Concepts and Architecture
In a Security Analytics and Logging (OnPrem) deployment, you can use a Secure Network Analytics appliance to store data from another Cisco product deployment. In the case of the Secure Firewall deployment, you can export your Security Events and data plane events from your Secure Firewall Threat Defense devices managed by the management center to a Manager to store that information.
You can deploy Secure Network Analytics as follows:
-
Data Store - Deploy Cisco Secure Network Analytics Flow Collectors (up to 5) to receive events, a Cisco Secure Network Analytics Data Store containing 1, 3, or more (in sets of 3) Cisco Secure Network Analytics Data Nodes to store events, and a Manager from which you can review and query events
Data Store
See the following diagram for an example of a Data Store deployment with a Manager, Data Nodes, and Flow Collector(s):
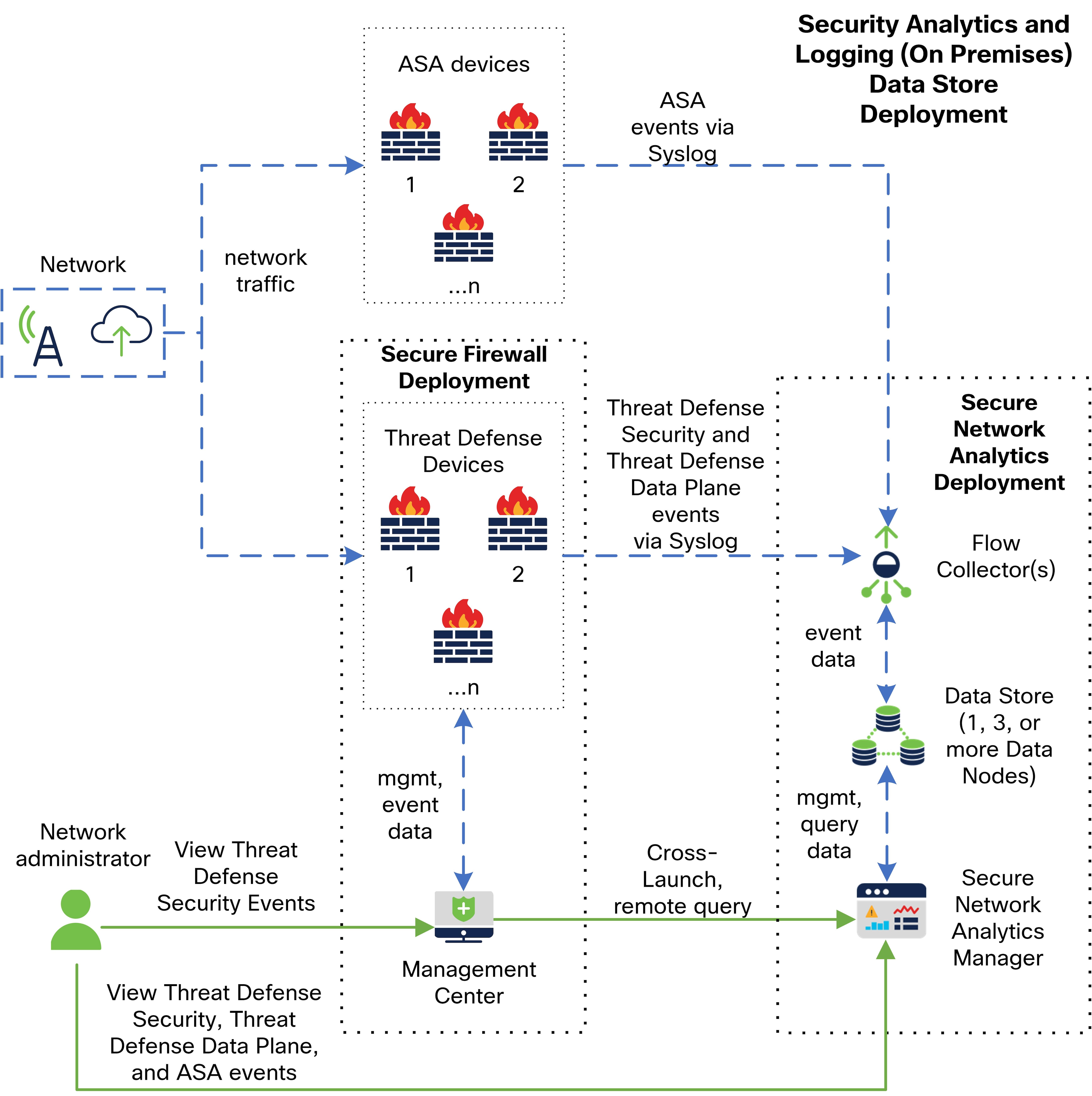
In this deployment, the threat defense and Secure Firewall ASA devices send Firewall events to the Flow Collector. The Flow Collector sends the events to the Data Store for storage. From the management center UI, users can cross-launch to the Manager to view more information about the stored events. They can also query remotely the events from the management center.

 Feedback
Feedback