About MITRE Framework
The MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) Framework is an extensive knowledge base and methodology that provides insights into the tactics, techniques, and procedures (TTPs) distributed by threat actors aiming to harm systems. ATT&CK is compiled into matrices that each represent operating systems or a particular platform. Each stage of an attack, which is known as "tactics", is mapped to the specific methods used to achieve those stages, which are known as "techniques."
 Note |
See https://attack.mitre.org for information about MITRE. |
Each technique in the ATT&CK framework is accompanied with information about the technique, associated procedures, probable defenses and detections, and real-world examples. The MITRE ATT&CK framework also incorporates groups to refer to threat groups, activity groups, or threat actors based on the set of tactics and techniques they employ. Usage of groups in the framework helps categorize and document behaviors.
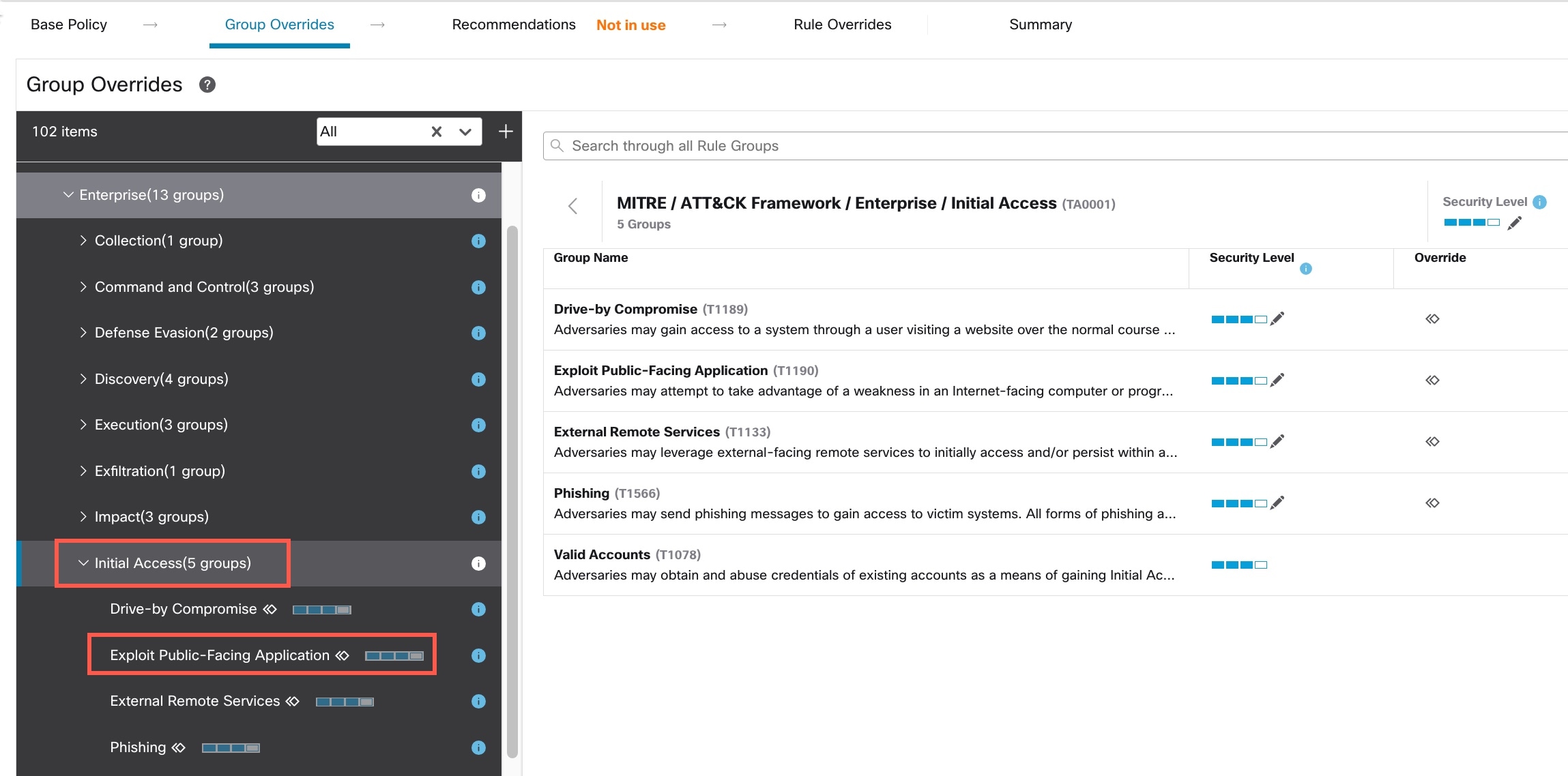
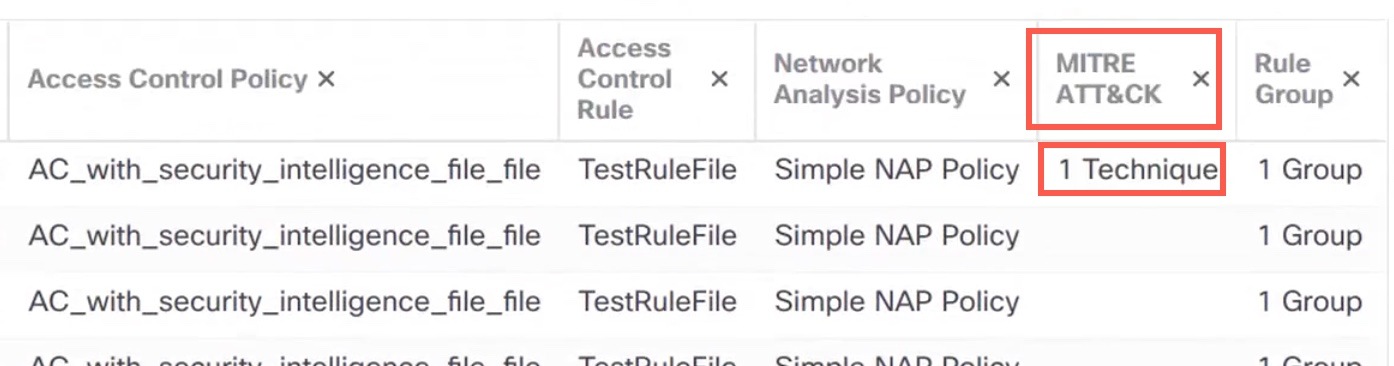
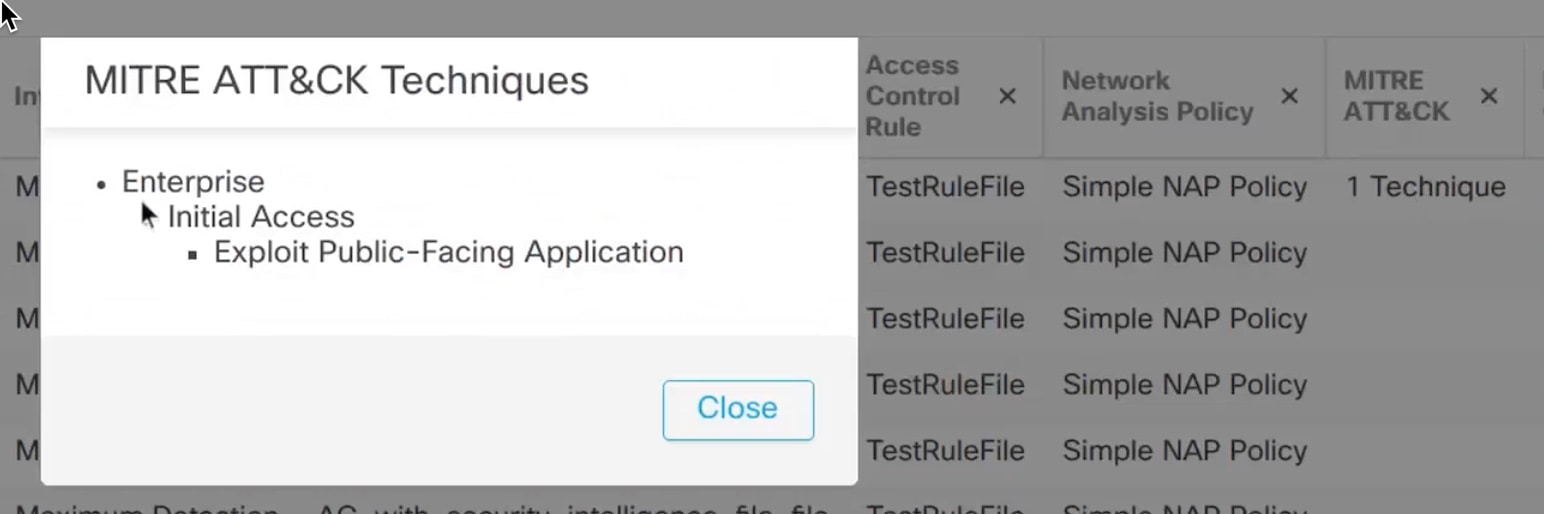
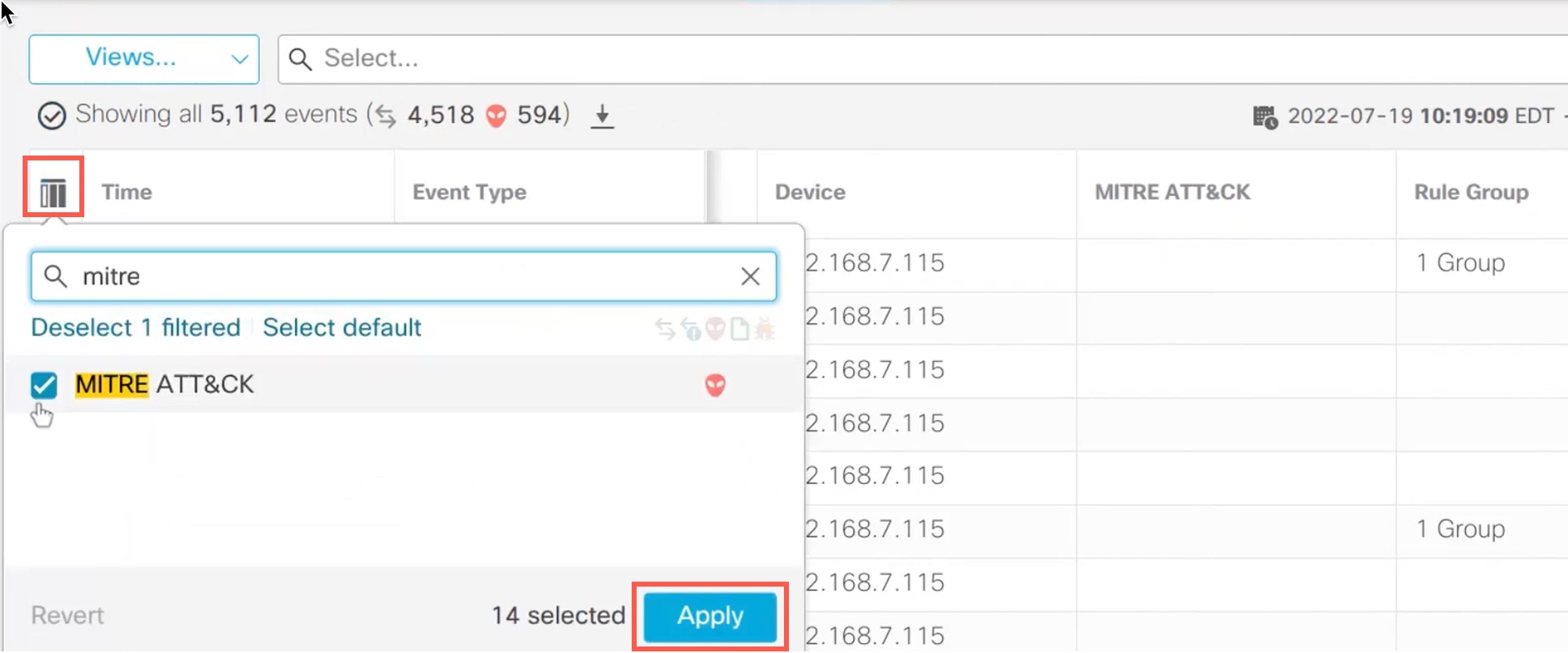
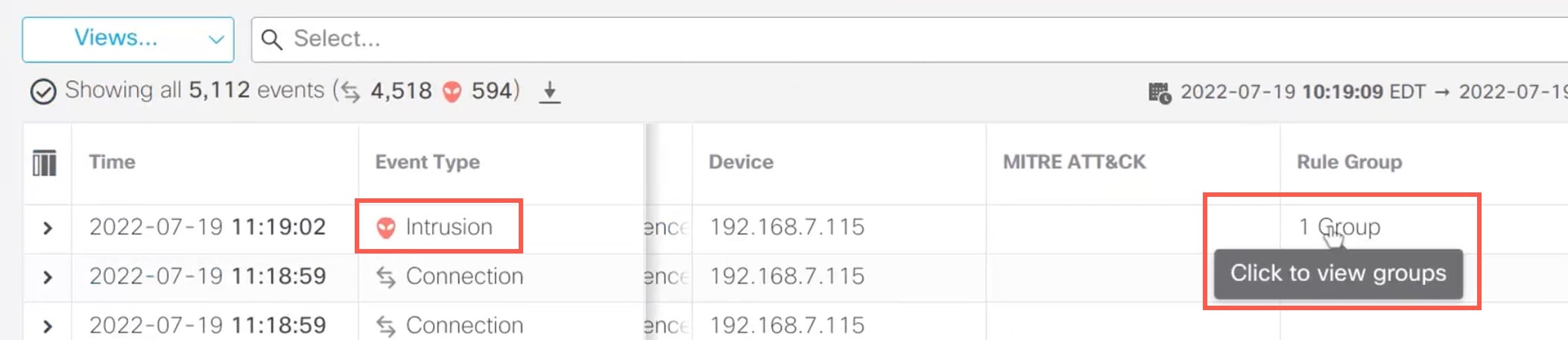
The MITRE framework enables you to navigate through your intrusion rules. MITRE is just another category of rule groups and is part of the Talos rule groups. In your Snort 3 intrusion policy, you can navigate through several levels of rule groups that provide more flexibility and logical grouping of rules.
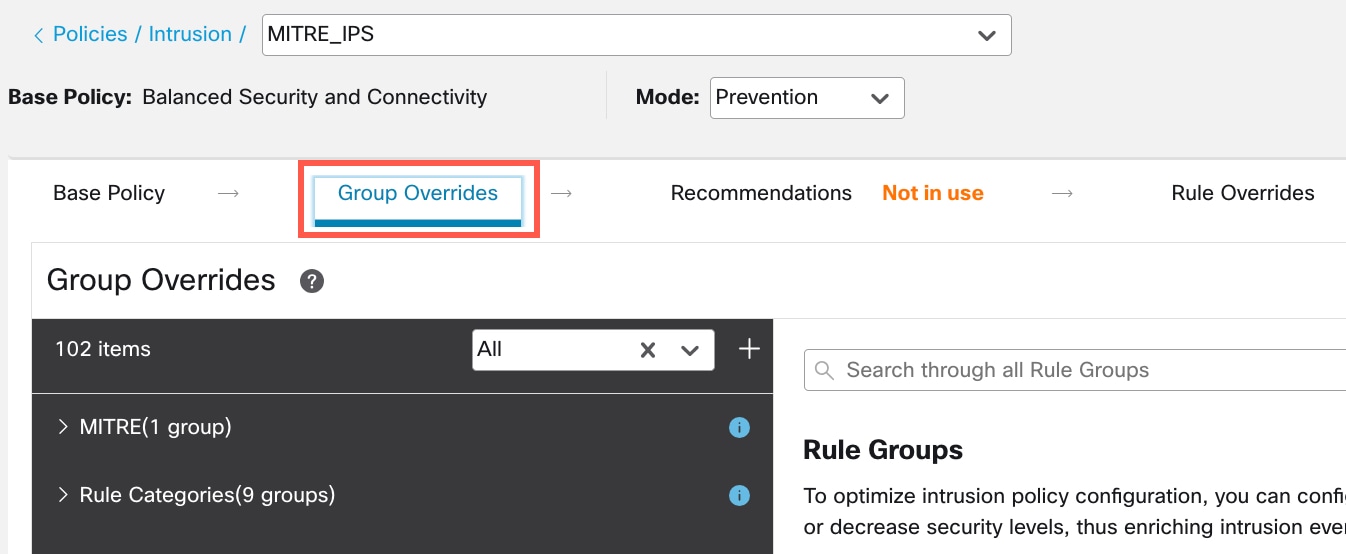
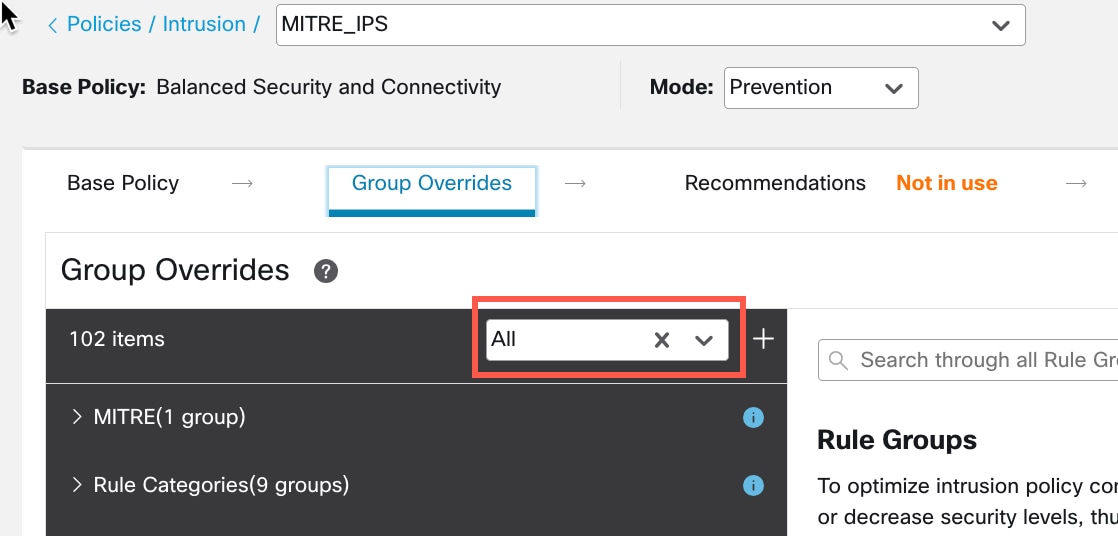
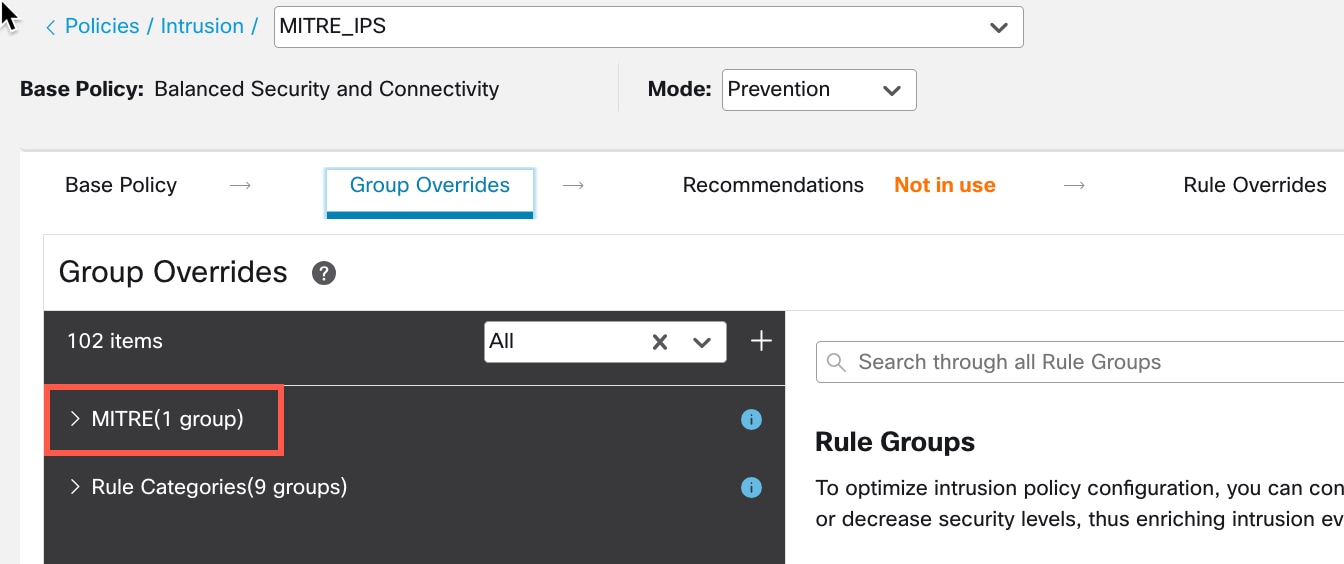
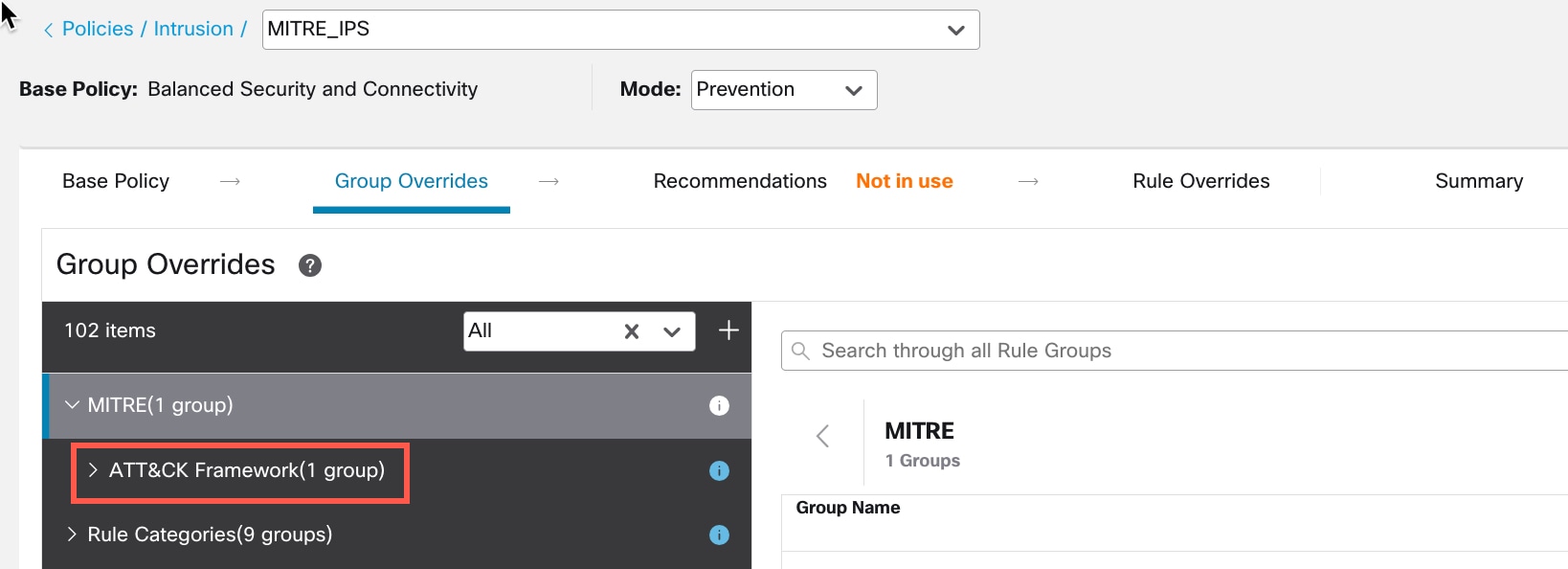
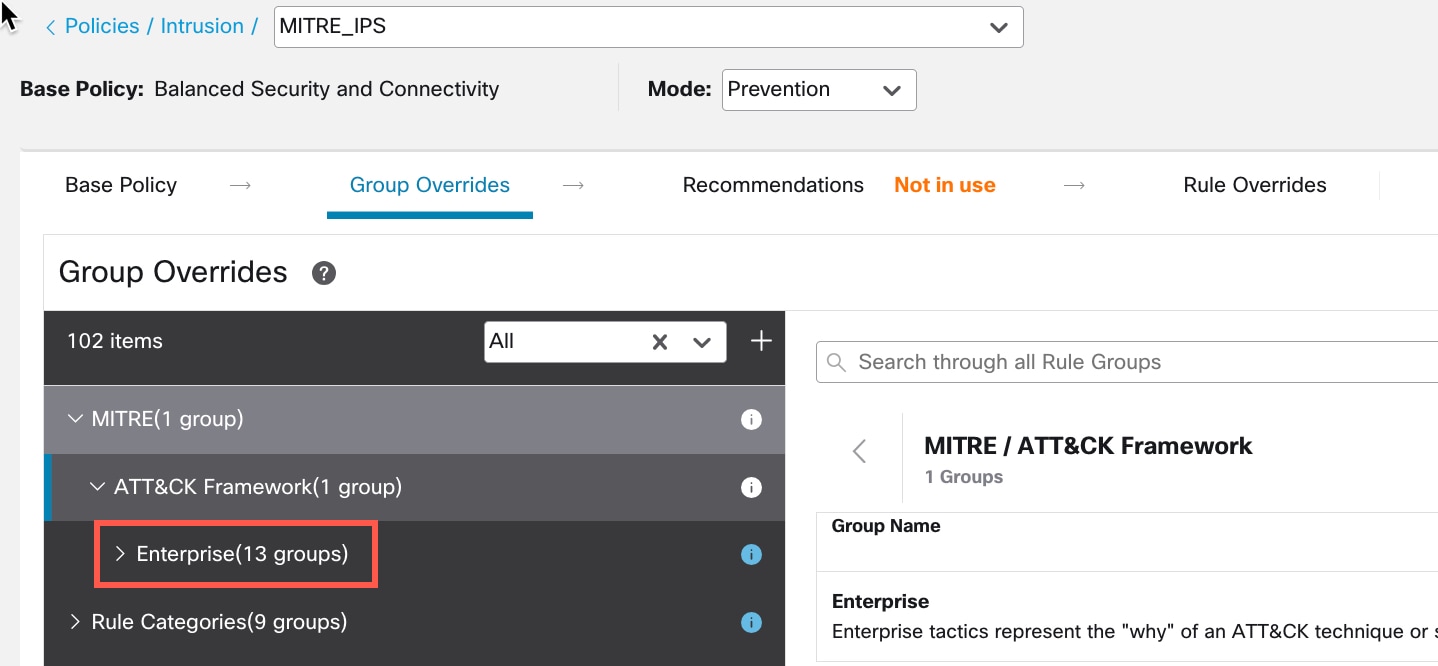
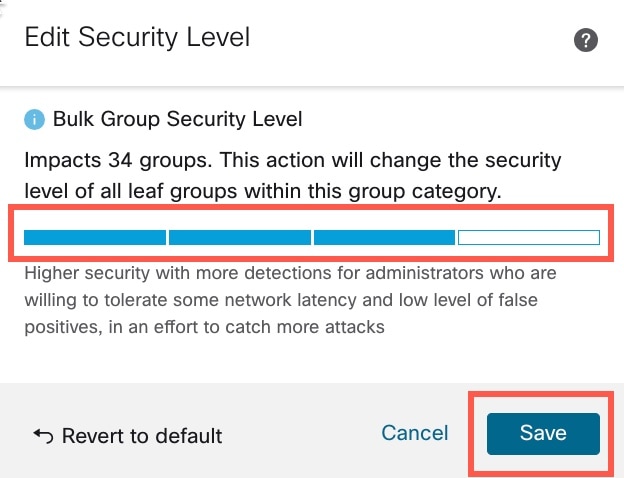
 ) next to the Security Level of the rule group to make bulk changes to the security level for all the associated rule groups
under the
) next to the Security Level of the rule group to make bulk changes to the security level for all the associated rule groups
under the 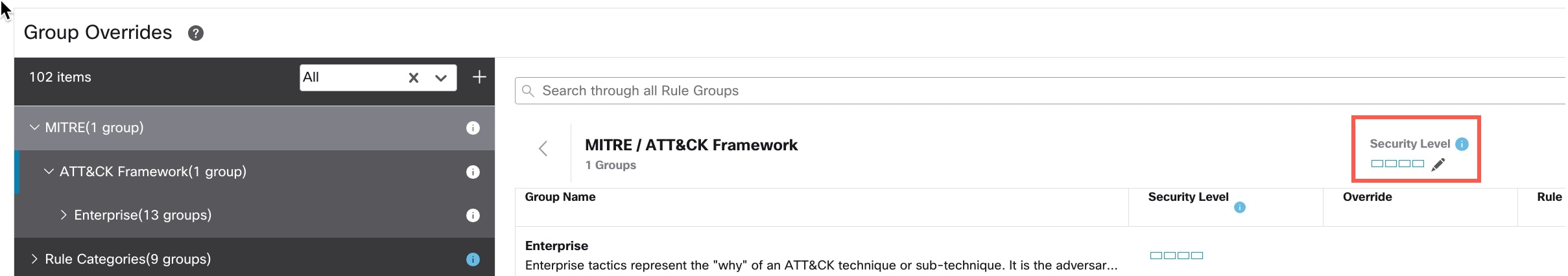
 Feedback
Feedback