Overview
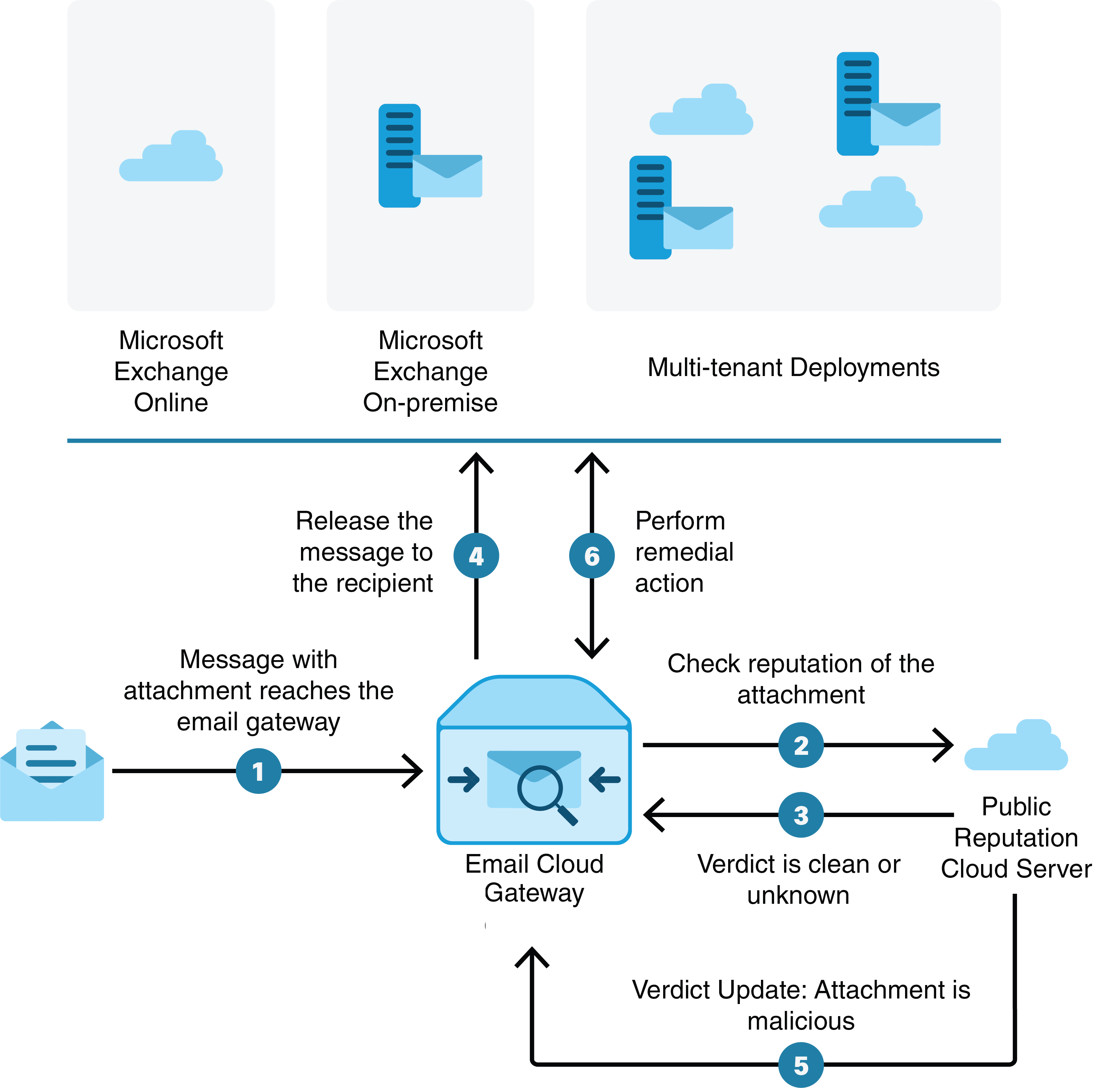
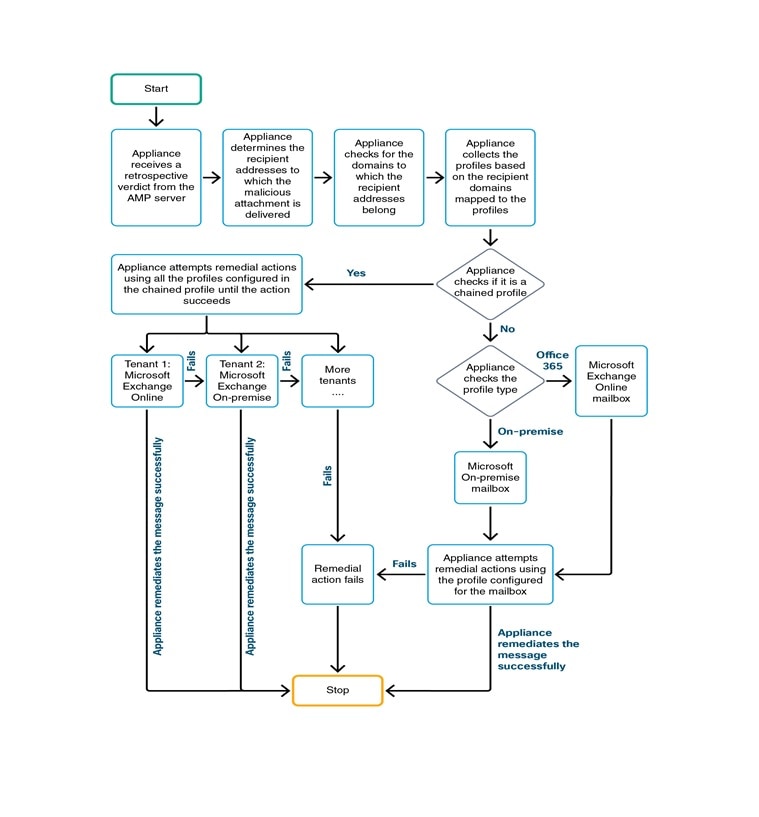
A file can turn malicious anytime, even after it has reached user’s mailbox. AMP can identify this as new information emerges and push retrospective alerts to your appliance. You can configure your appliance to perform auto-remedial actions on the messages in user mailbox when the threat verdict changes. For example, you can configure your appliance to delete the message from the recipient’s mailbox when the verdict of the attachment changes from clean to malicious.
The appliance can perform auto-remedial actions on the messages in the following mailbox deployments:
-
Microsoft Exchange online – mailbox hosted on Microsoft Office 365
-
Microsoft Exchange on-premise – a local Microsoft Exchange server
-
Hybrid/Multiple tenant configuration – a combination of mailboxes configured across Microsoft Exchange online and Microsoft Exchange on-premise deployments

 Feedback
Feedback