication-type static
router-id Loopback0
!
vlan 1
name Management
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration 1
member evpn-instance 1 vni 200001
!
Add NVE1 and VNI Mapping for Management
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 200001 mcast-group 225.0.0.1
!
DAG and DHCP settings via Underlay with Option 82 for Management
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration 1
member evpn-instance 1 vni 200001
!
interface Vlan1
description Meraki Mgt Distributed Anycast Gateway
mac-address 0000.0000.0001
vrf forwarding campus
ip address 10.103.64.1 255.255.255.0
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
Enable Corp L2VPN EVPN and VXLAN mapping
!
l2vpn evpn
replication-type static
router-id Loopback0
!
vlan 120
name Employee
!
l2vpn evpn instance 120 vlan-based
encapsulation vxlan
!
vlan configuration 120
member evpn-instance 120 vni 200120
!
NVE1 to VNI mapping for Corp
!
interface nve1
member vni 200120 mcast-group 225.0.0.120
!
DAG and DHCP settings via Underlay with Option 82 for Corp VLAN
!
interface Vlan120
description Employee Distributed Anycast Gateway
mac-address 0000.0000.0120
vrf forwarding campus
ip address 10.103.120.1 255.255.255.0
!
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
ip dhcp relay information option
ip dhcp relay information option vpn
!
Enable IoT L2VPN EVPN and VXLAN mapping
!
vlan 180
name IoT
!
l2vpn evpn instance 180 vlan-based
encapsulation vxlan
!
vlan configuration 180
member evpn-instance 180 vni 200180
!
NVE1 to VNI mapping for IoT
!
interface nve1
member vni 200180 mcast-group 225.0.0.120
!
DAG and DHCP settings via Underlay with Option 82 for IoT VLAN
!
interface Vlan180
description IoT Distributed Anycast Gateway
mac-address 0000.0000.0180
vrf forwarding campus
ip address 10.103.180.1 255.255.255.0
!
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
ip dhcp relay information option
ip dhcp relay information option vpn
!
Setup L3 VNIs to allow routing across the Underlay for Campus
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
!
VLAN 3001
name Campus-VRF-L3VNI
!
interface Vlan3001
vrf forwarding campus
ip unnumbered Loopback0
no autostate
!
!
vlan configuration 3001
member vni 303001
!
!
interface nve1
member vni 303001 vrf campus
!
Add Guest VRF
!
vrf definition guest
rd 65106:213
!
address-family ipv4
route-target export 65106:2
route-target import 65106:2
route-target export 65106:2 stitching
route-target import 65106:2 stitching
exit-address-family
!
BGP for Guest IPV4 VRF
!
router bgp 65106
!
address-family ipv4 vrf guest
advertise l2vpn evpn
redistribute connected
exit-address-family
!
Enable Guest L2VPN EVPN and VXLAN mapping
!
vlan 220
name Guest
!
l2vpn evpn instance 220 vlan-based
encapsulation vxlan
!
vlan configuration 220
member evpn-instance 220 vni 200220
!
NVE1 to VNI mapping for Guest
!
interface nve1
member vni 200220 mcast-group 225.0.0.120
!
DAG and DHCP settings via Underlay with Option 82 for Guest VLAN
!
interface Vlan220
description Guest Distributed Anycast Gateway
mac-address 0000.0000.0220
vrf forwarding guest
ip address 10.103.220.1 255.255.255.0
!
ip dhcp relay source-interface Loopback0
ip helper-address global 10.100.0.5
no autostate
!
ip dhcp relay information option
ip dhcp relay information option vpn
!
Setup L3 VNIs to allow routing across the Underlay for Guest
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
!
VLAN 3002
name Guest-VRF-L3VNI
!
interface Vlan3002
vrf forwarding guest
ip unnumbered Loopback0
no autostate
!
vlan configuration 3002
member vni 303002
!
interface nve1
member vni 303002 vrf guest
!
Downlinks to Access Layer
!
interface GigabitEthernet1/0/47
description Trunk to NYC103-FL04-SW01 port 23
switchport Trunk allowed vlan 1-3000,3003-4096
switchport mode trunk
switchport nonegotiate
!
interface GigabitEthernet1/0/48
description To Trunk to NYC103-FL04-SW03 port 24
switchport Trunk allowed vlan 1-3000,3003-4096
switchport mode trunk
switchport nonegotiate
!
Enable Inline Tagging
!
interface GigabitEthernet1/0/47
cts manual
policy static sgt 2 trusted
!
interface GigabitEthernet1/0/48
cts manual
policy static sgt 2 trusted
!
Enable Spanning-Tree with Bridge Priority and enable Root Guard
!
spanning-tree mst configuration
name region1
revision 1
exit
!
spanning-tree mst 0 priority 4096
!
interface GigabitEthernet1/0/47
spanning-tree guard root
!
interface GigabitEthernet1/0/48
spanning-tree guard root
!
Note: At this stage, you can plug the Access Switches and Access Points to Leaf 4 and wait for them to come online in Dashboard. Connect uplinks on the Access Points to Access switch and connect uplinks on Access switch to Leaf switch. Power on all devices and wait for them to come online in Dashboard.
Note: Please note that it might take a few minutes for the switches to download their configuration and firmware and reboot before they come steady online in Dashboard.
Configure Ether Channel for Access Switch (where applicable)
!
interface GigabitEthernet1/0/47
channel-group 1 mode active
!
interface GigabitEthernet1/0/48
channel-group 1 mode active
!
interface port-channel 1
description LACP Channel Group to NYC103-FL04-SW01 on ports 47-48
!
Note: The EtherChannel needs to be configured on the downstream 9200 switch first in passive mode.
Border Spine Switches
Please note that Border Spines are not part of the design outlined in this document as it consists of standalone Spine and Border Leaf switches. However, this is being provided for guidance in case the spine and border roles are being collapsed for a certain deployment (Please refer to below figure). The Border Spine template is provided below.
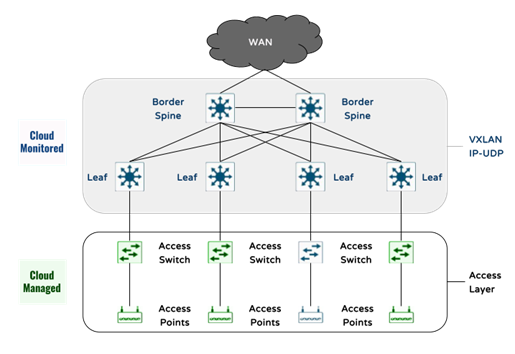
Please use the following template to configure your Fabric Border Spine Switch(es)
Border Spine Sample Configuration
Variables used in this template:
| Variable |
Value (Replace with your own values) |
| <hostname> |
|
| <TZ> |
|
| <UTC-offset-h> |
|
| <UTC-offset-m> |
|
| <DTZ> |
|
| <name-server-1> |
|
| <name-server-1> |
|
| <domain-name> |
|
| <enable-secret> |
|
| <admin-secret> |
|
| <Border-Spine-Loopback0-desc> |
|
| <Border-Spine-Loopback0-IP@> |
|
| <ntp-server> |
|
| <Border-Spine-underlay> |
|
| <Border-Spine-underlay-desc> |
|
| <<Border-Spine-underlay-IP@>> |
|
| <BGP-ASN> |
|
| <Leaf-Loopback0-IP@> |
|
| <msdp-IP@> |
|
| <rp-address> |
|
| <Border-Spine-underlay-to-core> |
|
| <Border-Spine-underlay-to-core-IP@> |
|
| <Core-IP@> |
|
| <underlay-network-to-core> |
|
| <underlay-network-to-core-mask> |
|
| <agg-underlay-network-to-core> |
|
| <agg-underlay-network-to-core-mask> |
|
| <from-core-to-underlay> |
|
| <to-core-from-underlay> |
|
| <agg-from-core-to-underlay> |
|
| <agg-to-core-to-underlay> |
|
| <VRF-name> |
|
| <RD> |
|
| <RT> |
|
| <overlay-network-to-core-VRF> |
|
| <overlay-network-to-core-VRF-mask> |
|
| <agg-overlay-network-to-core-VRF> |
|
| <agg-overlay-network-to-core-VRF-mask> |
|
| <overlay-to-core-VRF> |
|
| <overlay-from-core-VRF> |
|
| <overlay-to-core-VRF-network-mask> |
|
| <overlay-from-core-VRF-network-mask> |
|
| <L3-VLAN-id> |
|
| <L3-VLAN-name> |
|
| <L3-VLAN-int-id> |
|
| <L3-VNI-id> |
|
Base Configuration
!
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
!
hostname <hostname>
!
clock timezone zone <UTC-offset-h> <UTC-offset-m>
!
clock summer-time <DTZ> recurring
!
ip routing
!
ip name-server <name-server-1> <name-server-2>
ip domain name <domain-name>
!
license boot level network-advantage addon dna-advantage
!
system mtu 9198
!
errdisable recovery cause bpduguard
errdisable recovery interval 60
!
enable secret <enable-secret>
!
username username privilege 15 secret <admin-secret>
!
no ip http server
no ip http secure-server
!
line con 0
exec-timeout 60 0
privilege level 15
logging synchronous
login local
!
line vty 0 31
exec-timeout 60 0
privilege level 15
logging synchronous
login local
transport input telnet ssh
!
aaa new-model
!
interface Loopback0
description Primary loopback
ip address <Border-Spine-Loopback0-IP@> 255.255.255.255
!
ntp source Loopback0
ntp server <ntp-server> prefer
!
Underlay Links (excluding OSPF and Multicast)
!
! Spine to Leaf
!
interface <Border-Spine-underlay>
description To <Border-Spine-underlay-desc>
no switchport
ip address <Border-Spine-underlay-IP@> 255.255.255.252
speed nonegotiate
speed 40000
!
! Please repeat above step for all Underlay links to Leaf Switches
!
OSPF on Underlay links and Loopback0
!
router ospf 1
router-id loopback0-ip-address
auto-cost reference-bandwidth 100000
default-information originate metric 1000 metric-type 1
bfd all-interfaces
!
interface Loopback0
ip ospf 1 area 0
!
interface <Border-Spine-underlay>
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
! Please repeat above step for all Underlay links to Leaf Switches
!
BGP and Address Family for L2VPN EVPN
!
router bgp <BGP-ASN>
!
bgp router-id Loopback0-ip-address
bgp log-neighbor-changes
no bgp default ipv4-unicast
!
template peer-session leaf-ps
remote-as <BGP-ASN>
update-source Loopback0
fall-over bfd
exit-peer-session
!
neighbor <Leaf-Loopback0-IP@> inherit peer-session leaf-ps
!
! Please repeat neighbor inherit statement for all Leaf neighbors
!
address-family l2vpn evpn
neighbor <Leaf-Loopback0-IP@> activate
neighbor <Leaf-Loopback0-IP@> send-community both
exit-address-family
!
! Please repeat neighbor activate and send-community statements for all Leaf neighbors
!
Multicast; IP PIM Sparse Mode with Static RP and MSDP on Spine(s)
!
ip multicast-routing
!
!
interface Loopback1
description MSDP specific loopback
ip address MSDP-ip-address <msdp-IP@>
ip pim sparse-mode
ip ospf 1 area 0
!
interface Loopback2
description PIM RP Anycast specific loopback
ip address <rp-address> 255.255.255.255
ip pim sparse-mode
ip ospf 1 area 0
!
!
interface <Border-Spine-underlay>
ip pim sparse-mode
!
! Please repeat last interface statement for all underlay links
!
ip msdp peer msdp-peer-ip-address connect-source Loopback1
ip msdp cache-sa-state
!
ip pim rp-address Loopback2-ip-address
!
OSPF to Core (Underlay)
!
interface <Border-Spine-underlay-to-core>
description interface-to-external-core
no switchport
no ip address
cts manual
policy static sgt 2 trusted
!
<Border-Spine-underlay-to-core>.10
!
! .10 is a suggestion. Use a sub-interface number that is suitable for your deployment and make
! sure it matches the encapsulation configuration below
!
description underlay handoff
encapsulation dot1Q 10
ip address <Border-Spine-underlay-to-core-IP@> 255.255.255.252
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
BGP to Core (Underlay)
!
bfd interval 100 min_rx 100 multiplier 3
!
! BGP for Underlay to Core
!
router bgp <BGP-ASN>
!
neighbor <Core-IP@> remote-as as-number
neighbor <Core-IP@> fall-over bfd
!
! please repeat neighbor statements for all external neighbors
!
address-family ipv4
network <Underlay-network-to-core> mask <Underlay-network-to-core-mask>
!
! PLEASE REPEAT FOR ALL ADVERTISED NETWORKS (E.G. UNDERLAY)
!
aggregate-address <agg-Underlay-network-to-core> <Underlay-network-to-core-mask> summary-only
!
! PLEASE REPEAT FOR ALL AGGREGATED ADVERTISED NETWORKS
!
neighbor <Core-IP@> activate
neighbor <Core-IP@> route-map <from-core> in
neighbor <Core-IP@> route-map <to-core> out
!
! Repeat last neighbor statements for all external BGP neighbors
!
ip prefix-list <from-core-to-underlay> seq 5 permit <agg-from-core-to-underlay>
! ADD MORE ENTRIES AS REQUIRED
!
ip prefix-list <to-core-from-underlay> seq 5 permit <agg-to-core-from-underlay>
!
! ADD MORE ENTRIES AS REQUIRED
!
route-map <to-core-from-underlay> permit 10
match ip address prefix-list <to-core>
!
route-map <from-core-to-underlay> permit 10
match ip address prefix-list <from-core>
!
Add VRF
!
vrf definition <vrf-name>
rd <RD>
!
address-family ipv4
route-target export <RT>
route-target import <RT>
route-target export <RT> stitching
route-target import <RT> stitching
exit-address-family
!
! Please repeat the above section to add all VRFs in your design
!
Add VRF Handoff to Core (Overlay)
!
interface <Border-Spine-underlay-to-core>
!
description <Border-Spine-underlay-to-core-desc>
no switchport
mtu 9000
no ip address
cts manual
policy static sgt 2 trusted
bfd interval 100 min_rx 100 multiplier 3
!
interface interface-id.3001
! .3001 is just an identifier. Please make sure it is consistent with dot1Q enc
description handoff-to-core
encapsulation dot1Q 3001
! PLEASE MATCH WITH SUBINTERFACE FOR CONSISTENCY
vrf forwarding <vrf-name>
ip address <Border-Spine-vrf-handoff-IP@> 255.255.255.252
bfd interval 100 min_rx 100 multiplier 3
!
! Please repeat last section creating sub-interfaces for each VRF you have configured
!
Add VRF BGP to Core (Overlay)
!
! ASSUMING SAME CORE FOR OVERLAY & UNDERLAY HANDOFFS
! OTHERWISE REPLACE CORE WITH FUSION
!
router bgp <BGP-ASN>
neighbor <Core-IP@> remote-as as-number
neighbor <Core-IP@> fall-over bfd
!
! Please repeat above neighbor statements for all External BGP neighbors
!
address-family ipv4 vrf <vrf-name>
advertise l2vpn evpn
network <Overlay-network-to-core-VRF> mask <Overlay-network-to-core-VRF-mask>
!
! REPEAT FOR OVERLAY NETWORKS ADVERTISED IN THIS VRF
!
aggregate-address <agg-overlay-network-to-core-VRF> <agg-overlay-network-to-core-VRF-mask> summary-only
!
! ASSUMING SAME CORE FOR OVERLAY & UNDERLAY HANDOFFS
! OTHERWISE REPLACE CORE WITH FUSION
!
neighbor <Core-IP@> remote-as as-number
neighbor <Core-IP@> fall-over bfd
neighbor <Core-IP@> activate
neighbor <Core-IP@> route-map <overlay-from-core-VRF> in
neighbor <Core-IP@> route-map <overlay-to-core-VRF> out
!
! Repeat above neighbor statements for each external BGP neighbor
!
ip prefix-list <Overlay-from-core-VRF> seq 5 permit <Overlay-from-core-VRF-network-mask>
!
ip prefix-list <Overlay-to-core-VRF> seq 5 permit <Overlay-to-core-VRF-network-mask>
!
!
route-map <Overlay-from-core-VRF> permit 10
match ip address prefix-list <Overlay-from-core-VRF>
!
route-map <Overlay-to-core-VRF> permit 10
match ip address prefix-list <Overlay-to-core-VRF>
!
! Please repeat this section for all VRFs configured that needs to be routed externally
!
Setup L3 VNIs to allow routing across the Underlay
!
! note vlan is needed as it will be come the next hop in the active VRF
! routing table for L3 routes across the underlay
!
VLAN <L3-vlan-id>
name <L3-vlan-name>
!
! REPEAT FOR ALL LAYER 3 VLANS
!
interface <L3-VLAN-int-id>
vrf forwarding <vrf-name>
ip unnumbered Loopback0
no autostate
!
! REPEAT FOR ALL LAYER 3 VLANS
!
vlan configuration <L3-VLAN-id>
member vni <L3-VNI-id>
!
! REPEAT FOR ALL LAYER 3 VNIS
!
interface nve1
member vni <L3-VNI-id> vrf <vrf-name>
!
! REPEAT FOR ALL LAYER 3 VNI MEMBERS
!
Note: Please note that Leaf switch configurations are identical to that if the Border and Spine roles were not collapsed. Please refer to the previous section for guidance on Leaf switch configurations.
Fabric Expansions and Additions
This section provides guidance for expanding your fabric (e.g. Scaling up) or for simply adding new services such as a new SSID or VLAN on the Access layer.
The following templates can be used for each of the following use case:
Template for Adding VRFs
Note: Please also remember to adjust configuration on your border switches as required.
Note: The following configurations are required on ALL Leaf switches that require those new VRFs.
Variables used in this template:
| Variable |
Value (Replace with your own values) |
| <VRF-name> |
campus |
| <RD> |
65100:1 |
| <RT> |
65100:100 |
| <L2-vlan-id> |
1 |
| <L2-vlan-name> |
management |
| <L2-VNI-id> |
20001 |
| <mcast-group> |
255.0.0.1 |
| <L2-vlan-int-id> |
Vlan1 |
| <L3-vlan-id> |
3001 |
| <L3-vlan-name> |
Campus-L3-VLAN |
| <L3-vlan-int-id> |
Vlan3001 |
| <L3-VNI-id> |
30001 |
Add VRFs
!
vrf definition <VRF-name>
rd <RD>
!
address-family ipv4
route-target export <RT1>
route-target import <RT1>
route-target export <RT1> stitching
route-target import <RT1> stitching
exit-address-family
!
! REPEAT FOR ALL VRFs
!
BGP for IPV4 VRF
!
router bgp <BGP-ASN>
!
address-family ipv4 vrf <VRF-name>
advertise l2vpn evpn
redistribute connected
exit-address-family
!
! REPEAT FOR ALL NEW VRFs
!
L2VPN EVPN and VXLAN mapping
!
l2vpn evpn
replication-type static
router-id Loopback0
!
vlan <L2-vlan-id>
name <L2-vlan-name>
!
! REPEAT FOR ALL LAYER 2 VLANS PART OF THE NEW VRFS
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration <L2-vlan-id>
member evpn-instance 1 vni <L2-VNI-id>
!
! REPEAT FOR ALL LAYER 2 VLANS PART OF THE NEW VRFS
!
Add NVE1 and VNI Mapping
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni <L2-VNI-id> mcast-group <mcast-group>
!
! ADD MEMBERS FOR ALL LAYER 2 VLANs PART OF THE NEW VRFS
! ALL MEMBERS MUST BE PART OF NVE1
!
Setup L3 VNIs to allow routing across the Underlay
!
! note vlan is needed as it will become the next hop in the active VRF
! routing table for L3 routes across the underlay
!
!
VLAN <L3-vlan-id>
name <L3-vlan-name>
!
! REPEAT FOR ALL L3 VLANS PART OF THE NEW VRFS
!
interface <L3-vlan-int-id>
vrf forwarding <VRF-name>
ip unnumbered Loopback0
no autostate
!
! REPEAT FOR ALL LAYER 3 VLANS PART OF THE NEW VRFS
!
vlan configuration <L3-vlan-id>
member vni <L3-VNI-id>
!
! REPEAT FOR ALL LAYER 3 VLANS PART OF THE NEW VRFS
!
interface nve1
member vni <L3-VNI-id> vrf <VRF-name>
!
! ADD MEMBERS FOR ALL LAYER 3 VLANS PART OF THE NEW VRFS
!
Template for Adding VLANs
Note: The following configurations are required on ALL Leaf switches that require those new VLANs.
Variables used in this template:
| Variable |
Value (Replace with your own values) |
| <L2-vlan-id> |
1 |
| <L2-vlan-name> |
management |
| <L2-VNI-id> |
20001 |
| <mcast-group> |
255.0.0.1 |
| <L2-vlan-int-id> |
Vlan1 |
| <DAG-desc> |
|
| <DAG-mac> |
0000.0000.0001 |
| <DAG-gw-IP@> |
10.103.64.1 |
| <DAG-sub-mask> |
255.255.255.0 |
| <DHCP-server> |
10.100.0.1 |
L2VPN EVPN and VXLAN mapping
!
l2vpn evpn
replication-type static
router-id Loopback0
!
vlan <L2-vlan-id>
name <L2-vlan-name>
!
! REPEAT FOR ALL NEW LAYER 2 VLANS
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration <L2-vlan-id>
member evpn-instance 1 vni <L2-VNI-id>
!
! REPEAT FOR ALL NEW LAYER 2 VLANS
!
Add NVE1 and VNI Mapping
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni <L2-VNI-id> mcast-group <mcast-group>
!
! ADD MEMBERS FOR ALL NEW LAYER 2 VLANs
!
DAG and DHCP settings via Underlay with Option 82 (If required)
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration <L2-vlan-id>
member evpn-instance 1 vni <L2-VNI-id>
!
! REPEAT FOR ALL LAYER 2 VLANs
!
interface <L2-vlan-int-id>
description <DAG-desc>
mac-address <DAG-mac>
vrf forwarding <VRF-name>
ip address <DAG-gw-IP@> <DAG-sub-mask>
ip dhcp relay source-interface Loopback0
ip helper-address global <DHCP-server>
no autostate
!
! REPEAT FOR ALL DAGs ON ALL NEW LAYER 2 VLANS
!
Template for Adding SSIDs
Adding new SSIDs should be similar to adding VLANs assuming that a new broadcast domain is required for it. Please follow the same steps and template for adding VLANs in this case.
Template for Adding Leaf Switches
Variables used in this template:
| Variable |
Value (Replace with your own values) |
| <TZ> |
EST |
| <UTC-offset-h> |
-5 |
| <UTC-offset-m> |
0 |
| <DTZ> |
EDT |
| <name-server-1> |
1.1.1.1 |
| <name-server-1> |
1.1.1.2 |
| <domain-name> |
Customer.com |
| <hostname> |
Leaf-05 |
| <enable-secret> |
|
| <admin-secret> |
|
| <Leaf-Loopback0-desc> |
Loopback0 for Leaf |
| <Leaf-Loopback0-IP@> |
10.103.255.11 |
| <ntp-server> |
1.1.1.3 |
| <Leaf-underlay> |
Te1/1/1 |
| <Leaf-underlay-desc> |
Underlay to Spine |
| <<Leaf-underlay-IP@>> |
10.103.224.7 |
| <BGP-ASN> |
65100 |
| <Spine-Loopback0-IP@> |
10.10.3.255.1 |
| <rp-address> |
10.103.255.255 |
| <VRF-name> |
campus |
| <RD> |
65100:1 |
| <RT> |
65100:100 |
| <L2-vlan-id> |
1 |
| <L2-vlan-name> |
management |
| <L2-VNI-id> |
20001 |
| <mcast-group> |
255.0.0.1 |
| <L2-vlan-int-id> |
Vlan1 |
| <DAG-desc> |
|
| <DAG-mac> |
0000.0000.0001 |
| <DAG-gw-IP@> |
10.103.64.1 |
| <DAG-sub-mask> |
255.255.255.0 |
| <DHCP-server> |
10.100.0.1 |
| <L3-vlan-id> |
3001 |
| <L3-vlan-name> |
Campus-L3-VLAN |
| <L3-vlan-int-id> |
Vlan3001 |
| <L3-VNI-id> |
30001 |
| <Leaf-downlink> |
Te1/1/2 |
| <Leaf-downlink-desc> |
|
| <vlan-range> |
1-1000 |
| <sgt-id> |
2 |
| <Leaf-downlink1-etherchannel> |
Te1/1/2 |
| <Leaf-downlink2-etherchannel> |
Te1/1/3 |
| <Leaf-etherchannel-desc> |
|
| <Spine-underlay> |
Te1/1/1 |
| <Spine-underlay-desc> |
Underlay to Spine |
| <<Spine-underlay-IP@>> |
10.103.224.8 |
Base Configuration
!
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
!
hostname <hostname>
!
clock timezone <TZ> <UTC-offset-h> <UTC-offset-m>
clock summer-time <DTZ> recurring
!
ip routing
!
ip name-server <name-server-1> <name-server-2>
ip domain name <domain-name>
!
license boot level network-advantage addon dna-advantage
!
system mtu 9198
!
errdisable recovery cause bpduguard
errdisable recovery interval 60
!
enable secret <enable-secret>
!
username admin privilege 15 secret <admin-secret>
!
no ip http server
no ip http secure-server
!
line con 0
exec-timeout 60 0
privilege level 15
logging synchronous
login local
!
line vty 0 31
exec-timeout 60 0
privilege level 15
logging synchronous
login local
transport input telnet ssh
!
aaa new-model
!
interface Loopback0
description <Leaf-Loopback0-desc>
ip address <Leaf-Loopback0-IP@> 255.255.255.255
!
ntp source Loopback0
ntp server <ntp-server> prefer
!
lldp run
!
Underlay Links (excluding OSPF and Multicast)
! Leaf to Spine
!
interface <Leaf-underlay>
description <Leaf-underlay-desc>
no switchport
ip address <Leaf-underlay-IP@> 255.255.255.252
!
! REPEAT FOR ALL UNDERLAY INTERFACES ON LEAF
!
OSPF on Underlay links and Loopback0
!
router ospf 1
router-id <Leaf-Loopback0-IP@>
auto-cost reference-bandwidth 100000
bfd all-interfaces
!
interface Loopback0
ip ospf 1 area 0
!
interface <Leaf-underlay>
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
! REPEAT FOR ALL LEAF UNDERLAY INTERFACES
!
BGP and Address Family for L2VPN EVPN
!
router bgp <BGP-ASN>
!
bgp router-id <Loopback0-IP@>
bgp log-neighbor-changes
no bgp default ipv4-unicast
!
template peer-session spine-ps
remote-as <BGP-ASN>
update-source Loopback0
fall-over bfd
exit-peer-session
!
neighbor <Spine-Loopback0-IP@> inherit peer-session spine-ps
!
! REPEAT FOR ALL SPINE NEIGHBORS
!
address-family l2vpn evpn
neighbor <Spine-Loopback0-IP@> activate
neighbor <Spine-Loopback0-IP@> send-community both
!
! REPEAT FOR ALL SPINE NEIGHBORS
!
exit-address-family
!
Multicast; IP PIM Sparse Mode with Static RP and MSDP
!
ip multicast-routing
!
interface <Leaf-underlay>
ip pim sparse-mode
!
! REPEAT FOR ALL LEAF UNDERLAY INTERFACES
!
ip pim rp-address <rp-address>
!
Add VRFs
!
vrf definition <VRF-name>
rd <RD>
!
address-family ipv4
route-target export <RT>
route-target import <RT>
route-target export <RT> stitching
route-target import <RT> stitching
exit-address-family
!
! REPEAT FOR ALL VRFs
!
BGP for IPV4 VRF
!
router bgp <BGP-ASN>
!
address-family ipv4 vrf <VRF-name>
advertise l2vpn evpn
redistribute connected
exit-address-family
!
! REPEAT FOR ALL VRFs
!
L2VPN EVPN and VXLAN mapping
!
l2vpn evpn
replication-type static
router-id Loopback0
!
vlan <L2-vlan-id>
name <L2-vlan-name>
!
! REPEAT FOR ALL LAYER 2 VLANS
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration <L2-vlan-id>
member evpn-instance 1 vni <L2-VNI-id>
!
! REPEAT FOR ALL LAYER 2 VLANS
!
Add NVE1 and VNI Mapping
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni <L2-VNI-id> mcast-group <mcast-group>
!
! ADD MEMBERS FOR ALL LAYER 2 VLANs
!
DAG and DHCP settings via Underlay with Option 82
!
l2vpn evpn instance 1 vlan-based
encapsulation vxlan
!
vlan configuration <L2-vlan-id>
member evpn-instance 1 vni <L2-VNI-id>
!
! REPEAT FOR ALL LAYER 2 VLANs
!
interface <L2-vlan-int-id>
description <DAG-desc>
mac-address <DAG-mac>
vrf forwarding <VRF-name>
ip address <DAG-gw-IP@> <DAG-sub-mask>
ip dhcp relay source-interface Loopback0
ip helper-address global <DHCP-server>
no autostate
!
! REPEAT FOR ALL DAGs
!
Setup L3 VNIs to allow routing across the Underlay
!
! note vlan is needed as it will become the next hop in the active VRF
! routing table for L3 routes across the underlay
!
!
VLAN <L3-vlan-id>
name <L3-vlan-name>
!
! REPEAT FOR ALL L3 VLANS
!
interface <L3-vlan-int-id>
vrf forwarding <VRF-name>
ip unnumbered Loopback0
no autostate
!
! REPEAT FOR ALL LAYER 3 VLANS
!
vlan configuration <L3-vlan-id>
member vni <L3-VNI-id>
!
! REPEAT FOR ALL LAYER 3 VLANS
!
interface nve1
member vni <L3-VNI-id> vrf <VRF-name>
!
! ADD MEMBERS FOR ALL LAYER 3 VLANS
!
Downlinks to Access Layer
!
interface <Leaf-downlink>
description <Leaf-downlink-desc>
switchport Trunk allowed vlan <vlan-range>
switchport mode trunk
switchport nonegotiate
!
! REPEAT FOR ALL LEAF DOWNLINKS
!
Enable Inline Tagging
!
interface <Leaf-downlink>
cts manual
policy static sgt <sgt-id> trusted
!
! REPEAT FOR ALL LEAF DOWNLINKS
!
Enable Spanning-Tree with Bridge Priority and enable Root Guard
!
spanning-tree mst configuration
name region1
revision 1
exit
!
spanning-tree mst 0 priority 4096
!
interface <Leaf-downlink>
spanning-tree guard root
!
! REPEAT FOR ALL LEAF DOWNLINKS
!
Configure Ether Channel for Access Switch (where applicable)
!
interface <Leaf-downlink1-etherchannel>
channel-group 1 mode active
!
interface <Leaf-downlink2-etherchannel>
channel-group 1 mode active
!
interface port-channel 1
description <Leaf-etherchannel-desc>
!
Spine Configuration
! REPEAT ON ALL SPINE SWITCHES
! Spine to Leaf
!
interface <Spine-underlay>
description To <Spine-underlay-desc>
no switchport
ip address <Spine-underlay-IP@> 255.255.255.252
!
! REPEAT FOR ALL SPINE UNDERLAY INTERFACES
!
interface <Spine-underlay>
ip ospf network point-to-point
ip ospf 1 area 0
bfd interval 100 min_rx 100 multiplier 3
!
! REPEAT FOR ALL SPINE UNDERLAY INTERFACES
!
router bgp 65106
!
neighbor <Leaf-Loopback0-IP@> inherit peer-session leaf-ps
!
! REPEAT FOR ALL NEW LEAF SWITCHES
!
address-family l2vpn evpn
neighbor <Leaf-Loopback0-IP@> activate
neighbor <Leaf-Loopback0-IP@> inherit peer-policy leaf-pp
exit-address-family
!
interface <Spine-underlay>
ip pim sparse-mode
!
! REPEAT FOR ALL SPINE UNDERLAY INTERFACES
!
Testing and Verification
The following table lists the summary of testing and verification steps.
Table 10. Summary of Testing and Verification for Cloud Campus Fabric with BGP EVPN VXLAN
| Item |
Device |
Verification |
Expected Behavior |
| Underlay interfaces |
All Fabric Switches |
show ip interface brief show run interface loopback0 show cdp neighbors show lldp neighbors Port Summary (UI) |
Interfaces up/up Interface in ospf 1 Discoverable switches Discoverable switches Ports showing connected and passing traffic |
| OSPF |
All Fabric Switches |
show ip ospf neighbor show ip ospf interface show ip ospf 1 show ip route ospf show ip ospf database |
Neighbors in FULL state Interfaces participating and up Router ID, Area 0 Underlay and Loopback routes Router link states |
| Loopback0 |
All Fabric Switches |
ping <ip-address> source loopback0 |
Success, 0% loss |
| BGP L2VPN EVPN |
All Fabric Switches |
show ip bgp l2vpn evpn summary show ip bgp l2vpn evpn nei <ip-address> advertised-routes show ip bgp l2vpn evpn nei <ip-address> routes show ip bgp l2vpn evpn show ip bgp l2vpn evpn route-type 2 show ip bgp l2vpn evpn route-type 5 show ip bgp l2vpn evpn <mac-address> show ip bgp l2vpn evpn <network/mask> |
Verify peers and route count Verify advertised routes to a specific peer Verify received routes from a specific peer Verify full BGP RIB Verify all MAC/MAC-IP routes Verify all network routes Verify MAC routes Verify a network route |
| Multicast |
All Fabric Switches |
show ip pim interface show ip pim neighbor show ip pim rp show ip mroute |
Underlay interface(s) and mode (S/P) Neighbor status RP for multicast groups Multicast routes and RP assigned |
| Multicast |
Spine Switches |
Show ip interface brief show ip msdp summary show ip msdp peer |
Loopback1/2 up/up MSDP neighbor and state Detailed MSPD peer state |
| VLANs |
Leaf Switches |
show vlan |
VLAN config and L2/L3 mapping |
| VRFs |
Leaf Switches |
show vrf |
Configured VRFs and RD/RT |
| Virtual interfaces |
Leaf Switches |
show ip interface brief |
One per DAG, one per L3 VNI |
| NVE |
Leaf Switches |
show run interface nve1 show ip interface brief |
Verify L2/L3 VNIs Verify NVE1 up/up |
| Access Ports |
Leaf Switches |
show interface status show interface trunk show interface port1 |
Verify connected interfaces Verify allowed VLANs on Trunks Verify port channel |
| L2 Forwarding |
Leaf Switches |
show mac address-table dynamic show l2route evpn mac ip |
L2 forwarding table L2VPN = local, BGP = remote |
| L3 Routing |
Leaf Switches |
show ip bgp vpnv4 vrf <name> show ip bgp vpnv4 vrf <name> <network/mask> show ip route vrf <name> |
Verify EVPN address-family routes Verify L3 VNI, VTEPs, Encapsulation, L3 VNI Verify routes injected from BGP EPVN |
| VLANs |
Border Switches |
show vlan |
VLAN config and L2/L3 mapping |
| VRFs |
Border Switches |
show vrf |
Configured VRFs and RD/RT |
| L3 Routing |
Border Switches |
show ip bgp l2vpn evpn |
Verify routes injected from BGP EVPN |
| BGP |
Border Switches |
show ip bgp summary show ip bgp neighbors show ip bgp neighbor <ip-address> advertised-routes show ip bgp neighbor <ip-address> routes show ip bgp show ip route bgp |
Verify BGP status Verify peers and route count Verify advertised routes to a specific peer Verify received routes from a peer Verify full BGP RIB Verify BGP routes in RIB |
| BGP VPNV4 |
Border Switches |
show ip bgp vpnv4 vrf <name> show ip bgp vpnv4 vrf <name> neighbor <ip-address> advertised-routes show ip bgp vpnv4 vrf <name> neighbor <ip-address> routes show ip bgp vpnv4 vrf <name> show ip route vrf <name> |
Verify BGP injected routes Verify advertised routes to a specific peer (e.g. Fusion) Verify received routes from a specific peer (e.g. Fusion) Verify VRF BGP RIB for VRF Verify RIB for VRF |
| Cloud Monitoring |
All Cloud Monitored Switches |
Navigate to Switching > Switches, then check the status of all cloud monitored switches |
Online (i.e. Green) |
| Cloud Monitoring |
All Cloud Monitored Access Points |
Navigate to Wireless > Access Points, then check the status of all cloud monitored access points |
Online (i.e. Green) |
| Cloud Management |
All Cloud Managed Switches |
Navigate to Switching > Switches, then check the status of all cloud managed switches |
Online (i.e. Green) |
| Cloud Management |
All Cloud Managed Access Points |
Navigate to Wireless > Access Points, then check the status of all cloud managed access points |
Online (i.e. Green) |
| Micro-segmentation |
All Cloud Managed Devices |
Navigate to Network-wide > Clients, then check the adaptive policy group and VLAN assigned to clients. You can also check Adaptive Policies in Dashboard by navigating to Organization > Adaptive policy then Policies. |
Dynamic VLAN and Adaptive Policy assignment based on device posture
Policies in Dashboard in sync with Policies in Cisco ISE (Meraki Connector) |
The following sections explain the testing and verification steps for a Cloud Campus Fabric with BGP EVPN VXLAN solution.
Note: To access switch terminal in dashboard, navigate to Switching > Switches then click on the desired switch. Then click on Launch Terminal. Please note that the Cloud Monitored switches need to be onboarded and online to be able to access their Terminal in Dashboard.
Note: You can use Dashboard Terminal for show commands (e.g. show ip route vrf campus). Configuration is not allowed as well as ping and traceroute.
Underlay (All Fabric Switches and Access Switches)
Tech tip: You can use the Dashboard Terminal and the following commands: show ip interface brief.
NYC103-Spine-01
NYC103-Spine-01#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 unassigned YES NVRAM up down
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
TwentyFiveGigE1/0/1 10.103.224.29 YES NVRAM up up
TwentyFiveGigE1/0/2 10.103.224.37 YES NVRAM up up
TwentyFiveGigE1/0/3 10.103.224.45 YES NVRAM up up
TwentyFiveGigE1/0/4 10.103.224.53 YES NVRAM up up
TwentyFiveGigE1/0/5 unassigned YES unset down down
TwentyFiveGigE1/0/6 unassigned YES unset down down
TwentyFiveGigE1/0/7 unassigned YES unset down down
TwentyFiveGigE1/0/8 unassigned YES unset down down
TwentyFiveGigE1/0/9 unassigned YES unset down down
TwentyFiveGigE1/0/10 unassigned YES unset down down
TwentyFiveGigE1/0/11 unassigned YES unset down down
TwentyFiveGigE1/0/12 unassigned YES unset down down
TwentyFiveGigE1/0/13 unassigned YES unset down down
TwentyFiveGigE1/0/14 unassigned YES unset down down
TwentyFiveGigE1/0/15 unassigned YES unset down down
TwentyFiveGigE1/0/16 unassigned YES unset down down
TwentyFiveGigE1/0/17 unassigned YES unset down down
TwentyFiveGigE1/0/18 unassigned YES unset down down
TwentyFiveGigE1/0/19 unassigned YES unset down down
TwentyFiveGigE1/0/20 unassigned YES unset down down
TwentyFiveGigE1/0/21 unassigned YES unset down down
TwentyFiveGigE1/0/22 unassigned YES unset down down
TwentyFiveGigE1/0/23 unassigned YES unset down down
TwentyFiveGigE1/0/24 unassigned YES unset down down
HundredGigE1/0/25 10.103.224.9 YES NVRAM up up
HundredGigE1/0/26 10.103.224.21 YES NVRAM up up
HundredGigE1/0/27 unassigned YES unset down down
HundredGigE1/0/28 10.103.224.17 YES NVRAM up up
TLS-VIF0 20.0.122.247 YES TFTP up up
Loopback0 10.103.255.1 YES NVRAM up up
Loopback1 10.103.254.1 YES NVRAM up up
Loopback2 10.103.255.255 YES NVRAM up up
Loopback1000 20.0.122.247 YES manual up up
Tunnel0 10.103.255.255 YES unset up up
Tunnel1 10.103.255.255 YES unset up up
NYC103-Spine-02
NYC103-Spine-02#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 unassigned YES NVRAM up down
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
TwentyFiveGigE1/0/1 10.103.224.33 YES NVRAM up up
TwentyFiveGigE1/0/2 10.103.224.41 YES NVRAM up up
TwentyFiveGigE1/0/3 10.103.224.49 YES NVRAM up up
TwentyFiveGigE1/0/4 10.103.224.57 YES NVRAM up up
TwentyFiveGigE1/0/5 unassigned YES unset down down
TwentyFiveGigE1/0/6 unassigned YES unset down down
TwentyFiveGigE1/0/7 unassigned YES unset down down
TwentyFiveGigE1/0/8 unassigned YES unset down down
TwentyFiveGigE1/0/9 unassigned YES unset down down
TwentyFiveGigE1/0/10 unassigned YES unset down down
TwentyFiveGigE1/0/11 unassigned YES unset down down
TwentyFiveGigE1/0/12 unassigned YES unset down down
TwentyFiveGigE1/0/13 unassigned YES unset down down
TwentyFiveGigE1/0/14 unassigned YES unset down down
TwentyFiveGigE1/0/15 unassigned YES unset down down
TwentyFiveGigE1/0/16 unassigned YES unset down down
TwentyFiveGigE1/0/17 unassigned YES unset down down
TwentyFiveGigE1/0/18 unassigned YES unset down down
TwentyFiveGigE1/0/19 unassigned YES unset down down
TwentyFiveGigE1/0/20 unassigned YES unset down down
TwentyFiveGigE1/0/21 unassigned YES unset down down
TwentyFiveGigE1/0/22 unassigned YES unset down down
TwentyFiveGigE1/0/23 unassigned YES unset down down
TwentyFiveGigE1/0/24 unassigned YES unset down down
HundredGigE1/0/25 10.103.224.25 YES NVRAM up up
HundredGigE1/0/26 10.103.224.13 YES NVRAM up up
HundredGigE1/0/27 unassigned YES unset down down
HundredGigE1/0/28 10.103.224.18 YES NVRAM up up
TLS-VIF0 20.0.105.23 YES TFTP up up
Loopback0 10.103.255.2 YES NVRAM up up
Loopback1 10.103.254.2 YES NVRAM up up
Loopback2 10.103.255.255 YES NVRAM up up
Loopback1000 20.0.105.23 YES manual up up
Tunnel0 10.103.255.255 YES unset up up
Tunnel1 10.103.255.255 YES unset up up
NYC103-Border-01
NYC103-Border-01#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 unassigned YES NVRAM up up
Vlan3001 10.103.255.3 YES unset up up
Vlan3002 10.103.255.3 YES unset up up
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
GigabitEthernet1/0/1 unassigned YES unset up up
Gi1/0/1.10 10.103.224.2 YES NVRAM up up
GigabitEthernet1/0/2 unassigned YES unset up up
Gi1/0/2.3001 10.103.64.2 YES NVRAM up up
Gi1/0/2.3002 10.103.64.10 YES NVRAM up up
GigabitEthernet1/0/3 unassigned YES unset down down
GigabitEthernet1/0/4 unassigned YES unset down down
GigabitEthernet1/0/5 unassigned YES unset down down
GigabitEthernet1/0/6 unassigned YES unset down down
GigabitEthernet1/0/7 unassigned YES unset down down
GigabitEthernet1/0/8 unassigned YES unset down down
GigabitEthernet1/0/9 unassigned YES unset down down
GigabitEthernet1/0/10 unassigned YES unset down down
GigabitEthernet1/0/11 unassigned YES unset down down
GigabitEthernet1/0/12 unassigned YES unset down down
GigabitEthernet1/0/13 unassigned YES unset down down
GigabitEthernet1/0/14 unassigned YES unset down down
GigabitEthernet1/0/15 unassigned YES unset down down
GigabitEthernet1/0/16 unassigned YES unset down down
GigabitEthernet1/0/17 unassigned YES unset down down
GigabitEthernet1/0/18 unassigned YES unset down down
GigabitEthernet1/0/19 unassigned YES unset down down
GigabitEthernet1/0/20 unassigned YES unset down down
GigabitEthernet1/0/21 unassigned YES unset down down
GigabitEthernet1/0/22 unassigned YES unset down down
GigabitEthernet1/0/23 unassigned YES unset down down
GigabitEthernet1/0/24 unassigned YES unset down down
GigabitEthernet1/0/25 unassigned YES unset down down
GigabitEthernet1/0/26 unassigned YES unset down down
GigabitEthernet1/0/27 unassigned YES unset down down
GigabitEthernet1/0/28 unassigned YES unset down down
GigabitEthernet1/0/29 unassigned YES unset down down
GigabitEthernet1/0/30 unassigned YES unset down down
GigabitEthernet1/0/31 unassigned YES unset down down
GigabitEthernet1/0/32 unassigned YES unset down down
GigabitEthernet1/0/33 unassigned YES unset down down
GigabitEthernet1/0/34 unassigned YES unset down down
GigabitEthernet1/0/35 unassigned YES unset down down
GigabitEthernet1/0/36 unassigned YES unset down down
GigabitEthernet1/0/37 unassigned YES unset down down
GigabitEthernet1/0/38 unassigned YES unset down down
GigabitEthernet1/0/39 unassigned YES unset down down
GigabitEthernet1/0/40 unassigned YES unset down down
GigabitEthernet1/0/41 unassigned YES unset down down
GigabitEthernet1/0/42 unassigned YES unset down down
GigabitEthernet1/0/43 unassigned YES unset down down
GigabitEthernet1/0/44 unassigned YES unset down down
GigabitEthernet1/0/45 unassigned YES unset down down
GigabitEthernet1/0/46 unassigned YES unset down down
GigabitEthernet1/0/47 unassigned YES unset down down
GigabitEthernet1/0/48 unassigned YES unset down down
GigabitEthernet1/1/1 unassigned YES unset down down
GigabitEthernet1/1/2 unassigned YES unset down down
GigabitEthernet1/1/3 unassigned YES unset down down
GigabitEthernet1/1/4 unassigned YES unset down down
Te1/1/1 unassigned YES unset down down
Te1/1/2 unassigned YES unset down down
Te1/1/3 unassigned YES unset down down
Te1/1/4 unassigned YES unset down down
Te1/1/5 unassigned YES unset down down
Te1/1/6 unassigned YES unset down down
Te1/1/7 unassigned YES unset down down
Te1/1/8 unassigned YES unset down down
Fo1/1/1 10.103.224.10 YES NVRAM up up
Fo1/1/2 10.103.224.26 YES NVRAM up up
TwentyFiveGigE1/1/1 unassigned YES unset down down
TwentyFiveGigE1/1/2 unassigned YES unset down down
Ap1/0/1 unassigned YES unset up up
nve1 unassigned YES unset up up
Loopback0 10.103.255.3 YES NVRAM up up
Loopback1000 20.0.88.125 YES manual up up
TLS-VIF0 20.0.88.125 YES TFTP up up
Tunnel0 10.103.255.3 YES unset up up
Tunnel1 10.103.224.26 YES unset up up
NYC103-Border-02
NYC103-Border-02#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 unassigned YES NVRAM up up
Vlan3001 10.103.255.4 YES unset up up
Vlan3002 10.103.255.4 YES unset up up
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
GigabitEthernet1/0/1 unassigned YES unset up up
Gi1/0/1.10 10.103.224.6 YES NVRAM up up
GigabitEthernet1/0/2 unassigned YES unset up up
Gi1/0/2.3001 10.103.64.6 YES NVRAM up up
Gi1/0/2.3002 10.103.64.14 YES NVRAM up up
GigabitEthernet1/0/3 unassigned YES unset down down
GigabitEthernet1/0/4 unassigned YES unset down down
GigabitEthernet1/0/5 unassigned YES unset down down
GigabitEthernet1/0/6 unassigned YES unset down down
GigabitEthernet1/0/7 unassigned YES unset down down
GigabitEthernet1/0/8 unassigned YES unset down down
GigabitEthernet1/0/9 unassigned YES unset down down
GigabitEthernet1/0/10 unassigned YES unset down down
GigabitEthernet1/0/11 unassigned YES unset down down
GigabitEthernet1/0/12 unassigned YES unset down down
GigabitEthernet1/0/13 unassigned YES unset down down
GigabitEthernet1/0/14 unassigned YES unset down down
GigabitEthernet1/0/15 unassigned YES unset down down
GigabitEthernet1/0/16 unassigned YES unset down down
GigabitEthernet1/0/17 unassigned YES unset down down
GigabitEthernet1/0/18 unassigned YES unset down down
GigabitEthernet1/0/19 unassigned YES unset down down
GigabitEthernet1/0/20 unassigned YES unset down down
GigabitEthernet1/0/21 unassigned YES unset down down
GigabitEthernet1/0/22 unassigned YES unset down down
GigabitEthernet1/0/23 unassigned YES unset down down
GigabitEthernet1/0/24 unassigned YES unset down down
GigabitEthernet1/0/25 unassigned YES unset down down
GigabitEthernet1/0/26 unassigned YES unset down down
GigabitEthernet1/0/27 unassigned YES unset down down
GigabitEthernet1/0/28 unassigned YES unset down down
GigabitEthernet1/0/29 unassigned YES unset down down
GigabitEthernet1/0/30 unassigned YES unset down down
GigabitEthernet1/0/31 unassigned YES unset down down
GigabitEthernet1/0/32 unassigned YES unset down down
GigabitEthernet1/0/33 unassigned YES unset down down
GigabitEthernet1/0/34 unassigned YES unset down down
GigabitEthernet1/0/35 unassigned YES unset down down
GigabitEthernet1/0/36 unassigned YES unset down down
GigabitEthernet1/0/37 unassigned YES unset down down
GigabitEthernet1/0/38 unassigned YES unset down down
GigabitEthernet1/0/39 unassigned YES unset down down
GigabitEthernet1/0/40 unassigned YES unset down down
GigabitEthernet1/0/41 unassigned YES unset down down
GigabitEthernet1/0/42 unassigned YES unset down down
GigabitEthernet1/0/43 unassigned YES unset down down
GigabitEthernet1/0/44 unassigned YES unset down down
GigabitEthernet1/0/45 unassigned YES unset down down
GigabitEthernet1/0/46 unassigned YES unset down down
GigabitEthernet1/0/47 unassigned YES unset down down
GigabitEthernet1/0/48 unassigned YES unset down down
GigabitEthernet1/1/1 unassigned YES unset down down
GigabitEthernet1/1/2 unassigned YES unset down down
GigabitEthernet1/1/3 unassigned YES unset down down
GigabitEthernet1/1/4 unassigned YES unset down down
Te1/1/1 unassigned YES unset down down
Te1/1/2 unassigned YES unset down down
Te1/1/3 unassigned YES unset down down
Te1/1/4 unassigned YES unset down down
Te1/1/5 unassigned YES unset down down
Te1/1/6 unassigned YES unset down down
Te1/1/7 unassigned YES unset down down
Te1/1/8 unassigned YES unset down down
Fo1/1/1 10.103.224.22 YES NVRAM up up
Fo1/1/2 10.103.224.14 YES NVRAM up up
TwentyFiveGigE1/1/1 unassigned YES unset down down
TwentyFiveGigE1/1/2 unassigned YES unset down down
Ap1/0/1 unassigned YES unset up up
nve1 unassigned YES unset up up
Loopback0 10.103.255.4 YES NVRAM up up
Loopback1000 20.0.105.219 YES manual up up
TLS-VIF0 20.0.105.219 YES TFTP up up
Tunnel0 10.103.255.4 YES unset up up
Tunnel1 10.103.224.22 YES unset up up
NYC103-Leaf-01
NYC103-Leaf-01#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 10.103.64.1 YES NVRAM up up
Vlan120 10.103.120.1 YES NVRAM up up
Vlan180 10.103.180.1 YES NVRAM up up
Vlan220 10.103.220.1 YES NVRAM up up
Vlan3001 10.103.255.11 YES unset up up
Vlan3002 10.103.255.11 YES unset up up
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
GigabitEthernet1/0/1 unassigned YES unset down down
GigabitEthernet1/0/2 unassigned YES unset down down
GigabitEthernet1/0/3 unassigned YES unset down down
GigabitEthernet1/0/4 unassigned YES unset down down
GigabitEthernet1/0/5 unassigned YES unset down down
GigabitEthernet1/0/6 unassigned YES unset down down
GigabitEthernet1/0/7 unassigned YES unset down down
GigabitEthernet1/0/8 unassigned YES unset down down
GigabitEthernet1/0/9 unassigned YES unset down down
GigabitEthernet1/0/10 unassigned YES unset down down
GigabitEthernet1/0/11 unassigned YES unset down down
GigabitEthernet1/0/12 unassigned YES unset down down
GigabitEthernet1/0/13 unassigned YES unset down down
GigabitEthernet1/0/14 unassigned YES unset down down
GigabitEthernet1/0/15 unassigned YES unset down down
GigabitEthernet1/0/16 unassigned YES unset down down
GigabitEthernet1/0/17 unassigned YES unset down down
GigabitEthernet1/0/18 unassigned YES unset down down
GigabitEthernet1/0/19 unassigned YES unset down down
GigabitEthernet1/0/20 unassigned YES unset down down
GigabitEthernet1/0/21 unassigned YES unset down down
GigabitEthernet1/0/22 unassigned YES unset down down
GigabitEthernet1/0/23 unassigned YES unset down down
GigabitEthernet1/0/24 unassigned YES unset down down
GigabitEthernet1/0/25 unassigned YES unset down down
GigabitEthernet1/0/26 unassigned YES unset down down
GigabitEthernet1/0/27 unassigned YES unset down down
GigabitEthernet1/0/28 unassigned YES unset down down
GigabitEthernet1/0/29 unassigned YES unset down down
GigabitEthernet1/0/30 unassigned YES unset down down
GigabitEthernet1/0/31 unassigned YES unset down down
GigabitEthernet1/0/32 unassigned YES unset down down
GigabitEthernet1/0/33 unassigned YES unset down down
GigabitEthernet1/0/34 unassigned YES unset down down
GigabitEthernet1/0/35 unassigned YES unset down down
GigabitEthernet1/0/36 unassigned YES unset down down
GigabitEthernet1/0/37 unassigned YES unset down down
GigabitEthernet1/0/38 unassigned YES unset down down
GigabitEthernet1/0/39 unassigned YES unset down down
GigabitEthernet1/0/40 unassigned YES unset down down
GigabitEthernet1/0/41 unassigned YES unset down down
GigabitEthernet1/0/42 unassigned YES unset down down
GigabitEthernet1/0/43 unassigned YES unset down down
GigabitEthernet1/0/44 unassigned YES unset down down
GigabitEthernet1/0/45 unassigned YES unset down down
GigabitEthernet1/0/46 unassigned YES unset down down
GigabitEthernet1/0/47 unassigned YES unset up up
GigabitEthernet1/0/48 unassigned YES unset up up
GigabitEthernet1/1/1 unassigned YES unset down down
GigabitEthernet1/1/2 unassigned YES unset down down
GigabitEthernet1/1/3 unassigned YES unset down down
GigabitEthernet1/1/4 unassigned YES unset down down
Te1/1/1 unassigned YES unset down down
Te1/1/2 unassigned YES unset down down
Te1/1/3 unassigned YES unset down down
Te1/1/4 unassigned YES unset down down
Te1/1/5 unassigned YES unset down down
Te1/1/6 unassigned YES unset down down
Te1/1/7 unassigned YES unset down down
Te1/1/8 unassigned YES unset down down
Fo1/1/1 unassigned YES unset down down
Fo1/1/2 unassigned YES unset down down
TwentyFiveGigE1/1/1 10.103.224.30 YES NVRAM up up
TwentyFiveGigE1/1/2 10.103.224.34 YES NVRAM up up
Ap1/0/1 unassigned YES unset up up
Port-channel1 unassigned YES unset up up
TLS-VIF0 20.0.88.201 YES TFTP up up
nve1 unassigned YES unset up up
Loopback0 10.103.255.11 YES NVRAM up up
Loopback1000 20.0.88.201 YES manual up up
Tunnel0 10.103.255.11 YES unset up up
Tunnel1 10.103.224.30 YES unset up up
NYC103-Leaf-02
NYC103-Leaf-02#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 10.103.64.1 YES NVRAM up up
Vlan120 10.103.120.1 YES NVRAM up up
Vlan180 10.103.180.1 YES NVRAM up up
Vlan220 10.103.220.1 YES NVRAM up up
Vlan3001 10.103.255.12 YES unset up up
Vlan3002 10.103.255.12 YES unset up up
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
GigabitEthernet1/0/1 10.103.224.38 YES NVRAM up up
GigabitEthernet1/0/2 10.103.224.42 YES NVRAM up up
GigabitEthernet1/0/3 unassigned YES unset down down
GigabitEthernet1/0/4 unassigned YES unset down down
GigabitEthernet1/0/5 unassigned YES unset down down
GigabitEthernet1/0/6 unassigned YES unset down down
GigabitEthernet1/0/7 unassigned YES unset down down
GigabitEthernet1/0/8 unassigned YES unset down down
GigabitEthernet1/0/9 unassigned YES unset down down
GigabitEthernet1/0/10 unassigned YES unset down down
GigabitEthernet1/0/11 unassigned YES unset down down
GigabitEthernet1/0/12 unassigned YES unset down down
GigabitEthernet1/0/13 unassigned YES unset down down
GigabitEthernet1/0/14 unassigned YES unset down down
GigabitEthernet1/0/15 unassigned YES unset down down
GigabitEthernet1/0/16 unassigned YES unset down down
GigabitEthernet1/0/17 unassigned YES unset down down
GigabitEthernet1/0/18 unassigned YES unset down down
GigabitEthernet1/0/19 unassigned YES unset down down
GigabitEthernet1/0/20 unassigned YES unset down down
GigabitEthernet1/0/21 unassigned YES unset down down
GigabitEthernet1/0/22 unassigned YES unset down down
GigabitEthernet1/0/23 unassigned YES unset down down
GigabitEthernet1/0/24 unassigned YES unset down down
GigabitEthernet1/0/25 unassigned YES unset down down
GigabitEthernet1/0/26 unassigned YES unset down down
GigabitEthernet1/0/27 unassigned YES unset down down
GigabitEthernet1/0/28 unassigned YES unset down down
GigabitEthernet1/0/29 unassigned YES unset down down
GigabitEthernet1/0/30 unassigned YES unset down down
GigabitEthernet1/0/31 unassigned YES unset down down
GigabitEthernet1/0/32 unassigned YES unset down down
GigabitEthernet1/0/33 unassigned YES unset down down
GigabitEthernet1/0/34 unassigned YES unset down down
GigabitEthernet1/0/35 unassigned YES unset down down
GigabitEthernet1/0/36 unassigned YES unset down down
GigabitEthernet1/0/37 unassigned YES unset down down
GigabitEthernet1/0/38 unassigned YES unset down down
GigabitEthernet1/0/39 unassigned YES unset down down
GigabitEthernet1/0/40 unassigned YES unset down down
GigabitEthernet1/0/41 unassigned YES unset down down
GigabitEthernet1/0/42 unassigned YES unset down down
GigabitEthernet1/0/43 unassigned YES unset down down
GigabitEthernet1/0/44 unassigned YES unset down down
GigabitEthernet1/0/45 unassigned YES unset down down
GigabitEthernet1/0/46 unassigned YES unset down down
GigabitEthernet1/0/47 unassigned YES unset up up
GigabitEthernet1/0/48 unassigned YES unset up up
GigabitEthernet1/1/1 unassigned YES unset down down
GigabitEthernet1/1/2 unassigned YES unset down down
GigabitEthernet1/1/3 unassigned YES unset down down
GigabitEthernet1/1/4 unassigned YES unset down down
Te1/1/1 unassigned YES unset down down
Te1/1/2 unassigned YES unset down down
Te1/1/3 unassigned YES unset down down
Te1/1/4 unassigned YES unset down down
Te1/1/5 unassigned YES unset down down
Te1/1/6 unassigned YES unset down down
Te1/1/7 unassigned YES unset down down
Te1/1/8 unassigned YES unset down down
Fo1/1/1 unassigned YES unset down down
Fo1/1/2 unassigned YES unset down down
TwentyFiveGigE1/1/1 unassigned YES unset down down
TwentyFiveGigE1/1/2 unassigned YES unset down down
Ap1/0/1 unassigned YES unset up up
TLS-VIF0 20.0.66.11 YES TFTP up up
nve1 unassigned YES unset up up
Loopback0 10.103.255.12 YES NVRAM up up
Loopback1000 20.0.66.11 YES manual up up
Tunnel0 10.103.255.12 YES unset up up
Tunnel1 10.103.224.42 YES unset up up
NYC103-Leaf-03
NYC103-Leaf-03#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 10.103.64.1 YES NVRAM up up
Vlan120 10.103.120.1 YES NVRAM up up
Vlan180 10.103.180.1 YES NVRAM up up
Vlan220 10.103.220.1 YES NVRAM up up
Vlan3001 10.103.255.13 YES unset up up
Vlan3002 10.103.255.13 YES unset up up
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
GigabitEthernet1/0/1 10.103.224.46 YES NVRAM up up
GigabitEthernet1/0/2 10.103.224.50 YES NVRAM up up
GigabitEthernet1/0/3 unassigned YES unset down down
GigabitEthernet1/0/4 unassigned YES unset down down
GigabitEthernet1/0/5 unassigned YES unset down down
GigabitEthernet1/0/6 unassigned YES unset down down
GigabitEthernet1/0/7 unassigned YES unset down down
GigabitEthernet1/0/8 unassigned YES unset down down
GigabitEthernet1/0/9 unassigned YES unset down down
GigabitEthernet1/0/10 unassigned YES unset down down
GigabitEthernet1/0/11 unassigned YES unset down down
GigabitEthernet1/0/12 unassigned YES unset up up
GigabitEthernet1/0/13 unassigned YES unset up up
GigabitEthernet1/0/14 unassigned YES unset down down
GigabitEthernet1/0/15 unassigned YES unset down down
GigabitEthernet1/0/16 unassigned YES unset down down
GigabitEthernet1/0/17 unassigned YES unset down down
GigabitEthernet1/0/18 unassigned YES unset down down
GigabitEthernet1/0/19 unassigned YES unset down down
GigabitEthernet1/0/20 unassigned YES unset down down
GigabitEthernet1/0/21 unassigned YES unset down down
GigabitEthernet1/0/22 unassigned YES unset down down
GigabitEthernet1/0/23 unassigned YES unset down down
GigabitEthernet1/0/24 unassigned YES unset down down
GigabitEthernet1/0/25 unassigned YES unset down down
GigabitEthernet1/0/26 unassigned YES unset down down
GigabitEthernet1/0/27 unassigned YES unset down down
GigabitEthernet1/0/28 unassigned YES unset down down
GigabitEthernet1/0/29 unassigned YES unset down down
GigabitEthernet1/0/30 unassigned YES unset down down
GigabitEthernet1/0/31 unassigned YES unset down down
GigabitEthernet1/0/32 unassigned YES unset down down
GigabitEthernet1/0/33 unassigned YES unset down down
GigabitEthernet1/0/34 unassigned YES unset down down
GigabitEthernet1/0/35 unassigned YES unset down down
GigabitEthernet1/0/36 unassigned YES unset down down
GigabitEthernet1/0/37 unassigned YES unset down down
GigabitEthernet1/0/38 unassigned YES unset down down
GigabitEthernet1/0/39 unassigned YES unset down down
GigabitEthernet1/0/40 unassigned YES unset down down
GigabitEthernet1/0/41 unassigned YES unset down down
GigabitEthernet1/0/42 unassigned YES unset down down
GigabitEthernet1/0/43 unassigned YES unset down down
GigabitEthernet1/0/44 unassigned YES unset down down
GigabitEthernet1/0/45 unassigned YES unset down down
GigabitEthernet1/0/46 unassigned YES unset down down
GigabitEthernet1/0/47 unassigned YES unset down down
GigabitEthernet1/0/48 unassigned YES unset up up
GigabitEthernet1/1/1 unassigned YES unset down down
GigabitEthernet1/1/2 unassigned YES unset down down
GigabitEthernet1/1/3 unassigned YES unset down down
GigabitEthernet1/1/4 unassigned YES unset down down
Te1/1/1 unassigned YES unset down down
Te1/1/2 unassigned YES unset down down
Te1/1/3 unassigned YES unset down down
Te1/1/4 unassigned YES unset down down
Te1/1/5 unassigned YES unset down down
Te1/1/6 unassigned YES unset down down
Te1/1/7 unassigned YES unset down down
Te1/1/8 unassigned YES unset down down
Fo1/1/1 unassigned YES unset down down
Fo1/1/2 unassigned YES unset down down
TwentyFiveGigE1/1/1 unassigned YES unset down down
TwentyFiveGigE1/1/2 unassigned YES unset down down
Ap1/0/1 unassigned YES unset up up
TLS-VIF0 20.0.66.252 YES TFTP up up
nve1 unassigned YES unset up up
Loopback0 10.103.255.13 YES NVRAM up up
Loopback1000 20.0.66.252 YES manual up up
Tunnel0 10.103.255.13 YES unset up up
Tunnel1 10.103.224.50 YES unset up up
NYC103-Leaf-04
NYC103-Leaf-04#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 10.103.64.1 YES NVRAM up up
Vlan120 10.103.120.1 YES NVRAM up up
Vlan180 10.103.180.1 YES NVRAM up up
Vlan220 10.103.220.1 YES NVRAM up up
Vlan3001 10.103.255.14 YES unset up up
Vlan3002 10.103.255.14 YES unset up up
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
GigabitEthernet1/0/1 unassigned YES unset down down
GigabitEthernet1/0/2 unassigned YES unset down down
GigabitEthernet1/0/3 unassigned YES unset down down
GigabitEthernet1/0/4 unassigned YES unset down down
GigabitEthernet1/0/5 unassigned YES unset down down
GigabitEthernet1/0/6 unassigned YES unset down down
GigabitEthernet1/0/7 unassigned YES unset down down
GigabitEthernet1/0/8 unassigned YES unset down down
GigabitEthernet1/0/9 unassigned YES unset down down
GigabitEthernet1/0/10 unassigned YES unset down down
GigabitEthernet1/0/11 unassigned YES unset down down
GigabitEthernet1/0/12 unassigned YES unset down down
GigabitEthernet1/0/13 unassigned YES unset down down
GigabitEthernet1/0/14 unassigned YES unset down down
GigabitEthernet1/0/15 unassigned YES unset down down
GigabitEthernet1/0/16 unassigned YES unset down down
GigabitEthernet1/0/17 unassigned YES unset down down
GigabitEthernet1/0/18 unassigned YES unset down down
GigabitEthernet1/0/19 unassigned YES unset down down
GigabitEthernet1/0/20 unassigned YES unset down down
GigabitEthernet1/0/21 unassigned YES unset down down
GigabitEthernet1/0/22 unassigned YES unset down down
GigabitEthernet1/0/23 unassigned YES unset down down
GigabitEthernet1/0/24 unassigned YES unset down down
GigabitEthernet1/0/25 unassigned YES unset down down
GigabitEthernet1/0/26 unassigned YES unset down down
GigabitEthernet1/0/27 unassigned YES unset down down
GigabitEthernet1/0/28 unassigned YES unset down down
GigabitEthernet1/0/29 unassigned YES unset down down
GigabitEthernet1/0/30 unassigned YES unset down down
GigabitEthernet1/0/31 unassigned YES unset down down
GigabitEthernet1/0/32 unassigned YES unset down down
GigabitEthernet1/0/33 unassigned YES unset down down
GigabitEthernet1/0/34 unassigned YES unset down down
GigabitEthernet1/0/35 unassigned YES unset down down
GigabitEthernet1/0/36 unassigned YES unset down down
GigabitEthernet1/0/37 unassigned YES unset down down
GigabitEthernet1/0/38 unassigned YES unset down down
GigabitEthernet1/0/39 unassigned YES unset down down
GigabitEthernet1/0/40 unassigned YES unset down down
GigabitEthernet1/0/41 unassigned YES unset down down
GigabitEthernet1/0/42 unassigned YES unset down down
GigabitEthernet1/0/43 unassigned YES unset down down
GigabitEthernet1/0/44 unassigned YES unset down down
GigabitEthernet1/0/45 unassigned YES unset down down
GigabitEthernet1/0/46 unassigned YES unset down down
GigabitEthernet1/0/47 unassigned YES unset up up
GigabitEthernet1/0/48 unassigned YES unset up up
GigabitEthernet1/1/1 unassigned YES unset down down
GigabitEthernet1/1/2 unassigned YES unset down down
GigabitEthernet1/1/3 unassigned YES unset down down
GigabitEthernet1/1/4 unassigned YES unset down down
Te1/1/1 unassigned YES unset down down
Te1/1/2 unassigned YES unset down down
Te1/1/3 unassigned YES unset down down
Te1/1/4 unassigned YES unset down down
Te1/1/5 unassigned YES unset down down
Te1/1/6 unassigned YES unset down down
Te1/1/7 unassigned YES unset down down
Te1/1/8 unassigned YES unset down down
Fo1/1/1 unassigned YES unset down down
Fo1/1/2 unassigned YES unset down down
TwentyFiveGigE1/1/1 10.103.224.54 YES NVRAM up up
TwentyFiveGigE1/1/2 10.103.224.58 YES NVRAM up up
Ap1/0/1 unassigned YES unset up up
Port-channel1 unassigned YES unset up up
TLS-VIF0 20.0.82.26 YES TFTP up up
nve1 unassigned YES unset up up
Loopback0 10.103.255.14 YES NVRAM up up
Loopback1000 20.0.82.26 YES manual up up
Tunnel0 10.103.255.14 YES unset up up
Tunnel1 10.103.224.54 YES unset up up
NYC103-FL01-SW01

NYC103-FL02-SW01

NYC103-FL02-SW02

NYC103-FL02-SW03

NYC103-FL04-SW01

OSPF (All Fabric Switches)
Tech tip: You can use the Dashboard Terminal and the following commands: show ip ospf neighbors and show ip route ospf
NYC103-Spine-01
NYC103-Spine-01#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
10.103.255.2 0 FULL/ - 00:00:30 10.103.224.18 HundredGigE1/0/28
10.103.255.4 0 FULL/ - 00:00:31 10.103.224.22 HundredGigE1/0/26
10.103.255.3 0 FULL/ - 00:00:34 10.103.224.10 HundredGigE1/0/25
10.103.255.14 0 FULL/ - 00:00:39 10.103.224.54 TwentyFiveGigE1/0/4
10.103.255.13 0 FULL/ - 00:00:31 10.103.224.46 TwentyFiveGigE1/0/3
10.103.255.12 0 FULL/ - 00:00:37 10.103.224.38 TwentyFiveGigE1/0/2
10.103.255.11 0 FULL/ - 00:00:37 10.103.224.30 TwentyFiveGigE1/0/1
NYC103-Spine-01#show ip ospf interface
Loopback0 is up, line protocol is up
Internet Address 10.103.255.1/32, Interface ID 39, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.1, Network Type LOOPBACK, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Loopback interface is treated as a stub Host
Loopback1 is up, line protocol is up
Internet Address 10.103.254.1/32, Interface ID 40, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.1, Network Type LOOPBACK, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Loopback interface is treated as a stub Host
Loopback2 is up, line protocol is up
Internet Address 10.103.255.255/32, Interface ID 41, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.1, Network Type LOOPBACK, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Loopback interface is treated as a stub Host
HundredGigE1/0/28 is up, line protocol is up (connected)
Internet Address 10.103.224.17/30, Interface ID 48, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.1, Network Type POINT_TO_POINT, Cost: 2
Topology-MTID Cost Disabled Shutdown Topology Name
0 2 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:03
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/10/10, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.2
Suppress hello for 0 neighbor(s)
HundredGigE1/0/26 is up, line protocol is up (connected)
Internet Address 10.103.224.21/30, Interface ID 47, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.1, Network Type POINT_TO_POINT, Cost: 2
Topology-MTID Cost Disabled Shutdown Topology Name
0 2 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:02
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/9/9, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.4
Suppress hello for 0 neighbor(s)
HundredGigE1/0/25 is up, line protocol is up (connected)
NYC103-Spine-01#
NYC103-Spine-01#show ip ospf 1
Routing Process "ospf 1" with ID 10.103.255.1
Start time: 00:01:35.477, Time elapsed: 1w2d
Supports only single TOS(TOS0) routes
Supports opaque LSA
Supports Link-local Signaling (LLS)
Supports area transit capability
Supports NSSA (compatible with RFC 3101)
Supports Database Exchange Summary List Optimization (RFC 5243)
Event-log enabled, Maximum number of events: 1000, Mode: cyclic
It is an autonomous system boundary router
Redistributing External Routes from,
Router is not originating router-LSAs with maximum metric
Initial SPF schedule delay 50 msecs
Minimum hold time between two consecutive SPFs 200 msecs
Maximum wait time between two consecutive SPFs 5000 msecs
Incremental-SPF disabled
Initial LSA throttle delay 50 msecs
Minimum hold time for LSA throttle 200 msecs
Maximum wait time for LSA throttle 5000 msecs
Minimum LSA arrival 100 msecs
LSA group pacing timer 240 secs
Interface flood pacing timer 33 msecs
Retransmission pacing timer 66 msecs
EXCHANGE/LOADING adjacency limit: initial 300, process maximum 300
Number of external LSA 2. Checksum Sum 0x00F1EF
Number of opaque AS LSA 0. Checksum Sum 0x000000
Number of DCbitless external and opaque AS LSA 0
Number of DoNotAge external and opaque AS LSA 0
Number of areas in this router is 1. 1 normal 0 stub 0 nssa
Number of areas transit capable is 0
External flood list length 0
IETF NSF helper support enabled
Cisco NSF helper support enabled
BFD is enabled
Reference bandwidth unit is 100000 mbps
Area BACKBONE(0)
Number of interfaces in this area is 10 (3 loopback)
Area has no authentication
SPF algorithm last executed 1w2d ago
SPF algorithm executed 32 times
Area ranges are
Number of LSA 8. Checksum Sum 0x03DBF7
Number of opaque link LSA 0. Checksum Sum 0x000000
Number of DCbitless LSA 0
Number of indication LSA 0
Number of DoNotAge LSA 0
Flood list length 0
Maintenance Mode ID: 139668902607264
Maintenance Mode: disabled
Maintenance Mode Timer: stopped (0)
Graceful Reload FSU Global status : Not Supported (global: Not Supported)
NYC103-Spine-01#show ip route ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.224.22 to network 0.0.0.0
O*E1 0.0.0.0/0 [110/1102] via 10.103.224.22, 1w2d, HundredGigE1/0/26
[110/1102] via 10.103.224.10, 1w2d, HundredGigE1/0/25
10.0.0.0/8 is variably subnetted, 33 subnets, 2 masks
O 10.103.224.0/30 [110/102] via 10.103.224.10, 1w2d, HundredGigE1/0/25
O 10.103.224.4/30 [110/102] via 10.103.224.22, 1w2d, HundredGigE1/0/26
O 10.103.224.12/30 [110/4] via 10.103.224.22, 1w2d, HundredGigE1/0/26
[110/4] via 10.103.224.18, 1w2d, HundredGigE1/0/28
O 10.103.224.24/30 [110/4] via 10.103.224.18, 1w2d, HundredGigE1/0/28
[110/4] via 10.103.224.10, 1w2d, HundredGigE1/0/25
O 10.103.224.32/30 [110/12] via 10.103.224.18, 1w2d, HundredGigE1/0/28
O 10.103.224.40/30 [110/102] via 10.103.224.18, 1w2d, HundredGigE1/0/28
O 10.103.224.48/30 [110/102] via 10.103.224.18, 1w2d, HundredGigE1/0/28
O 10.103.224.56/30 [110/6] via 10.103.224.18, 1w2d, HundredGigE1/0/28
O 10.103.254.2/32 [110/3] via 10.103.224.18, 1w2d, HundredGigE1/0/28
O 10.103.255.2/32 [110/3] via 10.103.224.18, 1w2d, HundredGigE1/0/28
O 10.103.255.3/32 [110/3] via 10.103.224.10, 1w2d, HundredGigE1/0/25
O 10.103.255.4/32 [110/3] via 10.103.224.22, 1w2d, HundredGigE1/0/26
O 10.103.255.11/32
[110/11] via 10.103.224.30, 1w2d, TwentyFiveGigE1/0/1
O 10.103.255.12/32
[110/101] via 10.103.224.38, 1w2d, TwentyFiveGigE1/0/2
O 10.103.255.13/32
[110/101] via 10.103.224.46, 1w2d, TwentyFiveGigE1/0/3
O 10.103.255.14/32 [110/5] via 10.103.224.54, 1w2d, TwentyFiveGigE1/0/4
NYC103-Spine-01#show ip ospf database
OSPF Router with ID (10.103.255.1) (Process ID 1)
Router Link States (Area 0)
Link ID ADV Router Age Seq# Checksum Link count
10.103.255.1 10.103.255.1 1916 0x8000019E 0x00A79F 17
10.103.255.2 10.103.255.2 934 0x800001A2 0x00808E 17
10.103.255.3 10.103.255.3 595 0x80000195 0x0021A6 6
10.103.255.4 10.103.255.4 1858 0x80000194 0x007849 6
10.103.255.11 10.103.255.11 433 0x80000192 0x00E43B 5
10.103.255.12 10.103.255.12 602 0x80000191 0x00E9AA 5
10.103.255.13 10.103.255.13 1441 0x80000190 0x002B47 5
10.103.255.14 10.103.255.14 311 0x80000191 0x0020AF 5
Type-5 AS External Link States
Link ID ADV Router Age Seq# Checksum Tag
0.0.0.0 10.103.255.3 595 0x8000018D 0x00DE14 1
0.0.0.0 10.103.255.4 1858 0x8000018C 0x0013DB 1
NYC103-Spine-02
NYC103-Spine-02#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
10.103.255.4 0 FULL/ - 00:00:36 10.103.224.14 HundredGigE1/0/26
10.103.255.1 0 FULL/ - 00:00:38 10.103.224.17 HundredGigE1/0/28
10.103.255.3 0 FULL/ - 00:00:34 10.103.224.26 HundredGigE1/0/25
10.103.255.14 0 FULL/ - 00:00:31 10.103.224.58 TwentyFiveGigE1/0/4
10.103.255.13 0 FULL/ - 00:00:37 10.103.224.50 TwentyFiveGigE1/0/3
10.103.255.12 0 FULL/ - 00:00:30 10.103.224.42 TwentyFiveGigE1/0/2
10.103.255.11 0 FULL/ - 00:00:31 10.103.224.34 TwentyFiveGigE1/0/1
NYC103-Spine-02#show ip ospf interface
Loopback0 is up, line protocol is up
Internet Address 10.103.255.2/32, Interface ID 39, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.2, Network Type LOOPBACK, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Loopback interface is treated as a stub Host
Loopback1 is up, line protocol is up
Internet Address 10.103.254.2/32, Interface ID 40, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.2, Network Type LOOPBACK, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Loopback interface is treated as a stub Host
Loopback2 is up, line protocol is up
Internet Address 10.103.255.255/32, Interface ID 41, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.2, Network Type LOOPBACK, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Loopback interface is treated as a stub Host
HundredGigE1/0/26 is up, line protocol is up (connected)
Internet Address 10.103.224.13/30, Interface ID 47, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.2, Network Type POINT_TO_POINT, Cost: 2
Topology-MTID Cost Disabled Shutdown Topology Name
0 2 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:03
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/10/10, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.4
Suppress hello for 0 neighbor(s)
HundredGigE1/0/28 is up, line protocol is up (connected)
Internet Address 10.103.224.18/30, Interface ID 48, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.2, Network Type POINT_TO_POINT, Cost: 2
Topology-MTID Cost Disabled Shutdown Topology Name
0 2 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:04
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/9/9, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.1
Suppress hello for 0 neighbor(s)
HundredGigE1/0/25 is up, line protocol is up (connected)
NYC103-Spine-02#
NYC103-Spine-02#show ip ospf 1
Routing Process "ospf 1" with ID 10.103.255.2
Start time: 00:01:35.706, Time elapsed: 1w2d
Supports only single TOS(TOS0) routes
Supports opaque LSA
Supports Link-local Signaling (LLS)
Supports area transit capability
Supports NSSA (compatible with RFC 3101)
Supports Database Exchange Summary List Optimization (RFC 5243)
Event-log enabled, Maximum number of events: 1000, Mode: cyclic
It is an autonomous system boundary router
Redistributing External Routes from,
Router is not originating router-LSAs with maximum metric
Initial SPF schedule delay 50 msecs
Minimum hold time between two consecutive SPFs 200 msecs
Maximum wait time between two consecutive SPFs 5000 msecs
Incremental-SPF disabled
Initial LSA throttle delay 50 msecs
Minimum hold time for LSA throttle 200 msecs
Maximum wait time for LSA throttle 5000 msecs
Minimum LSA arrival 100 msecs
LSA group pacing timer 240 secs
Interface flood pacing timer 33 msecs
Retransmission pacing timer 66 msecs
EXCHANGE/LOADING adjacency limit: initial 300, process maximum 300
Number of external LSA 2. Checksum Sum 0x00F1EF
Number of opaque AS LSA 0. Checksum Sum 0x000000
Number of DCbitless external and opaque AS LSA 0
Number of DoNotAge external and opaque AS LSA 0
Number of areas in this router is 1. 1 normal 0 stub 0 nssa
Number of areas transit capable is 0
External flood list length 0
IETF NSF helper support enabled
Cisco NSF helper support enabled
BFD is enabled
Reference bandwidth unit is 100000 mbps
Area BACKBONE(0)
Number of interfaces in this area is 10 (3 loopback)
Area has no authentication
SPF algorithm last executed 1w2d ago
SPF algorithm executed 27 times
Area ranges are
Number of LSA 8. Checksum Sum 0x03DBF7
Number of opaque link LSA 0. Checksum Sum 0x000000
Number of DCbitless LSA 0
Number of indication LSA 0
Number of DoNotAge LSA 0
Flood list length 0
Maintenance Mode ID: 140219356546768
Maintenance Mode: disabled
Maintenance Mode Timer: stopped (0)
Graceful Reload FSU Global status : Not Supported (global: Not Supported)
NYC103-Spine-02#show ip route ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.224.26 to network 0.0.0.0
O*E1 0.0.0.0/0 [110/1102] via 10.103.224.26, 1w2d, HundredGigE1/0/25
[110/1102] via 10.103.224.14, 1w2d, HundredGigE1/0/26
10.0.0.0/8 is variably subnetted, 33 subnets, 2 masks
O 10.103.224.0/30 [110/102] via 10.103.224.26, 1w2d, HundredGigE1/0/25
O 10.103.224.4/30 [110/102] via 10.103.224.14, 1w2d, HundredGigE1/0/26
O 10.103.224.8/30 [110/4] via 10.103.224.26, 1w2d, HundredGigE1/0/25
[110/4] via 10.103.224.17, 1w2d, HundredGigE1/0/28
O 10.103.224.20/30 [110/4] via 10.103.224.17, 1w2d, HundredGigE1/0/28
[110/4] via 10.103.224.14, 1w2d, HundredGigE1/0/26
O 10.103.224.28/30 [110/12] via 10.103.224.17, 1w2d, HundredGigE1/0/28
O 10.103.224.36/30 [110/102] via 10.103.224.17, 1w2d, HundredGigE1/0/28
O 10.103.224.44/30 [110/102] via 10.103.224.17, 1w2d, HundredGigE1/0/28
O 10.103.224.52/30 [110/6] via 10.103.224.17, 1w2d, HundredGigE1/0/28
O 10.103.254.1/32 [110/3] via 10.103.224.17, 1w2d, HundredGigE1/0/28
O 10.103.255.1/32 [110/3] via 10.103.224.17, 1w2d, HundredGigE1/0/28
O 10.103.255.3/32 [110/3] via 10.103.224.26, 1w2d, HundredGigE1/0/25
O 10.103.255.4/32 [110/3] via 10.103.224.14, 1w2d, HundredGigE1/0/26
O 10.103.255.11/32
[110/11] via 10.103.224.34, 1w2d, TwentyFiveGigE1/0/1
O 10.103.255.12/32
[110/101] via 10.103.224.42, 1w2d, TwentyFiveGigE1/0/2
O 10.103.255.13/32
[110/101] via 10.103.224.50, 1w2d, TwentyFiveGigE1/0/3
O 10.103.255.14/32 [110/5] via 10.103.224.58, 1w2d, TwentyFiveGigE1/0/4
NYC103-Spine-02#show ip ospf database
OSPF Router with ID (10.103.255.2) (Process ID 1)
Router Link States (Area 0)
Link ID ADV Router Age Seq# Checksum Link count
10.103.255.1 10.103.255.1 1922 0x8000019E 0x00A79F 17
10.103.255.2 10.103.255.2 937 0x800001A2 0x00808E 17
10.103.255.3 10.103.255.3 600 0x80000195 0x0021A6 6
10.103.255.4 10.103.255.4 1863 0x80000194 0x007849 6
10.103.255.11 10.103.255.11 438 0x80000192 0x00E43B 5
10.103.255.12 10.103.255.12 607 0x80000191 0x00E9AA 5
10.103.255.13 10.103.255.13 1446 0x80000190 0x002B47 5
10.103.255.14 10.103.255.14 316 0x80000191 0x0020AF 5
Type-5 AS External Link States
Link ID ADV Router Age Seq# Checksum Tag
0.0.0.0 10.103.255.3 600 0x8000018D 0x00DE14 1
0.0.0.0 10.103.255.4 1863 0x8000018C 0x0013DB 1
NYC103-Border-01
NYC103-Border-01#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
10.103.255.2 0 FULL/ - 00:00:35 10.103.224.25 FortyGigabitEthernet1/1/2
10.103.255.1 0 FULL/ - 00:00:37 10.103.224.9 FortyGigabitEthernet1/1/1
NYC103-Border-01#show ip ospf interface
Loopback0 is up, line protocol is up
Internet Address 10.103.255.3/32, Interface ID 77, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.3, Network Type LOOPBACK, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Loopback interface is treated as a stub Host
FortyGigabitEthernet1/1/2 is up, line protocol is up (connected)
Internet Address 10.103.224.26/30, Interface ID 84, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.3, Network Type POINT_TO_POINT, Cost: 2
Topology-MTID Cost Disabled Shutdown Topology Name
0 2 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:09
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/4/4, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 2, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.2
Suppress hello for 0 neighbor(s)
FortyGigabitEthernet1/1/1 is up, line protocol is up (connected)
Internet Address 10.103.224.10/30, Interface ID 83, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.3, Network Type POINT_TO_POINT, Cost: 2
Topology-MTID Cost Disabled Shutdown Topology Name
0 2 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:05
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/3/3, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.1
Suppress hello for 0 neighbor(s)
GigabitEthernet1/0/1.10 is up, line protocol is up (connected)
Internet Address 10.103.224.2/30, Interface ID 79, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.3, Network Type BROADCAST, Cost: 100
Topology-MTID Cost Disabled Shutdown Topology Name
0 100 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State DR, Priority 1, BFD enabled
Designated Router (ID) 10.103.255.3, Interface address 10.103.224.2
No backup designated router on this network
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:08
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
NYC103-Border-01#
NYC103-Border-01#show ip ospf 1
Routing Process "ospf 1" with ID 10.103.255.3
Start time: 00:02:35.752, Time elapsed: 1w2d
Supports only single TOS(TOS0) routes
Supports opaque LSA
Supports Link-local Signaling (LLS)
Supports area transit capability
Supports NSSA (compatible with RFC 3101)
Supports Database Exchange Summary List Optimization (RFC 5243)
Event-log enabled, Maximum number of events: 1000, Mode: cyclic
It is an autonomous system boundary router
Redistributing External Routes from,
Router is not originating router-LSAs with maximum metric
Initial SPF schedule delay 50 msecs
Minimum hold time between two consecutive SPFs 200 msecs
Maximum wait time between two consecutive SPFs 5000 msecs
Incremental-SPF disabled
Initial LSA throttle delay 50 msecs
Minimum hold time for LSA throttle 200 msecs
Maximum wait time for LSA throttle 5000 msecs
Minimum LSA arrival 100 msecs
LSA group pacing timer 240 secs
Interface flood pacing timer 33 msecs
Retransmission pacing timer 66 msecs
EXCHANGE/LOADING adjacency limit: initial 300, process maximum 300
Number of external LSA 2. Checksum Sum 0x00F1EF
Number of opaque AS LSA 0. Checksum Sum 0x000000
Number of DCbitless external and opaque AS LSA 0
Number of DoNotAge external and opaque AS LSA 0
Number of areas in this router is 1. 1 normal 0 stub 0 nssa
Number of areas transit capable is 0
External flood list length 0
IETF NSF helper support enabled
Cisco NSF helper support enabled
BFD is enabled
Reference bandwidth unit is 100000 mbps
Area BACKBONE(0)
Number of interfaces in this area is 4 (1 loopback)
Area has no authentication
SPF algorithm last executed 1w2d ago
SPF algorithm executed 16 times
Area ranges are
Number of LSA 8. Checksum Sum 0x03DBF7
Number of opaque link LSA 0. Checksum Sum 0x000000
Number of DCbitless LSA 0
Number of indication LSA 0
Number of DoNotAge LSA 0
Flood list length 0
Maintenance Mode ID: 140453915606304
Maintenance Mode: disabled
Maintenance Mode Timer: stopped (0)
Graceful Reload FSU Global status : None (global: None)
NYC103-Border-01#show ip route ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.224.1 to network 0.0.0.0
10.0.0.0/8 is variably subnetted, 31 subnets, 3 masks
O 10.103.224.4/30
[110/104] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
[110/104] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.224.12/30
[110/4] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.224.16/30
[110/4] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
[110/4] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.224.20/30
[110/4] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.224.28/30
[110/12] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.224.32/30
[110/12] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.224.36/30
[110/102] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.224.40/30
[110/102] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.224.44/30
[110/102] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.224.48/30
[110/102] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.224.52/30
[110/6] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.224.56/30
[110/6] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.254.1/32
[110/3] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.254.2/32
[110/3] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.255.1/32
[110/3] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.255.2/32
[110/3] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.255.4/32
[110/5] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
[110/5] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.255.11/32
[110/13] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
[110/13] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.255.12/32
[110/103] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
[110/103] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.255.13/32
[110/103] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
[110/103] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.255.14/32
[110/7] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
[110/7] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.255.255/32
[110/3] via 10.103.224.25, 1w2d, FortyGigabitEthernet1/1/2
[110/3] via 10.103.224.9, 1w2d, FortyGigabitEthernet1/1/1
NYC103-Border-01#show ip ospf database
OSPF Router with ID (10.103.255.3) (Process ID 1)
Router Link States (Area 0)
Link ID ADV Router Age Seq# Checksum Link count
10.103.255.1 10.103.255.1 1925 0x8000019E 0x00A79F 17
10.103.255.2 10.103.255.2 942 0x800001A2 0x00808E 17
10.103.255.3 10.103.255.3 602 0x80000195 0x0021A6 6
10.103.255.4 10.103.255.4 1868 0x80000194 0x007849 6
10.103.255.11 10.103.255.11 443 0x80000192 0x00E43B 5
10.103.255.12 10.103.255.12 612 0x80000191 0x00E9AA 5
10.103.255.13 10.103.255.13 1451 0x80000190 0x002B47 5
10.103.255.14 10.103.255.14 320 0x80000191 0x0020AF 5
Type-5 AS External Link States
Link ID ADV Router Age Seq# Checksum Tag
0.0.0.0 10.103.255.3 602 0x8000018D 0x00DE14 1
0.0.0.0 10.103.255.4 1868 0x8000018C 0x0013DB 1
NYC103-Border-02
NYC103-Border-02#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
10.103.255.2 0 FULL/ - 00:00:36 10.103.224.13 FortyGigabitEthernet1/1/2
10.103.255.1 0 FULL/ - 00:00:39 10.103.224.21 FortyGigabitEthernet1/1/1
NYC103-Border-02#show ip ospf interface
Loopback0 is up, line protocol is up
Internet Address 10.103.255.4/32, Interface ID 77, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.4, Network Type LOOPBACK, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Loopback interface is treated as a stub Host
FortyGigabitEthernet1/1/2 is up, line protocol is up (connected)
Internet Address 10.103.224.14/30, Interface ID 84, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.4, Network Type POINT_TO_POINT, Cost: 2
Topology-MTID Cost Disabled Shutdown Topology Name
0 2 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:07
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/4/4, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.2
Suppress hello for 0 neighbor(s)
FortyGigabitEthernet1/1/1 is up, line protocol is up (connected)
Internet Address 10.103.224.22/30, Interface ID 83, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.4, Network Type POINT_TO_POINT, Cost: 2
Topology-MTID Cost Disabled Shutdown Topology Name
0 2 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:08
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/3/3, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.1
Suppress hello for 0 neighbor(s)
GigabitEthernet1/0/1.10 is up, line protocol is up (connected)
Internet Address 10.103.224.6/30, Interface ID 79, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.4, Network Type BROADCAST, Cost: 100
Topology-MTID Cost Disabled Shutdown Topology Name
0 100 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State DR, Priority 1, BFD enabled
Designated Router (ID) 10.103.255.4, Interface address 10.103.224.6
No backup designated router on this network
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:00
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
NYC103-Border-02#
NYC103-Border-02#show ip ospf 1
Routing Process "ospf 1" with ID 10.103.255.4
Start time: 00:02:34.537, Time elapsed: 1w2d
Supports only single TOS(TOS0) routes
Supports opaque LSA
Supports Link-local Signaling (LLS)
Supports area transit capability
Supports NSSA (compatible with RFC 3101)
Supports Database Exchange Summary List Optimization (RFC 5243)
Event-log enabled, Maximum number of events: 1000, Mode: cyclic
It is an autonomous system boundary router
Redistributing External Routes from,
Router is not originating router-LSAs with maximum metric
Initial SPF schedule delay 50 msecs
Minimum hold time between two consecutive SPFs 200 msecs
Maximum wait time between two consecutive SPFs 5000 msecs
Incremental-SPF disabled
Initial LSA throttle delay 50 msecs
Minimum hold time for LSA throttle 200 msecs
Maximum wait time for LSA throttle 5000 msecs
Minimum LSA arrival 100 msecs
LSA group pacing timer 240 secs
Interface flood pacing timer 33 msecs
Retransmission pacing timer 66 msecs
EXCHANGE/LOADING adjacency limit: initial 300, process maximum 300
Number of external LSA 2. Checksum Sum 0x00F1EF
Number of opaque AS LSA 0. Checksum Sum 0x000000
Number of DCbitless external and opaque AS LSA 0
Number of DoNotAge external and opaque AS LSA 0
Number of areas in this router is 1. 1 normal 0 stub 0 nssa
Number of areas transit capable is 0
External flood list length 0
IETF NSF helper support enabled
Cisco NSF helper support enabled
BFD is enabled
Reference bandwidth unit is 100000 mbps
Area BACKBONE(0)
Number of interfaces in this area is 4 (1 loopback)
Area has no authentication
SPF algorithm last executed 1w2d ago
SPF algorithm executed 15 times
Area ranges are
Number of LSA 8. Checksum Sum 0x03DBF7
Number of opaque link LSA 0. Checksum Sum 0x000000
Number of DCbitless LSA 0
Number of indication LSA 0
Number of DoNotAge LSA 0
Flood list length 0
Maintenance Mode ID: 140105562550480
Maintenance Mode: disabled
Maintenance Mode Timer: stopped (0)
Graceful Reload FSU Global status : None (global: None)
NYC103-Border-02#show ip route ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.224.5 to network 0.0.0.0
10.0.0.0/8 is variably subnetted, 31 subnets, 3 masks
O 10.103.224.0/30
[110/104] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
[110/104] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.224.8/30
[110/4] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.224.16/30
[110/4] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
[110/4] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.224.24/30
[110/4] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.224.28/30
[110/12] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.224.32/30
[110/12] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.224.36/30
[110/102] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.224.40/30
[110/102] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.224.44/30
[110/102] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.224.48/30
[110/102] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.224.52/30
[110/6] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.224.56/30
[110/6] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.254.1/32
[110/3] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.254.2/32
[110/3] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.255.1/32
[110/3] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
O 10.103.255.2/32
[110/3] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.255.3/32
[110/5] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
[110/5] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.255.11/32
[110/13] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
[110/13] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.255.12/32
[110/103] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
[110/103] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.255.13/32
[110/103] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
[110/103] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.255.14/32
[110/7] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
[110/7] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
O 10.103.255.255/32
[110/3] via 10.103.224.21, 1w2d, FortyGigabitEthernet1/1/1
[110/3] via 10.103.224.13, 1w2d, FortyGigabitEthernet1/1/2
NYC103-Border-02#show ip ospf database
OSPF Router with ID (10.103.255.4) (Process ID 1)
Router Link States (Area 0)
Link ID ADV Router Age Seq# Checksum Link count
10.103.255.1 10.103.255.1 1929 0x8000019E 0x00A79F 17
10.103.255.2 10.103.255.2 945 0x800001A2 0x00808E 17
10.103.255.3 10.103.255.3 608 0x80000195 0x0021A6 6
10.103.255.4 10.103.255.4 1869 0x80000194 0x007849 6
10.103.255.11 10.103.255.11 446 0x80000192 0x00E43B 5
10.103.255.12 10.103.255.12 615 0x80000191 0x00E9AA 5
10.103.255.13 10.103.255.13 1454 0x80000190 0x002B47 5
10.103.255.14 10.103.255.14 324 0x80000191 0x0020AF 5
Type-5 AS External Link States
Link ID ADV Router Age Seq# Checksum Tag
0.0.0.0 10.103.255.3 608 0x8000018D 0x00DE14 1
0.0.0.0 10.103.255.4 1869 0x8000018C 0x0013DB 1
NYC103-Leaf-01
NYC103-Leaf-01#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
10.103.255.2 0 FULL/ - 00:00:36 10.103.224.33 TwentyFiveGigE1/1/2
10.103.255.1 0 FULL/ - 00:00:33 10.103.224.29 TwentyFiveGigE1/1/1
NYC103-Leaf-01#show ip ospf interface
Loopback0 is up, line protocol is up
Internet Address 10.103.255.11/32, Interface ID 76, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.11, Network Type LOOPBACK, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Loopback interface is treated as a stub Host
TwentyFiveGigE1/1/2 is up, line protocol is up (connected)
Internet Address 10.103.224.34/30, Interface ID 80, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.11, Network Type POINT_TO_POINT, Cost: 10
Topology-MTID Cost Disabled Shutdown Topology Name
0 10 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:00
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/3/3, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.2
Suppress hello for 0 neighbor(s)
TwentyFiveGigE1/1/1 is up, line protocol is up (connected)
Internet Address 10.103.224.30/30, Interface ID 79, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.11, Network Type POINT_TO_POINT, Cost: 10
Topology-MTID Cost Disabled Shutdown Topology Name
0 10 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:00
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/2/2, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.1
Suppress hello for 0 neighbor(s)
NYC103-Leaf-01#show ip ospf 1
Routing Process "ospf 1" with ID 10.103.255.11
Start time: 00:02:34.689, Time elapsed: 1w2d
Supports only single TOS(TOS0) routes
Supports opaque LSA
Supports Link-local Signaling (LLS)
Supports area transit capability
Supports NSSA (compatible with RFC 3101)
Supports Database Exchange Summary List Optimization (RFC 5243)
Event-log enabled, Maximum number of events: 1000, Mode: cyclic
Router is not originating router-LSAs with maximum metric
Initial SPF schedule delay 50 msecs
Minimum hold time between two consecutive SPFs 200 msecs
Maximum wait time between two consecutive SPFs 5000 msecs
Incremental-SPF disabled
Initial LSA throttle delay 50 msecs
Minimum hold time for LSA throttle 200 msecs
Maximum wait time for LSA throttle 5000 msecs
Minimum LSA arrival 100 msecs
LSA group pacing timer 240 secs
Interface flood pacing timer 33 msecs
Retransmission pacing timer 66 msecs
EXCHANGE/LOADING adjacency limit: initial 300, process maximum 300
Number of external LSA 2. Checksum Sum 0x00F1EF
Number of opaque AS LSA 0. Checksum Sum 0x000000
Number of DCbitless external and opaque AS LSA 0
Number of DoNotAge external and opaque AS LSA 0
Number of areas in this router is 1. 1 normal 0 stub 0 nssa
Number of areas transit capable is 0
External flood list length 0
IETF NSF helper support enabled
Cisco NSF helper support enabled
BFD is enabled
Reference bandwidth unit is 100000 mbps
Area BACKBONE(0)
Number of interfaces in this area is 3 (1 loopback)
Area has no authentication
SPF algorithm last executed 1w2d ago
SPF algorithm executed 10 times
Area ranges are
Number of LSA 8. Checksum Sum 0x03DBF7
Number of opaque link LSA 0. Checksum Sum 0x000000
Number of DCbitless LSA 0
Number of indication LSA 0
Number of DoNotAge LSA 0
Flood list length 0
Maintenance Mode ID: 139818590787088
Maintenance Mode: disabled
Maintenance Mode Timer: stopped (0)
Graceful Reload FSU Global status : None (global: None)
NYC103-Leaf-01#show ip route ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.224.33 to network 0.0.0.0
O*E1 0.0.0.0/0 [110/1112] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
[110/1112] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
10.0.0.0/8 is variably subnetted, 28 subnets, 2 masks
O 10.103.224.0/30
[110/112] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
[110/112] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.4/30
[110/112] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
[110/112] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.8/30 [110/12] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.12/30
[110/12] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
O 10.103.224.16/30
[110/12] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
[110/12] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.20/30
[110/12] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.24/30
[110/12] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
O 10.103.224.36/30
[110/110] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.40/30
[110/110] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
O 10.103.224.44/30
[110/110] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.48/30
[110/110] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
O 10.103.224.52/30
[110/14] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.56/30
[110/14] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
O 10.103.254.1/32 [110/11] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.254.2/32 [110/11] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
O 10.103.255.1/32 [110/11] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.255.2/32 [110/11] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
O 10.103.255.3/32 [110/13] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
[110/13] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.255.4/32 [110/13] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
[110/13] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.255.12/32
[110/111] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
[110/111] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.255.13/32
[110/111] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
[110/111] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.255.14/32
[110/15] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
[110/15] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
O 10.103.255.255/32
[110/11] via 10.103.224.33, 1w2d, TwentyFiveGigE1/1/2
[110/11] via 10.103.224.29, 1w2d, TwentyFiveGigE1/1/1
NYC103-Leaf-01#show ip ospf database
OSPF Router with ID (10.103.255.11) (Process ID 1)
Router Link States (Area 0)
Link ID ADV Router Age Seq# Checksum Link count
10.103.255.1 10.103.255.1 1932 0x8000019E 0x00A79F 17
10.103.255.2 10.103.255.2 949 0x800001A2 0x00808E 17
10.103.255.3 10.103.255.3 611 0x80000195 0x0021A6 6
10.103.255.4 10.103.255.4 1875 0x80000194 0x007849 6
10.103.255.11 10.103.255.11 448 0x80000192 0x00E43B 5
10.103.255.12 10.103.255.12 619 0x80000191 0x00E9AA 5
10.103.255.13 10.103.255.13 1458 0x80000190 0x002B47 5
10.103.255.14 10.103.255.14 328 0x80000191 0x0020AF 5
Type-5 AS External Link States
Link ID ADV Router Age Seq# Checksum Tag
0.0.0.0 10.103.255.3 611 0x8000018D 0x00DE14 1
0.0.0.0 10.103.255.4 1875 0x8000018C 0x0013DB 1
NYC103-Leaf-02
NYC103-Leaf-02#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
10.103.255.2 0 FULL/ - 00:00:34 10.103.224.41 GigabitEthernet1/0/2
10.103.255.1 0 FULL/ - 00:00:32 10.103.224.37 GigabitEthernet1/0/1
NYC103-Leaf-02#show ip ospf interface
Loopback0 is up, line protocol is up
Internet Address 10.103.255.12/32, Interface ID 76, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.12, Network Type LOOPBACK, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Loopback interface is treated as a stub Host
GigabitEthernet1/0/2 is up, line protocol is up (connected)
Internet Address 10.103.224.42/30, Interface ID 79, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.12, Network Type POINT_TO_POINT, Cost: 100
Topology-MTID Cost Disabled Shutdown Topology Name
0 100 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:05
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/3/3, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.2
Suppress hello for 0 neighbor(s)
GigabitEthernet1/0/1 is up, line protocol is up (connected)
Internet Address 10.103.224.38/30, Interface ID 78, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.12, Network Type POINT_TO_POINT, Cost: 100
Topology-MTID Cost Disabled Shutdown Topology Name
0 100 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:07
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/2/2, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.1
Suppress hello for 0 neighbor(s)
NYC103-Leaf-02#show ip ospf 1
Routing Process "ospf 1" with ID 10.103.255.12
Start time: 00:02:42.437, Time elapsed: 1w2d
Supports only single TOS(TOS0) routes
Supports opaque LSA
Supports Link-local Signaling (LLS)
Supports area transit capability
Supports NSSA (compatible with RFC 3101)
Supports Database Exchange Summary List Optimization (RFC 5243)
Event-log enabled, Maximum number of events: 1000, Mode: cyclic
Router is not originating router-LSAs with maximum metric
Initial SPF schedule delay 50 msecs
Minimum hold time between two consecutive SPFs 200 msecs
Maximum wait time between two consecutive SPFs 5000 msecs
Incremental-SPF disabled
Initial LSA throttle delay 50 msecs
Minimum hold time for LSA throttle 200 msecs
Maximum wait time for LSA throttle 5000 msecs
Minimum LSA arrival 100 msecs
LSA group pacing timer 240 secs
Interface flood pacing timer 33 msecs
Retransmission pacing timer 66 msecs
EXCHANGE/LOADING adjacency limit: initial 300, process maximum 300
Number of external LSA 2. Checksum Sum 0x00F1EF
Number of opaque AS LSA 0. Checksum Sum 0x000000
Number of DCbitless external and opaque AS LSA 0
Number of DoNotAge external and opaque AS LSA 0
Number of areas in this router is 1. 1 normal 0 stub 0 nssa
Number of areas transit capable is 0
External flood list length 0
IETF NSF helper support enabled
Cisco NSF helper support enabled
BFD is enabled
Reference bandwidth unit is 100000 mbps
Area BACKBONE(0)
Number of interfaces in this area is 3 (1 loopback)
Area has no authentication
SPF algorithm last executed 1w2d ago
SPF algorithm executed 22 times
Area ranges are
Number of LSA 8. Checksum Sum 0x03DBF7
Number of opaque link LSA 0. Checksum Sum 0x000000
Number of DCbitless LSA 0
Number of indication LSA 0
Number of DoNotAge LSA 0
Flood list length 0
Maintenance Mode ID: 139742029727248
Maintenance Mode: disabled
Maintenance Mode Timer: stopped (0)
Graceful Reload FSU Global status : None (global: None)
NYC103-Leaf-02#show ip route ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.224.41 to network 0.0.0.0
O*E1 0.0.0.0/0 [110/1202] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
[110/1202] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
10.0.0.0/8 is variably subnetted, 28 subnets, 2 masks
O 10.103.224.0/30
[110/202] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
[110/202] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.224.4/30
[110/202] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
[110/202] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.224.8/30
[110/102] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.224.12/30
[110/102] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
O 10.103.224.16/30
[110/102] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
[110/102] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.224.20/30
[110/102] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.224.24/30
[110/102] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
O 10.103.224.28/30
[110/110] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.224.32/30
[110/110] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
O 10.103.224.44/30
[110/200] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.224.48/30
[110/200] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
O 10.103.224.52/30
[110/104] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.224.56/30
[110/104] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
O 10.103.254.1/32
[110/101] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.254.2/32
[110/101] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
O 10.103.255.1/32
[110/101] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.255.2/32
[110/101] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
O 10.103.255.3/32
[110/103] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
[110/103] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.255.4/32
[110/103] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
[110/103] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.255.11/32
[110/111] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
[110/111] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.255.13/32
[110/201] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
[110/201] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.255.14/32
[110/105] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
[110/105] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
O 10.103.255.255/32
[110/101] via 10.103.224.41, 1w2d, GigabitEthernet1/0/2
[110/101] via 10.103.224.37, 1w2d, GigabitEthernet1/0/1
NYC103-Leaf-02#show ip ospf database
OSPF Router with ID (10.103.255.12) (Process ID 1)
Router Link States (Area 0)
Link ID ADV Router Age Seq# Checksum Link count
10.103.255.1 10.103.255.1 1935 0x8000019E 0x00A79F 17
10.103.255.2 10.103.255.2 952 0x800001A2 0x00808E 17
10.103.255.3 10.103.255.3 614 0x80000195 0x0021A6 6
10.103.255.4 10.103.255.4 1878 0x80000194 0x007849 6
10.103.255.11 10.103.255.11 453 0x80000192 0x00E43B 5
10.103.255.12 10.103.255.12 620 0x80000191 0x00E9AA 5
10.103.255.13 10.103.255.13 1461 0x80000190 0x002B47 5
10.103.255.14 10.103.255.14 331 0x80000191 0x0020AF 5
Type-5 AS External Link States
Link ID ADV Router Age Seq# Checksum Tag
0.0.0.0 10.103.255.3 614 0x8000018D 0x00DE14 1
0.0.0.0 10.103.255.4 1878 0x8000018C 0x0013DB 1
NYC103-Leaf-03
NYC103-Leaf-03#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
10.103.255.2 0 FULL/ - 00:00:33 10.103.224.49 GigabitEthernet1/0/2
10.103.255.1 0 FULL/ - 00:00:36 10.103.224.45 GigabitEthernet1/0/1
NYC103-Leaf-03#show ip ospf interface
Loopback0 is up, line protocol is up
Internet Address 10.103.255.13/32, Interface ID 76, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.13, Network Type LOOPBACK, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Loopback interface is treated as a stub Host
GigabitEthernet1/0/2 is up, line protocol is up (connected)
Internet Address 10.103.224.50/30, Interface ID 79, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.13, Network Type POINT_TO_POINT, Cost: 100
Topology-MTID Cost Disabled Shutdown Topology Name
0 100 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:00
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/3/3, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.2
Suppress hello for 0 neighbor(s)
GigabitEthernet1/0/1 is up, line protocol is up (connected)
Internet Address 10.103.224.46/30, Interface ID 78, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.13, Network Type POINT_TO_POINT, Cost: 100
Topology-MTID Cost Disabled Shutdown Topology Name
0 100 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:07
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/2/2, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.1
Suppress hello for 0 neighbor(s)
NYC103-Leaf-03#show ip ospf 1
Routing Process "ospf 1" with ID 10.103.255.13
Start time: 00:02:35.483, Time elapsed: 1w2d
Supports only single TOS(TOS0) routes
Supports opaque LSA
Supports Link-local Signaling (LLS)
Supports area transit capability
Supports NSSA (compatible with RFC 3101)
Supports Database Exchange Summary List Optimization (RFC 5243)
Event-log enabled, Maximum number of events: 1000, Mode: cyclic
Router is not originating router-LSAs with maximum metric
Initial SPF schedule delay 50 msecs
Minimum hold time between two consecutive SPFs 200 msecs
Maximum wait time between two consecutive SPFs 5000 msecs
Incremental-SPF disabled
Initial LSA throttle delay 50 msecs
Minimum hold time for LSA throttle 200 msecs
Maximum wait time for LSA throttle 5000 msecs
Minimum LSA arrival 100 msecs
LSA group pacing timer 240 secs
Interface flood pacing timer 33 msecs
Retransmission pacing timer 66 msecs
EXCHANGE/LOADING adjacency limit: initial 300, process maximum 300
Number of external LSA 2. Checksum Sum 0x00F1EF
Number of opaque AS LSA 0. Checksum Sum 0x000000
Number of DCbitless external and opaque AS LSA 0
Number of DoNotAge external and opaque AS LSA 0
Number of areas in this router is 1. 1 normal 0 stub 0 nssa
Number of areas transit capable is 0
External flood list length 0
IETF NSF helper support enabled
Cisco NSF helper support enabled
BFD is enabled
Reference bandwidth unit is 100000 mbps
Area BACKBONE(0)
Number of interfaces in this area is 3 (1 loopback)
Area has no authentication
SPF algorithm last executed 1w2d ago
SPF algorithm executed 25 times
Area ranges are
Number of LSA 8. Checksum Sum 0x03DBF7
Number of opaque link LSA 0. Checksum Sum 0x000000
Number of DCbitless LSA 0
Number of indication LSA 0
Number of DoNotAge LSA 0
Flood list length 0
Maintenance Mode ID: 140269749040656
Maintenance Mode: disabled
Maintenance Mode Timer: stopped (0)
Graceful Reload FSU Global status : None (global: None)
NYC103-Leaf-03#show ip route ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.224.49 to network 0.0.0.0
O*E1 0.0.0.0/0 [110/1202] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
[110/1202] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
10.0.0.0/8 is variably subnetted, 28 subnets, 2 masks
O 10.103.224.0/30
[110/202] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
[110/202] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.224.4/30
[110/202] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
[110/202] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.224.8/30
[110/102] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.224.12/30
[110/102] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
O 10.103.224.16/30
[110/102] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
[110/102] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.224.20/30
[110/102] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.224.24/30
[110/102] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
O 10.103.224.28/30
[110/110] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.224.32/30
[110/110] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
O 10.103.224.36/30
[110/200] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.224.40/30
[110/200] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
O 10.103.224.52/30
[110/104] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.224.56/30
[110/104] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
O 10.103.254.1/32
[110/101] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.254.2/32
[110/101] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
O 10.103.255.1/32
[110/101] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.255.2/32
[110/101] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
O 10.103.255.3/32
[110/103] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
[110/103] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.255.4/32
[110/103] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
[110/103] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.255.11/32
[110/111] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
[110/111] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.255.12/32
[110/201] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
[110/201] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.255.14/32
[110/105] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
[110/105] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
O 10.103.255.255/32
[110/101] via 10.103.224.49, 1w2d, GigabitEthernet1/0/2
[110/101] via 10.103.224.45, 1w2d, GigabitEthernet1/0/1
NYC103-Leaf-03#show ip ospf database
OSPF Router with ID (10.103.255.13) (Process ID 1)
Router Link States (Area 0)
Link ID ADV Router Age Seq# Checksum Link count
10.103.255.1 10.103.255.1 1938 0x8000019E 0x00A79F 17
10.103.255.2 10.103.255.2 955 0x800001A2 0x00808E 17
10.103.255.3 10.103.255.3 617 0x80000195 0x0021A6 6
10.103.255.4 10.103.255.4 1881 0x80000194 0x007849 6
10.103.255.11 10.103.255.11 456 0x80000192 0x00E43B 5
10.103.255.12 10.103.255.12 625 0x80000191 0x00E9AA 5
10.103.255.13 10.103.255.13 1462 0x80000190 0x002B47 5
10.103.255.14 10.103.255.14 334 0x80000191 0x0020AF 5
Type-5 AS External Link States
Link ID ADV Router Age Seq# Checksum Tag
0.0.0.0 10.103.255.3 617 0x8000018D 0x00DE14 1
0.0.0.0 10.103.255.4 1881 0x8000018C 0x0013DB 1
NYC103-Leaf-04
NYC103-Leaf-04#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
10.103.255.2 0 FULL/ - 00:00:35 10.103.224.57 TwentyFiveGigE1/1/2
10.103.255.1 0 FULL/ - 00:00:37 10.103.224.53 TwentyFiveGigE1/1/1
NYC103-Leaf-04#show ip ospf interface
Loopback0 is up, line protocol is up
Internet Address 10.103.255.14/32, Interface ID 76, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.14, Network Type LOOPBACK, Cost: 1
Topology-MTID Cost Disabled Shutdown Topology Name
0 1 no no Base
Enabled by interface config, including secondary ip addresses
Loopback interface is treated as a stub Host
TwentyFiveGigE1/1/2 is up, line protocol is up (connected)
Internet Address 10.103.224.58/30, Interface ID 80, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.14, Network Type POINT_TO_POINT, Cost: 4
Topology-MTID Cost Disabled Shutdown Topology Name
0 4 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:08
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/3/3, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.2
Suppress hello for 0 neighbor(s)
TwentyFiveGigE1/1/1 is up, line protocol is up (connected)
Internet Address 10.103.224.54/30, Interface ID 79, Area 0
Attached via Interface Enable
Process ID 1, Router ID 10.103.255.14, Network Type POINT_TO_POINT, Cost: 4
Topology-MTID Cost Disabled Shutdown Topology Name
0 4 no no Base
Enabled by interface config, including secondary ip addresses
Transmit Delay is 1 sec, State POINT_TO_POINT, BFD enabled
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 00:00:02
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Can be protected by per-prefix Loop-Free FastReroute
Can be used for per-prefix Loop-Free FastReroute repair paths
Not Protected by per-prefix TI-LFA
Index 1/2/2, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 2
Last flood scan time is 0 msec, maximum is 1 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 10.103.255.1
Suppress hello for 0 neighbor(s)
NYC103-Leaf-04#show ip ospf 1
Routing Process "ospf 1" with ID 10.103.255.14
Start time: 00:02:35.024, Time elapsed: 1w2d
Supports only single TOS(TOS0) routes
Supports opaque LSA
Supports Link-local Signaling (LLS)
Supports area transit capability
Supports NSSA (compatible with RFC 3101)
Supports Database Exchange Summary List Optimization (RFC 5243)
Event-log enabled, Maximum number of events: 1000, Mode: cyclic
Router is not originating router-LSAs with maximum metric
Initial SPF schedule delay 50 msecs
Minimum hold time between two consecutive SPFs 200 msecs
Maximum wait time between two consecutive SPFs 5000 msecs
Incremental-SPF disabled
Initial LSA throttle delay 50 msecs
Minimum hold time for LSA throttle 200 msecs
Maximum wait time for LSA throttle 5000 msecs
Minimum LSA arrival 100 msecs
LSA group pacing timer 240 secs
Interface flood pacing timer 33 msecs
Retransmission pacing timer 66 msecs
EXCHANGE/LOADING adjacency limit: initial 300, process maximum 300
Number of external LSA 2. Checksum Sum 0x00F1EF
Number of opaque AS LSA 0. Checksum Sum 0x000000
Number of DCbitless external and opaque AS LSA 0
Number of DoNotAge external and opaque AS LSA 0
Number of areas in this router is 1. 1 normal 0 stub 0 nssa
Number of areas transit capable is 0
External flood list length 0
IETF NSF helper support enabled
Cisco NSF helper support enabled
BFD is enabled
Reference bandwidth unit is 100000 mbps
Area BACKBONE(0)
Number of interfaces in this area is 3 (1 loopback)
Area has no authentication
SPF algorithm last executed 1w2d ago
SPF algorithm executed 12 times
Area ranges are
Number of LSA 8. Checksum Sum 0x03DBF7
Number of opaque link LSA 0. Checksum Sum 0x000000
Number of DCbitless LSA 0
Number of indication LSA 0
Number of DoNotAge LSA 0
Flood list length 0
Maintenance Mode ID: 139896724862480
Maintenance Mode: disabled
Maintenance Mode Timer: stopped (0)
Graceful Reload FSU Global status : None (global: None)
NYC103-Leaf-04#show ip route ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.224.57 to network 0.0.0.0
O*E1 0.0.0.0/0 [110/1106] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
[110/1106] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
10.0.0.0/8 is variably subnetted, 28 subnets, 2 masks
O 10.103.224.0/30
[110/106] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
[110/106] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.4/30
[110/106] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
[110/106] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.8/30 [110/6] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.12/30 [110/6] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
O 10.103.224.16/30 [110/6] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
[110/6] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.20/30 [110/6] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.24/30 [110/6] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
O 10.103.224.28/30
[110/14] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.32/30
[110/14] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
O 10.103.224.36/30
[110/104] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.40/30
[110/104] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
O 10.103.224.44/30
[110/104] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.224.48/30
[110/104] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
O 10.103.254.1/32 [110/5] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.254.2/32 [110/5] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
O 10.103.255.1/32 [110/5] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.255.2/32 [110/5] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
O 10.103.255.3/32 [110/7] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
[110/7] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.255.4/32 [110/7] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
[110/7] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.255.11/32
[110/15] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
[110/15] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.255.12/32
[110/105] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
[110/105] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.255.13/32
[110/105] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
[110/105] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
O 10.103.255.255/32
[110/5] via 10.103.224.57, 1w2d, TwentyFiveGigE1/1/2
[110/5] via 10.103.224.53, 1w2d, TwentyFiveGigE1/1/1
NYC103-Leaf-04#show ip ospf database
OSPF Router with ID (10.103.255.14) (Process ID 1)
Router Link States (Area 0)
Link ID ADV Router Age Seq# Checksum Link count
10.103.255.1 10.103.255.1 1942 0x8000019E 0x00A79F 17
10.103.255.2 10.103.255.2 958 0x800001A2 0x00808E 17
10.103.255.3 10.103.255.3 621 0x80000195 0x0021A6 6
10.103.255.4 10.103.255.4 1884 0x80000194 0x007849 6
10.103.255.11 10.103.255.11 459 0x80000192 0x00E43B 5
10.103.255.12 10.103.255.12 628 0x80000191 0x00E9AA 5
10.103.255.13 10.103.255.13 1467 0x80000190 0x002B47 5
10.103.255.14 10.103.255.14 335 0x80000191 0x0020AF 5
Type-5 AS External Link States
Link ID ADV Router Age Seq# Checksum Tag
0.0.0.0 10.103.255.3 621 0x8000018D 0x00DE14 1
0.0.0.0 10.103.255.4 1884 0x8000018C 0x0013DB 1
Loopback0 to Loopback0 on the Underlay
Note: Please note that extended ping (i.e. source-based ping) is not allowed from the Dashboard Terminal. Ping tests should be done through SSH.
NYC103-Spine-01
NYC103-Spine-01#ping 10.103.255.2 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.2, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-01#ping 10.103.255.3 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.3, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-01#ping 10.103.255.4 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.4, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-01#ping 10.103.255.11 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.11, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-01#ping 10.103.255.12 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.12, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-01#ping 10.103.255.13 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.13, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-01#ping 10.103.255.14 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.14, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-01#
NYC103-Spine-02
NYC103-Spine-02#ping 10.103.255.1 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.1, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-02#ping 10.103.255.3 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.3, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-02#ping 10.103.255.4 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.4, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-02#ping 10.103.255.11 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.11, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-02#ping 10.103.255.12 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.12, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-02#ping 10.103.255.13 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.13, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-02#ping 10.103.255.14 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.14, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Spine-02#
NYC103-Border-01
NYC103-Border-01#ping 10.103.255.1 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.1, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-01#ping 10.103.255.2 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.2, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-01#ping 10.103.255.4 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.4, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-01#ping 10.103.255.11 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.11, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-01#ping 10.103.255.12 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.12, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-01#ping 10.103.255.13 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.13, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-01#ping 10.103.255.14 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.14, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-01#
NYC103-Border-02
NYC103-Border-02#ping 10.103.255.1 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.1, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.4
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-02#ping 10.103.255.2 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.2, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.4
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-02#ping 10.103.255.3 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.3, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.4
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-02#ping 10.103.255.11 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.11, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.4
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-02#ping 10.103.255.12 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.12, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.4
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-02#ping 10.103.255.13 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.13, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.4
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-02#ping 10.103.255.14 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.14, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.4
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Border-02#
NYC103-Leaf-01
NYC103-Leaf-01#ping 10.103.255.1 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.1, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.11
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-01#ping 10.103.255.2 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.2, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.11
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-01#ping 10.103.255.3 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.3, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.11
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-01#ping 10.103.255.4 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.4, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.11
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-01#ping 10.103.255.12 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.12, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.11
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-01#ping 10.103.255.13 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.13, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.11
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-01#ping 10.103.255.14 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.14, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.11
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-01#
NYC103-Leaf-02
NYC103-Leaf-02#ping 10.103.255.1 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.1, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.12
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-02#ping 10.103.255.2 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.2, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.12
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-02#ping 10.103.255.3 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.3, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.12
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-02#ping 10.103.255.4 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.4, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.12
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-02#ping 10.103.255.11 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.11, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.12
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-02#ping 10.103.255.13 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.13, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.12
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-02#ping 10.103.255.14 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.14, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.12
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-02#
NYC103-Leaf-03
NYC103-Leaf-03#ping 10.103.255.1 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.1, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.13
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-03#ping 10.103.255.2 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.2, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.13
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-03#ping 10.103.255.3 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.3, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.13
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-03#ping 10.103.255.4 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.4, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.13
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-03#ping 10.103.255.11 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.11, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.13
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-03#ping 10.103.255.12 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.12, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.13
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-03#ping 10.103.255.14 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.14, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.13
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-03#
NYC103-Leaf-04
NYC103-Leaf-04#ping 10.103.255.1 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.1, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.14
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-04#ping 10.103.255.2 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.2, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.14
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-04#ping 10.103.255.3 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.3, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.14
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-04#ping 10.103.255.4 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.4, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.14
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-04#ping 10.103.255.11 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.11, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.14
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-04#ping 10.103.255.12 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.12, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.14
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-04#ping 10.103.255.13 source loopback0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.103.255.13, timeout is 2 seconds:
Packet sent with a source address of 10.103.255.14
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
NYC103-Leaf-04#
BGP L2VPN EVPN (All Fabric Switches)
NYC103-Spine-01
NYC103-Spine-01#show ip bgp l2vpn evpn summary
BGP router identifier 10.103.255.1, local AS number 65106
BGP table version is 5476, main routing table version 5476
79 network entries using 30336 bytes of memory
79 path entries using 18328 bytes of memory
24/24 BGP path/bestpath attribute entries using 7104 bytes of memory
2 BGP AS-PATH entries using 80 bytes of memory
20 BGP extended community entries using 880 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 56728 total bytes of memory
BGP activity 2758/2679 prefixes, 2777/2698 paths, scan interval 60 secs
84 networks peaked at 08:54:58 Jul 12 2024 EDT (4d10h ago)
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.103.255.3 4 65106 14616 18547 5476 0 0 1w2d 5
10.103.255.4 4 65106 14625 18570 5476 0 0 1w2d 5
10.103.255.11 4 65106 14631 18540 5476 0 0 1w2d 15
10.103.255.12 4 65106 18455 18538 5476 0 0 1w2d 32
10.103.255.13 4 65106 14633 18558 5476 0 0 1w2d 10
10.103.255.14 4 65106 14677 18552 5476 0 0 1w2d 12
NYC103-Spine-01#show ip bgp l2vpn evpn nei 10.103.255.11 advertised-routes
BGP table version is 5476, local router ID is 10.103.255.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
*>i [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
*>i [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:180
*>i [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:220
*>i [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.12:1
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B80][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6664F55B0][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6664F55B0][32][10.103.64.17]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D2E10][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D2E10][32][10.103.64.14]/24
10.103.255.12 0 100 0 ?
Route Distinguisher: 10.103.255.12:120
*>i [2][10.103.255.12:120][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][32][10.103.120.14]/24
10.103.255.12 0 100 0 ?
NYC103-Spine-01#
NYC103-Spine-01#show ip bgp l2vpn evpn nei 10.103.255.11 routes
BGP table version is 5476, local router ID is 10.103.255.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
*>i [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
*>i [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:180
*>i [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:220
*>i [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 65106:11
*>i [5][65106:11][0][24][10.103.64.0]/17
10.103.255.11 0 100 0 ?
*>i [5][65106:11][0][24][10.103.120.0]/17
10.103.255.11 0 100 0 ?
*>i [5][65106:11][0][24][10.103.180.0]/17
10.103.255.11 0 100 0 ?
Route Distinguisher: 65106:211
*>i [5][65106:211][0][24][10.103.220.0]/17
10.103.255.11 0 100 0 ?
Total number of prefixes 15
NYC103-Spine-01#show ip bgp l2vpn evpn
BGP table version is 5476, local router ID is 10.103.255.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
*>i [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
*>i [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:180
*>i [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:220
*>i [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.12:1
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B80][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6664F55B0][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6664F55B0][32][10.103.64.17]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D2E10][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D2E10][32][10.103.64.14]/24
10.103.255.12 0 100 0 ?
Route Distinguisher: 10.103.255.12:120
*>i [2][10.103.255.12:120][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][32][10.103.120.14]/24
10.103.255.12 0 100 0 ?
NYC103-Spine-01#
NYC103-Spine-01#show ip bgp l2vpn evpn route-type 2
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20, version 49
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:19 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24, version 113
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:30:35 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20, version 46
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:15 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20, version 45
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:14 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20, version 84
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:10:30 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24, version 118
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:30:45 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20, version 70
NYC103-Spine-01#
NYC103-Spine-01#show ip bgp l2vpn evpn route-type 5
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 100
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.64.0]/17, version 12
Paths: (1 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3), (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.128.0]/17, version 13
Paths: (1 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3), (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 102
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:4][0][18][10.103.64.0]/17, version 10
Paths: (1 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.4), (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:4][0][18][10.103.128.0]/17, version 11
Paths: (1 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.4), (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
NYC103-Spine-01#
NYC103-Spine-01#show ip bgp l2vpn evpn 0.0.0.0/0
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20, version 49
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:19 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20, version 46
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:15 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20, version 45
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:14 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20, version 84
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:10:30 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20, version 70
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:31 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20, version 201
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:29 EDT
BGP routing table entry for [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20, version 71
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200180
Extended Community: RT:65106:180 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:31 EDT
BGP routing table entry for [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20, version 72
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200220
Extended Community: RT:65106:220 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:31 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FD67B00][0][*]/20, version 81
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:50 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FD67B18][0][*]/20, version 94
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:13:21 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FE28B80][0][*]/20, version 80
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:48 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FE28B98][0][*]/20, version 78
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:40 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FE28F00][0][*]/20, version 82
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:52 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FE28F17][0][*]/20, version 75
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:34 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][C4D6664F55B0][0][*]/20, version 83
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:57 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][C4D6666D2E10][0][*]/20, version 79
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:46 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0BC6FD67B18][0][*]/20, version 87
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:11:17 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0BC6FE28B98][0][*]/20, version 64
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:17 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0BC6FE28F17][0][*]/20, version 4914
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 14 2024 16:34:14 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0CEC8FB4687][0][*]/20, version 204
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:37 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0CEC8FB47B7][0][*]/20, version 203
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:34 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0CEC8FB47DC][0][*]/20, version 202
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:31 EDT
BGP routing table entry for [2][10.103.255.12:180][0][48][A0BC6FD67B18][0][*]/20, version 89
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200180
Extended Community: RT:65106:180 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:11:17 EDT
BGP routing table entry for [2][10.103.255.12:180][0][48][A0BC6FE28B98][0][*]/20, version 65
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200180
Extended Community: RT:65106:180 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:17 EDT
BGP routing table entry for [2][10.103.255.12:180][0][48][A0BC6FE28F17][0][*]/20, version 4918
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200180
Extended Community: RT:65106:180 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 14 2024 16:42:34 EDT
BGP routing table entry for [2][10.103.255.12:220][0][48][A0BC6FD67B18][0][*]/20, version 90
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200220
Extended Community: RT:65106:220 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:11:18 EDT
BGP routing table entry for [2][10.103.255.12:220][0][48][A0BC6FE28B98][0][*]/20, version 66
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200220
Extended Community: RT:65106:220 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:17 EDT
BGP routing table entry for [2][10.103.255.12:220][0][48][A0BC6FE28F17][0][*]/20, version 5476
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200220
Extended Community: RT:65106:220 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 16 2024 11:35:29 EDT
BGP routing table entry for [2][10.103.255.13:1][0][48][C4D666D93140][0][*]/20, version 409
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.13 (metric 101) (via default) from 10.103.255.13 (10.103.255.13)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 8 2024 10:58:10 EDT
BGP routing table entry for [2][10.103.255.13:120][0][48][A0CEC8FB4689][0][*]/20, version 207
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.13 (metric 101) (via default) from 10.103.255.13 (10.103.255.13)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:02 EDT
BGP routing table entry for [2][10.103.255.13:120][0][48][A0CEC8FB47A7][0][*]/20, version 206
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.13 (metric 101) (via default) from 10.103.255.13 (10.103.255.13)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:59 EDT
BGP routing table entry for [2][10.103.255.14:1][0][48][9433D8078517][0][*]/20, version 2692
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.14 (metric 5) (via default) from 10.103.255.14 (10.103.255.14)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 12 2024 09:16:15 EDT
BGP routing table entry for [2][10.103.255.14:1][0][48][9433D8078518][0][*]/20, version 2690
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.14 (metric 5) (via default) from 10.103.255.14 (10.103.255.14)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 12 2024 09:16:15 EDT
BGP routing table entry for [2][10.103.255.14:1][0][48][9433D8078547][0][*]/20, version 2698
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.14 (metric 5) (via default) from 10.103.255.14 (10.103.255.14)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 12 2024 09:16:23 EDT
BGP routing table entry for [2][10.103.255.14:1][0][48][C4D6666D0F80][0][*]/20, version 2704
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.14 (metric 5) (via default) from 10.103.255.14 (10.103.255.14)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 12 2024 09:17:36 EDT
BGP routing table entry for [2][10.103.255.14:120][0][48][A0CEC8FB4677][0][*]/20, version 2695
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.14 (metric 5) (via default) from 10.103.255.14 (10.103.255.14)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 12 2024 09:16:15 EDT
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 100
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 102
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:23][0][0][0.0.0.0]/17, version 101
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65100 65100 65100, (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin IGP, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303002, MPLS VPN Label 0
Extended Community: RT:65106:2 ENCAP:8 Router MAC:246C.847E.E0CB
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:24][0][0][0.0.0.0]/17, version 103
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65100 65100 65100, (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin IGP, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303002, MPLS VPN Label 0
Extended Community: RT:65106:2 ENCAP:8 Router MAC:3488.1824.764B
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
NYC103-Spine-01# show ip bgp l2vpn evpn route-type 5
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 100
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.64.0]/17, version 12
Paths: (1 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3), (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.128.0]/17, version 13
Paths: (1 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3), (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 102
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:4][0][18][10.103.64.0]/17, version 10
Paths: (1 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.4), (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:4][0][18][10.103.128.0]/17, version 11
Paths: (1 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.4), (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
NYC103-Spine-01#
NYC103-Spine-02
NYC103-Spine-02#show ip bgp l2vpn evpn summary
BGP router identifier 10.103.255.2, local AS number 65106
BGP table version is 5476, main routing table version 5476
79 network entries using 30336 bytes of memory
79 path entries using 18328 bytes of memory
24/24 BGP path/bestpath attribute entries using 7104 bytes of memory
2 BGP AS-PATH entries using 80 bytes of memory
20 BGP extended community entries using 880 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 56728 total bytes of memory
BGP activity 2758/2679 prefixes, 2777/2698 paths, scan interval 60 secs
84 networks peaked at 08:54:58 Jul 12 2024 EDT (4d10h ago)
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.103.255.3 4 65106 14608 18577 5476 0 0 1w2d 5
10.103.255.4 4 65106 14618 18552 5476 0 0 1w2d 5
10.103.255.11 4 65106 14636 18563 5476 0 0 1w2d 15
10.103.255.12 4 65106 18452 18545 5476 0 0 1w2d 32
10.103.255.13 4 65106 14646 18564 5476 0 0 1w2d 10
10.103.255.14 4 65106 14673 18554 5476 0 0 1w2d 12
NYC103-Spine-02#show ip bgp l2vpn evpn nei 10.103.255.11 advertised-routes
BGP table version is 5476, local router ID is 10.103.255.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
*>i [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
*>i [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:180
*>i [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:220
*>i [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.12:1
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B80][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6664F55B0][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6664F55B0][32][10.103.64.17]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D2E10][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D2E10][32][10.103.64.14]/24
10.103.255.12 0 100 0 ?
Route Distinguisher: 10.103.255.12:120
*>i [2][10.103.255.12:120][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][32][10.103.120.14]/24
10.103.255.12 0 100 0 ?
NYC103-Spine-02#
NYC103-Spine-02#show ip bgp l2vpn evpn nei 10.103.255.11 routes
BGP table version is 5476, local router ID is 10.103.255.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
*>i [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
*>i [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:180
*>i [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:220
*>i [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 65106:11
*>i [5][65106:11][0][24][10.103.64.0]/17
10.103.255.11 0 100 0 ?
*>i [5][65106:11][0][24][10.103.120.0]/17
10.103.255.11 0 100 0 ?
*>i [5][65106:11][0][24][10.103.180.0]/17
10.103.255.11 0 100 0 ?
Route Distinguisher: 65106:211
*>i [5][65106:211][0][24][10.103.220.0]/17
10.103.255.11 0 100 0 ?
Total number of prefixes 15
NYC103-Spine-02#show ip bgp l2vpn evpn
BGP table version is 5476, local router ID is 10.103.255.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
*>i [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
*>i [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:180
*>i [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:220
*>i [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.12:1
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B80][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6664F55B0][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6664F55B0][32][10.103.64.17]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D2E10][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D2E10][32][10.103.64.14]/24
10.103.255.12 0 100 0 ?
Route Distinguisher: 10.103.255.12:120
*>i [2][10.103.255.12:120][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][32][10.103.120.14]/24
10.103.255.12 0 100 0 ?
NYC103-Spine-02#
NYC103-Spine-02#show ip bgp l2vpn evpn route-type 2
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20, version 49
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:19 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24, version 113
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:30:35 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20, version 46
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:15 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20, version 45
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:14 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20, version 84
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:10:30 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24, version 118
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:30:45 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20, version 70
NYC103-Spine-02#
NYC103-Spine-02#show ip bgp l2vpn evpn route-type 5
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 100
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.64.0]/17, version 12
Paths: (1 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3), (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.128.0]/17, version 13
Paths: (1 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3), (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 102
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:4][0][18][10.103.64.0]/17, version 10
Paths: (1 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.4), (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:4][0][18][10.103.128.0]/17, version 11
Paths: (1 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.4), (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
NYC103-Spine-02#
NYC103-Spine-02#show ip bgp l2vpn evpn 0.0.0.0/0
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20, version 49
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:19 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20, version 46
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:15 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20, version 45
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:14 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20, version 84
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:10:30 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20, version 70
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:31 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20, version 201
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:29 EDT
BGP routing table entry for [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20, version 71
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200180
Extended Community: RT:65106:180 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:31 EDT
BGP routing table entry for [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20, version 72
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200220
Extended Community: RT:65106:220 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:31 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FD67B00][0][*]/20, version 81
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:50 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FD67B18][0][*]/20, version 94
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:13:21 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FE28B80][0][*]/20, version 80
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:49 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FE28B98][0][*]/20, version 78
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:40 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FE28F00][0][*]/20, version 82
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:52 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FE28F17][0][*]/20, version 75
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:34 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][C4D6664F55B0][0][*]/20, version 83
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:58 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][C4D6666D2E10][0][*]/20, version 79
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:46 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0BC6FD67B18][0][*]/20, version 87
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:11:17 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0BC6FE28B98][0][*]/20, version 64
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:17 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0BC6FE28F17][0][*]/20, version 4914
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 14 2024 16:34:14 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0CEC8FB4687][0][*]/20, version 204
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:37 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0CEC8FB47B7][0][*]/20, version 203
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:34 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0CEC8FB47DC][0][*]/20, version 202
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:31 EDT
BGP routing table entry for [2][10.103.255.12:180][0][48][A0BC6FD67B18][0][*]/20, version 89
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200180
Extended Community: RT:65106:180 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:11:17 EDT
BGP routing table entry for [2][10.103.255.12:180][0][48][A0BC6FE28B98][0][*]/20, version 65
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200180
Extended Community: RT:65106:180 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:17 EDT
BGP routing table entry for [2][10.103.255.12:180][0][48][A0BC6FE28F17][0][*]/20, version 4918
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200180
Extended Community: RT:65106:180 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 14 2024 16:42:34 EDT
BGP routing table entry for [2][10.103.255.12:220][0][48][A0BC6FD67B18][0][*]/20, version 90
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200220
Extended Community: RT:65106:220 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:11:18 EDT
BGP routing table entry for [2][10.103.255.12:220][0][48][A0BC6FE28B98][0][*]/20, version 66
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200220
Extended Community: RT:65106:220 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:09:17 EDT
BGP routing table entry for [2][10.103.255.12:220][0][48][A0BC6FE28F17][0][*]/20, version 5476
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.12 (metric 101) (via default) from 10.103.255.12 (10.103.255.12)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200220
Extended Community: RT:65106:220 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 16 2024 11:35:29 EDT
BGP routing table entry for [2][10.103.255.13:1][0][48][C4D666D93140][0][*]/20, version 409
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.13 (metric 101) (via default) from 10.103.255.13 (10.103.255.13)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 8 2024 10:58:10 EDT
BGP routing table entry for [2][10.103.255.13:120][0][48][A0CEC8FB4689][0][*]/20, version 207
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.13 (metric 101) (via default) from 10.103.255.13 (10.103.255.13)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:02 EDT
BGP routing table entry for [2][10.103.255.13:120][0][48][A0CEC8FB47A7][0][*]/20, version 206
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.13 (metric 101) (via default) from 10.103.255.13 (10.103.255.13)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:59 EDT
BGP routing table entry for [2][10.103.255.14:1][0][48][9433D8078517][0][*]/20, version 2692
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.14 (metric 5) (via default) from 10.103.255.14 (10.103.255.14)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 12 2024 09:16:15 EDT
BGP routing table entry for [2][10.103.255.14:1][0][48][9433D8078518][0][*]/20, version 2690
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.14 (metric 5) (via default) from 10.103.255.14 (10.103.255.14)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 12 2024 09:16:15 EDT
BGP routing table entry for [2][10.103.255.14:1][0][48][9433D8078547][0][*]/20, version 2698
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.14 (metric 5) (via default) from 10.103.255.14 (10.103.255.14)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 12 2024 09:16:23 EDT
BGP routing table entry for [2][10.103.255.14:1][0][48][C4D6666D0F80][0][*]/20, version 2704
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.14 (metric 5) (via default) from 10.103.255.14 (10.103.255.14)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 12 2024 09:17:36 EDT
BGP routing table entry for [2][10.103.255.14:120][0][48][A0CEC8FB4677][0][*]/20, version 2695
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.14 (metric 5) (via default) from 10.103.255.14 (10.103.255.14)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 12 2024 09:16:15 EDT
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 100
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 102
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:23][0][0][0.0.0.0]/17, version 101
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65100 65100 65100, (Received from a RR-client)
10.103.255.3 (metric 3) (via default) from 10.103.255.3 (10.103.255.3)
Origin IGP, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303002, MPLS VPN Label 0
Extended Community: RT:65106:2 ENCAP:8 Router MAC:246C.847E.E0CB
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:24][0][0][0.0.0.0]/17, version 103
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65100 65100 65100, (Received from a RR-client)
10.103.255.4 (metric 3) (via default) from 10.103.255.4 (10.103.255.4)
Origin IGP, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303002, MPLS VPN Label 0
Extended Community: RT:65106:2 ENCAP:8 Router MAC:3488.1824.764B
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
NYC103-Spine-02#sh ip bgp l2vpn evpn a0:ce:c8:fb:46:7f
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20, version 201
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:29 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 208
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (Received from a RR-client)
10.103.255.11 (metric 11) (via default) from 10.103.255.11 (10.103.255.11)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:05 EDT
NYC103-Spine-02#
NYC103-Border-01
NYC103-Border-01#show ip bgp l2vpn evpn summary
BGP router identifier 10.103.255.3, local AS number 65106
BGP table version is 144, main routing table version 144
43 network entries using 16512 bytes of memory
81 path entries using 18792 bytes of memory
20/20 BGP path/bestpath attribute entries using 5920 bytes of memory
10 BGP rrinfo entries using 400 bytes of memory
3 BGP AS-PATH entries using 104 bytes of memory
18 BGP extended community entries using 768 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 42496 total bytes of memory
BGP activity 138/62 prefixes, 280/150 paths, scan interval 60 secs
46 networks peaked at 08:54:58 Jul 12 2024 EDT (4d10h ago)
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.103.255.1 4 65106 18553 14622 144 0 0 1w2d 38
10.103.255.2 4 65106 18578 14610 144 0 0 1w2d 38
NYC103-Border-01#show ip bgp l2vpn evpn
BGP table version is 144, local router ID is 10.103.255.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
* i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.12:1
* i [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][C4D6664F55B0][32][10.103.64.17]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][C4D6666D2E10][32][10.103.64.14]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
Route Distinguisher: 10.103.255.12:120
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][32][10.103.120.14]/24
10.103.255.12 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:120][0][48][A0CEC8FB47B7][32][10.103.120.13]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:120][0][48][A0CEC8FB47DC][32][10.103.120.11]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
Route Distinguisher: 10.103.255.13:1
* i [2][10.103.255.13:1][0][48][C4D666D93140][32][10.103.64.20]/24
10.103.255.13 0 100 0 ?
*>i 10.103.255.13 0 100 0 ?
Route Distinguisher: 10.103.255.13:120
* i [2][10.103.255.13:120][0][48][A0CEC8FB4689][32][10.103.120.23]/24
10.103.255.13 0 100 0 ?
*>i 10.103.255.13 0 100 0 ?
* i [2][10.103.255.13:120][0][48][A0CEC8FB47A7][32][10.103.120.16]/24
10.103.255.13 0 100 0 ?
*>i 10.103.255.13 0 100 0 ?
Route Distinguisher: 10.103.255.14:1
* i [2][10.103.255.14:1][0][48][9433D8078547][32][10.103.64.26]/24
10.103.255.14 0 100 0 ?
*>i 10.103.255.14 0 100 0 ?
*>i [2][10.103.255.14:1][0][48][C4D6666D0F80][32][10.103.64.28]/24
10.103.255.14 0 100 0 ?
* i 10.103.255.14 0 100 0 ?
Route Distinguisher: 10.103.255.14:120
* i [2][10.103.255.14:120][0][48][A0CEC8FB4677][32][10.103.120.15]/24
10.103.255.14 0 100 0 ?
*>i 10.103.255.14 0 100 0 ?
Route Distinguisher: 65106:3 (default for vrf campus)
*> [5][65106:3][0][0][0.0.0.0]/17
10.103.64.1 0 65102 65100 65101 ?
*> [5][65106:3][0][18][10.103.64.0]/17
0.0.0.0 32768 i
NYC103-Border-01#
NYC103-Border-01#show ip bgp l2vpn evpn route-type 2
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24, version 49
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:30:35 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:30:35 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24, version 55
Paths: (2 available, best #1, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:30:45 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:30:45 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 62
Paths: (2 available, best #1, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:05 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 19:44:05 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24, version 46
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.12 (metric 103) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
NYC103-Border-01#
NYC103-Border-01#
NYC103-Border-01#show ip bgp l2vpn evpn route-type 5
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 38
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, imported path from base
10.103.64.1 (via vrf campus) from 10.103.64.1 (10.100.255.3)
Origin incomplete, localpref 100, valid, external, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, local vtep: 10.103.255.3, VNI Label 303001, MPLS VPN Label 20
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.64.0]/17, version 10
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3), imported path from base
0.0.0.0 (via default) from 0.0.0.0 (10.103.255.3)
Origin IGP, localpref 100, weight 32768, valid, aggregated, local, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, local vtep: 10.103.255.3, VNI Label 303001, MPLS VPN Label 16
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:23 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.128.0]/17, version 11
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3), imported path from base
0.0.0.0 (via default) from 0.0.0.0 (10.103.255.3)
Origin IGP, localpref 100, weight 32768, valid, aggregated, local, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, local vtep: 10.103.255.3, VNI Label 303001, MPLS VPN Label 17
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:23 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 40
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101
10.103.255.4 (metric 5) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
Originator: 10.103.255.4, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65101
10.103.255.4 (metric 5) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
Originator: 10.103.255.4, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:4][0][18][10.103.64.0]/17, version 14
Paths: (2 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Not advertised to any peer
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.4)
10.103.255.4 (metric 5) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
Originator: 10.103.255.4, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.4)
10.103.255.4 (metric 5) (via default) from 10.103.255.2 (10.103.255.2)
NYC103-Border-01#
NYC103-Border-01#show ip bgp l2vpn evpn 0.0.0.0/0
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 38
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, imported path from base
10.103.64.1 (via vrf campus) from 10.103.64.1 (10.100.255.3)
Origin incomplete, localpref 100, valid, external, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, local vtep: 10.103.255.3, VNI Label 303001, MPLS VPN Label 20
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 40
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101
10.103.255.4 (metric 5) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
Originator: 10.103.255.4, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65101
10.103.255.4 (metric 5) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
Originator: 10.103.255.4, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:23][0][0][0.0.0.0]/17, version 39
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65100 65100 65100, imported path from base
10.103.64.9 (via vrf guest) from 10.103.64.9 (10.100.255.3)
Origin IGP, localpref 100, valid, external, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, local vtep: 10.103.255.3, VNI Label 303002, MPLS VPN Label 21
Extended Community: RT:65106:2 ENCAP:8 Router MAC:246C.847E.E0CB
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:24][0][0][0.0.0.0]/17, version 41
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65100 65100 65100
10.103.255.4 (metric 5) (via default) from 10.103.255.2 (10.103.255.2)
Origin IGP, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303002, MPLS VPN Label 0
Extended Community: RT:65106:2 ENCAP:8 Router MAC:3488.1824.764B
Originator: 10.103.255.4, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65100 65100 65100
10.103.255.4 (metric 5) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303002, MPLS VPN Label 0
Extended Community: RT:65106:2 ENCAP:8 Router MAC:3488.1824.764B
Originator: 10.103.255.4, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
NYC103-Border-01#
NYC103-Border-01#sh ip bgp l2vpn evpn a0:ce:c8:fb:46:7f
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 62
Paths: (2 available, best #1, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:05 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 19:44:05 EDT
NYC103-Border-01#
NYC103-Border-02
NYC103-Border-02#show ip bgp l2vpn evpn summary
BGP router identifier 10.103.255.4, local AS number 65106
BGP table version is 141, main routing table version 141
43 network entries using 16512 bytes of memory
81 path entries using 18792 bytes of memory
20/20 BGP path/bestpath attribute entries using 5920 bytes of memory
10 BGP rrinfo entries using 400 bytes of memory
3 BGP AS-PATH entries using 104 bytes of memory
18 BGP extended community entries using 768 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 42496 total bytes of memory
BGP activity 136/60 prefixes, 276/146 paths, scan interval 60 secs
46 networks peaked at 08:54:58 Jul 12 2024 EDT (4d10h ago)
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.103.255.1 4 65106 18582 14637 141 0 0 1w2d 38
10.103.255.2 4 65106 18560 14626 141 0 0 1w2d 38
NYC103-Border-02#show ip bgp l2vpn evpn
BGP table version is 141, local router ID is 10.103.255.4
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
* i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.12:1
* i [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][C4D6664F55B0][32][10.103.64.17]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][C4D6666D2E10][32][10.103.64.14]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
Route Distinguisher: 10.103.255.12:120
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][32][10.103.120.14]/24
10.103.255.12 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:120][0][48][A0CEC8FB47B7][32][10.103.120.13]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:120][0][48][A0CEC8FB47DC][32][10.103.120.11]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
Route Distinguisher: 10.103.255.13:1
* i [2][10.103.255.13:1][0][48][C4D666D93140][32][10.103.64.20]/24
10.103.255.13 0 100 0 ?
*>i 10.103.255.13 0 100 0 ?
Route Distinguisher: 10.103.255.13:120
* i [2][10.103.255.13:120][0][48][A0CEC8FB4689][32][10.103.120.23]/24
10.103.255.13 0 100 0 ?
*>i 10.103.255.13 0 100 0 ?
* i [2][10.103.255.13:120][0][48][A0CEC8FB47A7][32][10.103.120.16]/24
10.103.255.13 0 100 0 ?
*>i 10.103.255.13 0 100 0 ?
Route Distinguisher: 10.103.255.14:1
* i [2][10.103.255.14:1][0][48][9433D8078547][32][10.103.64.26]/24
10.103.255.14 0 100 0 ?
*>i 10.103.255.14 0 100 0 ?
*>i [2][10.103.255.14:1][0][48][C4D6666D0F80][32][10.103.64.28]/24
10.103.255.14 0 100 0 ?
* i 10.103.255.14 0 100 0 ?
Route Distinguisher: 10.103.255.14:120
* i [2][10.103.255.14:120][0][48][A0CEC8FB4677][32][10.103.120.15]/24
10.103.255.14 0 100 0 ?
*>i 10.103.255.14 0 100 0 ?
Route Distinguisher: 65106:3
* i [5][65106:3][0][0][0.0.0.0]/17
10.103.255.3 0 100 0 65102 65100 65101 ?
*>i 10.103.255.3 0 100 0 65102 65100 65101 ?
*>i [5][65106:3][0][18][10.103.64.0]/17
NYC103-Border-02#
NYC103-Border-02#show ip bgp l2vpn evpn route-type 2
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24, version 46
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:30:35 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:30:35 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24, version 52
Paths: (2 available, best #1, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:30:45 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:30:45 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 59
Paths: (2 available, best #1, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:05 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 19:44:05 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24, version 43
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.12 (metric 103) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
NYC103-Border-02#
NYC103-Border-02#show ip bgp l2vpn evpn route-type 5
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 37
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101
10.103.255.3 (metric 5) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65101
10.103.255.3 (metric 5) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.64.0]/17, version 14
Paths: (2 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Not advertised to any peer
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 5) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 5) (via default) from 10.103.255.2 (10.103.255.2)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.128.0]/17, version 15
Paths: (2 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Not advertised to any peer
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 5) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 5) (via default) from 10.103.255.2 (10.103.255.2)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 35
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, imported path from base
10.103.64.5 (via vrf campus) from 10.103.64.5 (10.100.255.3)
Origin incomplete, localpref 100, valid, external, best
NYC103-Border-02#
NYC103-Border-02#show ip bgp l2vpn evpn 0.0.0.0/0
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 37
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101
10.103.255.3 (metric 5) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65101
10.103.255.3 (metric 5) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 35
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65101, imported path from base
10.103.64.5 (via vrf campus) from 10.103.64.5 (10.100.255.3)
Origin incomplete, localpref 100, valid, external, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, local vtep: 10.103.255.4, VNI Label 303001, MPLS VPN Label 20
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:23][0][0][0.0.0.0]/17, version 38
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65100 65100 65100
10.103.255.3 (metric 5) (via default) from 10.103.255.2 (10.103.255.2)
Origin IGP, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303002, MPLS VPN Label 0
Extended Community: RT:65106:2 ENCAP:8 Router MAC:246C.847E.E0CB
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65100 65100 65100
10.103.255.3 (metric 5) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303002, MPLS VPN Label 0
Extended Community: RT:65106:2 ENCAP:8 Router MAC:246C.847E.E0CB
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:24][0][0][0.0.0.0]/17, version 36
Paths: (1 available, best #1, table EVPN-BGP-Table)
Advertised to update-groups:
1
Refresh Epoch 1
65102 65100 65100 65100 65100, imported path from base
10.103.64.13 (via vrf guest) from 10.103.64.13 (10.100.255.3)
Origin IGP, localpref 100, valid, external, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, local vtep: 10.103.255.4, VNI Label 303002, MPLS VPN Label 21
Extended Community: RT:65106:2 ENCAP:8 Router MAC:3488.1824.764B
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
NYC103-Border-02#sh ip bgp l2vpn evpn a0:ce:c8:fb:46:7f
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 59
Paths: (2 available, best #1, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:05 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 13) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 19:44:05 EDT
NYC103-Leaf-01
NYC103-Leaf-01#show ip bgp l2vpn evpn summary
BGP router identifier 10.103.255.11, local AS number 65106
BGP table version is 16144, main routing table version 16144
127 network entries using 48768 bytes of memory
191 path entries using 44312 bytes of memory
29/29 BGP path/bestpath attribute entries using 8584 bytes of memory
10 BGP rrinfo entries using 400 bytes of memory
2 BGP AS-PATH entries using 80 bytes of memory
22 BGP extended community entries using 928 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 103072 total bytes of memory
BGP activity 5536/5385 prefixes, 10646/10415 paths, scan interval 60 secs
137 networks peaked at 08:54:58 Jul 12 2024 EDT (4d10h ago)
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.103.255.1 4 65106 18556 14647 16144 0 0 1w2d 64
10.103.255.2 4 65106 18574 14647 16144 0 0 1w2d 64
NYC103-Leaf-01#show ip bgp l2vpn evpn nei 10.103.255.1 advertised-routes
BGP table version is 16144, local router ID is 10.103.255.11
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
*> [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
0.0.0.0 32768 ?
*> [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
0.0.0.0 32768 ?
Route Distinguisher: 10.103.255.11:120
*> [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
0.0.0.0 32768 ?
Route Distinguisher: 10.103.255.11:180
*> [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
0.0.0.0 32768 ?
Route Distinguisher: 10.103.255.11:220
*> [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
0.0.0.0 32768 ?
Route Distinguisher: 65106:11 (default for vrf campus)
*> [5][65106:11][0][24][10.103.64.0]/17
0.0.0.0 0 32768 ?
*> [5][65106:11][0][24][10.103.120.0]/17
0.0.0.0 0 32768 ?
*> [5][65106:11][0][24][10.103.180.0]/17
0.0.0.0 0 32768 ?
Route Distinguisher: 65106:211 (default for vrf guest)
*> [5][65106:211][0][24][10.103.220.0]/17
0.0.0.0 0 32768 ?
Total number of prefixes 15
NYC103-Leaf-01#show ip bgp l2vpn evpn nei 10.103.255.1 routes
BGP table version is 16144, local router ID is 10.103.255.11
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
*>i [2][10.103.255.11:1][0][48][9433D8078517][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][9433D8078518][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][9433D8078547][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][9433D8078547][32][10.103.64.26]/24
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FD67B00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FE28B80][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FE28F00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0CEC8FB4677][32][10.103.120.15]/24
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0CEC8FB4687][32][10.103.120.14]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0CEC8FB4689][32][10.103.120.23]/24
10.103.255.13 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0CEC8FB47A7][32][10.103.120.16]/24
10.103.255.13 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0CEC8FB47B7][32][10.103.120.13]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0CEC8FB47DC][32][10.103.120.11]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D6664F55B0][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D6664F55B0][32][10.103.64.17]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D6666D0F80][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D6666D0F80][32][10.103.64.28]/24
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D6666D2E10][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D6666D2E10][32][10.103.64.14]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D666D93140][0][*]/20
10.103.255.13 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D666D93140][32][10.103.64.20]/24
10.103.255.13 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
*>i [2][10.103.255.11:120][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB4677][0][*]/20
10.103.255.14 0 100 0 ?
NYC103-Leaf-01#
NYC103-Leaf-01#show ip bgp l2vpn evpn
BGP table version is 16144, local router ID is 10.103.255.11
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
*> [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
0.0.0.0 32768 ?
*> [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
0.0.0.0 32768 ?
*>i [2][10.103.255.11:1][0][48][9433D8078517][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][9433D8078518][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][9433D8078547][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][9433D8078547][32][10.103.64.26]/24
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FD67B00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FE28B80][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FE28F00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0CEC8FB4677][32][10.103.120.15]/24
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0CEC8FB4687][32][10.103.120.14]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0CEC8FB4689][32][10.103.120.23]/24
10.103.255.13 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0CEC8FB47A7][32][10.103.120.16]/24
10.103.255.13 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0CEC8FB47B7][32][10.103.120.13]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][A0CEC8FB47DC][32][10.103.120.11]/24
10.103.255.12 0 100 0 ?
*> [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
0.0.0.0 32768 ?
*>i [2][10.103.255.11:1][0][48][C4D6664F55B0][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D6664F55B0][32][10.103.64.17]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D6666D0F80][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D6666D0F80][32][10.103.64.28]/24
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D6666D2E10][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D6666D2E10][32][10.103.64.14]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C4D666D93140][0][*]/20
NYC103-Leaf-01#
NYC103-Leaf-01#show ip bgp l2vpn evpn route-type 2
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20, version 91
Paths: (1 available, best #1, table evi_1)
Advertised to update-groups:
1
Refresh Epoch 1
Local
0.0.0.0 (via default) from 0.0.0.0 (10.103.255.11)
Origin incomplete, localpref 100, weight 32768, valid, sourced, local, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Local irb vxlan vtep:
vrf:campus, l3-vni:303001
local router mac:3488.1828.4B72
core-irb interface:Vlan3001
vtep-ip:10.103.255.11
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:19 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24, version 252
Paths: (1 available, best #1, table evi_1)
Advertised to update-groups:
1
Refresh Epoch 1
Local
0.0.0.0 (via default) from 0.0.0.0 (10.103.255.11)
Origin incomplete, localpref 100, weight 32768, valid, sourced, local, best
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Local irb vxlan vtep:
vrf:campus, l3-vni:303001
local router mac:3488.1828.4B72
core-irb interface:Vlan3001
vtep-ip:10.103.255.11
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:30:35 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20, version 84
Paths: (1 available, best #1, table evi_1)
Advertised to update-groups:
1
Refresh Epoch 1
Local
0.0.0.0 (via default) from 0.0.0.0 (10.103.255.11)
Origin incomplete, localpref 100, weight 32768, valid, sourced, local, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Local irb vxlan vtep:
vrf:campus, l3-vni:303001
local router mac:3488.1828.4B72
core-irb interface:Vlan3001
vtep-ip:10.103.255.11
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:15 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20, version 83
Paths: (1 available, best #1, table evi_1)
Advertised to update-groups:
1
Refresh Epoch 1
Local
0.0.0.0 (via default) from 0.0.0.0 (10.103.255.11)
Origin incomplete, localpref 100, weight 32768, valid, sourced, local, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Local irb vxlan vtep:
vrf:campus, l3-vni:303001
local router mac:3488.1828.4B72
core-irb interface:Vlan3001
vtep-ip:10.103.255.11
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:14 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][9433D8078517][0][*]/20, version 7893
Paths: (1 available, best #1, table evi_1)
Not advertised to any peer
Refresh Epoch 1
Local, imported path from [2][10.103.255.14:1][0][48][9433D8078517][0][*]/20 (global)
NYC103-Leaf-01#
NYC103-Leaf-01#show ip bgp l2vpn evpn route-type 5
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 222
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101
10.103.255.3 (metric 13) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65101
10.103.255.3 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.64.0]/17, version 2
Paths: (2 available, best #1, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 13) (via default) from 10.103.255.2 (10.103.255.2)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.128.0]/17, version 3
Paths: (2 available, best #1, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 13) (via default) from 10.103.255.2 (10.103.255.2)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 224
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101
10.103.255.4 (metric 13) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
Originator: 10.103.255.4, Cluster list: 10.103.255.2
NYC103-Leaf-01#
NYC103-Leaf-01#show ip bgp l2vpn evpn 0.0.0.0/0
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20, version 91
Paths: (1 available, best #1, table evi_1)
Advertised to update-groups:
1
Refresh Epoch 1
Local
0.0.0.0 (via default) from 0.0.0.0 (10.103.255.11)
Origin incomplete, localpref 100, weight 32768, valid, sourced, local, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Local irb vxlan vtep:
vrf:campus, l3-vni:303001
local router mac:3488.1828.4B72
core-irb interface:Vlan3001
vtep-ip:10.103.255.11
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:19 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20, version 84
Paths: (1 available, best #1, table evi_1)
Advertised to update-groups:
1
Refresh Epoch 1
Local
0.0.0.0 (via default) from 0.0.0.0 (10.103.255.11)
Origin incomplete, localpref 100, weight 32768, valid, sourced, local, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Local irb vxlan vtep:
vrf:campus, l3-vni:303001
local router mac:3488.1828.4B72
core-irb interface:Vlan3001
vtep-ip:10.103.255.11
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:15 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20, version 83
Paths: (1 available, best #1, table evi_1)
Advertised to update-groups:
1
Refresh Epoch 1
Local
0.0.0.0 (via default) from 0.0.0.0 (10.103.255.11)
Origin incomplete, localpref 100, weight 32768, valid, sourced, local, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Local irb vxlan vtep:
vrf:campus, l3-vni:303001
local router mac:3488.1828.4B72
core-irb interface:Vlan3001
vtep-ip:10.103.255.11
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:14 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][9433D8078517][0][*]/20, version 7893
Paths: (1 available, best #1, table evi_1)
Not advertised to any peer
Refresh Epoch 1
Local, imported path from [2][10.103.255.14:1][0][48][9433D8078517][0][*]/20 (global)
10.103.255.14 (metric 15) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.14, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 12 2024 09:16:15 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][9433D8078518][0][*]/20, version 7885
Paths: (1 available, best #1, table evi_1)
Not advertised to any peer
Refresh Epoch 1
Local, imported path from [2][10.103.255.14:1][0][48][9433D8078518][0][*]/20 (global)
10.103.255.14 (metric 15) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.14, Cluster list: 10.103.255.1
NYC103-Leaf-01#
NYC103-Leaf-01#sh ip bgp l2vpn evpn a0:ce:c8:fb:46:7f
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20, version 498
Paths: (1 available, best #1, table evi_120)
Advertised to update-groups:
1
Refresh Epoch 1
Local
0.0.0.0 (via default) from 0.0.0.0 (10.103.255.11)
Origin incomplete, localpref 100, weight 32768, valid, sourced, local, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
Local irb vxlan vtep:
vrf:campus, l3-vni:303001
local router mac:3488.1828.4B72
core-irb interface:Vlan3001
vtep-ip:10.103.255.11
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:29 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 517
Paths: (1 available, best #1, table evi_120)
Advertised to update-groups:
1
Refresh Epoch 1
Local
0.0.0.0 (via default) from 0.0.0.0 (10.103.255.11)
Origin incomplete, localpref 100, weight 32768, valid, sourced, local, best
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Local irb vxlan vtep:
vrf:campus, l3-vni:303001
local router mac:3488.1828.4B72
core-irb interface:Vlan3001
vtep-ip:10.103.255.11
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:05 EDT
NYC103-Leaf-02
NYC103-Leaf-02#show ip bgp l2vpn evpn summary
BGP router identifier 10.103.255.12, local AS number 65106
BGP table version is 5790, main routing table version 5790
108 network entries using 41472 bytes of memory
155 path entries using 35960 bytes of memory
29/29 BGP path/bestpath attribute entries using 8584 bytes of memory
10 BGP rrinfo entries using 400 bytes of memory
2 BGP AS-PATH entries using 80 bytes of memory
22 BGP extended community entries using 928 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 87424 total bytes of memory
BGP activity 2891/2764 prefixes, 3169/2979 paths, scan interval 60 secs
118 networks peaked at 08:54:58 Jul 12 2024 EDT (4d10h ago)
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.103.255.1 4 65106 18555 18473 5790 0 0 1w2d 47
10.103.255.2 4 65106 18558 18464 5790 0 0 1w2d 47
NYC103-Leaf-02#show ip bgp l2vpn evpn nei 10.103.255.1 advertised-routes
BGP table version is 5790, local router ID is 10.103.255.12
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.12:1
*> [2][10.103.255.12:1][0][48][A0BC6FD67B00][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][A0BC6FD67B18][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][A0BC6FE28B80][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][A0BC6FE28B98][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][A0BC6FE28F00][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][A0BC6FE28F17][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][C4D6664F55B0][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][C4D6664F55B0][32][10.103.64.17]/24
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][C4D6666D2E10][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][C4D6666D2E10][32][10.103.64.14]/24
0.0.0.0 32768 ?
Route Distinguisher: 10.103.255.12:120
*> [2][10.103.255.12:120][0][48][A0BC6FD67B18][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:120][0][48][A0BC6FE28B98][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:120][0][48][A0BC6FE28F17][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:120][0][48][A0CEC8FB4687][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:120][0][48][A0CEC8FB4687][32][10.103.120.14]/24
0.0.0.0 32768 ?
*> [2][10.103.255.12:120][0][48][A0CEC8FB47B7][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:120][0][48][A0CEC8FB47B7][32][10.103.120.13]/24
0.0.0.0 32768 ?
*> [2][10.103.255.12:120][0][48][A0CEC8FB47DC][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:120][0][48][A0CEC8FB47DC][32][10.103.120.11]/24
0.0.0.0 32768 ?
Route Distinguisher: 10.103.255.12:180
*> [2][10.103.255.12:180][0][48][A0BC6FD67B18][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:180][0][48][A0BC6FE28B98][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:180][0][48][A0BC6FE28F17][0][*]/20
0.0.0.0 32768 ?
Route Distinguisher: 10.103.255.12:220
*> [2][10.103.255.12:220][0][48][A0BC6FD67B18][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:220][0][48][A0BC6FE28B98][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:220][0][48][A0BC6FE28F17][0][*]/20
0.0.0.0 32768 ?
Route Distinguisher: 65106:12 (default for vrf campus)
*> [5][65106:12][0][24][10.103.64.0]/17
0.0.0.0 0 32768 ?
*> [5][65106:12][0][24][10.103.120.0]/17
NYC103-Leaf-02#
NYC103-Leaf-02#show ip bgp l2vpn evpn nei 10.103.255.1 routes
BGP table version is 5790, local router ID is 10.103.255.12
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
*>i [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
*>i [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:180
*>i [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:220
*>i [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.12:1
*>i [2][10.103.255.12:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][9433D8078517][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][9433D8078518][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][9433D8078547][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][9433D8078547][32][10.103.64.26]/24
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0CEC8FB4677][32][10.103.120.15]/24
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0CEC8FB4689][32][10.103.120.23]/24
10.103.255.13 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0CEC8FB47A7][32][10.103.120.16]/24
10.103.255.13 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D0F80][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D0F80][32][10.103.64.28]/24
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D666D93140][0][*]/20
10.103.255.13 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D666D93140][32][10.103.64.20]/24
10.103.255.13 0 100 0 ?
Route Distinguisher: 10.103.255.12:120
NYC103-Leaf-02#
NYC103-Leaf-02#show ip bgp l2vpn evpn
BGP table version is 5790, local router ID is 10.103.255.12
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
* i [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
* i [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:180
* i [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:220
* i [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.12:1
*>i [2][10.103.255.12:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][9433D8078517][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][9433D8078518][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][9433D8078547][0][*]/20
10.103.255.14 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][9433D8078547][32][10.103.64.26]/24
10.103.255.14 0 100 0 ?
*> [2][10.103.255.12:1][0][48][A0BC6FD67B00][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][A0BC6FD67B18][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][A0BC6FE28B80][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.12:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
0.0.0.0 32768 ?
NYC103-Leaf-02#
NYC103-Leaf-02#show ip bgp l2vpn evpn route-type 2
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20, version 70
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:18 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:18 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24, version 158
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:30:34 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:30:34 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20, version 65
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:14 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:14 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20, version 62
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
NYC103-Leaf-02#
NYC103-Leaf-02#show ip bgp l2vpn evpn route-type 5
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 145
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101
10.103.255.3 (metric 103) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:33 EDT
Refresh Epoch 1
65102 65100 65101
10.103.255.3 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:33 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.64.0]/17, version 16
Paths: (2 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Not advertised to any peer
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:23 EDT
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 103) (via default) from 10.103.255.2 (10.103.255.2)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:06:23 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.128.0]/17, version 17
Paths: (2 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Not advertised to any peer
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:23 EDT
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 103) (via default) from 10.103.255.2 (10.103.255.2)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:06:23 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 147
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101
10.103.255.4 (metric 103) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
NYC103-Leaf-02#
NYC103-Leaf-02#show ip bgp l2vpn evpn 0.0.0.0/0
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20, version 70
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:18 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:18 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20, version 65
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:14 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:14 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20, version 62
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:13 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:13 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20, version 119
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
NYC103-Leaf-02#
NYC103-Leaf-02#sh ip bgp l2vpn evpn a0:ce:c8:fb:46:7f
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20, version 260
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 19:43:29 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:29 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 275
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 19:44:05 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:05 EDT
BGP routing table entry for [2][10.103.255.12:1][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 279
Paths: (1 available, best #1, table evi_1)
Not advertised to any peer
Refresh Epoch 1
Local, imported path from [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24 (global)
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:05 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0CEC8FB467F][0][*]/20, version 262
Paths: (1 available, best #1, table evi_120)
Not advertised to any peer
Refresh Epoch 1
Local, imported path from [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20 (global)
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:29 EDT
BGP routing table entry for [2][10.103.255.12:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 278
Paths: (1 available, best #1, table evi_120)
Not advertised to any peer
Refresh Epoch 1
NYC103-Leaf-02#
NYC103-Leaf-03
NYC103-Leaf-03#show ip bgp l2vpn evpn summary
BGP router identifier 10.103.255.13, local AS number 65106
BGP table version is 15981, main routing table version 15981
131 network entries using 50304 bytes of memory
200 path entries using 46400 bytes of memory
27/27 BGP path/bestpath attribute entries using 7992 bytes of memory
10 BGP rrinfo entries using 400 bytes of memory
2 BGP AS-PATH entries using 80 bytes of memory
22 BGP extended community entries using 928 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 106104 total bytes of memory
BGP activity 5542/5387 prefixes, 10504/10264 paths, scan interval 60 secs
141 networks peaked at 08:54:58 Jul 12 2024 EDT (4d10h ago)
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.103.255.1 4 65106 18577 14652 15981 0 0 1w2d 69
10.103.255.2 4 65106 18578 14660 15981 0 0 1w2d 69
NYC103-Leaf-03#show ip bgp l2vpn evpn nei 10.103.255.1 advertised-routes
BGP table version is 15981, local router ID is 10.103.255.13
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.13:1
*> [2][10.103.255.13:1][0][48][C4D666D93140][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.13:1][0][48][C4D666D93140][32][10.103.64.20]/24
0.0.0.0 32768 ?
Route Distinguisher: 10.103.255.13:120
*> [2][10.103.255.13:120][0][48][A0CEC8FB4689][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.13:120][0][48][A0CEC8FB4689][32][10.103.120.23]/24
0.0.0.0 32768 ?
*> [2][10.103.255.13:120][0][48][A0CEC8FB47A7][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.13:120][0][48][A0CEC8FB47A7][32][10.103.120.16]/24
0.0.0.0 32768 ?
Route Distinguisher: 65106:13 (default for vrf campus)
*> [5][65106:13][0][24][10.103.64.0]/17
0.0.0.0 0 32768 ?
*> [5][65106:13][0][24][10.103.120.0]/17
0.0.0.0 0 32768 ?
*> [5][65106:13][0][24][10.103.180.0]/17
0.0.0.0 0 32768 ?
Route Distinguisher: 65106:213 (default for vrf guest)
*> [5][65106:213][0][24][10.103.220.0]/17
0.0.0.0 0 32768 ?
Total number of prefixes 10
NYC103-Leaf-03#show ip bgp l2vpn evpn nei 10.103.255.1 routes
BGP table version is 15981, local router ID is 10.103.255.13
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
*>i [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
*>i [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:180
*>i [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:220
*>i [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.12:1
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B80][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6664F55B0][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6664F55B0][32][10.103.64.17]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D2E10][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D2E10][32][10.103.64.14]/24
10.103.255.12 0 100 0 ?
Route Distinguisher: 10.103.255.12:120
*>i [2][10.103.255.12:120][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][32][10.103.120.14]/24
10.103.255.12 0 100 0 ?
NYC103-Leaf-03#
NYC103-Leaf-03#show ip bgp l2vpn evpn
BGP table version is 15981, local router ID is 10.103.255.13
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
* i [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
* i [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:180
* i [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:220
* i [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.12:1
* i [2][10.103.255.12:1][0][48][A0BC6FD67B00][0][*]/20
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28B80][0][*]/20
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28F00][0][*]/20
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
NYC103-Leaf-03#
NYC103-Leaf-03#show ip bgp l2vpn evpn route-type 2
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20, version 99
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:18 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:18 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24, version 276
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:30:35 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:30:35 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20, version 90
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:15 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:15 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20, version 87
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
NYC103-Leaf-03#
NYC103-Leaf-03#show ip bgp l2vpn evpn route-type 5
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 246
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101
10.103.255.3 (metric 103) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65101
10.103.255.3 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.64.0]/17, version 16
Paths: (2 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Not advertised to any peer
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:23 EDT
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 103) (via default) from 10.103.255.2 (10.103.255.2)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:06:23 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.128.0]/17, version 17
Paths: (2 available, best #1, table EVPN-BGP-Table)
Flag: 0x100
Not advertised to any peer
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:23 EDT
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 103) (via default) from 10.103.255.2 (10.103.255.2)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:06:23 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 248
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101
10.103.255.4 (metric 103) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
NYC103-Leaf-03#
NYC103-Leaf-03#show ip bgp l2vpn evpn 0.0.0.0/0
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20, version 99
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:18 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:18 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20, version 90
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:15 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:15 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20, version 87
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:13 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:13 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20, version 206
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
NYC103-Leaf-03#
NYC103-Leaf-03#sh ip bgp l2vpn evpn a0:ce:c8:fb:46:7f
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20, version 529
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 19:43:29 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:29 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 547
Paths: (2 available, best #1, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:05 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 111) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 19:44:05 EDT
BGP routing table entry for [2][10.103.255.13:1][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 549
Paths: (1 available, best #1, table evi_1)
Not advertised to any peer
Refresh Epoch 1
Local, imported path from [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24 (global)
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:05 EDT
BGP routing table entry for [2][10.103.255.13:120][0][48][A0CEC8FB467F][0][*]/20, version 531
Paths: (1 available, best #1, table evi_120)
Not advertised to any peer
Refresh Epoch 1
Local, imported path from [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20 (global)
10.103.255.11 (metric 111) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:29 EDT
BGP routing table entry for [2][10.103.255.13:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 548
Paths: (1 available, best #1, table evi_120)
Not advertised to any peer
Refresh Epoch 1
NYC103-Leaf-03#
NYC103-Leaf-04
NYC103-Leaf-04#show ip bgp l2vpn evpn summary
BGP router identifier 10.103.255.14, local AS number 65106
BGP table version is 15737, main routing table version 15737
130 network entries using 49920 bytes of memory
197 path entries using 45704 bytes of memory
27/27 BGP path/bestpath attribute entries using 7992 bytes of memory
10 BGP rrinfo entries using 400 bytes of memory
2 BGP AS-PATH entries using 80 bytes of memory
22 BGP extended community entries using 928 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 105024 total bytes of memory
BGP activity 5466/5312 prefixes, 10312/10075 paths, scan interval 60 secs
135 networks peaked at 08:54:58 Jul 12 2024 EDT (4d10h ago)
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.103.255.1 4 65106 18571 14697 15737 0 0 1w2d 67
10.103.255.2 4 65106 18569 14688 15737 0 0 1w2d 67
NYC103-Leaf-04#show ip bgp l2vpn evpn nei 10.103.255.1 advertised-routes
BGP table version is 15737, local router ID is 10.103.255.14
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.14:1
*> [2][10.103.255.14:1][0][48][9433D8078517][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.14:1][0][48][9433D8078518][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.14:1][0][48][9433D8078547][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.14:1][0][48][9433D8078547][32][10.103.64.26]/24
0.0.0.0 32768 ?
*> [2][10.103.255.14:1][0][48][C4D6666D0F80][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.14:1][0][48][C4D6666D0F80][32][10.103.64.28]/24
0.0.0.0 32768 ?
Route Distinguisher: 10.103.255.14:120
*> [2][10.103.255.14:120][0][48][A0CEC8FB4677][0][*]/20
0.0.0.0 32768 ?
*> [2][10.103.255.14:120][0][48][A0CEC8FB4677][32][10.103.120.15]/24
0.0.0.0 32768 ?
Route Distinguisher: 65106:14 (default for vrf campus)
*> [5][65106:14][0][24][10.103.64.0]/17
0.0.0.0 0 32768 ?
*> [5][65106:14][0][24][10.103.120.0]/17
0.0.0.0 0 32768 ?
*> [5][65106:14][0][24][10.103.180.0]/17
0.0.0.0 0 32768 ?
Route Distinguisher: 65106:214 (default for vrf guest)
*> [5][65106:214][0][24][10.103.220.0]/17
0.0.0.0 0 32768 ?
Total number of prefixes 12
NYC103-Leaf-04#show ip bgp l2vpn evpn nei 10.103.255.1 routes
BGP table version is 15737, local router ID is 10.103.255.14
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
*>i [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
*>i [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:180
*>i [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:220
*>i [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.12:1
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B80][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F00][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6664F55B0][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6664F55B0][32][10.103.64.17]/24
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D2E10][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:1][0][48][C4D6666D2E10][32][10.103.64.14]/24
10.103.255.12 0 100 0 ?
Route Distinguisher: 10.103.255.12:120
*>i [2][10.103.255.12:120][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][0][*]/20
10.103.255.12 0 100 0 ?
*>i [2][10.103.255.12:120][0][48][A0CEC8FB4687][32][10.103.120.14]/24
10.103.255.12 0 100 0 ?
NYC103-Leaf-04#
NYC103-Leaf-04#show ip bgp l2vpn evpn
BGP table version is 15737, local router ID is 10.103.255.14
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.103.255.11:1
* i [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:1][0][48][C414A20289A0][32][10.103.64.19]/24
10.103.255.11 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:120
* i [2][10.103.255.11:120][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
* i [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
*>i [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24
10.103.255.11 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:180
* i [2][10.103.255.11:180][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.11:220
* i [2][10.103.255.11:220][0][48][8C44A5718318][0][*]/20
10.103.255.11 0 100 0 ?
*>i 10.103.255.11 0 100 0 ?
Route Distinguisher: 10.103.255.12:1
* i [2][10.103.255.12:1][0][48][A0BC6FD67B00][0][*]/20
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FD67B00][32][10.103.64.12]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FD67B18][0][*]/20
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28B80][0][*]/20
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28B80][32][10.103.64.11]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28B98][0][*]/20
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28F00][0][*]/20
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28F00][32][10.103.64.13]/24
10.103.255.12 0 100 0 ?
*>i 10.103.255.12 0 100 0 ?
* i [2][10.103.255.12:1][0][48][A0BC6FE28F17][0][*]/20
10.103.255.12 0 100 0 ?
NYC103-Leaf-04#
NYC103-Leaf-04#show ip bgp l2vpn evpn route-type 2
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20, version 83
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:19 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:19 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][32][10.103.64.15]/24, version 256
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:30:35 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001, Label2 303001
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:30:35 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20, version 74
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:15 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:15 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20, version 71
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
NYC103-Leaf-04#
NYC103-Leaf-04#
NYC103-Leaf-04#show ip bgp l2vpn evpn route-type 5
BGP routing table entry for [5][65106:3][0][0][0.0.0.0]/17, version 226
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101
10.103.255.3 (metric 7) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65101
10.103.255.3 (metric 7) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.64.0]/17, version 8
Paths: (2 available, best #1, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 7) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 7) (via default) from 10.103.255.2 (10.103.255.2)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:3][0][18][10.103.128.0]/17, version 9
Paths: (2 available, best #1, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 7) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate, best
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:06:24 EDT
Refresh Epoch 1
Local, (aggregated by 65106 10.103.255.3)
10.103.255.3 (metric 7) (via default) from 10.103.255.2 (10.103.255.2)
Origin IGP, metric 0, localpref 100, valid, internal, atomic-aggregate
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:06:24 EDT
BGP routing table entry for [5][65106:4][0][0][0.0.0.0]/17, version 228
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101
10.103.255.4 (metric 7) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Gateway Address: 0.0.0.0, VNI Label 303001, MPLS VPN Label 0
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
Originator: 10.103.255.4, Cluster list: 10.103.255.2
NYC103-Leaf-04#
NYC103-Leaf-04#show ip bgp l2vpn evpn 0.0.0.0/0
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718300][0][*]/20, version 83
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:19 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:19 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718317][0][*]/20, version 74
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:15 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:15 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][8C44A5718318][0][*]/20, version 71
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:08:14 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:08:14 EDT
BGP routing table entry for [2][10.103.255.11:1][0][48][C414A20289A0][0][*]/20, version 190
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200001
Extended Community: RT:65106:1 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
NYC103-Leaf-04#
NYC103-Leaf-04#sh ip bgp l2vpn evpn a0:ce:c8:fb:46:7f
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20, version 505
Paths: (2 available, best #2, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 19:43:29 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:29 EDT
BGP routing table entry for [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 525
Paths: (2 available, best #1, table EVPN-BGP-Table)
Not advertised to any peer
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:05 EDT
Refresh Epoch 1
Local
10.103.255.11 (metric 15) (via default) from 10.103.255.2 (10.103.255.2)
Origin incomplete, metric 0, localpref 100, valid, internal
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.2
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 19:44:05 EDT
BGP routing table entry for [2][10.103.255.14:1][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 527
Paths: (1 available, best #1, table evi_1)
Not advertised to any peer
Refresh Epoch 1
Local, imported path from [2][10.103.255.11:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24 (global)
10.103.255.11 (metric 15) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120, Label2 303001
Extended Community: RT:65106:1 RT:65106:120 ENCAP:8
Router MAC:3488.1828.4B72
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:44:05 EDT
BGP routing table entry for [2][10.103.255.14:120][0][48][A0CEC8FB467F][0][*]/20, version 507
Paths: (1 available, best #1, table evi_120)
Not advertised to any peer
Refresh Epoch 1
Local, imported path from [2][10.103.255.11:120][0][48][A0CEC8FB467F][0][*]/20 (global)
10.103.255.11 (metric 15) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 200120
Extended Community: RT:65106:120 ENCAP:8
Originator: 10.103.255.11, Cluster list: 10.103.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 19:43:29 EDT
BGP routing table entry for [2][10.103.255.14:120][0][48][A0CEC8FB467F][32][10.103.120.12]/24, version 526
Paths: (1 available, best #1, table evi_120)
Not advertised to any peer
Refresh Epoch 1
NYC103-Leaf-04#
Multicast
NYC103-Spine-01
NYC103-Spine-01#show ip pim interface
Address Interface Ver/ Nbr Query DR DR
Mode Count Intvl Prior
10.103.254.1 Loopback1 v2/S 0 30 1 10.103.254.1
10.103.255.255 Loopback2 v2/S 0 30 1 10.103.255.255
10.103.224.29 TwentyFiveGigE1/0/1 v2/S 1 30 1 10.103.224.30
10.103.224.37 TwentyFiveGigE1/0/2 v2/S 1 30 1 10.103.224.38
10.103.224.45 TwentyFiveGigE1/0/3 v2/S 1 30 1 10.103.224.46
10.103.224.53 TwentyFiveGigE1/0/4 v2/S 1 30 1 10.103.224.54
10.103.224.9 HundredGigE1/0/25 v2/S 1 30 1 10.103.224.10
10.103.224.21 HundredGigE1/0/26 v2/S 1 30 1 10.103.224.22
10.103.224.17 HundredGigE1/0/28 v2/S 1 30 1 10.103.224.18
NYC103-Spine-01#show ip pim neighbor
PIM Neighbor Table
Mode: B - Bidir Capable, DR - Designated Router, N - Default DR Priority,
P - Proxy Capable, S - State Refresh Capable, G - GenID Capable,
L - DR Load-balancing Capable
Neighbor Interface Uptime/Expires Ver DR
Address Prio/Mode
10.103.224.30 TwentyFiveGigE1/0/1 1w2d/00:01:25 v2 1 / DR S P G
10.103.224.38 TwentyFiveGigE1/0/2 1w2d/00:01:42 v2 1 / DR S P G
10.103.224.46 TwentyFiveGigE1/0/3 1w2d/00:01:38 v2 1 / DR S P G
10.103.224.54 TwentyFiveGigE1/0/4 1w2d/00:01:19 v2 1 / DR S P G
10.103.224.10 HundredGigE1/0/25 1w2d/00:01:16 v2 1 / DR S P G
10.103.224.22 HundredGigE1/0/26 1w2d/00:01:34 v2 1 / DR S P G
10.103.224.18 HundredGigE1/0/28 1w2d/00:01:43 v2 1 / DR S P G
NYC103-Spine-01#show ip pim rp
Group: 224.0.1.40, RP: 10.103.255.255
NYC103-Spine-01#show ip mroute
IP Multicast Routing Table
Flags: D - Dense, S - Sparse, B - Bidir Group, s - SSM Group, C - Connected,
L - Local, P - Pruned, R - RP-bit set, F - Register flag,
T - SPT-bit set, J - Join SPT, M - MSDP created entry, E - Extranet,
X - Proxy Join Timer Running, A - Candidate for MSDP Advertisement,
U - URD, I - Received Source Specific Host Report,
Z - Multicast Tunnel, z - MDT-data group sender,
Y - Joined MDT-data group, y - Sending to MDT-data group,
G - Received BGP C-Mroute, g - Sent BGP C-Mroute,
N - Received BGP Shared-Tree Prune, n - BGP C-Mroute suppressed,
Q - Received BGP S-A Route, q - Sent BGP S-A Route,
V - RD & Vector, v - Vector, p - PIM Joins on route,
x - VxLAN group, c - PFP-SA cache created entry,
* - determined by Assert, # - iif-starg configured on rpf intf,
e - encap-helper tunnel flag, l - LISP decap ref count contributor
Outgoing interface flags: H - Hardware switched, A - Assert winner, p - PIM Join
t - LISP transit group
Timers: Uptime/Expires
Interface state: Interface, Next-Hop or VCD, State/Mode
(*, 224.0.1.40), 1w2d/00:03:27, RP 10.103.255.255, flags: SJCL
Incoming interface: Null, RPF nbr 0.0.0.0
Outgoing interface list:
Loopback1, Forward/Sparse, 1w2d/00:02:02, flags:
HundredGigE1/0/26, Forward/Sparse, 1w2d/00:03:27, flags:
NYC103-Spine-01#Show ip interface brief
Interface IP-Address OK? Method Status Protocol
Vlan1 unassigned YES NVRAM up down
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
TwentyFiveGigE1/0/1 10.103.224.29 YES NVRAM up up
TwentyFiveGigE1/0/2 10.103.224.37 YES NVRAM up up
TwentyFiveGigE1/0/3 10.103.224.45 YES NVRAM up up
TwentyFiveGigE1/0/4 10.103.224.53 YES NVRAM up up
TwentyFiveGigE1/0/5 unassigned YES unset down down
TwentyFiveGigE1/0/6 unassigned YES unset down down
TwentyFiveGigE1/0/7 unassigned YES unset down down
TwentyFiveGigE1/0/8 unassigned YES unset down down
TwentyFiveGigE1/0/9 unassigned YES unset down down
TwentyFiveGigE1/0/10 unassigned YES unset down down
TwentyFiveGigE1/0/11 unassigned YES unset down down
TwentyFiveGigE1/0/12 unassigned YES unset down down
TwentyFiveGigE1/0/13 unassigned YES unset down down
TwentyFiveGigE1/0/14 unassigned YES unset down down
TwentyFiveGigE1/0/15 unassigned YES unset down down
TwentyFiveGigE1/0/16 unassigned YES unset down down
TwentyFiveGigE1/0/17 unassigned YES unset down down
TwentyFiveGigE1/0/18 unassigned YES unset down down
TwentyFiveGigE1/0/19 unassigned YES unset down down
TwentyFiveGigE1/0/20 unassigned YES unset down down
TwentyFiveGigE1/0/21 unassigned YES unset down down
TwentyFiveGigE1/0/22 unassigned YES unset down down
TwentyFiveGigE1/0/23 unassigned YES unset down down
TwentyFiveGigE1/0/24 unassigned YES unset down down
HundredGigE1/0/25 10.103.224.9 YES NVRAM up up
HundredGigE1/0/26 10.103.224.21 YES NVRAM up up
HundredGigE1/0/27 unassigned YES unset down down
HundredGigE1/0/28 10.103.224.17 YES NVRAM up up
TLS-VIF0 20.0.122.247 YES TFTP up up
Loopback0 10.103.255.1 YES NVRAM up up
Loopback1 10.103.254.1 YES NVRAM up up
Loopback2 10.103.255.255 YES NVRAM up up
Loopback1000 20.0.122.247 YES manual up up
Tunnel0 10.103.255.255 YES unset up up
Tunnel1 10.103.255.255 YES unset up up
NYC103-Spine-01#show ip msdp summary
MSDP Peer Status Summary
Peer Address AS State Uptime/ Reset SA Peer Name
Downtime Count Count
10.103.254.2 ? Up 1w2d 0 0 ?
NYC103-Spine-01#show ip msdp peer
MSDP Peer 10.103.254.2 (?), AS ?
Connection status:
State: Up, Resets: 0, Connection source: Loopback1 (10.103.254.1)
Uptime(Downtime): 1w2d, Messages sent/received: 13296/13296
Output messages discarded: 0
Connection and counters cleared 1w2d ago
SA Filtering:
Input (S,G) filter: none, route-map: none
Input RP filter: none, route-map: none
Output (S,G) filter: none, route-map: none
Output RP filter: none, route-map: none
SA-Requests:
Input filter: none
Peer ttl threshold: 0
SAs learned from this peer: 0
Number of connection transitions to Established state: 1
Input queue size: 0, Output queue size: 0
MD5 signature protection on MSDP TCP connection: not enabled
Message counters:
RPF Failure count: 0
SA Messages in/out: 0/0
SA Requests in: 0
SA Responses out: 0
Data Packets in/out: 0/0
NYC103-Spine-01#show ip interface loopback1
Loopback1 is up, line protocol is up
Internet address is 10.103.254.1/32
Broadcast address is 255.255.255.255
Address determined by non-volatile memory
MTU is 9212 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Multicast reserved groups joined: 224.0.0.1 224.0.0.2 224.0.0.22 224.0.0.13
224.0.0.5
Outgoing Common access list is not set
Outgoing access list is not set
Inbound Common access list is not set
Inbound access list is not set
Proxy ARP is enabled
Local Proxy ARP is disabled
Security level is default
Split horizon is enabled
ICMP redirects are always sent
ICMP unreachables are always sent
ICMP mask replies are never sent
IP fast switching is enabled
IP Flow switching is disabled
IP CEF switching is enabled
IP CEF switching turbo vector
IP Null turbo vector
Associated unicast routing topologies:
Topology "base", operation state is UP
Associated multicast routing topologies:
Topology "base", operation state is UP
IP multicast fast switching is enabled
IP multicast distributed fast switching is disabled
IP route-cache flags are Fast, CEF
Router Discovery is disabled
IP output packet accounting is disabled
IP access violation accounting is disabled
TCP/IP header compression is disabled
RTP/IP header compression is disabled
Probe proxy name replies are disabled
Policy routing is disabled
Network address translation is disabled
BGP Policy Mapping is disabled
Input features: MCI Check
IPv4 WCCP Redirect outbound is disabled
IPv4 WCCP Redirect inbound is disabled
IPv4 WCCP Redirect exclude is disabled
IP Clear Dont Fragment is disabled
NYC103-Spine-01#show ip interface loopback2
Loopback2 is up, line protocol is up
Internet address is 10.103.255.255/32
Broadcast address is 255.255.255.255
Address determined by non-volatile memory
MTU is 9212 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Multicast reserved groups joined: 224.0.0.1 224.0.0.2 224.0.0.22 224.0.0.13
224.0.0.5
Outgoing Common access list is not set
Outgoing access list is not set
Inbound Common access list is not set
Inbound access list is not set
Proxy ARP is enabled
Local Proxy ARP is disabled
Security level is default
Split horizon is enabled
ICMP redirects are always sent
ICMP unreachables are always sent
ICMP mask replies are never sent
IP fast switching is enabled
IP Flow switching is disabled
IP CEF switching is enabled
IP CEF switching turbo vector
IP Null turbo vector
Associated unicast routing topologies:
Topology "base", operation state is UP
Associated multicast routing topologies:
Topology "base", operation state is UP
IP multicast fast switching is enabled
IP multicast distributed fast switching is disabled
IP route-cache flags are Fast, CEF
Router Discovery is disabled
IP output packet accounting is disabled
IP access violation accounting is disabled
TCP/IP header compression is disabled
RTP/IP header compression is disabled
Probe proxy name replies are disabled
Policy routing is disabled
Network address translation is disabled
BGP Policy Mapping is disabled
Input features: MCI Check
IPv4 WCCP Redirect outbound is disabled
IPv4 WCCP Redirect inbound is disabled
IPv4 WCCP Redirect exclude is disabled
IP Clear Dont Fragment is disabled
NYC103-Spine-01#
NYC103-Spine-02
NYC103-Spine-02#show ip pim interface
Address Interface Ver/ Nbr Query DR DR
Mode Count Intvl Prior
10.103.254.2 Loopback1 v2/S 0 30 1 10.103.254.2
10.103.255.255 Loopback2 v2/S 0 30 1 10.103.255.255
10.103.224.33 TwentyFiveGigE1/0/1 v2/S 1 30 1 10.103.224.34
10.103.224.41 TwentyFiveGigE1/0/2 v2/S 1 30 1 10.103.224.42
10.103.224.49 TwentyFiveGigE1/0/3 v2/S 1 30 1 10.103.224.50
10.103.224.57 TwentyFiveGigE1/0/4 v2/S 1 30 1 10.103.224.58
10.103.224.25 HundredGigE1/0/25 v2/S 1 30 1 10.103.224.26
10.103.224.13 HundredGigE1/0/26 v2/S 1 30 1 10.103.224.14
10.103.224.18 HundredGigE1/0/28 v2/S 1 30 1 10.103.224.18
NYC103-Spine-02#show ip pim neighbor
PIM Neighbor Table
Mode: B - Bidir Capable, DR - Designated Router, N - Default DR Priority,
P - Proxy Capable, S - State Refresh Capable, G - GenID Capable,
L - DR Load-balancing Capable
Neighbor Interface Uptime/Expires Ver DR
Address Prio/Mode
10.103.224.34 TwentyFiveGigE1/0/1 1w2d/00:01:24 v2 1 / DR S P G
10.103.224.42 TwentyFiveGigE1/0/2 1w2d/00:01:16 v2 1 / DR S P G
10.103.224.50 TwentyFiveGigE1/0/3 1w2d/00:01:32 v2 1 / DR S P G
10.103.224.58 TwentyFiveGigE1/0/4 1w2d/00:01:27 v2 1 / DR S P G
10.103.224.26 HundredGigE1/0/25 1w2d/00:01:38 v2 1 / DR S P G
10.103.224.14 HundredGigE1/0/26 1w2d/00:01:30 v2 1 / DR S P G
10.103.224.17 HundredGigE1/0/28 1w2d/00:01:37 v2 1 / S P G
NYC103-Spine-02#show ip pim rp
Group: 225.0.0.1, RP: 10.103.255.255
Group: 224.0.1.40, RP: 10.103.255.255
Group: 225.0.0.120, RP: 10.103.255.255
Group: 225.0.0.180, RP: 10.103.255.255
Group: 225.0.0.220, RP: 10.103.255.255
NYC103-Spine-02#show ip mroute
IP Multicast Routing Table
Flags: D - Dense, S - Sparse, B - Bidir Group, s - SSM Group, C - Connected,
L - Local, P - Pruned, R - RP-bit set, F - Register flag,
T - SPT-bit set, J - Join SPT, M - MSDP created entry, E - Extranet,
X - Proxy Join Timer Running, A - Candidate for MSDP Advertisement,
U - URD, I - Received Source Specific Host Report,
Z - Multicast Tunnel, z - MDT-data group sender,
Y - Joined MDT-data group, y - Sending to MDT-data group,
G - Received BGP C-Mroute, g - Sent BGP C-Mroute,
N - Received BGP Shared-Tree Prune, n - BGP C-Mroute suppressed,
Q - Received BGP S-A Route, q - Sent BGP S-A Route,
V - RD & Vector, v - Vector, p - PIM Joins on route,
x - VxLAN group, c - PFP-SA cache created entry,
* - determined by Assert, # - iif-starg configured on rpf intf,
e - encap-helper tunnel flag, l - LISP decap ref count contributor
Outgoing interface flags: H - Hardware switched, A - Assert winner, p - PIM Join
t - LISP transit group
Timers: Uptime/Expires
Interface state: Interface, Next-Hop or VCD, State/Mode
(*, 225.0.0.1), 1w2d/00:03:26, RP 10.103.255.255, flags: S
Incoming interface: Null, RPF nbr 0.0.0.0
Outgoing interface list:
TwentyFiveGigE1/0/3, Forward/Sparse, 1w2d/00:02:59, flags:
TwentyFiveGigE1/0/2, Forward/Sparse, 1w2d/00:03:26, flags:
TwentyFiveGigE1/0/4, Forward/Sparse, 1w2d/00:03:02, flags:
TwentyFiveGigE1/0/1, Forward/Sparse, 1w2d/00:02:33, flags:
(*, 224.0.1.40), 1w2d/00:03:29, RP 10.103.255.255, flags: SJCL
Incoming interface: Null, RPF nbr 0.0.0.0
Outgoing interface list:
Loopback1, Forward/Sparse, 1w2d/00:02:00, flags:
TwentyFiveGigE1/0/3, Forward/Sparse, 1w2d/00:03:29, flags:
TwentyFiveGigE1/0/2, Forward/Sparse, 1w2d/00:03:00, flags:
HundredGigE1/0/25, Forward/Sparse, 1w2d/00:03:25, flags:
TwentyFiveGigE1/0/4, Forward/Sparse, 1w2d/00:03:25, flags:
TwentyFiveGigE1/0/1, Forward/Sparse, 1w2d/00:03:29, flags:
(*, 225.0.0.120), 1w2d/00:03:22, RP 10.103.255.255, flags: S
Incoming interface: Null, RPF nbr 0.0.0.0
Outgoing interface list:
TwentyFiveGigE1/0/3, Forward/Sparse, 1w2d/00:03:22, flags:
TwentyFiveGigE1/0/2, Forward/Sparse, 1w2d/00:03:12, flags:
TwentyFiveGigE1/0/4, Forward/Sparse, 1w2d/00:03:18, flags:
TwentyFiveGigE1/0/1, Forward/Sparse, 1w2d/00:03:10, flags:
(*, 225.0.0.180), 1w2d/00:03:24, RP 10.103.255.255, flags: S
Incoming interface: Null, RPF nbr 0.0.0.0
Outgoing interface list:
TwentyFiveGigE1/0/3, Forward/Sparse, 1w2d/00:02:53, flags:
TwentyFiveGigE1/0/2, Forward/Sparse, 1w2d/00:03:12, flags:
TwentyFiveGigE1/0/4, Forward/Sparse, 1w2d/00:03:24, flags:
TwentyFiveGigE1/0/1, Forward/Sparse, 1w2d/00:02:53, flags:
(*, 225.0.0.220), 1w2d/00:03:27, RP 10.103.255.255, flags: S
Incoming interface: Null, RPF nbr 0.0.0.0
Outgoing interface list:
TwentyFiveGigE1/0/3, Forward/Sparse, 1w2d/00:03:27, flags:
TwentyFiveGigE1/0/2, Forward/Sparse, 1w2d/00:03:00, flags:
TwentyFiveGigE1/0/4, Forward/Sparse, 1w2d/00:02:43, flags:
TwentyFiveGigE1/0/1, Forward/Sparse, 1w2d/00:02:42, flags:
NYC103-Spine-02#Show ip interface brief
Interface IP-Address OK? Method Status Protocol
Vlan1 unassigned YES NVRAM up down
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
TwentyFiveGigE1/0/1 10.103.224.33 YES NVRAM up up
TwentyFiveGigE1/0/2 10.103.224.41 YES NVRAM up up
TwentyFiveGigE1/0/3 10.103.224.49 YES NVRAM up up
TwentyFiveGigE1/0/4 10.103.224.57 YES NVRAM up up
TwentyFiveGigE1/0/5 unassigned YES unset down down
TwentyFiveGigE1/0/6 unassigned YES unset down down
TwentyFiveGigE1/0/7 unassigned YES unset down down
TwentyFiveGigE1/0/8 unassigned YES unset down down
TwentyFiveGigE1/0/9 unassigned YES unset down down
TwentyFiveGigE1/0/10 unassigned YES unset down down
TwentyFiveGigE1/0/11 unassigned YES unset down down
TwentyFiveGigE1/0/12 unassigned YES unset down down
TwentyFiveGigE1/0/13 unassigned YES unset down down
TwentyFiveGigE1/0/14 unassigned YES unset down down
TwentyFiveGigE1/0/15 unassigned YES unset down down
TwentyFiveGigE1/0/16 unassigned YES unset down down
TwentyFiveGigE1/0/17 unassigned YES unset down down
TwentyFiveGigE1/0/18 unassigned YES unset down down
TwentyFiveGigE1/0/19 unassigned YES unset down down
TwentyFiveGigE1/0/20 unassigned YES unset down down
TwentyFiveGigE1/0/21 unassigned YES unset down down
TwentyFiveGigE1/0/22 unassigned YES unset down down
TwentyFiveGigE1/0/23 unassigned YES unset down down
TwentyFiveGigE1/0/24 unassigned YES unset down down
HundredGigE1/0/25 10.103.224.25 YES NVRAM up up
HundredGigE1/0/26 10.103.224.13 YES NVRAM up up
HundredGigE1/0/27 unassigned YES unset down down
HundredGigE1/0/28 10.103.224.18 YES NVRAM up up
TLS-VIF0 20.0.105.23 YES TFTP up up
Loopback0 10.103.255.2 YES NVRAM up up
Loopback1 10.103.254.2 YES NVRAM up up
Loopback2 10.103.255.255 YES NVRAM up up
Loopback1000 20.0.105.23 YES manual up up
Tunnel0 10.103.255.255 YES unset up up
Tunnel1 10.103.255.255 YES unset up up
NYC103-Spine-02#show ip msdp summary
MSDP Peer Status Summary
Peer Address AS State Uptime/ Reset SA Peer Name
Downtime Count Count
10.103.254.1 ? Up 1w2d 0 0 ?
NYC103-Spine-02#show ip msdp peer
MSDP Peer 10.103.254.1 (?), AS ?
Connection status:
State: Up, Resets: 0, Connection source: Loopback1 (10.103.254.2)
Uptime(Downtime): 1w2d, Messages sent/received: 13294/13294
Output messages discarded: 0
Connection and counters cleared 1w2d ago
SA Filtering:
Input (S,G) filter: none, route-map: none
Input RP filter: none, route-map: none
Output (S,G) filter: none, route-map: none
Output RP filter: none, route-map: none
SA-Requests:
Input filter: none
Peer ttl threshold: 0
SAs learned from this peer: 0
Number of connection transitions to Established state: 1
Input queue size: 0, Output queue size: 0
MD5 signature protection on MSDP TCP connection: not enabled
Message counters:
RPF Failure count: 0
SA Messages in/out: 0/0
SA Requests in: 0
SA Responses out: 0
Data Packets in/out: 0/0
NYC103-Spine-02#
NYC103-Spine-02#sh ip int loopback1
Loopback1 is up, line protocol is up
Internet address is 10.103.254.2/32
Broadcast address is 255.255.255.255
Address determined by non-volatile memory
MTU is 9212 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Multicast reserved groups joined: 224.0.0.1 224.0.0.2 224.0.0.22 224.0.0.13
224.0.0.5
Outgoing Common access list is not set
Outgoing access list is not set
Inbound Common access list is not set
Inbound access list is not set
Proxy ARP is enabled
Local Proxy ARP is disabled
Security level is default
Split horizon is enabled
ICMP redirects are always sent
ICMP unreachables are always sent
ICMP mask replies are never sent
IP fast switching is enabled
IP Flow switching is disabled
IP CEF switching is enabled
IP CEF switching turbo vector
IP Null turbo vector
Associated unicast routing topologies:
Topology "base", operation state is UP
Associated multicast routing topologies:
Topology "base", operation state is UP
IP multicast fast switching is enabled
IP multicast distributed fast switching is disabled
IP route-cache flags are Fast, CEF
Router Discovery is disabled
IP output packet accounting is disabled
IP access violation accounting is disabled
TCP/IP header compression is disabled
RTP/IP header compression is disabled
Probe proxy name replies are disabled
Policy routing is disabled
Network address translation is disabled
BGP Policy Mapping is disabled
Input features: MCI Check
IPv4 WCCP Redirect outbound is disabled
IPv4 WCCP Redirect inbound is disabled
IPv4 WCCP Redirect exclude is disabled
IP Clear Dont Fragment is disabled
NYC103-Spine-02#sh ip int loopback2
Loopback2 is up, line protocol is up
Internet address is 10.103.255.255/32
Broadcast address is 255.255.255.255
Address determined by non-volatile memory
MTU is 9212 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Multicast reserved groups joined: 224.0.0.1 224.0.0.2 224.0.0.22 224.0.0.13
224.0.0.5
Outgoing Common access list is not set
Outgoing access list is not set
Inbound Common access list is not set
Inbound access list is not set
Proxy ARP is enabled
Local Proxy ARP is disabled
Security level is default
Split horizon is enabled
ICMP redirects are always sent
ICMP unreachables are always sent
ICMP mask replies are never sent
IP fast switching is enabled
IP Flow switching is disabled
IP CEF switching is enabled
IP CEF switching turbo vector
IP Null turbo vector
Associated unicast routing topologies:
Topology "base", operation state is UP
Associated multicast routing topologies:
Topology "base", operation state is UP
IP multicast fast switching is enabled
IP multicast distributed fast switching is disabled
IP route-cache flags are Fast, CEF
Router Discovery is disabled
IP output packet accounting is disabled
IP access violation accounting is disabled
TCP/IP header compression is disabled
RTP/IP header compression is disabled
Probe proxy name replies are disabled
Policy routing is disabled
Network address translation is disabled
BGP Policy Mapping is disabled
Input features: MCI Check
IPv4 WCCP Redirect outbound is disabled
IPv4 WCCP Redirect inbound is disabled
IPv4 WCCP Redirect exclude is disabled
IP Clear Dont Fragment is disabled
NYC103-Spine-02#
NYC103-Border-01
NYC103-Border-01#show ip pim interface
Address Interface Ver/ Nbr Query DR DR
Mode Count Intvl Prior
10.103.224.10 Fo1/1/1 v2/S 1 30 1 10.103.224.10
10.103.224.26 Fo1/1/2 v2/S 1 30 1 10.103.224.26
NYC103-Border-01#show ip pim neighbor
PIM Neighbor Table
Mode: B - Bidir Capable, DR - Designated Router, N - Default DR Priority,
P - Proxy Capable, S - State Refresh Capable, G - GenID Capable,
L - DR Load-balancing Capable
Neighbor Interface Uptime/Expires Ver DR
Address Prio/Mode
10.103.224.9 Fo1/1/1 1w2d/00:01:19 v2 1 / S P G
10.103.224.25 Fo1/1/2 1w2d/00:01:20 v2 1 / S P G
NYC103-Border-01#show ip pim rp
Group: 224.0.1.40, RP: 10.103.255.255, uptime 1w2d, expires never
NYC103-Border-01#show ip mroute
IP Multicast Routing Table
Flags: D - Dense, S - Sparse, B - Bidir Group, s - SSM Group, C - Connected,
L - Local, P - Pruned, R - RP-bit set, F - Register flag,
T - SPT-bit set, J - Join SPT, M - MSDP created entry, E - Extranet,
X - Proxy Join Timer Running, A - Candidate for MSDP Advertisement,
U - URD, I - Received Source Specific Host Report,
Z - Multicast Tunnel, z - MDT-data group sender,
Y - Joined MDT-data group, y - Sending to MDT-data group,
G - Received BGP C-Mroute, g - Sent BGP C-Mroute,
N - Received BGP Shared-Tree Prune, n - BGP C-Mroute suppressed,
Q - Received BGP S-A Route, q - Sent BGP S-A Route,
V - RD & Vector, v - Vector, p - PIM Joins on route,
x - VxLAN group, c - PFP-SA cache created entry,
* - determined by Assert, # - iif-starg configured on rpf intf,
e - encap-helper tunnel flag, l - LISP decap ref count contributor
Outgoing interface flags: H - Hardware switched, A - Assert winner, p - PIM Join
t - LISP transit group
Timers: Uptime/Expires
Interface state: Interface, Next-Hop or VCD, State/Mode
(*, 224.0.1.40), 1w2d/00:02:56, RP 10.103.255.255, flags: SJCL
Incoming interface: Fo1/1/2, RPF nbr 10.103.224.25
Outgoing interface list:
Fo1/1/1, Forward/Sparse, 1w2d/00:02:56, flags:
NYC103-Border-01#
NYC103-Border-02
NYC103-Border-02#show ip pim interface
Address Interface Ver/ Nbr Query DR DR
Mode Count Intvl Prior
10.103.224.22 Fo1/1/1 v2/S 1 30 1 10.103.224.22
10.103.224.14 Fo1/1/2 v2/S 1 30 1 10.103.224.14
NYC103-Border-02#show ip pim neighbor
PIM Neighbor Table
Mode: B - Bidir Capable, DR - Designated Router, N - Default DR Priority,
P - Proxy Capable, S - State Refresh Capable, G - GenID Capable,
L - DR Load-balancing Capable
Neighbor Interface Uptime/Expires Ver DR
Address Prio/Mode
10.103.224.21 Fo1/1/1 1w2d/00:01:37 v2 1 / S P G
10.103.224.13 Fo1/1/2 1w2d/00:01:20 v2 1 / S P G
NYC103-Border-02#show ip pim rp
Group: 224.0.1.40, RP: 10.103.255.255, uptime 1w2d, expires never
NYC103-Border-02#show ip mroute
IP Multicast Routing Table
Flags: D - Dense, S - Sparse, B - Bidir Group, s - SSM Group, C - Connected,
L - Local, P - Pruned, R - RP-bit set, F - Register flag,
T - SPT-bit set, J - Join SPT, M - MSDP created entry, E - Extranet,
X - Proxy Join Timer Running, A - Candidate for MSDP Advertisement,
U - URD, I - Received Source Specific Host Report,
Z - Multicast Tunnel, z - MDT-data group sender,
Y - Joined MDT-data group, y - Sending to MDT-data group,
G - Received BGP C-Mroute, g - Sent BGP C-Mroute,
N - Received BGP Shared-Tree Prune, n - BGP C-Mroute suppressed,
Q - Received BGP S-A Route, q - Sent BGP S-A Route,
V - RD & Vector, v - Vector, p - PIM Joins on route,
x - VxLAN group, c - PFP-SA cache created entry,
* - determined by Assert, # - iif-starg configured on rpf intf,
e - encap-helper tunnel flag, l - LISP decap ref count contributor
Outgoing interface flags: H - Hardware switched, A - Assert winner, p - PIM Join
t - LISP transit group
Timers: Uptime/Expires
Interface state: Interface, Next-Hop or VCD, State/Mode
(*, 224.0.1.40), 1w2d/00:02:52, RP 10.103.255.255, flags: SJPCL
Incoming interface: Fo1/1/1, RPF nbr 10.103.224.21
Outgoing interface list: Null
NYC103-Border-02#
NYC103-Leaf-01
NYC103-Leaf-01#show ip pim interface
Address Interface Ver/ Nbr Query DR DR
Mode Count Intvl Prior
10.103.224.30 TwentyFiveGigE1/1/1 v2/S 1 30 1 10.103.224.30
10.103.224.34 TwentyFiveGigE1/1/2 v2/S 1 30 1 10.103.224.34
10.103.255.11 Tunnel0 v2/P 0 30 1 10.103.255.11
NYC103-Leaf-01#show ip pim neighbor
PIM Neighbor Table
Mode: B - Bidir Capable, DR - Designated Router, N - Default DR Priority,
P - Proxy Capable, S - State Refresh Capable, G - GenID Capable,
L - DR Load-balancing Capable
Neighbor Interface Uptime/Expires Ver DR
Address Prio/Mode
10.103.224.29 TwentyFiveGigE1/1/1 1w2d/00:01:22 v2 1 / S P G
10.103.224.33 TwentyFiveGigE1/1/2 1w2d/00:01:44 v2 1 / S P G
NYC103-Leaf-01#show ip pim rp
Group: 225.0.0.1, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 224.0.1.40, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 225.0.0.120, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 225.0.0.180, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 225.0.0.220, RP: 10.103.255.255, uptime 1w2d, expires never
NYC103-Leaf-01#show ip mroute
IP Multicast Routing Table
Flags: D - Dense, S - Sparse, B - Bidir Group, s - SSM Group, C - Connected,
L - Local, P - Pruned, R - RP-bit set, F - Register flag,
T - SPT-bit set, J - Join SPT, M - MSDP created entry, E - Extranet,
X - Proxy Join Timer Running, A - Candidate for MSDP Advertisement,
U - URD, I - Received Source Specific Host Report,
Z - Multicast Tunnel, z - MDT-data group sender,
Y - Joined MDT-data group, y - Sending to MDT-data group,
G - Received BGP C-Mroute, g - Sent BGP C-Mroute,
N - Received BGP Shared-Tree Prune, n - BGP C-Mroute suppressed,
Q - Received BGP S-A Route, q - Sent BGP S-A Route,
V - RD & Vector, v - Vector, p - PIM Joins on route,
x - VxLAN group, c - PFP-SA cache created entry,
* - determined by Assert, # - iif-starg configured on rpf intf,
e - encap-helper tunnel flag, l - LISP decap ref count contributor
Outgoing interface flags: H - Hardware switched, A - Assert winner, p - PIM Join
t - LISP transit group
Timers: Uptime/Expires
Interface state: Interface, Next-Hop or VCD, State/Mode
(*, 225.0.0.1), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: TwentyFiveGigE1/1/2, RPF nbr 10.103.224.33
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
(10.103.255.11, 225.0.0.1), 00:02:53/00:00:06, flags: PTx
Incoming interface: Null, RPF nbr 0.0.0.0
Outgoing interface list: Null
(*, 224.0.1.40), 1w2d/00:02:10, RP 10.103.255.255, flags: SJCL
Incoming interface: TwentyFiveGigE1/1/2, RPF nbr 10.103.224.33
Outgoing interface list:
TwentyFiveGigE1/1/1, Forward/Sparse, 1w2d/00:02:10, flags:
(*, 225.0.0.120), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: TwentyFiveGigE1/1/2, RPF nbr 10.103.224.33
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
(*, 225.0.0.180), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: TwentyFiveGigE1/1/2, RPF nbr 10.103.224.33
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
(*, 225.0.0.220), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: TwentyFiveGigE1/1/2, RPF nbr 10.103.224.33
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
NYC103-Leaf-01#
NYC103-Leaf-02
NYC103-Leaf-02#show ip pim interface
Address Interface Ver/ Nbr Query DR DR
Mode Count Intvl Prior
10.103.224.38 GigabitEthernet1/0/1 v2/S 1 30 1 10.103.224.38
10.103.224.42 GigabitEthernet1/0/2 v2/S 1 30 1 10.103.224.42
10.103.255.12 Tunnel0 v2/P 0 30 1 10.103.255.12
NYC103-Leaf-02#show ip pim neighbor
PIM Neighbor Table
Mode: B - Bidir Capable, DR - Designated Router, N - Default DR Priority,
P - Proxy Capable, S - State Refresh Capable, G - GenID Capable,
L - DR Load-balancing Capable
Neighbor Interface Uptime/Expires Ver DR
Address Prio/Mode
10.103.224.37 GigabitEthernet1/0/1 1w2d/00:01:28 v2 1 / S P G
10.103.224.41 GigabitEthernet1/0/2 1w2d/00:01:35 v2 1 / S P G
NYC103-Leaf-02#show ip pim rp
Group: 225.0.0.1, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 224.0.1.40, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 225.0.0.120, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 225.0.0.180, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 225.0.0.220, RP: 10.103.255.255, uptime 1w2d, expires never
NYC103-Leaf-02#show ip mroute
IP Multicast Routing Table
Flags: D - Dense, S - Sparse, B - Bidir Group, s - SSM Group, C - Connected,
L - Local, P - Pruned, R - RP-bit set, F - Register flag,
T - SPT-bit set, J - Join SPT, M - MSDP created entry, E - Extranet,
X - Proxy Join Timer Running, A - Candidate for MSDP Advertisement,
U - URD, I - Received Source Specific Host Report,
Z - Multicast Tunnel, z - MDT-data group sender,
Y - Joined MDT-data group, y - Sending to MDT-data group,
G - Received BGP C-Mroute, g - Sent BGP C-Mroute,
N - Received BGP Shared-Tree Prune, n - BGP C-Mroute suppressed,
Q - Received BGP S-A Route, q - Sent BGP S-A Route,
V - RD & Vector, v - Vector, p - PIM Joins on route,
x - VxLAN group, c - PFP-SA cache created entry,
* - determined by Assert, # - iif-starg configured on rpf intf,
e - encap-helper tunnel flag, l - LISP decap ref count contributor
Outgoing interface flags: H - Hardware switched, A - Assert winner, p - PIM Join
t - LISP transit group
Timers: Uptime/Expires
Interface state: Interface, Next-Hop or VCD, State/Mode
(*, 225.0.0.1), 1w2d/00:02:44, RP 10.103.255.255, flags: SJCx
Incoming interface: GigabitEthernet1/0/2, RPF nbr 10.103.224.41
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
(*, 224.0.1.40), 1w2d/00:02:18, RP 10.103.255.255, flags: SJCL
Incoming interface: GigabitEthernet1/0/2, RPF nbr 10.103.224.41
Outgoing interface list:
GigabitEthernet1/0/1, Forward/Sparse, 1w2d/00:02:18, flags:
(*, 225.0.0.120), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: GigabitEthernet1/0/2, RPF nbr 10.103.224.41
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
(*, 225.0.0.180), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: GigabitEthernet1/0/2, RPF nbr 10.103.224.41
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
(*, 225.0.0.220), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: GigabitEthernet1/0/2, RPF nbr 10.103.224.41
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
NYC103-Leaf-02#
NYC103-Leaf-03
NYC103-Leaf-03#show ip pim interface
Address Interface Ver/ Nbr Query DR DR
Mode Count Intvl Prior
10.103.224.46 GigabitEthernet1/0/1 v2/S 1 30 1 10.103.224.46
10.103.224.50 GigabitEthernet1/0/2 v2/S 1 30 1 10.103.224.50
10.103.255.13 Tunnel0 v2/P 0 30 1 10.103.255.13
NYC103-Leaf-03#show ip pim neighbor
PIM Neighbor Table
Mode: B - Bidir Capable, DR - Designated Router, N - Default DR Priority,
P - Proxy Capable, S - State Refresh Capable, G - GenID Capable,
L - DR Load-balancing Capable
Neighbor Interface Uptime/Expires Ver DR
Address Prio/Mode
10.103.224.45 GigabitEthernet1/0/1 1w2d/00:01:39 v2 1 / S P G
10.103.224.49 GigabitEthernet1/0/2 1w2d/00:01:36 v2 1 / S P G
NYC103-Leaf-03#show ip pim rp
Group: 225.0.0.1, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 224.0.1.40, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 225.0.0.120, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 225.0.0.180, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 225.0.0.220, RP: 10.103.255.255, uptime 1w2d, expires never
NYC103-Leaf-03#show ip mroute
IP Multicast Routing Table
Flags: D - Dense, S - Sparse, B - Bidir Group, s - SSM Group, C - Connected,
L - Local, P - Pruned, R - RP-bit set, F - Register flag,
T - SPT-bit set, J - Join SPT, M - MSDP created entry, E - Extranet,
X - Proxy Join Timer Running, A - Candidate for MSDP Advertisement,
U - URD, I - Received Source Specific Host Report,
Z - Multicast Tunnel, z - MDT-data group sender,
Y - Joined MDT-data group, y - Sending to MDT-data group,
G - Received BGP C-Mroute, g - Sent BGP C-Mroute,
N - Received BGP Shared-Tree Prune, n - BGP C-Mroute suppressed,
Q - Received BGP S-A Route, q - Sent BGP S-A Route,
V - RD & Vector, v - Vector, p - PIM Joins on route,
x - VxLAN group, c - PFP-SA cache created entry,
* - determined by Assert, # - iif-starg configured on rpf intf,
e - encap-helper tunnel flag, l - LISP decap ref count contributor
Outgoing interface flags: H - Hardware switched, A - Assert winner, p - PIM Join
t - LISP transit group
Timers: Uptime/Expires
Interface state: Interface, Next-Hop or VCD, State/Mode
(*, 225.0.0.1), 1w2d/00:02:31, RP 10.103.255.255, flags: SJCx
Incoming interface: GigabitEthernet1/0/2, RPF nbr 10.103.224.49
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
(*, 224.0.1.40), 1w2d/00:02:11, RP 10.103.255.255, flags: SJCL
Incoming interface: GigabitEthernet1/0/2, RPF nbr 10.103.224.49
Outgoing interface list:
GigabitEthernet1/0/1, Forward/Sparse, 1w2d/00:02:11, flags:
(*, 225.0.0.120), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: GigabitEthernet1/0/2, RPF nbr 10.103.224.49
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
(*, 225.0.0.180), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: GigabitEthernet1/0/2, RPF nbr 10.103.224.49
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
(*, 225.0.0.220), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: GigabitEthernet1/0/2, RPF nbr 10.103.224.49
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
NYC103-Leaf-03#
NYC103-Leaf-04
NYC103-Leaf-04#show ip pim interface
Address Interface Ver/ Nbr Query DR DR
Mode Count Intvl Prior
10.103.224.54 TwentyFiveGigE1/1/1 v2/S 1 30 1 10.103.224.54
10.103.224.58 TwentyFiveGigE1/1/2 v2/S 1 30 1 10.103.224.58
10.103.255.14 Tunnel0 v2/P 0 30 1 10.103.255.14
NYC103-Leaf-04#show ip pim neighbor
PIM Neighbor Table
Mode: B - Bidir Capable, DR - Designated Router, N - Default DR Priority,
P - Proxy Capable, S - State Refresh Capable, G - GenID Capable,
L - DR Load-balancing Capable
Neighbor Interface Uptime/Expires Ver DR
Address Prio/Mode
10.103.224.53 TwentyFiveGigE1/1/1 1w2d/00:01:18 v2 1 / S P G
10.103.224.57 TwentyFiveGigE1/1/2 1w2d/00:01:15 v2 1 / S P G
NYC103-Leaf-04#show ip pim rp
Group: 225.0.0.1, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 224.0.1.40, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 225.0.0.120, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 225.0.0.180, RP: 10.103.255.255, uptime 1w2d, expires never
Group: 225.0.0.220, RP: 10.103.255.255, uptime 1w2d, expires never
NYC103-Leaf-04#show ip mroute
IP Multicast Routing Table
Flags: D - Dense, S - Sparse, B - Bidir Group, s - SSM Group, C - Connected,
L - Local, P - Pruned, R - RP-bit set, F - Register flag,
T - SPT-bit set, J - Join SPT, M - MSDP created entry, E - Extranet,
X - Proxy Join Timer Running, A - Candidate for MSDP Advertisement,
U - URD, I - Received Source Specific Host Report,
Z - Multicast Tunnel, z - MDT-data group sender,
Y - Joined MDT-data group, y - Sending to MDT-data group,
G - Received BGP C-Mroute, g - Sent BGP C-Mroute,
N - Received BGP Shared-Tree Prune, n - BGP C-Mroute suppressed,
Q - Received BGP S-A Route, q - Sent BGP S-A Route,
V - RD & Vector, v - Vector, p - PIM Joins on route,
x - VxLAN group, c - PFP-SA cache created entry,
* - determined by Assert, # - iif-starg configured on rpf intf,
e - encap-helper tunnel flag, l - LISP decap ref count contributor
Outgoing interface flags: H - Hardware switched, A - Assert winner, p - PIM Join
t - LISP transit group
Timers: Uptime/Expires
Interface state: Interface, Next-Hop or VCD, State/Mode
(*, 225.0.0.1), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: TwentyFiveGigE1/1/2, RPF nbr 10.103.224.57
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
(*, 224.0.1.40), 1w2d/00:02:43, RP 10.103.255.255, flags: SJCL
Incoming interface: TwentyFiveGigE1/1/2, RPF nbr 10.103.224.57
Outgoing interface list:
TwentyFiveGigE1/1/1, Forward/Sparse, 1w2d/00:02:43, flags:
(*, 225.0.0.120), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: TwentyFiveGigE1/1/2, RPF nbr 10.103.224.57
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
(*, 225.0.0.180), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: TwentyFiveGigE1/1/2, RPF nbr 10.103.224.57
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
(*, 225.0.0.220), 1w2d/stopped, RP 10.103.255.255, flags: SJCx
Incoming interface: TwentyFiveGigE1/1/2, RPF nbr 10.103.224.57
Outgoing interface list:
Tunnel0, Forward/Sparse-Dense, 1w2d/stopped, flags:
NYC103-Leaf-04#
Leaf Switches (VLANs, VRFs, Virtual Interfaces, Access Ports)
NYC103-Leaf-01
NYC103-Leaf-01#sh vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Gi1/0/1, Gi1/0/2, Gi1/0/3, Gi1/0/4, Gi1/0/5, Gi1/0/6, Gi1/0/7, Gi1/0/8, Gi1/0/9, Gi1/0/10, Gi1/0/11, Gi1/0/12, Gi1/0/13, Gi1/0/14, Gi1/0/15, Gi1/0/16, Gi1/0/17, Gi1/0/18, Gi1/0/19, Gi1/0/20, Gi1/0/21, Gi1/0/22, Gi1/0/23
Gi1/0/24, Gi1/0/25, Gi1/0/26, Gi1/0/27, Gi1/0/28, Gi1/0/29, Gi1/0/30, Gi1/0/31, Gi1/0/32, Gi1/0/33, Gi1/0/34, Gi1/0/35, Gi1/0/36, Gi1/0/37, Gi1/0/38, Gi1/0/39, Gi1/0/40, Gi1/0/41, Gi1/0/42, Gi1/0/43, Gi1/0/44, Gi1/0/45
Gi1/0/46, Ap1/0/1
120 Employee active
121 VLAN0121 active
180 IoT active
220 Guest active
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
3001 Campus-VRF-L3VNI active
3002 Guest-VRF-L3VNI active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1 enet 100001 1500 - - - - - 0 0
120 enet 100120 1500 - - - - - 0 0
121 enet 100121 1500 - - - - - 0 0
180 enet 100180 1500 - - - - - 0 0
220 enet 100220 1500 - - - - - 0 0
1002 fddi 101002 1500 - - - - - 0 0
1003 tr 101003 1500 - - - - - 0 0
1004 fdnet 101004 1500 - - - ieee - 0 0
1005 trnet 101005 1500 - - - ibm - 0 0
3001 enet 103001 1500 - - - - - 0 0
3002 enet 103002 1500 - - - - - 0 0
Remote SPAN VLANs
------------------------------------------------------------------------------
Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
NYC103-Leaf-01#sh vrf
Name Default RD Protocols Interfaces
Mgmt-vrf <not set> ipv4,ipv6 Gi0/0
campus 65106:11 ipv4 Vl1
Vl120
Vl180
Vl3001
guest 65106:211 ipv4 Vl220
Vl3002
NYC103-Leaf-01#sh run int nve1
Building configuration...
Current configuration : 387 bytes
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 200120 mcast-group 225.0.0.120
member vni 200180 mcast-group 225.0.0.180
member vni 303001 vrf campus
member vni 200001 mcast-group 225.0.0.1
member vni 200220 mcast-group 225.0.0.220
member vni 303002 vrf guest
end
NYC103-Leaf-01#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 10.103.64.1 YES NVRAM up up
Vlan120 10.103.120.1 YES NVRAM up up
Vlan180 10.103.180.1 YES NVRAM up up
Vlan220 10.103.220.1 YES NVRAM up up
Vlan3001 10.103.255.11 YES unset up up
Vlan3002 10.103.255.11 YES unset up up
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
GigabitEthernet1/0/1 unassigned YES unset down down
GigabitEthernet1/0/2 unassigned YES unset down down
GigabitEthernet1/0/3 unassigned YES unset down down
GigabitEthernet1/0/4 unassigned YES unset down down
GigabitEthernet1/0/5 unassigned YES unset down down
GigabitEthernet1/0/6 unassigned YES unset down down
GigabitEthernet1/0/7 unassigned YES unset down down
GigabitEthernet1/0/8 unassigned YES unset down down
GigabitEthernet1/0/9 unassigned YES unset down down
GigabitEthernet1/0/10 unassigned YES unset down down
GigabitEthernet1/0/11 unassigned YES unset down down
GigabitEthernet1/0/12 unassigned YES unset down down
GigabitEthernet1/0/13 unassigned YES unset down down
GigabitEthernet1/0/14 unassigned YES unset down down
GigabitEthernet1/0/15 unassigned YES unset down down
GigabitEthernet1/0/16 unassigned YES unset down down
GigabitEthernet1/0/17 unassigned YES unset down down
GigabitEthernet1/0/18 unassigned YES unset down down
GigabitEthernet1/0/19 unassigned YES unset down down
GigabitEthernet1/0/20 unassigned YES unset down down
GigabitEthernet1/0/21 unassigned YES unset down down
GigabitEthernet1/0/22 unassigned YES unset down down
GigabitEthernet1/0/23 unassigned YES unset down down
GigabitEthernet1/0/24 unassigned YES unset down down
GigabitEthernet1/0/25 unassigned YES unset down down
GigabitEthernet1/0/26 unassigned YES unset down down
GigabitEthernet1/0/27 unassigned YES unset down down
GigabitEthernet1/0/28 unassigned YES unset down down
GigabitEthernet1/0/29 unassigned YES unset down down
GigabitEthernet1/0/30 unassigned YES unset down down
GigabitEthernet1/0/31 unassigned YES unset down down
GigabitEthernet1/0/32 unassigned YES unset down down
GigabitEthernet1/0/33 unassigned YES unset down down
GigabitEthernet1/0/34 unassigned YES unset down down
GigabitEthernet1/0/35 unassigned YES unset down down
GigabitEthernet1/0/36 unassigned YES unset down down
GigabitEthernet1/0/37 unassigned YES unset down down
GigabitEthernet1/0/38 unassigned YES unset down down
GigabitEthernet1/0/39 unassigned YES unset down down
GigabitEthernet1/0/40 unassigned YES unset down down
GigabitEthernet1/0/41 unassigned YES unset down down
GigabitEthernet1/0/42 unassigned YES unset down down
GigabitEthernet1/0/43 unassigned YES unset down down
GigabitEthernet1/0/44 unassigned YES unset down down
GigabitEthernet1/0/45 unassigned YES unset down down
GigabitEthernet1/0/46 unassigned YES unset down down
GigabitEthernet1/0/47 unassigned YES unset up up
GigabitEthernet1/0/48 unassigned YES unset up up
GigabitEthernet1/1/1 unassigned YES unset down down
GigabitEthernet1/1/2 unassigned YES unset down down
GigabitEthernet1/1/3 unassigned YES unset down down
GigabitEthernet1/1/4 unassigned YES unset down down
Te1/1/1 unassigned YES unset down down
Te1/1/2 unassigned YES unset down down
Te1/1/3 unassigned YES unset down down
Te1/1/4 unassigned YES unset down down
Te1/1/5 unassigned YES unset down down
Te1/1/6 unassigned YES unset down down
Te1/1/7 unassigned YES unset down down
Te1/1/8 unassigned YES unset down down
Fo1/1/1 unassigned YES unset down down
Fo1/1/2 unassigned YES unset down down
TwentyFiveGigE1/1/1 10.103.224.30 YES NVRAM up up
TwentyFiveGigE1/1/2 10.103.224.34 YES NVRAM up up
Ap1/0/1 unassigned YES unset up up
Port-channel1 unassigned YES unset up up
TLS-VIF0 20.0.88.201 YES TFTP up up
nve1 unassigned YES unset up up
Loopback0 10.103.255.11 YES NVRAM up up
Loopback1000 20.0.88.201 YES manual up up
Tunnel0 10.103.255.11 YES unset up up
Tunnel1 10.103.224.30 YES unset up up
NYC103-Leaf-01#
NYC103-Leaf-01#show interface status
Port Name Status Vlan Duplex Speed Type
Gi1/0/1 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/2 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/3 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/4 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/5 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/6 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/7 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/8 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/9 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/10 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/11 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/12 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/13 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/14 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/15 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/16 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/17 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/18 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/19 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/20 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/21 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/22 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/23 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/24 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/25 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/26 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/27 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/28 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/29 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/30 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/31 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/32 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/33 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/34 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/35 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/36 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/37 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/38 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/39 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/40 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/41 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/42 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/43 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/44 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/45 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/46 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/47 Trunk to NYC103-FL connected trunk a-full a-1000 10/100/1000BaseTX
Gi1/0/48 Trunk to NYC103-FL connected trunk a-full a-1000 10/100/1000BaseTX
Twe1/1/1 To NYC103-Spine-01 connected routed full 10G SFP-10GBase-CX1
Twe1/1/2 To NYC103-Spine-02 connected routed full 10G SFP-10GBase-CX1
Ap1/0/1 connected 1 a-full a-1000 App-hosting port
Po1 LACP Channel Group connected trunk a-full a-1000 N/A
NYC103-Leaf-01#show interface trunk
Port Mode Encapsulation Status Native vlan
Po1 on 802.1q trunking 1
Port Vlans allowed on trunk
Po1 1-3000,3003-4094
Port Vlans allowed and active in management domain
Po1 1,120-121,180,220
Port Vlans in spanning tree forwarding state and not pruned
Po1 1,120-121,180,220
NYC103-Leaf-01#show interface port1
Port-channel1 is up, line protocol is up (connected)
Hardware is EtherChannel, address is 3488.1828.4b30 (bia 3488.1828.4b30)
Description: LACP Channel Group to NYC103-FL01-SW01 on ports 47-48
MTU 9198 bytes, BW 2000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 1000Mb/s, link type is auto, media type is N/A
input flow-control is on, output flow-control is unsupported
Members in this channel: Gi1/0/47 Gi1/0/48
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:02, output 00:00:00, output hang never
Last clearing of "show interface" counters never
Input queue: 0/2000/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 20000 bits/sec, 9 packets/sec
5 minute output rate 18000 bits/sec, 10 packets/sec
9915642 packets input, 1328993168 bytes, 0 no buffer
Received 6788282 broadcasts (6760395 multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 6760395 multicast, 0 pause input
0 input packets with dribble condition detected
6341428 packets output, 1053055823 bytes, 0 underruns
Output 8 broadcasts (2534674 multicasts)
0 output errors, 0 collisions, 1 interface resets
0 unknown protocol drops
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 pause output
0 output buffer failures, 0 output buffers swapped out
NYC103-Leaf-01#
NYC103-Leaf-02
NYC103-Leaf-02#sh vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Gi1/0/3, Gi1/0/4, Gi1/0/5, Gi1/0/6, Gi1/0/7, Gi1/0/8, Gi1/0/9, Gi1/0/10, Gi1/0/11, Gi1/0/12, Gi1/0/13, Gi1/0/14, Gi1/0/15, Gi1/0/16, Gi1/0/17, Gi1/0/18, Gi1/0/19, Gi1/0/20, Gi1/0/21, Gi1/0/22, Gi1/0/23, Gi1/0/24, Gi1/0/25
Gi1/0/26, Gi1/0/27, Gi1/0/28, Gi1/0/29, Gi1/0/30, Gi1/0/31, Gi1/0/32, Gi1/0/33, Gi1/0/34, Gi1/0/35, Gi1/0/36, Gi1/0/37, Gi1/0/38, Gi1/0/39, Gi1/0/40, Gi1/0/41, Gi1/0/42, Gi1/0/43, Gi1/0/44, Gi1/0/45, Gi1/0/46, Ap1/0/1
120 Employee active
121 VLAN0121 active
180 IoT active
220 Guest active
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
3001 Campus-VRF-L3VNI active
3002 Guest-VRF-L3VNI active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1 enet 100001 1500 - - - - - 0 0
120 enet 100120 1500 - - - - - 0 0
121 enet 100121 1500 - - - - - 0 0
180 enet 100180 1500 - - - - - 0 0
220 enet 100220 1500 - - - - - 0 0
1002 fddi 101002 1500 - - - - - 0 0
1003 tr 101003 1500 - - - - - 0 0
1004 fdnet 101004 1500 - - - ieee - 0 0
1005 trnet 101005 1500 - - - ibm - 0 0
3001 enet 103001 1500 - - - - - 0 0
3002 enet 103002 1500 - - - - - 0 0
Remote SPAN VLANs
------------------------------------------------------------------------------
Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
NYC103-Leaf-02#sh vrf
Name Default RD Protocols Interfaces
Mgmt-vrf <not set> ipv4,ipv6 Gi0/0
campus 65106:12 ipv4 Vl1
Vl120
Vl180
Vl3001
guest 65106:212 ipv4 Vl220
Vl3002
NYC103-Leaf-02#sh run int nve1
Building configuration...
Current configuration : 387 bytes
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 200120 mcast-group 225.0.0.120
member vni 200180 mcast-group 225.0.0.180
member vni 303001 vrf campus
member vni 200001 mcast-group 225.0.0.1
member vni 200220 mcast-group 225.0.0.220
member vni 303002 vrf guest
end
NYC103-Leaf-02#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 10.103.64.1 YES NVRAM up up
Vlan120 10.103.120.1 YES NVRAM up up
Vlan180 10.103.180.1 YES NVRAM up up
Vlan220 10.103.220.1 YES NVRAM up up
Vlan3001 10.103.255.12 YES unset up up
Vlan3002 10.103.255.12 YES unset up up
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
GigabitEthernet1/0/1 10.103.224.38 YES NVRAM up up
GigabitEthernet1/0/2 10.103.224.42 YES NVRAM up up
GigabitEthernet1/0/3 unassigned YES unset down down
GigabitEthernet1/0/4 unassigned YES unset down down
GigabitEthernet1/0/5 unassigned YES unset down down
GigabitEthernet1/0/6 unassigned YES unset down down
GigabitEthernet1/0/7 unassigned YES unset down down
GigabitEthernet1/0/8 unassigned YES unset down down
GigabitEthernet1/0/9 unassigned YES unset down down
GigabitEthernet1/0/10 unassigned YES unset down down
GigabitEthernet1/0/11 unassigned YES unset down down
GigabitEthernet1/0/12 unassigned YES unset down down
GigabitEthernet1/0/13 unassigned YES unset down down
GigabitEthernet1/0/14 unassigned YES unset down down
GigabitEthernet1/0/15 unassigned YES unset down down
GigabitEthernet1/0/16 unassigned YES unset down down
GigabitEthernet1/0/17 unassigned YES unset down down
GigabitEthernet1/0/18 unassigned YES unset down down
GigabitEthernet1/0/19 unassigned YES unset down down
GigabitEthernet1/0/20 unassigned YES unset down down
GigabitEthernet1/0/21 unassigned YES unset down down
GigabitEthernet1/0/22 unassigned YES unset down down
GigabitEthernet1/0/23 unassigned YES unset down down
GigabitEthernet1/0/24 unassigned YES unset down down
GigabitEthernet1/0/25 unassigned YES unset down down
GigabitEthernet1/0/26 unassigned YES unset down down
GigabitEthernet1/0/27 unassigned YES unset down down
GigabitEthernet1/0/28 unassigned YES unset down down
GigabitEthernet1/0/29 unassigned YES unset down down
GigabitEthernet1/0/30 unassigned YES unset down down
GigabitEthernet1/0/31 unassigned YES unset down down
GigabitEthernet1/0/32 unassigned YES unset down down
GigabitEthernet1/0/33 unassigned YES unset down down
GigabitEthernet1/0/34 unassigned YES unset down down
GigabitEthernet1/0/35 unassigned YES unset down down
GigabitEthernet1/0/36 unassigned YES unset down down
GigabitEthernet1/0/37 unassigned YES unset down down
GigabitEthernet1/0/38 unassigned YES unset down down
GigabitEthernet1/0/39 unassigned YES unset down down
GigabitEthernet1/0/40 unassigned YES unset down down
GigabitEthernet1/0/41 unassigned YES unset down down
GigabitEthernet1/0/42 unassigned YES unset down down
GigabitEthernet1/0/43 unassigned YES unset down down
GigabitEthernet1/0/44 unassigned YES unset down down
GigabitEthernet1/0/45 unassigned YES unset down down
GigabitEthernet1/0/46 unassigned YES unset down down
GigabitEthernet1/0/47 unassigned YES unset up up
GigabitEthernet1/0/48 unassigned YES unset up up
GigabitEthernet1/1/1 unassigned YES unset down down
GigabitEthernet1/1/2 unassigned YES unset down down
GigabitEthernet1/1/3 unassigned YES unset down down
GigabitEthernet1/1/4 unassigned YES unset down down
Te1/1/1 unassigned YES unset down down
Te1/1/2 unassigned YES unset down down
Te1/1/3 unassigned YES unset down down
Te1/1/4 unassigned YES unset down down
Te1/1/5 unassigned YES unset down down
Te1/1/6 unassigned YES unset down down
Te1/1/7 unassigned YES unset down down
Te1/1/8 unassigned YES unset down down
Fo1/1/1 unassigned YES unset down down
Fo1/1/2 unassigned YES unset down down
TwentyFiveGigE1/1/1 unassigned YES unset down down
TwentyFiveGigE1/1/2 unassigned YES unset down down
Ap1/0/1 unassigned YES unset up up
TLS-VIF0 20.0.66.11 YES TFTP up up
nve1 unassigned YES unset up up
Loopback0 10.103.255.12 YES NVRAM up up
Loopback1000 20.0.66.11 YES manual up up
Tunnel0 10.103.255.12 YES unset up up
Tunnel1 10.103.224.42 YES unset up up
NYC103-Leaf-02#
NYC103-Leaf-02#show interface status
Port Name Status Vlan Duplex Speed Type
Gi1/0/1 To NYC103-Spine-01 connected routed a-full a-1000 10/100/1000BaseTX
Gi1/0/2 To NYC103-Spine-02 connected routed a-full a-1000 10/100/1000BaseTX
Gi1/0/3 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/4 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/5 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/6 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/7 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/8 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/9 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/10 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/11 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/12 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/13 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/14 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/15 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/16 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/17 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/18 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/19 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/20 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/21 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/22 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/23 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/24 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/25 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/26 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/27 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/28 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/29 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/30 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/31 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/32 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/33 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/34 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/35 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/36 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/37 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/38 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/39 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/40 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/41 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/42 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/43 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/44 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/45 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/46 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/47 Trunk to NYC103-FL connected trunk a-full a-1000 10/100/1000BaseTX
Gi1/0/48 Trunk to NYC103-FL connected trunk a-full a-1000 10/100/1000BaseTX
Ap1/0/1 connected 1 a-full a-1000 App-hosting port
NYC103-Leaf-02#show interface trunk
Port Mode Encapsulation Status Native vlan
Gi1/0/47 on 802.1q trunking 1
Gi1/0/48 on 802.1q trunking 1
Port Vlans allowed on trunk
Gi1/0/47 1-3000,3003-4094
Gi1/0/48 1-3000,3003-4094
Port Vlans allowed and active in management domain
Gi1/0/47 1,120-121,180,220
Gi1/0/48 1,120-121,180,220
Port Vlans in spanning tree forwarding state and not pruned
Gi1/0/47 1,120-121,180,220
Gi1/0/48 1,120-121,180,220
NYC103-Leaf-02#
NYC103-Leaf-03
NYC103-Leaf-03#sh vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Gi1/0/3, Gi1/0/4, Gi1/0/5, Gi1/0/6, Gi1/0/7, Gi1/0/8, Gi1/0/9, Gi1/0/10, Gi1/0/11, Gi1/0/14, Gi1/0/15, Gi1/0/16, Gi1/0/17, Gi1/0/18, Gi1/0/19, Gi1/0/20, Gi1/0/21, Gi1/0/22, Gi1/0/23, Gi1/0/24, Gi1/0/25, Gi1/0/26, Gi1/0/27
Gi1/0/28, Gi1/0/29, Gi1/0/30, Gi1/0/31, Gi1/0/32, Gi1/0/33, Gi1/0/34, Gi1/0/35, Gi1/0/36, Gi1/0/37, Gi1/0/38, Gi1/0/39, Gi1/0/40, Gi1/0/41, Gi1/0/42, Gi1/0/43, Gi1/0/44, Gi1/0/45, Gi1/0/46, Gi1/0/47, Ap1/0/1
120 Employee active Gi1/0/12, Gi1/0/13
121 VLAN0121 active
180 IoT active
220 Guest active
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
3001 Campus-VRF-L3VNI active
3002 Guest-VRF-L3VNI active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1 enet 100001 1500 - - - - - 0 0
120 enet 100120 1500 - - - - - 0 0
121 enet 100121 1500 - - - - - 0 0
180 enet 100180 1500 - - - - - 0 0
220 enet 100220 1500 - - - - - 0 0
1002 fddi 101002 1500 - - - - - 0 0
1003 tr 101003 1500 - - - - - 0 0
1004 fdnet 101004 1500 - - - ieee - 0 0
1005 trnet 101005 1500 - - - ibm - 0 0
3001 enet 103001 1500 - - - - - 0 0
3002 enet 103002 1500 - - - - - 0 0
Remote SPAN VLANs
------------------------------------------------------------------------------
Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
NYC103-Leaf-03#sh vrf
Name Default RD Protocols Interfaces
Mgmt-vrf <not set> ipv4,ipv6 Gi0/0
campus 65106:13 ipv4 Vl1
Vl120
Vl180
Vl3001
guest 65106:213 ipv4 Vl220
Vl3002
NYC103-Leaf-03#
NYC103-Leaf-03#sh run int nve1
Building configuration...
Current configuration : 387 bytes
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 200120 mcast-group 225.0.0.120
member vni 200180 mcast-group 225.0.0.180
member vni 303001 vrf campus
member vni 200001 mcast-group 225.0.0.1
member vni 200220 mcast-group 225.0.0.220
member vni 303002 vrf guest
end
NYC103-Leaf-03#
NYC103-Leaf-03#
NYC103-Leaf-03#
NYC103-Leaf-03#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 10.103.64.1 YES NVRAM up up
Vlan120 10.103.120.1 YES NVRAM up up
Vlan180 10.103.180.1 YES NVRAM up up
Vlan220 10.103.220.1 YES NVRAM up up
Vlan3001 10.103.255.13 YES unset up up
Vlan3002 10.103.255.13 YES unset up up
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
GigabitEthernet1/0/1 10.103.224.46 YES NVRAM up up
GigabitEthernet1/0/2 10.103.224.50 YES NVRAM up up
GigabitEthernet1/0/3 unassigned YES unset down down
GigabitEthernet1/0/4 unassigned YES unset down down
GigabitEthernet1/0/5 unassigned YES unset down down
GigabitEthernet1/0/6 unassigned YES unset down down
GigabitEthernet1/0/7 unassigned YES unset down down
GigabitEthernet1/0/8 unassigned YES unset down down
GigabitEthernet1/0/9 unassigned YES unset down down
GigabitEthernet1/0/10 unassigned YES unset down down
GigabitEthernet1/0/11 unassigned YES unset down down
GigabitEthernet1/0/12 unassigned YES unset up up
GigabitEthernet1/0/13 unassigned YES unset up up
GigabitEthernet1/0/14 unassigned YES unset down down
GigabitEthernet1/0/15 unassigned YES unset down down
GigabitEthernet1/0/16 unassigned YES unset down down
GigabitEthernet1/0/17 unassigned YES unset down down
GigabitEthernet1/0/18 unassigned YES unset down down
GigabitEthernet1/0/19 unassigned YES unset down down
GigabitEthernet1/0/20 unassigned YES unset down down
GigabitEthernet1/0/21 unassigned YES unset down down
GigabitEthernet1/0/22 unassigned YES unset down down
GigabitEthernet1/0/23 unassigned YES unset down down
GigabitEthernet1/0/24 unassigned YES unset down down
GigabitEthernet1/0/25 unassigned YES unset down down
GigabitEthernet1/0/26 unassigned YES unset down down
GigabitEthernet1/0/27 unassigned YES unset down down
GigabitEthernet1/0/28 unassigned YES unset down down
GigabitEthernet1/0/29 unassigned YES unset down down
GigabitEthernet1/0/30 unassigned YES unset down down
GigabitEthernet1/0/31 unassigned YES unset down down
GigabitEthernet1/0/32 unassigned YES unset down down
GigabitEthernet1/0/33 unassigned YES unset down down
GigabitEthernet1/0/34 unassigned YES unset down down
GigabitEthernet1/0/35 unassigned YES unset down down
GigabitEthernet1/0/36 unassigned YES unset down down
GigabitEthernet1/0/37 unassigned YES unset down down
GigabitEthernet1/0/38 unassigned YES unset down down
GigabitEthernet1/0/39 unassigned YES unset down down
GigabitEthernet1/0/40 unassigned YES unset down down
GigabitEthernet1/0/41 unassigned YES unset down down
GigabitEthernet1/0/42 unassigned YES unset down down
GigabitEthernet1/0/43 unassigned YES unset down down
GigabitEthernet1/0/44 unassigned YES unset down down
GigabitEthernet1/0/45 unassigned YES unset down down
GigabitEthernet1/0/46 unassigned YES unset down down
GigabitEthernet1/0/47 unassigned YES unset down down
GigabitEthernet1/0/48 unassigned YES unset up up
GigabitEthernet1/1/1 unassigned YES unset down down
GigabitEthernet1/1/2 unassigned YES unset down down
GigabitEthernet1/1/3 unassigned YES unset down down
GigabitEthernet1/1/4 unassigned YES unset down down
Te1/1/1 unassigned YES unset down down
Te1/1/2 unassigned YES unset down down
Te1/1/3 unassigned YES unset down down
Te1/1/4 unassigned YES unset down down
Te1/1/5 unassigned YES unset down down
Te1/1/6 unassigned YES unset down down
Te1/1/7 unassigned YES unset down down
Te1/1/8 unassigned YES unset down down
Fo1/1/1 unassigned YES unset down down
Fo1/1/2 unassigned YES unset down down
TwentyFiveGigE1/1/1 unassigned YES unset down down
TwentyFiveGigE1/1/2 unassigned YES unset down down
Ap1/0/1 unassigned YES unset up up
TLS-VIF0 20.0.66.252 YES TFTP up up
nve1 unassigned YES unset up up
Loopback0 10.103.255.13 YES NVRAM up up
Loopback1000 20.0.66.252 YES manual up up
Tunnel0 10.103.255.13 YES unset up up
Tunnel1 10.103.224.50 YES unset up up
NYC103-Leaf-03#
NYC103-Leaf-03#show interface status
Port Name Status Vlan Duplex Speed Type
Gi1/0/1 To NYC103-Spine-01 connected routed a-full a-1000 10/100/1000BaseTX
Gi1/0/2 To NYC103-Spine-02 connected routed a-full a-1000 10/100/1000BaseTX
Gi1/0/3 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/4 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/5 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/6 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/7 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/8 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/9 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/10 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/11 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/12 To NYC103-Client36 connected 120 a-full a-100 10/100/1000BaseTX
Gi1/0/13 To NYC103-Client37 connected 120 a-full a-100 10/100/1000BaseTX
Gi1/0/14 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/15 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/16 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/17 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/18 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/19 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/20 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/21 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/22 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/23 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/24 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/25 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/26 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/27 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/28 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/29 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/30 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/31 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/32 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/33 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/34 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/35 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/36 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/37 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/38 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/39 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/40 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/41 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/42 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/43 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/44 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/45 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/46 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/47 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/48 Trunk to NYC103-FL connected trunk a-full a-1000 10/100/1000BaseTX
Ap1/0/1 connected 1 a-full a-1000 App-hosting port
NYC103-Leaf-03#show interface trunk
Port Mode Encapsulation Status Native vlan
Gi1/0/48 on 802.1q trunking 1
Port Vlans allowed on trunk
Gi1/0/48 1-3000,3003-4094
Port Vlans allowed and active in management domain
Gi1/0/48 1,120-121,180,220
Port Vlans in spanning tree forwarding state and not pruned
Gi1/0/48 1,120-121,180,220
NYC103-Leaf-03#
NYC103-Leaf-04
NYC103-Leaf-04#sh vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Gi1/0/1, Gi1/0/2, Gi1/0/3, Gi1/0/4, Gi1/0/5, Gi1/0/6, Gi1/0/7, Gi1/0/8, Gi1/0/9, Gi1/0/10, Gi1/0/11, Gi1/0/12, Gi1/0/13, Gi1/0/14, Gi1/0/15, Gi1/0/16, Gi1/0/17, Gi1/0/18, Gi1/0/19, Gi1/0/20, Gi1/0/21, Gi1/0/22, Gi1/0/23
Gi1/0/24, Gi1/0/25, Gi1/0/26, Gi1/0/27, Gi1/0/28, Gi1/0/29, Gi1/0/30, Gi1/0/31, Gi1/0/32, Gi1/0/33, Gi1/0/34, Gi1/0/35, Gi1/0/36, Gi1/0/37, Gi1/0/38, Gi1/0/39, Gi1/0/40, Gi1/0/41, Gi1/0/42, Gi1/0/43, Gi1/0/44, Gi1/0/45
Gi1/0/46, Ap1/0/1
120 Employee active
121 VLAN0121 active
180 IoT active
220 Guest active
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
3001 Campus-VRF-L3VNI active
3002 Guest-VRF-L3VNI active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1 enet 100001 1500 - - - - - 0 0
120 enet 100120 1500 - - - - - 0 0
121 enet 100121 1500 - - - - - 0 0
180 enet 100180 1500 - - - - - 0 0
220 enet 100220 1500 - - - - - 0 0
1002 fddi 101002 1500 - - - - - 0 0
1003 tr 101003 1500 - - - - - 0 0
1004 fdnet 101004 1500 - - - ieee - 0 0
1005 trnet 101005 1500 - - - ibm - 0 0
3001 enet 103001 1500 - - - - - 0 0
3002 enet 103002 1500 - - - - - 0 0
Remote SPAN VLANs
------------------------------------------------------------------------------
Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
NYC103-Leaf-04#sh vrf
Name Default RD Protocols Interfaces
Mgmt-vrf <not set> ipv4,ipv6 Gi0/0
campus 65106:14 ipv4 Vl1
Vl120
Vl180
Vl3001
guest 65106:214 ipv4 Vl220
Vl3002
NYC103-Leaf-04#
NYC103-Leaf-04#sh run int nve1
Building configuration...
Current configuration : 387 bytes
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 200120 mcast-group 225.0.0.120
member vni 200180 mcast-group 225.0.0.180
member vni 303001 vrf campus
member vni 200001 mcast-group 225.0.0.1
member vni 200220 mcast-group 225.0.0.220
member vni 303002 vrf guest
end
NYC103-Leaf-04#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 10.103.64.1 YES NVRAM up up
Vlan120 10.103.120.1 YES NVRAM up up
Vlan180 10.103.180.1 YES NVRAM up up
Vlan220 10.103.220.1 YES NVRAM up up
Vlan3001 10.103.255.14 YES unset up up
Vlan3002 10.103.255.14 YES unset up up
GigabitEthernet0/0 unassigned YES NVRAM administratively down down
GigabitEthernet1/0/1 unassigned YES unset down down
GigabitEthernet1/0/2 unassigned YES unset down down
GigabitEthernet1/0/3 unassigned YES unset down down
GigabitEthernet1/0/4 unassigned YES unset down down
GigabitEthernet1/0/5 unassigned YES unset down down
GigabitEthernet1/0/6 unassigned YES unset down down
GigabitEthernet1/0/7 unassigned YES unset down down
GigabitEthernet1/0/8 unassigned YES unset down down
GigabitEthernet1/0/9 unassigned YES unset down down
GigabitEthernet1/0/10 unassigned YES unset down down
GigabitEthernet1/0/11 unassigned YES unset down down
GigabitEthernet1/0/12 unassigned YES unset down down
GigabitEthernet1/0/13 unassigned YES unset down down
GigabitEthernet1/0/14 unassigned YES unset down down
GigabitEthernet1/0/15 unassigned YES unset down down
GigabitEthernet1/0/16 unassigned YES unset down down
GigabitEthernet1/0/17 unassigned YES unset down down
GigabitEthernet1/0/18 unassigned YES unset down down
GigabitEthernet1/0/19 unassigned YES unset down down
GigabitEthernet1/0/20 unassigned YES unset down down
GigabitEthernet1/0/21 unassigned YES unset down down
GigabitEthernet1/0/22 unassigned YES unset down down
GigabitEthernet1/0/23 unassigned YES unset down down
GigabitEthernet1/0/24 unassigned YES unset down down
GigabitEthernet1/0/25 unassigned YES unset down down
GigabitEthernet1/0/26 unassigned YES unset down down
GigabitEthernet1/0/27 unassigned YES unset down down
GigabitEthernet1/0/28 unassigned YES unset down down
GigabitEthernet1/0/29 unassigned YES unset down down
GigabitEthernet1/0/30 unassigned YES unset down down
GigabitEthernet1/0/31 unassigned YES unset down down
GigabitEthernet1/0/32 unassigned YES unset down down
GigabitEthernet1/0/33 unassigned YES unset down down
GigabitEthernet1/0/34 unassigned YES unset down down
GigabitEthernet1/0/35 unassigned YES unset down down
GigabitEthernet1/0/36 unassigned YES unset down down
GigabitEthernet1/0/37 unassigned YES unset down down
GigabitEthernet1/0/38 unassigned YES unset down down
GigabitEthernet1/0/39 unassigned YES unset down down
GigabitEthernet1/0/40 unassigned YES unset down down
GigabitEthernet1/0/41 unassigned YES unset down down
GigabitEthernet1/0/42 unassigned YES unset down down
GigabitEthernet1/0/43 unassigned YES unset down down
GigabitEthernet1/0/44 unassigned YES unset down down
GigabitEthernet1/0/45 unassigned YES unset down down
GigabitEthernet1/0/46 unassigned YES unset down down
GigabitEthernet1/0/47 unassigned YES unset up up
GigabitEthernet1/0/48 unassigned YES unset up up
GigabitEthernet1/1/1 unassigned YES unset down down
GigabitEthernet1/1/2 unassigned YES unset down down
GigabitEthernet1/1/3 unassigned YES unset down down
GigabitEthernet1/1/4 unassigned YES unset down down
Te1/1/1 unassigned YES unset down down
Te1/1/2 unassigned YES unset down down
Te1/1/3 unassigned YES unset down down
Te1/1/4 unassigned YES unset down down
Te1/1/5 unassigned YES unset down down
Te1/1/6 unassigned YES unset down down
Te1/1/7 unassigned YES unset down down
Te1/1/8 unassigned YES unset down down
Fo1/1/1 unassigned YES unset down down
Fo1/1/2 unassigned YES unset down down
TwentyFiveGigE1/1/1 10.103.224.54 YES NVRAM up up
TwentyFiveGigE1/1/2 10.103.224.58 YES NVRAM up up
Ap1/0/1 unassigned YES unset up up
Port-channel1 unassigned YES unset up up
TLS-VIF0 20.0.82.26 YES TFTP up up
nve1 unassigned YES unset up up
Loopback0 10.103.255.14 YES NVRAM up up
Loopback1000 20.0.82.26 YES manual up up
Tunnel0 10.103.255.14 YES unset up up
Tunnel1 10.103.224.54 YES unset up up
NYC103-Leaf-04#
NYC103-Leaf-04#show interface status
Port Name Status Vlan Duplex Speed Type
Gi1/0/1 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/2 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/3 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/4 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/5 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/6 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/7 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/8 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/9 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/10 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/11 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/12 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/13 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/14 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/15 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/16 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/17 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/18 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/19 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/20 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/21 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/22 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/23 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/24 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/25 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/26 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/27 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/28 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/29 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/30 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/31 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/32 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/33 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/34 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/35 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/36 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/37 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/38 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/39 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/40 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/41 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/42 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/43 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/44 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/45 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/46 notconnect 1 auto auto 10/100/1000BaseTX
Gi1/0/47 Trunk to NYC103-FL connected trunk a-full a-1000 10/100/1000BaseTX
Gi1/0/48 Trunk to NYC103-FL connected trunk a-full a-1000 10/100/1000BaseTX
Twe1/1/1 To NYC103-Spine-01 connected routed full 25G SFP-H25GBase-CU1M
Twe1/1/2 To NYC103-Spine-02 connected routed full 25G SFP-H25GBase-CU1M
Ap1/0/1 connected 1 a-full a-1000 App-hosting port
Po1 LACP Channel Group connected trunk a-full a-1000 N/A
NYC103-Leaf-04#show interface trunk
Port Mode Encapsulation Status Native vlan
Po1 on 802.1q trunking 1
Port Vlans allowed on trunk
Po1 1-3000,3003-4094
Port Vlans allowed and active in management domain
Po1 1,120-121,180,220
Port Vlans in spanning tree forwarding state and not pruned
Po1 1,120-121,180,220
NYC103-Leaf-04#show interface port1
Port-channel1 is up, line protocol is up (connected)
Hardware is EtherChannel, address is 242a.0490.e730 (bia 242a.0490.e730)
Description: LACP Channel Group to NYC103-FL01-SW01 on ports 47-48
MTU 9198 bytes, BW 2000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 1000Mb/s, link type is auto, media type is N/A
input flow-control is on, output flow-control is unsupported
Members in this channel: Gi1/0/47 Gi1/0/48
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:04, output 00:00:00, output hang never
Last clearing of "show interface" counters never
Input queue: 0/2000/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 124000 bits/sec, 46 packets/sec
5 minute output rate 44000 bits/sec, 36 packets/sec
3709342 packets input, 1205288620 bytes, 0 no buffer
Received 121836 broadcasts (101654 multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 101654 multicast, 0 pause input
0 input packets with dribble condition detected
6221127 packets output, 2667521581 bytes, 0 underruns
Output 153 broadcasts (1782529 multicasts)
0 output errors, 0 collisions, 1 interface resets
0 unknown protocol drops
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 pause output
0 output buffer failures, 0 output buffers swapped out
NYC103-Leaf-04#
Leaf Switches (L2 Forwarding, L3 Routing)
NYC103-Leaf-01
NYC103-Leaf-01#show mac address-table dynamic
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 8c44.a571.8300 DYNAMIC Po1
1 8c44.a571.8317 DYNAMIC Po1
1 8c44.a571.8318 DYNAMIC Po1
1 c414.a202.89a0 DYNAMIC Po1
120 8c44.a571.8318 DYNAMIC Po1
120 a0ce.c8fb.467f DYNAMIC Po1
180 8c44.a571.8318 DYNAMIC Po1
220 8c44.a571.8318 DYNAMIC Po1
121 8c44.a571.8318 DYNAMIC Po1
Total Mac Addresses for this criterion: 9
NYC103-Leaf-01#show l2route evpn mac ip
EVI ETag Prod Mac Address Host IP Next Hop(s)
----- ---------- ----- -------------- --------------------------------------- --------------------------------------------------
1 0 L2VPN 8c44.a571.8300 10.103.64.15 Po1:1
1 0 BGP 9433.d807.8547 10.103.64.26 V:200001 10.103.255.14
1 0 BGP a0bc.6fd6.7b00 10.103.64.12 V:200001 10.103.255.12
1 0 BGP a0bc.6fe2.8b80 10.103.64.11 V:200001 10.103.255.12
1 0 BGP a0bc.6fe2.8f00 10.103.64.13 V:200001 10.103.255.12
1 0 BGP a0ce.c8fb.4677 10.103.120.15 V:200120 10.103.255.14
1 0 BGP a0ce.c8fb.4687 10.103.120.14 V:200120 10.103.255.12
1 0 BGP a0ce.c8fb.4689 10.103.120.23 V:200120 10.103.255.13
1 0 BGP a0ce.c8fb.47a7 10.103.120.16 V:200120 10.103.255.13
1 0 BGP a0ce.c8fb.47b7 10.103.120.13 V:200120 10.103.255.12
1 0 BGP a0ce.c8fb.47dc 10.103.120.11 V:200120 10.103.255.12
1 0 L2VPN c414.a202.89a0 10.103.64.19 Po1:1
1 0 BGP c4d6.664f.55b0 10.103.64.17 V:200001 10.103.255.12
1 0 BGP c4d6.666d.0f80 10.103.64.28 V:200001 10.103.255.14
1 0 BGP c4d6.666d.2e10 10.103.64.14 V:200001 10.103.255.12
1 0 BGP c4d6.66d9.3140 10.103.64.20 V:200001 10.103.255.13
120 0 BGP a0ce.c8fb.4677 10.103.120.15 V:200120 10.103.255.14
120 0 L2VPN a0ce.c8fb.467f 10.103.120.12 Po1:120
120 0 BGP a0ce.c8fb.4687 10.103.120.14 V:200120 10.103.255.12
120 0 BGP a0ce.c8fb.4689 10.103.120.23 V:200120 10.103.255.13
120 0 BGP a0ce.c8fb.47a7 10.103.120.16 V:200120 10.103.255.13
120 0 BGP a0ce.c8fb.47b7 10.103.120.13 V:200120 10.103.255.12
120 0 BGP a0ce.c8fb.47dc 10.103.120.11 V:200120 10.103.255.12
NYC103-Leaf-01#show ip bgp vpnv4 vrf campus
BGP table version is 131, local router ID is 10.103.255.11
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:11 (default for vrf campus)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 3/1000
Ow ip
*>i 10.103.255.3 0 100 0 65102 65100 65101 ?
* i 10.103.64.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.13 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
*> 0.0.0.0 0 32768 ?
* i 10.103.64.0/18 10.103.255.4 0 100 0 i
*>i 10.103.255.3 0 100 0 i
*>i 10.103.64.11/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.12/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.13/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.14/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.17/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.20/32 10.103.255.13 0 100 0 ?
*>i 10.103.64.26/32 10.103.255.14 0 100 0 ?
*>i 10.103.64.28/32 10.103.255.14 0 100 0 ?
* i 10.103.120.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.13 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
*> 0.0.0.0 0 32768 ?
*>i 10.103.120.11/32 10.103.255.12 0 100 0 ?
*>i 10.103.120.13/32 10.103.255.12 0 100 0 ?
*>i 10.103.120.14/32 10.103.255.12 0 100 0 ?
*>i 10.103.120.15/32 10.103.255.14 0 100 0 ?
*>i 10.103.120.16/32 10.103.255.13 0 100 0 ?
*>i 10.103.120.23/32 10.103.255.13 0 100 0 ?
* i 10.103.128.0/18 10.103.255.4 0 100 0 i
*>i 10.103.255.3 0 100 0 i
* i 10.103.180.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.13 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
*> 0.0.0.0 0 32768 ?
NYC103-Leaf-01#show ip bgp vpnv4 vrf campus 0.0.0.0/0
BGP routing table entry for 65106:11:0.0.0.0/0, version 25
Paths: (2 available, best #2, table campus)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101, imported path from [5][65106:4][0][0][0.0.0.0]/17 (global)
10.103.255.4 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
Originator: 10.103.255.4, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:campus, vni:303001
local router mac:3488.1828.4B72
encap:1
vtep-ip:10.103.255.11
bdi:Vlan3001
Remote VxLAN:
Topoid 0x2(vrf campus)
Remote Router MAC:3488.1824.7672
Encap 8
Egress VNI 303001
RTEP 10.103.255.4
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65101, imported path from [5][65106:3][0][0][0.0.0.0]/17 (global)
10.103.255.3 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:campus, vni:303001
local router mac:3488.1828.4B72
encap:1
vtep-ip:10.103.255.11
bdi:Vlan3001
Remote VxLAN:
Topoid 0x2(vrf campus)
Remote Router MAC:246C.847E.E0F2
Encap 8
Egress VNI 303001
RTEP 10.103.255.3
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
NYC103-Leaf-01#show ip route vrf campus
Routing Table: campus
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.255.3 to network 0.0.0.0
B* 0.0.0.0/0 [200/0] via 10.103.255.3, 1w2d, Vlan3001
10.0.0.0/8 is variably subnetted, 25 subnets, 3 masks
B 10.103.64.0/18 [200/0] via 10.103.255.3, 1w2d, Vlan3001
C 10.103.64.0/24 is directly connected, Vlan1
L 10.103.64.1/32 is directly connected, Vlan1
B 10.103.64.11/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.12/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.13/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.14/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
S 10.103.64.15/32 is directly connected, Vlan1
B 10.103.64.17/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
S 10.103.64.19/32 is directly connected, Vlan1
B 10.103.64.20/32 [200/0] via 10.103.255.13, 1w1d, Vlan3001
B 10.103.64.26/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
B 10.103.64.28/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
C 10.103.120.0/24 is directly connected, Vlan120
L 10.103.120.1/32 is directly connected, Vlan120
B 10.103.120.11/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
S 10.103.120.12/32 is directly connected, Vlan120
B 10.103.120.13/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.14/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.15/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
B 10.103.120.16/32 [200/0] via 10.103.255.13, 1w2d, Vlan3001
B 10.103.120.23/32 [200/0] via 10.103.255.13, 1w2d, Vlan3001
B 10.103.128.0/18 [200/0] via 10.103.255.3, 1w2d, Vlan3001
C 10.103.180.0/24 is directly connected, Vlan180
L 10.103.180.1/32 is directly connected, Vlan180
NYC103-Leaf-01#show ip bgp vpnv4 vrf guest
BGP table version is 131, local router ID is 10.103.255.11
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:211 (default for vrf guest)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 1/1000
* i 0.0.0.0 10.103.255.4 0 100 0 65102 65100 65100 65100 65100 i
*>i 10.103.255.3 0 100 0 65102 65100 65100 65100 65100 i
*>i 10.103.64.8/30 10.103.255.3 0 100 0 i
*>i 10.103.64.12/30 10.103.255.4 0 100 0 i
* i 10.103.220.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.13 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
*> 0.0.0.0 0 32768 ?
NYC103-Leaf-01#show ip bgp vpnv4 vrf guest 0.0.0.0/0
BGP routing table entry for 65106:211:0.0.0.0/0, version 27
Paths: (2 available, best #2, table guest)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65100 65100 65100, imported path from [5][65106:24][0][0][0.0.0.0]/17 (global)
10.103.255.4 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal
Extended Community: RT:65106:2 ENCAP:8 Router MAC:3488.1824.764B
Originator: 10.103.255.4, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:guest, vni:303002
local router mac:3488.1828.4B4B
encap:1
vtep-ip:10.103.255.11
bdi:Vlan3002
Remote VxLAN:
Topoid 0x3(vrf guest)
Remote Router MAC:3488.1824.764B
Encap 8
Egress VNI 303002
RTEP 10.103.255.4
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65100 65100 65100, imported path from [5][65106:23][0][0][0.0.0.0]/17 (global)
10.103.255.3 (metric 13) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, best
Extended Community: RT:65106:2 ENCAP:8 Router MAC:246C.847E.E0CB
Originator: 10.103.255.3, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:guest, vni:303002
local router mac:3488.1828.4B4B
encap:1
vtep-ip:10.103.255.11
bdi:Vlan3002
Remote VxLAN:
Topoid 0x3(vrf guest)
Remote Router MAC:246C.847E.E0CB
Encap 8
Egress VNI 303002
RTEP 10.103.255.3
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
NYC103-Leaf-01#show ip route vrf guest
Routing Table: guest
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.255.3 to network 0.0.0.0
B* 0.0.0.0/0 [200/0] via 10.103.255.3, 1w2d, Vlan3002
10.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
B 10.103.64.8/30 [200/0] via 10.103.255.3, 1w2d, Vlan3002
B 10.103.64.12/30 [200/0] via 10.103.255.4, 1w2d, Vlan3002
C 10.103.220.0/24 is directly connected, Vlan220
L 10.103.220.1/32 is directly connected, Vlan220
NYC103-Leaf-01#
NYC103-Leaf-02
NYC103-Leaf-02#show mac address-table dynamic
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 a0bc.6fd6.7b00 DYNAMIC Gi1/0/47
1 a0bc.6fd6.7b18 DYNAMIC Gi1/0/47
1 a0bc.6fe2.8b80 DYNAMIC Gi1/0/48
1 a0bc.6fe2.8b98 DYNAMIC Gi1/0/48
1 a0bc.6fe2.8f00 DYNAMIC Gi1/0/47
1 a0bc.6fe2.8f17 DYNAMIC Gi1/0/47
1 c4d6.664f.55b0 DYNAMIC Gi1/0/48
1 c4d6.666d.2e10 DYNAMIC Gi1/0/47
120 a0bc.6fd6.7b18 DYNAMIC Gi1/0/47
120 a0bc.6fe2.8b98 DYNAMIC Gi1/0/48
120 a0bc.6fe2.8f17 DYNAMIC Gi1/0/47
120 a0ce.c8fb.4687 DYNAMIC Gi1/0/47
120 a0ce.c8fb.47b7 DYNAMIC Gi1/0/47
120 a0ce.c8fb.47dc DYNAMIC Gi1/0/48
180 a0bc.6fd6.7b18 DYNAMIC Gi1/0/47
180 a0bc.6fe2.8b98 DYNAMIC Gi1/0/48
180 a0bc.6fe2.8f17 DYNAMIC Gi1/0/47
220 a0bc.6fd6.7b18 DYNAMIC Gi1/0/47
220 a0bc.6fe2.8b98 DYNAMIC Gi1/0/48
220 a0bc.6fe2.8f17 DYNAMIC Gi1/0/47
121 a0bc.6fd6.7b18 DYNAMIC Gi1/0/47
121 a0bc.6fe2.8b98 DYNAMIC Gi1/0/48
121 a0bc.6fe2.8f17 DYNAMIC Gi1/0/47
Total Mac Addresses for this criterion: 23
NYC103-Leaf-02#show l2route evpn mac ip
EVI ETag Prod Mac Address Host IP Next Hop(s)
----- ---------- ----- -------------- --------------------------------------- --------------------------------------------------
1 0 BGP 8c44.a571.8300 10.103.64.15 V:200001 10.103.255.11
1 0 BGP 9433.d807.8547 10.103.64.26 V:200001 10.103.255.14
1 0 L2VPN a0bc.6fd6.7b00 10.103.64.12 Gi1/0/47:1
1 0 L2VPN a0bc.6fe2.8b80 10.103.64.11 Gi1/0/48:1
1 0 L2VPN a0bc.6fe2.8f00 10.103.64.13 Gi1/0/47:1
1 0 BGP a0ce.c8fb.4677 10.103.120.15 V:200120 10.103.255.14
1 0 BGP a0ce.c8fb.467f 10.103.120.12 V:200120 10.103.255.11
1 0 BGP a0ce.c8fb.4689 10.103.120.23 V:200120 10.103.255.13
1 0 BGP a0ce.c8fb.47a7 10.103.120.16 V:200120 10.103.255.13
1 0 BGP c414.a202.89a0 10.103.64.19 V:200001 10.103.255.11
1 0 L2VPN c4d6.664f.55b0 10.103.64.17 Gi1/0/48:1
1 0 BGP c4d6.666d.0f80 10.103.64.28 V:200001 10.103.255.14
1 0 L2VPN c4d6.666d.2e10 10.103.64.14 Gi1/0/47:1
1 0 BGP c4d6.66d9.3140 10.103.64.20 V:200001 10.103.255.13
120 0 BGP a0ce.c8fb.4677 10.103.120.15 V:200120 10.103.255.14
120 0 BGP a0ce.c8fb.467f 10.103.120.12 V:200120 10.103.255.11
120 0 L2VPN a0ce.c8fb.4687 10.103.120.14 Gi1/0/47:120
120 0 BGP a0ce.c8fb.4689 10.103.120.23 V:200120 10.103.255.13
120 0 BGP a0ce.c8fb.47a7 10.103.120.16 V:200120 10.103.255.13
120 0 L2VPN a0ce.c8fb.47b7 10.103.120.13 Gi1/0/47:120
120 0 L2VPN a0ce.c8fb.47dc 10.103.120.11 Gi1/0/48:120
NYC103-Leaf-02#show ip bgp vpnv4 vrf campus
BGP table version is 114, local router ID is 10.103.255.12
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:12 (default for vrf campus)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 3/1000
* i 0.0.0.0 10.103.255.4 0 100 0 65102 65100 65101 ?
*>i 10.103.255.3 0 100 0 65102 65100 65101 ?
* i 10.103.64.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
* i 10.103.255.13 0 100 0 ?
*> 0.0.0.0 0 32768 ?
*>i 10.103.64.0/18 10.103.255.3 0 100 0 i
* i 10.103.255.4 0 100 0 i
*>i 10.103.64.15/32 10.103.255.11 0 100 0 ?
*>i 10.103.64.19/32 10.103.255.11 0 100 0 ?
*>i 10.103.64.20/32 10.103.255.13 0 100 0 ?
*>i 10.103.64.26/32 10.103.255.14 0 100 0 ?
*>i 10.103.64.28/32 10.103.255.14 0 100 0 ?
* i 10.103.120.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
* i 10.103.255.13 0 100 0 ?
*> 0.0.0.0 0 32768 ?
*>i 10.103.120.12/32 10.103.255.11 0 100 0 ?
*>i 10.103.120.15/32 10.103.255.14 0 100 0 ?
*>i 10.103.120.16/32 10.103.255.13 0 100 0 ?
*>i 10.103.120.23/32 10.103.255.13 0 100 0 ?
*>i 10.103.128.0/18 10.103.255.3 0 100 0 i
* i 10.103.255.4 0 100 0 i
* i 10.103.180.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
* i 10.103.255.13 0 100 0 ?
*> 0.0.0.0 0 32768 ?
NYC103-Leaf-02#show ip bgp vpnv4 vrf campus 0.0.0.0/0
BGP routing table entry for 65106:12:0.0.0.0/0, version 25
Paths: (2 available, best #2, table campus)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101, imported path from [5][65106:4][0][0][0.0.0.0]/17 (global)
10.103.255.4 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
Originator: 10.103.255.4, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:campus, vni:303001
local router mac:648F.3E3F.1472
encap:1
vtep-ip:10.103.255.12
bdi:Vlan3001
Remote VxLAN:
Topoid 0x2(vrf campus)
Remote Router MAC:3488.1824.7672
Encap 8
Egress VNI 303001
RTEP 10.103.255.4
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:33 EDT
Refresh Epoch 1
65102 65100 65101, imported path from [5][65106:3][0][0][0.0.0.0]/17 (global)
10.103.255.3 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:campus, vni:303001
local router mac:648F.3E3F.1472
encap:1
vtep-ip:10.103.255.12
bdi:Vlan3001
Remote VxLAN:
Topoid 0x2(vrf campus)
Remote Router MAC:246C.847E.E0F2
Encap 8
Egress VNI 303001
RTEP 10.103.255.3
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:33 EDT
NYC103-Leaf-02#show ip route vrf campus
Routing Table: campus
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.255.3 to network 0.0.0.0
B* 0.0.0.0/0 [200/0] via 10.103.255.3, 1w2d, Vlan3001
10.0.0.0/8 is variably subnetted, 25 subnets, 3 masks
B 10.103.64.0/18 [200/0] via 10.103.255.3, 1w2d, Vlan3001
C 10.103.64.0/24 is directly connected, Vlan1
L 10.103.64.1/32 is directly connected, Vlan1
S 10.103.64.11/32 is directly connected, Vlan1
S 10.103.64.12/32 is directly connected, Vlan1
S 10.103.64.13/32 is directly connected, Vlan1
S 10.103.64.14/32 is directly connected, Vlan1
B 10.103.64.15/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
S 10.103.64.17/32 is directly connected, Vlan1
B 10.103.64.19/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
B 10.103.64.20/32 [200/0] via 10.103.255.13, 1w1d, Vlan3001
B 10.103.64.26/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
B 10.103.64.28/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
C 10.103.120.0/24 is directly connected, Vlan120
L 10.103.120.1/32 is directly connected, Vlan120
S 10.103.120.11/32 is directly connected, Vlan120
B 10.103.120.12/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
S 10.103.120.13/32 is directly connected, Vlan120
S 10.103.120.14/32 is directly connected, Vlan120
B 10.103.120.15/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
B 10.103.120.16/32 [200/0] via 10.103.255.13, 1w2d, Vlan3001
B 10.103.120.23/32 [200/0] via 10.103.255.13, 1w2d, Vlan3001
B 10.103.128.0/18 [200/0] via 10.103.255.3, 1w2d, Vlan3001
C 10.103.180.0/24 is directly connected, Vlan180
L 10.103.180.1/32 is directly connected, Vlan180
NYC103-Leaf-02#show ip bgp vpnv4 vrf guest
BGP table version is 114, local router ID is 10.103.255.12
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:212 (default for vrf guest)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 1/1000
* i 0.0.0.0 10.103.255.4 0 100 0 65102 65100 65100 65100 65100 i
*>i 10.103.255.3 0 100 0 65102 65100 65100 65100 65100 i
*>i 10.103.64.8/30 10.103.255.3 0 100 0 i
*>i 10.103.64.12/30 10.103.255.4 0 100 0 i
* i 10.103.220.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
* i 10.103.255.13 0 100 0 ?
*> 0.0.0.0 0 32768 ?
NYC103-Leaf-02#show ip bgp vpnv4 vrf guest 0.0.0.0/0
BGP routing table entry for 65106:212:0.0.0.0/0, version 27
Paths: (2 available, best #2, table guest)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65100 65100 65100, imported path from [5][65106:24][0][0][0.0.0.0]/17 (global)
10.103.255.4 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal
Extended Community: RT:65106:2 ENCAP:8 Router MAC:3488.1824.764B
Originator: 10.103.255.4, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:guest, vni:303002
local router mac:648F.3E3F.144B
encap:1
vtep-ip:10.103.255.12
bdi:Vlan3002
Remote VxLAN:
Topoid 0x3(vrf guest)
Remote Router MAC:3488.1824.764B
Encap 8
Egress VNI 303002
RTEP 10.103.255.4
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:33 EDT
Refresh Epoch 1
65102 65100 65100 65100 65100, imported path from [5][65106:23][0][0][0.0.0.0]/17 (global)
10.103.255.3 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, best
Extended Community: RT:65106:2 ENCAP:8 Router MAC:246C.847E.E0CB
Originator: 10.103.255.3, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:guest, vni:303002
local router mac:648F.3E3F.144B
encap:1
vtep-ip:10.103.255.12
bdi:Vlan3002
Remote VxLAN:
Topoid 0x3(vrf guest)
Remote Router MAC:246C.847E.E0CB
Encap 8
Egress VNI 303002
RTEP 10.103.255.3
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:33 EDT
NYC103-Leaf-02#show ip route vrf guest
Routing Table: guest
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.255.3 to network 0.0.0.0
B* 0.0.0.0/0 [200/0] via 10.103.255.3, 1w2d, Vlan3002
10.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
B 10.103.64.8/30 [200/0] via 10.103.255.3, 1w2d, Vlan3002
B 10.103.64.12/30 [200/0] via 10.103.255.4, 1w2d, Vlan3002
C 10.103.220.0/24 is directly connected, Vlan220
L 10.103.220.1/32 is directly connected, Vlan220
NYC103-Leaf-02#
NYC103-Leaf-03
NYC103-Leaf-03#show mac address-table dynamic
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 c4d6.66d9.3140 DYNAMIC Gi1/0/48
120 a0ce.c8fb.4689 DYNAMIC Gi1/0/13
120 a0ce.c8fb.47a7 DYNAMIC Gi1/0/12
Total Mac Addresses for this criterion: 3
NYC103-Leaf-03#show l2route evpn mac ip
EVI ETag Prod Mac Address Host IP Next Hop(s)
----- ---------- ----- -------------- --------------------------------------- --------------------------------------------------
1 0 BGP 8c44.a571.8300 10.103.64.15 V:200001 10.103.255.11
1 0 BGP 9433.d807.8547 10.103.64.26 V:200001 10.103.255.14
1 0 BGP a0bc.6fd6.7b00 10.103.64.12 V:200001 10.103.255.12
1 0 BGP a0bc.6fe2.8b80 10.103.64.11 V:200001 10.103.255.12
1 0 BGP a0bc.6fe2.8f00 10.103.64.13 V:200001 10.103.255.12
1 0 BGP a0ce.c8fb.4677 10.103.120.15 V:200120 10.103.255.14
1 0 BGP a0ce.c8fb.467f 10.103.120.12 V:200120 10.103.255.11
1 0 BGP a0ce.c8fb.4687 10.103.120.14 V:200120 10.103.255.12
1 0 BGP a0ce.c8fb.47b7 10.103.120.13 V:200120 10.103.255.12
1 0 BGP a0ce.c8fb.47dc 10.103.120.11 V:200120 10.103.255.12
1 0 BGP c414.a202.89a0 10.103.64.19 V:200001 10.103.255.11
1 0 BGP c4d6.664f.55b0 10.103.64.17 V:200001 10.103.255.12
1 0 BGP c4d6.666d.0f80 10.103.64.28 V:200001 10.103.255.14
1 0 BGP c4d6.666d.2e10 10.103.64.14 V:200001 10.103.255.12
1 0 L2VPN c4d6.66d9.3140 10.103.64.20 Gi1/0/48:1
120 0 BGP a0ce.c8fb.4677 10.103.120.15 V:200120 10.103.255.14
120 0 BGP a0ce.c8fb.467f 10.103.120.12 V:200120 10.103.255.11
120 0 BGP a0ce.c8fb.4687 10.103.120.14 V:200120 10.103.255.12
120 0 L2VPN a0ce.c8fb.4689 10.103.120.23 Gi1/0/13:120
120 0 L2VPN a0ce.c8fb.47a7 10.103.120.16 Gi1/0/12:120
120 0 BGP a0ce.c8fb.47b7 10.103.120.13 V:200120 10.103.255.12
120 0 BGP a0ce.c8fb.47dc 10.103.120.11 V:200120 10.103.255.12
NYC103-Leaf-03#show ip bgp vpnv4 vrf campus
BGP table version is 124, local router ID is 10.103.255.13
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:13 (default for vrf campus)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 3/1000
* i 0.0.0.0 10.103.255.4 0 100 0 65102 65100 65101 ?
*>i 10.103.255.3 0 100 0 65102 65100 65101 ?
* i 10.103.64.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
*> 0.0.0.0 0 32768 ?
*>i 10.103.64.0/18 10.103.255.3 0 100 0 i
* i 10.103.255.4 0 100 0 i
*>i 10.103.64.11/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.12/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.13/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.14/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.15/32 10.103.255.11 0 100 0 ?
*>i 10.103.64.17/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.19/32 10.103.255.11 0 100 0 ?
*>i 10.103.64.26/32 10.103.255.14 0 100 0 ?
*>i 10.103.64.28/32 10.103.255.14 0 100 0 ?
* i 10.103.120.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
*> 0.0.0.0 0 32768 ?
*>i 10.103.120.11/32 10.103.255.12 0 100 0 ?
*>i 10.103.120.12/32 10.103.255.11 0 100 0 ?
*>i 10.103.120.13/32 10.103.255.12 0 100 0 ?
*>i 10.103.120.14/32 10.103.255.12 0 100 0 ?
*>i 10.103.120.15/32 10.103.255.14 0 100 0 ?
*>i 10.103.128.0/18 10.103.255.3 0 100 0 i
* i 10.103.255.4 0 100 0 i
* i 10.103.180.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
*> 0.0.0.0 0 32768 ?
NYC103-Leaf-03#show ip bgp vpnv4 vrf campus 0.0.0.0/0
BGP routing table entry for 65106:13:0.0.0.0/0, version 25
Paths: (2 available, best #2, table campus)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101, imported path from [5][65106:4][0][0][0.0.0.0]/17 (global)
10.103.255.4 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
Originator: 10.103.255.4, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:campus, vni:303001
local router mac:246C.847E.B272
encap:1
vtep-ip:10.103.255.13
bdi:Vlan3001
Remote VxLAN:
Topoid 0x2(vrf campus)
Remote Router MAC:3488.1824.7672
Encap 8
Egress VNI 303001
RTEP 10.103.255.4
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65101, imported path from [5][65106:3][0][0][0.0.0.0]/17 (global)
10.103.255.3 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:campus, vni:303001
local router mac:246C.847E.B272
encap:1
vtep-ip:10.103.255.13
bdi:Vlan3001
Remote VxLAN:
Topoid 0x2(vrf campus)
Remote Router MAC:246C.847E.E0F2
Encap 8
Egress VNI 303001
RTEP 10.103.255.3
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
NYC103-Leaf-03#show ip route vrf campus
Routing Table: campus
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.255.3 to network 0.0.0.0
B* 0.0.0.0/0 [200/0] via 10.103.255.3, 1w2d, Vlan3001
10.0.0.0/8 is variably subnetted, 25 subnets, 3 masks
B 10.103.64.0/18 [200/0] via 10.103.255.3, 1w2d, Vlan3001
C 10.103.64.0/24 is directly connected, Vlan1
L 10.103.64.1/32 is directly connected, Vlan1
B 10.103.64.11/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.12/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.13/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.14/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.15/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
B 10.103.64.17/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.19/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
S 10.103.64.20/32 is directly connected, Vlan1
B 10.103.64.26/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
B 10.103.64.28/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
C 10.103.120.0/24 is directly connected, Vlan120
L 10.103.120.1/32 is directly connected, Vlan120
B 10.103.120.11/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.12/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
B 10.103.120.13/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.14/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.15/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
S 10.103.120.16/32 is directly connected, Vlan120
S 10.103.120.23/32 is directly connected, Vlan120
B 10.103.128.0/18 [200/0] via 10.103.255.3, 1w2d, Vlan3001
C 10.103.180.0/24 is directly connected, Vlan180
L 10.103.180.1/32 is directly connected, Vlan180
NYC103-Leaf-03#show ip bgp vpnv4 vrf guest
BGP table version is 124, local router ID is 10.103.255.13
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:213 (default for vrf guest)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 1/1000
* i 0.0.0.0 10.103.255.4 0 100 0 65102 65100 65100 65100 65100 i
*>i 10.103.255.3 0 100 0 65102 65100 65100 65100 65100 i
*>i 10.103.64.8/30 10.103.255.3 0 100 0 i
*>i 10.103.64.12/30 10.103.255.4 0 100 0 i
* i 10.103.220.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
*> 0.0.0.0 0 32768 ?
NYC103-Leaf-03#show ip bgp vpnv4 vrf guest 0.0.0.0/0
BGP routing table entry for 65106:213:0.0.0.0/0, version 27
Paths: (2 available, best #2, table guest)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65100 65100 65100, imported path from [5][65106:24][0][0][0.0.0.0]/17 (global)
10.103.255.4 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal
Extended Community: RT:65106:2 ENCAP:8 Router MAC:3488.1824.764B
Originator: 10.103.255.4, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:guest, vni:303002
local router mac:246C.847E.B24B
encap:1
vtep-ip:10.103.255.13
bdi:Vlan3002
Remote VxLAN:
Topoid 0x3(vrf guest)
Remote Router MAC:3488.1824.764B
Encap 8
Egress VNI 303002
RTEP 10.103.255.4
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65100 65100 65100, imported path from [5][65106:23][0][0][0.0.0.0]/17 (global)
10.103.255.3 (metric 103) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, best
Extended Community: RT:65106:2 ENCAP:8 Router MAC:246C.847E.E0CB
Originator: 10.103.255.3, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:guest, vni:303002
local router mac:246C.847E.B24B
encap:1
vtep-ip:10.103.255.13
bdi:Vlan3002
Remote VxLAN:
Topoid 0x3(vrf guest)
Remote Router MAC:246C.847E.E0CB
Encap 8
Egress VNI 303002
RTEP 10.103.255.3
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
NYC103-Leaf-03#show ip route vrf guest
Routing Table: guest
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.255.3 to network 0.0.0.0
B* 0.0.0.0/0 [200/0] via 10.103.255.3, 1w2d, Vlan3002
10.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
B 10.103.64.8/30 [200/0] via 10.103.255.3, 1w2d, Vlan3002
B 10.103.64.12/30 [200/0] via 10.103.255.4, 1w2d, Vlan3002
C 10.103.220.0/24 is directly connected, Vlan220
L 10.103.220.1/32 is directly connected, Vlan220
NYC103-Leaf-03#
NYC103-Leaf-04
NYC103-Leaf-04#show mac address-table dynamic
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 9433.d807.8517 DYNAMIC Po1
1 9433.d807.8518 DYNAMIC Po1
1 9433.d807.8547 DYNAMIC Po1
1 c4d6.666d.0f80 DYNAMIC Po1
120 a0ce.c8fb.4677 DYNAMIC Po1
Total Mac Addresses for this criterion: 5
NYC103-Leaf-04#show l2route evpn mac ip
EVI ETag Prod Mac Address Host IP Next Hop(s)
----- ---------- ----- -------------- --------------------------------------- --------------------------------------------------
1 0 BGP 8c44.a571.8300 10.103.64.15 V:200001 10.103.255.11
1 0 L2VPN 9433.d807.8547 10.103.64.26 Po1:1
1 0 BGP a0bc.6fd6.7b00 10.103.64.12 V:200001 10.103.255.12
1 0 BGP a0bc.6fe2.8b80 10.103.64.11 V:200001 10.103.255.12
1 0 BGP a0bc.6fe2.8f00 10.103.64.13 V:200001 10.103.255.12
1 0 BGP a0ce.c8fb.467f 10.103.120.12 V:200120 10.103.255.11
1 0 BGP a0ce.c8fb.4687 10.103.120.14 V:200120 10.103.255.12
1 0 BGP a0ce.c8fb.4689 10.103.120.23 V:200120 10.103.255.13
1 0 BGP a0ce.c8fb.47a7 10.103.120.16 V:200120 10.103.255.13
1 0 BGP a0ce.c8fb.47b7 10.103.120.13 V:200120 10.103.255.12
1 0 BGP a0ce.c8fb.47dc 10.103.120.11 V:200120 10.103.255.12
1 0 BGP c414.a202.89a0 10.103.64.19 V:200001 10.103.255.11
1 0 BGP c4d6.664f.55b0 10.103.64.17 V:200001 10.103.255.12
1 0 L2VPN c4d6.666d.0f80 10.103.64.28 Po1:1
1 0 BGP c4d6.666d.2e10 10.103.64.14 V:200001 10.103.255.12
1 0 BGP c4d6.66d9.3140 10.103.64.20 V:200001 10.103.255.13
120 0 L2VPN a0ce.c8fb.4677 10.103.120.15 Po1:120
120 0 BGP a0ce.c8fb.467f 10.103.120.12 V:200120 10.103.255.11
120 0 BGP a0ce.c8fb.4687 10.103.120.14 V:200120 10.103.255.12
120 0 BGP a0ce.c8fb.4689 10.103.120.23 V:200120 10.103.255.13
120 0 BGP a0ce.c8fb.47a7 10.103.120.16 V:200120 10.103.255.13
120 0 BGP a0ce.c8fb.47b7 10.103.120.13 V:200120 10.103.255.12
120 0 BGP a0ce.c8fb.47dc 10.103.120.11 V:200120 10.103.255.12
NYC103-Leaf-04#show ip bgp vpnv4 vrf campus
BGP table version is 68, local router ID is 10.103.255.14
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:14 (default for vrf campus)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 3/1000
* i 0.0.0.0 10.103.255.4 0 100 0 65102 65100 65101 ?
*>i 10.103.255.3 0 100 0 65102 65100 65101 ?
* i 10.103.64.0/24 10.103.255.13 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
*> 0.0.0.0 0 32768 ?
* i 10.103.64.0/18 10.103.255.4 0 100 0 i
*>i 10.103.255.3 0 100 0 i
*>i 10.103.64.11/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.12/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.13/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.14/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.15/32 10.103.255.11 0 100 0 ?
*>i 10.103.64.17/32 10.103.255.12 0 100 0 ?
*>i 10.103.64.19/32 10.103.255.11 0 100 0 ?
*>i 10.103.64.20/32 10.103.255.13 0 100 0 ?
* i 10.103.120.0/24 10.103.255.13 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
*> 0.0.0.0 0 32768 ?
*>i 10.103.120.11/32 10.103.255.12 0 100 0 ?
*>i 10.103.120.12/32 10.103.255.11 0 100 0 ?
*>i 10.103.120.13/32 10.103.255.12 0 100 0 ?
*>i 10.103.120.14/32 10.103.255.12 0 100 0 ?
*>i 10.103.120.16/32 10.103.255.13 0 100 0 ?
*>i 10.103.120.23/32 10.103.255.13 0 100 0 ?
* i 10.103.128.0/18 10.103.255.4 0 100 0 i
*>i 10.103.255.3 0 100 0 i
* i 10.103.180.0/24 10.103.255.13 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
*> 0.0.0.0 0 32768 ?
NYC103-Leaf-04#show ip bgp vpnv4 vrf campus 0.0.0.0/0
BGP routing table entry for 65106:14:0.0.0.0/0, version 23
Paths: (2 available, best #2, table campus)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65101, imported path from [5][65106:4][0][0][0.0.0.0]/17 (global)
10.103.255.4 (metric 7) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal
Extended Community: RT:65106:1 ENCAP:8 Router MAC:3488.1824.7672
Originator: 10.103.255.4, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:campus, vni:303001
local router mac:242A.0490.E772
encap:1
vtep-ip:10.103.255.14
bdi:Vlan3001
Remote VxLAN:
Topoid 0x2(vrf campus)
Remote Router MAC:3488.1824.7672
Encap 8
Egress VNI 303001
RTEP 10.103.255.4
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65101, imported path from [5][65106:3][0][0][0.0.0.0]/17 (global)
10.103.255.3 (metric 7) (via default) from 10.103.255.1 (10.103.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
Extended Community: RT:65106:1 ENCAP:8 Router MAC:246C.847E.E0F2
Originator: 10.103.255.3, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:campus, vni:303001
local router mac:242A.0490.E772
encap:1
vtep-ip:10.103.255.14
bdi:Vlan3001
Remote VxLAN:
Topoid 0x2(vrf campus)
Remote Router MAC:246C.847E.E0F2
Encap 8
Egress VNI 303001
RTEP 10.103.255.3
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
NYC103-Leaf-04#show ip route vrf campus
Routing Table: campus
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.255.3 to network 0.0.0.0
B* 0.0.0.0/0 [200/0] via 10.103.255.3, 1w2d, Vlan3001
10.0.0.0/8 is variably subnetted, 25 subnets, 3 masks
B 10.103.64.0/18 [200/0] via 10.103.255.3, 1w2d, Vlan3001
C 10.103.64.0/24 is directly connected, Vlan1
L 10.103.64.1/32 is directly connected, Vlan1
B 10.103.64.11/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.12/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.13/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.14/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.15/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
B 10.103.64.17/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.19/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
B 10.103.64.20/32 [200/0] via 10.103.255.13, 1w1d, Vlan3001
S 10.103.64.26/32 is directly connected, Vlan1
S 10.103.64.28/32 is directly connected, Vlan1
C 10.103.120.0/24 is directly connected, Vlan120
L 10.103.120.1/32 is directly connected, Vlan120
B 10.103.120.11/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.12/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
B 10.103.120.13/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.14/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
S 10.103.120.15/32 is directly connected, Vlan120
B 10.103.120.16/32 [200/0] via 10.103.255.13, 1w2d, Vlan3001
B 10.103.120.23/32 [200/0] via 10.103.255.13, 1w2d, Vlan3001
B 10.103.128.0/18 [200/0] via 10.103.255.3, 1w2d, Vlan3001
C 10.103.180.0/24 is directly connected, Vlan180
L 10.103.180.1/32 is directly connected, Vlan180
NYC103-Leaf-04#show ip bgp vpnv4 vrf guest
BGP table version is 68, local router ID is 10.103.255.14
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:214 (default for vrf guest)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 1/1000
* i 0.0.0.0 10.103.255.4 0 100 0 65102 65100 65100 65100 65100 i
*>i 10.103.255.3 0 100 0 65102 65100 65100 65100 65100 i
*>i 10.103.64.8/30 10.103.255.3 0 100 0 i
*>i 10.103.64.12/30 10.103.255.4 0 100 0 i
* i 10.103.220.0/24 10.103.255.13 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
*> 0.0.0.0 0 32768 ?
NYC103-Leaf-04#show ip bgp vpnv4 vrf guest 0.0.0.0/0
BGP routing table entry for 65106:214:0.0.0.0/0, version 25
Paths: (2 available, best #2, table guest)
Not advertised to any peer
Refresh Epoch 1
65102 65100 65100 65100 65100, imported path from [5][65106:24][0][0][0.0.0.0]/17 (global)
10.103.255.4 (metric 7) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal
Extended Community: RT:65106:2 ENCAP:8 Router MAC:3488.1824.764B
Originator: 10.103.255.4, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:guest, vni:303002
local router mac:242A.0490.E74B
encap:1
vtep-ip:10.103.255.14
bdi:Vlan3002
Remote VxLAN:
Topoid 0x3(vrf guest)
Remote Router MAC:3488.1824.764B
Encap 8
Egress VNI 303002
RTEP 10.103.255.4
rx pathid: 0, tx pathid: 0
Updated on Jul 7 2024 14:18:34 EDT
Refresh Epoch 1
65102 65100 65100 65100 65100, imported path from [5][65106:23][0][0][0.0.0.0]/17 (global)
10.103.255.3 (metric 7) (via default) from 10.103.255.1 (10.103.255.1)
Origin IGP, metric 0, localpref 100, valid, internal, best
Extended Community: RT:65106:2 ENCAP:8 Router MAC:246C.847E.E0CB
Originator: 10.103.255.3, Cluster list: 10.103.255.1
Local vxlan vtep:
vrf:guest, vni:303002
local router mac:242A.0490.E74B
encap:1
vtep-ip:10.103.255.14
bdi:Vlan3002
Remote VxLAN:
Topoid 0x3(vrf guest)
Remote Router MAC:246C.847E.E0CB
Encap 8
Egress VNI 303002
RTEP 10.103.255.3
rx pathid: 0, tx pathid: 0x0
Updated on Jul 7 2024 14:18:34 EDT
NYC103-Leaf-04#show ip route vrf guest
Routing Table: guest
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.255.3 to network 0.0.0.0
B* 0.0.0.0/0 [200/0] via 10.103.255.3, 1w2d, Vlan3002
10.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
B 10.103.64.8/30 [200/0] via 10.103.255.3, 1w2d, Vlan3002
B 10.103.64.12/30 [200/0] via 10.103.255.4, 1w2d, Vlan3002
C 10.103.220.0/24 is directly connected, Vlan220
L 10.103.220.1/32 is directly connected, Vlan220
NYC103-Leaf-04#
Border Switches (VLANs, VRFs, NVE1)
NYC103-Border-01
NYC103-Border-01#show vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Gi1/0/3, Gi1/0/4, Gi1/0/5, Gi1/0/6, Gi1/0/7, Gi1/0/8, Gi1/0/9, Gi1/0/10, Gi1/0/11, Gi1/0/12, Gi1/0/13, Gi1/0/14, Gi1/0/15, Gi1/0/16, Gi1/0/17, Gi1/0/18, Gi1/0/19, Gi1/0/20, Gi1/0/21, Gi1/0/22, Gi1/0/23, Gi1/0/24, Gi1/0/25
Gi1/0/26, Gi1/0/27, Gi1/0/28, Gi1/0/29, Gi1/0/30, Gi1/0/31, Gi1/0/32, Gi1/0/33, Gi1/0/34, Gi1/0/35, Gi1/0/36, Gi1/0/37, Gi1/0/38, Gi1/0/39, Gi1/0/40, Gi1/0/41, Gi1/0/42, Gi1/0/43, Gi1/0/44, Gi1/0/45, Gi1/0/46, Gi1/0/47
Gi1/0/48, Ap1/0/1
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
3001 Campus-VRF-L3VNI active
3002 Guest-VRF-L3VNI active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1 enet 100001 1500 - - - - - 0 0
1002 fddi 101002 1500 - - - - - 0 0
1003 tr 101003 1500 - - - - - 0 0
1004 fdnet 101004 1500 - - - ieee - 0 0
1005 trnet 101005 1500 - - - ibm - 0 0
3001 enet 103001 1500 - - - - - 0 0
3002 enet 103002 1500 - - - - - 0 0
Remote SPAN VLANs
------------------------------------------------------------------------------
Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
NYC103-Border-01#show vrf
Name Default RD Protocols Interfaces
Mgmt-vrf <not set> ipv4,ipv6 Gi0/0
campus 65106:3 ipv4 Gi1/0/2.3001
Vl3001
guest 65106:23 ipv4 Gi1/0/2.3002
Vl3002
NYC103-Border-01#
NYC103-Border-01#sh run int nve1
Building configuration...
Current configuration : 217 bytes
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 303001 vrf campus
member vni 303002 vrf guest
end
NYC103-Border-01#
NYC103-Border-02
NYC103-Border-02#show vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Gi1/0/3, Gi1/0/4, Gi1/0/5, Gi1/0/6, Gi1/0/7, Gi1/0/8, Gi1/0/9, Gi1/0/10, Gi1/0/11, Gi1/0/12, Gi1/0/13, Gi1/0/14, Gi1/0/15, Gi1/0/16, Gi1/0/17, Gi1/0/18, Gi1/0/19, Gi1/0/20, Gi1/0/21, Gi1/0/22, Gi1/0/23, Gi1/0/24, Gi1/0/25
Gi1/0/26, Gi1/0/27, Gi1/0/28, Gi1/0/29, Gi1/0/30, Gi1/0/31, Gi1/0/32, Gi1/0/33, Gi1/0/34, Gi1/0/35, Gi1/0/36, Gi1/0/37, Gi1/0/38, Gi1/0/39, Gi1/0/40, Gi1/0/41, Gi1/0/42, Gi1/0/43, Gi1/0/44, Gi1/0/45, Gi1/0/46, Gi1/0/47
Gi1/0/48, Ap1/0/1
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
3001 Campus-VRF-L3VNI active
3002 Guest-VRF-L3VNI active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1 enet 100001 1500 - - - - - 0 0
1002 fddi 101002 1500 - - - - - 0 0
1003 tr 101003 1500 - - - - - 0 0
1004 fdnet 101004 1500 - - - ieee - 0 0
1005 trnet 101005 1500 - - - ibm - 0 0
3001 enet 103001 1500 - - - - - 0 0
3002 enet 103002 1500 - - - - - 0 0
Remote SPAN VLANs
------------------------------------------------------------------------------
Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
NYC103-Border-02#show vrf
Name Default RD Protocols Interfaces
Mgmt-vrf <not set> ipv4,ipv6 Gi0/0
campus 65106:4 ipv4 Gi1/0/2.3001
Vl3001
guest 65106:24 ipv4 Gi1/0/2.3002
Vl3002
NYC103-Border-02#
NYC103-Border-02#sh run int nve1
Building configuration...
Current configuration : 217 bytes
!
interface nve1
description Network Virtualization Endpoint for encap-decap
no ip address
source-interface Loopback0
host-reachability protocol bgp
member vni 303001 vrf campus
member vni 303002 vrf guest
end
NYC103-Border-02#
Border Switches (BGP GRT, VPNV4)
NYC103-Border-01
NYC103-Border-01#show ip bgp summary
BGP router identifier 10.103.255.3, local AS number 65106
BGP table version is 8, main routing table version 8
5 network entries using 1240 bytes of memory
5 path entries using 680 bytes of memory
3/3 BGP path/bestpath attribute entries using 888 bytes of memory
10 BGP rrinfo entries using 400 bytes of memory
3 BGP AS-PATH entries using 104 bytes of memory
18 BGP extended community entries using 768 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 4080 total bytes of memory
BGP activity 138/62 prefixes, 280/150 paths, scan interval 60 secs
5 networks peaked at 14:07:09 Jul 7 2024 EDT (1w2d ago)
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.103.224.1 4 65100 14658 14651 8 0 0 1w2d 1
NYC103-Border-01#show ip bgp neighbors
BGP neighbor is 10.103.224.1, remote AS 65100, external link
Fall over configured for session
BFD is configured. BFD peer is Up. Using BFD to detect fast fallover (single-hop).
BGP version 4, remote router ID 10.100.255.11
BGP state = Established, up for 1w2d
Last read 00:00:14, last write 00:00:45, hold time is 180, keepalive interval is 60 seconds
Last update received: 1w2d
Neighbor sessions:
1 active, is not multisession capable (disabled)
Neighbor capabilities:
Route refresh: advertised and received(new)
Four-octets ASN Capability: advertised and received
Address family IPv4 Unicast: advertised and received
Enhanced Refresh Capability: advertised and received
Multisession Capability:
Stateful switchover support enabled: NO for session 1
Message statistics:
InQ depth is 0
OutQ depth is 0
Sent Rcvd
Opens: 1 1
Notifications: 0 0
Updates: 2 2
Keepalives: 14648 14655
Route Refresh: 0 0
Total: 14651 14658
Do log neighbor state changes (via global configuration)
Default minimum time between advertisement runs is 30 seconds
For address family: IPv4 Unicast
Session: 10.103.224.1
BGP table version 8, neighbor version 8/0
Output queue size : 0
Index 1, Advertise bit 0
1 update-group member
Inbound path policy configured
Outbound path policy configured
Route map for incoming advertisements is bgp-underlay-in-from-core
Route map for outgoing advertisements is bgp-underlay-out-to-core
Slow-peer detection is disabled
Slow-peer split-update-group dynamic is disabled
Sent Rcvd
Prefix activity: ---- ----
Prefixes Current: 2 1 (Consumes 136 bytes)
Prefixes Total: 2 1
Implicit Withdraw: 0 0
Explicit Withdraw: 0 0
Used as bestpath: n/a 1
Used as multipath: n/a 0
Used as secondary: n/a 0
Outbound Inbound
Local Policy Denied Prefixes: -------- -------
Suppressed due to dampening: 2 n/a
Other Policies: 1 n/a
Total: 3 0
Number of NLRIs in the update sent: max 2, min 0
Current session network count peaked at 1 entries at 14:07:09 Jul 7 2024 EDT (1w2d ago)
Highest network count observed at 1 entries at 14:07:09 Jul 7 2024 EDT (1w2d ago)
Last detected as dynamic slow peer: never
Dynamic slow peer recovered: never
Refresh Epoch: 1
Last Sent Refresh Start-of-rib: never
Last Sent Refresh End-of-rib: never
Last Received Refresh Start-of-rib: never
Last Received Refresh End-of-rib: never
Sent Rcvd
Refresh activity: ---- ----
Refresh Start-of-RIB 0 0
Refresh End-of-RIB 0 0
Address tracking is enabled, the RIB does have a route to 10.103.224.1
NYC103-Border-01#
NYC103-Border-01#show ip bgp neighbor 10.103.224.1 advertised-routes
BGP table version is 8, local router ID is 10.103.255.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 10.103.224.0/24 0.0.0.0 32768 i
*> 10.103.255.0/24 0.0.0.0 32768 i
Total number of prefixes 2
NYC103-Border-01#show ip bgp neighbor 10.103.224.1 routes
BGP table version is 8, local router ID is 10.103.255.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 0.0.0.0 10.103.224.1 0 65100 i
Total number of prefixes 1
NYC103-Border-01#show ip bgp
BGP table version is 8, local router ID is 10.103.255.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 0.0.0.0 10.103.224.1 0 65100 i
s> 10.103.224.0/30 0.0.0.0 0 32768 i
*> 10.103.224.0/24 0.0.0.0 32768 i
*> 10.103.255.0/24 0.0.0.0 32768 i
s> 10.103.255.3/32 0.0.0.0 0 32768 i
NYC103-Border-01#show ip route bgp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.224.1 to network 0.0.0.0
B* 0.0.0.0/0 [20/0] via 10.103.224.1, 1w2d
10.0.0.0/8 is variably subnetted, 31 subnets, 3 masks
B 10.103.224.0/24 [200/0], 1w2d, Null0
B 10.103.255.0/24 [200/0], 1w2d, Null0
NYC103-Border-01#show ip bgp vpnv4 vrf campus
BGP table version is 195, local router ID is 10.103.255.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:3 (default for vrf campus)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 3/1000
* i 0.0.0.0 10.103.255.4 0 100 0 65102 65100 65101 ?
*> 10.103.64.1 0 65102 65100 65101 ?
s> 10.103.64.0/30 0.0.0.0 0 32768 i
s>i 10.103.64.0/24 10.103.255.14 0 100 0 ?
s i 10.103.255.11 0 100 0 ?
s i 10.103.255.13 0 100 0 ?
s i 10.103.255.12 0 100 0 ?
* i 10.103.64.0/18 10.103.255.4 0 100 0 i
*> 0.0.0.0 32768 i
s>i 10.103.64.11/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.12/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.13/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.14/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.15/32 10.103.255.11 0 100 0 ?
s>i 10.103.64.17/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.19/32 10.103.255.11 0 100 0 ?
s>i 10.103.64.20/32 10.103.255.13 0 100 0 ?
s>i 10.103.64.26/32 10.103.255.14 0 100 0 ?
s>i 10.103.64.28/32 10.103.255.14 0 100 0 ?
s>i 10.103.120.0/24 10.103.255.14 0 100 0 ?
s i 10.103.255.11 0 100 0 ?
s i 10.103.255.13 0 100 0 ?
s i 10.103.255.12 0 100 0 ?
s>i 10.103.120.11/32 10.103.255.12 0 100 0 ?
s>i 10.103.120.12/32 10.103.255.11 0 100 0 ?
s>i 10.103.120.13/32 10.103.255.12 0 100 0 ?
s>i 10.103.120.14/32 10.103.255.12 0 100 0 ?
s>i 10.103.120.15/32 10.103.255.14 0 100 0 ?
s>i 10.103.120.16/32 10.103.255.13 0 100 0 ?
s>i 10.103.120.23/32 10.103.255.13 0 100 0 ?
* i 10.103.128.0/18 10.103.255.4 0 100 0 i
*> 0.0.0.0 32768 i
s>i 10.103.180.0/24 10.103.255.14 0 100 0 ?
s i 10.103.255.11 0 100 0 ?
s i 10.103.255.13 0 100 0 ?
s i 10.103.255.12 0 100 0 ?
NYC103-Border-01#show ip bgp vpnv4 vrf campus
BGP table version is 195, local router ID is 10.103.255.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:3 (default for vrf campus)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 3/1000
* i 0.0.0.0 10.103.255.4 0 100 0 65102 65100 65101 ?
*> 10.103.64.1 0 65102 65100 65101 ?
s> 10.103.64.0/30 0.0.0.0 0 32768 i
s>i 10.103.64.0/24 10.103.255.14 0 100 0 ?
s i 10.103.255.11 0 100 0 ?
s i 10.103.255.13 0 100 0 ?
s i 10.103.255.12 0 100 0 ?
* i 10.103.64.0/18 10.103.255.4 0 100 0 i
*> 0.0.0.0 32768 i
s>i 10.103.64.11/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.12/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.13/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.14/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.15/32 10.103.255.11 0 100 0 ?
s>i 10.103.64.17/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.19/32 10.103.255.11 0 100 0 ?
s>i 10.103.64.20/32 10.103.255.13 0 100 0 ?
s>i 10.103.64.26/32 10.103.255.14 0 100 0 ?
s>i 10.103.64.28/32 10.103.255.14 0 100 0 ?
s>i 10.103.120.0/24 10.103.255.14 0 100 0 ?
s i 10.103.255.11 0 100 0 ?
s i 10.103.255.13 0 100 0 ?
s i 10.103.255.12 0 100 0 ?
s>i 10.103.120.11/32 10.103.255.12 0 100 0 ?
s>i 10.103.120.12/32 10.103.255.11 0 100 0 ?
s>i 10.103.120.13/32 10.103.255.12 0 100 0 ?
s>i 10.103.120.14/32 10.103.255.12 0 100 0 ?
s>i 10.103.120.15/32 10.103.255.14 0 100 0 ?
s>i 10.103.120.16/32 10.103.255.13 0 100 0 ?
s>i 10.103.120.23/32 10.103.255.13 0 100 0 ?
* i 10.103.128.0/18 10.103.255.4 0 100 0 i
*> 0.0.0.0 32768 i
s>i 10.103.180.0/24 10.103.255.14 0 100 0 ?
s i 10.103.255.11 0 100 0 ?
s i 10.103.255.13 0 100 0 ?
s i 10.103.255.12 0 100 0 ?
NYC103-Border-01#show ip route vrf campus
Routing Table: campus
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.64.1 to network 0.0.0.0
B* 0.0.0.0/0 [20/0] via 10.103.64.1, 1w2d
10.0.0.0/8 is variably subnetted, 24 subnets, 4 masks
B 10.103.64.0/18 [200/0], 1w2d, Null0
B 10.103.64.0/24 [200/0] via 10.103.255.14, 1w2d, Vlan3001
C 10.103.64.0/30 is directly connected, GigabitEthernet1/0/2.3001
L 10.103.64.2/32 is directly connected, GigabitEthernet1/0/2.3001
B 10.103.64.11/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.12/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.13/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.14/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.15/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
B 10.103.64.17/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.19/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
B 10.103.64.20/32 [200/0] via 10.103.255.13, 1w1d, Vlan3001
B 10.103.64.26/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
B 10.103.64.28/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
B 10.103.120.0/24 [200/0] via 10.103.255.14, 1w2d, Vlan3001
B 10.103.120.11/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.12/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
B 10.103.120.13/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.14/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.15/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
B 10.103.120.16/32 [200/0] via 10.103.255.13, 1w2d, Vlan3001
B 10.103.120.23/32 [200/0] via 10.103.255.13, 1w2d, Vlan3001
B 10.103.128.0/18 [200/0], 1w2d, Null0
B 10.103.180.0/24 [200/0] via 10.103.255.14, 1w2d, Vlan3001
NYC103-Border-01#show ip bgp vpnv4 vrf guest
BGP table version is 195, local router ID is 10.103.255.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:23 (default for vrf guest)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 2/1000
* i 0.0.0.0 10.103.255.4 0 100 0 65102 65100 65100 65100 65100 i
*> 10.103.64.9 0 65102 65100 65100 65100 65100 i
*> 10.103.64.8/30 0.0.0.0 0 32768 i
*>i 10.103.64.12/30 10.103.255.4 0 100 0 i
*>i 10.103.220.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
* i 10.103.255.13 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
NYC103-Border-01#show ip bgp vpnv4 vrf guest
BGP table version is 195, local router ID is 10.103.255.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:23 (default for vrf guest)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 2/1000
* i 0.0.0.0 10.103.255.4 0 100 0 65102 65100 65100 65100 65100 i
*> 10.103.64.9 0 65102 65100 65100 65100 65100 i
*> 10.103.64.8/30 0.0.0.0 0 32768 i
*>i 10.103.64.12/30 10.103.255.4 0 100 0 i
*>i 10.103.220.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
* i 10.103.255.13 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
NYC103-Border-01#show ip route vrf guest
Routing Table: guest
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.64.9 to network 0.0.0.0
B* 0.0.0.0/0 [20/0] via 10.103.64.9, 1w2d
10.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
C 10.103.64.8/30 is directly connected, GigabitEthernet1/0/2.3002
L 10.103.64.10/32 is directly connected, GigabitEthernet1/0/2.3002
B 10.103.64.12/30 [200/0] via 10.103.255.4, 1w2d, Vlan3002
B 10.103.220.0/24 [200/0] via 10.103.255.14, 1w2d, Vlan3002
NYC103-Border-01#
NYC103-Border-02
NYC103-Border-02#show ip bgp summary
BGP router identifier 10.103.255.4, local AS number 65106
BGP table version is 11, main routing table version 11
5 network entries using 1240 bytes of memory
5 path entries using 680 bytes of memory
3/3 BGP path/bestpath attribute entries using 888 bytes of memory
10 BGP rrinfo entries using 400 bytes of memory
3 BGP AS-PATH entries using 104 bytes of memory
18 BGP extended community entries using 768 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 4080 total bytes of memory
BGP activity 136/60 prefixes, 276/146 paths, scan interval 60 secs
5 networks peaked at 14:06:41 Jul 7 2024 EDT (1w2d ago)
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.103.224.5 4 65100 14661 14649 11 0 0 1w2d 1
NYC103-Border-02#show ip bgp neighbors
BGP neighbor is 10.103.224.5, remote AS 65100, external link
Fall over configured for session
BFD is configured. BFD peer is Up. Using BFD to detect fast fallover (single-hop).
BGP version 4, remote router ID 10.100.255.12
BGP state = Established, up for 1w2d
Last read 00:00:51, last write 00:00:00, hold time is 180, keepalive interval is 60 seconds
Last update received: 1w2d
Neighbor sessions:
1 active, is not multisession capable (disabled)
Neighbor capabilities:
Route refresh: advertised and received(new)
Four-octets ASN Capability: advertised and received
Address family IPv4 Unicast: advertised and received
Enhanced Refresh Capability: advertised and received
Multisession Capability:
Stateful switchover support enabled: NO for session 1
Message statistics:
InQ depth is 0
OutQ depth is 0
Sent Rcvd
Opens: 1 1
Notifications: 0 0
Updates: 2 2
Keepalives: 14646 14658
Route Refresh: 0 0
Total: 14649 14661
Do log neighbor state changes (via global configuration)
Default minimum time between advertisement runs is 30 seconds
For address family: IPv4 Unicast
Session: 10.103.224.5
BGP table version 11, neighbor version 11/0
Output queue size : 0
Index 1, Advertise bit 0
1 update-group member
Inbound path policy configured
Outbound path policy configured
Route map for incoming advertisements is bgp-underlay-in-from-core
Route map for outgoing advertisements is bgp-underlay-out-to-core
Slow-peer detection is disabled
Slow-peer split-update-group dynamic is disabled
Sent Rcvd
Prefix activity: ---- ----
Prefixes Current: 2 1 (Consumes 136 bytes)
Prefixes Total: 2 1
Implicit Withdraw: 0 0
Explicit Withdraw: 0 0
Used as bestpath: n/a 1
Used as multipath: n/a 0
Used as secondary: n/a 0
Outbound Inbound
Local Policy Denied Prefixes: -------- -------
Suppressed due to dampening: 2 n/a
Other Policies: 1 n/a
Total: 3 0
Number of NLRIs in the update sent: max 2, min 0
Current session network count peaked at 1 entries at 14:06:41 Jul 7 2024 EDT (1w2d ago)
Highest network count observed at 1 entries at 14:06:41 Jul 7 2024 EDT (1w2d ago)
Last detected as dynamic slow peer: never
Dynamic slow peer recovered: never
Refresh Epoch: 1
Last Sent Refresh Start-of-rib: never
Last Sent Refresh End-of-rib: never
Last Received Refresh Start-of-rib: never
Last Received Refresh End-of-rib: never
Sent Rcvd
Refresh activity: ---- ----
Refresh Start-of-RIB 0 0
Refresh End-of-RIB 0 0
Address tracking is enabled, the RIB does have a route to 10.103.224.5
NYC103-Border-02#
NYC103-Border-02#show ip bgp
BGP table version is 11, local router ID is 10.103.255.4
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 0.0.0.0 10.103.224.5 0 65100 i
*> 10.103.224.0/24 0.0.0.0 32768 i
s> 10.103.224.4/30 0.0.0.0 0 32768 i
*> 10.103.255.0/24 0.0.0.0 32768 i
s> 10.103.255.4/32 0.0.0.0 0 32768 i
NYC103-Border-02#show ip route bgp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.224.5 to network 0.0.0.0
B* 0.0.0.0/0 [20/0] via 10.103.224.5, 1w2d
10.0.0.0/8 is variably subnetted, 31 subnets, 3 masks
B 10.103.224.0/24 [200/0], 1w2d, Null0
B 10.103.255.0/24 [200/0], 1w2d, Null0
NYC103-Border-02#show ip bgp vpnv4 vrf campus
BGP table version is 191, local router ID is 10.103.255.4
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:4 (default for vrf campus)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 3/1000
* i 0.0.0.0 10.103.255.3 0 100 0 65102 65100 65101 ?
*> 10.103.64.5 0 65102 65100 65101 ?
s>i 10.103.64.0/24 10.103.255.14 0 100 0 ?
s i 10.103.255.11 0 100 0 ?
s i 10.103.255.13 0 100 0 ?
s i 10.103.255.12 0 100 0 ?
* i 10.103.64.0/18 10.103.255.3 0 100 0 i
*> 0.0.0.0 32768 i
s> 10.103.64.4/30 0.0.0.0 0 32768 i
s>i 10.103.64.11/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.12/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.13/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.14/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.15/32 10.103.255.11 0 100 0 ?
s>i 10.103.64.17/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.19/32 10.103.255.11 0 100 0 ?
s>i 10.103.64.20/32 10.103.255.13 0 100 0 ?
s>i 10.103.64.26/32 10.103.255.14 0 100 0 ?
s>i 10.103.64.28/32 10.103.255.14 0 100 0 ?
s>i 10.103.120.0/24 10.103.255.14 0 100 0 ?
s i 10.103.255.11 0 100 0 ?
s i 10.103.255.13 0 100 0 ?
s i 10.103.255.12 0 100 0 ?
s>i 10.103.120.11/32 10.103.255.12 0 100 0 ?
s>i 10.103.120.12/32 10.103.255.11 0 100 0 ?
s>i 10.103.120.13/32 10.103.255.12 0 100 0 ?
s>i 10.103.120.14/32 10.103.255.12 0 100 0 ?
s>i 10.103.120.15/32 10.103.255.14 0 100 0 ?
s>i 10.103.120.16/32 10.103.255.13 0 100 0 ?
s>i 10.103.120.23/32 10.103.255.13 0 100 0 ?
* i 10.103.128.0/18 10.103.255.3 0 100 0 i
*> 0.0.0.0 32768 i
s>i 10.103.180.0/24 10.103.255.14 0 100 0 ?
s i 10.103.255.11 0 100 0 ?
s i 10.103.255.13 0 100 0 ?
s i 10.103.255.12 0 100 0 ?
NYC103-Border-02#show ip bgp vpnv4 vrf campus
BGP table version is 191, local router ID is 10.103.255.4
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:4 (default for vrf campus)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 3/1000
* i 0.0.0.0 10.103.255.3 0 100 0 65102 65100 65101 ?
*> 10.103.64.5 0 65102 65100 65101 ?
s>i 10.103.64.0/24 10.103.255.14 0 100 0 ?
s i 10.103.255.11 0 100 0 ?
s i 10.103.255.13 0 100 0 ?
s i 10.103.255.12 0 100 0 ?
* i 10.103.64.0/18 10.103.255.3 0 100 0 i
*> 0.0.0.0 32768 i
s> 10.103.64.4/30 0.0.0.0 0 32768 i
s>i 10.103.64.11/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.12/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.13/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.14/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.15/32 10.103.255.11 0 100 0 ?
s>i 10.103.64.17/32 10.103.255.12 0 100 0 ?
s>i 10.103.64.19/32 10.103.255.11 0 100 0 ?
s>i 10.103.64.20/32 10.103.255.13 0 100 0 ?
s>i 10.103.64.26/32 10.103.255.14 0 100 0 ?
s>i 10.103.64.28/32 10.103.255.14 0 100 0 ?
s>i 10.103.120.0/24 10.103.255.14 0 100 0 ?
s i 10.103.255.11 0 100 0 ?
s i 10.103.255.13 0 100 0 ?
s i 10.103.255.12 0 100 0 ?
s>i 10.103.120.11/32 10.103.255.12 0 100 0 ?
s>i 10.103.120.12/32 10.103.255.11 0 100 0 ?
s>i 10.103.120.13/32 10.103.255.12 0 100 0 ?
s>i 10.103.120.14/32 10.103.255.12 0 100 0 ?
s>i 10.103.120.15/32 10.103.255.14 0 100 0 ?
s>i 10.103.120.16/32 10.103.255.13 0 100 0 ?
s>i 10.103.120.23/32 10.103.255.13 0 100 0 ?
* i 10.103.128.0/18 10.103.255.3 0 100 0 i
*> 0.0.0.0 32768 i
s>i 10.103.180.0/24 10.103.255.14 0 100 0 ?
s i 10.103.255.11 0 100 0 ?
s i 10.103.255.13 0 100 0 ?
s i 10.103.255.12 0 100 0 ?
NYC103-Border-02#show ip route vrf campus
Routing Table: campus
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.64.5 to network 0.0.0.0
B* 0.0.0.0/0 [20/0] via 10.103.64.5, 1w2d
10.0.0.0/8 is variably subnetted, 24 subnets, 4 masks
B 10.103.64.0/18 [200/0], 1w2d, Null0
B 10.103.64.0/24 [200/0] via 10.103.255.14, 1w2d, Vlan3001
C 10.103.64.4/30 is directly connected, GigabitEthernet1/0/2.3001
L 10.103.64.6/32 is directly connected, GigabitEthernet1/0/2.3001
B 10.103.64.11/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.12/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.13/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.14/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.15/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
B 10.103.64.17/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.64.19/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
B 10.103.64.20/32 [200/0] via 10.103.255.13, 1w1d, Vlan3001
B 10.103.64.26/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
B 10.103.64.28/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
B 10.103.120.0/24 [200/0] via 10.103.255.14, 1w2d, Vlan3001
B 10.103.120.11/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.12/32 [200/0] via 10.103.255.11, 1w2d, Vlan3001
B 10.103.120.13/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.14/32 [200/0] via 10.103.255.12, 1w2d, Vlan3001
B 10.103.120.15/32 [200/0] via 10.103.255.14, 4d10h, Vlan3001
B 10.103.120.16/32 [200/0] via 10.103.255.13, 1w2d, Vlan3001
B 10.103.120.23/32 [200/0] via 10.103.255.13, 1w2d, Vlan3001
B 10.103.128.0/18 [200/0], 1w2d, Null0
B 10.103.180.0/24 [200/0] via 10.103.255.14, 1w2d, Vlan3001
NYC103-Border-02#show ip bgp vpnv4 vrf guest
BGP table version is 191, local router ID is 10.103.255.4
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:24 (default for vrf guest)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 2/1000
* i 0.0.0.0 10.103.255.3 0 100 0 65102 65100 65100 65100 65100 i
*> 10.103.64.13 0 65102 65100 65100 65100 65100 i
*>i 10.103.64.8/30 10.103.255.3 0 100 0 i
*> 10.103.64.12/30 0.0.0.0 0 32768 i
*>i 10.103.220.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
* i 10.103.255.13 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
NYC103-Border-02#show ip bgp vpnv4 vrf guest
BGP table version is 191, local router ID is 10.103.255.4
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path, L long-lived-stale,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65106:24 (default for vrf guest)
AF-Private Import to Address-Family: L2VPN E-VPN, Pfx Count/Limit: 2/1000
* i 0.0.0.0 10.103.255.3 0 100 0 65102 65100 65100 65100 65100 i
*> 10.103.64.13 0 65102 65100 65100 65100 65100 i
*>i 10.103.64.8/30 10.103.255.3 0 100 0 i
*> 10.103.64.12/30 0.0.0.0 0 32768 i
*>i 10.103.220.0/24 10.103.255.14 0 100 0 ?
* i 10.103.255.11 0 100 0 ?
* i 10.103.255.13 0 100 0 ?
* i 10.103.255.12 0 100 0 ?
NYC103-Border-02#show ip route vrf guest
Routing Table: guest
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.103.64.13 to network 0.0.0.0
B* 0.0.0.0/0 [20/0] via 10.103.64.13, 1w2d
10.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
B 10.103.64.8/30 [200/0] via 10.103.255.3, 1w2d, Vlan3002
C 10.103.64.12/30 is directly connected, GigabitEthernet1/0/2.3002
L 10.103.64.14/32 is directly connected, GigabitEthernet1/0/2.3002
B 10.103.220.0/24 [200/0] via 10.103.255.14, 1w2d, Vlan3002
NYC103-Border-02#
Cloud Monitoring for Catalyst Switches
Navigate to Switching > Switches then check the status of Cloud Campus Fabric switches.
Note: Cloud Monitored Switches will be shown with a Monitor Only identifier.
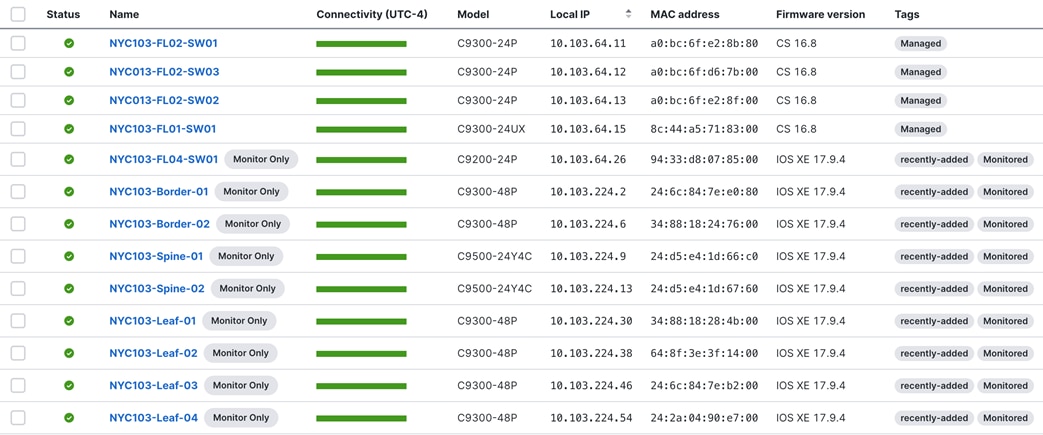
Cloud Monitoring for Catalyst Wireless Access Points
Navigate to Wireless > Access points then check the status of Cloud Campus Fabric Access Points and Wireless LAN Controllers from Wireless > Wireless LAN Controllers.
Note: You might need to navigate to a different Dashboard Network in case that monitored Switches and Access Points are not part of the same Dashboard Network.
Cloud Management for Catalyst Switches
Navigate to Switching > Switches then click on the desired switch. Check the status of Cloud Managed Access switches.
NYC103-FL01-SW01
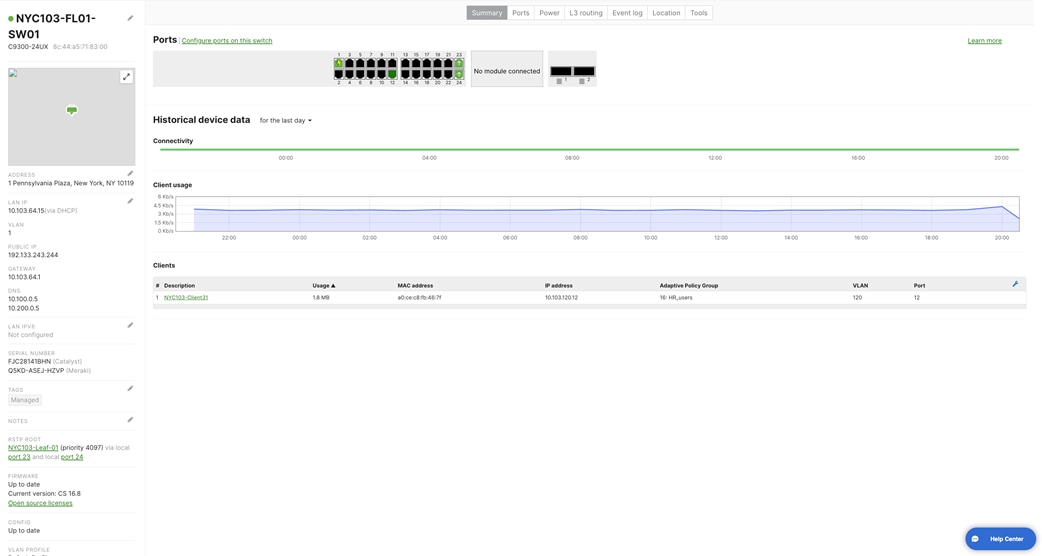
NYC103-FL02-SW01
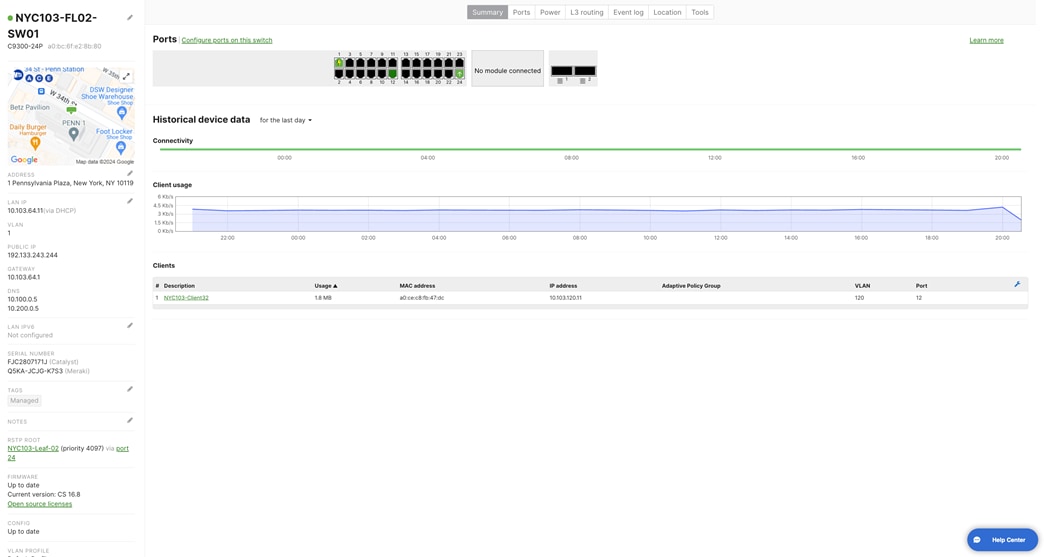
NYC103-FL02-SW02
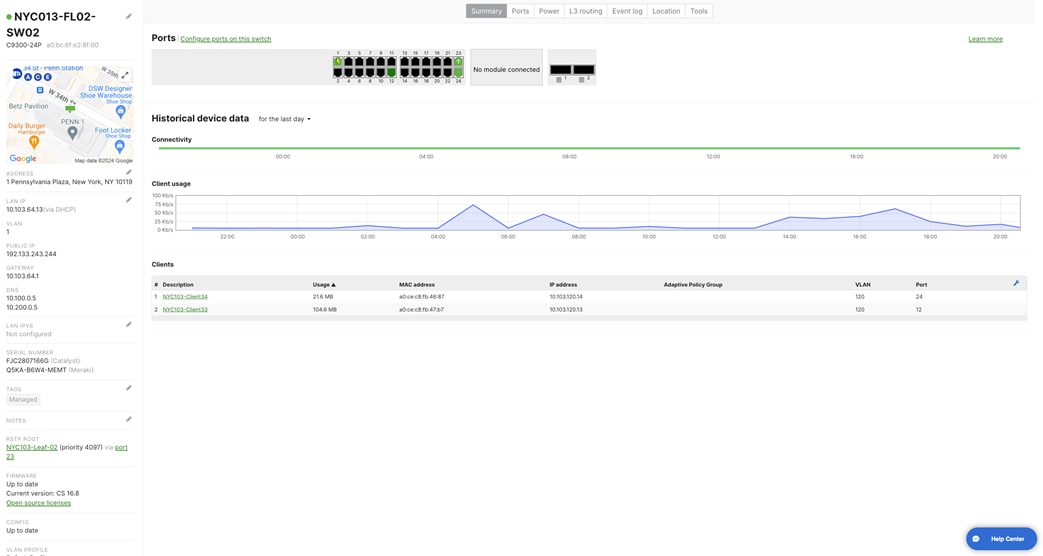
NYC103-FL02-SW03
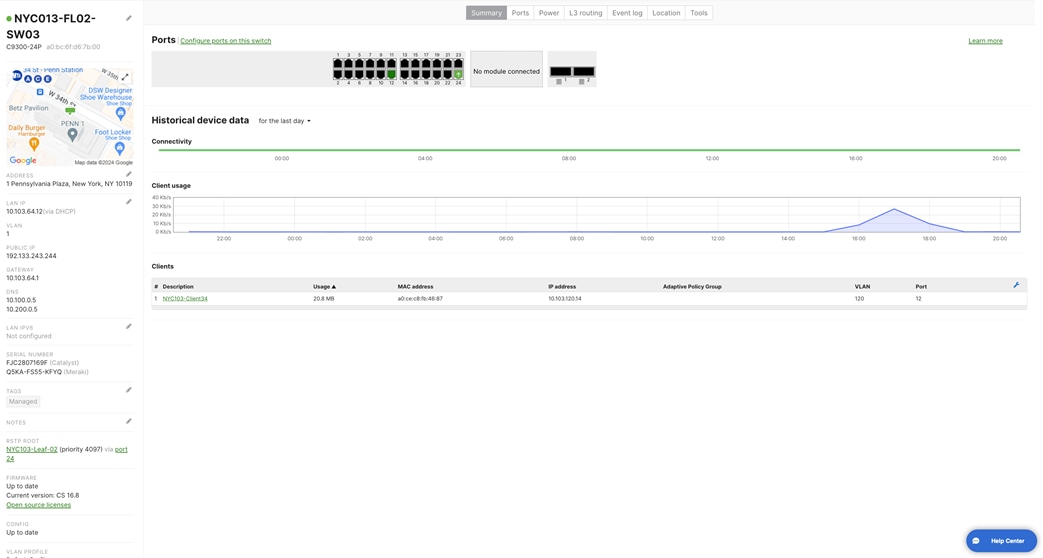
Cloud Managed for Catalyst Wireless Access Points
NYC103-FL01-AP01
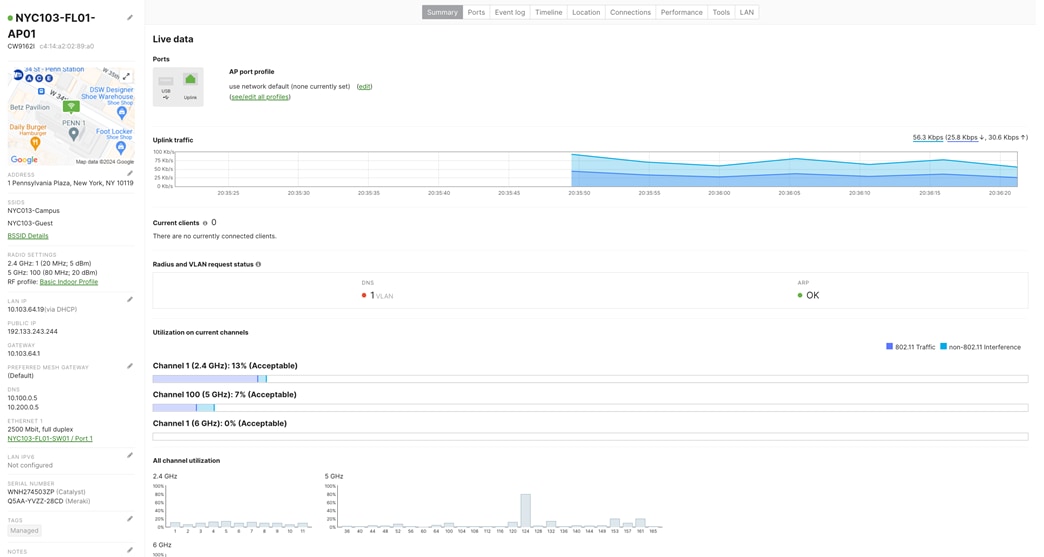
NYC103-FL02-AP01
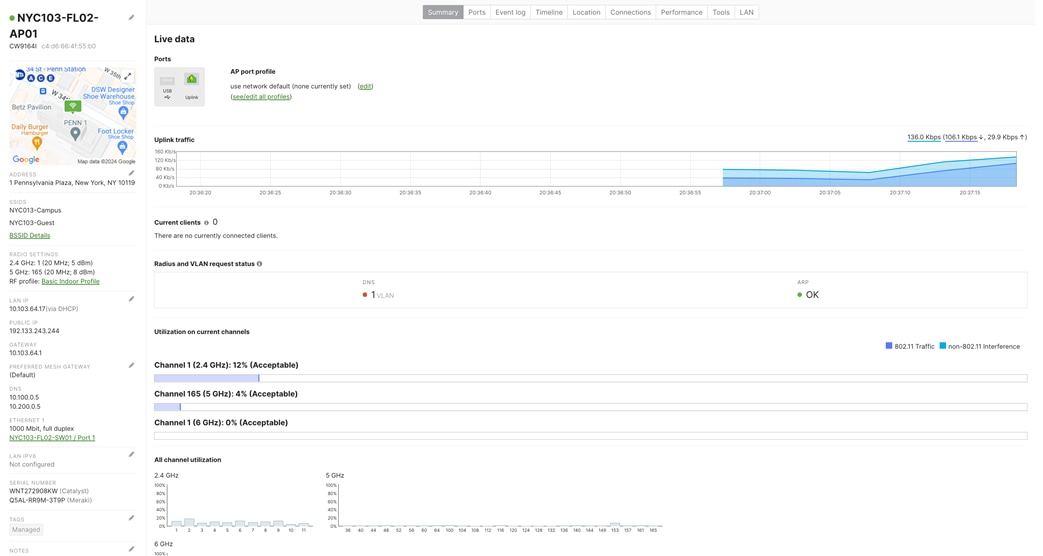
NYC103-FL02-AP02
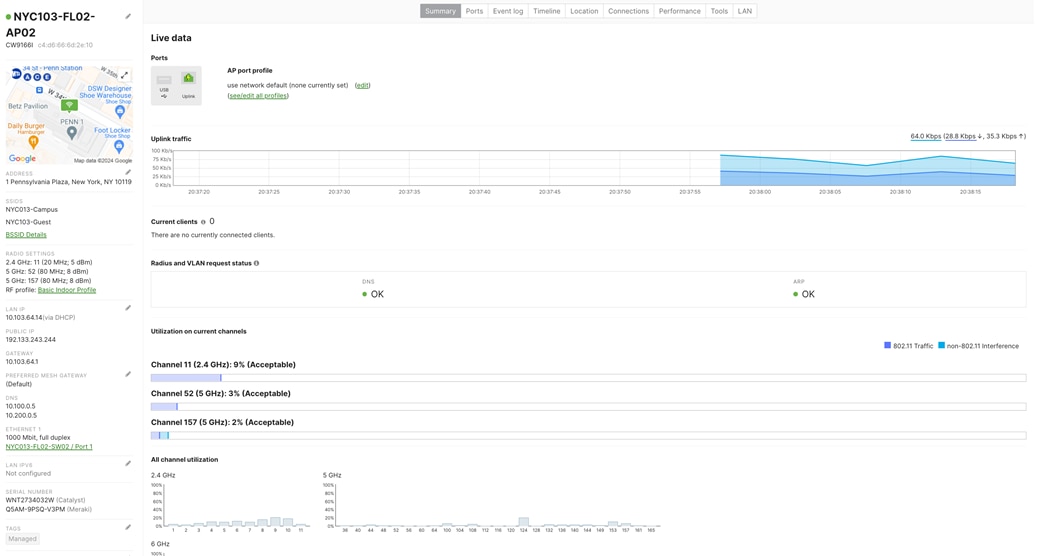
NYC103-FL03-AP04
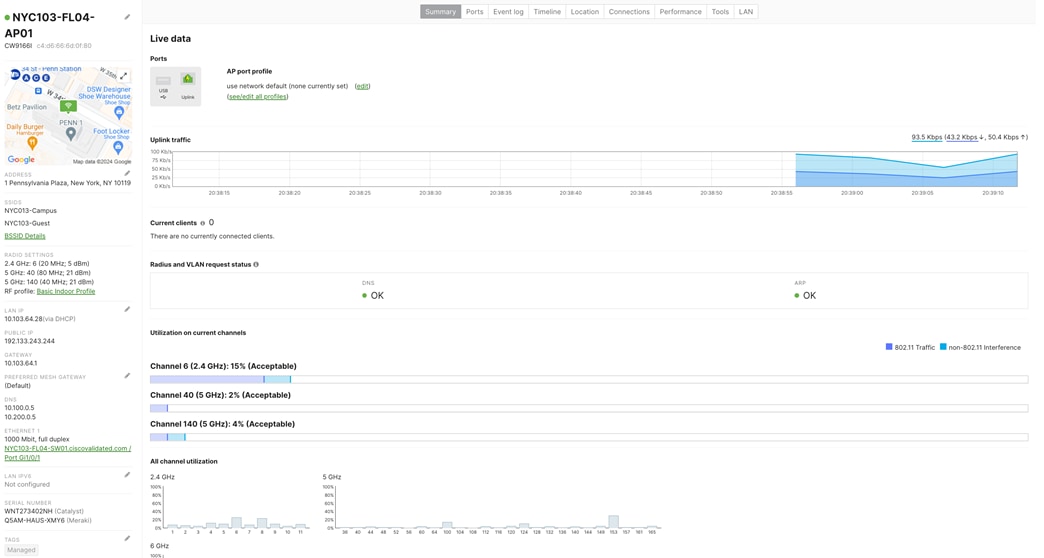
Adaptive Policy
All Access Switches / Access Points
You can verify the Adaptive Policy settings and enforcement by checking the network clients. Navigate to Network-wide > Clients then check the VLAN and Adaptive policy group assigned to client(s).
Tech tip: You can filter for clients connected to a specific device (e.g. Access switch) by clicking on the search field then selecting the device desired (e.g. NYC103-FL01-SW01)
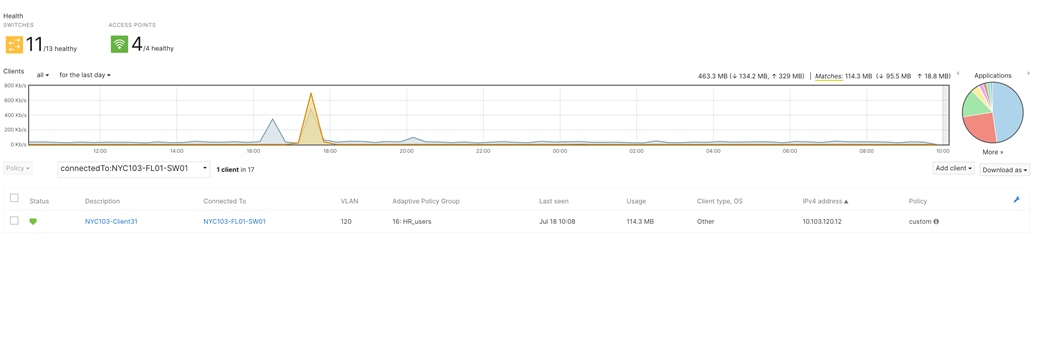
Note: Please refer to Cisco ISE logs for details on the Policy group applied to this specific user.
Note: You can change the view in Dashboard by clicking on the wrench icon on the right-hand side and selecting the columns you want to view. You can also change the order by dragging the columns to the desired position.
 P10
P10
 Feedback
Feedback