- About this Guide
-
- Configuring IPSec and ISAKMP
- Configuring L2TP over IPSec
- Setting General VPN Parameters
- Configuring Tunnel Groups, Group Policies, and Users
- Configuring IP Addresses for VPN
- Configuring Remote Access VPNs
- Configuring Network Admission Control
- Configuring Easy VPN on the ASA 5505
- Configuring the PPPoE Client
- Configuring LAN-to-LAN VPNs
- Configuring AnyConnect VPN Client Connections
- Configuring AnyConnect Host Scan
- Configuring an External Server for Authorization and Authentication
-
- Clientless SSL VPN Overview
- Basic Clientless SSL VPN Configuration
- Advanced Clientless SSL VPN Configuration
- Configuring Policy Groups
- Clientless SSL VPN Remote Users
- Configuring Clientless SSL VPN Users
- Using Clientless SSL VPN with Mobile Devices
- Customizing Clientless SSL VPN
- Clientless SSL VPN Troubleshooting
- Clientless SSL VPN Licensing
- Index
- Clientless SSL VPN End User Setup
Clientless SSL VPN End User Setup
This section is for the system administrator who sets up Clientless SSL VPN for end users. It describes how to customize the end-user interface.
This section summarizes configuration requirements and tasks for a remote system. It specifies information to communicate to users to get them started using Clientless SSL VPN. It includes the following topics:
- Defining the End User Interface
- Customizing Clientless SSL VPN Pages
- Information About Customization
- Exporting a Customization Template
- Editing the Customization Template
Defining the End User Interface
The Clientless SSL VPN end user interface consists of a series of HTML panels. A user logs on to Clientless SSL VPN by entering the IP address of an ASA interface in the format https:// address . The first panel that displays is the login screen (Figure 21-1).
Figure 21-1 Clientless SSL VPN Login Screen
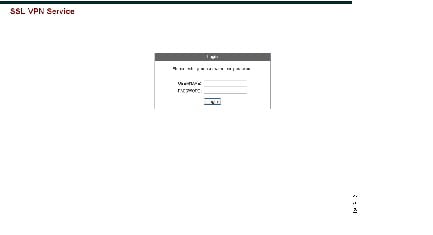
Viewing the Clientless SSL VPN Home Page
After the user logs in, the portal page opens.
The home page displays all of the Clientless SSL VPN features you have configured, and its appearance reflects the logo, text, and colors you have selected. This sample home page includes all available Clientless SSL VPN features with the exception of identifying specific file shares. It lets users browse the network, enter URLs, access specific websites, and use Application Access (port forwarding and smart tunnels) to access TCP applications.
Viewing the Clientless SSL VPN Application Access Panel
To start port forwarding or smart tunnels, a user clicks the Go button in the Application Access box. The Application Access window opens (Figure 21-2).
Figure 21-2 Clientless SSL VPN Application Access Window
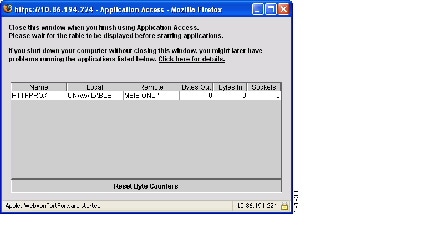
This window displays the TCP applications configured for this Clientless SSL VPN connection. To use an application with this panel open, the user starts the application in the normal way.

Note A stateful failover does not retain sessions established using Application Access. Users must reconnect following a failover.
Viewing the Floating Toolbar
The floating toolbar shown in Figure 21-3 represents the current Clientless SSL VPN session.
Figure 21-3 Clientless SSL VPN Floating Toolbar
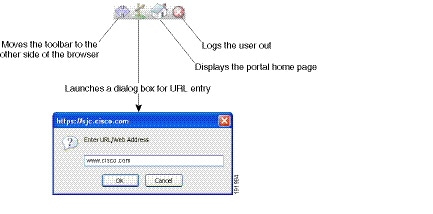
Be aware of the following characteristics of the floating toolbar:
- The toolbar lets you enter URLs, browse file locations, and choose preconfigured Web connections without interfering with the main browser window.
- If you configure your browser to block popups, the floating toolbar cannot display.
- If you close the toolbar, the ASA prompts you to end the Clientless SSL VPN session.
Customizing Clientless SSL VPN Pages
You can change the appearance of the portal pages displayed to Clientless SSL VPN users. This includes the Login page displayed to users when they connect to the security appliance, the Home page displayed to users after the security appliance authenticates them, the Application Access window displayed when users launch an application, and the Logout page displayed when users log out of Clientless SSL VPN sessions.
After you customize the portal pages, you can save your customization and apply it to a specific connection profile, group policy, or user. The changes do not take effect until you reload the ASA, or you switch off and then enable clientless SSL.
You can create and save many customization objects, enabling the security appliance to change the appearance of portal pages for individual users or groups of users.
Information About Customization
The ASA uses customization objects to define the appearance of user screens. A customization object is compiled from an XML file which contains XML tags for all the customizable screen items displayed to remote users. The ASA software contains a customization template that you can export to a remote PC. You can edit this template and import the template back into the ASA as a new customization object.
When you export a customization object, an XML file containing XML tags is created at the URL you specify. The XML file created by the customization object named Template contains empty XML tags, and provides the basis for creating new customization objects. This object cannot be changed or deleted from cache memory but can be exported, edited, and imported back into the ASA as a new customization object.
Customization Objects, Connection Profiles, and Group Policies
Initially, when a user first connects, the default customization object (named DfltCustomization ) identified in the connection profile (tunnel group) determines how the logon screen appears. If the connection profile list is enabled, and the user selects a different group which has its own customization, the screen changes to reflect the customization object for that new group.
After the remote user is authenticated, the screen appearance is determined by whether a customization object that has been assigned to the group policy.
Exporting a Customization Template
When you export a customization object, an XML file is created at the URL you specify. The customization template (named Template ) contains empty XML tags and provides the basis for creating new customization objects. This object cannot be changed or deleted from cache memory but can be exported, edited, and imported back into the ASA as a new customization object.
DETAILED STEPS
Editing the Customization Template
This section shows the contents of the customization template and has convenient figures to help you quickly choose the correct XML tag and make changes that affect the screens.
You can use a text editor or an XML editor to edit the XML file. The following example shows the XML tags of the customization template. Some redundant tags have been removed for easier viewing:
Figure 21-4 shows the Logon page and its customizing XML tags. All these tags are nested within the higher-level tag <auth-page>.
Figure 21-4 Logon Page and Associated XML Tags
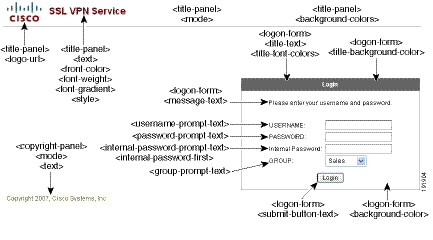
Figure 21-5 shows the Language Selector drop-down list that is available on the Logon page, and the XML tags for customizing this feature. All these tags are nested within the higher-level <auth-page> tag.
Figure 21-5 Language Selector on Logon Screen and Associated XML Tags
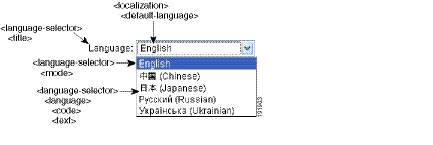
Figure 21-6 shows the Information Panel that is available on the Logon page, and the XML tags for customizing this feature. This information can appear to the left or right of the login box. These tags are nested within the higher-level <auth-page> tag.
Figure 21-6 Information Panel on Logon Screen and Associated XML Tags

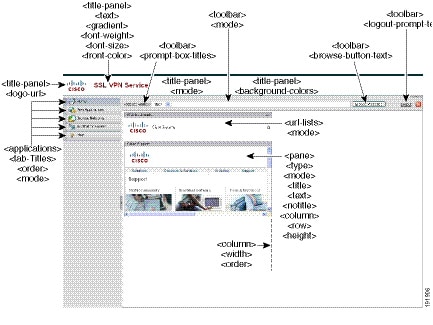
Figure 21-7 shows the Portal page and the XML tags for customizing this feature. These tags are nested within the higher-level <auth-page> tag.
Figure 21-7 Portal Page and Associated XML Tags
Importing a Customization Object
After you edit and save the XML file, import it into cache memory of the ASA using the following commands:
DETAILED STEPS
Applying Customizations to Connection Profiles, Group Policies and Users
After you create a customization, you can apply the customization to a connection profile (tunnel group), a group, or a user, with the customization command. The options displayed with this command are different depending on the mode you are in.

Note After you customize the portal pages, the changes do not take effect until you reload the ASA, or you disable and then enable clientless SSL.
For more information about configuring connection profiles, group policies, and users, see Chapter4, “Configuring Connection Profiles, Group Policies, and Users”.
DETAILED STEPS
Login Screen Advanced Customization
If you prefer to use your own, custom login screen, rather than changing specific screen elements of the login screen we provide, you can perform this advanced customization using the Full Customization feature.
With Full Customization, you provide the HTML for your own login screen, and you insert Cisco HTML code that calls functions on the ASA that create the Login form and the Language Selector drop-down list.
This section describes the modifications you need to make to your HTML code and the tasks required to configure the ASA to use your code.
Figure 21-8 shows the standard Cisco login screen that displays to Clientless SSL VPN users. The Login form is displayed by a function called by the HTML code.
Figure 21-8 Standard Cisco Login Page
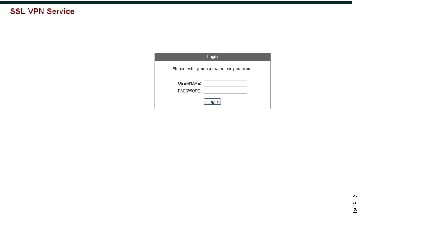
Figure 21-9 shows the Language Selector drop-down list. This feature is an option for Clientless SSL VPN users and is also called by a function in the HTML code of the login screen.
Figure 21-9 Language Selector Drop-down List

Figure 21-10 shows a simple example of a custom login screen enabled by the Full Customization feature.
Figure 21-10 Example of Full Customization of Login Screens

The following HTML code is used as an example and is the code that displays:
The indented code injects the Login form and the Language Selector on the screen. The function csco_ShowLoginForm('lform') injects the logon form. csco_ShowLanguageSelector('selector') injects the Language Selector.
DETAILED STEPS
Step 1 Name your file logon.inc. When you import the file, the ASA recognizes this filename as the logon screen.
Step 2 Modify the paths of images used by the file to include /+CSCOU+/.
Files that are displayed to remote users before authentication must reside in a specific area of the ASA cache memory represented by the path /+CSCOU+/. Therefore, the source for each image in the file must include this path. For example:
Step 3 Insert the special HTML code below. This code contains the Cisco functions, described earlier, that inject the login form and language selector onto the screen.
Customizing Bookmark Help
The ASA displays help content on the application panels for each selected bookmark. You can customize those help files or create help files in other languages. You then import them to flash memory for display during subsequent sessions. You can also retrieve previously imported help content files, modify them, and reimport them to flash memory.
Each application panel displays its own help file content using a predetermined filename. The prospective location of each is in the /+CSCOE+/help/ language / URL within flash memory of the ASA. Table 21-1 shows the details about each of the help files you can maintain for VPN sessions.
language is the abbreviation of the language rendered by the browser. This field is not used for file translation; it indicates the language used in the file. To specify a particular language code, copy the language abbreviation from the list of languages rendered by your browser. For example, a dialog window displays the languages and associated language codes when you use one of the following procedures:
- Open Internet Explorer and choose Tools > Internet Options > Languages > Add .
- Open Mozilla Firefox and choose Tools > Options > Advanced > General , click Choose next to Languages, and click Select a language to add .
The following sections describe how to customize the help contents:
- Customizing a Help File Provided By Cisco
- Creating Help Files for Languages Not Provided by Cisco
- Importing a Help File to Flash Memory
- Exporting a Previously Imported Help File from Flash Memory
Customizing a Help File Provided By Cisco
To customize a help file provided by Cisco, you need to get a copy of the file from the flash memory card first. Get the copy and customize it as follows:
DETAILED STEPS
Step 1 Use your browser to establish a Clientless SSL VPN session with the ASA.
Step 2 Display the help file by appending the string in “URL of Help File in Flash Memory of the Security Appliance” in Table 21-1 , to the address of the ASA, then press Enter.

Note Enter en in place of language to get the help file in English.
The following example address displays the English version of the Terminal Servers help:
https:// address_of_security_appliance /+CSCOE+/help/en/rdp-hlp.inc
Step 3 Choose File > Save (Page) As .

Note Do not change the contents of the File name box.
Step 4 Change the Save as type option to Web Page, HTML only and click Save .
Step 5 Use your preferred HTML editor to modify the file.

Note You can use most HTML tags, but do not use tags that define the document and its structure (e.g., do not use <html>, <title>, <body>, <head>, <h1>, <h2>, etc. You can use character tags, such as the <b> tag, and the <p>, <ol>, <ul>, and <li> tags to structure content.
Step 6 Save the file as HTML only, using the original filename and extension.
Step 7 Ensure the filename matches the one in Table 21-1 , and that it does not have an extra filename extension.
Creating Help Files for Languages Not Provided by Cisco
Use HTML to create help files in other languages.
We recommend creating a separate folder for each language to support.
Save the file as HTML only. Use the filename following the last slash in “URL of Help File in Flash Memory of the Security Appliance” in Table 21-1 .
See the next section to import the files for display during VPN sessions.
Restrictions
You can use most HTML tags, but do not use tags that define the document and its structure (e.g., do not use <html>, <title>, <body>, <head>, <h1>, <h2>, etc. You can use character tags, such as the <b> tag, and the <p>, <ol>, <ul>, and <li> tags to structure content.
DETAILED STEPS
import webvpn webcontent destination_url source_url hostname# import webvpn webcontent /+CSCOE+/help/en/app-access-hlp.inc tftp://209.165.200.225/app-access-hlp.inc |
Imports a help content file to flash memory for display in Clientless SSL VPN sessions.
Copies the help file app-access-hlp.inc to flash memory from the TFTP server at 209.165.200.225. The URL includes the abbreviation en for the English language. |
DETAILED STEPS
export webvpn webcontent source_url destination_url hostname# export webvpn webcontent /+CSCOE+/help/en/file-access-hlp.inc tftp://209.165.200.225/file-access-hlp.inc |
Retrieves a previously imported help content file for subsequent edits.
Copies the English language help file file-access-hlp.inc displayed on the Browser Networks panel to TFTP Server 209.165.200.225. |
Translating the Language of User Messages
The ASA provides language translation for the entire Clientless SSL VPN session. This includes login, logout banners, and portal pages displayed after authentication such as plugins and AnyConnect.
This section describes how to configure the ASA to translate these user messages and includes the following sections:
- Understanding Language Translation
- Creating Translation Tables
- Referencing the Language in a Customization Object
- Changing a Group Policy or User Attributes to Use the Customization Object
Understanding Language Translation
Functional areas and their messages that are visible to remote users are organized into translation domains. Table 21-2 shows the translation domains and the functional areas translated.
Table 21-2 Language Translation Domain Options
The ASA includes a translation table template for each domain that is part of standard functionality. The templates for plug-ins are included with the plug-ins and define their own translation domains.
You can export the template for a translation domain, which creates an XML file of the template at the URL you provide. The message fields in this file are empty. You can edit the messages and import the template to create a new translation table object that resides in flash memory.
You can also export an existing translation table. The XML file created displays the messages you edited previously. Reimporting this XML file with the same language name creates a new version of the translation table object, overwriting previous messages.
Some templates are static, but some change based on the configuration of the ASA. Because you can customize the logon and logout pages, portal page, and URL bookmarks for clientless users, the ASA generates the customization and url-list translation domain templates dynamically, and the template automatically reflects your changes to these functional areas.
After creating translation tables, they are available to customization objects that you create and apply to group policies or user attributes. With the exception of the AnyConnect translation domain, a translation table has no affect, and messages are not translated on user screens until you create a customization object, identify a translation table to use in that object, and specify that customization for the group policy or user. Changes to the translation table for the AnyConnect domain are immediately visible to AnyConnect client users.
Creating Translation Tables
You can create translation tables in both single context mode and multi-context mode:
DETAILED STEPS
If you import a translation table for the AnyConnect domain, your changes are effective immediately. If you import a translation table for any other domain, you must create a customization object, identify the translation table to use in that object, and specify that customization object for the group policy or user.
Referencing the Language in a Customization Object
This section describes how to export the customization template, edit it, and import it as a customization object so that you can refer to it.
Prerequisites
For the customization object to call these translation tables correctly, the tables must have been previously imported using the same names. These names must be compatible with language options of the browser.
DETAILED STEPS
Changing a Group Policy or User Attributes to Use the Customization Object
This section describes how to activate your changes for specific groups or users.
 Feedback
Feedback