Workflow for Check Point to MultiCloud Defense Migration
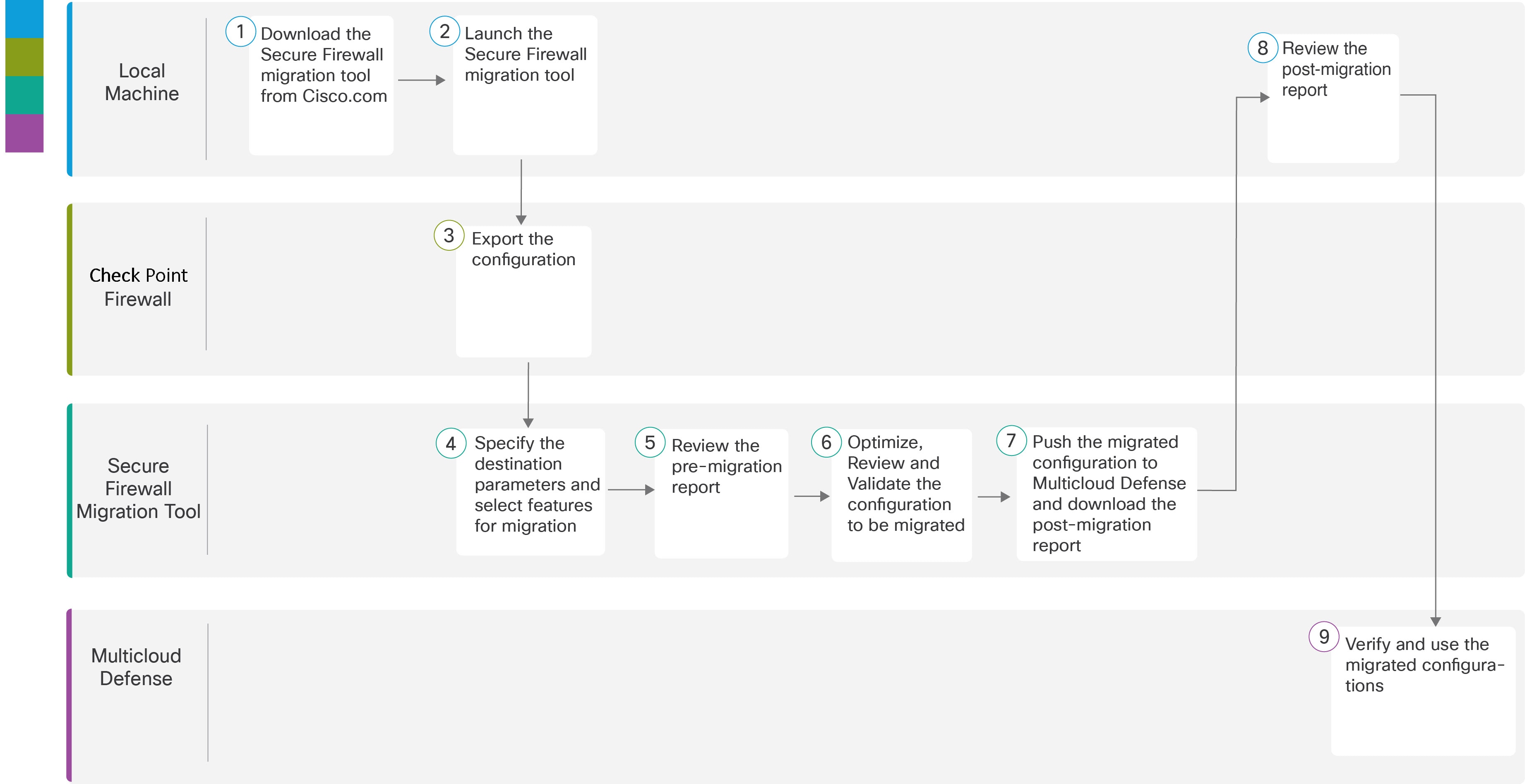
The following flowchart illustrates the workflow for migrating a Check Point firewall to Multicloud defense using the Secure Firewall Migration Tool.
|
Workspace |
Steps |
|
|---|---|---|
|
|
Local machine |
Download the latest version of the Secure Firewall Migration Tool from Cisco.com. For detailed steps, see Download the Secure Firewall Migration Tool from Cisco.com. |
|
|
Local Machine |
In the local machine, initiate the Secure Firewall Migration tool by double-clicking in the application file that you downloaded from Cisco.com. |
|
|
Check Point Firewall |
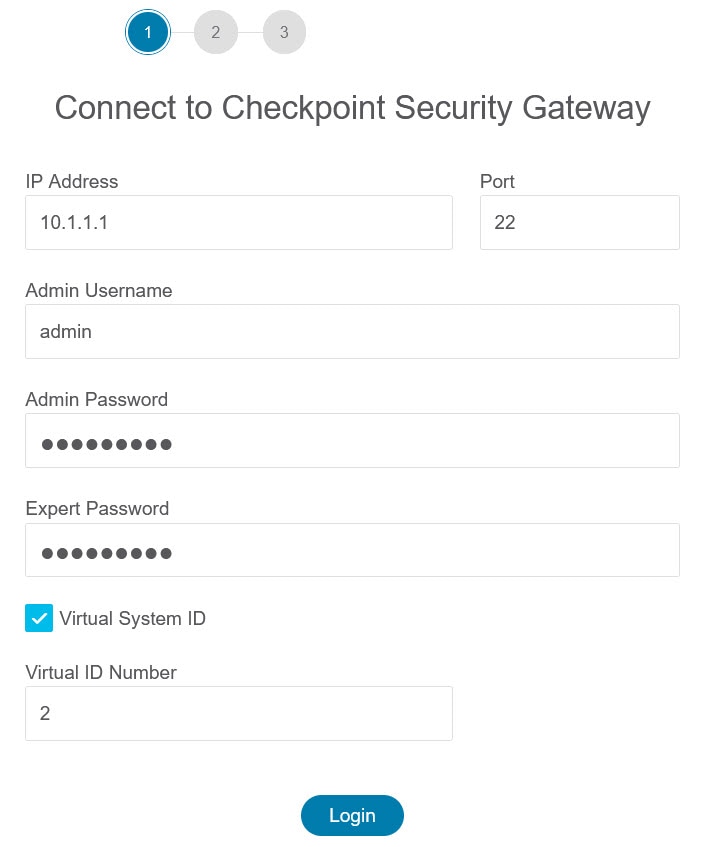
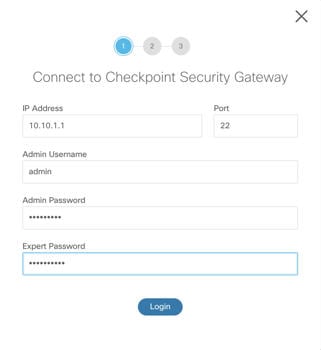
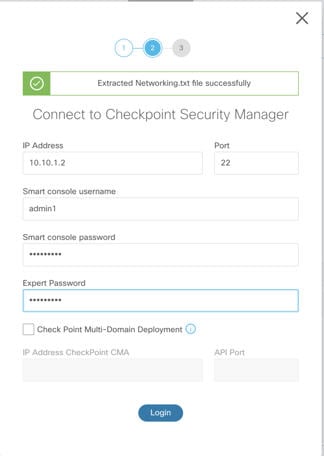
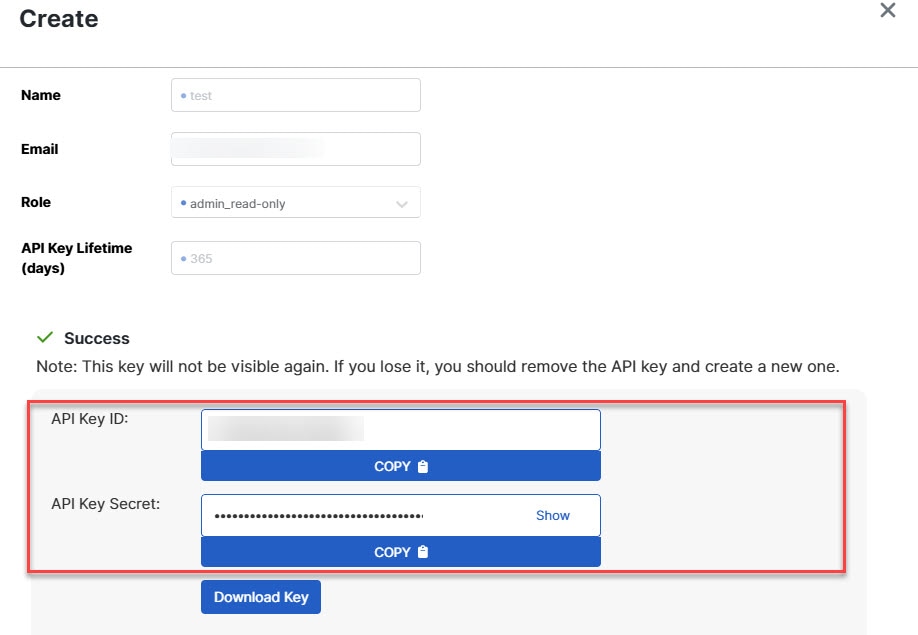
Export the configuration file. To export the configuration from the Check Point firewall, see Export the Check Point Configuration Files for r80. |
|
|
Secure Firewall Migration Tool |
During this step, you can specify the destination parameters for Multicloud Defense. For detailed steps, see Specify Destination Parameters for Multicloud Defense. |
|
|
Secure Firewall Migration Tool |
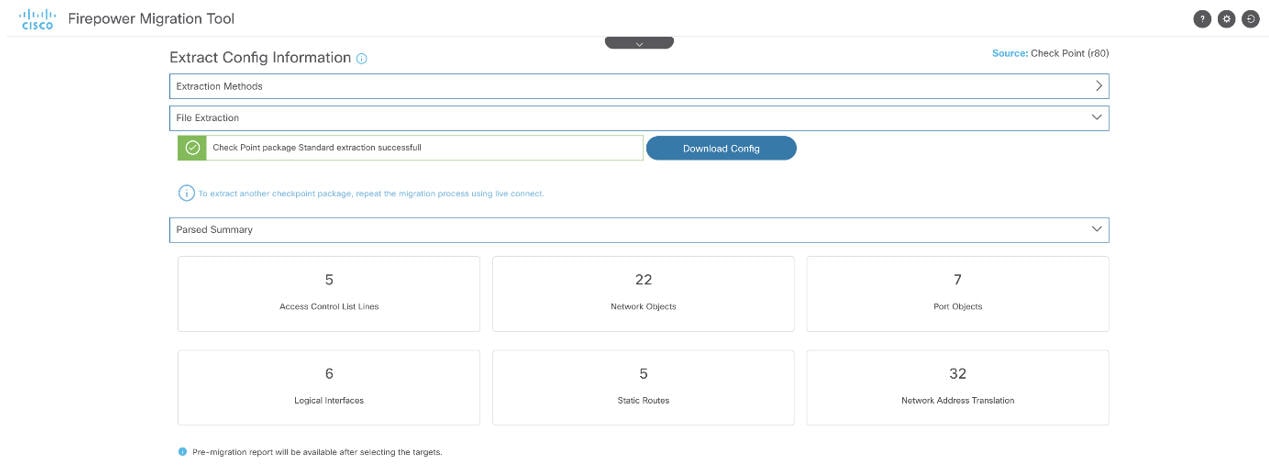
Navigate to the location where you downloaded the premigration report and review the report. For detailed steps, see Review the Pre-Migration Report. |
|
|
Secure Firewall Migration Tool |
Optimize and review the configuration carefully and validate that it is correct. For detailed steps, see Optimize, Review, and Validate the Configuration to be Migrated. |
|
|
Secure Firewall Migration Tool |
This step in the migration process sends the migrated configuration to Multicloud Defense and allows you to download the postmigration report. For detailed steps, see Push the Configuration to Multicloud Defense. |
|
|
Local Machine |
Navigate to the location where you downloaded the postmigration report and review the report. For detailed steps, see Review the Post-Migration Report and Complete the Migration. |
|
|
Multicloud Defense |
Verify the migrated configurations and use them as required in configuring gateways. |




 Feedback
Feedback