Overview of Cisco Optical Network Controller
Cisco Optical Network Controller (Cisco ONC) is an SDN Domain Controller for Cisco optical networks. Cisco Optical Network Controller behaves as a Provisioning Network Controller (PNC) and performs the following functions.
-
Collects information about the inventory and topology of the managed network.
-
Monitors the physical or virtual topology of the network.
-
Notifies of changes in topology and service changes.
-
Supports optical path creation and deletion.
Cisco Optical Network Controller collects relevant data needed for optical applications. This data is also used to provide abstract network information to higher layer controllers, thus enabling a centralized control of optical network.
Some of the functions supported by Cisco Optical Network Controller are given below.
-
Optical Domain Controller
Cisco Optical Network Controller behaves as a domain controller for Cisco optical products. The domain controller feeds data into hierarchical controllers. Optical Network Controller has a North Bound Interface (NBI) based on the TAPI standard which enables it to connect to any hierarchical controller which has a TAPI compliant South Bound Interface (SBI) and provide its functions to the controller.
-
Path Compute Engine (PCE)
PCE service provides optical path computation to ensure optically valid paths are provisioned within the supplied constraints. PCE uses the latest network status.
-
Model Based Network Abstraction
Cisco Optical Network Controller supports a standardized TAPI model which enables it to abstract the device level details from the hierarchical controller.
 Note |
|
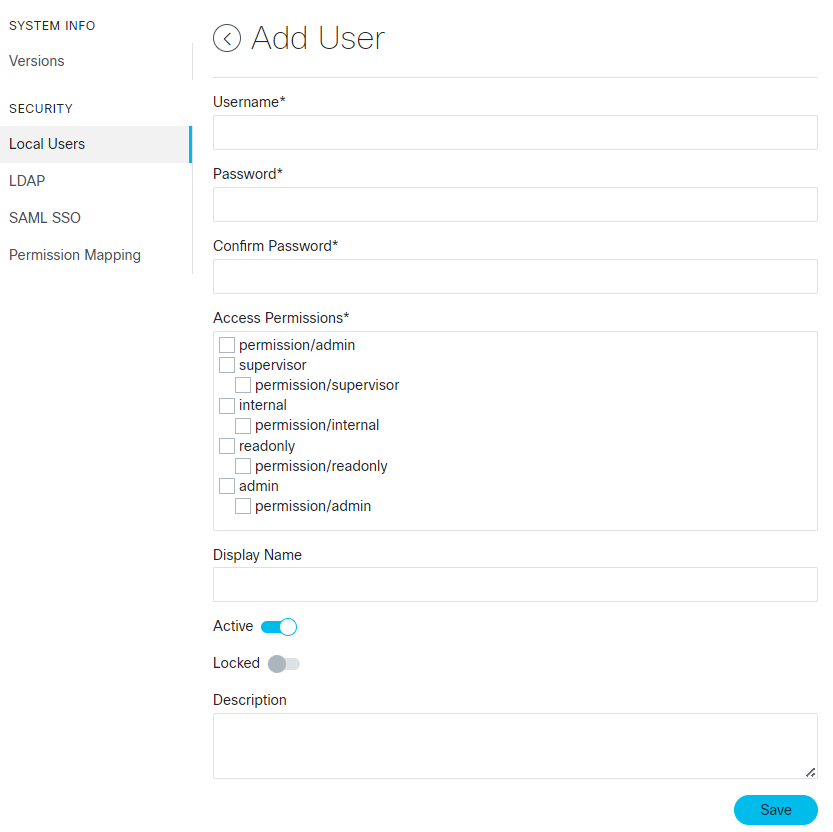
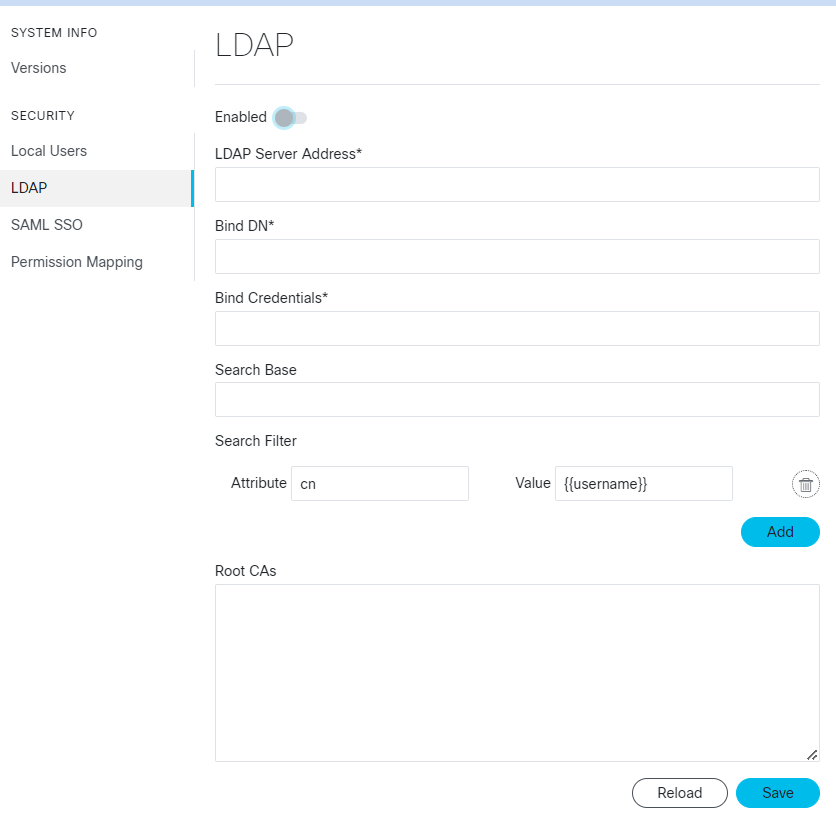
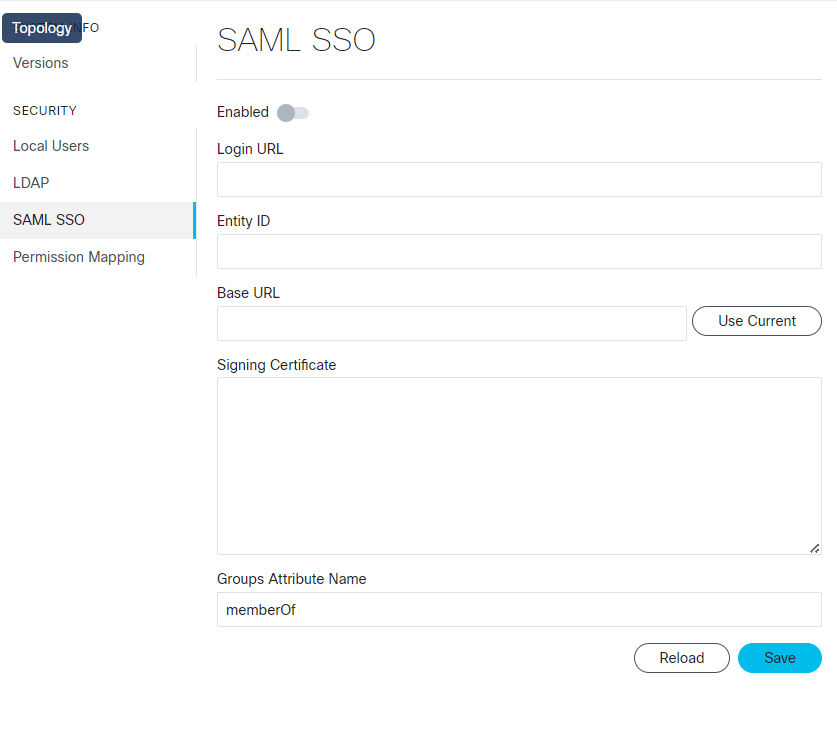
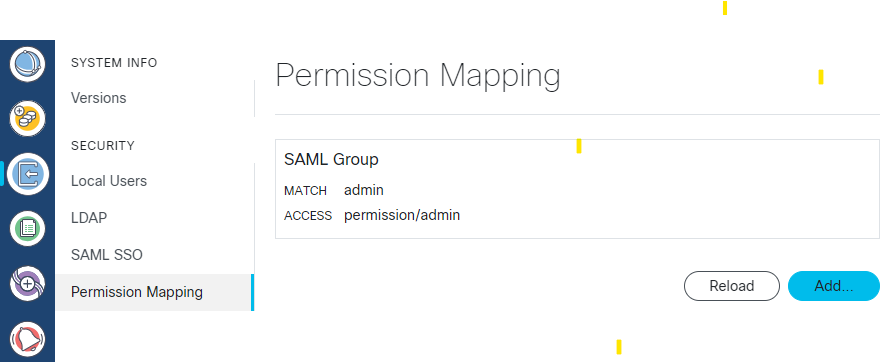
 Feedback
Feedback