|
Home
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Home > Introduction
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Home > Dashboard
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Context Visibility
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Context Visibility > Endpoints
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Context Visibility > Users
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Context Visibility > Network Devices
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Context Visibility > Application
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Operations
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
√
|
|
Operations > Adaptive Network Control
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Operations > Adaptive Network Control > Policy List
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Operations > Adaptive Network Control > Endpoint Assignment
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Operations > Reports
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > RADIUS
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > RADIUS > Live Logs
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > RADIUS > Live Sessions
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Threat-Centric NAC Live Logs
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > TACACS
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
√
|
|
Operations > TACACS > Live Logs
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
√
|
|
Operations > Troubleshoot
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Download Logs
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > General Tools
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > General Tools > RADIUS Authentication Troubleshooting
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > General Tools > Execute Network Device Command
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > General Tools > Evaluate Configuration Validator
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > General Tools > Posture Troubleshooting
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > General Tools > Agentless Posture Troubleshooting
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > General Tools > EndPoint Debug
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > General Tools > TCP Dump
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > General Tools > Session Trace Tests
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > Security Group Access Tools
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > Security Group Access Tools > SXP-IP Mappings
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > Security Group Access Tools > IP User SGT
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > Security Group Access Tools > Egress (SGACL) Policy
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Diagnostic Tools > Security Group Access Tools > Device SGT
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Debug Wizard
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Debug Wizard > Debug Log Configuration
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Operations > Troubleshoot > Debug Wizard > Debug Profile Configuration
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Dictionaries
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Library Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Library Conditions > Simple Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Smart Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Authorization
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Authorization > Simple Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Authorization > Compound Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Time and Date
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Anti-Spyware Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Application Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Dictionary Compound Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Dictionary Simple Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Disk Encryption Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > External DataSource Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > File Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Firewall Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Hardware Attributes Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Patch Management Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Registry Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Service Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > USB Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Anti-Malware Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Anti-Virus Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Posture > Compound Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Network Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Network Conditions > Endstation Network Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Network Conditions > Device Port Network Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Network Conditions > Device Network Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Conditions > Profiling
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Authentication
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Authentication > Allowed Protocols
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Authorization
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Authorization > Authorization Profiles
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Authorization > Downloadable ACLs
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Profiling
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Profiling > Exception Actions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Profiling > Network Scan (NMAP) Actions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Requirements
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > Anti-Malware Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > Anti-Virus Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > Firewall Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > Link Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > Script Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > USB Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > Windows Update Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > Application Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > Anti-Spyware Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > File Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > Launch Program Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > Patch Management Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Posture > Remediation Actions > Windows Server Update Services Remediation
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Client Provisioning
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Elements > Results > Client Provisioning > Resources
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Authentication
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Authorization
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Profiling
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Posture
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Policy > Client Provisioning
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Administration
|
√
|
√
|
x
|
√
|
√
|
√
|
√
|
x
|
√
|
√
|
|
Administration > Identity Management
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Administration > Identity Management > Identities
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Identity Management > Identities > Users
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Identity Management > Identities > Latest Manual Network Scan Results
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Identity Management > Groups
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Identity Management > External Identity Sources
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Administration > Identity Management > Identity Source Sequences
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Identity Management > Settings
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Identity Management > Settings > User Custom Attributes
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Identity Management > Settings > Endpoint Purge
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Identity Management > Settings > User Authentication Settings
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Identity Management > Settings > Endpoint Custom Attributes
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Identity Management > Settings > REST ID Store Settings
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Device Portal Management
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Administration > Device Portal Management > BYOD
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Administration > Device Portal Management > Client Provisioning
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Administration > Device Portal Management > My Devices
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Administration > Device Portal Management > Blocked List
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Administration > Device Portal Management > Certificate Provisioning
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Device Portal Management > Mobile Device Management
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Administration > Device Portal Management > Custom Portal Files
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Device Portal Management > Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Administration > Device Portal Management > Settings > Retry URL
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Administration > Device Portal Management > Settings > Employee Registered Devices
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Administration > Network Resources
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > Network Devices
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > Network Devices > Default Device
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > Network Devices > Network Devices
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > Network Devices > Device Security Settings
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > Network Device Groups
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > External RADIUS Servers
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > NAC Managers
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > Location Services
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > Location Services > Location Servers
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > Location Services > Location Tree
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > Network Device Profiles
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > RADIUS Server Sequences
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Network Resources > External MDM
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Summary
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Client Management
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Client Management > Clients
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Client Management > Policy
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Client Management > Groups
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Client Management > Certificates
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Client Management > pxCloud Connection
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Client Management > pxCloud Policy
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Diagnostics
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Diagnostics > WebSocket
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Diagnostics > Log
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Diagnostics > Tests
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > pxGrid Services > Settings
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System
|
√
|
√
|
x
|
x
|
x
|
√
|
√
|
x
|
x
|
√
|
|
Administration > System > Backup & Restore
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Backup & Restore > Policy Export
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Backup & Restore > Backup & Restore
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Admin Access
|
√
|
x
|
x
|
x
|
x
|
√
|
√
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Administrators
|
√
|
x
|
x
|
x
|
x
|
√
|
√
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Administrators > Admin Users
|
√
|
x
|
x
|
x
|
x
|
√
|
√
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Administrators > Admin Groups
|
√
|
x
|
x
|
x
|
x
|
√
|
√
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Authentication
|
√
|
x
|
x
|
x
|
x
|
√
|
√
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Authorization
|
√
|
x
|
x
|
x
|
x
|
√
|
√
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Authorization > Permissions
|
√
|
x
|
x
|
x
|
x
|
√
|
√
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Authorization > Permissions > Menu Access
|
√
|
x
|
x
|
x
|
x
|
√
|
√
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Authorization > Permissions > Data Access
|
√
|
x
|
x
|
x
|
x
|
√
|
√
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Authorization > Policy
|
√
|
x
|
x
|
x
|
x
|
√
|
√
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Settings
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Settings > Access
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Settings > Session
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Admin Access > Settings > Portal Customization
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Max Sessions
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Interactive User Guide
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > DHCP & DNS Services
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Light Session Directory
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Protocols
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Protocols > EAP-FAST
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Protocols > EAP-FAST > EAP FAST Settings
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Protocols > EAP-FAST > Generate PAC
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Protocols > EAP-TTLS
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Protocols > EAP-TLS
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Protocols > PEAP
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Protocols > IPSec
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Protocols > RADIUS
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Network Success Diagnostics
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Network Success Diagnostics > Telemetry
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Network Success Diagnostics > Cisco Support Diagnostics
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Client Provisioning
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > FIPS Mode
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Security Settings
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Proxy
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > SMTP Server
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > SMS Gateway
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > System Time(Primary Node)
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Alarm Settings
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Posture
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Posture > Updates
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Posture > General Settings
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Posture > Reassessments
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Posture > Acceptable Use Policy
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Profiling
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Endpoint Scripts
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Endpoint Scripts > Login Configuration
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > Endpoint Scripts > Settings
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Settings > API Gateway Settings
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Deployment
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
√
|
|
Administration > System > Licensing
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Upgrade
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > System > Health Checks
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Management
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Management > Trusted Certificates
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Management > Certificate Signing Requests
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Management > System Certificates
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Management > OCSP Client Profile
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Management > Certificate Periodic Check Settings
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Authority
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Authority > Certificate Authority Certificates
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Authority > Overview
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Authority > Issued Certificates
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Authority > Internal CA Settings
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Authority > Certificate Templates
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificates > Certificate Authority > External CA Settings
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Logging
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Logging > Logging Categories
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Logging > Collection Filters
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Logging > Log Settings
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Logging > Remote Logging Targets
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Logging > Message Catalog
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Maintenance
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Maintenance > Repository
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Maintenance > Localdisk Management
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Maintenance > Patch Management
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Maintenance > Operational Data Purging
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Session Info
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > System > System Time(Secondary Node)
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Server Certificate
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > System > Certificate Signing Requests
|
√
|
x
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > Feed Service
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > Feed Service > Profiler
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Administration > Threat Centric NAC
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Administration > Threat Centric NAC > Third Party Vendors
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Work Centers
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
|
Work Centers > TrustSec
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > TrustSec > Components
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Components > IP SGT Static Mapping
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Components > Network Devices
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Components > Security Groups
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Components > Security Group ACLs
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Components > Trustsec Servers
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Components > Trustsec Servers > AAA Servers
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Components > Trustsec Servers > HTTPS Servers
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > TrustSec Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > TrustSec Policy > Egress Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > TrustSec Policy > Egress Policy > Matrix
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > TrustSec Policy > Egress Policy > Destination Tree
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > TrustSec Policy > Egress Policy > Matrices List
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > TrustSec Policy > Egress Policy > Source Tree
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > TrustSec Policy > Network Device Authorization
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Authorization Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > SXP
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > SXP > SXP Devices
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > SXP > All SXP Mappings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > ACI
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Reports
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > TrustSec > Overview
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Overview > Introduction
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Overview > Dashboard
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Authentication Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Troubleshoot
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > TrustSec > Troubleshoot > Egress (SGACL) Policy
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > TrustSec > Troubleshoot > IP User SGT
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > TrustSec > Troubleshoot > SXP-IP Mappings
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > TrustSec > Troubleshoot > Device SGT
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > TrustSec > Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Settings > General TrustSec Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Settings > Work Process Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Settings > ACI Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Settings > TrustSec Matrix Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > TrustSec > Settings > SXP Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Profiler > Ext Id Sources
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Endpoint Classification
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Node Config
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Manual Scans
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Manual Scans > Manual NMAP Scan Results
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Manual Scans > Manual NMAP Scan
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Authorization Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Reports
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Profiler > Feeds
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Policy Elements
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Policy Elements > Profiler Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Policy Elements > NMAP Scan Actions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Policy Elements > Exception Actions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Profiling Policies
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Troubleshoot
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Profiler > Troubleshoot > Execute Network Device Command
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Profiler > Troubleshoot > EndPoint Debug
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Troubleshoot > Evaluate Configuration Validator
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Profiler > Troubleshoot > TCP Dump
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Settings > Profiler Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Settings > NMAP Scan Subnet Exclusions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Dictionaries
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Overview
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Profiler > Network Devices
|
√
|
√
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
|
Work Centers > Posture > Network Devices
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Posture Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Authorization Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Reports
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Posture > Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Settings > Posture General Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Settings > Acceptable Use Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Settings > Software Updates
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Settings > Software Updates > Client Provisioning
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Settings > Software Updates > Posture Updates
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Settings > Software Updates > Proxy Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Settings > Reassessment configurations
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Overview
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Client Provisioning
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Posture > Client Provisioning > Client Provisioning Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Client Provisioning > Client Provisioning Portal
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Posture > Client Provisioning > Resources
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Anti-Spyware
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Application
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Compound
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Dictionary Compound
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > File
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Registry
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Anti-Malware
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Anti-Virus
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Dictionary Simple
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Disk Encryption
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > External DataSource
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Firewall Condition
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Hardware Attributes Condition
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Patch Management
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > Service
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Conditions > USB
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Requirements
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations > Anti-Virus
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations > Firewall
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations > Link
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations > Script
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations > Windows Server Update Services
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations > Anti-Malware
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations > Anti-Spyware
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations > File
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations > Launch Program
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations > Patch Management
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations > USB
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Remediations > Windows Update
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Elements > Authorization Profiles
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Authentication Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Posture > Troubleshoot
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Posture > Troubleshoot > Agentless Posture Troubleshooting
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Device Administration
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
√
|
|
Work Centers > Device Administration > Overview
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Overview > Introduction
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Overview > TACACS Livelog
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Overview > Deployment
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Identities
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Identities > Users
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > User Identity Groups
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Ext Id Sources
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Network Resources
|
√
|
√
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Network Resources > Network Devices
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Network Resources > Network Device Groups
|
√
|
√
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Network Resources > Default Devices
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Network Resources > TACACS External Servers
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Network Resources > TACACS Server Sequence
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Conditions > Authentication Simple Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Conditions > Library Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Conditions > Smart Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Conditions > Authorization Simple Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Conditions > Authorization Compound Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Network Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Network Conditions > Endstation Network Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Network Conditions > Device Network Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Network Conditions > Device Port Network Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Results
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Results > Allowed Protocols
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Results > TACACS Command Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Policy Elements > Results > TACACS Profiles
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Device Admin Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > Device Administration > Reports
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
√
|
|
Work Centers > Device Administration > Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
|
Work Centers > PassiveID
|
√
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Overview
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Overview > Introduction
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Overview > Dashboard
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Overview > Live Sessions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Troubleshoot
|
√
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Certificates
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Certificates > System Certificates
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Certificates > OCSP Client Profile
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Certificates > Certificate Periodic Check Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Certificates > Issued Certificates
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Certificates > Internal CA Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Certificates > Certificate Templates
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Certificates > Trusted Certificates
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Certificates > Certificate Signing Requests
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Certificates > Overview
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Certificates > Certificate Authority Certificates
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Reports
|
√
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Providers
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Providers > Agents
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Providers > SPAN
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Providers > Mapping Filters
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Providers > Active Directory
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Providers > API Providers
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Providers > Syslog Providers
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Providers > Endpoint Probes
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > PassiveID > Subscribers
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
|
Work Centers > BYOD > Overview
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Network Devices
|
√
|
√
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Client Provisioning
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Client Provisioning > Resources
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Client Provisioning > Client Provisioning Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Elements
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Elements > Results
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Elements > Results > Authorization Profiles
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Elements > Results > Allowed Protocols
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Elements > Results > Downloadable ACLs
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Elements > Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Elements > Conditions > Authentication Simple Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Elements > Conditions > Authorization Simple Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Elements > Conditions > Library Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Elements > Conditions > Smart Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Elements > Conditions > Authorization Compound Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Authentication Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Reports
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > BYOD > Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Settings > Employee Registered Devices
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Settings > Client Provisioning
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Settings > Retry URL
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Identities
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Identities > Endpoints
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Identities > Identity Source Sequences
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Identities > Network Access Users
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Identity Groups
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Ext Id Sources
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Portals & Components
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > BYOD > Portals & Components > BYOD Portals
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > BYOD > Portals & Components > Blocked List Portal
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > BYOD > Portals & Components > My Devices Portals
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > BYOD > Portals & Components > Certificates
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Portals & Components > Certificates > Certificate Templates
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Portals & Components > Certificates > Internal CA Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Portals & Components > Certificates > External CA Templates
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Authorization Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > BYOD > Custom Portal Files
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Network Access > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Authentication Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Reports
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Network Access > Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Settings > Client Provisioning
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Settings > Collection Filters
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Settings > Protocols
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Settings > Protocols > EAP TLS
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Settings > Protocols > EAP-FAST
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Settings > Protocols > EAP-FAST > EAP FAST
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Settings > Protocols > EAP-FAST > Generate PAC
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Settings > Protocols > PEAP
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Settings > Protocols > RADIUS
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Settings > Proxy Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Dictionaries
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Overview
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Overview > Introduction
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Overview > RADIUS Livelog
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Identities
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Identities > Endpoints
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Identities > Network Access Users
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Identities > Identity Source Sequences
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Id Groups
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Ext Id Sources
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Network Resources
|
√
|
√
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Network Resources > Network Devices
|
√
|
√
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Network Resources > Device Groups
|
√
|
√
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Network Resources > Default Device
|
√
|
√
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Network Resources > External RADIUS Servers
|
√
|
√
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Network Resources > RADIUS Server Sequences
|
√
|
√
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Network Resources > External MDM Servers
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Elements
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Elements > Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Elements > Conditions > Authentication Simple Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Elements > Conditions > Library Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Elements > Conditions > Smart Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Elements > Conditions > Authorization Simple Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Elements > Conditions > Authorization Compound Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Elements > Conditions > Time and Date Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Elements > Results
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Elements > Results > Allowed Protocols
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Elements > Results > Authorization Profiles
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Policy Elements > Results > Downloadable ACLs
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Authorization Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Troubleshoot
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Network Access > Troubleshoot > EndPoint Debug
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Troubleshoot > TCP Dump
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Network Access > Troubleshoot > Collection Filters
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Network Access > Troubleshoot > RADIUS Authentication Troubleshooting
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Guest Access
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
|
Work Centers > Guest Access > Overview
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Administration
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Administration > SMS Gateway Providers
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Administration > Certificates
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Administration > Certificates > System Certificates
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Administration > Certificates > Certificate Periodic Check Settings
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Administration > Certificates > Certificate Signing Requests
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Administration > SMTP Server
|
√
|
√
|
x
|
x
|
x
|
√
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Portals & Components
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Portals & Components > Guest Types
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Portals & Components > Sponsor Portals
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Portals & Components > Guest Portals
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Portals & Components > Sponsor Groups
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Authorization Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Custom Portal Files
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Identities
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Identities > Endpoints
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Identities > Network Access Users
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Identities > Identity Source Sequences
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Identity Groups
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Ext Id Sources
|
√
|
√
|
x
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Network Devices
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Manage Accounts
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Policy Elements
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Policy Elements > Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Policy Elements > Conditions > Authorization Simple Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Policy Elements > Conditions > Common Time and Date Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Policy Elements > Conditions > Authorization Compound Conditions
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Policy Elements > Results
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Policy Elements > Results > Allowed Protocols
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Policy Elements > Results > Downloadable ACLs
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Policy Elements > Results > Authorization Profiles
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Policy Sets
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Authentication Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Work Centers > Guest Access > Reports
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
√
|
x
|
x
|
|
Work Centers > Guest Access > Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Settings > Guest Password Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Settings > Guest Account Purge Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Settings > Guest Email Settings
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Settings > Guest Username Policy
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Settings > Logging
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Settings > Custom Fields
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > Guest Access > Settings > Guest Locations and SSIDs
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
√
|
x
|
|
Work Centers > GPC
|
√
|
√
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Wizard
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
|
Settings
|
√
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
x
|
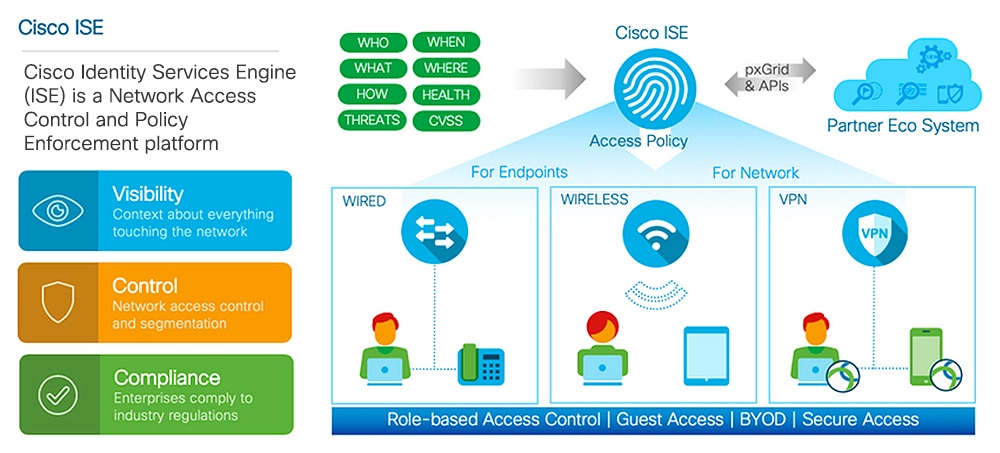

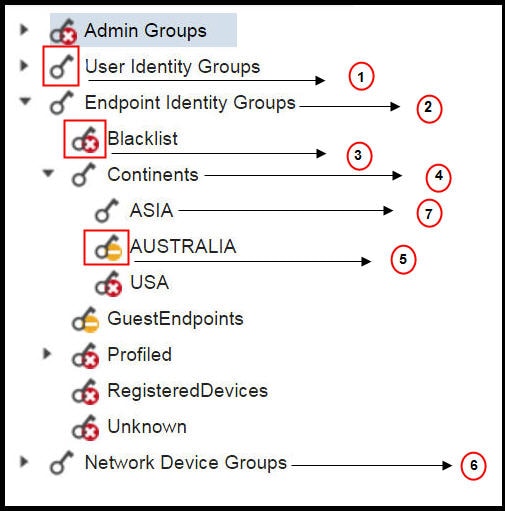
 Feedback
Feedback