Extending the Cisco ACI Fabric to the Public Cloud
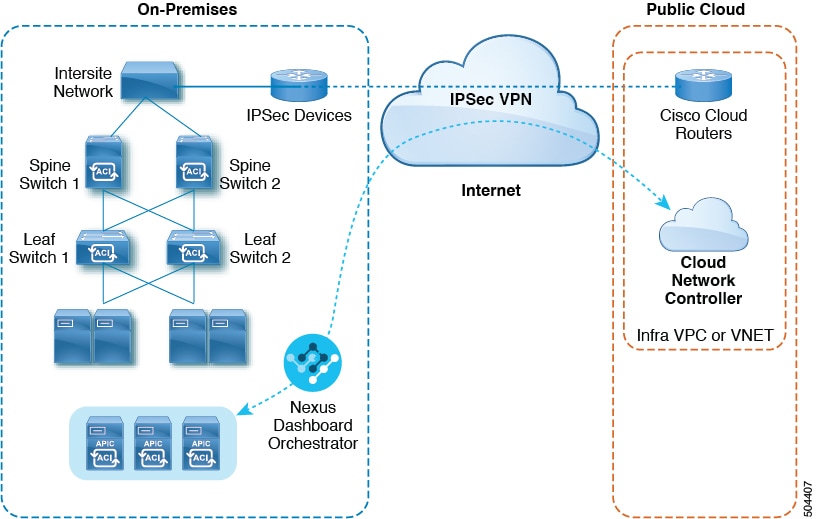
Cisco Application Centric Infrastructure (ACI) customers who own a private cloud sometimes may run part of their workload on a public cloud. However, migrating the workload to the public cloud requires working with a different interface and learning different ways to set up connectivity and define security policies. Meeting these challenges can result in increased operational cost and loss of consistency.
Cisco ACI can use Cisco Cloud Network Controller to extend a multi-site fabric to Amazon Web Services (AWS), Microsoft Azure, and Google Cloud public clouds.
What Cisco Cloud Network Controller Is
Cisco Cloud Network Controller is a software component of Cisco APIC that can be deployed on a cloud-based virtual machine (VM). Cisco Cloud Network Controller provides the following features:
-
Provides an interface that is similar to the existing Cisco APIC to interact with the Amazon AWS, Microsoft Azure, or Google Cloud public clouds.
-
Automates the deployment and configuration of cloud connectivity.
-
Configures the cloud router control plane.
-
Configures the data path between the on-premises Cisco ACI fabric and the cloud site.
-
Translates Cisco ACI policies to cloud native policies.
-
Discovers endpoints.
How Users Can Benefit from Cisco ACI Extension to the Public Cloud
Cisco Cloud Network Controller is a key part of Cisco ACI extension to the public cloud. Cisco Cloud Network Controller provides consistent policy, security, and analytics for workloads deployed either on or across on-premises data centers and the public cloud.
Cisco ACI extension to the public cloud also provides an automated connection between on-premises data centers and the public cloud with easy provisioning and monitoring. It also provides a single point for managing, monitoring, and troubleshooting policies across on-premises data centers and the public cloud or between cloud sites.
Azure Government Support
Cisco Cloud Network Controller supports Azure Government for on-premises-to-cloud connectivity (Hybrid-Cloud and Hybrid Multi-Cloud), cloud site-to-cloud site connectivity (Multi-Cloud), and single-cloud configurations (Cloud First).
Cisco Cloud Network Controller supports the following Azure Government regions:
-
US DoD Central
-
US DoD East
-
US Gov Arizona
-
US Gov Texas
-
US Gov Virginia

 Feedback
Feedback