Cisco ISE-PIC Upgrade Overview
This chapter describes how to upgrade Cisco ISE-PIC software on virtual machines from Release 3.1 or 3.2 to Release 3.3.
Upgrading a Cisco ISE-PIC deployment is a multi-step process and must be performed in the order specified in this document. Upgrade is expected to take approximately 240 minutes + 60 minutes for every 15 GB of data.
Factors that may affect upgrade time include the number of:
-
Endpoints and users in your network
-
Logs in the primary node
 Note |
You must use the Cisco ISE upgrade bundle to upgrade Cisco ISE-PIC. You can download the upgrade bundle from the Cisco ISE Download Software Center. |
In order to upgrade your deployment with minimum-possible downtime while providing maximum resiliency and ability to roll back, and minimum errors, perform the upgrade in the following order:
-
Back up all configuration data before beginning upgrade in order to ensure you can easily roll back manually if necessary.
-
Choose the upgrade process based on your deployment:
-
Standalone deployment
-
Upgrade the node. Refer to Upgrade a Standalone Node.
-
Run upgrade verification and network tests after you upgrade the node. Refer to

Note
For details about the parts of this step, refer to:
-
-
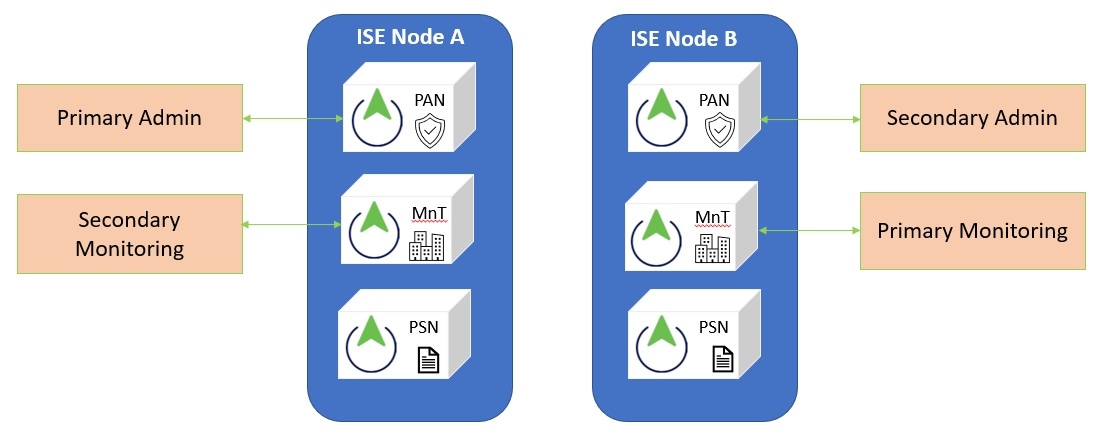
High Availability (two nodes) Deployment
-
Upgrade the secondary node first, keeping the PAN at the previous version until the secondary node upgrade is confirmed, in order to use the PAN for rollback if the initial upgrade fails.
-
Run upgrade verification and network tests after you upgrade the seconary node.
-
Upgrade the PAN.
After upgrading both nodes, the Secondary Administration Node is now the Primary Administration Node, installed with the upgraded version, and the original Primary Administration Node is now the Secondary Administration Node, also installed with the upgraded version.
-
Re-run the upgrade verification and network tests after you upgrade the Primary Administration Node.
-
When you finish upgrading the original primary node (the second upgrade), in the Edit Node window from the currently secondary node, click Promote to Primary to promote it to become the Primary Administration Node (as was in your old deployment), if required.
-
-

 Feedback
Feedback