- Application Firewall-Instant Message Traffic Enforcement
- E-mail Inspection Engine
- ESMTP Support for Cisco IOS Firewall
- Firewall N2H2 Support
- Firewall Support for SIP
- Firewall Support of Skinny Client Control Protocol
- Firewall Stateful Inspection of ICMP
- Granular Protocol Inspection
- TCP Out-of-Order Packet Support for Cisco IOS Firewall and Cisco IOS IPS
Firewall Support for SIP
The Firewall Support for SIP feature integrates Cisco IOS firewalls, Voice over IP (VoIP) protocol, and Session Initiation Protocol (SIP) within a Cisco IOS-based platform, enabling better network convergence.
 Note |
Some Cisco IOS versions earlier than 12.2(11)YU and 12.2(15)T may accept the configuration commands for SIP that are shown in this document; however, those earlier versions will not function properly. |
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the Feature Information Table at the end of this document.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Restrictions for Firewall Support for SIP
DNS Name Resolution
Although SIP methods can have Domain Name System (DNS) names instead of raw IP addresses, this feature currently does not support DNS names.
SIP UDP Support Only
This feature supports only the SIP User Datagram Protocol (UDP) format for signaling; the TCP format is not supported.
SIP Abbreviated Header
This feature does not support the compact form of SIP header fields.
Earlier Versions of Cisco IOS
Some Cisco IOS versions earlier than 12.2(11)YU and 12.2(15)T may accept the configuration commands for SIP that are shown in this document; however, those earlier versions will not function properly.
Information About Firewall Support for SIP
- Cisco IOS Firewall
- SIP - Session Initiation Protocol
- SIP Messages
- Firewall for SIP Functionality Description
- SIP Message Treatment by the Firewall
- Call Database
Cisco IOS Firewall
The Cisco IOS firewall extends the concept of static access control lists (ACLs) by introducing dynamic ACL entries that open on the basis of the necessary application ports on a specific application and close these ports at the end of the application session. The Cisco IOS firewall achieves this functionality by inspecting the application data, checking for conformance of the application protocol, extracting the relevant port information to create the dynamic ACL entries, and closing these ports at the end of the session. The Cisco IOS firewall is designed to easily allow a new application inspection whenever support is needed.
SIP - Session Initiation Protocol
SIP is an ASCII-based, application-layer control protocol that can be used to establish, maintain, and terminate calls between two or more endpoints. Like other VoIP protocols, SIP is designed to address the functions of signaling and session management within a packet telephony network. Signaling allows call information to be carried across network boundaries. Session management provides the ability to control the attributes of an end-to-end call.
SIP Messages
SIP has two types of messages--requests and responses--that have the following generic structure:
generic-message = Request-Line | Status-Line
* ( general-header | request-header
| response-header | entity-header )
CRLF
[ message-body]
 Note |
Any of these message components may contain embedded IP addresses. |
The table below identifies the six available SIP request messages.
| Table 1 | SIP Request Messages |
| SIP Message |
Purpose |
|---|---|
| ACK |
Confirms receipt of a final response to INVITE |
| BYE |
Is sent by either side to end the call |
| CANCEL |
Is sent to end a call that has not yet been connected |
| INVITE |
Is a request from a User Agent Client (UAC) to initiate a session |
| OPTIONS |
Are sent to query capabilities of the user agents and network servers
|
| REGISTER |
Is sent by the client to register the address with a SIP proxy |
The table below identifies the available SIP response methods.
| Table 2 | SIP Response Messages |
Firewall for SIP Functionality Description
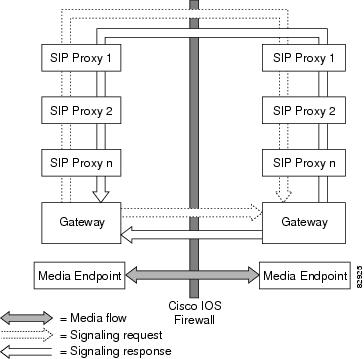
The Firewall for SIP Support feature allows SIP signaling requests to traverse directly between gateways or through a series of proxies to the destination gateway or phone. After the initial request, if the Record-Route header field is not used, subsequent requests can traverse directly to the destination gateway address as specified in the Contact header field. Thus, the Cisco IOS firewall is aware of all surrounding proxies and gateways and allows the following functionality:
- SIP signaling responses can travel the same path as SIP signaling requests.
- Subsequent signaling requests can travel directly to the endpoint (destination gateway).
- Media endpoints can exchange data between each other.
See the figure below for a sample topology that displays these functionalities.
| Figure 1 | Cisco IOS Firewall for SIP Awareness Sample Topology |
SIP Message Treatment by the Firewall
See the table below for information on the treatment of SIP methods by the Cisco IOS firewall.
| Table 3 | Treatment of SIP Methods by the Cisco IOS Firewall |
| SIP Message |
Purpose |
|---|---|
| 200 OK |
Signifies the end of the call creation phase. The packet is checked for validity against the call database, and the contact information of the server is taken from it. Temporary call-flow-based openings in the firewall are created for allowing the BYE message, which can be initiated from the inside or outside. |
| 200 OK for BYE |
Signifies the graceful termination of the call and is in response to the BYE message. The same action as the CANCEL message is taken. |
| ACK |
Signifies that the message is passed after checking for validity. |
| BYE |
Signifies the intent to terminate the call. The database state is updated and temporary openings in the firewall are created for response to the BYE message. |
| CANCEL |
Signifies abnormal data termination. The signaling sessions, media sessions, pregenerated temporary openings in the firewall, and the call database entry for the call are removed. |
| INVITE |
Occurs typically at the start of the call. The firewall will create a database entry upon receipt of this method and fill the database with relevant information extracted from this message. Temporary openings in the firewall will allow for a series of responses to the INVITE request. The temporary openings will be call-flow sensitive and will allow for responses for a fixed amount of time (t = 30 secs). |
| NO MATCH |
Signifies a signaling message that is not present in the database. |
| Other Methods |
Signifies that the message is passed if the call ID is present in the call database. |
| REGISTER |
Results in the creation of an entry in the call database. Time-based, flow-control ACL firewall openings will allow for the response to the REGISTER and subsequent INVITE messages. |
| SESSION PROGRESS |
Contains a response to the INVITE message, and it is a packet during the call creation phase. The packet is checked against the call database for validity of call ID and the media ports; the server proxy information is gathered from the packet. Media channels should be created in this phase. |
Call Database
A call database, which contains the details of a call leg, is maintained for all call flows. A call database is created and maintained because there can be numerous signaling sessions for each call. The table below identifies the information available in the call database.
| Table 4 | Call Database Information |
| Type |
Purpose |
|---|---|
| call_int_over |
Checks to see whether or not call initialization is over, and if so, checks to see of the call is in the teardown phase |
| C con ip & C con port |
Signifies the IP address and port in the contact field of the initiator; for example, "Contact:<sip:1111@172.16.0.3:5060;user=phone>" |
| C media ip & C media port |
Signifies the IP address in the media field of the initiator; for example, "c=IN IP4 172.16.0.3" |
| C media port |
Signifies the port in the media field of the initiator; for example, "m=audio 20758 RTP/AVP 0" |
| C src ip & C src port |
Signifies the actual IP address and port of the initiator |
| C via ip & C via port |
Signifies the IP address and port in the via field of the initiator (the first via line); for example, "Via: SIP/2.0/UDP 172.16.0.3:5060" |
| current sip state |
Is the current state of the call (which helps to avoid retransmission) |
| from/to/callid |
Is extracted from the "INVITE" SIP request message to identify the call |
| media header |
Keeps the list of media sessions for the call |
| media opened |
Signifies multiple messages that may have media information, so you need to check to see whether or not the media has been opened for the call |
| prev sip state |
Signifies the previous state of the call (which helps to avoid retransmission) |
| S con ip & S con port |
Signifies the IP address and port in the contact field for the responder |
| S media ip |
Signifies the IP address in the media field for the responder |
| S media port |
Signifies the port in the media field for the responder |
| S src ip & S src port |
Signifies the actual IP address and port of the responder |
| S via ip & S via port |
Signifies the IP address and port in the via field for the responder |
| signal header |
Keeps the list of signaling sessions for the call |
| sip_proxy_traversed |
Makes the firewall topologically aware of whether the call has traversed through proxies |
How to Configure Your Firewall for SIP
- Configuring Firewall for SIP Support
- Verifying Firewall for SIP Support
- Monitoring Firewall for SIP Support
Configuring Firewall for SIP Support
To enable a firewall to support SIP, use the following commands.
Before you configure Cisco IOS firewall support for SIP on your router, you first need to configure access lists, whose purpose normally is to block SIP traffic from unprotected networks for which the firewall will create temporary openings for specific traffic.
DETAILED STEPS
Verifying Firewall for SIP Support
To verify Cisco IOS firewall session information, perform the following optional steps:
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
|
|
Example: Router> enable |
Enables privileged EXEC mode.
|
|
|
Example: Router# show ip inspect name voip |
(Optional) Displays the configured inspection rule. |
|
|
Example: Router# show ip inspect session |
(Optional) Displays existing sessions that are currently being tracked and inspected by the Cisco IOS firewall.
|
|
|
Example: Router# show ip access-list |
(Optional) Displays the contents of all current IP access lists. |
Monitoring Firewall for SIP Support
To monitor firewall events, perform the following optional steps:
 Note |
Effective with Cisco IOS Release 12.4(20)T, the debug ip inspect command is replaced by the debug policy-firewall command. See the Cisco IOS Debug Command Reference for more information. |
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
|
|
Example: Router> enable |
Enables privileged EXEC mode.
|
|
|
Example: Router# debug ip inspect sip |
(Optional) Displays the operations of the SIP inspection engine for debugging purposes. |
Configuration Examples for Firewall SIP Support
Example Firewall and SIP Configuration
The following example shows how to allow outside initiated calls and internal calls. For outside initiated calls, an ACL needs to be punched to allow for the traffic from the initial signaling packet from outside. Subsequent signaling and media channels will be allowed by the inspection module.
ip inspect name voip sip interface FastEthernet0/0 ip inspect voip in ! ! interface FastEthernet0/1 ip inspect voip in ip access-group 100 in ! ! access-list 100 permit udp host <gw ip> any eq 5060 access-list 100 permit udp host <proxy ip> any eq 5060 access-list deny ip any any
Additional References
Related Documents
| Related Topic |
Document Title |
|---|---|
| Cisco IOS firewall information and configuration tasks |
"Configuring Context-Based Access Control" |
| Cisco IOS firewall commands |
Cisco IOS Security Command Reference |
Standards
| Standards |
Title |
|---|---|
| None |
-- |
MIBs
| MIBs |
MIBs Link |
|---|---|
| None |
To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL: |
RFCs
| RFCs1 |
Title |
|---|---|
| RFC 2543 |
SIP: Session Initiation Protocol |
Technical Assistance
| Description |
Link |
|---|---|
| The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password. |
Feature Information for Firewall SIP Support
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
| Table 5 | Feature Information for Firewall SIP Support |
| Feature Name |
Releases |
Feature Information |
|---|---|---|
| Firewall SIP Support |
12.2(11)YU 12.2(15)T |
The Firewall Support for SIP feature integrates Cisco IOS firewalls, Voice over IP (VoIP) protocol, and Session Initiation Protocol (SIP) within a Cisco IOS-based platform, enabling better network convergence. The following commands were introduced or modified: debug ip inspect, ip inspect name. |
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
 Feedback
Feedback