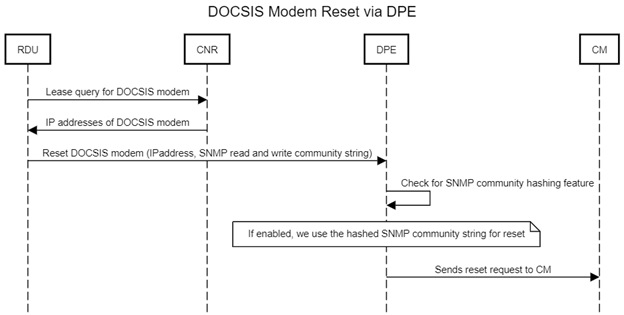
When a user performs a device reset, the RDU uses the SNMP read and write community value configured via the RDU Admin UI
(or which may be in any one of the following hierarchy levels: device, DHCP Criteria, COS or system defaults level) to perform
the device reset operation. The RDU sends this community string to the DPE along with the device IP address to perform the
device reset.
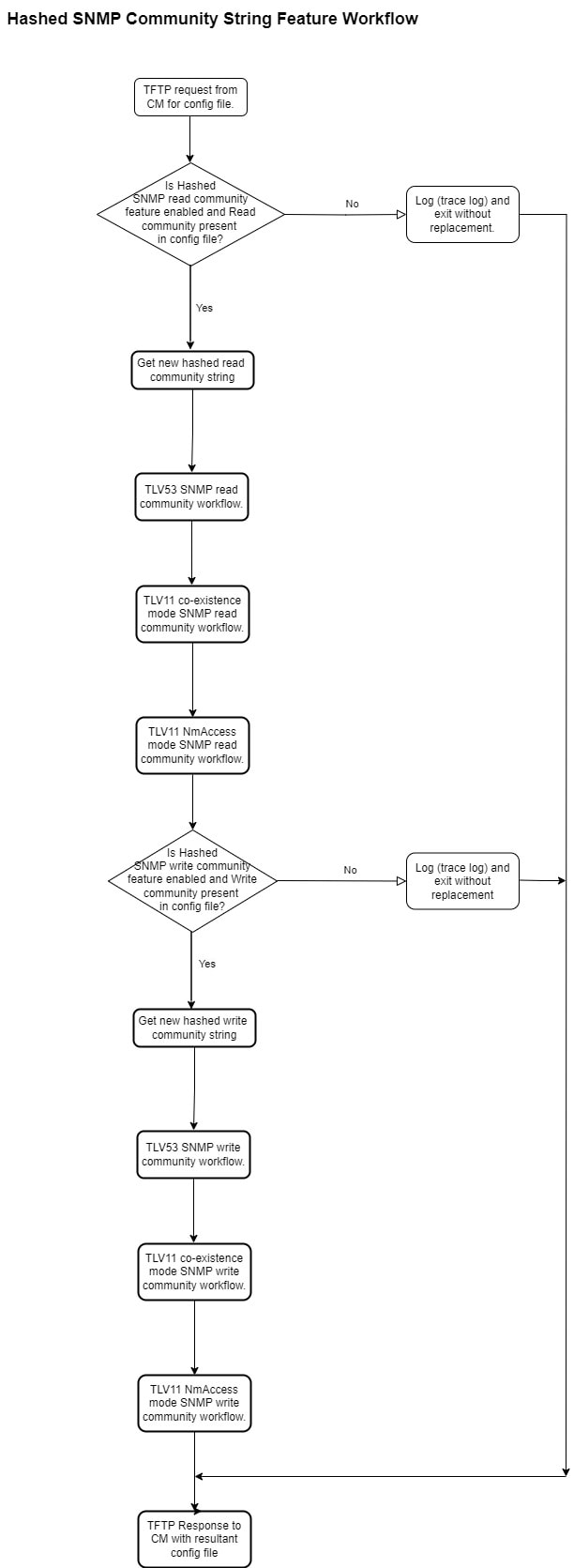
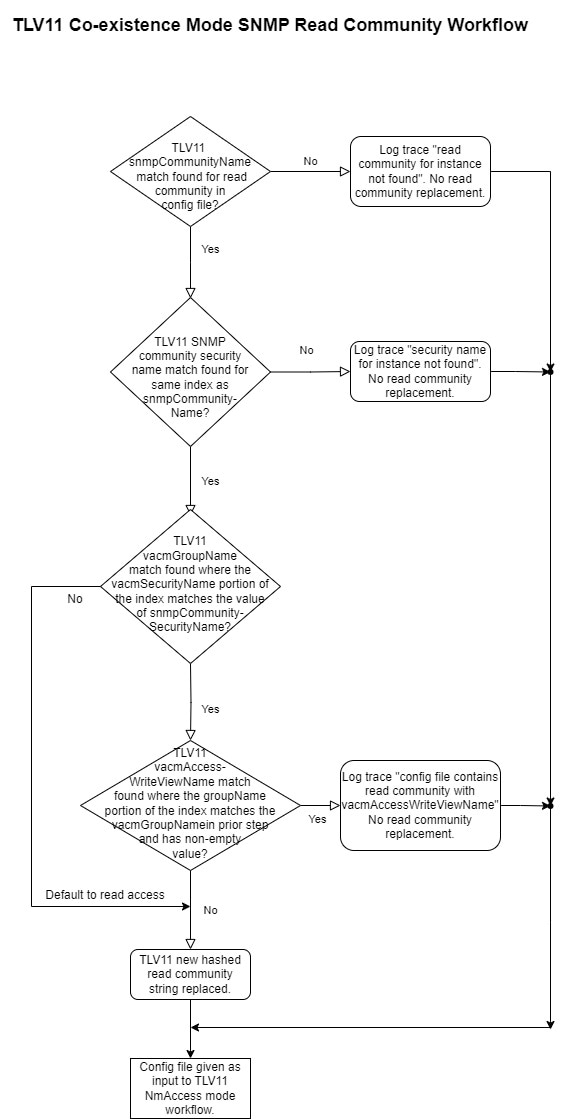
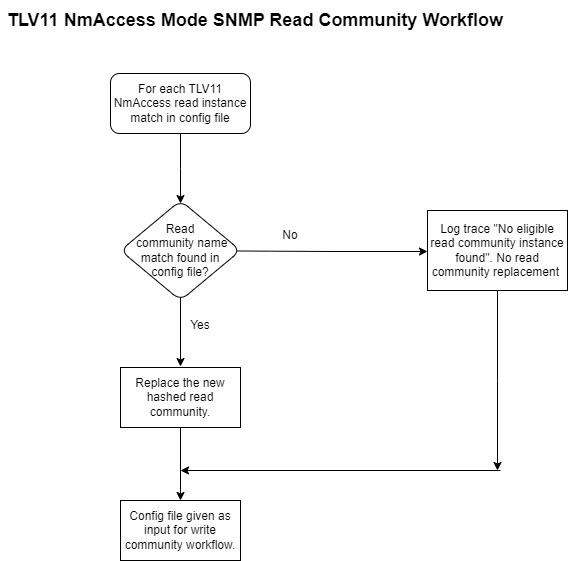
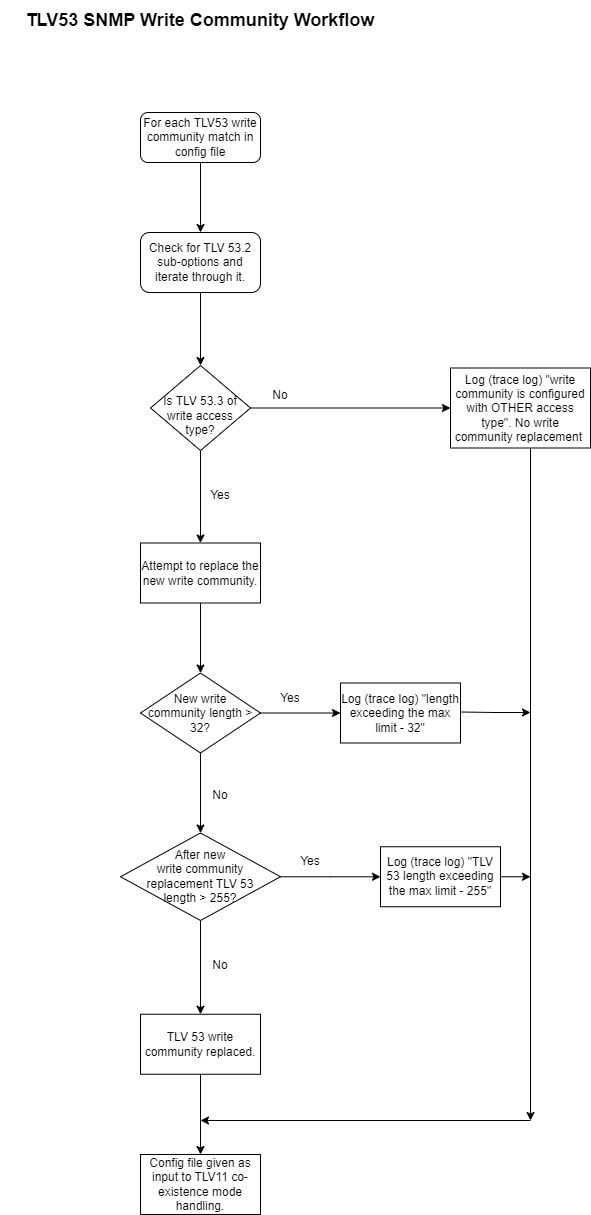
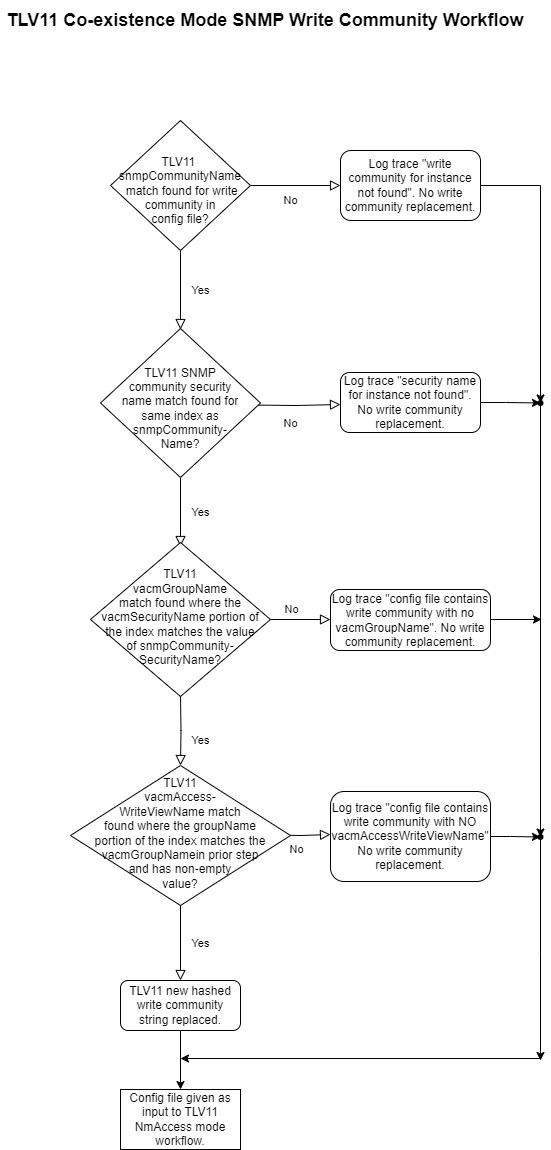
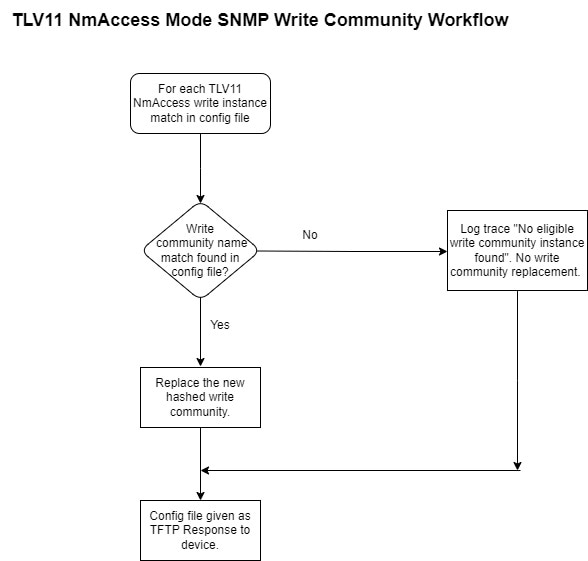
If the hashed SNMP feature is enabled, then the DPE verifies if the SNMP community string values received from RDU are the
same as the values configured in the DPE CLI. If a match is found, the DPE replaces the SNMP community string values with
the hashed SNMP community string (computed based on the device IP address) for the device reset operation. If the values differ,
the SNMP community string values passed from RDU is used for device reset operation.

 Feedback
Feedback