Overview of Configuring the Gateway to Receive Email
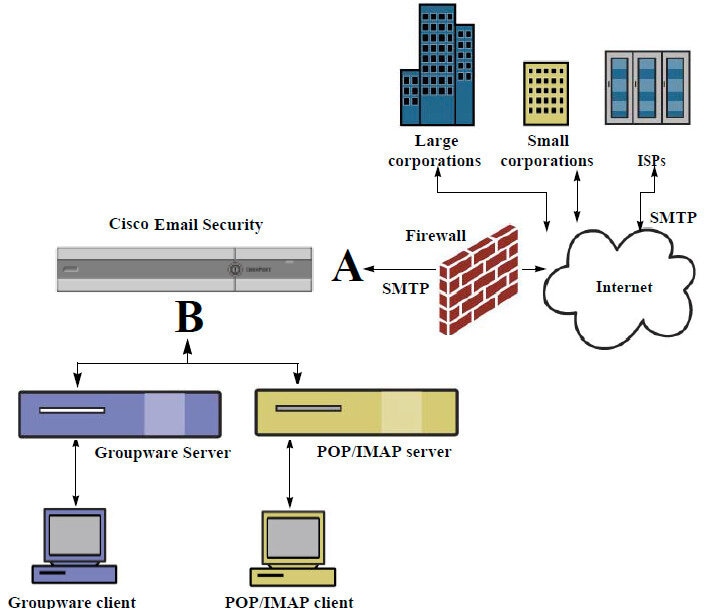
The email gateway functions as the gateway for your organization, servicing email connections, accepting messages, and relaying them to the appropriate systems. The email gateway can service email connections from the Internet to recipients hosts inside your network, and from systems inside your network to the Internet. Typically, email connection requests use Simple Mail Transfer Protocol (SMTP). The appliance services SMTP connections by default, and acts as the SMTP gateway, also known as a mail exchanger or “MX,” for the network.
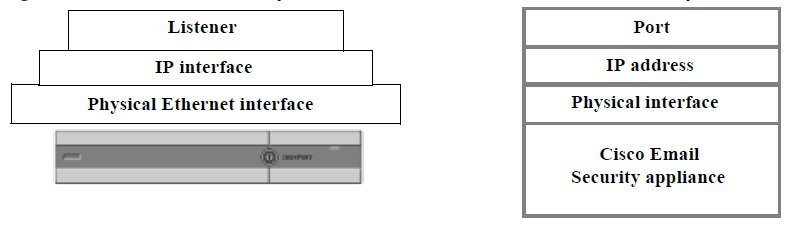
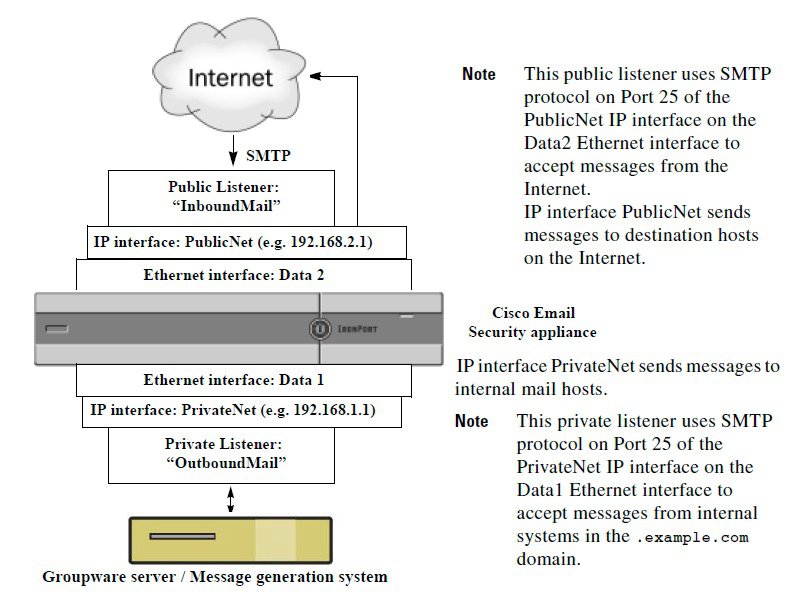
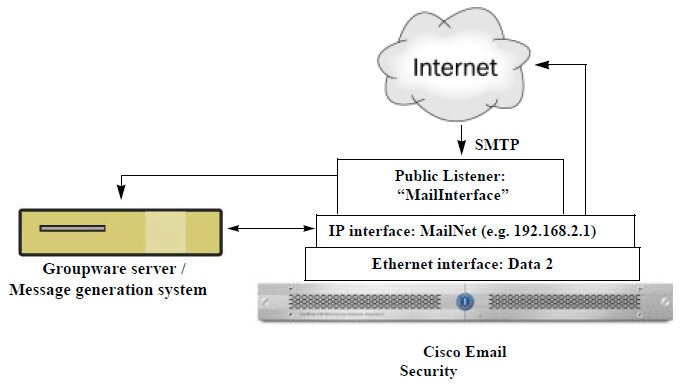
The email gateway uses listeners to service incoming SMTP connection requests, A listener describes an email processing service that is configured on a particular IP interface. Listeners apply to email entering the appliance, from either the Internet or from systems within your network trying to reach the Internet. Use listeners to specify criteria that messages and connections must meet in order to be accepted and for messages to be relayed to recipient hosts. You can think of a listener as an “SMTP daemon” running on a specific port for each IP address specified. Also, listeners define how the email gateway communicates with systems that try to send email to the email gateway.
You can create the following types of listeners:
-
Public. Listens for and accepts email messages coming in from the Internet. Public listeners receive connections from many hosts and direct messages to a limited number of recipients.
-
Private. Listens for and accepts email messages coming from systems within the network, typically from internal groupware and email servers (POP/IMAP), intended for recipients outside the network in the Internet. Private listeners receive connections from a limited (known) number of hosts and direct messages to many recipients.
When you create a listener, you also must specify the following information:
-
Listener properties. Define global properties that apply to all listeners, and properties specific to each listener. For example, you can specify the IP interface and port to use for a listener, and whether it is a public or private listener. For details on how to do this, see Working with Listeners.
-
Which hosts that are allowed to connect to the listener. Define a set of rules that control incoming connections from remote hosts. For example, you can define remote hosts and whether or not they can connect to the listener. For details on how to do this, see Defining Which Hosts Are Allowed to Connect Using the Host Access Table.
-
(Public listeners only) The local domains for which the listener accepts messages. Define which recipients are accepted by the public listener. For example, if your organization uses the domain
currentcompany.comand it previously usedoldcompany.com, then you might accept messages for both currentcompany.com andoldcompany.com. For details on how to do this, see Accepting or Rejecting Connections Based on Domain Name or Recipient Address.
The settings configured in the listener, including its Host Access Table and Recipient Access Table, affect how the listener communicates with an SMTP server during the SMTP conversation. This allows the email gateway to block a spamming host before the connection is closed.

 Feedback
Feedback