- Introduction
- ?
- aaa accounting commands
- aaa authentication attempts
- aaa authentication enable default
- aaa authentication login default
- accelerate-packet-drops
- access-list
- application slot replace force completion
- asymmetric-l2-support
- attack-detector default
- attack-detector
- attack-detector number
- attack-detector tcp-port-list | udp-port-list
- attack-filter
- attack-filter dont-filter | force-filter
- attack-filter subscriber-notification ports
- auto-negotiate
- bandwidth
- blink
- boot system
- calendar set
- cd
- cdp enable
- cdp holdtime
- cdp mode
- cdp run
- cdp timer
- clear arp-cache
- clear cdp counters
- clear cdp table
- clear diameter counters
- clear diameter Gx counters
- clear diameter Gy counters
- clear interface linecard counters
- clear interface linecard flow-filter
- clear interface linecard mac-resolver arp-cache
- clear interface linecard subscriber anonymous all
- clear interface linecard subscriber db counters
- clear interface linecard traffic-counter
- clear interface linecard vpn
- clear interface range
- clear logger
- clear management-agent notifications counters
- clear rdr-formatter
- clear scmp name counters
- clock read-calendar
- clock set
- clock summertime
- clock timezone
- clock update-calendar
- configure
- connection-mode
- copy
- copy ftp://
- copy-passive
- copy running-config startup-config
- copy source-file ftp://
- copy source-file startup-config
- copy startup-config destination-file
- default subscriber template all
- delete
- diameter
- diameter Gx
- diameter Gx failure-grace-time
- diameter Gx PCRF-connection-failure-grace-time
- diameter Gx tx-timer
- diameter Gy send-attributes
- diameter Gy charging-id-mapping
- diameter Gy subscriber-attribute-mapping
- diameter Gy tx-timer
- diameter origin-realm
- diameter peer
- diameter port
- diameter realm
- diameter realm forwarding-mode
- diameter tx-timer
- dir
- disable
- do
- duplex
- enable
- enable password
- end
- erase startup-config-all
- exit
- external-bypass
- failure-recovery operation-mode
- flow-capture
- flow-capture controllers
- force failure-condition
- help
- history
- history size
- hostname
- interface gigabitethernet
- interface linecard
- interface range gigabitethernet (SCE8000 GBE only)
- interface range tengigabitethernet
- interface tengigabitethernet
- ip access-class
- ip address
- ip advertising
- ip default-gateway
- ip domain-lookup
- ip domain-name
- ip ftp password
- ip ftp username
- ip host
- ip name-server
- ip radius-client retry limit
- ip route
- ip rpc-adapter
- ip rpc-adapter port
- ip rpc-adapter security-level
- ip ssh
- ip ssh key
- ip-tunnel gre skip
- ip-tunnel dscp-marking-skip
- ip-tunnel ipinip skip
- ip-tunnel l2tp skip
- l2tp identify-by
- line vty
- link failure-reflection
- link mode
- logger add-user-message
- logger device
- logger device user-file-log max-file-size
- logger get support-file
- logger get user-log file-name
- logout
- mac-resolver arp
- management-agent sce-api ignore-cascade-violation
- management-agent sce-api logging
- management-agent sce-api timeout
- management-agent system
- mkdir
- more
- more user-log
- mpls
- no subscriber
- no subscriber mappings included-in
- periodic-records aggregate-by-cpu
- ping
- pqi install file
- pqi rollback file
- pqi uninstall file
- pqi upgrade file
- pwd
- queue
- rdr-formatter category number
- rdr-formatter destination
- rdr-formatter destination protocol netflowv9 template data timeout
- rdr-formatter forwarding-mode
- rdr-formatter history-size
- rdr-formatter protocol netflowv9 dscp
- rdr-formatter rdr-mapping
- reload
- reload shutdown
- rename
- rmdir
- salt
- sce-url-database add-entry
- sce-url-database import
- sce-url-database protection
- sce-url-database remove-all
- scmp
- scmp keepalive-interval
- scmp loss-of-sync-timeout
- scmp name
- scmp reconnect-interval
- scmp subscriber force-single-sce
- scmp subscriber id append-to-guid
- scmp subscriber send-session-start
- script capture
- script print
- script run
- script stop
- service-bandwidth-prioritization-mode
- service password-encryption
- service rdr-formatter
- service telnetd
- show access-lists
- show blink
- show calendar
- show cdp
- show cdp entry
- show cdp neighbors
- show cdp traffic
- show clock
- show diameter
- show diameter forwarding-mode
- show diameter Gx
- show diameter Gy
- show diameter Gy charging-id-mapping
- show diameter peer
- show diameter peer-table
- show diameter realm
- show diameter routing table
- show environment all
- show environment cooling
- show environment power
- show environment temperature
- show environment voltage
- show failure-recovery operation-mode
- show hostname
- show hosts
- show interface gigabitethernet
- show interface linecard
- show interface linecard accelerate-packet-drops
- show interface linecard application
- show interface linecard asymmetric-l2-support
- show interface linecard asymmetric-routing-topology
- show interface linecard attack-detector
- show interface linecard attack-filter
- show interface linecard cascade connection-status
- show interface linecard cascade peer-sce-information
- show interface linecard cascade redundancy-status
- show interface linecard connection-mode
- show interface linecard counters
- show interface linecard duplicate-packets-mode
- show interface linecard external-bypass
- show interface linecard flow-capture
- show interface linecard flow-open-mode
- show interface linecard ip-tunnel
- show interface linecard ip-tunnel ipinip
- show interface linecard ipv6
- show interface linecard l2tp
- show interface linecard link mode
- show interface linecard link-to-port-mapping
- show interface linecard mac-mapping
- show interface linecard mac-resolver arp
- show interface linecard periodic-records aggregation
- show interface linecard physically-connected-links
- show interface linecard sce-url-database
- show interface linecard sce-url-database protection
- show interface linecard service-bandwidth-prioritization-mode
- show interface linecard shutdown
- show interface linecard silent
- show interface linecard subscriber
- show interface linecard subscriber aging
- show interface linecard subscriber anonymous
- show interface linecard subscriber anonymous-group
- show interface linecard subscriber db counters
- show interface linecard subscriber mapping
- show interface linecard subscriber max-subscribers
- show interface linecard subscriber name
- show interface linecard subscriber name breach-state
- show interface linecard subscriber name bucket-state
- show interface linecard subscriber name bucket-state id
- show interface linecard subscriber properties
- show interface linecard subscriber sm-connection-failure
- show interface linecard subscriber templates
- show interface linecard tos-marking
- show interface linecard traffic-counter
- show interface linecard traffic-rule
- show interface linecard virtual-links
- show interface linecard vlan
- show interface linecard vpn
- show interface linecard wap
- show interface tengigabitethernet
- show inventory
- show ip access-class
- show ip advertising
- show ip default-gateway
- show ip filter
- show ip radius-client
- show ip route
- show ip rpc-adapter
- show ip ssh
- show line vty
- show log
- show logger device
- show management-agent
- show management-agent sce-api quota
- show pqi file
- show pqi last-installed
- show processes cpu
- show rdr-formatter
- show rdr-formatter connection-status
- show rdr-formatter counters
- show rdr-formatter destination
- show rdr-formatter enabled
- show rdr-formatter forwarding-mode
- show rdr-formatter history-size
- show rdr-formatter protocol netflowv9 dscp
- show rdr-formatter rdr-mapping
- show rdr-formatter statistics
- show running-config
- show scmp
- show snmp
- show snmp community
- show snmp contact
- show snmp enabled
- show snmp host
- show snmp location
- show snmp mib
- show snmp traps
- show sntp
- show startup-config
- show sub-attribute configuration
- show sub-attribute dictionary
- show system operation-status
- show system-uptime
- show tacacs
- show telnet sessions
- show telnet status
- show timezone
- show users
- show version
- show version all
- show version software
- silent
- snmp-server
- snmp-server community
- snmp-server contact
- snmp-server enable traps
- snmp-server host
- snmp-server interface
- snmp-server location
- sntp broadcast client
- sntp server
- sntp update-interval
- speed
- sub-attribute add-attribute
- subscriber aging
- subscriber anonymous-group export csv-file
- subscriber anonymous-group import csv-file
- subscriber anonymous-group name ip-range
- subscriber capacity-options
- subscriber export csv-file
- subscriber import csv-file
- subscriber max-subscribers
- subscriber name property name
- subscriber sm-connection-failure
- subscriber template export csv-file
- subscriber template import csv-file
- tacacs-server host
- tacacs-server key
- tacacs-server timeout
- telnet
- timeout
- tracert
- traffic-counter
- traffic-rule
- traffic-side (SCE8000 10G platform only)
- unzip
- username
- username privilege
- virtual-links index direction
- vlan
- wap
CLI Command Reference
Introduction
This chapter contains all of the CLI commands available on the SCE8000 platform at the admin authorization level or lower.
Each command description includes the information shown in Table 2-1.
Syntax and Conventions
The CLI commands are written in the following format:
command required-parameter [optional-parameter]
no is an optional parameter that may appear before the command name.
When entering commands, you may enclose parameters in quotation marks, and you must do so when a parameter name includes a space.
?
Lists all of the commands available for the current command mode. You can also use the ? command to obtain specific information about a keyword or argument.
To display a list of commands that begin with a particular character string, enter the abbreviated command entry immediately followed by a question mark (?). This form of help is called partial help, because it lists only the commands that begin with the abbreviation you entered.
?
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
All
Usage Guidelines
To list a command's associated keywords or arguments, enter a question mark (?) in place of a keyword or argument on the command line. This form of help is called argument help because it lists the keywords or arguments that apply based on the command, keywords, and arguments you have already entered.
Examples
The following example shows how to request help using the ? wildcard:
SCE(config)#ip ?
default-gateway Sets the default gateway
domain-lookup Enables the IP DNS-based host name-to-address translation
domain-name Define a default domain name
host Add a host to the host table
name-server Specify the address of one or more name servers to use for name and
address resolution route Add IP routing entry SCE(config)#ip d? default-gateway domain-lookup domain-name SCE(config)#ip de? default-gateway SCE(config)#ip de
aaa accounting commands
Enables TACACS+ accounting.
To disable TACACS+ accounting, use the no form of this command.
aaa accounting commands level default stop-start group tacacs+
no aaa accounting commands level default
Syntax Description
Defaults
TACACS+ accounting is disabled.
Command Modes
Global Configuration
Usage Guidelines
If TACACS+ accounting is enabled, the SCE platform sends an accounting message to the TACACS+ server after every command execution. The accounting message is logged in the TACACS+ server for use by the network administrator.
The start-stop keyword (required) indicates that the accounting message is sent at the beginning and the end (if the command was successfully executed) of the execution of a CLI command.
Authorization: admin
Examples
The following example shows how to enable TACACS+ accounting for the admin privilege level (10):
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)# aaa accounting commands 10 default stop-start group tacacs+
SCE(config)#
Related Commands
aaa authentication attempts
Specifies the number of login attempts allowed before a Telnet session is terminated.
aaa authentication attempts login [number-of-attempts]
Syntax Description
login number-of- attempts |
Maximum number of login attempts that will be permitted before the Telnet session is terminated. |
Defaults
The default number of authentication attempts is 3.
Command Modes
Global Configuration
Usage Guidelines
The maximum number of login attempts is relevant only for Telnet sessions. From the local console, the number of retries is unlimited.
Authorization: admin
Examples
The following example shows how to set the maximum number of login attempts to 5:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)# aaa authentication attempts login 5 SCE(config)#
Related Commands
aaa authentication enable default
Specifies which privilege level authentication methods are to be used, and in what order of preference.
To delete the privilege level authentication methods list, use the no form of this command.
aaa authentication enable default method1 [method2...]
no aaa authentication enable default
Syntax Description
method1... |
Privilege level authentication methods to be used. You may specify up to four different methods, in the order in which they are to be used. See Usage Guidelines for more information. |
Defaults
The default privilege level authentication method is enable.
Command Modes
Global Configuration
Usage Guidelines
Use this command to configure "backup" privilege level authentication methods to be used if the primary privilege level authentication method fails. The following methods are available:
•![]() group tacacs+—Use TACACS+ authentication.
group tacacs+—Use TACACS+ authentication.
•![]() local—Use the local username database for authentication.
local—Use the local username database for authentication.
•![]() enable (default)—Use the enable password for authentication.
enable (default)—Use the enable password for authentication.
•![]() none—Use no authentication.
none—Use no authentication.
If the privilege level authentication methods list is deleted, the default privilege level authentication method only (enable password) is used. TACACS+ authentication is not used.
Authorization: admin
Examples
The following example shows how to configure privilege level authentication methods:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)# aaa authentication enable default group tacacs+ enable none SCE(config)#
Related Commands
aaa authentication login default
Specifies which login authentication methods are to be used, and in what order of preference.
To delete the login authentication methods list, use the no form of this command.
aaa authentication login default method1 [method2...]
no aaa authentication login default
Syntax Description
method1... |
Login authentication methods to be used. You may specify up to four different methods, in the order in which they are to be used. See Usage Guidelines for more information. |
Defaults
The default login authentication method is enable.
Command Modes
Global Configuration
Usage Guidelines
Use this command to configure "backup" login authentication methods to be used if the primary login authentication method fails. The following methods are available:
•![]() group tacacs+—Use TACACS+ authentication.
group tacacs+—Use TACACS+ authentication.
•![]() local—Use the local username database for authentication.
local—Use the local username database for authentication.
•![]() enable (default)—Use the enable password for authentication.
enable (default)—Use the enable password for authentication.
•![]() none—Use no authentication.
none—Use no authentication.
If the login authentication methods list is deleted, the default login authentication method only (enable password) is used. TACACS+ authentication is not used.
Authorization: admin
Examples
The following example shows how to configure login authentication methods:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)# aaa authentication login default group tacacs+ enable none SCE(config)#
Related Commands
accelerate-packet-drops
Enables drop-wred-packets-by-hardware mode. This mode improves performance, but prevents the application from being able to count all dropped packets.
To disable drop-wred-packets-by-hardware mode, enabling the software to count all dropped packets (at the expense of some loss of performance), use the no form of this command.
accelerate-packet-drops
no accelerate-packet-drops
Syntax Description
This command has no arguments or keywords.
Defaults
This command (drop-wred-packets-by-hardware mode) is enabled.
Command Modes
Linecard Interface Configuration
Usage Guidelines
By default, the SCE platform hardware drops WRED packets (packets that are marked to be dropped due to bandwidth-control criteria). However, dropping these packets might be a problem if you need to know the number of dropped packets per service.
You can disable drop-wred-packets-by-hardware mode. The application can then retrieve the number of dropped packets for every flow and provide better visibility into the exact number of dropped packets and their distribution.
Note that counting all dropped packets impacts system performance and therefore, by default, drop-wred-packets-by-hardware mode is enabled.

Note ![]() The MIB object tpTotalNumWredDiscardedPackets counts dropped packets. The value in this counter is absolute only in no accelerate-packet-drops mode. When in accelerate-packet-drops mode (the default mode), this MIB counter provides only a relative value indicating the trend of the number of packet drops, with a factor of approximately 1:6.
The MIB object tpTotalNumWredDiscardedPackets counts dropped packets. The value in this counter is absolute only in no accelerate-packet-drops mode. When in accelerate-packet-drops mode (the default mode), this MIB counter provides only a relative value indicating the trend of the number of packet drops, with a factor of approximately 1:6.
Authorization: admin
Examples
The following example shows how to disable drop-wred-packets-by-hardware mode so that the application can count all dropped packets:
SCE>enable 10 password:<cisco> SCE#>config SCE(config)#interface linecard 0 SCE(config if)#no accelerate-packet-drops SCE(config if)#
Related Commands
|
|
|
show interface linecard accelerate-packet-drops |
Displays the currently configured hardware packet drop mode. |
access-list
Adds an entry to the bottom of the specified access list.
To remove an entry from the specified access list, use the no form of this command.
access-list number permission address
no access-list number
Syntax Description
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
The SCE platform can be configured with access control lists (ACLs), which are used to permit or deny incoming connections on any of the management interfaces. An access control list is an ordered list of entries, each consisting of the following elements:
•![]() Permit/deny field
Permit/deny field
•![]() IP address
IP address
•![]() Optional wildcard "mask" defining an IP address range
Optional wildcard "mask" defining an IP address range
The order of the entries in the list is important. The default action of the first entry that matches the connection is used. If no entry in the access list matches the connection, or if the access list is empty, the default action is deny. Table 2-2 lists valid permission values.
Authorization: admin
Examples
The following example adds entries to the bottom of access-list 1. The first entry permits access to 10.1.1.0 to 10.1.1.255. The second entry denies access to any address. Together, this list allows access only to addresses 10.1.1.*.
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#access-list 1 permit 10.1.1.0 0.0.0.255 SCE(config)#access-list 1 deny any SCE(config)#
The following example defines access-list 2, a list that denies access to all IP addresses in the range 10.1.2.0 to 10.1.2.255, permits access to all other addresses in the range 10.1.0.0 to 10.1.15.255, and denies access to all other IP addresses. Note that, because the first range is contained within the second range, the order of entries is important. If they had been entered in the opposite order, the deny entry would not have any effect.
SCE>enable 10 Password:<cisco> SCE#config SCE (config)#access-list 2 deny 10.1.2.0 0.0.0.255 SCE (config)#access-list 2 permit 10.1.0.0 0.0.15.255 SCE(config)#
Related Commands
|
|
|
ip access-class |
Specifies which access control list (ACL) controls global access to the SCE platform. |
show access-lists |
Displays all access lists or a specific access list. |
application slot replace force completion
Forces the current application replace process to complete and immediately start finalization (killing all old flows).
application slot slot-number replace force completion
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to force the application replace operation to complete immediately:
SCE>enable 10 Password:<cisco> SCE#application slot 0 replace force completion SCE#
asymmetric-l2-support
Configures the system to treat flows as having asymmetric Layer 2 characteristics (including Ethernet, VLAN, and L2TP), for the purpose of packet injection.
To disable asymmetric L2 support, use the no form of this command.
asymmetric-l2-support
no asymmetric-l2-support
Syntax Description
This command has no arguments or keywords.
Defaults
Asymmetric Layer 2 support is disabled.
Command Modes
Linecard Interface Configuration
Usage Guidelines
You should enable asymmetric Layer 2 support when the following conditions apply for any flows:
•![]() Each direction of the flow has a different pair of MAC addresses.
Each direction of the flow has a different pair of MAC addresses.
•![]() The routers do not accept packets with the MAC address of the other link.
The routers do not accept packets with the MAC address of the other link.

Note ![]() "Asymmetric routing topology" support and "asymmetric tunneling support" are two separate features. Asymmetric routing topology refers to topologies where the SCE platform might see some flows only in one direction (upstream or downstream).
"Asymmetric routing topology" support and "asymmetric tunneling support" are two separate features. Asymmetric routing topology refers to topologies where the SCE platform might see some flows only in one direction (upstream or downstream).
Asymmetric tunneling support (asymmetric L2 support) refers to the ability to support topologies where the SCE platform sees both directions of all flows, but some of the flows may have different Layer 2 characteristics (such as MAC addresses, VLAN tags, and L2TP headers), which the SCE platform must specifically take into account when injecting packets into the traffic (such as in block and redirect operations).
Note as well that, to support asymmetric Layer 2, the SCE platform switches to asymmetric flow open mode, which impacts performance. This limitation is not the case for asymmetric routing topology.
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#configure
SCE(config)#interface linecard 0
SCE(config if)# asymmetric-L2-support
Related Commands
|
|
|
show interface linecard |
Displays information for a specific line card interface. |
attack-detector default
Defines default thresholds and attack handling action. If a specific attack detector is defined for a particular situation (protocol, attack direction, or side), the detector overrides the defaults.
To delete the user-defined defaults, use the no form of this command. The system defaults are used instead.
attack-detector default protocol protocol attack-direction attack-direction side side [action action] [open-flows open-flows] [ddos-suspected-flows ddos-suspected-flows] [suspected-flows-ratio suspected-flows-ratio] [notify-subscriber | dont-notify-subscriber] [alarm |noalarm]
no attack-detector default protocol protocol attack-direction attack-direction side side [action action] [open-flows open-flows] [ddos-suspected-flows ddos-suspected-flows] [suspected-flows- ratio suspected-flows-ratio]
Syntax Description
Defaults
The default attack detector uses the following default values:
•![]() Action—report
Action—report
•![]() Thresholds—varies according to the attack type
Thresholds—varies according to the attack type
•![]() Subscriber notification—disabled
Subscriber notification—disabled
•![]() Sending an SNMP trap—disabled
Sending an SNMP trap—disabled
Command Modes
Linecard Interface Configuration
Usage Guidelines
Use the attack-detector number command to configure a specific attack detector.
Authorization: admin
Examples
The following example shows how to configure a default attack detector for TCP flows from the attack source:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface LineCard 0 SCE(config if)#attack-detector default protocol TCP attack-direction attack-source side both action report open-flows 500 ddos-suspected-flows 75 suspected-flows-ratio 50 SCE(config if)#
The following example shows how to enable subscriber notification for the specified default attack detector:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface LineCard 0 SCE(config if)#attack-detector default protocol TCP attack-direction attack-source side both notify-subscriber SCE(config if)#
Related Commands
attack-detector
Enables the specified attack detector and assigns an access control list (ACL) to it.
attack-detector number access-list access-list
Syntax Description
number |
Number of the attack detector. |
access-list |
Number of the ACL containing the IP addresses selected by this detector. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Use the following commands to define the attack detector and the ACL:
•![]() attack-detector
attack-detector
•![]() access-list
access-list
Authorization: admin
Examples
The following example shows how to enable attack detector number 2 and assign ACL 8:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface LineCard 0 SCE(config if)#attack-detector 2 access-list 8 SCE(config if)#
Related Commands
attack-detector number
Configures a specific attack detector for a particular attack type (protocol, attack direction, or side) with the assigned number.
To configure the default attack detector for the specified attack type, use the default form of this command.
To delete the specified attack detector, use the no form of this command.
attack-detector number protocol {TCP | UDP | ICMP | other | all} [destination-port destination-port] attack-direction attack-direction side side [action action] [open-flows open-flows] [ddos-suspected-flows ddos-suspected-flows] [suspected-flows-ratio suspected-flows-ratio] [notify-subscriber | dont-notify-subscriber] [alarm | no-alarm]
no attack-detector number
attack-detector default protocol {TCP | UDP | ICMP | other | all} [destination-port destination-port] attack-direction attack-direction side side [action action] [open-flows open-flows] [ddos-suspected-flows ddos-suspected-flows] [suspected-flows-ratio suspected-flows-ratio] [notify-subscriber | dont-notify-subscriber] [alarm | no-alarm]
no attack-detector default protocol {TCP | UDP | ICMP | other | all} [destination-port destination-port] attack-direction attack-direction side side
default attack-detector {all | all-numbered}
default attack-detector number protocol {all | IMCP | other | TCP | UDP} [destination-port destination-port] attack-direction attack-direction side side
Syntax Description
Defaults
The default attack detector uses the following default values:
•![]() Action—report
Action—report
•![]() Thresholds—varies according to the attack type
Thresholds—varies according to the attack type
•![]() Subscriber notification—disabled
Subscriber notification—disabled
•![]() Sending an SNMP trap—disabled
Sending an SNMP trap—disabled
Command Modes
Linecard Interface Configuration
Usage Guidelines
If a specific attack detector is defined for a particular attack type, this detector overrides the configured default attack detector.
If the selected protocol is either TCP or UDP, specify whether destination ports are specific, not specific, or both. If the destination ports are specific, configure the ports using the attack-detector command.
To enable a configured attack detector, use the attack-detector command.
To configure a default attack detector, use the attack-detector default command.
Authorization: admin
Examples
The following example shows how to configure attack detector number 2:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface LineCard 0 SCE(config if)# attack-detector 2 protocol UDP dest-port not-specific attack-direction single-side-destination side both action block open-flows-rate 500 suspected-flows-rate 500 suspected-flows-ratio 50 notify-subscriber alarm SCE(config if)#
The following example shows how to delete attack detector number 2:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface LineCard 0 SCE(config if)#no attack-detector 2 SCE(config if)#
The following example shows how to disable subscriber notification for attack detector number 2:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface LineCard 0 SCE(config if)#attack-detector 2 protocol UDP dest-port not-specific attack-direction single-side-destination side both dont-notify-subscriber SCE(config if)#
Related Commands
attack-detector tcp-port-list | udp-port-list
Defines the list of destination ports for specific port detections for TCP or UDP protocols.
attack-detector number {tcp-port-list | udp-port-list} {all | port1 [port2...]}
Syntax Description
number |
Number of the attack detector for which this list of specific ports is relevant. |
port1 ... |
List of up to 15 specific port numbers. |
all |
Includes all ports in the list. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
TCP and UDP protocols may be configured for specified ports only (port-based). Use this command to configure the list of specified destination ports for each protocol. Up to 15 different TCP port numbers and 15 different UDP port numbers can be specified.
Configuring a TCP or UDP port list for an attack detector affects only those attack types that have the same protocol (TCP or UDP) and are port-based (that is, detect a specific destination port). Settings for other attack types are not affected by the configured port list.
Authorization: admin
Examples
The following example shows how to configure the destination port list for the TCP protocol for attack detector 10:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#interface LineCard 0
SCE(config if)#attack-detector 10 tcp-port-list 100 101 102 103
SCE(config if)#
Related Commands
attack-filter
Enables specific attack detection for a specified protocol and attack direction.
To disable attack detection, use the no form of this command.
attack-filter protocol {TCP | UDP | ICMP | other | all} [dest-port destination-port] attack-direction attack-direction
no attack-filter protocol {TCP | UDP | ICMP | other | all} [dest-port destination-port] attack-direction attack-direction
Syntax Description
Defaults
This command is enabled.
The default for protocol is all (no protocol specified).
The default for destination-port is both (port-based and port-less).
The default for attack-direction is all (all directions).
Command Modes
Linecard Interface Configuration
Usage Guidelines
Specific attack filtering is configured in two steps:
1. ![]() Enabling specific IP filtering for the particular attack type (using this command).
Enabling specific IP filtering for the particular attack type (using this command).
2. ![]() Configuring an attack detector for the relevant attack type (using the attack-detector numbercommand). Each attack detector specifies the thresholds that define an attack and the action to be taken when an attack is detected.
Configuring an attack detector for the relevant attack type (using the attack-detector numbercommand). Each attack detector specifies the thresholds that define an attack and the action to be taken when an attack is detected.
In addition, you can manually override the configured attack detectors to either force or prevent attack filtering in a particular situation (using the attack filter force filter | dont-filter command).
By default, specific IP detection is enabled for all attack types. You can configure specific IP detection to be enabled or disabled for a specific defined situation only, depending on the following options:
•![]() For a selected protocol only
For a selected protocol only
•![]() For TCP and UDP protocols, for only port-based or only port-less detections
For TCP and UDP protocols, for only port-based or only port-less detections
•![]() For a selected attack direction, either for all protocols or for a selected protocol
For a selected attack direction, either for all protocols or for a selected protocol
If the selected protocol is either TCP or UDP, specify whether the destination port is specific (port-based), not specific (port-less), or both. If the destination ports are specific, configure the ports using the attack-detector tcp-port-list | udp-port-listcommand.
Authorization: admin
Examples
The following example shows how to enable specific, dual-sided attack detection for TCP protocol only:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface LineCard 0 SCE(config if)#attack-filter protocol TCP dest-port specific attack-direction dual-sided SCE(config if)#
The following example shows how to enable single-sided attack detection for ICMP protocol only:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#interface LineCard 0
SCE(config if)# attack-filter protocol ICMP attack-direction single-side-source
SCE(config if)#
The following example shows how to disable attack detection for all protocols that are not TCP, UDP, or ICMP:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#interface LineCard 0
SCE(config if)#no attack-filter protocol other attack-direction all
SCE(config if)#
Related Commands
attack-filter dont-filter | force-filter
Prevents attack filtering for a specified IP address or protocol. If filtering is already in process, it will be stopped. When attack filtering has been stopped, it remains stopped until explicitly restored by another CLI command (either specific or general). To restore attack filtering, use the no form of this command.
The force-filter option forces attack filtering for a specified IP address or protocol. When attack filtering has been forced, it continues until explicitly stopped by another CLI command (either specific or general). To stop attack filtering, use the no form of this command.
attack-filter force-filter [action {block | report}] protocol {TCP | UDP | ICMP | other} [destination-port {port-number | not-specific}] attack-direction {single-side-source | single-side-destination | single-side-both} {ip ip-address | dual-sided source-ip ip-address destination-ip ip-address} side side
attack-filter dont-filter protocol {TCP | UDP | ICMP | other} [destination-port {port-number | not-specific}] attack-direction {single-side-source | single-side-destination | single-side-both} {ip ip-address | dual-sided source-ip ip-address destination-ip ip-address} side side
no attack-filter dont-filter protocol {TCP | UDP | ICMP | other} [destination-port {port-number | not-specific}] attack-direction {single-side-source | single-side-destination | single-side-both} {ip ip-address | dual-sided source-ip ip-address destination-ip ip-address} side side
no attack-filter force-filter protocol {TCP | UDP | ICMP | other} [destination-port {port-number | not-specific}] attack-direction {single-side-source | single-side-destination | single-side-both) {ip ip-address | dual-sided source-ip ip-address destination-ip ip-address} side side
no attack-filter force-filter all
no attack-filter dont-filter all
Syntax Description
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
After configuring the attack detectors, the SCE platform automatically detects attacks and handles them according to the configuration. However, to manually intervene (either for debugging purposes or because reconfiguring the SCE attack detectors properly would be difficult), you can use the CLI attack- filtering commands to:
•![]() Prevent or stop filtering of an attack related to a protocol, direction, and specified IP address
Prevent or stop filtering of an attack related to a protocol, direction, and specified IP address
•![]() Force filtering of an attack related to a protocol, direction, and specified IP address
Force filtering of an attack related to a protocol, direction, and specified IP address
Attack filtering can be prevented for a specified IP address or protocol by executing a dont-filter CLI command. If filtering is already in process, it will be stopped. When attack filtering has been stopped, it remains stopped until explicitly restored by another CLI command (either force-filter or no dont-filter).
Authorization: admin
Examples
The following example shows how to prevent attack filtering for the specified conditions:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#attack-filter dont-filter protocol other attack-direction single-side-source ip 10.10.10.10 side both SCE(config if)#
The following example shows how to restore all attack filtering:
SCE>enable 10 SCE#config SCE(config)#interface linecard 0 SCE(config if)#no attack-filter dont-filter all SCE(config if)# Password:<cisco>
The following example shows how to force attack filtering:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#attack-filter force-filter protocol TCP dest-port not-specific attack-direction dual-sided source-ip 10.10.10.10 destination-ip 20.20.20.20 side both SCE(config if)#
The following example shows how to stop all forced attack filtering:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#no attack-filter force-filter all SCE#
Related Commands
|
|
|
attack-filter |
Enables specific attack detection for a specified protocol and attack direction. |
attack-filter subscriber-notification ports
Specifies a port as a subscriber notification port. TCP traffic from the subscriber side to this port will never be blocked by the attack filter, leaving it always available for subscriber notification.
To remove the port from the subscriber notification port list, use the no form of this command.
attack-filter subscriber-notification ports port
no attack-filter subscriber-notification ports port
Syntax Description
port |
Port number. One port can be specified as the subscriber notification port. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
This command configures the port to be used for subscriber notification as configured using the attack-filter and attack-detector number commands.
Authorization: admin
Examples
The following example shows how to specify port 100 as the subscriber notification port:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#interface linecard 0
SCE(config if)#attack-filter subscriber-notification ports 100
SCE(config if)#
Related Commands
auto-negotiate
Configures GigabitEthernet interface auto-negotiation mode. Use this command to either enable or disable auto-negotiation.
To always have auto-negotiation disabled, regardless of the connection mode, use the no form of this command.
auto-negotiate
no auto-negotiate
default auto-negotiate
Syntax Description
This command has no arguments or keywords.
Defaults
Auto-negotiation is:
•![]() On for inline connection mode
On for inline connection mode
•![]() Off for receive-only connection mode
Off for receive-only connection mode
Command Modes
GigabitEthernet Interface Configuration
Usage Guidelines
Auto-negotiation does not work when the SCE platform is connected through an optical splitter (receive-only connection mode).
In the SCE8000 10GBE platform, auto-negotiation is supported by the GBE management interface only (1/1). The connection mode is not relevant to the management interface.
Authorization: admin
Examples
The following example shows how to configure all the GigabitEthernet line interfaces on the specified SPA to perform no auto-negotiation:
SCE_GBE>enable 10 Password:<cisco> SCE_GBE#config SCE_GBE(config)#interface range GigabitEthernet 3/0/0-7 SCE_GBE(config range if)#no auto-negotiate SCE_GBE(config range if)#
Related Commands
|
|
|
show interface gigabitethernet |
Displays the details of the GigabitEthernet management interface. |
bandwidth
Sets Ethernet shaping for the TenGigabitEthernet line interfaces.
bandwidth bandwidth burst-size burstsize
Syntax Description
bandwidth |
Bandwidth measured in kbps. |
burstsize |
Burst size in bytes. |
Defaults
The default bandwidth is 100000K (100 Mbps).
The default burst size is 5000 (5K bytes).
Command Modes
TenGigabitEthernet Interface Configuration
Usage Guidelines
This command is valid for a specified TenGigabitEthernet line interface only. It must be executed explicitly for each interface.
Authorization: admin
Examples
The following example shows how to set the bandwidth and burst size for the TenGigabitEthernet line interface 3/2/0:
SCE#config
SCE(config)#interface TenGigabitEthernet 3/2/0
SCE(config if)#bandwidth 100000 burstsize 5000
SCE(config if)#
Related Commands
|
|
|
interface tengigabitethernet |
Displays the details of a TenGigabitEthernet interface. |
queue |
Sets the queue shaping. |
blink
Blinks a slot LED for visual identification.
To stop slot blinking, use the no form of this command.
blink slot slot-number
no blink slot slot-number
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
Not blinking
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to configure the SCE platform to stop blinking:
SCE>enable 10 Password:<cisco> SCE#no blink slot 0 SCE#
Related Commands
|
|
|
show blink |
Displays the blinking status of a slot. |
boot system
Specifies a new package file to install. The SCE platform extracts the actual image files from the specified package file only during the copy running-config startup-config command.
boot system ftp://username[:password]@server-address[:port]/path/source-file destination-file
no boot system
Syntax Description
ftp://...destination-file |
FTP site and path of a package file that contains the new firmware. The filename should end with the .pkg file type. |
Defaults
The FTP site and path of a package file that contains the new firmware. The filename should end with the .pkg file type.
Command Modes
Global Configuration
Usage Guidelines
Use this command to upgrade the SCE platform embedded firmware. The package file is verified for the system and checked that it is not corrupted. The actual upgrade takes place only after executing the copy running-config startup-config command and rebooting the SCE platform.
Authorization: admin
Examples
The following example shows how to upgrade the system:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#boot system ftp://user:1234@10.10.10.10/downloads/SENum.pkg.pkg Verifying package file... Package file verified OK. SCE(config)#do copy running-config startup-config Backing -up configuration file... Writing configuration file... Extracting new system image... Extracted OK.
Related Commands
|
|
|
copy running-config startup-config |
Builds a configuration file with general configuration commands called config.txt, which is used in successive boots. |
calendar set
Sets the system calendar. The calendar is a system clock that continues functioning even when the system shuts down.
calendar set hh:mm:ss day month year
Syntax Description
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Always coordinate between the calendar and clock by using the clock read-calendar command after setting the calendar.
Authorization: admin
Examples
The following example shows how to set the calendar to 20 minutes past 10 a.m., January 13, 2006, synchronize the real-time clock to the calendar time, and display the result:
SCE>enable 10 Password:<cisco> SCE#calendar set 10:20:00 13 jan 2006 SCE#clock read-calendar SCE#show calendar 10:20:03 UTC THU January 13 2006 SCE#show clock 10:20:05 UTC THU January 13 2006 SCE#
Related Commands
cd
Changes the path of the current working directory.
cd new-path
Syntax Description
new-path |
Path name of the new directory. This name can be either a full path or a relative path. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
The new path should already have been created in the local flash file system.
Authorization: admin
Examples
The following example shows how to display the current directory (root directory) and then change the directory to the log directory located under the root directory:
SCE>enable 10 Password:<cisco> SCE>enable 10 SCE#pwd system SCE#cd log SCE#pwd system:log SCE#
Related Commands
|
|
|
pwd |
Displays the current working directory. |
mkdir |
Creates a new directory. |
cdp enable
Enables Cisco Discovery Protocol (CDP) on a specific traffic interface. Use the no form of the command to disable CDP on a specific interface.
CDP is not supported on management interfaces.
cdp enable
no cdp enable
Syntax Description
This command has no arguments or keywords.
Defaults
By default, CDP is enabled on all traffic interfaces.
Command Modes
SCE8000 GBE: GigabitEthernet Interface Configuration (traffic interfaces only)
SCE8000 10G: TenGigabitEthernet Interface Configuration
Usage Guidelines
By default, CDP is enabled on all traffic interfaces. CDP must be enabled globally on the SCE8000 platform (cdp run command) in order to enable a specific interface.

Tip ![]() For consistent CDP operation, it is recommended that both ports of any one traffic link be either enabled or disabled.
For consistent CDP operation, it is recommended that both ports of any one traffic link be either enabled or disabled.
Authorization: admin
Examples
The following example illustrates how to disable CDP on both 10 Gigabit Ethernet traffic interfaces of the first traffic link on an SCE8000 10G platform.
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#interface range TenGigabitEthernet 3/0-1/0
SCE(config if range)#no cdp enable
Related Commands
|
|
|
|---|---|
cdp mode |
|
cdp run |
|
show cdp |
cdp holdtime
Specifies the amount of time the receiving device should hold a Cisco Discovery Protocol (CDP) packet from your router before discarding it.
Use either the no or the default form of the command to restore the holdtime to the default value (180 seconds).
cdp holdtime seconds
no cdp holdtime
default cdp holdtime
Syntax Description
seconds |
Hold time value to be sent in the CDP update packets in seconds. |
Defaults
180 seconds
Command Modes
Global Configuration
Usage Guidelines
CDP packets are sent with a time to live, or hold time, value. The receiving device will discard the CDP information in the CDP packet after the hold time has elapsed.
You can set the hold time lower than the default setting of 180 seconds if you want the receiving devices to update their CDP information more rapidly.
The specified CDP hold time must be greater than the time between CDP transmissions, which is set using the cdp timer command.
Authorization: admin
Examples
The following example sets the CDP hold time to 60 seconds.
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#cdp holdtime 60
SCE(config)#
Related Commands
|
|
|
|---|---|
cdp run |
|
cdp enable |
|
cdp timer |
|
show cdp |
cdp mode
Sets the Cisco Discovery Protocol (CDP) mode on the SCE8000 platform.
To reset the CDP mode to the default mode (bypass) use the default form of the command.
cdp mode (standard | monitor | bypass)
default cdp mode
Syntax Description
Defaults
Bypass
Command Modes
Global Configuration
Usage Guidelines
The Cisco SCE8000 is usually installed as a bump-in-the-wire device, and therefore forwards packets (including CDP packets) from one interface to the corresponding interface, whereas a typical Cisco device never forwards CDP packets from one interface to another interface. Therefore, the Cisco SCE8000 extends the enabled state with three different CDP modes, allowing it to either function as a typical CDP device, or to only monitor the CDP packets, or to bypass them altogether.

Note ![]() When CDP is either not running or disabled at the interface level, CDP packets are discarded and CDP packets are not generated, regardless of the CDP mode.
When CDP is either not running or disabled at the interface level, CDP packets are discarded and CDP packets are not generated, regardless of the CDP mode.

Authorization: admin
Examples
The following example illustrates how to set the CDP to "standard" so that CDP functions on the SCE8000 platform like it does on a typical Cisco device.
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#cdp mode standard
SCE(config)#
Related Commands
|
|
|
|---|---|
cdp run |
|
cdp enable |
|
show cdp |
cdp run
Enables Cisco Discovery Protocol (CDP) globally on the SCE8000 platform. Use the no form of the command to disable CDP.
cdp run
no cdp run
Syntax Description
This command has no arguments or keywords.
Defaults
By default, CDP is enabled.
Command Modes
Global Configuration
Usage Guidelines
By default, CDP is enabled on the Cisco SCE8000. If you prefer not to use the CDP device discovery capability, use the no cdp run command to disable it.
By default, when CDP is enabled, it is enabled on all traffic interfaces. To disable CDP on a specific interface, use the no cdp enable command in interface configuration mode.

Note ![]() By default, when you enable CDP, it is set to bypass mode. To change the mode, use the cdp mode command.
By default, when you enable CDP, it is set to bypass mode. To change the mode, use the cdp mode command.
Authorization: admin
Examples
The following example illustrates how to disable CDP.
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#no cdp run
SCE(config)#
Related Commands
|
|
|
|---|---|
cdp mode |
|
cdp enable |
|
show cdp |
cdp timer
Specifies how often the SCE8000 platform sends Cisco Discovery Protocol (CDP) updates.
Use either the no or the default form of the command to restore the timer to the default value (60 seconds).
cdp timer
no cdp timer
default cdp timer
Syntax Description
seconds |
How often the SCE8000 platform sends CDP updates, in seconds. |
Defaults
60 seconds
Command Modes
Global Configuration
Usage Guidelines
Adjust the value to balance the advantage of more up-to-date CDP information with the increased bandwidth required for more frequent transmissions.
The specified CDP timer value must be less than the hold time value sent in the CDP updated packets, which is set using the cdp holdtime command.
Authorization: admin
Examples
The following example sets the timer value to 80 seconds.
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#cdp timer 80
SCE(config)#
Related Commands
|
|
|
|---|---|
cdp run |
|
cdp enable |
|
cdp holdtime |
|
show cdp |
clear arp-cache
Deletes all dynamic entries from the ARP cache. The Address Resolution Protocol (ARP) is a TCP/IP protocol that converts IP addresses to physical addresses. Dynamic entries are automatically added to and deleted from the cache during normal use. Entries that are not reused age and expire within a short period of time. Entries that are reused have a longer cache life.
clear arp-cache
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to clear the ARP cache:
SCE>enable 10 Password:<cisco> SCE#clear arp-cache SCE#
Related Commands
|
|
|
clear interface linecard mac-resolver arp-cache |
Clears all the MAC addresses in the MAC resolver database. |
clear cdp counters
Resets the Cisco Discovery Protocol (CDP) traffic counters to zero.
clear cdp counters
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example illustrates how to use this command. The show cdp traffic output shows that all of the traffic counters have been reset to zero.
SCE>enable 10 Password:<cisco> SCE#clear cdp counters
SCE#show cdp traffic
CDP counters:
Total packets output: 0, Input: 0
Hdr syntax: 0, Chksum error: 0, Encaps failed: 0
No memory: 0, Invalid packet: 0, Fragmented: 0
CDP version 1 advertisements output: 0, Input: 0
CDP version 2 advertisements output: 0, Input: 0
SCE#
Related Commands
|
|
|
|---|---|
clear cdp table |
|
show cdp traffic |
clear cdp table
Clears the table that contains Cisco Discovery Protocol (CDP) information about neighbors.
clear cdp table
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example illustrates how to use this command. The output of the show cdp neighbors command shows that all information has been deleted from the table.
SCE>enable 10 Password:<cisco> SCE#clear cdp table
SCE#show cdp neighbors
Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge
S - Switch, H - Host, I - IGMP
Device ID Local Intrfce Holdtme Capability Platform Port I
SCE#
Related Commands
|
|
|
|---|---|
clear cdp counters |
|
show cdp neighbors |
clear diameter counters
Resets all diameter stack message statistics.
clear diameter counters
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to use this command.
SCE>enable 10
Password:<cisco>
SCE#clear diameter counters SCE#
Related Commands
|
|
|
show diameter counters |
Displays stack message statistics. |
clear diameter Gx counters
Resets all Gx application message statistics.
clear diameter Gx counters
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to use this command.
SCE>enable 10
Password:<cisco>
SCE#clear diameter Gx counters SCE#
Related Commands
|
|
|
show diameter Gx counters |
Displays Gx message statistics. |
clear diameter Gy counters
Resets Gy application counters.
clear diameter Gy counters
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to use this command.
SCE>enable 10
Password:<cisco>
SCE#clear diameter Gy counters SCE#
Related Commands
|
|
|
show diameter Gy counters |
Displays Gy counters. |
clear interface linecard counters
Clears the line card interface counters.
clear interface linecard slot-number counters
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to clear the counters for line card 0:
SCE>enable 10 Password:<cisco> SCE#clear interface linecard 0 counters SCE#
Related Commands
|
|
|
show interface linecard counters |
Displays the hardware counters for the line card interface. |
clear interface linecard flow-filter
Clears all flow filter rules for the specified partition.
clear interface linecard slot-number flow-filter partition name name
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
name |
Name of the partition for which to clear the flow filter rules. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 15 Password:<cisco> SCE#>clear interface linecard 0 flow-filter partition name partition_1 SCE#>
Related Commands
|
|
|
show interface linecard flow-filter |
clear interface linecard mac-resolver arp-cache
Clears all the MAC addresses in the MAC resolver database.
clear interface linecard slot-number mac-resolver arp-cache
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#clear interface linecard 0 mac-resolver arp-cache SCE#
Related Commands
clear interface linecard subscriber anonymous all
Clears all anonymous subscribers in the system.
clear interface linecard slot-number subscriber anonymous all
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to clear all anonymous subscribers:
SCE>enable 10 Password:<cisco> SCE#clear interface linecard 0 subscriber anonymous all SCE#
Related Commands
clear interface linecard subscriber db counters
Clears the "total" and "maximum" subscriber database counters.
clear interface linecard slot-number subscriber db counters
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to clear all anonymous subscribers:
SCE>enable 10 Password:<cisco> SCE#clear interface linecard 0 subscriber db counters SCE#
Related Commands
|
|
|
show interface linecard subscriber db counters |
Displays the subscriber database counters. |
clear interface linecard traffic-counter
Clears the specified traffic counter.
clear interface linecard slot-number traffic-counter {name | all}
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
name |
Name of the traffic counter to be cleared. |
all |
Clears all traffic counters. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to clear the traffic counter named counter1:
SCE>enable 10 Password:<cisco> SCE#clear interface linecard 0 traffic-counter name counter1 SCE#
Related Commands
|
|
|
traffic-counter |
Defines a new traffic counter. |
show interface linecard traffic-counter |
Displays the specified traffic counter. |
\
clear interface linecard vpn
Removes VLAN VPNs that were created automatically by the SCE platform.
clear interface linecard slot-number vpn automatic
Syntax Description
slot-number |
The number of the identified slot. Enter a value of 0. |
Defaults
This command has no default settings.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example illustrates the use of this command.
SCE>enable 10 Password:<cisco> SCE#clear interface linecard 0 vpn automatic SCE#
Related Commands
|
|
|
clear interface range
Clears all the specified interfaces.
clear interface range interface-type [sce-id/]bay-range/interface-range
Syntax Description
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
The clear interface range command clears a group of interfaces with one command, with the limitation that all the interfaces in the group must be of the same physical and logical type.
•![]() For the SCE8000 10GBE platform, use the following command syntax:
For the SCE8000 10GBE platform, use the following command syntax:
clear interface range tengigabitethernet sce-id/bay-range/0
•![]() For the SCE8000 GBE platform traffic ports, use the following command syntax (the bay numbers are in the range of 0-1):
For the SCE8000 GBE platform traffic ports, use the following command syntax (the bay numbers are in the range of 0-1):
clear interface range gigabitethernet sce-id/bay-range/interface-range
•![]() For the SCE8000 GBE cascade ports, use the following command syntax (the bay numbers are in the range of 2-3):
For the SCE8000 GBE cascade ports, use the following command syntax (the bay numbers are in the range of 2-3):
clear interface range tengigabitethernet sce-id/bay-range/0
Authorization: admin
Examples
The following example shows how to clear all the traffic interfaces in SCE8000 platform 1 of a cascaded SCE8000 GBE system:
SCE>enable 10
Password:<cisco>
SCE#clear interface range gigabitethernet 1/0-1/0-7
SCE#
The following example shows how to clear the cascade interfaces in the same SCE8000 GBE platform:
SCE>enable 10
Password:<cisco>
SCE#clear interface range tengigabitethernet 1/2-3/0
SCE#
The following example shows how to clear all the interfaces in SCE8000 platform 1 of a cascaded SCE8000 10GBE system:
SCE>enable 10
Password:<cisco>
SCE#clear interface range tengigabitethernet 1/0-3/0
SCE#
Related Commands
|
|
|
show interface linecard counters |
Displays the hardware counters for the line card interface. |
clear logger
Clears the SCE platform logger (user log files). This operation erases the information stored in the user log files.
clear logger device {user-file-log | line-attack-file-log} [counters | nv-counters]
Syntax Description
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
The user log files have a size limit, with new entries overwriting the oldest entries, so you do not need to regularly clear the log files. Use this operation when you are certain that the information contained in the logs is irrelevant and might be confusing (for example, when reinstalling the system at a new site whose administrators do not need old information).
•![]() The counters keyword clears the counters of the SCE platform logger (user log files). These counters keep track of the number of info, warning, error, and fatal messages.
The counters keyword clears the counters of the SCE platform logger (user log files). These counters keep track of the number of info, warning, error, and fatal messages.
•![]() The nv-counters keyword clears the nonvolatile counters for the entire log or for only the specified SCE platform. These counters are not cleared during bootup, and must be cleared explicitly by using this command.
The nv-counters keyword clears the nonvolatile counters for the entire log or for only the specified SCE platform. These counters are not cleared during bootup, and must be cleared explicitly by using this command.
Authorization: admin
Examples
The following example shows how to clear the SCE platform user log file:
SCE>enable 10 Password:<cisco> SCE#clear logger device user-file-log Are you sure? Y SCE#
The following example shows how to clear the SCE platform user log file counters:
SCE>enable 10 Password:<cisco> SCE#clear logger device user-file-log counters Are you sure? Y SCE#
The following example shows how to clear the user log file nonvolatile counters:
SCE>enable 10 Password:<cisco> SCE#clear logger device user-file-log nv-counters Are you sure? Y SCE#
Related Commands
|
|
|
show logger device |
Displays the configuration of the specified SCE platform logger file. |
show log |
Displays the contents of the user log file. |
clear management-agent notifications counters
Clears the counters for the number of notifications sent to the management agent
clear management-agent notifications counters
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to clear the management agent notifications counters:
SCE>enable 10 Password:<cisco> SCE#clear management-agent notifications counters SCE#
Related Commands
|
|
|
clear rdr-formatter
Clears the RDR formatter counters and statistics.
clear rdr-formatter
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to clear the RDR formatter counters:
SCE>enable 10 Password:<cisco> SCE#clear rdr-formatter SCE#
Related Commands
|
|
|
show rdr-formatter counters |
Displays the RDR formatter counters. |
clear scmp name counters
Clears the counters for the specified SCMP peer device.
clear scmp name name counters
Syntax Description
name |
Name of the SCMP peer device. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to clear the counters for the SCMP peer device named device_1:
SCE>enable 10 Password:<cisco> SCE#clear scmp name device_1 counters SCE#
Related Commands
|
|
|
show scmp |
Displays the SCMP (ISG) general configuration and status. |
clock read-calendar
Synchronizes clocks by setting the system clock from the calendar.
clock read-calendar
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to update the system clock from the calendar:
SCE>enable 10 Password:<cisco> SCE#clock read-calendar SCE#
Related Commands
clock set
Manually sets the system clock.
clock set hh:mm:ss day month year
Syntax Description
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Always coordinate between the calendar and clock by using the clock update-calendar command after setting the clock.
Authorization: admin
Examples
The following example shows how to set the clock to 20 minutes past 10 p.m. on January 13, 2006:
SCE>enable 10 Password:<cisco> SCE#clock set 22:20:00 13 jan 2006 SCE#clock update-calendar SCE#show clock 22:21:10 UTC THU January 13 2006 SCE#show calendar 22:21:18 UTC THU January 13 2006 SCE#
Related Commands
clock summertime
Configures the SCE platform to automatically switch to daylight saving time on a specified date, and also to switch back to standard time. In addition, the time-zone code can be configured to vary with daylight saving time if required. (For example, in the eastern United States, standard time is designated as EST, and daylight saving time is designated as EDT).
To cancel the daylight saving time transitions configuration, use the no form of this command.
clock summertime
no clock summertime
Syntax Description
Defaults
For recurring configurations, offset is 60 minutes.
The following recurrent time changes are configured:
•![]() Daylight saving time begins at 2:00 (a.m.) on the second Sunday of March.
Daylight saving time begins at 2:00 (a.m.) on the second Sunday of March.
•![]() Daylight saving time ends at 2:00 (a.m.) on the first Sunday of November.
Daylight saving time ends at 2:00 (a.m.) on the first Sunday of November.
Command Modes
Global Configuration
Usage Guidelines
The format of the command varies somewhat, depending on how the dates for the beginning and end of daylight saving time are determined for the particular location:
•![]() If daylight saving time always begins and ends on the same day every year (recurring, as in the United States):
If daylight saving time always begins and ends on the same day every year (recurring, as in the United States):
–![]() Use the clock summertime recurring command.
Use the clock summertime recurring command.
–![]() Do not specify the year keyword.
Do not specify the year keyword.
•![]() If the start and end of daylight saving time is different every year (not recurring, as in Israel):
If the start and end of daylight saving time is different every year (not recurring, as in Israel):
–![]() Use the clock summertime command.
Use the clock summertime command.
–![]() Specify the year keyword.
Specify the year keyword.
Authorization: admin
General Guidelines
The following guidelines apply to configuring daylight saving time transitions:
•![]() Specify the time-zone code for daylight saving time.
Specify the time-zone code for daylight saving time.
•![]() For recurring configurations, specify a day of the month (week number/first|last/day of the week/month).
For recurring configurations, specify a day of the month (week number/first|last/day of the week/month).
•![]() For nonrecurring configurations, specify a date (month/day of the month/year).
For nonrecurring configurations, specify a date (month/day of the month/year).
•![]() Define two days:
Define two days:
–![]() day1 is the beginning of daylight saving time.
day1 is the beginning of daylight saving time.
–![]() day2 is the end of daylight saving time.
day2 is the end of daylight saving time.
•![]() In the Southern hemisphere, month2 must be earlier than month1, because daylight saving time begins in the fall and ends in the spring.
In the Southern hemisphere, month2 must be earlier than month1, because daylight saving time begins in the fall and ends in the spring.
•![]() Specify the exact time that the transition should occur (24-hour clock):
Specify the exact time that the transition should occur (24-hour clock):
–![]() Time of transition into daylight saving time, according to local standard time
Time of transition into daylight saving time, according to local standard time
–![]() Time of transition out of daylight saving time, according to local daylight saving time
Time of transition out of daylight saving time, according to local daylight saving time
Recurring Configurations
For the clock summertime recurring command, the default values are the United States transition rules:
•![]() Daylight saving time begins at 2:00 (a.m.) on the second Sunday of March.
Daylight saving time begins at 2:00 (a.m.) on the second Sunday of March.
•![]() Daylight saving time ends at 2:00 (a.m.) on the first Sunday of November.
Daylight saving time ends at 2:00 (a.m.) on the first Sunday of November.
Use the recurring keyword if daylight saving time always begins and ends on the same day every year.
Specifying Explicit Days
To specify the occurrence of a day of the week in a specified month, use the first and last keywords. For example, last Sunday March.
For a nonrecurring configuration, use a specific date, including the year. For example, March 29, 2004.
For a recurring configuration, use week/day of the week/month (no year):
•![]() Use the first or last occurrence of a day of the week in a specified month. For example, last Sunday March (the last Sunday in March).
Use the first or last occurrence of a day of the week in a specified month. For example, last Sunday March (the last Sunday in March).
•![]() Use the day of the week in a specific week in a specified month. For example, 4 Sunday March (the fourth Sunday in March). This day is different from the last Sunday of a month that has five Sundays.
Use the day of the week in a specific week in a specified month. For example, 4 Sunday March (the fourth Sunday in March). This day is different from the last Sunday of a month that has five Sundays.
Examples
The following examples show how to use this command.
Example 1
The following example shows how to configure recurring daylight saving time for a time zone designated as DST:
•![]() Daylight saving time begins at 0:00 on the last Sunday of March.
Daylight saving time begins at 0:00 on the last Sunday of March.
•![]() Daylight savings time ends at 23:59 on the Saturday of the fourth week of November.
Daylight savings time ends at 23:59 on the Saturday of the fourth week of November.
•![]() Offset is 1 hour (default).
Offset is 1 hour (default).
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#clock summertime DST recurring last Sunday March 00:00 4 Saturday November 23:59 SCE(config)#
Example 2
The following example shows how to configure nonrecurring daylight saving time for a time zone designated as DST:
•![]() Daylight savings time begins at 0:00 on April 16, 2007.
Daylight savings time begins at 0:00 on April 16, 2007.
•![]() Daylight savings time ends at 23:59 October 23, 2007.
Daylight savings time ends at 23:59 October 23, 2007.
•![]() Offset is 1 hour (default).
Offset is 1 hour (default).
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#clock summertime DST April 16 2005 00:00 October 23 2005 23:59
SCE(config)#
Example 3
The following example shows how to cancel the daylight saving time configuration:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#no clock summertime SCE(config)#
Related Commands
clock timezone
Sets the time zone so that the system can correctly interpret time-stamp data coming from systems located in other time zones.
To remove current time zone settings, use the no form of this command.
clock timezone zone hours [minutes]
no clock timezone
Syntax Description
Defaults
UTC (hours = 0)
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to set the time zone to Pacific Standard Time with an offset of 10 hours behind UTC:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#clock timezone PST -10 SCE(config)#
Related Commands
|
|
|
calendar set |
Sets the system calendar. |
clock set |
Manually sets the system clock. |
show calendar |
Displays the time maintained by the real-time system calendar clock. |
clock update-calendar
Synchronizes clocks by setting the calendar from the system clock.
clock update-calendar
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to update the calendar according to the clock:
SCE>enable 10 Password:<cisco> SCE#clock update-calendar SCE#
Related Commands
|
|
|
clock set |
Manually sets the system clock. |
calendar set |
Sets the system calendar. |
clock read-calendar |
Synchronizes clocks by setting the system clock from the calendar. |
configure
Enables the user to move from Privileged EXEC mode to Global Configuration mode.
configure
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
After you enter the configure command, the system prompt changes from <hostname># to <hostname>(config)#, indicating that the system is in Global Configuration mode. To leave Global Configuration mode and return to the Privileged EXEC mode prompt, use the exit command.
Authorization: admin
Examples
The following example shows how to enter Global Configuration mode:
SCE>enable 10 Password:<cisco> SCE#configure SCE#(config) #
Related Commands
|
|
|
exit |
Exits from the current mode to the next "lower" mode. |
connection-mode
Sets the connection mode parameters.
connection-mode connection-mode sce-id sce-id priority priority on-failure on-failure
Syntax Description
Defaults
The default for connection-mode is inline.
The default for sce-id is 0.
The default for priority is primary.
The defaults for on-failure are:
–![]() external-bypass for inline mode.
external-bypass for inline mode.
–![]() bypass for inline-cascade mode.
bypass for inline-cascade mode.
Command Modes
Linecard Interface Configuration
Usage Guidelines


Note ![]() The sce-id argument, which identifies the SCE platform, replaces the physically-connected-link argument, which identified the link. This change was required with the introduction of the SCE8000 GBE platform, which supports multiple links. However, for backward compatibility, the physically-connected-link argument is still recognized and the number of the link assigned to that argument (0 or 1) is defined as the SCE ID.
The sce-id argument, which identifies the SCE platform, replaces the physically-connected-link argument, which identified the link. This change was required with the introduction of the SCE8000 GBE platform, which supports multiple links. However, for backward compatibility, the physically-connected-link argument is still recognized and the number of the link assigned to that argument (0 or 1) is defined as the SCE ID.
Authorization: admin
Examples
The following example shows how to configure the primary SCE 8000 platform in a two-SCE platform inline topology. This device is designated as SCE platform 0, and the behavior of the SCE platform if a failure occurs is bypass (default).
SCE>enable 10 Password: <cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#connection-mode inline-cascade sce-id 0 priority primary on-failure bypass SCE(config if)#
Related Commands
copy
Copies any file from a source directory to a destination directory on the local flash file system.
copy source-file destination-file
Syntax Description
source-file |
Name of the original file. |
destination-file |
Name of the new destination file. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Both filenames should be in 8.3 format, that is, the names have a maximum of eight characters before the period and three characters after it.
Authorization: admin
Examples
The following example shows how to copy the local analysis.sli file located in the root directory to the applications directory:
SCE>enable 10 Password:<cisco> SCE#copy analysis.sli applications/analysis.sli SCE#
Related Commands
|
|
|
copy ftp:// |
Uploads or downloads a file system using FTP. |
copy-passive |
Uploads or downloads a file using passive FTP. |
copy ftp://
Uploads or downloads a file system using FTP.
copy ftp://username[:password]@server-address[:port]/path/source-file destination-file
copy source-file ftp://username[:password]@server-address[:port]/path/destination-file
Syntax Description
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Use the following syntax for remote upload or download using FTP:
ftp://username[:password]@server-address[:port]/path/file
You can configure keyword shortcuts for the copy command using the following commands:
•![]() ip ftp password to configure a password shortcut
ip ftp password to configure a password shortcut
•![]() ip ftp username to configure a username shortcut
ip ftp username to configure a username shortcut
Authorization: admin
Examples
The following example shows how to download the ftp.sli file from the host 10.10.10.10 with the username user and the password a1234:
SCE>enable 10 Password:<cisco> SCE#copy ftp://user:a1234@10.10.10.10/p:/applications/ftp.sli appl/analysis.sli SCE#
Related Commands
copy-passive
Uploads or downloads a file using passive FTP.
copy-passive source-file ftp://username[:password]@server-address[:port]/path/destination-file [overwrite]
copy-passive ftp://username[:password]@server-address[:port]/path/source-file destination-file
Syntax Description
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Use the following syntax for remote upload or download using FTP:
ftp://username[:password]@serveraddress[:port]/path/file
You can configure keyword shortcuts for the copy command using the following commands:
•![]() ip ftp password to configure a password shortcut
ip ftp password to configure a password shortcut
•![]() ip ftp username to configure a username shortcut
ip ftp username to configure a username shortcut
Authorization: admin
Examples
The following example shows how to download the analysis.sli file from the host 10.10.10.10 with the username user and the password a1234:
SCE>enable 10 Password:<cisco>0 SCE#copy-passive ftp://user:a1234@10.10.10.10/p:/applications/analysis.sli appl/analysis.sli SCE#
Related Commands
copy running-config startup-config
Builds a configuration file called config.txt that contains general configuration commands. This file is used in successive boots.
copy running-config startup-config
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
This command must be entered to save newly configured parameters so that they will be effective after a reboot. To view the running configuration before saving it, use the more running-config command.
The old configuration file is automatically saved in the /system/prevconf directory.
Authorization: admin
Examples
The following example shows how to save the current configuration for successive boots:
SCE>enable 10 Password:<cisco> SCE#copy running-config startup-config Backing-up configuration file... Writing configuration file... SCE#
Related Commands
|
|
|
more |
Displays the contents of a file. |
show running-config |
Displays the current configuration. |
copy source-file ftp://
Uploads a file to a remote station using FTP.
copy source-file ftp://username[:password]@server-address[:port]/path/destination-file
Syntax Description
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Use the following syntax for remote upload or download using FTP:
ftp://username[:password]@serveraddress[:port]/path/file
You can configure keyword shortcuts for the copy command using the following commands:
•![]() ip ftp password to configure a password shortcut
ip ftp password to configure a password shortcut
•![]() ip ftp username to configure a username shortcut
ip ftp username to configure a username shortcut
Authorization: admin
Examples
The following example shows how to upload the analysis.sli file located on the local flash file system to the host 10.1.1.105:
SCE>enable 10
Password:<cisco>
SCE#copy /appl/analysis.sli ftp://myname:mypw@10.1.1.105/p:/applications/analysis.sli
SCE#
Related Commands
|
|
|
copy ftp:// |
Uploads or downloads a file system using FTP. |
copy source-file startup-config
Copies the specified source file to the startup-config file.
The command uploads a backup configuration file created using the copy startup-config destination-file command. In a cascaded solution, you can copy the configuration from one SCE platform to the other.
copy source-file startup-config
Syntax Description
source-file |
Name of the backup configuration file. Choose either: • • |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
The source filename should be in 8.3 format, that is, the names have a maximum of eight characters before the period and three characters after it.
Authorization: admin
Examples
The following example shows how to upload a backup configuration file:
SCE>enable 10
Password:<cisco>
SCE#copy ftp://user:pass@host/drive:/dir/bakupcfg.txt startup-config
SCE#
Related Commands
|
|
|
copy startup-config destination-file |
Copies the startup-config file to the specified destination file. |
copy startup-config destination-file
Copies the startup-config file to the specified destination file.
The command creates a backup configuration file. In a cascaded solution, you can copy the configuration from one SCE platform to the other. The file created by this command can be uploaded to the second SCE platform using the copy source-file startup-config command.
copy startup-config destination-file
Syntax Description
destination-file |
Name of the file to which the configuration is copied. Choose either: • • |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
The destination filename should be in 8.3 format, that is, the names have a maximum of eight characters before the period and three characters after it.
Authorization: admin
Examples
The following example shows how to create a backup configuration file:
SCE>enable 10 Password:<cisco> SCE#copy startup-config ftp://user:pass@host/drive:/dir/bckupcfg.txt SCE#
Related Commands
|
|
|
copy source-file startup-config |
Copies the specified source file to the startup-config file. |
default subscriber template all
Removes all user-defined subscriber templates from the system. Only the default template remains.
default subscriber template all
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to remove all user-defined subscriber templates:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)# default subscriber template all SCE(config if)#
Related Commands
delete
Deletes a file from the local flash file system.
delete filename [/recursive]
Syntax Description
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to delete the file oldlog.txt:
SCE>enable 10 Password:<cisco> SCE#delete oldlog.txt SCE#
The following example shows how to delete the directory oldlogs:
SCE>enable 10 Password:<cisco> SCE#delete oldlogs /recursive 3 files and 1 directories will be deleted. Are you sure? y 3 files and 1 directories have been deleted. SCE#
Related Commands
|
|
|
dir |
Displays the files in the current directory. |
rmdir |
Removes an empty directory. |
diameter
Starts the diameter stack.
To stop the stack, use the no form of this command.
To reset the stack to the default state (stopped), use the default form of this command.
diameter
no diameter
default diameter
Syntax Description
This command has no arguments or keywords.
Defaults
Diameter stack is stopped.
Command Modes
Global Configuration
Usage Guidelines
Stopping the stack using this command is a brute force shutdown. All messages and states may be lost.
Authorization: admin
Examples
The following example shows how to stop the stack.
SCE>enable 10
Password:<cisco>
SCE# configure
SCE(config)#no diameter
SCE(config)#
Related Commands
|
|
|
|---|---|
show diameter |
Displays the current diameter stack state. |
diameter Gx
Starts the Gx application.
To stop the Gx application, use the no form of this command.
diameter Gx
no diameter Gx
Syntax Description
This command has no arguments or keywords.
Defaults
Gx application is stopped.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to stop the Gx application.
SCE>enable 10
Password:<cisco>
SCE# configure
SCE(config)#no diameter Gx
SCE(config)#
Related Commands
|
|
|
|---|---|
show diameter Gx |
Displays the current Gx application state. |
diameter Gx failure-grace-time
Configures Gx detection time out. If no connection to any server is detected for the configured length of time, all diameter sessions are closed and a new connection must be established. The sessions will be reopened once a connection is reestablished.
To reset the grace period to the default, use the default form of this command.
diameter Gx failure-grace-time time
default Gx failure-grace-time
Syntax Description
time |
Detection grace period in seconds. |
Defaults
300 seconds
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to use this command.
SCE>enable 10
Password:<cisco>
SCE# configure
SCE(config)#diameter Gx failure-grace-time 360
SCE(config)#
Related Commands
|
|
|
|---|---|
diameter Gx PCRF-connection-failure-grace-time
Configures the diameter Gxconnection failure grace period.
To reset the grace period to the default, use the default form of this command.
diameter Gx pcrf-connection-failure-grace-time time
default diameter Gx pcrf-connection-failure-grace-time
Syntax Description
time |
Grace period in seconds. |
Defaults
150 seconds
Command Modes
Global Configuration
Usage Guidelines
Failover functions as follows:
•![]() If a connection fails and is reestablished within the failover grace period, no failover action is taken
If a connection fails and is reestablished within the failover grace period, no failover action is taken
•![]() If a connection fails and is not reestablished within the failover grace period, failover action is taken.
If a connection fails and is not reestablished within the failover grace period, failover action is taken.
•![]() If a server fails, all its sessions remain open for the failover grace period. After that period has expired, all the server sessions are closed and reopened on secondary server.
If a server fails, all its sessions remain open for the failover grace period. After that period has expired, all the server sessions are closed and reopened on secondary server.
•![]() If a server fails on a system using session-sharing, no failover action is taken.
If a server fails on a system using session-sharing, no failover action is taken.
Authorization: admin
Examples
The following example shows how to use this command.
SCE>enable 10
Password:<cisco>
SCE# configure
SCE(config)#diameter Gx pcrf-connection-failure-grace-time 120
SCE(config)#
Related Commands
|
|
|
|---|---|
diameter Gx tx-timer
Configures the transmit timeout value for messages.
To reset the tx timeout to the default value, use the default form of this command.
diameter Gx tx-timer time
default diameter Gx tx-timer
Syntax Description
time |
Timeout interval in seconds. |
Defaults
5 seconds
Command Modes
Global Configuration
Usage Guidelines
If the PCRF does not respond to a Gx message in the configured tx-timer seconds, the message is considered timed out. The message is dumped if it arrives after tx-timer expires.
Authorization: admin
Examples
The following example shows how to use this command.
SCE>enable 10
Password:<cisco>
SCE# configure
SCE(config)#diameter Gx tx-timeout 20
SCE(config)#
Related Commands
|
|
|
|---|---|
diameter Gy send-attributes
Configures when to transmit subscriber attributes, as well as when to extract them.
To disable transmitting subscriber attributes, use the no form of this command.
diameter Gy send-attributes (on-initial | on-change | always)
no diameter Gy send-attributes
Syntax Description
Defaults
on-initial
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to use this command.
SCE>enable 10
Password:<cisco>
SCE# configure
SCE(config)#diameter Gy send-attributes on-change
SCE(config)#
Related Commands
|
|
|
|---|---|
diameter Gy charging-id-mapping
Adds an entry to the charging ID mapping table. Maps SCA BB parameters of package and bucket to the Gy interface parameters of service and rating group, so that a specified bucket from a specified package will always be output by the Gy interface as a particular service and rating group.
To delete the mapping table entry for the specified package-id and bucket-id, use the no form of this command.
To clear the charging ID mapping table, use the no...all form of the command.
diameter Gy charging-id-mapping package-id package-id bucket-id bucket-id service-id service-id rating-group rating-group
no diameter Gy charging-id-mapping package-id package-id bucket-id bucket-id
no diameter Gy charging-id-mapping all
Syntax Description
Defaults
None
Command Modes
Global Configuration
Usage Guidelines
Charging ID Mapping Table Guidelines
•![]() The translation is done if and only if the mapping table is not empty.
The translation is done if and only if the mapping table is not empty.
–![]() If the mapping table is not empty, and there is a corresponding entry in the table, the translation is done to the configured numbers.
If the mapping table is not empty, and there is a corresponding entry in the table, the translation is done to the configured numbers.
–![]() If the mapping table is not empty, but there is no corresponding entry in the table, an appropriate error counter is increased.
If the mapping table is not empty, but there is no corresponding entry in the table, an appropriate error counter is increased.
•![]() If the mapping table is not empty, it must be complete! All entries must be present in the table, even though only a partial mapping is required. Therefore, an entry must be configured even for a pair that does not have to be translated (for example, package-id 5/bucket-id 7 to service-id 5/rating-group 7).
If the mapping table is not empty, it must be complete! All entries must be present in the table, even though only a partial mapping is required. Therefore, an entry must be configured even for a pair that does not have to be translated (for example, package-id 5/bucket-id 7 to service-id 5/rating-group 7).
•![]() The package ID / bucket ID pair and the service ID / rating group pair are unique for each entry. Trying to add a duplicate pair will result in an error.
The package ID / bucket ID pair and the service ID / rating group pair are unique for each entry. Trying to add a duplicate pair will result in an error.
•![]() The table can hold up to 1000 mappings.
The table can hold up to 1000 mappings.
Authorization: admin
Examples
The following example shows how to map the first three buckets in package-id 5 to service-id 1 rating-groups 10-12.
SCE>enable 15 Password:<cisco> SCE#> configure SCE(config)#diameter Gy charging-id-mapping package-id 5 bucket-id 1 service-id 1 rating-group 10
SCE(config)#diameter Gy charging-id-mapping package-id 5 bucket-id 2 service-id 1 rating-group 11
SCE(config)#diameter Gy charging-id-mapping package-id 5 bucket-id 3 service-id 1 rating-group 12
SCE(config)#>
Related Commands
|
|
|
|---|---|
show diameter Gy charging-id-mapping |
Displays the charging ID mapping table. |
diameter Gy subscriber-attribute-mapping
Maps the specified PS Information AVP (3GPP-charging-characteristics) into the specified realm.
diameter Gy subscriber-attribute-mapping attribute-name 3GPP-charging-characteristics attribute-value attribute-value realm-id realm-id
Syntax Description
Defaults
As configured for peer.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to use this command. This example maps all subscriber s that logged in with VSA attribute 3GPP-charging-characteristics value = 0800 to the realm called `PrePaidSubsRealm'.

Note ![]() If the specified realm is not found in the realm table, the first realm in the table is used as default.
If the specified realm is not found in the realm table, the first realm in the table is used as default.
SCE>enable 10
Password:<cisco>
SCE# configure
SCE(config)#diameter Gy subscriber-attribute-mapping attribute-name 3GPP-charging-characteristics attribute-value 0800 realm-id PrePaidSubsRealm
SCE(config)#
Related Commands
|
|
|
|---|---|
diameter Gy tx-timer
Configures the transmit timeout value for messages.
To reset the tx timeout to the default value, use the default form of this command.
diameter Gy tx-timer time
default diameter Gy tx-timer
Syntax Description
time |
Timeout interval in seconds. |
Defaults
5 seconds
Command Modes
Global Configuration
Usage Guidelines
If the PCRF does not respond to a Gy message in the configured tx-timer seconds, the message is considered timed out. The message is dumped if it arrives after tx-timer expires.
Authorization: admin
Examples
The following example shows how to use this command.
SCE>enable 10
Password:<cisco>
SCE# configure
SCE(config)#diameter Gy tx-timeout 20
SCE(config)#
Related Commands
|
|
|
|---|---|
diameter origin-realm
Configures the name of the stack realm.
To reset the stack realm to the default, use the default form of this command.
diameter origin-realm realm
default diameter origin-realm
Syntax Description
realm |
Name of the realm. |
Defaults
sce.cisco.com
Command Modes
Global Configuration
Usage Guidelines

Authorization: admin
Examples
The following example shows how to use this command.
SCE>enable 10
Password:<cisco>
SCE# configure
SCE(config)#no diameter
SCE(config)#diameter origin-realm realm1
Related Commands
|
|
|
|---|---|
no diameter |
Stops the diameter stack. |
diameter peer
Adds an entry to the peer table.
To remove an entry from the peer table, use the no form of this command.
To clear the peer table, removing all the entries, use the no diameter peer all command.
diameter peer name peer-host ip-address [port port#]
no diameter peer name
no diameter peer all
Syntax Description
Defaults
None
Command Modes
Global Configuration
Usage Guidelines
The peer table holds a list of all the peers with which the SCE has a direct connection. The information for each entry includes:
•![]() Peer host - The host IP
Peer host - The host IP
•![]() Peer port
Peer port
•![]() State - Up, Down, or N/A (stack is not currently activated). This information is non-configurable.
State - Up, Down, or N/A (stack is not currently activated). This information is non-configurable.
•![]() Peer name - Name assigned by this command
Peer name - Name assigned by this command

Note ![]() Removing a peer from the peer table removes all the peer related configuration information from the Routing table and from the forwarding scheme.
Removing a peer from the peer table removes all the peer related configuration information from the Routing table and from the forwarding scheme.
General Guidelines
•![]() Do not assign the same IP address to two peers, even if the port numbers are different, unless they are in different domains.
Do not assign the same IP address to two peers, even if the port numbers are different, unless they are in different domains.
•![]() To remove one entry from the peer table, use the no diameter peer name command.
To remove one entry from the peer table, use the no diameter peer name command.
•![]() To clear the peer table, use the use the no diameter peer all command.
To clear the peer table, use the use the no diameter peer all command.
Authorization: admin
Examples
Example 1
The following example shows how to add an entry to the peer table for a peer named "test_peer".
SCE>enable 10 Password:<cisco> SCE# configure SCE(config)#diameter peer test_peer peer-host 1.1.1.1
Example 2
The following example shows how to clear the peer table.
SCE>enable 10 Password:<cisco> SCE# configure SCE(config)#no diameter peer all
Related Commands
|
|
|
|---|---|
show diameter peer |
|
show diameter peer-table |
diameter port
Configures the stack host.
To reset the stack port to the default, use the default form of this command.
diameter port port
default diameter port
Syntax Description
port |
Port number to be used by the stack. |
Defaults
3868
Command Modes
Global Configuration
Usage Guidelines

Authorization: admin
Examples
The following example shows how to use this command.
SCE>enable 10
Password:<cisco>
SCE# configure
SCE(config)#no diameter
SCE(config)#diameter port 3333
Related Commands
|
|
|
|---|---|
diameter realm
Adds an entry to the routing table.
To remove an entry from the routing table, use the no form of this command.
To clear the routing table, removing all the entries, use the no diameter realm all command.
diameter realm realm-name (Gx|Gy) peer peer-name priority priority
no diameter realm realm-name [Gx|Gy] peer peer-name
no diameter realm all
Syntax Description
Defaults
None
Command Modes
Global Configuration
Usage Guidelines
The routing table contains the peer application support and the forwarding scheme priority information. The information for each entry includes:
•![]() peer name
peer name
•![]() supported application (Gx or Gy)
supported application (Gx or Gy)
•![]() realm
realm
•![]() priority
priority
General Guidelines
•![]() Priority is required except for the first peer entry assigned to a realm. If a priority is not assigned to the first peer entry for a realm, a priority of 100 is assigned automatically.
Priority is required except for the first peer entry assigned to a realm. If a priority is not assigned to the first peer entry for a realm, a priority of 100 is assigned automatically.
•![]() In the Gx application there is one realm with many peers supporting that realm.
In the Gx application there is one realm with many peers supporting that realm.
•![]() In the Gy application there can be several realms, each with multiple peers.
In the Gy application there can be several realms, each with multiple peers.
•![]() Peers can support more than one application.
Peers can support more than one application.
•![]() To remove the entry for a peer only for a specific application, specify Gx or Gy in the no form of the command. If you do not specify the application, if two peer entries exist, they will both be removed.
To remove the entry for a peer only for a specific application, specify Gx or Gy in the no form of the command. If you do not specify the application, if two peer entries exist, they will both be removed.
•![]() To clear the routing table use the no diameter realm all command.
To clear the routing table use the no diameter realm all command.
Authorization: admin
Examples
Example 1
The following example shows how to add a route.
SCE>enable 10 Password:<cisco> SCE# configure SCE(config)#diameter realm test_realm.cisco.com Gy peer test_peer
Example 2
The following example shows how delete one entry from the routing table.
SCE>enable 10 Password:<cisco> SCE# configure SCE(config)#no diameter realm test_realm.cisco.com Gy peer test_peer
Example 3
The following example is similar to Example 2, but it removes both entries for the specified peer from the routing table.
SCE>enable 10 Password:<cisco> SCE# configure SCE(config)#no diameter realm test_realm.cisco.com peer test_peer
Related Commands
|
|
|
|---|---|
show diameter realm |
|
show diameter routing table |
diameter realm forwarding-mode
Configures the forwarding mode for the specified realm and application.
diameter realm realm-name(Gx |Gy) forwarding-mode (load-balancing| high-availability [shared-session-on [stickness-on |stickness-off]| shared-session-off])
Syntax Description
realm-name |
Name of the realm. |
Gx or Gy |
Indicate whether the forwarding mode applies to Gx or Gy applications. |
Defaults
Load-Balancing
Command Modes
Global Configuration
Usage Guidelines
Load Balancing
Load balancing is completed by round robin using the available servers. The available servers are round robin cycled per session and not per message, meaning the messages for a specific session are all sent to the same server.
When a server fails, it is removed from the round robin.
High Availability (Failover)
When the high availably scheme is used, there is no load balancing between servers. The high availability scheme is strictly an active and standby scheme.
Each server is assigned a priority. Only the server with the highest priority handles the session. When the active server fails, all new sessions will be started on the next server in the priority list order.
High availability mode has additional options:
•![]() shared-session-on: Sessions are common to all servers, and therefore sessions on a failed server do not need to be reopened on a different server if the server fails.
shared-session-on: Sessions are common to all servers, and therefore sessions on a failed server do not need to be reopened on a different server if the server fails.
–![]() stickiness-on: Sessions move back to the original server when it restarts.
stickiness-on: Sessions move back to the original server when it restarts.
–![]() stickiness-off: Sessions do not move back to the original server when it restarts.
stickiness-off: Sessions do not move back to the original server when it restarts.
•![]() shared-session-off: Sessions are not common to all servers, and therefore sessions on a failed server must be reopened on a different server if the server fails.
shared-session-off: Sessions are not common to all servers, and therefore sessions on a failed server must be reopened on a different server if the server fails.
Authorization: admin
Examples
The following example shows how to configure high-availability forwarding mode where the sessions will be common to all servers and will not return to the original server after failure when that server restarts.
SCE>enable 10 Password:<cisco> SCE#configure SCE(config)#diameter realm test_realm.cisco.com Gy forwarding-mode high-availability shared-session-on stickiness-off
SCE(config)#
Related Commands
|
|
|
|---|---|
show diameter forwarding-mode |
Displays the forwarding mode table. |
diameter tx-timer
Configures the diameter transmit timeout value for messages.
To reset the timeout to the default, use the default form of this command.
diameter tx-timer time
default diameter tx-timer
Syntax Description
time |
Timeout interval in seconds. Range is 5-6000. |
Defaults
30 seconds
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to use this command.
SCE>enable 10
Password:<cisco>
SCE# configure
SCE(config)#diameter tx-timeout 20
SCE(config)#
Related Commands
|
|
|
|---|---|
dir
Displays the files in the current directory.
dir [applications] [-r]
Syntax Description
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to display the files in the current directory (root):
SCE>enable 10 Password:<cisco> SCE#dir File list for /system/ 512TUE JAN 01 00:00:00 1980LOGDBG DIR 512TUE JAN 01 00:00:00 1980LOG DIR 7653 TUE JAN 01 00:00:00 1980FTP.SLI 29 TUE JAN 01 00:00:00 1980SCRIPT.TXT 512 TUE JAN 01 00:00:00 1980SYSTEM DIR SCE#
Related Commands
|
|
|
pwd |
Displays the current working directory. |
cd |
Changes the path of the current working directory. |
disable
Moves the user from a higher level of authorization to a lower user level.
disable level
Syntax Description
level |
User authorization level (0, 5, 10, 15) as specified in CLI Authorization Levels. |
Defaults
None.
Command Modes
Privileged EXEC and Viewer
Usage Guidelines
Use this command with the level argument to lower the user privilege level, as illustrated in Figure 2-1. If a level is not specified, it defaults to User mode.
Figure 2-1 Disable Command
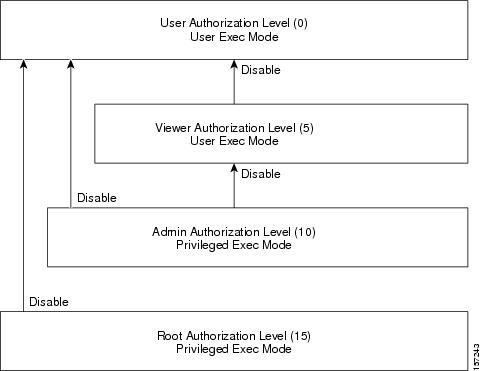
Note that you must exit to Privileged EXEC command mode to use this command.
Authorization: user
Examples
The following example shows how to change from root to admin mode:
SCE>enable 15
Password:<cisco>
SCE#>disable 10
SCE#
Related Commands
|
|
|
enable |
Allows the user to access a higher authorization level. |
do
Executes an EXEC mode command (such as a show command) or a privileged EXEC command (such as show running-config) without exiting to the relevant command mode.
do command
Syntax Description
command |
Command to be executed. |
Defaults
None.
Command Modes
All configuration modes
Usage Guidelines
Use this command when in any configuration command mode (global configuration, linecard configuration, or any interface configuration) to execute a User EXEC or Privileged EXEC command.
Enter the entire command with all parameters as you would if you were in the relevant command mode.
Authorization: admin
Examples
The following example assumes that the on-failure action of the SCE platform has been changed to bypass. The connection mode configuration is then displayed to verify that the parameter was changed. The do command is used to avoid having to exit to User EXEC mode.
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#connection-mode on-failure bypass SCE(config if)#do show interface linecard 0 connection-mode slot 0 connection mode Connection mode is inline slot failure mode is bypass Redundancy status is standalone SCE(config if)#
Related Commands
|
|
|
duplex
Configures the duplex operation of the GigabitEthernet management interface.
duplex [mode]
no duplex
Syntax Description
mode |
Sets duplex operation to one of the following modes: • • • |
Defaults
The default duplex mode is auto.
Command Modes
GigabitEthernet Interface Configuration
Usage Guidelines
Use this command to configure the duplex mode of the GigabitEthernet management interface.
If the speed of the management interface is configured to auto (see the speed command), changing this configuration has no effect.
Authorization: admin
Examples
The following example shows how to configure the management port to auto mode. The interface designation is 1/1.
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#interface GigabitEthernet 1/1
SCE(config if)#duplex auto
SCE(config if)#
Related CommandsE
|
|
|
speed |
Configures the speed of the management interface. |
show interface gigabitethernet |
Displays the details of the GigabitEthernet management interface. |
enable
Enables the user to access a higher authorization level.
enable [level]
Syntax Description
level |
User authorization level (0, 5, 10, 15) as specified in CLI Authorization Levels, page 1-2. |
Defaults
The default authorization level is admin (10).
Command Modes
User EXEC
Usage Guidelines
Figure 2-2 shows the authorization levels.
Figure 2-2 Enable Command
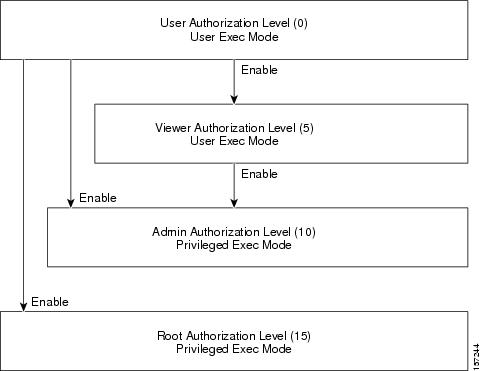
If a level is not specified, it defaults to admin authorization (level 10).
Note that you cannot use the enable command from Privileged EXEC or any of the configuration command modes.
Authorization: user
Examples
The following example shows how to access the administrator authorization level. Note that the prompt changes from SCE> to SCE#, indicating that the level is the administrator privilege level.
SCE>enable
Password:<cisco>
SCE#
Related Commands
|
|
|
disable |
Moves the user from a higher level of authorization to a lower user level. |
enable password |
Configures a password for the specified authorization level. |
enable password
Configures a password for the specified authorization level, which prevents unauthorized users from accessing the SCE platform.
To disable the password for the specified authorization level, use the no form of this command.
enable password [level level] [encryption-type ] [password]
no enable password [level level]
Syntax Description
Defaults
The default authorization level is admin (10).
The default password is cisco.
Command Modes
Global Configuration
Usage Guidelines
After the command is entered, any user executing the enable command must supply the specified password. The following conditions apply to passwords:
•![]() Must be at least 4 and no more than 100 characters long
Must be at least 4 and no more than 100 characters long
•![]() Can contain any printable characters
Can contain any printable characters
•![]() Must begin with a letter
Must begin with a letter
•![]() Cannot contain spaces
Cannot contain spaces
•![]() Are case-sensitive
Are case-sensitive
Authorization: admin
Examples
The following example shows how to set a level 10 password:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#enable password level 10 a123*man
SCE(config)#
Related Commands
|
|
|
enable |
Allows the user to access a higher authorization level. |
service password-encryption |
Enables password encryption. |
end
Exits from Global Configuration mode or an interface configuration mode to the User EXEC authorization level.
end
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Linecard Interface Configuration
Interface GigabitEthernet Configuration
Interface Range GigabitEthernet Configuration
Interface TenGigabitEthernet Configuration
Interface Range TenGigabitEthernet Configuration
Global Configuration
Usage Guidelines
Use this command to exit to the User EXEC authorization level in one command, rather than having to execute the exit command twice. The system prompt changes to reflect the lower-level mode.
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#end SCE#
Related Commands
erase startup-config-all
Removes all current configurations by removing all configuration files.
erase startup-config-all
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
The following data is deleted by this command:
•![]() General configuration files
General configuration files
•![]() Application configuration files
Application configuration files
•![]() Static party DB files
Static party DB files
•![]() Management agent installed MBeans
Management agent installed MBeans
After using this command, the SCE platform should be reloaded immediately to ensure that it returns to the "factory default" state.
To create a backup of the current configuration before it is deleted, use the copy startup-config destination-file command.
Authorization: admin
Examples
The following example shows how to erase the startup configuration:
SCE>enable 10 Password:<cisco> SCE#erase startup-config-all
Related Commands
|
|
|
reload |
Reboots the SCE platform. |
copy startup-config destination-file |
Copies the startup-config file to the specified destination file. |
exit
Exits from the current mode to the next "lower" mode. When executed from Privileged EXEC or User EXEC mode, the command logs out of the CLI session.
exit
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
All
Usage Guidelines
Use this command each time you want to exit a mode. The system prompt changes to reflect the lower-level mode.

Tip ![]() Use the end command to exit to the User EXEC authorization level.
Use the end command to exit to the User EXEC authorization level.
Authorization: admin
Examples
The following example shows how to exit from Linecard Interface Configuration mode to Global Configuration mode and then to Privileged EXEC mode and then log out:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#exit SCE(config)#exit SCE#exit Connection closed by foreign host.
Related Commands
external-bypass
Manually activates the external bypass modules.
To deactivate the external bypass modules, use the no form of this command.
To return the external bypass module to the default state (deactivated), use the default form of this command.
external-bypass
no external-bypass
default external-bypass
Syntax Description
This command has no arguments or keywords.
Defaults
The external bypass module is deactivated.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#external-bypass SCE(config if)#
Related Commands
|
|
|
show interface linecard external-bypass |
Displays the state of the external bypass module. |
failure-recovery operation-mode
Specifies the operation mode to be applied when the system reboots after a failure.
If you use the default form of the command, you do not have to specify the mode.
failure-recovery operation-mode mode
default failure-recovery operation-mode
Syntax Description
mode |
Indicates whether or not the system boots as operational following a failure. Choose operational or non-operational. |
Defaults
The default mode is operational.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to set the system to boot as operational after a failure:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#failure-recovery operation-mode operational
SCE(config)#
Related Commands
|
|
|
show failure-recovery operation-mode |
Displays the operation mode to apply after booting resulted from a failure. |
flow-capture
Executes flow-capture operations.
flow-capture {start format cap file-name-prefix filename | stop}
Syntax Description
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Flow capturing is a useful debugging capability that captures packets from the traffic stream in real time and stores them for later analysis using a standard cap format. The classification of the traffic portion to be captured is based on L4 attributes. The captured information is sent to a specified FTP destination. In a system with two SCE8000-SCM modules installed, a separate cap file is created by each SCE8000-SCM module.
The FTP transaction is done online on SCE2000 platforms, or immediately after the capture process concludes on SCE8000 platforms.
The following flow-capture operations are available:
•![]() start—Starts recording.
start—Starts recording.
•![]() stop—Stops recording.
stop—Stops recording.
Note that traffic can be captured only when an application is loaded.
To perform a flow capture, follow these steps:
1. ![]() (Optional) Configure limits to the flow-capture operation using the flow-capture controllers command. Limits prevent a negative impact on traffic processing.
(Optional) Configure limits to the flow-capture operation using the flow-capture controllers command. Limits prevent a negative impact on traffic processing.
You may skip this step and use the default controller values.
2. ![]() Configure an appropriate recording rule using the traffic-rule command. Assign the flow-capture action to the rule (see traffic-rule).
Configure an appropriate recording rule using the traffic-rule command. Assign the flow-capture action to the rule (see traffic-rule).

Tip ![]() You must use the traffic-rule command to define the recording rule. You cannot use the flow-filter command.
You must use the traffic-rule command to define the recording rule. You cannot use the flow-filter command.
3. ![]() Start the actual capture. The capture will not start if a valid recording rule has not been defined.
Start the actual capture. The capture will not start if a valid recording rule has not been defined.
Use the flow-capture start command.
4. ![]() (Optional) Stop the capture.
(Optional) Stop the capture.
Use the flow-capture stop command.
If you do not stop the flow capture, it will stop when the maximum duration or capacity has been reached.
At any point, you can use the show interface linecard flow-capture command to display the flow- capture status, including whether flow capture is currently recording or is stopped, the capacity already used, and the number of packets recorded.
Authorization: admin
Examples
The following examples show how to use this command. All examples show output for an SCE8000 with two SCE8000-SCM modules installed.
Example 1
The following example shows how to perform all the steps in a flow capture:
1. ![]() Define the limits (flow-capture controllers max-l4-payload-length and flow-capture controllers time).
Define the limits (flow-capture controllers max-l4-payload-length and flow-capture controllers time).
2. ![]() Define a counter to be assigned to the traffic rule. (Optional)
Define a counter to be assigned to the traffic rule. (Optional)
3. ![]() Define the recording traffic rule (traffic-rule with action flow-capture option).
Define the recording traffic rule (traffic-rule with action flow-capture option).
4. ![]() Start the capture (flow-capture start).
Start the capture (flow-capture start).
(The show command shows that recording is in progress.)
5. ![]() Stop the capture (flow-capture stop).
Stop the capture (flow-capture stop).
SCE>enable 10 Password:<cisco> SCE#configure SCE(config)#interface linecard 0 SCE(config if)#flow-capture controllers max-l4-payload-length 200 SCE(config if)#flow-capture controllers time 45 SCE(config if)#traffic-counter name counter2 count-packets SCE(config if)#traffic-rule name FlowCaptureRule IP-addresses subscriber-side all network-side all protocol 250 direction both traffic-counter name counter2 action flow-capture SCE(config if)#end SCE#flow-capture start format cap file-name-prefix ftp://myUser:myPassword@10.10.10.80/./myCap SCE#show interface linecard 0 flow-capture Flow Capture Status (module #1):
--------------------------------
Flow capture status: RECORDING
Capturing type: ONLINE
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap1.cap
Target file size (bytes): 26580
Time limit (sec): 45
Max L4 payload length (bytes): 200
Number of recorded packets: 152
Number of lost packets: 0
Flow Capture Status (module #2):
--------------------------------
Flow capture status: RECORDING
Capturing type: ONLINE
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap2.cap
Target file size (bytes): 28944
Time limit (sec): 45
Max L4 payload length (bytes): 200
Number of recorded packets: 167
Number of lost packets: 0
SCE#flow-capture stop
SCE#show interface linecard 0 flow-capture
Flow Capture Status (module #1):
--------------------------------
Flow capture status: NOT RECORDING
Capturing type: ONLINE
Last stop cause: User Request
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap1.cap
Target file size (bytes): 99392
Time limit (sec): 45
Max L4 payload length (bytes): 200
Number of recorded packets: 573
Number of lost packets: 0
Flow Capture Status (module #2):
--------------------------------
Flow capture status: NOT RECORDING
Capturing type: ONLINE
Last stop cause: User Request
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap2.cap
Target file size (bytes): 159344
Time limit (sec): 45
Max L4 payload length (bytes): 200
SCE#
Example 2
The following example is identical to the previous one, except that instead of using the stop command, the capturing process continues until the defined time limit is reached.
1. ![]() Define the limits (flow-capture controllers max-l4-payload-length and flow-capture controllers time).
Define the limits (flow-capture controllers max-l4-payload-length and flow-capture controllers time).
2. ![]() Define a counter to be assigned to the traffic rule. (Optional)
Define a counter to be assigned to the traffic rule. (Optional)
3. ![]() Define the recording traffic rule (traffic-rule with action flow-capture option).
Define the recording traffic rule (traffic-rule with action flow-capture option).
4. ![]() Start the capture (flow-capture start).
Start the capture (flow-capture start).
(The show command shows that recording is in progress.)
5. ![]() Capture concludes automatically after 45 seconds.
Capture concludes automatically after 45 seconds.
SCE>enable 10 Password:<cisco> SCE#configure SCE(config)#interface linecard 0 SCE(config if)#flow-capture controllers max-l4-payload-length 200 SCE(config if)#flow-capture controllers time 45 SCE(config if)#traffic-counter name counter2 count-packets SCE(config if)#traffic-rule name FlowCaptureRule IP-addresses subscriber-side all network-side all protocol 250 direction both traffic-counter name counter2 action flow-capture SCE(config if)#end SCE#flow-capture start format cap file-name-prefix ftp://myUser:myPassword@10.10.10.80/./myCap SCE#show interface linecard 0 flow-capture Flow Capture Status (module #1):
--------------------------------
Flow capture status: RECORDING
Capturing type: ONLINE
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap1.cap
Target file size (bytes): 26580
Time limit (sec): 45
Max L4 payload length (bytes): 200
Number of recorded packets: 152
Number of lost packets: 0
Flow Capture Status (module #2):
--------------------------------
Flow capture status: RECORDING
Capturing type: ONLINE
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap2.cap
Target file size (bytes): 28944
Time limit (sec): 45
Max L4 payload length (bytes): 200
Number of recorded packets: 167
Number of lost packets: 0
after 45 seconds...
SCE>show interface linecard 0 flow-capture
Flow Capture Status (module #1):
--------------------------------
Flow capture status: NOT RECORDING
Capturing type: ONLINE
Last stop cause: Time Limit
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap1.cap
Target file size (bytes): 558716
Time limit (sec): 45
Max L4 payload length (bytes): 200
Number of recorded packets: 2696
Number of lost packets: 0
Flow Capture Status (module #2):
--------------------------------
Flow capture status: NOT RECORDING
Capturing type: ONLINE
Last stop cause: Time Limit
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap2.cap
Target file size (bytes): 673840
Time limit (sec): 45
Max L4 payload length (bytes): 200
Number of recorded packets: 3335
Number of lost packets: 0
SCE#
Example 3
In this example, instead of using the stop command, the capturing process continues until the defined file-size limit (64 MB for each SCE8000-SCM) is reached on the first SCE8000-SCM. The other module is stopped using the flow-capture stop command
1. ![]() Set the limits back to the defaults (default flow-capture controllers max-l4-payload-length and default flow-capture controllers time).
Set the limits back to the defaults (default flow-capture controllers max-l4-payload-length and default flow-capture controllers time).
2. ![]() Define a counter to be assigned to the traffic rule. (Optional)
Define a counter to be assigned to the traffic rule. (Optional)
3. ![]() Define the recording traffic rule (traffic-rule with action flow-capture option).
Define the recording traffic rule (traffic-rule with action flow-capture option).
4. ![]() Start the capture (flow-capture start).
Start the capture (flow-capture start).
(The show command shows that recording is in progress.)
5. ![]() Capture on the first SCE8000-SCM concludes automatically when the file size reaches the limit.
Capture on the first SCE8000-SCM concludes automatically when the file size reaches the limit.
6. ![]() Stop the capture on the second SCE8000-SCM (flow-capture stop).
Stop the capture on the second SCE8000-SCM (flow-capture stop).
SCE>enable 10 Password:<cisco> SCE#configure SCE(config)#interface linecard 0 SCE(config if)#default flow-capture controllers max-l4-payload-length SCE(config if)#default flow-capture controllers time SCE(config if)#traffic-counter name counter2 count-packets SCE(config if)#traffic-rule name FlowCaptureRule IP-addresses subscriber-side all network-side all protocol 250 direction both traffic-counter name counter2 action flow-capture SCE(config if)#end SCE#flow-capture start format cap file-name-prefix ftp://myUser:myPassword@10.10.10.80/./myCap SCE#show interface linecard 0 flow-capture Flow Capture Status (module #1):
--------------------------------
Flow capture status: RECORDING
Capturing type: ONLINE
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap1.cap
Target file size (bytes): 11141528
Time limit (sec): 3600
Max L4 payload length (bytes): Unlimited
Number of recorded packets: 20687
Number of lost packets: 0
Flow Capture Status (module #2):
--------------------------------
Flow capture status: RECORDING
Capturing type: ONLINE
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap2.cap
Target file size (bytes): 4150456
Time limit (sec): 3600
Max L4 payload length (bytes): Unlimited
Number of recorded packets: 8365
Number of lost packets: 0
after 32 minutes...
SCE#show interface linecard 0 flow-capture
Flow Capture Status (module #1):
--------------------------------
Flow capture status: NOT RECORDING
Capturing type: ONLINE
Last stop cause: Cannot Write To File or Max Allowed File Size Exceeded
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap1.cap
Target file size (bytes): 67108164
Time limit (sec): 3600
Max L4 payload length (bytes): Unlimited
Number of recorded packets: 124916
Number of lost packets: 0
Flow Capture Status (module #2):
--------------------------------
Flow capture status: RECORDING
Capturing type: ONLINE
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap2.cap
Target file size (bytes): 27551456
Time limit (sec): 3600
Max L4 payload length (bytes): Unlimited
Number of recorded packets: 55140
Number of lost packets: 0
after 5 more minutes...
SCE#flow-capture stop
SCE#show interface linecard 0 flow-capture
Flow Capture Status (module #1):
--------------------------------
Flow capture status: NOT RECORDING
Capturing type: ONLINE
Last stop cause: Cannot Write To File or Max Allowed File Size Exceeded
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap1.cap
Target file size (bytes): 67108164
Time limit (sec): 3600
Max L4 payload length (bytes): Unlimited
Number of recorded packets: 124916
Number of lost packets: 0
Flow Capture Status (module #2):
--------------------------------
Flow capture status: NOT RECORDING
Capturing type: ONLINE
Last stop cause: User Request
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap2.cap
Target file size (bytes): 31647736
Time limit (sec): 3600
Max L4 payload length (bytes): Unlimited
Number of recorded packets: 63463
Number of lost packets: 0
SCE(config if)#
Related Commands
|
|
|
flow-capture controllers |
Configures limitations on the flow capture feature. |
traffic-rule |
Defines a new traffic rule. |
show interface linecard flow-capture |
flow-capture controllers
Configures limitations on the flow-capture feature.
To reset all options to the default values, use the default form of this command.
flow-capture controllers time {duration | unlimited}
flow-capture controllers max-l4-payload-length {length | unlimited}
default flow-capture controllers {time | max-l4-payload-length}
Syntax Description
Defaults
The default for duration is 3600 seconds.
The default for length is unlimited.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Flow capturing is a useful debugging capability that captures packets from the traffic stream in real time and stores them for later analysis. The classification of the traffic portion to be captured is based on L4 attributes.
The portion of traffic that is captured does not receive service (is not processed by the application). Therefore, it is important to control the capturing scenario so that service is not negatively affected. You can limit certain aspects of the flow capture using the following options:
•![]() time (flow-capture recording time)—The duration of the flow capture may be limited to the specified time limit, or it may be unlimited, so that the flow capture is stopped only by executing an explicit stop command or when the maximum file size is reached (128 MB on the SCE8000 platform).
time (flow-capture recording time)—The duration of the flow capture may be limited to the specified time limit, or it may be unlimited, so that the flow capture is stopped only by executing an explicit stop command or when the maximum file size is reached (128 MB on the SCE8000 platform).
•![]() max-l4-payload-length (payload size)—The maximum number of L4 bytes captured from each packet may be specified. This keyword relates to each packet in the traffic stream rather than to overall flow-capture capacity. Using this keyword, the flow-capture throughput (in terms of captured packets) can be increased.
max-l4-payload-length (payload size)—The maximum number of L4 bytes captured from each packet may be specified. This keyword relates to each packet in the traffic stream rather than to overall flow-capture capacity. Using this keyword, the flow-capture throughput (in terms of captured packets) can be increased.
Authorization: admin
Examples
The following example shows how to configure limitations to the flow capture:
SCE>enable 10 Password:<cisco> SCE#>configure SCE(config)#interface linecard 0 SCE(config if)#flow-capture controllers time 120 SCE(config if)#flow-capture controllers max-l4-payload-length 200 SCE(config if)#
Related Commands
|
|
|
traffic-rule |
Defines a new traffic rule. |
flow-capture |
Executes flow capture operations. |
show interface linecard flow-capture |
force failure-condition
Forces a virtual failure condition, and exits from the failure condition, when performing an application upgrade.
To disable forcing a virtual failure condition, use the no form of this command.
force failure-condition
no force failure-condition
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
When upgrading the application in a cascaded system, use this command to force failure in the active SCE8000 platform (see System Upgrades in the Cisco SCE8000 10GBE Software Configuration Guide or System Upgrades in the Cisco SCE8000 GBE Software Configuration Guide).
Authorization: admin
Examples
The following example shows how to force a virtual failure condition.
At the displayed "n," type Y and press Enter to confirm the forced failure.
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#force failure-condition Forcing failure will cause a failover - do you want to continue? n SCE(config if)#
Related Commands
|
|
|
pqi upgrade file |
Upgrades the application using the specified pqi file and any specified upgrade options. |
help
Displays information relating to all available CLI commands.
help {bindings | tree}
Syntax Description
bindings |
Prints a list of keyboard bindings (shortcut commands). |
tree |
Displays the entire tree of all available CLI commands. |
Defaults
None.
Command Modes
EXEC
Usage Guidelines
Authorization: user
Examples
The following example shows partial output from the help bindings command:
SCE>help bindings Line Cursor Movements --------------------- Ctrl-F /->Moves cursor one character to the right. Ctrl-B /<-Moves cursor one character to the left. Esc-FMoves cursor one word to the right. Esc-BMoves cursor one word to the left. Ctrl-AMoves cursor to the start of the line. Ctrl-EMoves cursor to the end of the line. Esc F Moves cursor forward one word. Esc BMoves cursor backward one word. Editing ------- Ctrl-DDeletes the character where the cursor is located. Esc-DDeletes from the cursor position to the end of the word. BackspaceDeletes the character before the current location of the cursor. Ctrl-H Deletes the character before the current location of the cursor. Ctrl-KDeletes from the cursor position to the end of the line. Ctrl-UDeletes all characters from the cursor to the beginning of the line. Ctrl-XDeletes all characters from the cursor to the beginning of the line. Ctrl-WDeletes the word to the left of the cursor. Ctrl-YRecall the last item deleted. Help and Operation Features ---------------------------- ? Argument help. <Tab>Toggles between possible endings for the typed prefix. <Esc><Tab>Displays all the possible arguments backwards. Ctrl-I <TAB> SCE>
Related Commands
|
|
|
history
Enables the history feature,which is a record of the last command lines that executed.
To disable the history feature, use the no form of this command.
history
no history
Syntax Description
This command has no arguments or keywords.
Defaults
History is enabled.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to enable the history feature:
SCE>enable 10 Password:<cisco> SCE#history SCE#
The following example shows how to disable the history feature:
SCE>enable 10 Password:<cisco> SCE#no history SCE#
Related Commands
|
|
|
history size |
Sets the number of command lines that the system records in history. |
history size
Sets the number of command lines that the system records in the history.
To restore the default size, use the no form of this command.
history size [size]
no history size
Syntax Description
size |
Number of command lines stored in the history of commands for quick recall. |
Defaults
The default buffer size is 10 lines.
Command Modes
Privileged EXEC
Usage Guidelines
The size of the history buffer can be any number from 0 to 50. Use the no form of this command to restore the default size.
Authorization: admin
Examples
The following example shows how to set the history buffer size to 50 command lines:
SCE>enable 10 Password:<cisco> SCE#history size 50 SCE#
Related Commands
|
|
|
history |
Enables the history feature, which is a record of the last command lines that were executed. |
hostname
Modifies the name of the SCE platform. The hostname is part of the displayed prompt.
hostname [hostname]
Syntax Description
hostname |
New hostname. Maximum length is 20 characters. |
Defaults
The default hostname is SCE.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to change the hostname to MyHost:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#>hostname MyHost MyHost(config)#>
Related Commands
|
|
|
show hostname |
Displays the currently configured hostname. |
interface gigabitethernet
Enters GigabitEthernet Interface Configuration mode.
In the Cisco SCE8000 10GBE platform, only the management interfaces in slot 1 are Gigabit Ethernet interfaces. (To configure the 10 Gigabit Ethernet line interfaces, use the interface tengigabitethernet command.)
In the Cisco SCE8000 GBE platform, both the management interfaces in slot 1 and the line interfaces in slot 3 are Gigabit Ethernet interfaces.

Note ![]() To configure two or more GBE line interfaces with a single command, use the interface range gigabitethernet command.
To configure two or more GBE line interfaces with a single command, use the interface range gigabitethernet command.
interface gigabitethernet slot-number/interface-number
interface gigabitethernet slot-number/bay-number/interface-number
interface gigabitethernet sce-id /slot-number/bay-number/interface-number
Syntax Description
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
The format of this command depends on the version of the SCE8000 platform and the type of interface being configured, as described Table 2-4.
To return to Global Configuration mode, use the exit command.
The system prompt changes to reflect GigabitEthernet Interface Configuration mode.
Authorization: admin
Examples
The following example shows how to enter GigabitEthernet Interface Configuration mode to configure the management port (SCE8000 GBE and SCE8000 10GBE):
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface gigabitethernet 1/1 SCE(config if)#
The following example shows how to enter GigabitEthernet Interface Configuration mode to configure a GBE line port in subslot 1 of platform 0 in a cascaded pair (SCE8000 GBE only):
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface gigabitethernet 0/3/1/5 SCE(config if)#
Related Commands
interface linecard
Enters Linecard Interface Configuration mode.
interface linecard slot-number
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
The system prompt changes to reflect Linecard Configuration mode. To return to Global Configuration mode, use the exit command.
Authorization: admin
Examples
The following example shows how to enter Linecard Interface Configuration mode:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#
Related Commands
|
|
|
exit |
Exits from the current mode to the next "lower" level. |
interface range gigabitethernet (SCE8000 GBE only)
Enters GigabitEthernet Interface Configuration mode for two or more GBE line interfaces. You can specify a range of bays as well as a range of ports. You can also specify both SCE8000 platforms of a cascaded pair.
interface range gigabitethernet slot-number/bay-range/interface-range
interface range gigabitethernet sce-id/slot-number/bay-range/interface-range
Syntax Description
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
The interface range command performs a CLI operation on a group of interfaces with one command, with the limitation that all the interfaces in the group must be of the same physical and logical type.
The format of this command depends on the topology of the installation, as described in Table 2-5.
To return to Global Configuration mode, use the exit command.
The system prompt changes to reflect GigabitEthernet Interface Configuration mode.
The following commands are executed on all interfaces specified in the interface range gigabitethernet command as long as you remain in GigabitEthernet Interface Configuration mode:
•![]() auto-negotiate (for a cascaded system, supported for the GBE traffic ports only, not for the 10GBE cascade ports)
auto-negotiate (for a cascaded system, supported for the GBE traffic ports only, not for the 10GBE cascade ports)
•![]() global-controller bandwidth
global-controller bandwidth
•![]() global-controller name
global-controller name
Authorization: admin
Examples
The following example shows how to enter GigabitEthernet Interface Configuration mode to configure interfaces 3 to 6 of both 8-port SPA modules:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface range gigabitethernet 3/0-1/3-6 SCE(config if range)#
The following example shows how to enter GigabitEthernet Interface Configuration mode to configure interfaces 3 to 6 of both 8-port SPA modules on SCE8000 platform 0 of a cascaded pair:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface range gigabitethernet 0/3/0-1/3-6 SCE(config if range)#
Related Commands
interface range tengigabitethernet
Enters TenGigabitEthernet Interface Configuration mode for two or more 10GBE line interfaces. You can specify a range of bays.
Note that in the SCE8000 GBE platform, only the cascade ports in bays 2 and 3 support 10GBE interfaces.
interface range tengigabitethernet 3/bay-range/0
Syntax Description
bay-range |
For the SCE8000 10GBE, specify the range of bays in the format bay1-bay2, where the overall range of possible bay numbers is 0 to 3. For the SCE8000 GBE, enter a value of 2, 3, or 2-3. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
The interface range command performs a CLI operation on a group of interfaces with one command, with the limitation that all the interfaces in the group must be of the same physical and logical type.
Because each SPA has only one interface (numbered 0), the only argument that has a possible range is the number of the bay or subslot.
To return to Global Configuration mode, use the exit command.
The system prompt changes to reflect the interface range configuration mode.
Authorization: admin
Examples
The following example shows how to enter TenGigabitEthernet Interface Configuration mode on an SCE8000 10GBE platform to configure all the interfaces:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface range tengigabitethernet 3/0-3/0 SCE(config if range)#
The following example shows how to enter TenGigabitEthernet Interface Configuration mode on an SCE8000 GBE platform to configure both the cascade interfaces:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface range tengigabitethernet 3/2-3/0 SCE(config if range)#
Related CommandsE
interface tengigabitethernet
Enters TenGigabitEthernet Interface Configuration mode for the 10GBE line interfaces.
Note that in the SCE8000 GBE platform, only the cascade ports in bays 2 and 3 support 10GBE interfaces.
interface tengigabitethernet 3/bay-number/0
Syntax Description
bay-number |
For the SCE8000 10GBE, possible bay numbers are 0 to 3. For the SCE8000 GBE, possible bay numbers are 2 or 3. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
To return to Global Configuration mode, use the exit command.
The system prompt changes to reflect the interface configuration mode.
Authorization: admin
Examples
The following example shows how to enter TenGigabitEthernet Interface Configuration mode on an SCE8000 10GBE platform to configure the interface in bay 1:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface tengigabitethernet 3/1/0 SCE(config if range)#
Related CommandsE
ip access-class
Specifies which access control list (ACL) controls global access to the SCE platform.
To permit global access to the SCE platform from any IP address, use the no form of this command.
ip access-class number
no ip access-class
Syntax Description
number |
Number of the access list (1 to 99) to use to allow global access to the SCE platform. |
Defaults
None (all IP addresses can access the system).
Command Modes
Global Configuration
Usage Guidelines
The ACL specified in this command contains the definitions for all IP addresses with permission to access the SCE platform. IP addresses not permitted in this access list cannot access or detect the SCE platform; even a ping command does not receive a response if it is not from a permitted IP address.
Authorization: admin
Examples
The following example shows how to set access list 1 as the global ACL:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip access-class 1 SCE(config)#
Related Commands
|
|
|
access-list |
Adds an entry to the bottom of the specified access list. |
show access-lists |
Displays all access lists or a specific access list. |
ip address
Sets the IP address and subnet mask of the management interface.
ip address new-address subnet-mask
Syntax Description
new-address |
New IP address. |
subnet-mask |
Network mask for the associated IP network. |
Defaults
None.
Command Modes
GigabitEthernet Interface Configuration
Usage Guidelines

Note ![]() Changing the IP address of the management interface using Telnet results in the loss of the Telnet connection and the inability to reconnect with the interface.
Changing the IP address of the management interface using Telnet results in the loss of the Telnet connection and the inability to reconnect with the interface.

Note ![]() After changing the IP address, you must reload the SCE platform (see reload) so that the change will take effect properly in all internal and external components of the SCE platform.
After changing the IP address, you must reload the SCE platform (see reload) so that the change will take effect properly in all internal and external components of the SCE platform.
If a routing table entry maps to the old address, but not to the new address, the command may fail.
Authorization: admin
Examples
The following example shows how to set the IP address of the SCE platform to 10.1.1.1 and the subnet mask to 255.255.0.0:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#gigabitethernet interface 1/1 SCE(config if)#ip address 10.1.1.1 255.255.0.0 SCE(config if)#
Related Commands
|
|
|
gigabitethernet interface |
Enters GigabitEthernet Interface Configuration mode. |
ip advertising
Enables IP advertising. If either the destination or interval is not configured, the default values are used.
To disable IP advertising, use the no form of this command.
To restore the IP advertising destination or interval to the default values, use the default form of this command.
ip advertising [destination destination | interval interval]
no ip advertising
default ip advertising [destination | interval]
Syntax Description
destination |
IP address of the destination for the ping requests |
interval |
Frequency of the ping requests, in seconds |
Defaults
IP advertising is disabled.
The default destination is 127.0.0.1.
The default interval is 300 seconds.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to enable IP advertising and specify a destination and an interval:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip advertising destination 10.1.1.1 SCE(config)#ip advertising interval 240 SCE(config)#
The following example shows how to restore the IP advertising destination to the default value:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#default ip advertising destination SCE(config)#
Related Commands
|
|
|
show ip advertising |
Displays the status of IP advertising, the configured destination, and the configured interval. |
ip default-gateway
Configures the default gateway for the SCE platform.
To remove the SCE platform default gateway configuration, use the no form of this command.
ip default-gateway x.x.x.x
no ip default-gateway
Syntax Description
x.x.x.x |
IP address of the default gateway for the SCE platform. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to set the default gateway IP of the SCE platform to 10.1.1.1:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip default-gateway 10.1.1.1 SCE(config)#
Related Commands
|
|
|
show ip default-gateway |
Displays the configured default gateway. |
ip domain-lookup
Enables or disables the domain name lookups.
To disable domain name lookup, use the no form of this command.
ip domain-lookup
no ip domain-lookup
Syntax Description
This command has no arguments or keywords.
Defaults
Domain name lookup is enabled.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to enable domain lookup:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip domain-lookup
SCE(config)#
The following example shows how to disable domain lookup:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#no ip domain-lookup SCE(config)#
Related Commands
ip domain-name
Defines a default domain name.
To remove the current default domain name, use the no form of this command. You do not have to specify the domain name.
ip domain-name domain-name
no ip domain-name
Syntax Description
domain-name |
Default domain name used to complete hostnames that do not specify a domain. Do not include the initial period that separates an unqualified name from the domain name. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to configure a domain name:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip domain-name cisco.com SCE(config)#
The following example shows how to remove the configured domain name:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#no ip domain-name SCE(config)#
Related Commands
ip ftp password
Specifies the password to be used for FTP connections for the current session. The system uses this password if no password is specified with the copy ftp command.
ip ftp password [password]
Syntax Description
password |
Password for FTP connections. |
Defaults
The default password is admin.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to set the password to be used in the FTP connection to mypw:
SCE>enable 10 Password:<cisco> SCE#ip ftp password mypw SCE#
Related Commands
ip ftp username
Configures the username for FTP connections for the current session. This username is used if no username is specified with the copy ftp command.
ip ftp username [username]
Syntax Description
username |
Username for FTP connections. |
Defaults
The default username is anonymous.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to set myname as the username for FTP connections:
SCE>enable 10 Password:<cisco> SCE#ip ftp username myname SCE#
Related Commands
ip host
Adds a hostname and address to the host table.
To remove a hostname and address from the host table, use the no form of this command.
ip host hostname ip-address
no ip host hostname [ip-address]
Syntax Description
hostname |
Hostname to be added or removed. |
ip-address |
Host IP address in x.x.x.x format. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to add a host to the host table:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip host PC85 10.1.1.1 SCE(config)#
Related Commands
|
|
|
show hosts |
Displays the default domain name, the address of the name server, and the contents of the host table. |
ip name-server
Specifies the address of one or more servers to use for name and address resolution. The system maintains a list of up to three name servers. If the current list is not empty, the command adds the specified servers to the list.
To remove specified servers from the current list, use the no form of this command.
ip name-server server-address1 [server-address2] [server-address3]
no ip name-server
Syntax Description
server-address1 |
IP address of the name server. |
server-address2 |
IP address of an additional name server. |
server-address3 |
IP address of an additional name server. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to add the DNS 10.1.1.1 and 10.1.1.2 to the list of configured servers:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip name-server 10.1.1.1 10.1.1.2 SCE(config)#
Related Commands
|
|
|
ip domain-lookup |
Enables or disables domain name lookups. |
show hosts |
Displays the default domain name, the address of the name server, and the contents of the host table. |
ip radius-client retry limit
Configures the parameters for retransmitting unacknowledged RADIUS client messages.
ip radius-client retry limit [times] [timeout timeout]
Syntax Description
times |
Maximum number of times the RADIUS client can try unsuccessfully to send a message. |
timeout |
Timeout interval for retransmitting a message, in seconds |
Defaults
The default for times is 3.
The default for timeout is 5 seconds.
Command Modes
Global Configuration
Usage Guidelines
Because of the unreliable nature of UDP, the RADIUS client retransmits requests to the SCMP peer device if they were not acknowledged within the configured number of seconds. Messages that were not acknowledged can be retransmitted up to the configured maximum number of retries.
The optional timeout keyword limits the time interval for retransmitting a message.
Authorization: admin
Examples
The following example shows how to configure the retransmission parameters:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)# ip radius-client retry limit 5 timeout 5
SCE(config)#
Related Commands
|
|
|
scmp name |
Adds an SCMP peer device. |
show ip radius-client |
Displays the RADIUS client general configuration. |
ip route
Adds an IP routing entry to the routing table.
To remove an IP routing entry from the routing table, use the no form of this command.
ip route ip-address mask [next-hop]
no ip route prefix mask [next-hop]
no ip route all
Syntax Description
ip-address |
IP address of the new entry. |
mask |
Relevant subnet mask. |
next-hop |
Next hop in the route. |
all |
Used with the no form of the command, removes all IP routing entries from the routing table. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
All addresses must be in dotted notation.
The next-hop address must be within the Management Interface subnet.
Authorization: admin
Examples
The following example shows how to set the next-hop address for IP addresses in the specified range:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip route 10.10.10.0 255.255.255.0 20.2.2.2 SCE(config)#
The following example shows how to remove the entry added in the previous example:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#no ip route 10.10.10.0 255.255.255.0 SCE(config)#
Related Commands
|
|
|
show ip route |
Displays the entire routing table and the destination of last resort (default gateway). |
ip rpc-adapter
Enables the RPC adapter.
To disable the RPC adapter, use the no form of this command.
ip rpc-adapter
no ip rpc-adapter
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to enable the RPC adapter:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip rpc-adapter SCE(config)#
The following example shows how to disable the RPC adapter:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#no ip rpc-adapter SCE(config)#
Related Commands
ip rpc-adapter port
Defines the RPC adapter port.
To reset the RPC adapter port assignment to the default port of 14374, use the default form of this command.
ip rpc-adapter port [port-number]
default ip rpc-adapter port
Syntax Description
port-number |
Number of the port assigned to the RPC adapter. |
Defaults
The default port number is 14374.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to configure the RPC interface, specifying 1444 as the RPC adapter port:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip rpc-adapter SCE(config)#ip rpc-adapter port 1444
The following example shows how reset the RPC adapter port:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#default ip rpc-adapter port
Related Commands
|
|
|
ip rpc-adapter |
Enables the RPC adapter. |
show ip rpc-adapter |
Displays the status of the RPC adapter and the configured port. |
ip rpc-adapter security-level
Sets the PRPC server security level.
ip rpc-adapter security-level [level]
Syntax Description
level |
Security level for the PRPC server. Choose full, semi, or none. See Usage Guidelines for more information. |
Defaults
The default security level is semi.
Command Modes
Global Configuration
Usage Guidelines
Specify the PRPC server security level as follows:
•![]() full—All PRPC connections require authentication.
full—All PRPC connections require authentication.
•![]() semi—PRPC connections that supply a username and password during connection establishment are authenticated. Connections that do not supply a username and password are accepted with no authentication.
semi—PRPC connections that supply a username and password during connection establishment are authenticated. Connections that do not supply a username and password are accepted with no authentication.
•![]() none—No authentication is performed.
none—No authentication is performed.
Authorization: admin
Examples
The following example shows how to set the PRPC server security level:
SCE>enable 10 Password:<cisco> SCE#configure SCE(config)#ip rpc-adapter security-level full SCE>
Related Commands
|
|
|
ip rpc-adapter |
Enables the RPC adapter. |
show ip rpc-adapter |
Displays the status of the RPC adapter and the configured port. |
ip ssh
Enables the SSH server.
To disable the SSH server, use the no form of this command.
ip ssh [sshv1]
no ip ssh [sshv1]
Syntax Description
sshv1 |
Enables SSHv1. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
If the sshv1 keyword is not specified, both SSHv1 and SSHv2 are enabled. If you want to enable only SSHv2, use the no form of this command to disable SSHv1. Use the ip ssh sshv1 command to reenable SSHv1.
When using an SSH server, you should also generate an SSH key set (ip ssh key command). A set of keys must be generated at least once before enabling the SSH server.
Authorization: admin
Examples
The following example shows how to enable the SSH server. Both SSHV1 and SSHv2 are enabled.
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip ssh SCE(config)#
The following example shows how to disable the SSH server:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#no ip ssh SCE(config)#
The following example shows how to disable SSHv1 so that only SSHv2 is enabled:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip ssh
SCE(config)#no ip ssh sshv1
SCE(config)#
Related Commands
|
|
|
ip ssh key |
Generates or removes the SSH key set. |
show ip ssh |
Displays the status of the SSH server, including current SSH sessions. |
ip ssh key
Generates or removes the SSH key set. A set of keys must be generated at least once before enabling the SSH server.
ip ssh key [generate | remove]
Syntax Description
generate |
Generates a new SSH key set and saves it to nonvolatile memory. Key size is always 2048 bits. |
remove |
Removes the existing key set. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
Each SSH server should define a set of keys (DSA2, RSA2, and RSA1) to be used when communicating with various clients. The key sets are pairs of public and private keys. The server publishes the public key, while keeping the private key in nonvolatile memory. The private key is never transmitted to SSH clients.
Note that the keys are kept on the /system/ file, which means that a person with knowledge of the enable password can access both the private and public keys. The SSH server implementation provides protection against eavesdroppers who can monitor the management communication channels of the SCE platform, but it does not provide protection against a user with knowledge of the enable password.
When using an SSH server, you should also enable the SSH server (ip ssh command).
Authorization: admin
Examples
The following example shows how to generate a new SSH key set:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip ssh key generate SCE(config)#
The following example shows how to remove the SSH key set:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#ip ssh key remove SCE(config)#
Related Commands
|
|
|
ip ssh |
Enables the SSH server. |
ip ssh access-class |
|
show ip ssh |
Displays the status of the SSH server, including current SSH sessions. |
ip-tunnel gre skip
Enables the recognition of G RE tunnels and skipping into the internal IP packet.
To disable tunnel recognition and classify traffic by the external IP address, use the no form of this command.
ip-tunnel gre skip
no ip-tunnel gre skip
Syntax Description
This command has no arguments or keywords.
Defaults
IP tunnel recognition is disabled.
Command Modes
Linecard Interface Configuration
Usage Guidelines
GRE is an IP-based tunneling protocol. If GRE tunnel recognition is not configured, the system treats the external IP header as the subscriber traffic. All of the flows in the tunnel are seen as a single flow.
IP tunnel mode is mutually exclusive with other VLAN-based classifications.

Authorization: admin
Examples
The following example shows how to use this command. Note that you must access the root level to shut down the line card, even though the DSCP marking command is at the admin level.
SCE>enable 15
Password:<cisco>
SCE#> configure
SCE(config)#>interface linecard 0
SCE(config if)#>shutdown
SCE(config if)#>ip-tunnel gre skip
SCE(config if)#>no shutdown
Related Commands
|
|
|
|---|---|
show interface linecard ip-tunnel |
Displays the current IP tunnel configuration. |
ip-tunnel dscp-marking-skip
Configures the SCE platform to perform DSCP marking on the internal IP header of IPinIP or GRE traffic.
To perform DSCP marking on the external IP header, use the no form of this command.
ip-tunnel (gre | ipinip) dscp-marking-skip
no ip-tunnel (gre | ipinip) dscp-marking-skip
Syntax Description
This command has no arguments or keywords.
Defaults
DSCP marking is performed on the external IP header (no form of the command).
Command Modes
Linecard Interface Configuration
Usage Guidelines
DSCP marking modifies the DSCP bits of the IPv4 header. IPinIP and GRE tunnels have at least two IP headers. By default, DSCP marking is performed only on the external IP header. Use this command to mark the DSCP bits of the internal IP header.
This command takes effect only when ipinip skip or gre skip is enabled (see the ip-tunnel ipinip skip command or the ip-tunnel gre skip command).

Note ![]() DSCP marking should be enabled and configured through the SCA BB console. Refer to the section "How to Manage DSCP Marker Values" in the Cisco Service Control Application for Broadband User Guide for more information.
DSCP marking should be enabled and configured through the SCA BB console. Refer to the section "How to Manage DSCP Marker Values" in the Cisco Service Control Application for Broadband User Guide for more information.

Authorization: admin
Examples
The following example shows how to configure the SCE platform to perform DSCP marking on the internal IP header of an IPinIP flow.
Note that you must access the root level to shut down the line card, even though the DSCP marking command is at the admin level.
SCE>enable 15
Password:<cisco>
SCE#> configure
SCE(config)#>interface linecard 0
SCE(config if)#>shutdown
SCE(config if)#>ip-tunnel ipinip dscp-marking-skip
SCE(config if)#>no shutdown
Related Commands
|
|
|
|---|---|
ip-tunnel gre skip |
|
ip-tunnel ipinip skip |
ip-tunnel ipinip skip
Enables the recognition of IPinIP tunnels and skipping into the internal IP packet.
To disable IPinIP skip, use the no form of this command.
ip-tunnel ipinip skip
no ip-tunnel ipinip skip
Syntax Description
This command has no arguments or keywords.
Defaults
IPinIP skip is disabled.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Use this command as follows:
•![]() IPinIP and other tunnels—IPinIP is supported simultaneously with plain IP traffic and any other tunneling protocol supported by the SCE platform.
IPinIP and other tunnels—IPinIP is supported simultaneously with plain IP traffic and any other tunneling protocol supported by the SCE platform.
•![]() Overlapping IP addresses—Overlapping IP addresses within different IPinIP tunnels are not supported.
Overlapping IP addresses—Overlapping IP addresses within different IPinIP tunnels are not supported.
•![]() IPinIP can be enabled or disabled only when no applications are loaded or the line card is shut down.
IPinIP can be enabled or disabled only when no applications are loaded or the line card is shut down.
•![]() DSCP marking—For IPinIP traffic, DSCP marking can be done on either the external or the internal IP header exclusively.
DSCP marking—For IPinIP traffic, DSCP marking can be done on either the external or the internal IP header exclusively.
See the ip-tunnel dscp-marking-skip command for more information.
Authorization: admin
Examples
The following example shows how to use this command.
Note that you must access the root level to shut down the line card, even though the ipinip command is at the admin level.
SCE>enable 15
Password:<cisco>
SCE#> configure
SCE(config)#>interface linecard 0
SCE(config if)#>shutdown
SCE(config if)#>ip-tunnel ipinip skip
SCE(config if)#>no shutdown
Related Commands
ip-tunnel l2tp skip
Configures the recognition of L2TP tunnels and skipping into the internal IP packet.
To disable tunnel recognition and classify traffic by the external IP address, use the no form of this command.
ip-tunnel l2tp skip
no ip-tunnel
Syntax Description
This command has no arguments or keywords.
Defaults
IP tunnel recognition is disabled.
Command Modes
Linecard Interface Configuration
Usage Guidelines
L2TP is an IP-based tunneling protocol. The system must be specifically configured to recognize the L2TP flows, based on the UDP port used for L2TP. The SCE platform can then skip the external IP, UDP, and L2TP headers and reach the internal IP, which is the actual subscriber traffic.
If L2TP is not configured, the system treats the external IP header as the subscriber traffic. All of the flows in the tunnel are seen as a single flow.
IP tunnel mode is mutually exclusive with other VLAN-based classifications.
To configure the port number that the LNS and LAC use for L2TP tunnels, use the l2tp identify-by command.

Authorization: admin
Examples
The following example shows how to enable recognition of L2TP tunnels.
Note that you must access the root level to shut down the line card, even though the DSCP marking command is at the admin level.
SCE>enable 15
Password:<cisco>
SCE#> configure
SCE(config)#>interface linecard 0
SCE(config if)#>shutdown
SCE(config if)#>ip-tunnel l2tp skip
SCE(config if)#>no shutdown
Related Commands
l2tp identify-by
Configures the port number that the LNS and LAC use for L2TP tunnels.
l2tp identify-by port-number [port-number]
l2tp identify-by default port
Syntax Description
port-number |
Port number to be configured for L2TP tunnels. |
default port |
Replaces the user-configured port number with the default port number (1701). |
Defaults
The default port number is 1701.
Command Modes
Linecard Interface Configuration
Usage Guidelines
If external fragmentation exists in the L2TP environment, you must configure a quick-forwarding-ignore traffic rule that bypasses all IP traffic targeted to either the LNS or LAC IP address. (See "Configuring Traffic Rules and Counters" in the Cisco SCE8000 10GBE Software Configuration Guide or "Configuring Traffic Rules and Counters" in the Cisco SCE8000 GBE Software Configuration Guide.) This rule ensures that any packets not having the L2TP port indication (that is, non-first fragments) will not require handling by the traffic processors.
In addition, to prevent reordering of L2TP tunneled fragments, you should define a quick-forwarding traffic rule for all the L2TP traffic. This rule can be based on the IP ranges in use by the internal IPs in the tunnel (as allocated by the LNS) or for all of the traffic passing through the SCE platform.
Note that flow redirection and flow blocking cannot be performed on the quick-forwarded traffic.
Authorization: admin
Examples
The following example shows how to configure port 1000 as the L2TP port:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#l2tp identify-by port-number 1000 SCE(config if)#
Related Commands
|
|
|
show interface linecard l2tp |
Displays the currently configured L2TP support parameters. |
ip-tunnel |
line vty
Enters Line Configuration mode for Telnet lines, which configures all Telnet lines.
line vty start-number [end-number]
Syntax Description
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
The system prompt changes to reflect Line Configuration mode. To return to Global Configuration mode, use the exit command.
Authorization: admin
Examples
The following example shows how to enter Line Configuration mode for all lines:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#line vty 0 SCE(config-line)#
Related Commands
|
|
|
show line vty |
Displays the Telnet configuration. |
exit |
Exits from the current mode to the next "lower" level. |
link failure-reflection
Enables link failure reflection.
To disable link failure reflection, use the no form of this command.
link failure-reflection [on-all-ports] [linecard-aware]
no link failure-reflection [linecard-aware]
Syntax Description
Defaults
Link failure reflection is disabled.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Use the linecard-aware keyword when each link of the SCE8000 10GBE platform (subscriber-side interface and the corresponding network-side interface) is connected to a different line card.
This mode reflects a failure of one port to the other three ports of the SCE8000 10GBE platform differently, depending on whether the failure appears to be in the SCE platform itself or not:
•![]() One interface of the SCE8000 10GBE platform is down, indicating a problem with the SCE platform—Link failure is reflected to the other three SCE platform ports.
One interface of the SCE8000 10GBE platform is down, indicating a problem with the SCE platform—Link failure is reflected to the other three SCE platform ports.
•![]() Two reciprocal ports of the SCE8000 10GBE platform are down, indicating a problem in the line card to which the SCE platform is connected and not in the interface—No action is taken. This response allows the second link in the SCE platform to continue functioning without interruption.
Two reciprocal ports of the SCE8000 10GBE platform are down, indicating a problem in the line card to which the SCE platform is connected and not in the interface—No action is taken. This response allows the second link in the SCE platform to continue functioning without interruption.
Use the no form of this command with the linecard-aware keyword to disable linecard-aware mode without disabling link failure reflection itself.
None of the keywords can be used with the SCE8000 GBE platform.
Authorization: admin
Examples
The following example shows how to enable the reflection of a link failure to all ports (SCE8000 10GBE platform only):
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#link failure-reflection on-all-ports SCE(config if)#
The following example shows how to enable the reflection of a link failure. This form of the command is the only one that can be used on the SCE8000 GBE platform (but it can also be used on the SCE8000 10GBE platform).
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#link failure-reflection SCE(config if)#
link mode
Configures the link mode. The link mode allows you to force the specified behavior on the link, which may be useful during installation and for debugging the network.
link mode {all-links mode}
Syntax Description
all-links |
Sets the link mode for all links. (The link mode cannot be set separately for individual links.) |
mode |
Establishes the link mode. Choose forwarding, bypass, or cutoff. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#link mode all-links bypass
Related Commands
|
|
|
show interface linecard link mode |
Displays the configured Linecard Interface link mode. |
logger add-user-message
Adds a message string to the user log files.
logger add-user-message message-text
Syntax Description
message-text |
Message string you want to add. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example show how to add "testing 123" as the message to the user log files:
SCE>enable 10 Password:<cisco> SCE#logger add-user-message testing 123 SCE#
logger device
Disables or enables the specified logger device.
logger device {line-attack-file-log | statistics-file-log | user-file-log} [status]
Syntax Description
Defaults
Log devices are enabled.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to disable the User-File-Log device:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#logger device user-file-log disabled SCE(config)#
Related Commands
logger device user-file-log max-file-size
Sets the maximum size of the log file.
logger device user-file-log max-file-size [size]
Syntax Description
size |
Maximum size for the user log (in bytes). |
Defaults
The default log size is 1,000,000 bytes.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to configure the maximum size of the user-file-log device to 65000 bytes:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#logger device user-file-log max-file-size 65000 SCE(config)#
Related Commands
|
|
|
logger device |
Disables or enables the specified logger device. |
show logger device |
Displays the configuration of the specified SCE platform logger file. |
logger get support-file
Generates a log file for technical support through FTP. Note that this operation may take some time.
logger get support-file filename
Syntax Description
filename |
Name of the generated log file. The specified file must be located on an FTP site, not on the local file system. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to generate a technical support log file (via FTP) named support.zip:
SCE>enable 10 Password:<cisco> SCE#logger get support-file ftp://user:1234@10.10.10.10/c:/support.zip SCE#
Related Commands
|
|
|
logger get user-log file-name
Outputs the current user log to a target file.
logger get user-log file-name target-file
Syntax Description
target-file |
Name of the output file to which the system will write the log file information. This file can be a local path, full path, or full FTP path filename. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to retrieve the current user log files:
SCE>enable 10 Password:<cisco> SCE#logger get user-log file-name ftp://myname:mypw@10.1.1.205/d:/log.txt SCE#
Related Commands
|
|
|
logger get support-file |
Generates a log file for technical support through FTP. |
logout
Logs out of the command-line interface of the SCE platform.
logout
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
EXEC
Usage Guidelines
Authorization: user
Examples
The following example shows how to log out:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#exit SCE>logout Connection closed by foreign host.
Related Commands
|
|
|
mac-resolver arp
Adds a static IP entry to the MAC resolver database.
To remove the static IP entry from the database, use the no form of this command.
mac-resolver arp ip-address [vlan vlan-tag] mac-address
no mac-resolver arp ip-address [vlan vlan-tag] mac-address
Syntax Description
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
When adding or removing a static IP entry:
•![]() Adding an entry
Adding an entry
If a client has previously registered a dynamic entry with the same IP address and VLAN tag, the entry receives the MAC address specified in the CLI command, and the entry is changed to static.
•![]() Removing an entry
Removing an entry
If an entry has been added both as a dynamic entry and a static entry, it exists in the database as a static entry only (as explained in the previous paragraph). Removing the static configuration changes the entry from a static entry to a dynamic entry and deletes the corresponding user-configured MAC address.
Authorization: admin
Examples
The following example shows how to assign the MAC address 1111.2222.3333 to the IP address 10.20.30.40:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#interface linecard 0
SCE(config mac-resolver arp 10.20.30.40 1111.2222.3333
SCE(config if)#
Related Commands
|
|
|
show interface linecard mac-resolver arp |
Displays a listing of all IP addresses and corresponding MAC addresses currently registered in the MAC resolver database. |
management-agent sce-api ignore-cascade-violation
Configures the agent to ignore the errors issued when login operations are performed on a standby SCE platform.
To configure the agent to issue an error when a login operation is performed on a standby SCE platform, use the no form of this command.
To set the value to the default, use the default form of this command. (The default behavior is to issue an error when a login operation is performed on a standby SCE platform.)
management-agent sce-api ignore-cascade-violation
no management-agent sce-api ignore-cascade-violation
default management-agent sce-api ignore-cascade-violation
Syntax Description
This command has no arguments or keywords.
Defaults
An error is issued when a login operation is performed on a standby SCE platform (no form of the command).
Command Modes
Global Configuration
Usage Guidelines
Starting in release 3.1.0, the SCE platform issues an error message when a login operation is performed on the standby SCE platform in a cascaded system. This behavior is not backward compatible for previous versions of the SCE subscriber API.
Use this command with SCOS release 3.1.0 to provide backward-compatible behavior to earlier releases in which such errors were not issued.
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)# management-agent sce-api ignore-cascade-violation SCE(config)#
Related Commands
|
|
|
management-agent sce-api logging
Enables SCE subscriber API troubleshooting logging. This information is written to the user log.
To disable SCE subscriber API troubleshooting logging, use the no form of this command.
management-agent sce-api logging
no management-agent sce-api logging
Syntax Description
This command has no arguments or keywords.
Defaults
SCE subscriber API troubleshooting logging is disabled.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to enable SCE subscriber API troubleshooting logging:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)# management-agent sce-api logging SCE(config)#
Related Commands
|
|
|
management-agent sce-api timeout
Defines the timeout interval for disconnection of an SCE subscriber API client. After the interval is reached, the resources allocated for this client are released.
management-agent sce-api timeout [timeout-interval]
Syntax Description
timeout-interval |
Time in seconds that the client waits before timing out. |
Defaults
The default interval is 300 seconds.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to configure a timeout interval of 10 seconds:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)# management-agent sce-api timeout 10
Related Commands
|
|
|
management-agent system
Specifies a new package file to install for the management agent. The SCE platform extracts the actual image files from the specified package file only during the copy running-config startup-config command.
When using the no form of this command, you do not have to specify the package filename.
management-agent system package-filename
no management-agent system
Syntax Description
package-filename |
Name of a package file that contains the new management agent software. The name should end with the .pkg file type. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
Use this command to upgrade the SCE platform management agent. The package file is verified for the system and checked that it is not corrupted. The actual upgrade takes place only after executing the copy running-config startup-config command and rebooting the SCE platform.
Authorization: admin
Examples
The following example shows how to upgrade the system with the mng45.pkg package:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#management-agent system mng45.pkg Verifying package file... Package file verified OK. SCE(config)#do copy running-config startup-config Backing -up configuration file... Writing configuration file... Extracting new management agent... Extracted OK.
Related Commands
|
|
|
copy running-config startup-config |
Builds a configuration file with general configuration commands called config.txt, which is used in successive boots. |
mkdir
Creates a new directory.
mkdir directory-name
Syntax Description
directory-name |
Name of the directory to be created. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to create a new directory named mydir:
SCE>enable 10 Password:<cisco> SCE#mkdir mydir CE#
Related Commands
|
|
|
dir |
Displays the files in the current directory. |
more
Displays the contents of a file.
more {filename | running-config [all-data] | startup-config}
Syntax Description
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
You can use the all-data keyword with the running-config keyword to see sample usage for many CLI configuration commands.
Authorization: admin
Examples
The following sample output displays the contents of the running configuration file:
SCE>enable 10 Password:<cisco> SCE#more running-config #This is a general configuration file (running-config). #Created on 16:48:11 UTC WED June 13 2001 cli-type 1 #version 1 service logger no service password-encryption enable password level 10 0 "cisco" enable password level 15 0 "cisco" service RDR-formatter no RDR-formatter destination all RDR-formatter history-size 0 clock timezone UTC 0 ip domain-lookup no ip domain-name no ip name-server service telnetd FastEthernet 0/0 ip address 10.1.5.120 255.255.0.0
auto duplex auto exit ip default-gateway 10.1.1.1 no ip route all line vty 0 4 no access-class in timeout 30 exit SCE#
Related Commands
|
|
|
show running-config |
Displays the current configuration. |
show startup-config |
Displays the startup configuration file. |
more user-log
Displays the user log on the CLI console screen.
more user-log
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to display the user log on the CLI console screen:
SCE>enable 10 Password:<cisco> SCE#more user-log <INFO>| 01/28/97 22:29:22 | CPU #000 | Logger: Task Initialized successfully
Related Commands
|
|
|
logger get user-log file-name |
Outputs the current user log to a target file. |
show log |
Displays the contents of the user log file. |
mpls
Configures the MPLS environment. Up to a maximum of 15 MPLS labels per packet are supported.
When all IP addresses are unique and MPLS labels are not mandatory (a non-MPLS/VPN environment), use the traffic-engineering skip form of this command.
To set the MPLS configuration to the default value, use the default form of this command.
mpls traffic-engineering skip
mpls vpn skip
default mpls
Syntax Description
See Usage Guidelines.
Defaults
traffic-engineering skip is enabled.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Use this command as follows:
•![]() traffic-engineering skip
traffic-engineering skip
Any packets that are injected by the SCE into the MPLS labeled traffic (block or redirect) are sent with no MPLS labels. Use this mode when the MPLS labels in the traffic are used only for traffic engineering, such as QOS, and not for routing.
This mode is the default, and it should be changed only if MPLS is used for routing in the network and block or redirect is being employed. However, first verify that no private IP conflicts exist in the network.
•![]() vpn skip
vpn skip
Use this command when all IP addresses are unique, MPLS labels are used, and the labels used for injection are the correct ones, as seen on the flow. This mode can be used when the MPLS labels are used for routing or for VPNs (assuming no private IP addresses are being used).
The vpn skip mode is an asymmetric Layer 2 mode. You should expect reduced performance and capacity, because the system must follow the flow and keep the Layer 2 information.
Authorization: admin
Examples
The following example shows the use of this command in a non-MPLS/VPN environment:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#mpls traffic-engineering skip SCE(config if)#
Related Commands
|
|
|
show interface linecard mpls |
no subscriber
Removes a specified subscriber from the system.
no subscriber name subscriber-name
no subscriber scmp name scmp-name all
no subscriber sm all
no subscriber all [with-vpn-mappings]
Syntax Description
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines

Authorization: admin
Examples
The following example shows how to remove all subscribers:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)# no subscriber all
SCE(config if)#
Related Commands
|
|
|
show interface linecard subscriber |
Displays subscribers that meet specified criteria. |
no subscriber mappings included-in
Removes all existing subscriber mappings from a specified IP range.
no subscriber mappings included-in ip-range ip-range
Syntax Description
ip-range |
Removes all existing subscriber mappings from the specified IP range. |
ip-range |
IP address and mask length defining the IP range. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to remove any existing subscriber mappings from the specified IP range:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)# no subscriber mappings included-in ip-range 10.10.10.10/0
Related Commands
|
|
|
periodic-records aggregate-by-cpu
Enables RDR aggregation for the specified RDRs. By default, RDR aggregation is enabled.
Use the no form of the command to disable record aggregation.
The SCE platform aggregates certain RDRs, thus reducing the load on the CM without affecting the usability of the information provided. The RDR aggregation feature is relevant only to global records. More specifically, only periodic records are aggregated, because other records relate to events like a single transaction or flow, and cannot be aggregated across processors - if they are aggregated, they loose the required granularity.
Currently the following RDRs are aggregated:
•![]() Virtual Link Usage RDRs (VLURs )
Virtual Link Usage RDRs (VLURs )
•![]() Link Usage RDRs (LURs)
Link Usage RDRs (LURs)
•![]() Package Usage RDRs (PURs)
Package Usage RDRs (PURs)
periodic-records aggregate-by-cpu [all | LUR | PUR | VLUR]
no periodic-records aggregate-by-cpu [all | LUR | PUR | VLUR]
Syntax Description
all |
Enables or disables aggregation of all relevant types of RDRs. |
LUR | PUR | VLUR |
Enables or disables aggregation of the specified type of RDR only. |
Defaults
By default, all record types are aggregated.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Authorization: admin
Examples
The following example illustrates how to disable RDR aggregation for PURs.
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#interface linecard 0
SCE(config if)#no periodic-records aggregate-by-cpu PUR
SCE(config if)#
Related Commands
|
|
|
|---|---|
show interface linecard periodic-records aggregation |
ping
Pings a host to test for connectivity. The ping program sends a test message (packet) to an address and then awaits a reply. Ping output can help you evaluate path-to-host reliability, delays over the path, and whether the host can be reached or is functioning.
ping hostname
Syntax Description
hostname |
Hostname or IP address of a remote station to ping. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to ping host 10.1.1.201:
SCE>enable 10 Password:<cisco> SCE#ping 10.1.1.201 pinging 10.1.1.201... PING 10.1.1.201: 56 data bytes 64 bytes from host (10.1.1.201): icmp_seq=0. time=0. ms 64 bytes from host (10.1.1.201): icmp_seq=1. time=0. ms 64 bytes from host (10.1.1.201): icmp_seq=2. time=0. ms 64 bytes from host (10.1.1.201): icmp_seq=3. time=0. ms ----10.1.1.201 PING Statistics---- 4 packets transmitted, 4 packets received, 0% packet loss round-trip (ms) min/avg/max = 0/0/0 SCE#
Related Commands
|
|
|
pqi install file
Installs the specified pqi file using the installation options specified (if any). This procedure may take up to 5 minutes.
pqi install file filename [options options]
Syntax Description
filename |
Filename of the pqi application file to be installed. |
options |
Installation options. Use the show pqi file command to display the available options. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Always run the pqi uninstall file command before installing a new pqi file to prevent the accumulation of old files on the disk.
Authorization: admin
Examples
The following example shows how to install the Subscriber Manager anr10015.pqi file. No options are specified.
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#pqi install file anr10015.pqi SCE(config if)#
Related Commands
|
|
|
show pqi file |
Displays information about the specified application file. |
pqi uninstall file |
Uninstalls the specified pqi file. |
pqi rollback file
Reverses an upgrade of the specified pqi file. This procedure may take up to 5 minutes.
pqi rollback file filename
Syntax Description
filename |
Filename of the pqi application file to be rolled back. The file must be the pqi file that was last upgraded. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Always specify the last pqi file that was upgraded. To find the name of this file, use the show pqi last-installed command.
Authorization: admin
Examples
The following example shows how to reverse the upgrade for the Subscriber Manager using the anr100155.pqi file:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#pqi rollback file anr100155.pqi SCE(config if)#
Related Commands
|
|
|
show pqi last-installed |
Displays the name of the last pqi file that was installed. |
pqi uninstall file
Uninstalls the specified pqi file. This procedure may take up to 5 minutes.
pqi uninstall file filename
Syntax Description
filename |
Filename of the pqi application file to be uninstalled. The file must be the pqi file that was installed last. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Always specify the last pqi file that was installed. To find the name of this file, use the show pqi last-installed command.
Always run the pqi uninstall command before installing a new pqi file to prevent the accumulation of old files on the disk.
Authorization: admin
Examples
The following example shows how to uninstall the Subscriber Manager anr10015.pqi file:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#pqi uninstall file anr10015.pqi SCE(config if)#
Related Commands
|
|
|
show pqi last-installed |
Displays the name of the last pqi file that was installed. |
pqi install file |
Installs the specified pqi file using any specified installation options. |
pqi upgrade file
Upgrades the application using the specified pqi file and any specified upgrade options. This procedure may take up to 5 minutes.
pqi upgrade file filename [options options]
Syntax Description
filename |
Filename of the pqi application file to be used for the upgrade. |
options |
Upgrade options. Use the show pqi file command to display the available options. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
A pqi upgrade file is suitable for upgrading only from specific previously installed pqi files. The upgrade procedure checks that an upgrade is possible from the currently installed pqi file. The upgrade procedure will be stopped with an error message if the upgrade is not possible.
When upgrading the application in a cascaded system, use the force failure-condition command to force failure in the active SCE8000 platform. (See System Upgrades in the Cisco SCE8000 10GBE Software Configuration Guide or System Upgrades in the Cisco SCE8000 GBE Software Configuration Guide.)
Authorization: admin
Examples
The following example shows how to upgrade the Subscriber Manager using the anr100155.pqi file. No options are specified.
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#pqi upgrade file anr100155.pqi SCE(config if)#
Related Commands
pwd
Displays the current working directory.
pwd
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to display the current working directory (system):
SCE>enable 10 Password:<cisco> SCE#pwd system: SCE#
Related Commands
|
|
|
cd |
Changes the path of the current working directory. |
queue
Sets the queue shaping.
queue queue-number bandwidth bandwidth burst-size burstsize
Syntax Description
Defaults
The default bandwidth is 100000K (100 Mbps).
The default burst size is 8000 (8K bytes).
Command Modes
TenGigabitEthernet Interface Configuration
Usage Guidelines
This command is valid for a specified TenGigabitEthernet line interface only. It must be executed explicitly for each interface.
Use the interface tengigabitethernet command to access the configuration mode for the desired interface.
Authorization: admin
Examples
The following example shows how to configure queue shaping for queue 1 for the 10GBE interface in bay 3:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface TenGigabitEthernet 3/3/0 SCE(config if)#queue 1 bandwidth 20000 burstsize 1000
Related CommandsE
rdr-formatter category number
Assigns a meaningful name to a category. This category name can then be used in any rdr-formatter command in place of the category number.
To disassociate the name from the category, use the no form of this command. The name will not be recognized by any CLI commands.
rdr-formatter category number number name category-name
no rdr-formatter category number number name category-name
Syntax Description
number |
Number of the category. Can be 1 to 4. |
category-name |
User-defined name to be assigned to the category. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to assign a name (prepaid) to Category 1:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#rdr-formatter category number 1 name prepaid SCE(config)#
Related Commands
rdr-formatter destination
Configures an RDRv1 or NetFlow destination. The RDR formatter sends the records (RDRs or export packets) it produces to this destination.
To remove the mappings of a destination to categories, use the no form of this command. When all categories for a destination are removed, the entire destination is removed.
rdr-formatter destination ip-address port port-number [category {name category-name}| {number number}] [priority priority-value ] [category ...] protocol {rrdrv1 | netflowv9} [transport {udp | tcp}]
no rdr-formatter destination ip-address port port-number [category {name category-name }| {number number}]
no rdr-formatter destination all
Syntax Description
Defaults
The default protocol is RDRv1.
Command Modes
Global Configuration
Usage Guidelines
Up to eight destinations can be configured. Multiple destinations over the same category must have distinct priorities. In redundancy mode, the entry with the highest priority is used by the RDR formatter; in multicast mode or load-balancing mode, priorities have no meaning.
In its simplest form, this command specifies only the IP address and port number of the destination and the protocol being used. In addition, a global priority may be assigned to the destination. Or, a specific priority may be assigned to any or all of the four categories for the specified destination. If a global priority is not explicitly configured, the highest priority is assigned automatically.
Categories may be identified by either name or number.
A specific destination may be configured to one or more categories at the same time. A maximum of three destinations may be assigned to a specific category.

Note ![]() RDRv1 may be configured only with the transport type of TCP. NetFlowV9 may be configured only with the transport type of UDP.
RDRv1 may be configured only with the transport type of TCP. NetFlowV9 may be configured only with the transport type of UDP.
Priorities
The following guidelines apply to configuring priorities for report destinations:
•![]() In redundancy mode, the entry with the highest priority is used by the RDR formatter, provided that a connection with this destination can be established.
In redundancy mode, the entry with the highest priority is used by the RDR formatter, provided that a connection with this destination can be established.
•![]() Priority configuration is not relevant in multicast mode, because all reports are sent to all destinations.
Priority configuration is not relevant in multicast mode, because all reports are sent to all destinations.
•![]() Priority configuration is not relevant in load-balancing mode, because all destinations are used for load balancing.
Priority configuration is not relevant in load-balancing mode, because all destinations are used for load balancing.
•![]() For the first destination defined, if no priority is set, the highest priority is automatically assigned.
For the first destination defined, if no priority is set, the highest priority is automatically assigned.
•![]() For all subsequently defined destinations, the priority must be explicitly defined; otherwise, it will collide with the first destination priority.
For all subsequently defined destinations, the priority must be explicitly defined; otherwise, it will collide with the first destination priority.
•![]() You can also assign a different priority to each category for each destination. If no category is specified, the same priority is assigned to all categories for that destination.
You can also assign a different priority to each category for each destination. If no category is specified, the same priority is assigned to all categories for that destination.
•![]() The same priority cannot be assigned to the same category for two different destinations.
The same priority cannot be assigned to the same category for two different destinations.
Authorization: admin
Examples
The following example shows how to configure a NetFlow destination with the default priority (highest) to be used by all categories:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#rdr-formatter destination 10.1.1.205 port 33000 protocol netflowv9 transport udp SCE(config)#
The following example shows how to configure an RDR formatter destination for two categories with a different priority for each category. This configuration sends RDRs from category 2 to this destination, but usually not RDRs from category 1.
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#rdr-formatter destination 10.1.1.206 port 34000 category number 1 priority 10 category number 2 priority 90 protocol rrdrv1 SCE(config)#
Related Commands
rdr-formatter destination protocol netflowv9 template data timeout
Configures the interval after which all NetFlow templates must be exported to the specified destination (refreshed).
To disable the template refresh mechanism, use the no form or the default form of this command.
rdr-formatter destination ip-address port port-number protocol netflowv9 template data timeout timeout-value
no rdr-formatter destination ip-address port port-number protocol netflowv9 template data
default rdr-formatter destination ip-address port port-number protocol netflowv9 template data
Syntax Description
Defaults
The refresh mechanism is disabled.
Command Modes
Global Configuration
Usage Guidelines
A template record defines the structure of each NetFlow data record. The RDR formatter transmits only the templates along with their matching data records. The RDR formatter refreshes the templates on the collector by resending them at configured intervals.
The no form of the command disables the refresh mechanism.
The default form of the command also disables the refresh mechanism, because the default state is disabled.
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#rdr-formatter destination 10.1.1.205 port 33000 protocol netflowv9 template data timeout 240 SCE(config)#
Related Commands
rdr-formatter forwarding-mode
Defines the mode in which the RDR formatter sends RDRs to the destinations.
rdr-formatter forwarding-mode [mode]
Syntax Description
mode |
Choose redundancy, multicast, or simple-load-balancing, as described in Table 2-5 in Usage Guidelines. |
Defaults
The default mode is redundancy.
Command Modes
Global Configuration
Usage Guidelines
Table 2-6 lists the valid mode settings.
Authorization: admin
Examples
The following example shows how to set the RDR formatter mode to redundancy:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#rdr-formatter forwarding-mode redundancy SCE(config)#
Related Commands
|
|
|
show rdr-formatter forwarding-mode |
Displays the configured RDR formatter forwarding mode. |
rdr-formatter history-size
Configures the size of the history buffer. This command is currently not supported.
rdr-formatter history-size [size]
Syntax Description
size |
Size of the history buffer in bytes. Must be 0 (the default). |
Defaults
The default size is 0.
Command Modes
Global Configuration
Usage Guidelines
Do not change the size of the history buffer from the default value.
Because currently only RDRv1 is supported, the size of the history buffer must be zero bytes, even though the system will accept a command specifying a larger size.
Authorization: admin
Examples
None (command currently not supported).
Related Commands
|
|
|
show rdr-formatter history-size |
Displays the configured size of the RDR formatter history buffer. |
rdr-formatter protocol netflowv9 dscp
Defines the DSCP value to be assigned to the NetFlow packets.
rdr-formatter protocol netflowv9 dscp dscp-value
Syntax Description
dscp-value |
DSCP value to be assigned to the NetFlow packets, in hexadecimal format. Valid range is 0 to 63. |
Defaults
The default DSCP value is 0.
Command Modes
Global Configuration
Usage Guidelines
You can assign a DSCP value to specify the diffserv value of the NetFlow traffic exported from your SCE platform.
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#rdr-formatter protocol netflowv9 dscp 0x20 SCE(config)#
Related Commands
|
|
|
show rdr-formatter protocol netflowv9 dscp |
Displays the DSCP value assigned by NetFlowV9. |
rdr-formatter rdr-mapping
Adds a dynamic RDR mapping to a category or removes one from a category.
To remove an existing mapping, use the no form of this command.
rdr-formatter rdr-mapping [tag-id tag-number category-number category-number]
no rdr-formatter rdr-mapping [tag-id tag-number category-number category-number]
Syntax Description
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
The configuration of categories to RDR tags is done by adding and removing mappings. You can add a mapping of RDR tag to a category and remove a mapping, including the default mapping. If the table already contains a mapping with the same tag and category number, an error is issued and nothing is done.
If all categories are removed from a tag, the tag is ignored and is not formatted and sent. This process is `ignore mapping'.
Authorization: admin
Examples
The following example shows how to add a mapping to a category:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#rdr-formatter rdr-mapping tag-id 0xf0f0f000 category-number 1
SCE(config)#
The following example shows how to restore the default mapping for a specified RDR tag:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#default rdr-formatter rdr-mapping tag-id 0xf0f0f000 SCE(config)#
Related Commands
|
|
|
show rdr-formatter rdr-mapping |
Displays to which RDR formatter category a specified RDR tag is mapped. |
reload

Note ![]() To not lose the current configuration, use the copy running-config-all startup-config-all command before using the reload command.
To not lose the current configuration, use the copy running-config-all startup-config-all command before using the reload command.
Reboots the SCE platform.
reload
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to back up the configuration and perform a system reboot:
SCE>enable 10 Password:<cisco> SCE#copy running-config-all startup-config-all SCE#reload Are you sure? Y The system is about to reboot, this will end your CLI session
Related Commands
reload shutdown
Shuts down the SCE platform, preparing it to be turned off.
reload shutdown
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Use this command to shut down the SCE platform in an orderly manner before turning it off. After issuing this command, the only way to revive the SCE platform from its power-down state is to turn it off, then back on.
This command can only be issued from the serial CLI console port. When issued during a Telnet CLI session, an error message is returned and the command is ignored. This response prevents the possibility of shutting the platform down from a remote location, from which it is not possible to power back up.
Authorization: admin
Examples
The following example shows how to shut down the SCE platform:
SCE>enable 10 Password:<cisco> SCE#reload shutdown You are about to shut down the system. The only way to resume system operation after this is to cycle the power off, and then back on. Continue? Y IT IS NOW SAFE TO TURN THE POWER OFF.
Related Commands
|
|
|
reload |
Reboots the SCE platform. |
rename
Changes the filename to the specified name.
rename existing-filename new-filename
Syntax Description
existing-filename |
Original name of the file. |
new-filename |
New name of the file. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to change the name of file test1.pkg to test3.pkg:
SCE>enable 10 Password:<cisco> SCE#rename test1.pkg test3.pkg SCE#
Related Commands
|
|
|
rmdir
Removes an empty directory.
To remove a directory that is not empty, use the delete command with the /recursive switch.
rmdir directory-name
Syntax Description
directory-name |
Name of the directory to be removed. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
You can only remove an empty directory. Use the dir command to verify that no files are listed in this directory.
Authorization: admin
Examples
The following example shows how to delete the directory named code:
SCE>enable 10 Password:<cisco> SCE#rmdir code SCE#
Related Commands
|
|
|
dir |
Displays the files in the current directory. |
delete |
Deletes a file from the local flash file system. |
salt
Configures the value of the salt to be applied to the Personally Identifying Field of Extended Transaction Usage RDRs before hashing it.
To reset the salt to the default value, use the default form of this command.
salt salt-value1 salt-value2 salt-value3 salt-value4
default salt
Syntax Description
salt-value1 ... salt-value4 |
Four 4-byte salt values in hexadecimal format. |
Defaults
The default salt value is 0x12345678 0x12345678 0x12345678 0x12345678.
Command Modes
Linecard Interface Configuration
Usage Guidelines
When generating Extended Transaction Usage RDRs for analyzing subscriber browsing patterns, you must hash the Personally Identifying Field to protect the identity of the subscriber. This command configures the salt to be applied to the field before hashing.
Always save the running configuration using the copy running-config startup-config command.
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10
Password:<cisco>
SCE#configure
SCE(config)#interface linecard 0
SCE(config if)#salt 0xfafafafa 0xfafafafa 0xfafafafa 0xfafafafa
SCE(config if)#
sce-url-database add-entry
Adds a single entry to the protected URL database.
sce-url-database add-entry url-wildcard url-wildcard-format flavor-id flavor-id
Syntax Description
url-wildcard-format |
(* | [*] [host-suffix] | [*] [host-suffix] / [url-prefix [*]] [url-suffix] See Table 2-7 for examples of how to define the URL. |
flavor-id |
ID of the flavor to be applied to the entry. The specified flavor must be the one that was designated for the blacklist in the pqb file that was applied; otherwise, the operation will fail. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Use this command to add only a few new entries to the database. Add a large number of new URLs by importing an updated protected URL database file.
Table 2-6 includes URL examples.
The user executing the command must have write permission for the protected URL database.
Authorization: admin
Examples
The following example shows how to add an entry to the database. Because the flavor ID is included in the command, it is not present in the import file.
SCE>enable 10
Password:<cisco>
SCE#>configure
SCE(config)#interface linecard 0
SCE(config if)#sce-url-database add-entry url-wildcard *.com/media*mp4?download flavor-id
50
SCE(config if)#
Related Commands
sce-url-database import
Imports entries from an encrypted or clear-text file into the protected URL database.
sce-url-database import {cleartext-file | encrypted-file filename} [flavor-id flavor-id]
Syntax Description
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
An encrypted file can be imported only if a matching encryption key has been configured. (See sce-url-database protection.)
Guidelines for Managing the Protected URL Database
•![]() The user executing the command must have write permission for the protected URL database.
The user executing the command must have write permission for the protected URL database.
•![]() When a new file is imported, the existing database is cleared before the import. Incremental updating is not supported, so the import file must contain all the relevant URLs, not just new ones to be added to the database.
When a new file is imported, the existing database is cleared before the import. Incremental updating is not supported, so the import file must contain all the relevant URLs, not just new ones to be added to the database.
•![]() Add a large number of new URLs by importing an updated protected URL database file. Typically, if the database is protected, this process is done with an encrypted file.
Add a large number of new URLs by importing an updated protected URL database file. Typically, if the database is protected, this process is done with an encrypted file.
•![]() Add a few new URLs by adding them with the sce-url-database add-entry command.
Add a few new URLs by adding them with the sce-url-database add-entry command.
Protected URL Database Import File
The database import file may either contain clear text or be encrypted. If the file is encrypted, the matching encryption key must be configured by the database owner.
If the file is encrypted, it must be prefixed with a clear-text header. The encrypted file header format must be exactly as follows:
Encrypted file version: 0x01
Block cipher index: 0x01
Mode of operation index: 0x02
Padder index: 0x02
IV length: 0x10
IV: <16 unformatted bytes that form the 128 bits IV of the encrypted data>
After the header, the following data should appear in AES 128, CFB mode, encrypted format:
A random number (in the range 16 to 31) of random bytes, followed by the word "Signed" and then another 32 random bytes
Each subsequent line represents a single URL.
Protected URL Database Import File Format
[flavor Tab] url
where:
•![]() flavor—The flavor ID must either be included for every line in the file or for none of the lines. The flavor must be separated from the URL by a tab.
flavor—The flavor ID must either be included for every line in the file or for none of the lines. The flavor must be separated from the URL by a tab.
•![]() url—(* | [*] [host-suffix] | [*] [host-suffix] / [url-prefix [*]] [url-suffix] [? params-prefix])
url—(* | [*] [host-suffix] | [*] [host-suffix] / [url-prefix [*]] [url-suffix] [? params-prefix])
See Table 2-7 for examples of how to define the URL.
Results
•![]() The SCE URL database is first cleared.
The SCE URL database is first cleared.
•![]() The entries from the file are written to the database.
The entries from the file are written to the database.
•![]() Duplicate keys in the file are overwritten with no warning.
Duplicate keys in the file are overwritten with no warning.
•![]() In case of a failure, writing continues to the next entry.
In case of a failure, writing continues to the next entry.
The total number of failures and a listing of the failed file line numbers are reported when the import is finished.
Authorization: admin
Examples
The following example shows how to import the protected URL database from an encrypted file. Because the flavor ID is included in the command, it is not present in the import file.
SCE>enable 10 Password:<cisco> SCE#>configure SCE(config)#interface linecard 0 SCE(config if)#sce-url-database import encrypted-file blacklist-file flavor-id 50
SCE(config if)#
Related Commands
sce-url-database protection
Configures user authorization for the protected URL database.
To remove either all protection settings or only the encryption key, use the no form of this command.
sce-url-database protection owner {myself | name username}
sce-url-database protection allow-write {all-users | owner-only}
sce-url-database protection allow-lookup {owner-only | no-user}
sce-url-database protection encryption-key encryption-key
no sce-url-database protection
no sce-url-database protection encryption-key
Syntax Description
Defaults
•![]() The database does not have a designated owner.
The database does not have a designated owner.
•![]() Read permission—no-user. This setting is not configurable.
Read permission—no-user. This setting is not configurable.
•![]() Write permission:
Write permission:
–![]() If no owner has been assigned, the default is all-users.
If no owner has been assigned, the default is all-users.
–![]() If an owner has been assigned, the default is owner-only.
If an owner has been assigned, the default is owner-only.
•![]() Lookup permission:
Lookup permission:
–![]() If no owner has been assigned, the default is all-users.
If no owner has been assigned, the default is all-users.
–![]() If an owner has been assigned, the default is no-user.
If an owner has been assigned, the default is no-user.
•![]() Encryption key—No key.
Encryption key—No key.
Command Modes
Linecard Interface Configuration
Usage Guidelines
When the protected URL database is protected, one user is designated as the owner of the database and only that user can execute the protection CLI commands on the database. The database manipulation commands are restricted according to the owner configuration. This restriction requires defining the AAA authorization method (either based on local users or based on a TACACS+ server, and so on) and defining at least one user who should be assigned as the owner of the database.
If the database is defined to be protected, none of the database information (including the owner, the database entries, and the authorization information itself) is accessible to any users, including the relevant saved configuration in the log files and in the relevant SCA BB reports. The database-owner user may change the authorizations using the CLI; however, when any of the protections are relaxed (or all of the protections are relaxed by removing the protections entirely) the database is reset.
To ensure the secrecy of the database information, the database entries may be imported to the SCE (using the CLI) in an encrypted form using 128-, 192-, or 256-bit key length AES. The key may be set or updated using the appropriate CLI command; typically, this command should be run over a secure Telnet session.
User Authorization Guidelines
•![]() The default user cannot be the owner.
The default user cannot be the owner.
•![]() When no owner is designated, the SCE URL database is unprotected, and the contents can be read and modified by any user.
When no owner is designated, the SCE URL database is unprotected, and the contents can be read and modified by any user.
•![]() Only the owner can configure the protection settings. If no owner is designated, the database is unprotected, and any user has read and write permissions. A user may be configured to be the owner of the database only while no owner user is designated for the database.
Only the owner can configure the protection settings. If no owner is designated, the database is unprotected, and any user has read and write permissions. A user may be configured to be the owner of the database only while no owner user is designated for the database.
•![]() When any protection setting is relaxed, the database is reset. Protection is relaxed in the following cases:
When any protection setting is relaxed, the database is reset. Protection is relaxed in the following cases:
–![]() Protection is removed completely using the no sce-url-database protection command.
Protection is removed completely using the no sce-url-database protection command.
–![]() Write permission is changed from owner-only to all-users.
Write permission is changed from owner-only to all-users.
–![]() Lookup permission is changed from no-user to owner-only.
Lookup permission is changed from no-user to owner-only.
•![]() The SCE URL database configuration information is not accessible as part of the running config and startup config files.
The SCE URL database configuration information is not accessible as part of the running config and startup config files.
–![]() Protected information is not displayed when a show or more command is executed on the config files.
Protected information is not displayed when a show or more command is executed on the config files.
–![]() Protected information is included when a copy command is executed on the config files.
Protected information is included when a copy command is executed on the config files.
Authorization: admin
Examples
The following example shows how to configure protected URL database protection:
SCE>enable 10 Password:<cisco> SCE#>configure SCE(config)#interface linecard 0 SCE(config if)#sce-url-database protection owner myself
SCE(config if)#sce-url-database protection allow-write all-users
SCE(config if)#sce-url-database protection allow-lookup no-user
SCE(config if)#sce-url-database protection encryption-key
AABBCCDDEEFF11223344556677889900
SCE(config if)#
Related Commands
sce-url-database remove-all
Clears the protected URL database.
sce-url-database remove-all
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
To execute this command, you must have write permission for the protected URL database.
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#>configure SCE(config)#interface linecard 0 SCE(config if)#sce-url-database remove-all
SCE(config if)#
Related Commands
scmp
Enables the Service Control Management Protocol functionality.
To disable SCMP, use the no form of this command.
scmp
no scmp
Syntax Description
This command has no arguments or keywords.
Defaults
SCMP is disabled.
Command Modes
Global Configuration
Usage Guidelines
SCMP is a protocol by which an SCE platform communicates with peers such as Cisco routers running ISG to manage subscriber sessions.
SCMP performs the following functions:
•![]() Manages the connection status to all SCMP peer devices
Manages the connection status to all SCMP peer devices
•![]() Encodes and decodes the SCMP messages
Encodes and decodes the SCMP messages
•![]() Orders northbound messages for each subscriber
Orders northbound messages for each subscriber
When the SCMP is disabled, all subscribers provisioned through this interface are removed.
Authorization: admin
Examples
The following example shows how to disable SCMP:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#no scmp SCE(config)#
Related Commands
scmp keepalive-interval
Defines the interval between keepalive messages to the SCMP peer device.
scmp keepalive-interval [interval]
Syntax Description
interval |
Interval between keepalive messages from the SCE platform to the SCMP peer device. |
Defaults
The default interval is 5 seconds.
Command Modes
Global Configuration
Usage Guidelines
The SCE platform sends keepalive messages to all connected SCMP peer devices at the defined interval.
•![]() If a response is received within the defined interval, the keepalive time stamp is updated.
If a response is received within the defined interval, the keepalive time stamp is updated.
•![]() If a response is not received within the defined interval, the connection is assumed to be down. The connection state is changed to not-connected, and the SCMP begins attempts to reconnect.
If a response is not received within the defined interval, the connection is assumed to be down. The connection state is changed to not-connected, and the SCMP begins attempts to reconnect.
Authorization: admin
Examples
The following example shows how to define the SCMP keepalive message interval:
SCE>enable 10 Password:<cisco> SCE#configure SCE(config)#scmp keepalive-interval 10 SCE(config)#
Related Commands
|
|
|
show scmp |
Displays the SCMP (ISG) general configuration and status. |
scmp loss-of-sync-timeout
Defines the loss-of-sync timeout interval, which is the amount of time between loss of connection between the SCE platform and an SCMP peer device and the loss-of-sync event.
scmp loss-of-sync-timeout [interval]
Syntax Description
interval |
Loss-of-sync timeout interval in seconds. |
Defaults
The default interval is 90 seconds.
Command Modes
Global Configuration
Usage Guidelines
If the connection between an SCE platform and an SCMP peer device fails, a timer starts. If the connection exceeds the configured loss-of-sync timeout interval, the connection is assumed to be not-in-sync. In this case, a loss-of-sync event occurs, and the system performs the following actions:
•![]() Sets the connection status to not-in-sync
Sets the connection status to not-in-sync
•![]() Removes all messages from the SCMP buffers
Removes all messages from the SCMP buffers
•![]() Removes all subscribers associated with the SCMP peer device
Removes all subscribers associated with the SCMP peer device
Authorization: admin
Examples
The following example shows how to define the loss-of-sync timeout interval:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)# scmp loss-of-sync-timeout 120 SCE(config)#
Related Commands
|
|
|
show scmp |
Displays the SCMP (ISG) general configuration and status. |
scmp reconnect-interval |
Defines the SCMP reconnect interval. |
scmp name
Adds an SCMP peer device.
To delete the specified SCMP peer device, use the no form of this command.
scmp name name radius hostname secret secret [auth-port [auth-port]] [acct-port [acct-port] ]
no scmp name name
Syntax Description
name |
Name of the SCMP peer device. |
hostname |
IP address or name of the RADIUS host. |
secret |
RADIUS shared secret. |
auth-port |
Authentication port number. |
acct-port |
Accounting port number. |
Defaults
The default port configuration is as specified in RFC 2865 and RFC 2866.
The default authentication port is 1812.
The default accounting port is 1813.
Command Modes
Global Configuration
Usage Guidelines
After defining an SCMP peer device, you must associate it with one or more unmapped anonymous groups (see subscriber anonymous-group name scmp name). This association provides the ability to query the SCMP peer regarding unmapped IP addresses if the SCE platform is not updated when the subscriber session has started (see scmp subscriber send-session-start) or in recovery scenarios.
You cannot delete an SCMP device that has anonymous groups assigned to it. Use the no subscriber anonymous-group name scmp name command to remove all associated anonymous groups before deleting the device.
Authorization: admin
Examples
The following example shows how to define an SCMP peer device:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)# scmp name peer_device1 radius radius1 secret abcdef SCE(config)#
Related Commands
scmp reconnect-interval
Defines the SCMP reconnect interval, which is the amount of time between attempts by the SCE platform to reconnect with an SCMP peer.
scmp reconnect-interval [interval]
Syntax Description
interval |
Interval between attempts by the SCE platform to reconnect with an SCMP peer, in seconds. |
Defaults
The default interval is 30 seconds.
Command Modes
Global Configuration
Usage Guidelines
The SCE platform attempts to reconnect to the SCMP peer device at the defined intervals by sending an establish-peering-request message. If a valid reply is received, the SCMP connection state for the SCMP peer is changed, and the SCMP performs the required reconnection operations. These operations include:
•![]() Requerying the peer regarding all subscribers provisioned by this device
Requerying the peer regarding all subscribers provisioned by this device
•![]() Querying the peer regarding all anonymous subscribers created using the anonymous group assigned to this peer
Querying the peer regarding all anonymous subscribers created using the anonymous group assigned to this peer
Authorization: admin
Examples
The following example shows how to define the SCMP reconnect interval:
SCE>enable 10 Password:<cisco> SCE#configure SCE(config)#scmp reconnect-interval 60 SCE(config)#>
Related Commands
|
|
|
show scmp |
Displays the SCMP (ISG) general configuration and status. |
scmp loss-of-sync-timeout |
Defines the loss of sync timeout interval. |
scmp subscriber force-single-sce
Configures SCMP to make the SCMP peer device verify that each subscriber is provisioned for only one SCE platform. This configuration must be enabled in MGSCP deployments.
To disable verifying that each subscriber is provisioned for only one SCE platform, use the no form of this command.
scmp subscriber force-single-sce
no scmp subscriber force-single-sce
Syntax Description
This command has no arguments or keywords.
Defaults
Subscriber verification is disabled.
Command Modes
Global Configuration
Usage Guidelines
This command takes effect only if it is set before the connection with the SCMP peers is established. If active connections exist, use the no scmp and scmp commands to stop and then restart SCMP.
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#scmp subscriber force-single-sce SCE(config)#
Related Commands
|
|
|
show scmp |
Displays the SCMP (ISG) general configuration and status. |
scmp |
Enables the Service Control Management Protocol functionality. |
scmp subscriber id append-to-guid
Defines the subscriber ID structure for subscribers provisioned through the SCMP interface.
To clear the subscriber ID structure setting, use the no form of this command.
scmp subscriber id append-to-guid radius-attributes {calling-station-id | nas-port-id | user-name} [calling-station-id | nas-port-id | user-name] [calling-station-id | nas-port-id | user-name]
no scmp subscriber id append-to-guid
Syntax Description
radius-attributes |
Sets the subscriber ID structure. Choose one or more of the following options: calling-station-id, nas-port-id, or user-name. |
Defaults
All settings are cleared.
Command Modes
Global Configuration
Usage Guidelines
The GUID is a global unique ID assigned to each subscriber session by the SCMP peer device.
You can define the structure of the subscriber ID with this command by specifying which of the following RADIUS attributes to include and in which order:
•![]() Calling station ID
Calling station ID
•![]() NAS port
NAS port
•![]() Username
Username
The GUID is always appended at the end of the subscriber ID as defined by this command.
The no form of the command clears the subscriber ID structure setting, resulting in no other elements being used with the GUID to form the subscriber ID.
You must disable the SCMP interface before executing this command. (Use the no scmp command.)
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#no scmp
SCE(config)#scmp subscriber id append-to-guid radius-attributes user-name calling-station-id nas-port-id SCE(config)#scmp SCE(config)#
Related Commands
|
|
|
show scmp |
Displays the SCMP (ISG) general configuration and status. |
scmp |
Enables the Service Control Management Protocol functionality. |
scmp subscriber send-session-start
Configures SCMP to make the SCMP peer device push sessions to the SCE platform immediately when the session is created on the peer device. This feature must be disabled in MGSCP deployments.
To disable pushing of sessions from the SCMP peer device to the SCE platform, use the no form of this command.
scmp subscriber send-session-start
no scmp subscriber send-session-start
Syntax Description
This command has no arguments or keywords.
Defaults
Session pushing is disabled.
Command Modes
Global Configuration
Usage Guidelines
This command takes effect only if it is set before the connection with the SCMP peers is established. If active connections exist, use the no scmp and scmp commands to stop and then restart SCMP.
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#scmp subscriber send-session-start SCE(config)#
Related Commands
|
|
|
show scmp |
Displays the SCMP (ISG) general configuration and status. |
script capture
Begins the recording of a script. The command tracks all commands entered until the script stop command is used.
script capture script-filename
Syntax Description
script-filename |
Name of the output file where the script is stored. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Use this command to capture a sequence of repeated commands into a file for the purpose of executing the commands again.
Use the script stop command to stop capturing the script.
Authorization: admin
Examples
The following example shows the script capture for script1.txt:
SCE>enable 10 Password:<cisco> SCE#script capture script1.txt SCE#cd log SCE#cd.. SCE#pwd SCE#script stop
Related Commands
|
|
|
script stop |
Stops script capture. |
script print
Displays a script file.
script print script-filename
Syntax Description
script-filename |
Name of the file containing the script. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to print the commands captured in script1.txt:
SCE>enable 10
Password:<cisco>
SCE#script print script1.txt cd log
cd..
pwd
script stop
SCE#
Related Commands
|
|
|
script capture |
Begins the recording of a script. |
script run |
Runs a script. |
script run
Runs a script. The script may be created using the script capture command or it may be created as a text file containing the appropriate commands.
script run script-filename [halt]
Syntax Description
script-filename |
Name of the file containing the script. |
halt |
Breaks the script on errors. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Use this command to run a script that you have previously created using the script capture command.
Authorization: admin
Examples
The following example shows how to run the script named monitor.txt, which contains commands to enable the generation of the real-time subscriber usage RDRs for the specified subscribers.
The file contains the following command lines:
configure interface linecard 0 subscriber name Leonardo property name monitor value 1 subscriber name Raphael property name monitor value 1 subscriber name Donatello property name monitor value 1 subscriber name Michelangelo property name monitor value 1
The following example shows how to run the script:
SCE>enable 10 Password:<cisco> SCE#script run monitor.txt SCE#configure SCE(config)#interface linecard 0 SCE(config if)#subscriber name Leonardo property name monitor value 1 SCE(config if)#subscriber name Raphael property name monitor value 1 SCE(config if)#subscriber name Donatello property name monitor value 1 SCE(config if)#subscriber name Michelangelo property name monitor value 1 SCE(config if)#
Related Commands
|
|
|
script capture |
Begins the recording of a script. |
script print |
Displays a script file. |
script stop
Stops script capture. Used with the script capture command, it marks the end of a script being recorded.
script stop
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to stop capturing a script:
SCE>enable 10 Password:<cisco> SCE#script capture script1.txt SCE#cd log SCE#cd.. SCE#pwd SCE#script stop SCE#
Related Commands
|
|
|
script capture |
Begins the recording of a script. |
service-bandwidth-prioritization-mode
Defines the service bandwidth prioritization mode.
service-bandwidth-prioritization-mode [mode]
Syntax Description
mode |
Choose global or subscriber-internal. See Usage Guidelines for more information. |
Defaults
The default mode is subscriber-internal.
Command Modes
Linecard Interface Configuration
Usage Guidelines
This command configures how bandwidth controllers compete for bandwidth by specifying which assurance level (AL) value is used when allocating bandwidth between bandwidth controllers. The global controller AL can be taken from either of the following modes:
•![]() global prioritization mode—Taken from current bandwidth controller Assurance Level.
global prioritization mode—Taken from current bandwidth controller Assurance Level.
•![]() subscriber-internal prioritization mode—For each bandwidth controller, taken from the Primary BWC Relative Priority (the party or "total" bandwidth-controller Relative-Priority value).
subscriber-internal prioritization mode—For each bandwidth controller, taken from the Primary BWC Relative Priority (the party or "total" bandwidth-controller Relative-Priority value).
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#configure SCE(config)#interface linecard 0 SCE(config if)#service-bandwidth-prioritization-mode global SCE(config if)#
Related Commands
|
|
|
show interface linecard service-bandwidth-prioritization-mode |
Displays the currently configured service bandwidth prioritzation mode. |
service password-encryption
Enables password encryption so that the password remains secret when the configuration file is displayed.
To disable password encryption, use the no form of this command.
service password-encryption
no service password-encryption
Syntax Description
This command has no arguments or keywords.
Defaults
Password encryption is disabled.
Command Modes
Global Configuration
Usage Guidelines
Passwords that were configured in an encrypted format are not deciphered when password encryption is disabled.
Authorization: admin
Examples
The following example shows the effect of enabling password encryption:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#enable password abcd SCE(config)#do more running-config #This is a general configuration file (running-config). #Created on 10:20:57 ISR TUE July 3 2001 ... enable password level 10 0 "abcd" ... SCE(config)#service password-encryption SCE(config)#do more running-config #This is a general configuration file (running-config). #Created on 10:21:12 ISR TUE July 3 2001 ... service password-encryption enable password level 10 0 "e2fc714c4727ee9395f324cd2e7f331f" ... SCE(config)#
Related Commands
|
|
|
enable password |
Configures a password for the specified authorization level. |
service rdr-formatter
Enables or disables the RDR formatter. The RDR formatter is the element that formats the event reports produced by the line card and sends them to an external data collector.
To disable the RDR formatter, use the no form of this command.
service rdr-formatter
no service rdr-formatter
Syntax Description
This command has no arguments or keywords.
Defaults
The RDR formatter is enabled.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to enable the RDR formatter:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#service rdr-formatter SCE(config)#
The following example shows how to disable the RDR formatter:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#no service rdr-formatter SCE(config)#
Related Commands
service telnetd
Enables the Telnet daemon.
To disable the daemon, which prevents new users from accessing the SCE platform through Telnet, use the no form of this command.
service telnetd
no service telnetd
Syntax Description
This command has no arguments or keywords.
Defaults
The Telnet daemon is enabled.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to enable the Telnet daemon:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#service telnetd SCE(config)#
The following example shows how to disable the Telnet daemon:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#no service telnetd SCE(config)#
Related Commands
|
|
|
show telnet status |
Displays the status of the Telnet server domain. |
telnet |
Starts a Telnet session. |
show access-lists
Displays all access lists or a specific access list.
show access-lists [number]
Syntax Description
number |
Number of the access list to show |
Defaults
The default access list number is 1.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to display the configuration of access list 5:
SCE>enable 5 Password:<cisco> SCE#show access-lists 5 Standard IP access list 5 Permit 10.1.1.0, wildcard bits 0.0.0.255 deny any SCE#
Related Commands
|
|
|
access-list |
Adds an entry to the bottom of the specified access list. |
show blink
Displays the blinking status of a slot. A slot blinks after it receives a blink command.
show blink slot slot-number
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the blink status of slot 0:
SCE>enable 5 Password:<cisco> SCE>show blink slot 0 Slot 0 blink status: off SCE>
Related Commands
|
|
|
blink |
Blinks a slot LED for visual identification. |
show calendar
Displays the time maintained by the real-time system calendar clock.
show calendar
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the current system calendar:
SCE>enable 5 Password:<cisco> SCE>show calendar 12:50:03 GMT MON November 13 2005 SCE>
Related Commands
|
|
|
calendar set |
Sets the system calendar. |
show cdp
Displays the following Cisco Discovery Protocol (CDP) information:
•![]() interval between transmissions of CDP advertisements (transmission timer)
interval between transmissions of CDP advertisements (transmission timer)
•![]() the number of seconds the CDP advertisement is valid for a given port (hold time)
the number of seconds the CDP advertisement is valid for a given port (hold time)
•![]() the version of the advertisement
the version of the advertisement
•![]() CDP mode
CDP mode
show cdp
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example illustrates sample output from this command.
SCE>enable 5 Password:<cisco> SCE>show cdp
Global CDP information:
Sending CDP packets every 60 seconds
Sending a holdtime value of 180 seconds
Sending CDPv2 advertisements is enabled
standard mode - CDP packets are received and processed. CDP packets are generated.
SCE>
Related Commands
|
|
|
|---|---|
show cdp entry |
|
show cdp neighbors |
|
show cdp traffic |
show cdp entry
Displays information about a specific neighboring device discovered using Cisco Discovery Protocol (CDP).
show cdp entry {* | device-name[*] [protocol | version]}
Syntax Description
Defaults
None
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following examples illustrate how to use this command.
Example 1
The following is sample output from the show cdp entry command with no limits. Information about the neighbor device.cisco.com is displayed, including device ID, address and protocol, platform, interface, hold time, and version.
SCE>enable 5 Password:<cisco> SCE>show cdp entry device.cisco.com
-------------------------
Device ID: device.cisco.com
Entry address(es):
IP address: 192.168.68.18
Platform: cisco 4500, Capabilities: Router
Interface: Ethernet0/1, Port ID (outgoing port): Ethernet0
Holdtime : 125 sec
Version :
Cisco IOS Software
Cisco IOS (tm) 4500 Software (C4500-J-M), Version 12.1(2)
Copyright (c) 1986-2000 by cisco Systems, Inc.
Compiled Mon 07-Apr-00 19:51 by joeuser
Example 2
The following is sample output from the show cdp entry protocol command. Only information about the protocols enabled on device.cisco.com is displayed.
SCE>enable 5
Password:<cisco>
SCE>show cdp entry device.cisco.com protocol
Protocol information for device.cisco.com:
IP address: 192.168.68.18
Example 3
The following is sample output from the show cdp entry version command. Only information about the version of software running on device.cisco.com is displayed.
SCE>enable 5
Password:<cisco>
SCE>show cdp entry device.cisco.com version
Version information for device.cisco.com:
Cisco IOS Software
Cisco IOS (tm) 4500 Software (C4500-J-M), Version 12.1(2)
Copyright (c) 1986-2000 by cisco Systems, Inc.
Compiled Mon 07-Apr-00 19:51 by joeuser
Related Commands
|
|
|
|---|---|
show cdp |
|
show cdp neighbors |
|
show cdp traffic |
show cdp neighbors
Displays information that was discovered regarding the neighboring devices.
show cdp neighbors [type number] [detail]
Syntax Description
type |
(Optional) Type of the interface connected to the neighbors about which you want information. |
number |
(Optional) Number of the interface connected to the neighbors about which you want information. |
detail |
(Optional) Displays detailed information about a neighbor (or neighbors). See the Additional Fields described in Table 2-9. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Displays the following information:
•![]() type of device that was discovered
type of device that was discovered
•![]() the name of the device
the name of the device
•![]() the number and type of the local interface (port)
the number and type of the local interface (port)
•![]() the number of seconds the CDP advertisement is valid for the port
the number of seconds the CDP advertisement is valid for the port
•![]() the device type
the device type
•![]() the device product number
the device product number
•![]() the port ID
the port ID
If you use the detail keyword, the following additional information is displayed for each device:
•![]() entry address(es)
entry address(es)
•![]() version
version
•![]() native VLAN ID
native VLAN ID
•![]() the duplex mode
the duplex mode
•![]() the VTP domain name associated with neighbor devices.
the VTP domain name associated with neighbor devices.
Authorization: viewer
Examples
Example 1
The following example shows how to display information about the neighboring devices.
SCE>enable 5 Password:<cisco> SCE>show cdp neighbors
Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge
S - Switch, H - Host, I - IGMP, r - Repeater, P - Phone
Device ID Local Intrfce Holdtme Capability Platform Port ID
Lab-Router Gig 3/0/0 169 R S I ME-C6524GSGig 1/5
Lab-Router Gig 3/0/1 169 R S I ME-C6524GSGig 1/6
Lab-Router Gig 3/0/2 169 R S I ME-C6524GSGig 1/7
Lab-Router Gig 3/0/3 169 R S I ME-C6524GSGig 1/8
sce>
Example 2
The following example shows how to display detailed information about the neighboring devices.
SCE>enable 5 Password:<cisco> SCE>show cdp neighbors detail
-------------------------
Device ID: Router
Entry address(es):
IP address: 1.1.1.10
Platform: cisco ME-C6524GS-8S, Capabilities: Router Switch IGMP
Interface: GigabitEthernet3/0/0, Port ID (outgoing port): GigabitEthernet1/5
Holdtime : 178 sec
Version :
Cisco Internetwork Operating System Software
IOS (tm) s6523_rp Software (s6523_rp-IPBASE-M), Version 12.2(18)ZU2, RELEASE SOFTWARE (fc2)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2007 by cisco Systems, Inc.
Compiled Tue 30-Jan-07 03:59 by alnguyen
advertisement version: 2
VTP Management Domain: demo
Duplex : full
Related Commands
|
|
|
|---|---|
show cdp |
|
show cdp entry |
|
show cdp traffic |
show cdp traffic
Displays information about traffic between devices gathered using Cisco Discovery Protocol (CDP).
show cdp traffic
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following is sample output from the show cdp traffic command.
SCE>enable 5 Password:<cisco> SCE>show cdp traffic
CDP counters:
Total packets output: 543, Input: 333
Hdr syntax: 0, Chksum error: 0, Encaps failed: 0
No memory: 0, Invalid: 0, Fragmented: 0
CDP version 1 advertisements output: 191, Input: 187
CDP version 2 advertisements output: 352, Input: 146
SCE>
Related Commands
|
|
|
|---|---|
show cdp |
|
show cdp entry |
|
show cdp neighbors |
show clock
Displays the time maintained by the system clock.
show clock
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the current system clock:
SCE>enable 5 Password:<cisco> SCE>show clock 12:50:03 GMT MON November 13 2005 SCE>
Related Commands
|
|
|
clock set |
Manually sets the system clock. |
show diameter
Displays the current diameter stack state. Use the counters option to display message statistics.
show diameter [counters]
Syntax Description
counters |
Displays stack message statistics. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
Example 1
The following example shows output from this command.
SCE>enable 5
Password:<cisco>
SCE>show diameter Stack State : Down
Host : 10.56.193.228
Realm : sce.cisco.com
Tx-Timer : 30
Log Level : OFF
SCE>
Example 2
The following example shows output from this command with the counters option.
SCE>enable 5
Password:<cisco>
SCE>show diameter counters WDR Sent : 150
WDR Received : 182
WDA Sent : 182
WDA Received : 150
CER Sent : 3
CER Received : 0
CEA Sent : 0
CEA Received : 3
DPR Sent : 0
PDA Sent : 1
SCE>
Related Commands
|
|
|
diameter |
Starts and stops the diameter stack. |
show diameter forwarding-mode
Displays the forwarding mode table.
show diameter forwarding-mode
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows output from this command.
SCE>enable 5
Password:<cisco>
SCE>show diameter forwarding-mode
----------------------------------------------
| Realm | Application | Scheme |
------------------------------------------------
| scos.com | Gx | Load-Balancing |
----------------------------------------------
SCE>
Related CommandsN
|
|
|
show diameter realm |
Displays all routing table entries for the specified realm. |
show diameter Gx
Displays the current Gx application state and connected peers. Use the counters option to display message statistics.
show diameter Gx [counters]
Syntax Description
counters |
Displays Gx message statistics. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
Example 1
The following example shows output from this command.
SCE>enable 5
Password:<cisco>
SCE>show diameter Gx Gx Application Status : Up
Gx Realm : scos.com
Gx tx-timer : 5
Gx PCRF-connection-failure-grace-time : 150
Gx fatal-grace-time : 300
Connected
SCE>
Example 2
The following example shows output from this command with the counters option.
SCE>enable 5
Password:<cisco>
SCE>show diameter Gx counters
CCR Initial Messages : 767
CCR Initial Messages Sent Failed : 0
CCR Initial Messages Timed Out : 0
CCR Update Messages : 0
CCR Update Messages Timed Out : 0
CCR Update Messages Sent Failed : 0
CCR Terminate Messages : 0
CCR Terminate Messages Timed Out : 0
CCR Terminate Messages Sent Failed : 0
SCE>
Related Commands
|
|
|
diameter Gx |
Starts and stops the Gx application. |
show diameter Gy
Displays the current Gy application state and connected peers.
•![]() Use the counters option to display message statistics.
Use the counters option to display message statistics.
show diameter Gy [counters]
Syntax Description
counters |
Displays Gy message statistics. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
Example 1
The following example shows output from this command.
SCE>enable 5
Password:<cisco>
SCE>show diameter Gy Gy Client Status : Enabled
Gy tx-timer : 5
SCE>
Example 2
The following example shows output from this command with the counters option.
SCE>enable 5
Password:<cisco>
SCE>show diameter Gy counters
Gy Client Counters:
-------------------
CCR Initial Sent Messages : 993815
CCR Update Sent Messages : 0
CCR Terminate Sent Messages : 743800
CCR Intial Messages (Package Switch) : 0
CCR Terminate Messages (Package Switch) : 0
CCR Messages Timed Out : 72
CCR Initial Messages Timed Out : 37
CCR Update Messages Timed Out : 0
CCR Terminate Messages Timed Out : 35
CCR Retransmitted Messages : 0
CCR Initial Retransmitted Messages : 0
CCR Update Retransmitted Messages : 0
CCR Terminate Retransmitted Messages : 0
CCR Aborted Retransmission Messages : 0
CCR Messages Sent To Alt Server : 0
CCR Initial Messages Sent To Alt Server : 0
CCR Update Messages Sent To Alt Server : 0
CCR Terminate Messages Sent To Alt Server: 0
CCR Message Failed on Creation : 0
CCR Message Failed on Send : 925
CCR Initial Message Failed on Send : 925
CCR Update Message Failed on Send : 0
CCR Terminate Message Failed on Send : 0
CCA Messages Received : 1737752
CCA Messages Received on Initial : 993882
CCA Messages Received on Update : 0
CCA Messages Received on Terminate : 743870
CCA Messages No MSCC Handled : 743870
Error CCA Messages Received : 0
Error CCA Messages Received on Initial : 0
Error CCA Messages Received on Update : 0
Error CCA Messages Received on Terminate : 0
RAR Messages Received : 0
RAA Sent Messages : 0
RAA Messages Failed on Send : 0
Gy Failure Messages : 72
Severe Failures : 925
CCR Rate :199.9
CCA Rate :200.8
Current Opened Sessions : 249980
Max Opened Sessions : 250072
Number of Active->Standby events : 0
SCE>
Related Commands
|
|
|
diameter Gy |
Starts and stops the Gy application. |
show diameter Gy charging-id-mapping
Displays the complete charging ID mapping table or a specified entry.
show diameter Gy charging-id-mapping [package-id package-id bucket-id bucket-id]
Syntax Description
package-id, bucket-id |
SCA BB package ID and bucket ID pair for which to display the entry in the charging ID mapping table. |
Defaults
None
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
Example 1
The following example shows sample output from this command.
SCE>enable 5
Password:<cisco>
SCE>show diameter Gy charging-id-mapping
Charging-ID Mapping Table:
-------------------------------------------------------------
| Package ID | Bucket ID | Service ID | Rating Group |
-------------------------------------------------------------
| 10 | 1 | 5 | 3 |
| 10 | 2 | 3 | 1 |
| 10 | 3 | 7 | 6 |
-------------------------------------------------------------
SCE>
Related Commands
|
|
|
|---|---|
diameter Gy charging-id-mapping |
Adds an entry to the charging ID mapping table. |
show diameter peer
Displays the specified peer table entry.
show diameter peer name
Syntax Description
name |
Name of peer to display. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows output from this command.
SCE>enable 5
Password:<cisco>
SCE>show diameter peer A Peer Table:
-----------------------------------------------------------------------
| Name | Host | Port | State |
-----------------------------------------------------------------------
| A | 64.103.125.22 | 3868 | Down |
SCE>
Related Commands
|
|
|
diameter peer |
Adds an entry to the peer table. |
show diameter peer-table |
Displays the peer table. |
show diameter peer-table
Displays the peer table.
show diameter peer-table
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows output from this command.
SCE>enable 5
Password:<cisco>
SCE>show diameter peer-table
Peer Table:
-------------------------------------------------------------
| Name | Host | Port | State |
-------------------------------------------------------------
| SER_GX | 10.121.64.38 | 3869 | Up |
| SER_GY | 10.121.64.46 | 3870 | Up |
-------------------------------------------------------------
SCE>
Related Commands
|
|
|
show diameter peer |
Displays the specified peer table entry. |
show diameter realm
Displays all routing table entries for the specified realm.
show diameter realm name
Syntax Description
name |
Name of the realm to display. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows output from this command.
SCE>enable 5
Password:<cisco>
SCE>show diameter realm scos.com Realm: scos.com
Application: Gx
Servers:
A
B
Scheme Type : Load Balancing
----------------------------
Session Sharing: Off
Stickiness : Off
Server: A Status : Not Connected
Server: B Status : Not Connected
SCE>
Related Commands
|
|
|
diameter realm |
Adds an entry to the routing table. |
show diameter routing table |
Displays the routing table. |
show diameter routing table
Displays the routing table.
show diameter routing table
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows output from this command.
SCE>enable 5
Password:<cisco>
SCE>show diameter routing table
---------------------------------------------------------
| Name | Realm | Application | Priority |
---------------------------------------------------------
| SER_GY | cisco.com | Gy | 0 |
| SER_GX | cisco.com | Gx | 0 |
---------------------------------------------------------
SCE>
Related Commands
|
|
|
show diameter realm |
Displays all routing table entries for the specified realm. |
show environment all
Displays information about the SCE platform environment. The information includes cooling, power supply units, temperature, and voltage.
show environment all
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show environment all
Environment information:
---------------------
Slot 1: SCE8000-SCM-E
---------------------
scm[0].smc[0].max1668[0] - temperature device
.
.
TEMPERATURE status:
========================================================================================== =======================================================
PCB_Upper local1 29C 29 29.0 29 0.0 -18 -8 60 75 OK 0000:00:00:54 ----------- ----:--:--:-- 0
.
.
.
VOLTAGE status:
.
.
.
FAN status:
CurrStatus : OK fan tray is in non-manual mode (0000:00:00:50)
PrevStatus : <none> (----:--:--:--)
Sts# : 0 (access=2, fail=0)
.
.
.
PSU status:
CurrStatus : OK (0000:00:00:50)
PrevStatus : <none> (----:--:--:--)
Sts# : 0 (access=1, fail=0)
.
.
.
Message summary:
INTERNAL status is: {OK}
VOLTAGE status is: {OK, <DISABLED>}
TEMPERATURE status is: {OK}
FAN status is: {OK}
PSU status is: {OK}
SCE>
show environment cooling
Displays information about the SCE platform cooling.
show environment cooling
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show environment cooling
Environment Cooling information:
-----------
SCE8000-FAN
-----------
fan-tray[0] - cooling device
INTERNAL status:
CurrStatus : OK (0000:00:01:43)
PrevStatus : <none> (----:--:--:--)
Sts# : 0 (access=7, fail=0)
FAN status:
CurrStatus : OK fan tray is in non-manual mode (0000:00:01:43)
PrevStatus : <none> (----:--:--:--)
Sts# : 0 (access=4, fail=0)
Status Register : 0xa4
Control Mode : HP (High Power)
Test Enable State : Disabled
Led Status : Green
Fan Status : OK
Thermistor Status : OK
Speed Level (1-4) : 1
Thermistor Value : 24 Celsius
Sw Version : 0x10000
Message summary:
INTERNAL status is: {OK}
VOLTAGE status is: {OK, <DISABLED>}
TEMPERATURE status is: {OK}
FAN status is: {OK}
PSU status is: {OK}
SCE>
show environment power
Displays information about the SCE platform PSUs (power supply units).
show environment power
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show environment power
Environment Power information:
-------------
PWR-2700-AC/4
-------------
psu[0] - power supply device
INTERNAL status:
CurrStatus : OK (0000:00:01:59)
PrevStatus : <none> (----:--:--:--)
Sts# : 0 (access=4, fail=0)
PSU status:
CurrStatus : OK (0000:00:01:59)
PrevStatus : <none> (----:--:--:--)
Sts# : 0 (access=4, fail=0)
Message summary:
INTERNAL status is: {OK}
VOLTAGE status is: {OK, <DISABLED>}
TEMPERATURE status is: {OK}
FAN status is: {OK}
PSU status is: {OK}
SCE>
show environment temperature
Displays information about the temperature of the SCE platform.
show environment temperature
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show environment temperature Environment Temperature information:
---------------------
Slot 1: SCE8000-SCM-E
---------------------
scm[0].smc[0].max1668[0] - temperature device
INTERNAL status:
CurrStatus : OK (0000:00:02:15)
PrevStatus : <none> (----:--:--:--)
Sts# : 0 (access=35, fail=0)
TEMPERATURE status:
Name General CurrVal MinVal AvgVal MaxVal DevVal ErrL WrnL WrnH ErrH CurrStatus dddd:hh:mm:ss PrevStatus dddd:hh:mm:ss Sts#
========================================================================================== =======================================================
PCB_Upper local1 29C 29 29.0 29 0.0 -18 -8 60 75 OK 0000:00:02:15 ----------- ----:--:--:-- 0
DPT sd_1 39C 38 38.7 39 0.5 -8 2 74 89 OK 0000:00:02:15 ----------- ----:--:--:-- 0
CLS sd_2 33C 32 32.8 33 0.4 -8 2 63 78 OK 0000:00:02:15 ----------- ----:--:--:-- 0
SCE>
show environment voltage
Displays information about the SCE platform voltage.
show environment voltage
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show environment voltage
Environment Voltage information:
---------------------
Slot 1: SCE8000-SCM-E
---------------------
scm[0].smc[0].summit766[0] - voltage device
INTERNAL status:
CurrStatus : OK (0000:00:01:28)
PrevStatus : <none> (----:--:--:--)
Sts# : 0 (access=23, fail=0)
VOLTAGE status:
Name General CurrVal MinVal AvgVal MaxVal DevVal ErrL WrnL WrnH ErrH CurrStatus dddd:hh:mm:ss PrevStatus dddd:hh:mm:ss Sts#
========================================================================================== =======================================================
Main_3_3 CH_A 3286mV 3286 3286.0 3286 0.0 3168 3234 3366 3432 OK 0000:00:01:28 ----------- ----:--:--:-- 0
Main_2_5 CH_B 2490mV 2490 2490.0 2490 0.0 2400 2450 2550 2600 OK 0000:00:01:28 ----------- ----:--:--:-- 0
SCE>
show failure-recovery operation-mode
Displays the operation mode to apply after booting resulted from a failure.
show failure-recovery operation-mode
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the failure recovery operation mode:
SCE>enable 5 Password:<cisco> SCE>show failure-recovery operation-mode System Operation mode on failure recovery is: operational SCE>
Related Commands
|
|
|
failure-recovery operation-mode |
Specifies the operation mode to be applied when the system reboots after a system failure. |
show hostname
Displays the currently configured hostname.
show hostname
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the current hostname:
SCE>enable 5 Password:<cisco> SCE>show hostname SCE8000 SCE>
Related Commands
|
|
|
hostname |
Modifies the name of the SCE platform. |
show hosts
Displays the default domain name, the address of the name server, and the contents of the host table.
show hosts
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the configured domain and hosts:
SCE>enable 5 Password:<cisco> SCE>show hosts Default domain is cisco.com Name/address lookup uses domain service Name servers are 10.1.1.60, 10.1.1.61 Host Address ---- ------- PC85 10.1.1.61 SCE>
Related Commands
show interface gigabitethernet
Displays the details of the GigabitEthernet management interface.
show interface gigabitethernet slot-number/interface-number [counters [direction]]
Syntax Description
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the GigabitEthernet details:
SCE>enable 5 Password:<cisco> SCE>show interface gigabitethernet 1/1 SCE>
Related Commands
|
|
|
interface gigabitethernet |
Enters GigabitEthernet Interface Configuration mode. |
show interface linecard
Displays information for a specific line card interface.
show interface linecard slot-number
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 The application assigned to slot 0 is /system/app/eng30102.sli Silent is off Configured shutdown is off Shutdown due to sm-connection-failure is off Resulting current shutdown state is off WAP handling is disabled SCE>
Related Commands
|
|
|
interface linecard |
Enters Linecard Interface Configuration mode. |
show interface linecard accelerate-packet-drops
Displays the currently configured hardware packet drop mode.
show interface linecard slot-number accelerate-packet-drops
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the current drop mode:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 accelerate-packet-drops Accelerated packet drops mode is enabled SCE>
Related Commands
|
|
|
accelerate-packet-drops |
Enables drop-wred-packets-by-hardware mode. |
show interface linecard application
Displays the name of the application loaded on the line card interface.
show interface linecard slot-number application
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the currently loaded application:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 application /system/app/eng30102.sli SCE>
Related Commands
|
|
|
show interface linecard asymmetric-l2-support
Displays the current asymmetric Layer 2 support configuration.
show interface linecard slot-number asymmetric-l2-support
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 asymmetric-l2-support Asymmetric layer 2 support is disabled SCE>
Related Commands
|
|
|
asymmetric-l2-support |
Configures the system to treat flows as having asymmetric Layer 2 characteristics for the purpose of packet injection. |
show interface linecard asymmetric-routing-topology
Displays information relating to asymmetric routing topology.
show interface linecard slot-number asymmetric-routing-topology
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
This command displays the following information:
•![]() Current asymmetric routing topology status.
Current asymmetric routing topology status.
•![]() The ratio of TCP unidirectional flows to total TCP flows per traffic processor (TCP unidirectional flows ratio).
The ratio of TCP unidirectional flows to total TCP flows per traffic processor (TCP unidirectional flows ratio).
The unidirectional flow ratio is displayed only for TCP flows, and reflects the way the flows were opened. It is calculated over the period of time since the SCE platform was last reloaded or since the counters were last reset.
To reset the asymmetric routing mode counters, use the clear interface linecard asymmetric-routing-topology counters command.

Note ![]() The SCE platform identifies unidirectional flows by default and regardless of the asymmetric routing mode.
The SCE platform identifies unidirectional flows by default and regardless of the asymmetric routing mode.
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 asymmetric-routing-topology Asymmetric Routing Topology mode is disabled TCP Unidirectional flows ratio statistics: ========================================== Traffic Processor 1 : 0% Traffic Processor 2 : 0% Traffic Processor 3 : 0% Traffic Processor 4 : 0% Traffic Processor 5 : 0% Traffic Processor 6 : 0% Traffic Processor 7 : 0% Traffic Processor 8 : 0% Traffic Processor 9 : 0% Traffic Processor 10 : 0% Traffic Processor 11 : 0% Traffic Processor 12 : 0% Note that the statistics are updated only if the system is configured to work in Enhanced Open Flow (i.e. following settings are disabled: Classical Open Flow mode, VAS, TCP no bypass est, etc.). The statistics are updated once every two minutes SCE>
Related Commands
|
|
|
asymmetric-routing- topology enabled |
|
clear interface linecard asymmetric-routing- topology counters |
Resets the asymmetric-routing-topology counters. |
show interface linecard attack-detector
Displays the configuration of the specified attack detector.
show interface linecard slot-number attack-detector [default | all]
show interface linecard slot-number attack-detector attack-detector
Syntax Description
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
When you specify the all or default keyword, the following information is displayed:
•![]() Protocol side—Whether the attack detector applies to attacks originating at the subscriber or network side.
Protocol side—Whether the attack detector applies to attacks originating at the subscriber or network side.
•![]() Direction—Whether the attack detector applies to single-sided or dual-sided attacks.
Direction—Whether the attack detector applies to single-sided or dual-sided attacks.
•![]() Action to take if an attack is detected.
Action to take if an attack is detected.
•![]() Thresholds:
Thresholds:
–![]() open-flows-rate—Default threshold for the rate of open flows (new open flows per second).
open-flows-rate—Default threshold for the rate of open flows (new open flows per second).
–![]() suspected-flows-rate—Default threshold for the rate of suspected DDoS flows (new suspected flows per second).
suspected-flows-rate—Default threshold for the rate of suspected DDoS flows (new suspected flows per second).
–![]() suspected-flows-ratio—Default threshold for the ratio of suspected flow rate to open flow rate.
suspected-flows-ratio—Default threshold for the ratio of suspected flow rate to open flow rate.
•![]() Subscriber notification—Enabled or disabled.
Subscriber notification—Enabled or disabled.
•![]() Alarm—Sending an SNMP trap is enabled or disabled.
Alarm—Sending an SNMP trap is enabled or disabled.
Authorization: viewer
Examples
The following examples show the use of the show interface linecard attack-detector command.
Example 1
The following example shows how to display the configuration of attack detector number 3:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 attack-detector 3 Detector #3: Comment: 'Sample' Access-list: 1 Effective only for TCP port(s) 21,23,80 Effective for all UDP ports Protocol|Side|Direction ||Action| Thresholds |Sub- |Alarm | | || |Open flows|Ddos-Suspected flows|notif| | | || |rate |rate |ratio | | --------|----|-----------||------|----------|------------|-------|-----|----- TCP |net.|source-only|| | | | | | TCP |net.|dest-only || | | | | | TCP |sub.|source-only|| | | | | | TCP |sub.|dest-only || | | | | | TCP |net.|source+dest|| | | | | | TCP |sub.|source+dest|| | | | | | TCP+port|net.|source-only||Block | | | | |Yes TCP+port|net.|dest-only || | | | | | TCP+port|sub.|source-only||Block | | | | |Yes TCP+port|sub.|dest-only || | | | | | TCP+port|net.|source+dest|| | | | | | TCP+port|sub.|source+dest|| | | | | | UDP |net.|source-only|| | | | | | UDP |net.|dest-only || | | | | | UDP |sub.|source-only|| | | | | | UDP |sub.|dest-only || | | | | | UDP |net.|source+dest|| | | | | | UDP |sub.|source+dest|| | | | | | UDP+port|net.|source-only|| | | | | | UDP+port|net.|dest-only || | | | | | UDP+port|sub.|source-only|| | | | | | UDP+port|sub.|dest-only || | | | | | UDP+port|net.|source+dest|| | | | | | UDP+port|sub.|source+dest|| | | | | | ICMP |net.|source-only|| | | | | | ICMP |net.|dest-only || | | | | | ICMP |sub.|source-only|| | | | |Yes | ICMP |sub.|dest-only || | | | | | other |net.|source-only|| | | | | | other |net.|dest-only || | | | | | other |sub.|source-only|| | | | | | other |sub.|dest-only || | | | | | Empty fields indicate that no value is set and configuration from the default attack detector is used. SCE>
Example 2
The following example shows how to display the configuration of the default attack detector:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 attack-detector default Protocol|Side|Direction ||Action| Thresholds |Sub- |Alarm | | || |Open flows|Ddos-Suspected Flows|notif| | | || |rate |rate |ratio | | --------|----|-----------||------|----------|------------|-------|-----|----- TCP |net.|source-only||Report| 1000| 500|50 |No |No TCP |net.|dest.-only ||Report| 1000| 500|50 |No |No TCP |sub.|source-only||Report| 1000| 500|50 |No |No TCP |sub.|dest.-only ||Report| 1000| 500|50 |No |No TCP |net.|source+dest||Report| 100| 50|50 |No |No TCP |sub.|source+dest||Report| 100| 50|50 |No |No TCP+port|net.|source-only||Report| 1000| 500|50 |No |No TCP+port|net.|dest.-only ||Report| 1000| 500|50 |No |No TCP+port|sub.|source-only||Report| 1000| 500|50 |No |No TCP+port|sub.|dest.-only ||Report| 1000| 500|50 |No |No TCP+port|net.|source+dest||Report| 100| 50|50 |No |No TCP+port|sub.|source+dest||Report| 100| 50|50 |No |No UDP |net.|source-only||Report| 1000| 500|50 |No |No UDP |net.|dest.-only ||Report| 1000| 500|50 |No |No UDP |sub.|source-only||Report| 1000| 500|50 |No |No UDP |sub.|dest.-only ||Report| 1000| 500|50 |No |No UDP |net.|source+dest||Report| 100| 50|50 |No |No UDP |sub.|source+dest||Report| 100| 50|50 |No |No UDP+port|net.|source-only||Report| 1000| 500|50 |No |No UDP+port|net.|dest.-only ||Report| 1000| 500|50 |No |No UDP+port|sub.|source-only||Report| 1000| 500|50 |No |No UDP+port|sub.|dest.-only ||Report| 1000| 500|50 |No |No UDP+port|net.|source+dest||Report| 100| 50|50 |No |No UDP+port|sub.|source+dest||Report| 100| 50|50 |No |No ICMP |net.|source-only||Report| 500| 250|50 |No |No ICMP |net.|dest.-only ||Report| 500| 250|50 |No |No ICMP |sub.|source-only||Report| 500| 250|50 |No |No ICMP |sub.|dest.-only ||Report| 500| 250|50 |No |No other |net.|source-only||Report| 500| 250|50 |No |No other |net.|dest.-only ||Report| 500| 250|50 |No |No other |sub.|source-only||Report| 500| 250|50 |No |No other |sub.|dest.-only ||Report| 500| 250|50 |No |No SCE>
Related Commands
show interface linecard attack-filter
Displays the attack-filtering configuration.
show interface linecard slot-number attack-filter [option]
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
option |
See Usage Guidelines for the list of options. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
The following options may be displayed:
•![]() query IP configured—Displays the configured threshold values and action as follows:
query IP configured—Displays the configured threshold values and action as follows:
–![]() query single-sided IP ip-address configured—Displays the configured threshold values and action for attack detection for a specified IP address (single-sided detection).
query single-sided IP ip-address configured—Displays the configured threshold values and action for attack detection for a specified IP address (single-sided detection).
–![]() query dual-sided source-IP ip-address1 dest ip-address2 configured—Displays the configured threshold values and action for attack detection between two specified IP addresses (dual-sided detection).
query dual-sided source-IP ip-address1 dest ip-address2 configured—Displays the configured threshold values and action for attack detection between two specified IP addresses (dual-sided detection).
–![]() dest-port port-number—Displays the configured threshold values and action for the specified port. You can include this argument with both single-sided and dual-sided queries.
dest-port port-number—Displays the configured threshold values and action for the specified port. You can include this argument with both single-sided and dual-sided queries.
•![]() query IP current—Displays the current counters for a specified attack detector for all protocols and attack directions as follows:
query IP current—Displays the current counters for a specified attack detector for all protocols and attack directions as follows:
–![]() query single-sided IP ip-address current—Displays the current counters for attack detection for a specified IP address (single-sided detection).
query single-sided IP ip-address current—Displays the current counters for attack detection for a specified IP address (single-sided detection).
–![]() query dual-sided source-IP ip-address1 dest ip-address2 current—Displays the current counters for attack detection between two specified IP addresses (dual-sided detection).
query dual-sided source-IP ip-address1 dest ip-address2 current—Displays the current counters for attack detection between two specified IP addresses (dual-sided detection).
–![]() dest-port port-number—Displays the configured threshold values and action for the specified port. You can include this argument with both single-sided and dual-sided queries.
dest-port port-number—Displays the configured threshold values and action for the specified port. You can include this argument with both single-sided and dual-sided queries.
•![]() current-attacks—Displays all currently handled attacks.
current-attacks—Displays all currently handled attacks.
•![]() counters—Displays all attack detection counters.
counters—Displays all attack detection counters.
•![]() dont-filter—Displays all existing stopped attack filters.
dont-filter—Displays all existing stopped attack filters.
•![]() force-filter—Displays all existing forced attack filters.
force-filter—Displays all existing forced attack filters.
•![]() subscriber-notification ports—Displays the list of subscriber-notification ports.
subscriber-notification ports—Displays the list of subscriber-notification ports.
•![]() subscriber-notification redirect—Displays the configuration of subscriber-notification redirection, such as the configured destination and dismissal URLs, and allowed hosts.
subscriber-notification redirect—Displays the configuration of subscriber-notification redirection, such as the configured destination and dismissal URLs, and allowed hosts.
Authorization: viewer
Examples
The following example shows how to display the configuration of attack detection between two specified IP addresses (dual-sided) for destination port 101:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 attack-filter query dual-sided source-IP 10.10.10.10 dest 10.10.10.145 dest-port 101 configured SCE>
The following example shows how to display all existing forced attack filters:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 attack-filter force-filter No force-filter commands are set for slot 0 SCE>
The following example shows how to display the subscriber notification ports:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 attack-filter subscriber-notification ports Configured Subscriber notification ports: 100 SCE>
Related Commands
show interface linecard cascade connection-status
Displays information about the connection between two cascaded SCE8000 platforms. This information can help assist in the installation of a cascaded system and to prevent incorrect cabling.
show interface linecard slot-number cascade connection-status
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the output from this command when the cascade interfaces of two cascaded Cisco SCE8000 10GBE platforms have not been connected correctly:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 cascade connection-status SCE is improperly connected to peer Please verify that each cascade port is connected to the correct port of the peer SCE. Note that in the current topology, the SCE must be connected to its peer as follows: Port 3/2/0 must be connected to port 3/2/0 at peer Port 3/3/0 must be connected to port 3/3/0 at peer SCE>
The following example shows the output from this command when the cascade interfaces of two cascaded Cisco SCE platforms have been connected correctly:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 cascade connection-status SCE is connected to peer
SCE>
Related Commands
|
|
|
connection-mode |
Sets the connection mode parameters. |
show interface linecard cascade peer-sce-information
Displays information about the peer SCE platform. The data is available even when the two platforms are no longer in cascade connection mode.
show interface linecard slot-number cascade peer-sce-information
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows typical output from this command when the two SCE platforms are connected correctly:
SCE>enable 5
Password:<cisco>
SCE>show interface linecard 0 cascade peer-sce-information
Peer SCE's IP address is 10.10.10.10
SCE>
The following example shows typical output from this command when the two SCE platforms are not connected correctly:
SCE>enable 5
Password:<cisco>
SCE>show interface linecard 0 cascade peer-sce-information
SCE is improperly connected to peer.
For further information, please consult cli show "cascade connection-status" command
Last known peer SCE's IP address was 10.10.10.10
Related Commands
|
|
|
connection-mode |
Sets the connection mode parameters. |
show interface linecard cascade redundancy-status
Displays the current redundancy status of the SCE platform.
show interface linecard slot-number cascade redundancy-status
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows typical output from this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 cascade redundancy-status Redundancy status is active SCE>
Related Commands
|
|
|
connection-mode |
Sets the connection mode parameters. |
show interface linecard connection-mode
Displays the current configuration of the SCE platform traffic link connection.
show interface linecard slot-number connection-mode
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows typical output from this command for a single SCE8000 platform:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 connection-mode slot 0 connection mode
Connection mode is inline
slot failure mode is external-bypass
Redundancy status is active SCE>
The following example shows typical output from this command for a cascaded SCE8000 platform:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 connection-mode slot 0 connection mode
Connection mode is inline-cascade
slot 0 sce-id is 1
slot 0 is secondary
slot 0 is connected to peer
slot failure mode is bypass
Redundancy status is standalone SCE>
Related Commands
|
|
|
connection-mode |
Sets the connection mode parameters. |
show interface linecard counters
Displays the hardware counters for the line card interface.
show interface linecard slot-number counters [bandwidth] [cpu-utilization]
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
bandwidth |
Displays only the bandwidth counters. |
cpu-utilization |
Displays only the CPU-utilization counters. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the hardware counters for the line card interface:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 counters
DP packets in: 340
DP packets out: 340
DP IP packets in: 340
DP Non-IP packets: 0
DP IP packets checksum err: 0
DP IP packets length err: 0
DP IP broadcast packets: 0
DP IP fragmented packets: 0
DP IP packets with TTL=0 err: 0
DP Non TCP/UDP packets: 0
DP TCP/UDP packets checksum err: 0
DP ARP packets: 0
DP PPP compressed packets: 0
DP packets dropped: 0
DP tuples to FF: 340
DP tuples from CLS: 340
DP L7 Filter congested packets: 0
DP VLAN packets: 0
DP MPLS packets: 0
DP parse errors: 0
DP IPinIP skipped packets: 0
DP no payload packets: 53
DP self-IP packets: 0
DP tunneled packets: 0
DP L2TP control packets: 0
DP L2TP packets with offset: 0
traffic-counters information:
-----------------------------
Counter 'myCounter' value: 0 L3 bytes. Rules using it: None.
1 counters listed out of 36 available ... SCE>
Related Commands
|
|
|
clear interface linecard counters |
Clears the counters for the line card interface. |
show interface linecard duplicate-packets-mode
Displays the currently configured duplicate packets mode.
show interface linecard slot-number duplicate-packets-mode
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 duplicate-packets-mode Packet duplication of flows due to Delay Sensitive <bundles>is enabled Packet duplication of flows due to No-Online-Control <set-flow>is enabled Packet duplication of flows due to No-Online-Control <set-flow>ratio percent is 70 Packet duplication in case of shortage is enabled SCE>
Related Commands
|
|
|
show interface linecard external-bypass
Displays the state of the external bypass module.
show interface linecard slot-number external-bypass
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the output from this command when both external bypass modules are functioning properly:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 external-bypass External bypass current state is `not activated'. External bypass failure state is `activated'. Amount of expected external bypass devices: 2 (automatically configured) SCE>
The following example shows the output from this command when one external bypass module is not detected:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 external-bypass External bypass current state is `not activated'. External bypass failure state is `activated'. Amount of expected external bypass devices: 2 (automatically configured) Warning: External bypass device expected but not detected on link #1 SCE>
Related Commands
|
|
|
external-bypass |
Manually activates the external bypass modules. |
show interface linecard flow-capture
Displays the flow capture status.
show interface linecard slot-number flow-capture
Syntax Description
slot-number |
The number of the identified slot. Enter a value of 0. |
Defaults
This command has no default settings.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command.
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 flow-capture Flow Capture Status (module #1):
--------------------------------
Flow capture status: RECORDING
Capturing type: ONLINE
Target file name: ftp://myUser:myPassword@10.10.10.80/./myCap1.cap
Target file size (bytes): 11141528
Time limit (sec): 3600
Max L4 payload length (bytes): Unlimited
Number of recorded packets: 20687
Number of lost packets: 0 SCE>
Related CommandsN
|
|
|
debug flow-capture |
|
flow-capture controllers |
|
traffic-rule |
show interface linecard flow-open-mode
Displays the currently configured flow open mode.
show interface linecard slot-number flow-open-mode
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 flow-open-mode
Enhanced flow open mode is disabled Asymmetric layer 2 support is disabled
Note that other settings may override all/part of the Enhanced Flow Open mode, e.g. VAS, TCP no bypass est, etc.(in which cases will behave as in the classical mode)
SCE>
Related Commands
|
|
|
flow-open-mode |
show interface linecard ip-tunnel
Displays the current IP tunnel configuration.
show interface linecard slot-number ip-tunnel
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 ip-tunnel no IP tunnel SCE>
Related Commands
|
|
|
ip tunnel |
show interface linecard ip-tunnel ipinip
Displays the current IPinIP configuration.
show interface linecard slot-number ip-tunnel ipinip
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 ip-tunnel ipinip IPinIP skip mode is enabled IPinIP DSCP skip mode is disabled SCE>
Related Commands
show interface linecard ipv6
Displays the current IPv6 state.
show interface linecard slot-number ipv6
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows typical output from this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 ipv6
IPv6 counting mode is enabled
SCE>
Related Commands
|
|
|
show interface linecard l2tp
Displays the currently configured L2TP support parameters.
show interface linecard slot-number l2tp
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use the show interface linecard l2tp command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 l2tp L2TP identify-by port-number 1701 SCE>
Related Commands
|
|
|
l2tp identify-by |
Configures the port number that the LNS and LAC use for L2TP tunnels. |
show interface linecard link mode
Displays the configured Linecard Interface link mode.
show interface linecard slot-number link mode
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the configured link mode for the line card interface:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 link mode Link mode on port1-port2 Current link mode is :forwarding Actual link mode on active is :forwarding Actual link mode on failure is :monopath-bypass SCE>
Related Commands
|
|
|
link mode |
Configures the link mode. |
show interface linecard link-to-port-mapping
Displays the mapping of links and ports resulting from the connection-mode command.
show interface linecard slot-number link-to-port-mapping
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the link-to-port mapping:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 link-to-port-mapping
Link Id | Upstream Port (Subscribers) | Downstream Port (Network)
---------------------------------------------------------------------------
0 | 0/3/0/0 | 0/3/0/1
1 | 0/3/0/2 | 0/3/0/3
2 | 0/3/0/4 | 0/3/0/5
3 | 0/3/0/6 | 0/3/0/7
4 | 0/3/1/0 | 0/3/1/1
5 | 0/3/1/2 | 0/3/1/3
6 | 0/3/1/4 | 0/3/1/5
7 | 0/3/1/6 | 0/3/1/7
8 (cascade) | 1/3/0/0 | 1/3/0/1
9 (cascade) | 1/3/0/2 | 1/3/0/3
10 (cascade) | 1/3/0/4 | 1/3/0/5
11 (cascade) | 1/3/0/6 | 1/3/0/7
12 (cascade) | 1/3/1/0 | 1/3/1/1
13 (cascade) | 1/3/1/2 | 1/3/1/3
14 (cascade) | 1/3/1/4 | 1/3/1/5
15 (cascade) | 1/3/1/6 | 1/3/1/7
SCE>
Related Commands
|
|
|
connection-mode |
Sets the connection mode parameters. |
show interface linecard mac-mapping
Displays the line card MAC mapping information.
show interface linecard slot-number mac-mapping
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the MAC mapping information:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 mac-mapping MAC mapping status is: disabled MAC mapping default mapping is: none set MAC mapping dynamic insertion to table is enabled SCE>
Related Commands
show interface linecard mac-resolver arp
Displays a listing of all IP addresses and corresponding MAC addresses currently registered in the MAC resolver database.
show interface linecard slot-number mac-resolver arp
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the entries in the MAC resolver ARP database:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 mac-resolver arp There are no entries in the mac-resolver arp database SCE>
Related Commands
|
|
|
mac-resolver arp |
Adds a static IP entry to the MAC resolver database. |
show interface linecard periodic-records aggregation
Displays the current RDR aggregation configuration.
show interface linecard slot-number periodic-records aggregation
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following shows sample output from this command.
SCE>enable 5
Password:<cisco>
SCE>show interface linecard 0 periodic-records aggregation
VLUR : enabled
LUR : enabled
PUR : enabled
CSCE>
Related Commands
|
|
|
|---|---|
periodic-records aggregate-by-cpu |
show interface linecard physically-connected-links
Displays the link mapping for the line card interface.
show interface linecard slot-number physically-connected-links
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the link mapping for the line card interface:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 physically-connected-links slot 0 is connected to link-0 and link-1 SCE>
Related Commands
|
|
|
connection-mode |
Sets the connection mode parameters. |
show interface linecard sce-url-database
Displays the contents of the protected URL database.
You can also use this command to look for a specific URL and display the related flavor ID.
show interface linecard slot-number sce-url-database
show interface linecard slot-number sce-url-database url url
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
url |
Specific URL to look up in the SCE URL database. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
To display the contents of the protected URL database, it must have all protection removed and no assigned owner. If the database has an assigned owner, it is protected and cannot be displayed.
To display the flavor ID of a specific URL, the user executing the command must have lookup permission for the protected URL database.
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10
Password:<cisco>
SCE#show interface linecard 0 sce-url-database
SCE#
Related Commands
|
|
|
sce-url-database protection |
Configures user authorization for the protected URL database. |
show interface linecard sce-url-database protection
Displays the current protected URL database protection settings, including owner username, current protection settings, and whether a key is configured.
show interface linecard slot-number sce-url-database protection
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 sce-url-database protection Protection Domain BLACK_LIST_DOMAIN Status: Domain owner:black Read is allowed to no user Write is allowed to user black only Lookup is allowed to no user Encryption key is not set
SCE>
Related Commands
|
|
|
show interface linecard sce-url-database |
Displays the contents of the protected URL database. |
show interface linecard service-bandwidth-prioritization-mode
Displays the currently configured service bandwidth prioritization mode.
show interface linecard slot-number service-bandwidth-prioritization-mode
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 service-bandwidth-prioritization-mode Service bandwidth prioritization mode is: Subscriber Internal SCE>
Related Commands
|
|
|
service-bandwidth- prioritization-mode |
Defines the service bandwidth prioritization mode. |
show interface linecard shutdown
Displays the current shutdown state.
show interface linecard slot-number shutdown
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the Linecard Interface shutdown state:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 shutdown off SCE>
Related Commands
|
|
|
shutdown |
show interface linecard silent
Displays the current Linecard Interface silent state. When the silent state is OFF, the line card events reporting function is enabled.
show interface linecard slot-number silent
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the Linecard Interface silent state:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 silent off SCE>
Related Commands
|
|
|
silent |
Disables the line card from reporting events. |
show interface linecard subscriber
Displays subscribers that meet specified criteria.
show interface linecard slot-number subscriber [amount] [prefix prefix] [suffix suffix]
[property property-name equals | bigger-than | less-than property-val] [all-names]
show interface linecard slot-number subscriber name subscriber-name
show interface linecard slot-number subscriber all-names
show interface linecard slot-number subscriber [amount] {prefix prefix | suffix suffix}
show interface linecard slot-number subscriber [amount] property property-name
{equals | bigger-than | less-than property-val}
Syntax Description
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Use this command to display names of subscribers or the number of subscribers meeting one of the following specified criteria:
•![]() Having a value of a subscriber property that is equal to, larger than, or smaller than a specified value
Having a value of a subscriber property that is equal to, larger than, or smaller than a specified value
•![]() Having a subscriber name that matches a specific prefix
Having a subscriber name that matches a specific prefix
•![]() Having a subscriber name that matches a specific suffix
Having a subscriber name that matches a specific suffix
Authorization: viewer
Examples
The following example lists the number of subscribers with the prefix "gold" in the subscriber name:
SCE>enable 5
Password:<cisco>
SCE>show interface linecard 0 subscriber amount prefix gold
There are 40 subscribers with name prefix 'gold'.
SCE>
The following example lists all subscribers currently in the SCE platform subscribers database:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 subscriber all-names There are 8 subscribers in the database. john_doe mary_smith david_jones betty_peters bill_jackson jane_doe bob_white andy_black SCE>
Related Commands
|
|
|
subscriber name property name |
Assigns a value to the specified property of the specified subscriber. |
show interface linecard subscriber aging
Displays the subscriber aging configuration for the specified type of subscriber (anonymous or introduced).
show interface linecard slot-number subscriber aging {anonymous | introduced}
Syntax Description
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the aging of introduced subscribers:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 subscriber aging introduced Introduced subscriber aging is enabled. Introduced subscriber aging time is 30 minutes. SCE>
Related Commands
|
|
|
subscriber aging |
Enables of disables subscriber aging for the specified type of subscribers. |
show interface linecard subscriber anonymous
Displays the subscribers in a specified anonymous subscriber group.
show interface linecard slot-number subscriber anonymous [amount] {name group-name}
Syntax Description
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the number of subscribers in the anonymous subscriber group anon1:
SCE>enable 5
Password:<cisco>
SCE>show interface linecard 0 subscriber anonymous amount name anon1
SCE>
Related Commands
|
|
|
clear interface linecard subscriber |
Clears all anonymous subscribers in the system. |
show interface linecard subscriber anonymous-group
Displays the configuration of the specified anonymous subscriber group.
show interface linecard slot-number subscriber anonymous-group {name group-name | all}
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
group-name |
Anonymous subscriber group. |
all |
Displays all existing anonymous subscriber groups. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the anonymous subscriber groups:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 subscriber anonymous-group all name IP range Template # ---- -------- ---------- Group1 10.10.10.10/99 0 1 anonymous groups are configured SCE>
Related Commands
|
|
|
show interface linecard subscriber db counters
Displays the subscriber database counters.
show interface linecard slot-number subscriber db counters
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Counter Definitions
The following sections present definitions of the counters displayed in the output of this command.
Current values:
Subscribers: Number of currently existing subscribers (excluding subscribers waiting to be removed).
Introduced subscribers: Number of introduced subscribers.
Anonymous subscribers: Number of anonymous subscribers.
Subscribers with mappings: Number of subscribers with mappings.
Single non-VPN IP mappings: Number of mappings to single IP addresses.
Non-VPN IP Range mappings: Number of mappings to ranges of IP addresses.
VLAN based subscribers (appears only if VLAN-based subscribers are enabled): Number of VLAN based VPNs with subscribers.
Subscribers with open sessions: Number of subscribers with open flows (sessions).
Sessions mapped to the default subscriber: Number of open flows (sessions) related to the default party.
Peak values:
Peak number of subscribers with mappings:
Peak number occurred at:
Peak number cleared at:
Event counters:
Subscriber introduced: Number of login calls resulting in adding a subscriber.
Subscriber pulled: Number of pullResponse calls.
Subscriber aged: Number of aged subscribers.
Pull-request notifications sent: Number of pull-request notifications sent.
State notifications sent: Number of state change notifications sent to peers.
Logout notifications sent: Number of logout events.
Examples
The following example shows the output from this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 subscriber db counters Current values: =============== Subscribers: 3 used out of 9999 max. Introduced/Pulled subscribers: 3. Anonymous subscribers: 0. Subscribers with mappings: 3 used out of 9999 max. Single non-VPN IP mappings: 1. non-VPN IP Range mappings: 1. Subscribers with open sessions: 0. Sessions mapped to the default subscriber: 0.
Related Commands
|
|
|
clear interface linecard subscriber db counters |
Clears the "total" and "maximum" subscribers database counters. |
show interface linecard subscriber mapping
Displays subscribers whose mapping meets the specified criteria.
show interface linecard slot-number subscriber mapping [IP ip-address/range] [[amount] included-in IP ip-range [VPN vpn-name | any-vpn]] [VLAN-id vlan-id ] [none]
Syntax Description
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Use this command to display subscribers whose mapping meets one of the following specified criteria:
•![]() Matches a specified IP address or range of IP addresses (exact match of the specified range)
Matches a specified IP address or range of IP addresses (exact match of the specified range)
•![]() Intersects a specified IP range (not necessarily an exact match of the specified range, but with IP addresses that are within the specified range)
Intersects a specified IP range (not necessarily an exact match of the specified range, but with IP addresses that are within the specified range)
•![]() Matches a specified VLAN tag (This option is provided for backwards compatibility and has certain restrictions. See Note below)
Matches a specified VLAN tag (This option is provided for backwards compatibility and has certain restrictions. See Note below)
•![]() Matches a specified VPN mapping (This option is provided for backwards compatibility and has certain restrictions. See Note below)
Matches a specified VPN mapping (This option is provided for backwards compatibility and has certain restrictions. See Note below)
•![]() Has no mapping
Has no mapping
The any-vpn keyword is a wildcard that matches all the mappings within the IP ranges, regardless of their VPN, including non-VPN mappings.
Note the specific results of the following options:
•![]() VLAN—if the VLAN tag is configured as a single subscriber (mapped to 0.0.0.0/0 on the VPN that is mapped to the specified VLAN tag) this option displays that subscriber.
VLAN—if the VLAN tag is configured as a single subscriber (mapped to 0.0.0.0/0 on the VPN that is mapped to the specified VLAN tag) this option displays that subscriber.
•![]() included-in IP (no VPN specified)—matches non-VPN mappings only
included-in IP (no VPN specified)—matches non-VPN mappings only
•![]() included-in IP VPN—matches private-IP mappings
included-in IP VPN—matches private-IP mappings
•![]() IP and VPN- the mapping must match the exact VPN as well as the IP range
IP and VPN- the mapping must match the exact VPN as well as the IP range

Note ![]() The VLAN option is provided for backward compatibility. The options require that the entire VLAN or VPN be defined as a single subscriber with an IP address of 0.0.0.0/0@vpn, which corresponds to the VPN and VLAN subscriber definition of pre-3.1.5 versions.
The VLAN option is provided for backward compatibility. The options require that the entire VLAN or VPN be defined as a single subscriber with an IP address of 0.0.0.0/0@vpn, which corresponds to the VPN and VLAN subscriber definition of pre-3.1.5 versions.
Authorization: viewer
Examples
The following example shows how to list the number of subscribers with no mapping:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 subscriber mapping amount none Subscribers with no mappings: N/A Total 1 subscribers listed. SCE>
Related Commands
|
|
|
show interface linecard subscriber max-subscribers
Displays the maximum number of subscribers. The command also indicates whether the capacity options have been disabled.
show interface linecard slot-number subscriber max-subscribers
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the maximum number of subscribers when the capacity options have not been disabled. (In which case the capacity options determine the maximum number of subscribers.)
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 subscriber max-subscribers Configured actual maximum number of subscribers: 80000. Note, however, that Subscriber Capacity Options are enabled, and they determine the actual maximum number of subscribers. SCE>
Related Commands
|
|
|
subscriber max-subscribers |
Specifies the maximum number of subscribers. |
subscriber capacity-options |
Overrides the capacity option when loading the SCA BB application. |
show interface linecard subscriber name
Displays information about a specified subscriber.
show interface linecard slot-number subscriber name name [mappings] [counters] [properties]
Syntax Description
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
The following information can be displayed:
•![]() Mappings
Mappings
•![]() OS counters (bandwidth and current number of flows)
OS counters (bandwidth and current number of flows)
•![]() All values of subscriber properties
All values of subscriber properties
•![]() All of the above
All of the above
If no category is specified, a complete listing of property values, mappings, and counters is displayed.
Authorization: viewer
Examples
The following example shows how to list the mappings for the specified subscriber:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 subscriber name gold123 mappings Subscriber 'gold123' mappings: IP 10.0.0.0 - Expiration (sec): Unlimited SCE>
Related Commands
|
|
|
subscriber name property name |
Assigns a value to the specified property of the specified subscriber. |
show interface linecard subscriber name breach-state
Displays all breached buckets for the specified subscriber.
show interface linecard slot-number subscriber name name breach-state
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
name |
Name of the subscriber for which to display the breach-state |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following examples show output from this command.
Example 1
SCE>enable 5
Password:<cisco>
SCE>show interface linecard 0 subscriber name john_doe breach-state
No BREACHED buckets
SCE>
Example 2
SCE>enable 5
Password:<cisco>
SCE>show interface linecard 0 subscriber name jane_smith breach-state
Bucket 2 is breached.
Bucket 3 is breached.
Bucket 4 is breached.
Bucket 5 is breached
Related Commands
|
|
|
show interface linecard subscriber name bucket-state |
Displays all buckets used by the specified subscriber |
show interface linecard subscriber name bucket-state
Displays all buckets used by the specified subscriber.
show interface linecard slot-number subscriber name name bucket-state
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
name |
Name of the subscriber for which to display the breach-state |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows output from this command.
SCE>enable 5
Password:<cisco>
SCE>show interface linecard 0 subscriber name john_doe bucket-state
Bucket 1 is used. Status - Not Breached.
Bucket 2 is used. Status - Breached.
Bucket 3 is used. Status - Breached.
Bucket 4 is used. Status - Breached.
Bucket 5 is used. Status - Breached.
Bucket 6 is used. Status - Not Breached.
Bucket 7 is used. Status - Not Breached.
Bucket 8 is used. Status - Not Breached.
Bucket 9 is used. Status - Not Breached.
Bucket 10 is used. Status - Not Breached.
Bucket 11 is used. Status - Not Breached.
Bucket 12 is used. Status - Not Breached.
Bucket 13 is used. Status - Not Breached.
Bucket 14 is used. Status - Not Breached.
Bucket 15 is used. Status - Not Breached.
Bucket 16 is used. Status - Not Breached.
SCE>
Related Commands
show interface linecard subscriber name bucket-state id
Displays specific bucket size, usage and state.
show interface linecard slot-number subscriber name name bucket-state id bucket#
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
name |
Name of the subscriber for which to display the breach-state |
bucket# |
Number of the bucket to display. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows output from this command.
SCE>enable 5
Password:<cisco>
SCE>show interface linecard 0 subscriber name john_doe bucket-state id 3
Bucket type: Sessions
Bucket state: Breached
Bucket size: 2
Bucket usage: 2
SCE>
Related Commands
|
|
|
show interface linecard subscriber name bucket-state |
Displays all buckets used by the specified subscriber. |
show interface linecard subscriber properties
Displays all existing subscriber properties.
show interface linecard slot-number subscriber properties
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the subscriber properties:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 subscriber properties Subscriber properties: "monitor" : int16, minValue=0, maxValue=1. "new_classification_policy" : Uint16. "packageId : Uint16, minValue=0, maxValue=4999. "QpLimit" : int32[18]. "QpSet" : Uint8[18]. Subscriber read-only properties: "concurrentAttacksNumber" : Uint8. "PU_QP_QuotaSetCounter" : Uint8[18]. "PU_QP_QuotaUsageCounter" : int32[18]. "PU_REP_nonReportedSessionsInTUR" : int32. "P_aggPeriodType" :Uint8. "P_blockReportCounter : int32 "P_endOfAggPeriodTimestamp : Uint32. "P_firstTimeParty" : bool. "P_localEndOfAggPeriodTimestamp : Uint32. "P_mibSubCounters16" : Uint16[36][2]. "P_mibSubCounters32" : Uint32[36][2]. "P_newParty" : bool. "P_numOfRedirections : Uint8. "P_partyCurrentPackage : Uint16 "P_partyGoOnlineTime : Uint32 "P_partyMonth : Uint16 SCE>
Related Commands
|
|
|
show interface linecard subscriber sm-connection-failure
Displays the current state of the SM-SCE platform connection, as well as the configured action to take if that connection fails.
show interface linecard slot-number subscriber sm-connection-failure [timeout]
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
timeout |
Displays the configured SM-SCE platform link failure timeout value. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the state of the SM-SCE platform connection:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 subscriber subscriber sm-connection-failure Current SM link state: down. Please note that this refers to the logical connection, which means the synchronization with the SM i.e. There might be cases where the connection at the SM will be up and down at the SE since synchronization hasn't been completed yet. Configured action to take when SM link is down: No action SCE>
The following example shows how to display the configured timeout value for the SM-SCE platform connection:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 subscriber subscriber sm-connection-failure timeout SM SCE link failure timeout is: 90 SCE>
Related Commands
|
|
|
subscriber sm-connection-failure |
Configures the behavior of the system if communication fails between the SM and the SCE platform. |
show interface linecard subscriber templates
Displays a specified subscriber template.
show interface linecard slot-number subscriber templates {all | index template-number}
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
template-number |
Index number of the template to be displayed. |
all |
Displays all existing subscriber templates. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display a specified subscriber template:
SCE>enable 5 SCE>show interface linecard 0 subscriber templates index 3 Subscriber template 3 properties monitor=0 new_classification_policy=0 packageId=0 QpLimit[0..17]=0*17,8 QpSet[0..17]=0*17,1 SCE> Password:<cisco>
Related Commands
|
|
|
show interface linecard tos-marking
Displays the current TOS marking state.
show interface linecard slot-number tos-marking
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Use this command to display the current TOS marking state, including the translation table and the marking mode for each interface (enable or disable).
Authorization: viewer
Examples
The following example shows a sample of the output from this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 tos-marking ToS Translation Table ===================== | tos-id | tos-value (DSCP) | |--------|------------------| | 1 | 00 (0x00) | | 2 | 00 (0x00) | | 3 | 00 (0x00) | | 4 | 00 (0x00) | | 5 | 00 (0x00) | | 6 | 00 (0x00) | | 7 | 00 (0x00) | ToS Marking state by egress interface ===================================== | Interface | State | |------------|----------| | 1 | Disabled | | 2 | Disabled | | 3 | Disabled | | 4 | Disabled | SCE>
Related Commands
|
|
|
tos-marking enabled |
|
tos-marking clear-table |
|
tos-marking set-table-entry |
show interface linecard traffic-counter
Displays the specified traffic counter.
show interface linecard slot-number traffic-counter {name | all}
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
name |
Name of the traffic counter to be displayed. |
all |
Displays all traffic counters. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display information for all existing traffic counters:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 traffic-counter all Counter 'cnt' value: 0 packets. Rules using it: None. Counter 'cnt2' value: 1284 packets. Rules using it: Rule2. 2 counters listed out of 32 available. SCE>
Related Commands
|
|
|
traffic-counter |
Defines a new traffic counter. |
clear interface linecard traffic-counter |
Clears the specified traffic counter. |
show interface linecard traffic-rule
Displays the specified traffic rule configuration.
show interface linecard slot-number traffic-rule {name name | tunnel-id-mode | all}
Syntax Description
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display traffic rule information:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 traffic-rule name Rule1 0 rules listed out of 127 available. SCE>
Related Commands
|
|
|
traffic-rule |
Defines a new traffic rule. |
show interface linecard virtual-links
Displays the currently configured virtual links.
show interface linecard slot-number virtual-links all
show interface linecard slot-number virtual-links changed
Syntax Description
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
You can also use this command to see which virtual links have global controllers whose values have been changed from the original SCA BB configuration.
Authorization: viewer
Examples
The following example shows how to display all existing virtual links:
SCE>enable 5
password<cisco>
SCE>show interface linecard 0 virtual-links all
Virtual Link enabled
Virtual link index 1 direction upstream
Virtual link index 2 direction upstream
Virtual link index 3 direction upstream
Virtual link index 4 direction upstream
Virtual link index 12 direction upstream
Virtual link index 13 direction upstream
Virtual link index 14 direction upstream
Virtual link index 15 direction upstream
The following example shows how to display the virtual links that have GCs with values that are different from the original configuration:
SCE>enable 5
password<cisco>
SCE>show interface linecard 0 virtual-links changed
Virtual Link enabled
Virtual link index 3 direction upstream
Global Controller index 0 timebased values = 300,300,300,300
Global Controller index 1 timebased values = 500,500,500,500
Virtual link index 12 direction upstream
Global Controller index 0 timebased values = 700,700,700,700
Virtual link index 14 direction upstream
Global Controller index 0 timebased values = 5500,5500,5500,5500
Global Controller index 1 timebased values = 1500,1500,1500,1500
Related Commands
|
|
|
|---|---|
virtual-links index direction |
Adds a new virtual link. |
show interface linecard vlan
Displays the VLAN tunnel configuration.
show interface linecard slot-number vlan
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the VLAN configuration:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 vlan VLAN symmetric skip SCE>
Related Commands
|
|
|
vlan |
Configures the VLAN environment. |
show interface linecard vpn
Displays information regarding currently logged-in VPNs.
show interface linecard slot-number VPN {name vpn-name | all-names [automatic]}
Syntax Description
slot-number |
The number of the identified slot. Enter a value of 0. |
vpn-name |
The name of the VPN in which to search for the IP mapping. |
Defaults
This command has no default settings.
Command Modes
User Exec
Usage Guidelines
Use the name option to specify a specific currently logged-in VPN for which to display the details.
Use the all-names keyword to display he names of all VPNs that are currently logged into the system.
Use the automatic keyword with the all-names option to display the names of all VPNs that were created automatically by the SCE platform.
Authorization: viewer
Examples
The following examples illustrate how to use this command.
EXAMPLE 1
The following example displays names of all currently logged in VPNs.
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 VPN all-names There are 2 VPNs in the data-base: VPN1 VPN2
EXAMPLE 2
The following example illustrates the output of this command for an empty VPN:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 VPN name Vpn2 VPN name: Vpn2 VPN has no mappings Number of subscriber mappings: 0 SCE>
EXAMPLE 3
The following example illustrates the output of this command for a VLAN-based VPN:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 VPN name Vpn3 VPN name: Vpn3 VLAN: 2 Number of subscriber mappings: 0 SCE>
EXAMPLE 4
The following example illustrates the output of this command for an automatically created VLAN VPN:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 VPN name Vpn2 VPN name: Vpn2 VLAN: 2 Number of subscriber mappings: 1 Automatically created VPN SCE>
Related Commands
|
|
|
show interface linecard wap
Displays the current WAP handling state.
show interface linecard slot-number wap
Syntax Description
slot-number |
Number of the identified slot. Enter a value of 0. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show interface linecard 0 wap WAP handling is disabled SCE>
Related Commands
|
|
|
wap |
Enables or disables operating in a WAP environment. |
show interface tengigabitethernet
Displays the details of a TenGigabitEthernet Interface.
show interface tengigabitethernet slot-number/bay-number/interface-number [counters [direction] | queue queue-number]
Syntax Description
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display information about the TenGigabitEthernet interface:
SCE>enable 5 Password:<cisco>
SCE>show interface TenGigabitEthernet 3/2/0
Auto negotiation configured: Disabled
Actual status:
Link is: ON
Auto negotiation: Disabled
Bandwidth (L1): 10000000 Kbps, Burst-size: 500000 bytes
Traffic side is "subscriber" (default configuration)
Pseudo IP Address: Not Configured
SCE>
Related Commands
show inventory
Displays UDI information for the SCE platform.
show inventory [raw]
Syntax Description
raw |
Displays the complete inventory of the SCE platform. When this keyword is not used, only field replaceable units (FRUs) are displayed. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Use this command to display the following UDI information for the SCE platform:
•![]() Device name
Device name
•![]() Description
Description
•![]() Product identifier
Product identifier
•![]() Version identifier
Version identifier
•![]() Serial number
Serial number
Authorization: viewer
Examples
The following examples show output from this command.
Example 1
The following example shows how to display the UDI information for the SCE platform:
SCE>enable 5 Password:<cisco> SCE>show inventory NAME: "Chassis", DESCR: "Cisco SCE 2020 Service Control Engine, Multi Mode, 4-port GE" PID: SCE2020-4XGBE-MM , VID: V01, SN: CAT093604K3 SCE>
Example 2
The following example shows how to display the inventory (UDIs) for the FRUs only:
SCE>enable 5 Password:<cisco> SCE>show inventory NAME: "SCE8000 Chassis", DESCR: "CISCO7604" PID: CISCO7604 , VID: V0 , SN: FOX105108X5 NAME: "SCE8000 Service Control Module (SCM) in slot 1", DESCR: "SCE8000-SCM-E" PID: SCE8000-SCM-E , VID: V0 , SN: CAT1122584N NAME: "SCE8000 SPA Interface Processor (SIP) in slot 3", DESCR: "SCE8000-SIP" PID: SCE8000-SIP , VID: V0 , SN: CAT1150G07F NAME: "SPA-1X10GE-L-V2", DESCR: "SPA-1X10GE-L-V2" PID: SPA-1X10GE-L-V2 , VID: V02, SN: JAE11517RMR NAME: "SPA-1X10GE-L-V2", DESCR: "SPA-1X10GE-L-V2" PID: SPA-1X10GE-L-V2 , VID: V02, SN: JAE11496E1P NAME: "SPA-1X10GE-L-V2", DESCR: "SPA-1X10GE-L-V2" PID: SPA-1X10GE-L-V2 , VID: V02, SN: JAE11517RIO NAME: "SPA-1X10GE-L-V2", DESCR: "SPA-1X10GE-L-V2" PID: SPA-1X10GE-L-V2 , VID: V02, SN: JAE115295HH NAME: "SCE8000 FAN 1", DESCR: "FAN-MOD-4HS" PID: FAN-MOD-4HS , VID: V0 , SN: DCH11013744 NAME: "SCE8000 AC or DC power supply 0", DESCR: "PWR-2700-AC/4" PID: PWR-2700-AC/4 , VID: V0 , SN: APQ105000MV NAME: "SCE8000 AC or DC power supply 1", DESCR: "PWR-2700-DC/4" PID: PWR-2700-AC/4 , VID: V0 , SN: APQ105000MV NAME: "XFP-10GLR-OC192SR ", DESCR: "XFP-10GLR-OC192SR " PID: XFP-10GLR-OC192SR , VID: V02, SN: AGA1142N4B7 NAME: "XFP-10GLR-OC192SR ", DESCR: "XFP-10GLR-OC192SR " PID: XFP-10GLR-OC192SR , VID: V02, SN: AGA1142N4AL NAME: "XFP-10GLR-OC192SR ", DESCR: "XFP-10GLR-OC192SR " PID: XFP-10GLR-OC192SR , VID: V02, SN: AGA1141N43R NAME: "XFP-10GLR-OC192SR ", DESCR: "XFP-10GLR-OC192SR " PID: XFP-10GLR-OC192SR , VID: V02, SN: AGA1143N4JN
Example 3
The following example shows how to display the complete inventory (UDIs) of the SCE platform:
SCE>enable 5 Password:<cisco> SCE>show inventory raw PID: CISCO7604 , VID: V0 , SN: FOX105108XB NAME: "SCE8000 Physical Slot 1", DESCR: "Container SCE8000 Service Control Module (SCM) slot" PID: "" , VID: "" , SN: "" NAME: "SCE8000 Physical Slot 2", DESCR: "Container SCE8000 Service Control Module (SCM) slot" PID: "" , VID: "" , SN: "" NAME: "SCE8000 Physical Slot 3", DESCR: "Container SCE8000 SPA Interface Processor (SIP) slot" PID: "" , VID: "" , SN: "" NAME: "SCE8000 Physical Slot 4", DESCR: "Container SCE8000 Optical Bypass slot" PID: "" , VID: "" , SN: "" NAME: "SCE8000 Fan Module", DESCR: "Container SCE8000 Fan Module" PID: "" , VID: "" , SN: "" NAME: "SCE8000 AC or DC power supply", DESCR: "Container SCE8000 AC or DC power supply" PID: "" , VID: "" , SN: "" NAME: "SCE8000 Link", DESCR: "Container SCE8000 Link" PID: "" , VID: "" , SN: "" NAME: "SCE8000 Backplane", DESCR: "Container SCE8000 Backplane " PID: "" , VID: "" , SN: "" NAME: "SCE8000 Service Control Module (SCM) in slot 1", DESCR: "SCE8000-SCM-E" PID: SCE8000-SCM-E , VID: V0 , SN: CAT1151G00Z NAME: "SCE8000 SPA Interface Processor (SIP) in slot 3", DESCR: "SCE8000-SIP" PID: SCE8000-SIP , VID: V0 , SN: CAT1204G020 NAME: "SCE8000 Link 0", DESCR: "SCE8000 Link" PID: "" , VID: "" , SN: "" NAME: "SCE8000 Link 1", DESCR: "SCE8000 Link" PID: "" , VID: "" , SN: "" NAME: "SCE8000 SIP bay 3/0", DESCR: "SCE8000 SIP bay" PID: "" , VID: "" , SN: "" NAME: "SCE8000 SIP bay 3/1", DESCR: "SCE8000 SIP bay" PID: "" , VID: "" , SN: "" NAME: "SCE8000 SIP bay 3/2", DESCR: "SCE8000 SIP bay" PID: "" , VID: "" , SN: "" NAME: "SCE8000 SIP bay 3/3", DESCR: "SCE8000 SIP bay" PID: "" , VID: "" , SN: "" NAME: "SPA-1X10GE-L-V2", DESCR: "SPA-1X10GE-L-V2" PID: SPA-1X10GE-L-V2 , VID: V02, SN: JAE11485LPJ NAME: "SPA-1X10GE-L-V2", DESCR: "SPA-1X10GE-L-V2" PID: SPA-1X10GE-L-V2 , VID: V02, SN: JAE11485L4C NAME: "SPA-1X10GE-L-V2", DESCR: "SPA-1X10GE-L-V2" PID: SPA-1X10GE-L-V2 , VID: V02, SN: JAE11485L9V NAME: "SPA-1X10GE-L-V2", DESCR: "SPA-1X10GE-L-V2" PID: SPA-1X10GE-L-V2 , VID: V02, SN: JAE11485LAP NAME: "TenGigabitEthernet3/0/0", DESCR: "SCE8000 SPA port" PID: "" , VID: "" , SN: "" NAME: "TenGigabitEthernet3/1/0", DESCR: "SCE8000 SPA port" PID: "" , VID: "" , SN: "" NAME: "TenGigabitEthernet3/2/0", DESCR: "SCE8000 SPA port" PID: "" , VID: "" , SN: "" NAME: "TenGigabitEthernet3/3/0", DESCR: "SCE8000 SPA port" PID: "" , VID: "" , SN: "" NAME: "SCE8000 FAN 1", DESCR: "FAN-MOD-4HS" PID: FAN-MOD-4HS , VID: V0 , SN: DCH10511402 NAME: "SCE8000 AC or DC power supply 0", DESCR: "PWR-2700-AC/4" PID: PWR-2700-AC/4 , VID: V0 , SN: APQ105100F8 NAME: "SCE8000 AC or DC power supply 1", DESCR: "PWR-2700-AC/4" PID: PWR-2700-AC/4 , VID: V0 , SN: APQ105100F8 NAME: "XFP-10GZR-OC192LR ", DESCR: "XFP-10GZR-OC192LR " PID: XFP-10GZR-OC192LR , VID: V01, SN: FNS11061SBB NAME: "XFP-10GZR-OC192LR ", DESCR: "XFP-10GZR-OC192LR " PID: XFP-10GZR-OC192LR , VID: V01, SN: FNS11021359 NAME: "XFP-10G-MM-SR ", DESCR: "XFP-10G-MM-SR " PID: XFP-10G-MM-SR , VID: V01, SN: FNS12130MLQ NAME: "XFP-10G-MM-SR ", DESCR: "XFP-10G-MM-SR " PID: XFP-10G-MM-SR , VID: V01, SN: FNS12130MHF NAME: "SCE8000 traffic processor 1", DESCR: "SCE8000 traffic processor" PID: "" , VID: "" , SN: "" NAME: "SCE8000 traffic processor 2", DESCR: "SCE8000 traffic processor" PID: "" , VID: "" , SN: "" NAME: "SCE8000 traffic processor 3", DESCR: "SCE8000 traffic processor" PID: "" , VID: "" , SN: "" NAME: "SCE8000 traffic processor 4", DESCR: "SCE8000 traffic processor" PID: "" , VID: "" , SN: "" NAME: "SCE8000 traffic processor 5", DESCR: "SCE8000 traffic processor" PID: "" , VID: "" , SN: "" NAME: "SCE8000 traffic processor 6", DESCR: "SCE8000 traffic processor" PID: "" , VID: "" , SN: "" NAME: "SCE8000 traffic processor 7", DESCR: "SCE8000 traffic processor" PID: "" , VID: "" , SN: "" NAME: "SCE8000 traffic processor 8", DESCR: "SCE8000 traffic processor" PID: "" , VID: "" , SN: "" NAME: "SCE8000 traffic processor 9", DESCR: "SCE8000 traffic processor" PID: "" , VID: "" , SN: "" NAME: "SCE8000 traffic processor 10", DESCR: "SCE8000 traffic processor" PID: "" , VID: "" , SN: "" NAME: "SCE8000 traffic processor 11", DESCR: "SCE8000 traffic processor" PID: "" , VID: "" , SN: "" NAME: "SCE8000 traffic processor 12", DESCR: "SCE8000 traffic processor" PID: "" , VID: "" , SN: ""
Related Commands
|
|
|
show ip access-class
Displays the access list defined for global IP access to the SCE platform. Only IP addresses permitted access according to this access list are allowed access to the system.
show ip access-class
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the IP access class mapping:
SCE>enable 5 Password:<cisco> SCE>show ip access-class IP layer is using access-list # 1. SCE>
Related Commands
|
|
|
ip access-class |
Specifies which access control list (ACL) controls global access to the SCE platform. |
show ip advertising
Displays the status of IP advertising, the configured destination, and the configured interval.
show ip advertising [destination | interval]
Syntax Description
destination |
Displays the IP advertising destination. |
interval |
Displays the interval between ping commands. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the IP advertising status and configuration:
SCE>enable 5 Password:<cisco> SCE>show ip advertising IP advertising is disabled IP advertising destination is 10.10.10.10 IP advertising interval is 853 seconds SCE>
Related Commands
|
|
|
ip advertising |
Enables IP advertising. |
show ip default-gateway
Displays the configured default gateway.
show ip default-gateway
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the default gateway:
SCE>enable 5 Password:<cisco> SCE>show ip default-gateway Default gateway: 10.1.1.1 SCE>
Related Commands
|
|
|
ip default-gateway |
Configures the default gateway for the SCE platform. |
show ip filter
Displays information about the management interface IP filtering.
show ip filter
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Use this command to display the following information for management interface IP filtering.
•![]() IP fragment filter enabled or disabled
IP fragment filter enabled or disabled
•![]() Configured attack threshold (permitted and not-permitted IP addresses)
Configured attack threshold (permitted and not-permitted IP addresses)
•![]() Configured end-of-attack threshold (permitted and not-permitted IP addresses)
Configured end-of-attack threshold (permitted and not-permitted IP addresses)
•![]() Burst size in seconds (permitted and not-permitted IP addresses)
Burst size in seconds (permitted and not-permitted IP addresses)
Authorization: viewer
Examples
The following example shows how to display information about management interface IP filtering:
SCE>enable 5 Password:<cisco> SCE>show ip filter is fragment filtered : 0 Input Bandwidth : 0 Kb/sec Input packets rate : 2 Pkt/sec Input bandwidth policer : CIR: 20000.00 Kb/sec BTime: 200 msec LP: 100 % Input packet rate policer : CIR: 5000.00 Pkt/sec BTime: 200 msec LP: 100 % Permit monitor :state : no_attack BW: 0 High : CIR: 20000.00 Kb/sec BTime: 10000 msec LP: 100 % Low : CIR: 20000.00 Kb/sec BTime: 10000 msec LP: 100 % Denied monitor :state : no_attack BW: 0 High : CIR: 20000.00 Kb/sec BTime: 10000 msec LP: 100 % Low : CIR: 20000.00 Kb/sec BTime: 10000 msec LP: 100 % in_bytes : 85115466 in_pkt : 371598 in_pkt_accept : 371598 in_pkt_denied : 0 drop_fragment_cnt : 0 action_delay_due_bw : 0 action_delay_due_pkt : 0 PERMIT events meStartAttack : 0 meStopAttack : 0 DENIED events meStartAttack : 0 SCE>
Related Commands
|
|
|
ip filter fragment |
|
ip filter monitor |
show ip radius-client
Displays the RADIUS client general configuration.
show ip radius-client
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#show ip radius-client SCE>
Related Commands
|
|
|
ip radius-client retry limit |
Configures the parameters for retransmitting unacknowledged RADIUS client messages. |
show ip route
Displays the entire routing table and the destination of last resort (default gateway). When you use the prefix and mask arguments, the command displays the routing entries from the subnet specified by the prefix and mask pair.
show ip route [prefix mask ]
Syntax Description
prefix |
Prefix of the routing entries to be included. |
mask |
Limits the search of routing entries. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the default gateway:
SCE>enable 5 Password:<cisco> SCE>show ip route gateway of last resort is 10.1.1.1 SCE>
The following example shows how to retrieve the IP route:
SCE>enable 5 Password:<cisco> SCE>show ip route 10.1.60.0 255.255.255.0 | prefix | mask | next hop | |--------------|--------------|--------------| | 10.1.60.0 | 255.255.255.0 | 10.1.1.5 | SCE>
Related Commands
|
|
|
ip route |
Adds an IP routing entry to the routing table. |
show ip rpc-adapter
Displays the status of the RPC adapter (enabled or disabled) and the configured port.
show ip rpc-adapter [sessions]
Syntax Description
sessions |
Displays information about RPC adapter sessions. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the configuration of the RPC adapter:
SCE>enable 5 Password:<cisco> SCE>show ip rpc-adapter RPC Server is OFFLINE RPC Server port is 14374 SCE>
Related Commands
|
|
|
ip rpc-adapter |
Enables the RPC adapter. |
ip rpc-adapter port |
Defines the RPC adapter port. |
show ip ssh
Displays the status of the SSH server, including current SSH sessions.
show ip ssh
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to retrieve the current SSH status:
SCE>enable 5 Password:<cisco> SCE>show ip ssh
SSH server is enabled. SSHv1 support is enabled SSH server does not use any access-list. There are no active SSH sessions. SCE>
Related Commands
|
|
|
ip ssh |
Enables the SSH server. |
show line vty
Displays the Telnet configuration.
show line vty {timeout | access-class in}
Syntax Description
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the access list configured for Telnet lines:
SCE>enable 5 Password:<cisco> SCE>show line vty access-class in Telnet server is using access-list # 1. SCE>
Related Commands
|
|
|
line vty |
Enters Line Configuration mode for Telnet lines, which configures all Telnet lines. |
show log
Displays the contents of the user log file.
show log
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show log 2006-01-25 00:14:46 | INFO | CPU #000 | User message files were successfully cleared, new files were opened 2006-01-25 00:23:07 | INFO | CPU #000 | A new password was set for level 10 2006-01-25 00:49:41 | INFO | CPU #000 | System hostname changed to :ecco" 2006-01-25 01:02:41 | INFO | CPU #000 | Time zone set to GMT 2006-01-25 01:06:33 | INFO | CPU #000 | A new password was set for level 15 2006-01-25 01:08:07 | INFO | CPU #000 | A new password was set for level 5 2006-01-25 01:23:07 | INFO | CPU #000 | IP address of slot 0, port 0 set to 10.10.10 2006-01-25 01:56:44 | INFO | CPU #000 | Configuration file '/system/config.txt' was saved - file size 1200 2006-01-25 05:34:45 | INFO | CPU #000 | A Telnet session from 20.20.20.20 was established SCE>
Related Commands
show logger device
Displays the configuration of the specified SCE platform logger file. The command also displays the current user log counters.
show logger device {line-attack-file-log | user-file-log [counters | max-file-size | status | nv-counters]}
Syntax Description
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the SCE platform line-attack-file-log status and configuration:
SCE>enable 5 Password:<cisco> SCE>show logger device Line-Attack-File-Log Line-Attack-File-Log status: Enabled Line-Attack-File-Log file size: 1000000 SCE>
The following example shows the SCE platform user-file-log counters:
SCE>enable 5 Password:<cisco> SCE>show logger device line-attack-file-log counters device User-File-Log counters Total info messages: 62 Total warning messages: 4 Total error messages: 0 Total fatal messages: 0 Last time these counters were cleared: 02:23:27 GMT TUES January 17 2006 SCE>
Related Commands
|
|
|
logger device |
Disables or enables the specified logger device. |
clear logger |
Clears the SCE platform logger (user log files). |
show management-agent
Displays information about the management agent.
show management-agent
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Use this command to display the following information for the management agent:
•![]() Status (enabled or disabled)
Status (enabled or disabled)
•![]() Access control list number assigned
Access control list number assigned
Authorization: viewer
Examples
The following example shows how to display the information about the management agent:
SCE>enable 5 Password:<cisco> SCE>show management-agent management agent is enabled. management agent is active, version: SCE Agent 3.0.3 Build 15 management agent does not use any access-list. SCE>
Related Commands
|
|
|
management-agent access-class |
|
service management-agent |
show management-agent sce-api quota
Displays information about the quota message buffer.
show management-agent sce-api quota
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Use this command to display the following information about the quota message buffer:
•![]() Quota rate control
Quota rate control
•![]() Maximum size of the buffer
Maximum size of the buffer
•![]() Number of messages currently in the buffer that are waiting to be sent to the QM
Number of messages currently in the buffer that are waiting to be sent to the QM
Authorization: viewer
Examples
The following example shows how to display the information about the quota message buffer:
SCE>enable 5
Password:<cisco>
SCE>show management-agent sce-api quota
Quota rate control : 125
Quota max buffer size : 1000
Quota msg in buffer : 0
SCE>
Related Commands
|
|
|
management-agent sce-api quota-buffer-size |
show pqi file
Displays information, such as installation options, about the specified application file.
show pqi file filename info
Syntax Description
filename |
Filename of the application file. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display application file information:
SCE>enable 5
Password:<cisco>
SCE>show pqi file myfile.pqi info
application: sm
description: SCE 1000 sm
target SCE : SCE 1000
module names: sm20001.pm0
SCE>
Related Commands
|
|
|
pqi install file |
Installs the specified pqi file using any specified installation options. |
show pqi last-installed
Displays the name of the last pqi file that was installed.
show pqi last-installed
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to find out which pqi file is installed:
SCE>enable 5 Password:<cisco> SCE>show pqi last-installed package name: SACS BB package version 3.0.1. build 02 package date: Tue Jun 10 17:27:55 GMT+00:00 2006 operation: Upgrade SCE>
Related Commands
|
|
|
pqi rollback file |
Reverses an upgrade of the specified pqi file. |
pqi uninstall file |
Uninstalls the specified pqi file. |
show processes cpu
Displays detailed CPU utilization statistics (CPU use per process).
show processes cpu [sorted]
Syntax Description
sorted |
(Optional) Displays CPU history sorted by percentage of utilization. |
Defaults
This command has no default settings.
Command Modes
User Exec
Usage Guidelines
Authorization: viewer
Examples
The following example illustrates the use of this command.
SCE>enable 5
Password:<cisco>
SCE>show processes cpu
CPU utilization for five seconds: 24%/ 0%; one minute: 29%; five minutes: 20%
PID Runtime(ms) Invoked uSecs 5Sec 1Min 5Min TTY Process
1 78790 6374 0 0.00% 0.00% 0.00% 0 (init)
2 10 1 0 0.00% 0.00% 0.00% 0 (kthreadd)
3 5010 501 0 0.00% 0.00% 0.00% 0 (migration/0)
4 90 9 0 0.00% 0.00% 0.00% 0 (ksoftirqd/0)
5 63130 6313 0 0.00% 0.00% 0.00% 0 (watchdog/0)
6 4940 494 0 0.00% 0.00% 0.00% 0 (migration/1)
7 0 0 0 0.00% 0.00% 0.00% 0 (ksoftirqd/1)
8 10530 1053 0 0.00% 0.00% 0.00% 0 (watchdog/1)
9 2606490 207337 0 0.00% 0.02% 0.03% 0 (events/0)
10 1246730 123793 0 0.00% 0.02% 0.02% 0 (events/1)
11 0 0 0 0.00% 0.00% 0.00% 0 (khelper)
12 177810 17781 0 0.00% 0.00% 0.00% 0 (kblockd/0)
13 8010 801 0 0.00% 0.00% 0.00% 0 (kblockd/1)
16 0 0 0 0.00% 0.00% 0.00% 0 (kswapd0)
17 0 0 0 0.00% 0.00% 0.00% 0 (aio/0)
18 0 0 0 0.00% 0.00% 0.00% 0 (aio/1)
19 0 0 0 0.00% 0.00% 0.00% 0 (nfsiod)
20 0 0 0 0.00% 0.00% 0.00% 0 (mtdblockd)
21 1198570 119326 0 0.00% 0.02% 0.02% 0 (skynet)
22 7413850 741207 0 0.00% 0.11% 0.10% 0 (hw-mon-regs)
23 556170 49614 0 0.00% 0.02% 0.01% 0 (scos-dump)
24 527310 52718 0 0.00% 0.00% 0.01% 0 (wdog-kernel)
Related Commands
|
|
|
show rdr-formatter
Displays the RDR formatter configuration.
show rdr-formatter
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the configuration of the RDR formatter:
SCE>enable 5 Password:<cisco> SCE>show rdr-formatter Status: enabled Connection is: down Forwarding mode: redundancy Connection table: ---------------------------------------------------------- Collector | Port | Status | Priority per Category: | IP Address / | | |--------------------------| Host-Name | | | Category1 | Category2 | ---------------------------------------------------------- 10.1.1.205 |33000 | Down | 100 | 100 | 10.1.1.206 |33000 | Down | 60 | 60 | 10.12.12.12 |33000 | Down | 40 | 40 | ---------------------------------------------------------- RDR: queued: 0, sent:4460807, thrown: 0, format-mismatch:0 UM: queued: 0, sent: 0, thrown: 0 Logger: queued: 0, sent: 39, thrown: 0 Errors: thrown: 0 Last time these counters were cleared: 20:23:05 IST WED March 14 2007 SCE>
Related Commands
|
|
|
rdr-formatter destination |
Configures an RDRv1 or NetFlow destination. |
service rdr-formatter |
Enables or disables the RDR formatter. |
show rdr-formatter connection-status
Displays information about the RDR formatter connections.
show rdr-formatter connection-status
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Use this command to display the following information about the RDR formatter connections:
•![]() Main connection
Main connection
•![]() Status—Status and forwarding mode connection table with the following information for each destination:
Status—Status and forwarding mode connection table with the following information for each destination:
–![]() Port
Port
–![]() Status
Status
–![]() Priority
Priority
Authorization: viewer
Examples
The following example shows how to display the RDR formatter connection status:
SCE>enable 5 Password:<cisco> SCE>show rdr-formatter connection-status Connection is: up Forwarding mode: redundancy Connection table: ---------------------------------------------------------- Collector | Port | Status | Priority per Category: | IP Address / | | |--------------------------| Host-Name | | | Category1 | Category2 | ---------------------------------------------------------- 10.1.1.205 |33000 | Up | 100 primary | 100 primary| 10.1.1.206 |33000 | Down | 60 | 60 | 10.12.12.12 |33000 | Up | 40 | 40 | ---------------------------------------------------------- SCE>
Related Commands
show rdr-formatter counters
Displays the RDR formatter counters.
show rdr-formatter counters
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the RDR formatter counters:
SCE>enable 5 Password:<cisco> SCE>show rdr-formatter counters RDR: queued: 0, sent:4460807, thrown: 0, format-mismatch:0 UM: queued: 0, sent: 0, thrown: 0 Logger: queued: 0, sent: 39, thrown: 0 Last time these counters were cleared: 20:23:05 IST WED March 14 2007 SCE>
Related Commands
show rdr-formatter destination
Displays the RDR formatter destinations, including protocol and transport type.
show rdr-formatter destination
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the configured RDRv1 formatter destinations:
SCE>enable 5 Password:<cisco> SCE>show rdr-formatter destination Destination: 10.56.201.50 Port: 33000 Protocol: RDRv1 Destination: 10.56.204.7 Port: 33000 Protocol: NetflowV9 Destination: 10.56.204.10 Port: 33000 Protocol: RDRv1 SCE>
Related Commands
show rdr-formatter enabled
Displays the RDR formatter status (enabled or disabled).
show rdr-formatter enabled
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the status of the RDR formatter (enabled):
SCE>enable 5 Password:<cisco> SCE>show rdr-formatter enabled Status: enabled SCE>
Related Commands
show rdr-formatter forwarding-mode
Displays the configured RDR formatter forwarding mode (redundancy, multicast, or simple load balancing).
show rdr-formatter forwarding-mode
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the RDR formatter forwarding mode:
SCE>enable 5 Password:<cisco> SCE>show rdr-formatter forwarding-mode Forwarding mode: redundancy SCE>
Related Commands
show rdr-formatter history-size
Displays the configured size of the RDR formatter history buffer.
show rdr-formatter history-size
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the size of the RDR formatter history buffer:
SCE>enable 5 Password:<cisco> SCE>show rdr-formatter history-size History buffer size: 16000 bytes SCE>
Related Commands
show rdr-formatter protocol netflowv9 dscp
Displays the DSCP value assigned by NetFlowv9.
show rdr-formatter protocol netflowv9 dscp
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command:
SCE>enable 5 Password:<cisco> SCE>show rdr-formatter protocol netflowv9 dscp Configured DSCP for Netflow traffic: 0 SCE>
Related Commands
show rdr-formatter rdr-mapping
Displays to which RDR formatter category a specified RDR tag is mapped.
show rdr-formatter rdr-mapping {all | tag-id}
Syntax Description
all |
Displays all current RDR category mappings. |
tag-id |
RDR tag. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to use this command and includes partial output:
SCE>enable 5 Password:<cisco> SCE>show rdr-formatter rdr-mapping all Tag Categories --- ---------- 0xb2d05e01 1 0xb2d05e02 1 0xb2d05e04 1 0xb2d05e05 1 0xf0f0f000 1 0xf0f0f002 1 0xf0f0f004 1 0xf0f0f005 1 0xf0f0f010 1 0xf0f0f016 1 0xf0f0f017 1 0xf0f0f018 1 ---More--- SCE>
Related Commands
show rdr-formatter statistics
Displays RDR formatter statistics.
show rdr-formatter statistics
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Use this command to display the following RDR formatter statistics:
•![]() Rates and counters for each connection
Rates and counters for each connection
•![]() Protocol and transport attributes for each connection
Protocol and transport attributes for each connection
•![]() For NetFlow destinations only:
For NetFlow destinations only:
–![]() Number of templates sent
Number of templates sent
–![]() Number of records sent
Number of records sent
Authorization: viewer
Examples
The following example shows how to display the current RDR statistics:
SCE>enable 5 Password:<cisco> SCE>show rdr-formatter statistics RDR-formatter statistics: ========================= Category 1: sent: 1794517 in-queue: 0 thrown: 0 format-mismatch: 0 unsupported-tags: 1701243 rate: 2 RDRs per second max-rate: 64 RDRs per second Category 2: sent: 12040436 in-queue: 0 thrown: 0 format-mismatch: 0 unsupported-tags: 0 rate: 12 RDRs per second max-rate: 453 RDRs per second Category 3: sent: 0 in-queue: 0 thrown: 0 format-mismatch: 0 unsupported-tags: 0 rate: 0 RDRs per second max-rate: 0 RDRs per second Category 4: sent: 0 in-queue: 0 thrown: 0 format-mismatch: 0 unsupported-tags: 0 rate: 0 RDRs per second max-rate: 0 RDRs per second Destination: 10.56.201.50 Port: 33000 Status: up Sent: 13835366 Rate: 211 Max: 679 Last connection establishment: 17 hours, 5 minutes, 14 seconds Destination: 10.56.204.7 Port: 33000 Status: up Sent: 12134054 Rate: 183 Max: 595 Sent Templates: 13732 Sent Data Records: 12134054 Refresh Timeout (Sec): 5 Last connection establishment: 17 hours, 5 minutes, 15 seconds SCE>
Related Commands
show running-config
Displays the current configuration.
show running-config [all-data]
Syntax Description
all-data |
Displays default and nondefault settings. Use this keyword to see sample usage for many CLI configuration commands. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows the output from the show running-config command:
SCE>enable 10 Password:<cisco> SCE#>show running-config all-data #This is a general configuration file (running-config). #Created on 12:06:13 UTC MON May 11 2009 #cli-type 1 #version 1 no management-agent notifications notification-list 1417,1418,804,815,1404,1405,1406,1407,1408,400 no management-agent notifications notification-list 402,421,440,441,444,445,446,450,437,457 no management-agent notifications notification-list 3593,3594,3595,10040 snmp-server community "public" ro RDR-formatter forwarding-mode multicast RDR-formatter destination 10.56.96.26 port 33000 category number 1 priority 100 RDR-formatter destination 10.56.96.26 port 33000 category number 2 priority 100 RDR-formatter destination 10.56.96.26 port 33000 category number 3 priority 100 RDR-formatter destination 10.56.96.26 port 33000 category number 4 priority 100 interface LineCard 0 connection-mode inline on-failure external-bypass no silent no shutdown attack-filter subscriber-notification ports 80 replace spare-memory code bytes 3145728 interface GigabitEthernet 1/1 ip address 10.56.96.46 255.255.252.0 interface TenGigabitEthernet 3/0/0 bandwidth 10000000 burst-size 50000 global-controller 0 name "Default Global Controller" interface TenGigabitEthernet 3/1/0 bandwidth 10000000 burst-size 50000 global-controller 0 name "Default Global Controller" interface TenGigabitEthernet 3/2/0 bandwidth 10000000 burst-size 50000 global-controller 0 name "Default Global Controller" interface TenGigabitEthernet 3/3/0 bandwidth 10000000 burst-size 50000 global-controller 0 name "Default Global Controller" exit ip default-gateway 10.56.96.1 line vty 0 4 exit management-agent property "com.pcube.management.framework.install.activation.operation" "Install" management-agent property "com.pcube.management.framework.install.activated.package" "SCA BB" management-agent property "com.pcube.management.framework.install.activated.version" "3.1.6 build 79" management-agent property "com.pcube.management.framework.install.activation.date" "Sun May 11 08:44:04 GMT+00:00 2008" flow-filter partition name "ignore_filter" first-rule 4 num-rules 32 flow-filter partition name "udpPortsToOpenBySw" first-rule 40 num-rules 21 SCE#
Related Commands
|
|
|
more |
Displays the contents of a file. |
show scmp
Displays the SCMP (ISG) general configuration and status.
show scmp {all | name name} [counters]
Syntax Description
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to display the SCMP counters for a specified destination:
SCE>enable 10 Password:<cisco> SCE#show scmp name scmp_peer1 counters SCMP Connection 'scmp_peer1' counters: Total messages sent: 72 Total messages received: 72 Establish requests sent: 1 Establish replies received: 1 Accounting requests sent: 20 Accounting replies received: 20 Subscriber queries sent: 0 Subscriber query response recv: 0 Request retry exceeded: 0 Requests replied with errors: 0 Subscriber requests received: 50 Subscriber responses sent: 50 Failed Requests: 0 Keep-alive sent: 1 Keep-alive received: 1 SCE>
Related Commands
|
|
|
clear scmp name counters |
Clears the counters for the specified SCMP peer device. |
scmp |
Enables the Service Control Management Protocol functionality. |
show snmp
Displays the SNMP configuration and counters.
show snmp
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the SNMP server configuration and statistics:
SCE>enable 5 Password:<cisco> SCE>show snmp SNMP server status: Enabled Location: London_Office Contact: Brenda Authentication Trap Status: Enabled Communities: ------------ Community: public, Access Authorization: RO, Access List Index: 1 Trap managers: ------------ Trap host: 10.1.1.205, community: public, version: SNMPv2c SNMP stats: 29 SNMP packets input 0 Bad SNMP version errors 29 Unknown community name 0 Illegal operation for community name supplied 0 Encoding errors 0 Number of requested variables 0 Number of altered variables 0 Get-request PDUs 0 Get-next PDUs 0 Set-request PDUs 29 SNMP packets output 0 Too big errors 0 No such name errors 0 Bad values errors 0 General errors 0 Response PDUs 29 Trap PDUs SCE>
Related Commands
show snmp community
Displays configured communities.
show snmp community
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the SNMP manager communities:
SCE>enable 5 Password:<cisco> SCE>show snmp community Community: public, Access Authorization: RO, Access List Index: 1 SCE>
Related Commands
|
|
|
snmp-server community |
Sets a community string. |
show snmp |
Displays the SNMP configuration and counters. |
show snmp contact
Displays the configured MIB-2 variable sysContact.
show snmp contact
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the system contact:
SCE>enable 5 Password:<cisco> SCE>show snmp contact Contact: Brenda@mycompany.com SCE>
Related Commands
|
|
|
snmp-server contact |
Sets the MIB-2 variable system contact. |
show snmp |
Displays the SNMP configuration and counters. |
show snmp enabled
Displays the SNMP agent status (enabled or disabled).
show snmp enabled
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the current status of the SNMP server (enabled):
SCE>enable 5 Password:<cisco> SCE>show snmp enabled SNMP server status: Enabled SCE>
Related Commands
|
|
|
snmp-server |
Enables the SNMP agent. |
show snmp |
Displays the SNMP configuration and counters. |
show snmp host
Displays the destination hosts for SNMP traps.
show snmp host
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the destination hosts for SNMP traps:
SCE>enable 5 Password:<cisco> SCE>show snmp host Trap host: 10.1.1.205, community: public, version: SNMPv2c SCE>
Related Commands
|
|
|
snmp-server host |
Sets destination hosts for SNMP traps. |
show snmp |
Displays the SNMP configuration and counters. |
show snmp location
Displays the configured MIB-2 variable sysLocation.
show snmp location
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the system location:
SCE>enable 5 Password:<cisco> SCE>show snmp location Location: London_Office SCE>
Related Commands
|
|
|
snmp-server location |
Assigns a name to the SCE platform location and sets the MIB-2 variable sysLocation. |
show snmp |
Displays the SNMP configuration and counters. |
show snmp mib
Displays MIB variables.
show snmp mib mib variables
Syntax Description
mib |
Name of the MIB to display. |
variables |
Name of the specific MIB group or object to display. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows the MIB-2 system group:
SCE>enable 5 Password:<cisco> SCE>show snmp mib mib-ii system sysDescr.0 = CiSco Service Engineering, SW version: Control Card Version 1.30 build 29, HW version: SCE GE "RevE" sysObjectID.0 = 1.3.6.1.4.1.5655.1.2 sysUpTime.0 = 14 hours, 25 minutes, 59 seconds sysContact.0 = Brenda@mycompany.com sysName.0 = SCE sysLocation.0 = London_Office sysServices.0 = 2 SCE>
Related Commands
|
|
|
show snmp traps
Displays the status of SNMP trap generation status (enabled or disabled).
show snmp traps
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the status of the SNMP server traps:
SCE>enable 5 Password:<cisco> SCE>show snmp traps Authentication-failure trap status: Disabled operational-status traps status: Enabled system-reset trap status: Enabled chassis traps status: Enabled RDR-formatter traps status: Enabled Telnet traps status: Enabled logger traps status: Enabled SNTP traps status: Enabled link-bypass traps status: Enabled subscriber traps status: Enabled pull-request-failure traps status: Disabled attack traps status: Enabled port-operational-status traps status: Enable SCE>
Related Commands
|
|
|
snmp-server enable traps |
Enables or disables SNMP traps. |
show sntp
Displays the SNTP configuration and update statistics.
show sntp
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display statistics from the SNTP clients:
SCE>enable 5 Password:<cisco> SCE>show sntp SNTP broadcast client: disabled last update time: not available SNTP uni-cast client: enabled there is one server: 1: 128.182.58.100 last update time: June 10 2009, 14:06:41 update interval: 100 seconds SCE>
Related Commands
show startup-config
Displays the startup configuration file.
show startup-config
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Use this command to compare the configuration used by the SCE platform at boot time with the current configuration to make sure that you approve of all the differences before you save the configuration with the copy running-config startup-config command.
Authorization: admin
Examples
The following example shows sample output from this command:
SCE>enable 10 Password:<cisco> SCE#show startup-config #Created on 12:06:13 UTC SUN May 11 2008 #cli-type 1 #version 1 no management-agent notifications notification-list 1417,1418,804,815,1404,1405,1406,1407,1408,400 no management-agent notifications notification-list 402,421,440,441,444,445,446,450,437,457 no management-agent notifications notification-list 3593,3594,3595,10040 snmp-server community "public" ro RDR-formatter forwarding-mode multicast RDR-formatter destination 10.56.96.26 port 33000 category number 1 priority 100 RDR-formatter destination 10.56.96.26 port 33000 category number 2 priority 100 RDR-formatter destination 10.56.96.26 port 33000 category number 3 priority 100 RDR-formatter destination 10.56.96.26 port 33000 category number 4 priority 100 interface LineCard 0 connection-mode inline on-failure external-bypass no silent no shutdown attack-filter subscriber-notification ports 80 replace spare-memory code bytes 3145728 interface GigabitEthernet 1/1 ip address 10.56.96.46 255.255.252.0 interface TenGigabitEthernet 3/0/0 bandwidth 10000000 burst-size 50000 global-controller 0 name "Default Global Controller" interface TenGigabitEthernet 3/1/0 bandwidth 10000000 burst-size 50000 global-controller 0 name "Default Global Controller" interface TenGigabitEthernet 3/2/0 bandwidth 10000000 burst-size 50000 global-controller 0 name "Default Global Controller" interface TenGigabitEthernet 3/3/0 bandwidth 10000000 burst-size 50000 global-controller 0 name "Default Global Controller" exit ip default-gateway 10.56.96.1 line vty 0 4 exit management-agent property "com.pcube.management.framework.install.activation.operation" "Install" management-agent property "com.pcube.management.framework.install.activated.package" "SCA BB" management-agent property "com.pcube.management.framework.install.activated.version" "3.1.6 build 79" management-agent property "com.pcube.management.framework.install.activation.date" "Sun May 11 08:44:04 GMT+00:00 2008" flow-filter partition name "ignore_filter" first-rule 4 num-rules 32 flow-filter partition name "udpPortsToOpenBySw" first-rule 40 num-rules 21 SCE#
Related Commands
|
|
|
more |
Displays the contents of a file. |
show sub-attribute configuration
Displays the attribute table, which contains the attributes currently selected to be captured, as well as the information from the attribute dictionary for each one.
show sub-attribute configuration
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows output from this command.
SCE>enable 5
Password:<cisco>
SCE>show sub-attribute configuration
VSA name Vendor-ID Attr-ID Data Type Protocol Interfaces
-----------------------------------------------------------------------------------------
3GPP-Charging-Characteristics 10415 13 UTF8String Diameter Gx
3GPP-GPRS-Negotiated-QoS-Profile 10415 5 UTF8String Diameter Gx
3GPP-SGSN-Address 10415 1228 Address Diameter Gx
SCE>
Related Commands
|
|
|
sub-attribute add-attribute |
Configures the capture of the specified attribute. |
show sub-attribute dictionary
Displays the complete dictionary table or the entry in the dictionary table for the specified attribute. This command shows the following information for each attribute:
•![]() attribute-name
attribute-name
•![]() vendor ID (if VSA used)
vendor ID (if VSA used)
•![]() attribute code
attribute code
•![]() data type
data type
•![]() protocol interface
protocol interface
show sub-attribute dictionary [attribute-name]
Syntax Description
attribute-name |
Name of the subscriber attribute for which to display the entry in the dictionary table. |
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
Example 1
The following example shows how to display the VSA dictionary.
SCE>enable 5
Password:<cisco>
SCE>show sub-attribute dictionary
VSA name Vendor-ID Attr-ID Data Type Protocol Intrf
----------------------------------------------------------------------------------------
Acct-Multi-Session-ID - 50 UTF8String Radius
Acct-Session-ID - 44 UTF8String Radius
Acct-Session-Time - 46 Uint32 Radius
Called-Station-ID - 30 OCTETString Radius
Calling-Station-ID - 31 OCTETString Radius
Class - 25 OCTETString Radius
CUI - 89 UTF8String Diameter
Framed-IP-Address - 8 Address Radius
NAS-Identifier - 32 OCTETString Radius
NAS-IP-Address - 4 Address Radius
NAS-Port-Type - 61 Uint32 Radius
User-Name - 1 OCTETString Radius
3GPP-Charging-Characteristics 10415 13 UTF8String Diameter
3GPP-Charging-Gateway-Address 10415 4 Address Diameter
3GPP-Charging-ID 10415 2 Uint32 Diameter
3GPP-GGSN-Address-Code-7 10415 7 Address Diameter
3GPP-GGSN-Address 10415 847 Address Diameter
3GPP-GGSN-MCC-MNC 10415 9 UTF8String Diameter
3GPP-GPRS-Negotiated-QoS-Profile 10415 5 UTF8String Diameter
3GPP-IMEISV 10415 20 UTF8String Diameter
3GPP-IMSI 10415 1 UTF8String Diameter
3GPP-MS-Timezone 10415 23 OCTETString Diameter
3GPP-NSAPI 10415 10 UTF8String Diameter
3GPP-PDP-Type 10415 3 Uint32 Diameter
3GPP-RAT-Type 10415 21 OCTETString Diameter
3GPP-Selection-Mode 10415 12 UTF8String Diameter
3GPP-SGSN-Address-Code-6 10415 6 Address Diameter
3GPP-SGSN-Address 10415 1228 Address Diameter
3GPP-SGSN-MCC-MNC 10415 18 UTF8String Diameter
3GPP-User-Location-Info 10415 22 OCTETString Diameter
WiMax-Active-Time 24757 39 Uint32 Diameter
WiMax-BSID 24757 46 UTF8String Diameter
SCE>
Example 2
The following example shows how to display a specific attribute.
SCE>enable 5
Password:<cisco>
SCE>show sub-attribute dictionary 3GPP-Charging-Gateway-Address
VSA name Vendor-ID Attr-ID Data Type Protocol Intrf
----------------------------------------------------------------------------------------
3GPP-Charging-Gateway-Address 10415 4 Address Diameter
SCE>
Related Commands
|
|
|
sub-attribute add-attribute |
Configures the capture of the specified attribute. |
show system operation-status
Displays the operating status of the system.
show system operation-status
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the system operating status:
SCE>enable 5 Password:<cisco> SCE>show system operation-status System Operation status is Operational SCE>
Related Commands
|
|
|
show system-uptime
Displays the length of time the system has been running since the last reboot.
show system-uptime
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the system uptime for the SCE platform:
SCE>enable 5 Password:<cisco> SCE>show system-uptime SCE uptime is 4 days, 13 hours, 21 minutes, 37 seconds SCE>
Related Commands
|
|
|
show tacacs
Displays statistics for the TACACS+ servers.
show tacacs [all]
Syntax Description
all |
Displays keys, timeouts, and other statistics. |
Defaults
None.
Command Modes
User EXEC
The all keyword is available only at the Privileged EXEC level.
Usage Guidelines
Note that, although most show commands are accessible to viewer-level users, the all keyword is available only at the admin authorization level. Use the enable 10 command to access the admin level.
Authorization: viewer
Examples
The following example shows how to display statistics for all TACACS+ servers:
SCE>enable 5 Password:<cisco> SCE>show tacacs Server: 100.10.10.10./49: opens=0 closes=0 error=0 messages in=0 messages out=0 SCE>
The following example shows how to display statistics, including keys and timeouts, for all TACACS+ servers:
SCE>enable 10 Password:<cisco> SCE# show tacacs all Server: 100.10.10.10./49: opens=0 closes=0 error=0 messages in=0 messages out=0 timeout=20 uses default timeout= yes key= a uses default key= no SCE#
Related Commands
show telnet sessions
Displays any active Telnet sessions.
show telnet sessions
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the currently active Telnet sessions (one):
SCE>enable 5 Password:<cisco> SCE>show telnet sessions There is 1 active telnet session: Index | Source ================ 0 | 10.1.1.201 SCE>
Related Commands
|
|
|
telnet |
Starts a Telnet session. |
show telnet status |
Displays the status of the Telnet server daemon. |
show telnet status
Displays the status of the Telnet server daemon.
show telnet status
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the current status of the Telnet daemon (enabled):
SCE>enable 5 Password:<cisco> SCE>show telnet status Telnet daemon is enabled. SCE>
Related Commands
|
|
|
service telnetd |
Enables the Telnet daemon. |
show telnet sessions |
Displays any active Telnet sessions. |
show timezone
Displays the current time zone and daylight saving time configuration as configured by the user.
show timezone
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the time zone configured by the user:
SCE>enable 5 Password:<cisco> SCE>show timezone Time zone: ISR minutes offset from UTC: 120 SCE>
Related Commands
|
|
|
clock timezone |
Sets the time zone. |
show users
Displays the users in the local database. The display includes passwords.
show users
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Note that, although most show commands are accessible to viewer-level users, this command is available only at the admin authorization level. To access the admin level, use the enable 10 command.
Authorization: admin
Examples
The following example shows how to display the users in the local database:
SCE>enable 10 Password:<cisco> SCE# show users User: name = Joe privilege level = 10 password = jasper is password encrypted = no SCE#
Related Commands
|
|
|
username |
Adds a new user to the local database. |
username privilege |
Sets the privilege level for the specified user. |
show version
Displays the configuration information for the system, including the hardware version, the software version, the application used, and other configuration information.
show version
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the current version information of the SCE platform:
SCE>enable 5 Password:<cisco> SCE>show version System version: Version 3.1.6S Build 279 Build time: Jun 10 2008, 19:27:47 (Change-list 335658) Software version is: Version 3.1.6S Build 279 Hardware information is: ---------------- Firmware ---------------- kernel : [kernel] 1.0.0/5 (inactive: [kernel] 1.0.0/5) u-boot : [uboot] 1.0.0/6 (field: [uboot] 0.8.1/13) select : [ubs-cf1] 1.0.0/5 (secondary: [ubs-cf1] 1.0.0/5) ---------------- Slot 1: SCM-8000 ---------------- serial-num : CAT1202G07D part-num : 73-10598-01 38 cpld : 0x8162 vtpld : 0xc001 summit-0 : 0x10008 summit-1 : 0x10008 dpt/tx : 0x4837 cls/ff : 0x2047 cls flow cap: 33554432 ---------------- TVR ---------------- #cpus : 1 cpu SVR : 0x80900120 cpu PVR : 0x80040202 cpu freq : 1000MHz cpu (eeprom): 2.1, 1000MHz cpld : 0xa1b7 cpld-ufm : 0xa803 summit : 0x10007 cf : Model=SMART CF, FwRev=0x20060811, Size=4062240KB ---------------- CFC-0 ---------------- board type : P2 #cpus : 3 cpu-0 SVR : 0x80900121 cpu-0 PVR : 0x80040202 cpu-0 freq : 1500MHz cpu-1 SVR : 0x80900121 cpu-1 PVR : 0x80040202 cpu-1 freq : 1500MHz cpu-2 SVR : 0x80900121 cpu-2 PVR : 0x80040202 cpu-2 freq : 1500MHz cpu (eeprom): 2.1, 1500MHz cpld-0 : 0xb20e cpld-1 : 0xb20e cpld-2 : 0xb20e cpld-0-ufm : 0xb803 cpld-1-ufm : 0xb803 cpld-2-ufm : 0xb803 summit-0 : 0x1000a summit-1 : 0x1000a fc : 0x1044 ---------------- CFC-1 ---------------- board type : P2 #cpus : 3 cpu-0 SVR : 0x80900121 cpu-0 PVR : 0x80040202 cpu-0 freq : 1500MHz cpu-1 SVR : 0x80900121 cpu-1 PVR : 0x80040202 cpu-1 freq : 1500MHz cpu-2 SVR : 0x80900121 cpu-2 PVR : 0x80040202 cpu-2 freq : 1500MHz cpu (eeprom): 2.1, 1500MHz cpld-0 : 0xb20e cpld-1 : 0xb20e cpld-2 : 0xb20e cpld-0-ufm : 0xb803 cpld-1-ufm : 0xb803 cpld-2-ufm : 0xb803 summit-0 : 0x1000a summit-1 : 0x1000a fc : 0x1044 ---------------- Slot 3: SIP-8000 ---------------- serial-num : CAT1204G01H part-num : 73-10947-01 cpld : 0x9162 summit-0 : 0x10006 summit-1 : 0x10006 dpt-0 : 0x3033 dpt-1 : 0x3033 spa[0] : SPA-1X10GE-L-V2 spa[1] : SPA-1XTENGE-XFP spa[2] : SPA-1X10GE-L-V2 spa[3] : SPA-1XTENGE-XFP ---------------- SCE8000 Chassis ---------------- product-num : CISCO7604 serial-num : FOX10420BKZ part-num : 73-9789-02 part-rev : A0 vid : V01
Part number: 73-10598-01 38 Revision: Software revision: LineCard S/N : CAT1202G07D Power Supply type: AC SML Application information is: No application is configured. Logger status: Enabled Platform: SCE8000 - 4x10GBE Management agent interface version: SCE Agent 3.1.6 Build 134 Software package file: ftp://ftpserver/simba.pkg SCE8000 uptime is 9 minutes, 54 seconds
SCE>
Related Commands
show version all
Displays complete version information as well as the running configuration for all components.
show version all
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display version and configuration information for all system components:
SCE>enable 5 Password:<cisco> SCE>show version all System version: Version 3.1.6S Build 279 Build time: Jun 10 2008, 19:27:47 (Change-list 335658) Software version is: Version 3.1.6S Build 279 Hardware information is: ---------------- Firmware ---------------- kernel : [kernel] 1.0.0/5 (inactive: [kernel] 1.0.0/5) u-boot : [uboot] 1.0.0/6 (field: [uboot] 0.8.1/13) select : [ubs-cf1] 1.0.0/5 (secondary: [ubs-cf1] 1.0.0/5) ---------------- Slot 1: SCM-8000 ---------------- serial-num : CAT1202G07D part-num : 73-10598-01 38 cpld : 0x8162 vtpld : 0xc001 summit-0 : 0x10008 summit-1 : 0x10008 dpt/tx : 0x4837 cls/ff : 0x2047 cls flow cap: 33554432 ---------------- TVR ---------------- #cpus : 1 cpu SVR : 0x80900120 cpu PVR : 0x80040202 cpu freq : 1000MHz cpu (eeprom): 2.1, 1000MHz cpld : 0xa1b7 cpld-ufm : 0xa803 summit : 0x10007 cf : Model=SMART CF, FwRev=0x20060811, Size=4062240KB ---------------- CFC-0 ---------------- board type : P2 #cpus : 3 cpu-0 SVR : 0x80900121 cpu-0 PVR : 0x80040202 cpu-0 freq : 1500MHz cpu-1 SVR : 0x80900121 cpu-1 PVR : 0x80040202 cpu-1 freq : 1500MHz cpu-2 SVR : 0x80900121 cpu-2 PVR : 0x80040202 cpu-2 freq : 1500MHz cpu (eeprom): 2.1, 1500MHz cpld-0 : 0xb20e cpld-1 : 0xb20e cpld-2 : 0xb20e cpld-0-ufm : 0xb803 cpld-1-ufm : 0xb803 cpld-2-ufm : 0xb803 summit-0 : 0x1000a summit-1 : 0x1000a fc : 0x1044 ---------------- CFC-1 ---------------- board type : P2 #cpus : 3 cpu-0 SVR : 0x80900121 cpu-0 PVR : 0x80040202 cpu-0 freq : 1500MHz cpu-1 SVR : 0x80900121 cpu-1 PVR : 0x80040202 cpu-1 freq : 1500MHz cpu-2 SVR : 0x80900121 cpu-2 PVR : 0x80040202 cpu-2 freq : 1500MHz cpu (eeprom): 2.1, 1500MHz cpld-0 : 0xb20e cpld-1 : 0xb20e cpld-2 : 0xb20e cpld-0-ufm : 0xb803 cpld-1-ufm : 0xb803 cpld-2-ufm : 0xb803 summit-0 : 0x1000a summit-1 : 0x1000a fc : 0x1044 ---------------- Slot 3: SIP-8000 ---------------- serial-num : CAT1204G01H part-num : 73-10947-01 cpld : 0x9162 summit-0 : 0x10006 summit-1 : 0x10006 dpt-0 : 0x3033 dpt-1 : 0x3033 spa[0] : SPA-1X10GE-L-V2 spa[1] : SPA-1XTENGE-XFP spa[2] : SPA-1X10GE-L-V2 spa[3] : SPA-1XTENGE-XFP ---------------- SCE8000 Chassis ---------------- product-num : CISCO7604 serial-num : FOX10420BKZ part-num : 73-9789-02 part-rev : A0 vid : V01
Part number: 73-10598-01 38 Revision: Software revision: LineCard S/N : CAT1202G07D Power Supply type: AC SML Application information is: No application is configured. Logger status: Enabled Platform: SCE8000 - 4x10GBE Management agent interface version: SCE Agent 3.1.6 Build 134 Software package file: ftp://ftpserver/simba.pkg SCE8000 uptime is 9 minutes, 54 seconds
====================== #This is a general configuration file (running-config). #Created on 10:14:59 UTC TUE November 12 2006 . interface LineCard 0 connection-mode active no silent . . Software package file: Not available Unified management package file: /system/images/um13012.pkg SCE>
Related Commands
|
|
|
show version |
Displays the configuration information for the system. |
show version software |
Displays version information for the current software. |
show version software
Displays version information for the current software.
show version software
Syntax Description
This command has no arguments or keywords.
Defaults
None.
Command Modes
User EXEC
Usage Guidelines
Authorization: viewer
Examples
The following example shows how to display the current software version:
SCE>enable 5 Password:<cisco> SCE>show version software Software version is: Version 3.0.5 Build 240 SCE>
Related Commands
|
|
|
show version |
Displays the configuration information for the system. |
show version all |
Displays complete version information as well as the running configuration for all components. |
silent
Disables the line card from reporting events.
To enable the line card to send reports, use the no form of this command.
silent
no silent
Syntax Description
This command has no arguments or keywords.
Defaults
Reporting events is disabled.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to change the line card state to silent:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#silent SCE(config if)#
Related Commands
|
|
|
show interface linecard silent |
Displays the current Linecard Interface silent state. |
snmp-server
Enables the SNMP agent. You can also use any of the other snmp-server commands to enable the SNMP agent.
To disable the SNMP agent from responding to SNMP managers, use the no form of this command. All SNMP settings are saved and then restored when the SNMP agent is reenabled.
snmp-server enable
no snmp-server
Syntax Description
enable |
Enables the SNMP agent. |
Defaults
The SNMP agent is disabled.
Command Modes
Global Configuration
Usage Guidelines
To allow SNMP access, you must define at least one community string.
Authorization: admin
Examples
The following example shows how to disable the SNMP server:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#no snmp-server SCE(config)#
Related Commands
|
|
|
snmp-server community |
Sets a community string. |
show snmp |
Displays the SNMP configuration and counters. |
snmp-server community
Sets a community string.
To remove a community string, use the no form of this command.
snmp-server community community-string [read-option acl]
no snmp-server community community-string [read-option acl]
no snmp-server community all
Syntax Description
Defaults
No SNMP access.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to configure an SNMP managers community that has read-only permissions for the SCE platform MIB. Only SNMP managers in access list 1 can access the SCE platform.
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#snmp-server community public ro 1 SCE(config)#
Related Commands
|
|
|
access-list |
Adds an entry to the bottom of the specified access list. |
show access-lists |
Displays all access lists or a specified access list. |
snmp-server contact
Sets the MIB-2 variable system contact.
To remove the contact setting, use the no form of this command.
snmp-server contact contact
no snmp-server contact
Syntax Description
contact |
Sring that identifies the system contact. |
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to configure the system contact:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#snmp-server contact Brenda@MyCompany.com
SCE(config)#
Related Commands
|
|
|
show snmp contact |
Displays the configured MIB-2 variable sysContact. |
snmp-server enable traps
Enables or disables SNMP traps. (Only authentication-failure traps and enterprise traps can be controlled using this command.)
To reset SNMP traps to the default status, use the default form of this command.
snmp-server enable traps [snmp [snmp-trap-name]] [enterprise [enterprise-trap-name]]
no snmp-server enable traps [snmp [snmp-trap-name]] [enterprise [enterprise-trap-name]]
default snmp-server enable traps [snmp [snmp-trap-name]] [enterprise [enterprise-trap-name]]
Syntax Description
Defaults
SNMP traps are disabled.
Enterprise traps are enabled.
Command Modes
Global Configuration
Usage Guidelines
The following classes of SNMP traps are controlled by this command:
•![]() SNMP traps
SNMP traps
•![]() Enterprise traps
Enterprise traps
The snmp and enterprise keywords specify the class of traps that are to be enabled or disabled by this command. Each class, or type, is composed of specific traps. Use these keywords as follows:
•![]() To enable or disable all traps of one type—Specify only snmp or enterprise.
To enable or disable all traps of one type—Specify only snmp or enterprise.
•![]() To enable or disable only one specific trap—Specify snmp or enterprise with the trap-name argument naming the trap.
To enable or disable only one specific trap—Specify snmp or enterprise with the trap-name argument naming the trap.
•![]() To enable or disable all traps—Do not specify either snmp or enterprise.
To enable or disable all traps—Do not specify either snmp or enterprise.
Because currently only the SNMP type of trap is the authentication trap, the snmp and authentication keywords are redundant.
Authorization: admin
Examples
The following example shows how to configure the SNMP server to send traps:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#snmp-server enable traps SCE(config)#
Related Commands
|
|
|
show snmp traps |
Displays the status of SNMP trap generation. |
snmp-server host
Sets destination hosts for SNMP traps.
snmp-server host address [traps] [version version] community-string
no snmp-server host address [traps] [version version] community-string
no snmp-server host all
Syntax Description
Defaults
SNMP traps do not have destination hosts.
Command Modes
Global Configuration
Usage Guidelines
If no communities are specified by the snmp-server community command, the community string specified by this command is used by the SCE platform, as if an snmp-server community community-string ro command was given.
Use the all keyword
Authorization: admin
Examples
The following example shows how to add a host destination for SNMP traps:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#snmp-server host 10.1.1.205 version 2c public
SCE(config)#
Related Commands
|
|
|
show snmp host |
Displays the destination hosts for SNMP traps. |
snmp-server interface
Defines a specific SNMP server interface.
To remove the interface definition, use the no form of this command.
snmp-server interface interface-number {alias alias | link-up-down-trap}
no snmp-server interface interface-number
Syntax Description
interface-number |
Number of the SNMP server interface. |
alias |
Logical name assigned to the interface. |
link-up-down-trap |
Enables the link up or down trap for the specified interface. |
Defaults
No SNMP server interface is defined.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to define an alias for the specified interface:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#snmp-server interface 4 alias snmp-server1
SCE(config)#
The following example shows how to enable the link up or down trap for the specified interface:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#snmp-server interface 4 link-up-down-trap SCE(config)#
Related Commands
|
|
|
snmp-server location
Assigns a name to the SCE platform location and sets the MIB-2 variable sysLocation.
To remove the location setting, use the no form of this command.
snmp-server location location
no snmp-server location
Syntax Description
location |
String that specifies the system location. |
Defaults
No location is defined.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to configure the system location:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#snmp-server location London_Office SCE(config)#
Related Commands
|
|
|
show snmp location |
Displays the configured MIB-2 variable sysLocation. |
sntp broadcast client
Enables the SNTP multicast client to accept SNTP broadcasts from any SNTP server.
To disable the SNTP multicast client, use the no form of this command.
sntp broadcast client
no sntp broadcast client
Syntax Description
This command has no arguments or keywords.
Defaults
The SNTP multicast client is disabled.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to enable the SNTP multicast client:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#sntp broadcast client SCE(config)#
Related Commands
sntp server
Enables the SNTP unicast client to query the specified SNTP server.
To disable the SNTP unicast server, use the no form of this command.
sntp server {address | hostname}
no sntp server hostname
no sntp server all
Syntax Description
address |
IP address of the SNTP server. |
hostname |
Hostname of the SNTP server. |
all |
Used with the no form of this command, disables all SNTP unicast servers. |
Defaults
The SNTP unicast server is disabled.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to enable an SNTP server at a specified IP address:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#sntp server 128.182.58.100 SCE(config)#
Related Commands
sntp update-interval
Defines the interval (in seconds) between SNTP unicast update queries.
sntp update-interval [interval]
Syntax Description
interval |
Length of the interval, in seconds. |
Defaults
The default interval is 64 seconds.
Command Modes
Global Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to set the SNTP update interval to 100 seconds:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#sntp update-interval 100 SCE(config)#
Related Commands
speed
Configures the speed of the management interface to either 10 Mbps, 100 Mbps, or 1000 Mbps. The auto option specifies auto-negotiation (do not force speed on the link).
speed [speed]
no speed
Syntax Description
speed |
Speed in Mbps or auto-negotiation. Can be set to 10, 100, 1000, or auto. |
Defaults
The default speed is auto.
Command Modes
GigabitEthernet Interface Configuration
Usage Guidelines
Use this command to configure the speed of the GigabitEthernet management interface.
If the duplex mode of the interface is configured to auto (see the duplex command), changing this configuration has no effect.
Authorization: admin
Examples
The following example shows how to configure the speed of the management port to auto. The designation for the interface is 1/1.
SCE2000>enable 10 Password:<cisco> SCE#config SCE(config)#interface GigabitEthernet 1/1 SCE(config if)#speed auto SCE2(config if)#
Related Commands
sub-attribute add-attribute
Configures the capture of the specified attribute. The attribute will be captured by the SCE platform to be reported to the billing server. Table 2-11 lists the supported VSAs.
To stop capturing the specified attribute and remove the entry from the attribute table, use the no form of the command. This also remove entries for the specified attribute from the subscriber database.
To stop capturing all VSA attributes and clear both the attribute table and the subscriber database, use the no...all form of the command.
sub-attribute add-attribute attribute-name
no sub-attribute add-attribute attribute-name
no sub-attribute add-attribute all
Syntax Description
attribute-name |
The PS information AVP to be mapped to the realm. |
Defaults
None
Command Modes
Global Configuration
Usage Guidelines
Up to 20 subscriber attributes can be captured, but each attribute must be configured in a separate command. The list of attributes to capture can be modified while the system is running.
The standard attribute name is used. To ensure the attribute name is entered correctly, the name is selected from multiple options with auto completion (not free text).

Note ![]() By default, the SCE platform converts the 3GPP-SGSN-Address-Code-6 VSA sent by Gx to 3GPP-SGSN-Address . Therefore, when using the SGSN Address, both these attributes should be selected. The same behavior applies to the GGSN address VSA pair (3GPP-GGSN-Address-Code-7 and 3GPP-GGSN-Address).
By default, the SCE platform converts the 3GPP-SGSN-Address-Code-6 VSA sent by Gx to 3GPP-SGSN-Address . Therefore, when using the SGSN Address, both these attributes should be selected. The same behavior applies to the GGSN address VSA pair (3GPP-GGSN-Address-Code-7 and 3GPP-GGSN-Address).
Authorization: admin
The following example shows how to use this command. The show sub-attribute configuration command is then executed to verify that the attribute is configured to be captured.
SCE>enable 10
Password:<cisco>
SCE# configure
SCE(config)#sub-attribute add-attribute 3GPP-Charging-Characteristics
SCE(config)#do show sub-attribute configuration
VSA name Vendor-ID Attr-ID Data Type Protocol Interfaces
-----------------------------------------------------------------------------------------
3GPP-Charging-Characteristics 10415 13 UTF8String Diameter Gx
SCE(config)#
Related Commands
subscriber aging
Enables or disables subscriber aging for the specified type of subscribers (anonymous or introduced). The aging period may also be defined when aging is enabled.
subscriber aging {anonymous | introduced} [timeout aging-time]
no subscriber aging {anonymous | introduced}
Syntax Description
aging-time |
Length of the aging period, in minutes. |
anonymous |
Anonymous subscribers. |
introduced |
Introduced subscribers. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
The most common usage for aging is for anonymous subscribers. Aging ensures that anonymous subscribers who have logged out of the network are removed from the SCE platform and are no longer occupying resources.
The aging time can be configured individually for introduced subscribers and for anonymous subscribers.
Authorization: admin
Examples
The following example shows how to enable subscriber aging for anonymous subscribers with a timeout period of 10 minutes:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#interface linecard 0
SCE(config if)#subscriber aging anonymous timeout 10
SCE(config if)#
Related Commands
|
|
|
show interface linecard subscriber aging |
Displays the subscriber aging configuration for the specified type of subscriber. |
subscriber anonymous-group export csv-file
Exports anonymous groups to the specified CSV file.
subscriber anonymous-group export csv-file filename
Syntax Description
filename |
Name of the CSV file to which the anonymous group information is to be exported. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to export anonymous group information to the specified file:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)# subscriber anonymous-group export csv-file s_g_0507.csv SCE(config if)#
Related Commands
|
|
|
subscriber anonymous-group import csv-file |
Creates anonymous groups by importing anonymous subscribers from the specifed CSV file. |
subscriber anonymous-group import csv-file
Creates anonymous groups by importing anonymous subscribers from the specified CSV file.
subscriber anonymous-group import csv-file filename
Syntax Description
filename |
Name of the CSV file containing the anonymous group information. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Anonymous Group CSV files have a fixed format. All lines have the following structure:
Anonymous-group-name, IP-range [, subscriber-template-number].
If no subscriber template number is specified, then the anonymous subscribers of that group will use the default template (0), which cannot be changed by template import operations.
The following example shows an anonymous group CSV file:
group1, 10.1.0.0/16, 2 group2, 176.23.34.0/24, 3 group3, 10.2.0.0/16
Authorization: admin
Examples
The following example shows how to import subscribers from the file subscribers_groups.csv:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)# subscriber anonymous-group import csv-file subscribers_groups.csv SCE(config if)#
Related Commands
|
|
|
subscriber anonymous-group export csv-file |
Exports anonymous groups to the specifed CSV file. |
subscriber anonymous-group name ip-range
Assigns the anonymous group to the specified range of IP addresses and optional template or to an SCMP device.
To delete the anonymous group or remove it from the specified SCMP destination, use the no form of this command.
subscriber anonymous-group name group-name ip-range range [template template]
subscriber anonymous-group name group-name ip-range range scmp name scmp-name
no subscriber anonymous-group {name group-name [scmp] | all}
Syntax Description
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
An anonymous subscriber group is a specified IP range, where each IP address in the given range is treated as a separate subscriber. You can assign a subscriber template to the group so that all subscribers in the group have properties as defined by that template.
This command defines the IP range of the specified anonymous group and optionally defines a subscriber template to be assigned to all subscribers within that IP range.
Anonymous groups can have overlapping IP ranges. When the SCE platform detects traffic for an IP address which is contained in more than one anonymous group, the group with the longest prefix is used to create the anonymous subscriber for that IP address.
Use the scmp option to assign the anonymous group to the specified SCMP destination. In this case, the specified anonymous group is the IP range managed by the SCMP peer device and subscribers for this anonymous group are generated when subscriber traffic from the SCMP peer device is detected. If a subscriber template has been assigned to the group, the anonymous subscribers generated have properties as defined by that template. If no subscriber template has been assigned, the default template is used.
You must define the specified SCMP peer device before assigning the anonymous group (see scmp name).
The no form of the command has three options:
•![]() Delete the specified anonymous subscriber group definition: no subscriber anonymous-group name group-name
Delete the specified anonymous subscriber group definition: no subscriber anonymous-group name group-name
•![]() Remove the specified anonymous subscriber group from the specified SCMP destination: no subscriber anonymous-group name group-name scmp
Remove the specified anonymous subscriber group from the specified SCMP destination: no subscriber anonymous-group name group-name scmp
•![]() Delete all anonymous subscriber group definitions: no subscriber anonymous-group all
Delete all anonymous subscriber group definitions: no subscriber anonymous-group all
Authorization: admin
Examples
The following example shows how to assign an anonymous group to an IP range and also assign a template:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#subscriber anonymous-group name anon_group IP-range 10.10.10.0/8 template 2 SCE(config if)#
The following example shows how to assign an anonymous group to an SCMP device:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#scmp name peer_device1 radius radius1 secret abcdef
SCE(config)#interface linecard 0 SCE(config if)#subscriber anonymous-group name anon_group IP-range 10.10.10.0/8 scmp name peer_device1 SCE(config if)#
The following example shows how to remove an anonymous group from an SCMP device:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#interface linecard 0
SCE(config if)#no subscriber anonymous-group name anon_group scmp
SCE(config if)#
The following example shows how to remove all currently defined anonymous groups:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#no subscriber anonymous-group all SCE(config if)#
Related Commands
|
|
|
subscriber capacity-options
To override the capacity option when loading the SCA BB application, use the disable form of this command.
To reenable the capacity option, use the enable form of this command.
subscriber capacity-options {enable | disable}
Syntax Description
This command has no arguments or keywords.
Defaults
The capacity option is enabled.
Command Modes
Linecard Interface Configuration
Usage Guidelines
You must first define the maximum number of subscribers using the subscriber max-subscribers command.
You must override the capacity option before installing the pqi file.
If you have disabled the capacity option but want to use it the next time you load a new application, you must reenable the option before you load the application file.
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#subscriber max-subscribers 500K
SCE(config if)#subscriber capacity-options disable SCE(config if)#pqi install file mov2008.pqi
Related Commands
|
|
|
subscriber max-subscribers |
Specifies the maximum number of subscribers. |
show interface linecard subscriber max-subscribers |
Displays the maximum number of subscribers. |
subscriber export csv-file
Exports subscribers to the specified CSV file.
subscriber export csv-file filename
Syntax Description
filename |
Name of the CSV file to which the subscriber information is to be exported. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Subscriber CSV files are application-specific. Refer to the relevant application documentation for the definition of the file format.
Only subscribers managed by CLI commands are exported:
•![]() Subscribers that were introduced dynamically by the SM, SCE subscriber API, or SCMP integration are not exported.
Subscribers that were introduced dynamically by the SM, SCE subscriber API, or SCMP integration are not exported.
•![]() Subscribers imported by the subscriber import CLI command are exported.
Subscribers imported by the subscriber import CLI command are exported.
To export subscribers managed by the SM, the SM GUI, or CLU should be used. (See the Cisco Service Control Management Suite Subscriber Manager User Guide.)
Authorization: admin
Examples
The following example shows how to export subscribers to the specified file:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)# subscriber export csv-file gold_subscribers_04072003.csv SCE(config if)#
Related Commands
|
|
|
subscriber import csv-file |
Imports subscribers from the specified CSV file. |
subscriber import csv-file
Imports subscribers from the specified CSV file.
subscriber import csv-file filename
Syntax Description
filename |
Name of the CSV file containing the subscriber information. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Subscriber CSV files are application-specific. Refer to the relevant application documentation for the definition of the file format.
A maximum of 80,000 static subscribers can be imported for each import operation. To import more than this limit, divide the subscribers into several CSV files and import each file separately.
Authorization: admin
Examples
The following example shows how to import subscribers from the file gold_subscribers.csv:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)# subscriber import csv-file gold_subscribers.csv SCE(config if)#
Related Commands
|
|
|
subscriber export csv-file |
Exports subscribers to the specified CSV file. |
subscriber max-subscribers
Specifies the maximum number of subscribers.
subscriber max-subscribers [subscriber-number]
Syntax Description
subscriber-number |
Maximum number of subscribers. Choose either 100K, 250K, 500K, or 1M. |
Defaults
The default number of subscribers is 250,000 (250K).
Command Modes
Linecard Interface Configuration
Usage Guidelines
For this maximum number to take effect, you must also:
1. ![]() Disable the capacity option (see subscriber capacity-options).
Disable the capacity option (see subscriber capacity-options).
2. ![]() Load a new application (see pqi install).
Load a new application (see pqi install).
Authorization: admin
Examples
The following example shows how to use this command:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#subscriber max-subscribers 500K
SCE(config if)#subscriber capacity-options disable SCE(config if)#pqi install file mov2008.pqi
Related Commands
subscriber name property name
Assigns a value to the specified property of the specified subscriber.
subscriber name subs-name property name property-name value property-val
Syntax Description
subs-name |
Name of the subscriber. |
property-name |
Subscriber property for which the value is to be assigned. |
property-val |
Value to be assigned. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
This command can be used to enable or disable the generation of the real-time subscriber usage RDRs (see the example).
•![]() To enable RDR generation, set property-name to monitor and property-val to 1.
To enable RDR generation, set property-name to monitor and property-val to 1.
•![]() To disable RDR generation, set property-name to monitor and property-val to 0.
To disable RDR generation, set property-name to monitor and property-val to 0.
•![]() To enable subscriber monitoring for a group of subscribers, create a text file containing the sequence of CLI commands, including the commands to access the appropriate CLI mode. The file might look like this:
To enable subscriber monitoring for a group of subscribers, create a text file containing the sequence of CLI commands, including the commands to access the appropriate CLI mode. The file might look like this:
configure
interface linecard 0
subscriber name Jerry property name monitor value 1
subscriber name George property name monitor value 1
subscriber name Elaine property name monitor value 1
subscriber name Kramer property name monitor value 1
subscriber name Newman property name monitor value 1
Use the script run command to run the script.
Authorization: admin
Examples
The following example shows how to disable the generation of the real-time subscriber usage RDRs for subscriber jane_smith:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#subscriber name jane_smith property name monitor value 0 SCE(config if)#
Related Commands
|
|
|
show interface linecard subscriber name |
Displays information about a specified subscriber. |
subscriber sm-connection-failure
Configures the behavior of the system if communication fails between the SM and the SCE platform.
subscriber sm-connection-failure {warning | action {force-failure | none | remove-mappings | shut}}
subscriber sm-connection-failure timeout timeout
default subscriber sm-connection-failure
Syntax Description
Defaults
The default action is none.
Command Modes
Linecard Interface Configuration
Usage Guidelines
If SM functionality is not critical to the operation of the system, no action needs to be configured.
If SM functionality is critical to the operation of the system, configure forced failure of the SCE platform in the event of any loss of connection with the SM.
If no action is required, you may want to configure the system operational status to be set to "warning" when communication is lost. Use the warning keyword for this option.
Authorization: admin
Examples
The following example shows how to configure forced failure of the SCE platform if the SM fails:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE (config if)#subscriber sm-connection-failure action force-failure SCE (config if)#
The following example shows how to set the timeout interval to 2 minutes (120 seconds):
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE (config if)#subscriber sm-connection-failure timeout 120 SCE (config if)#
Related Commands
subscriber template export csv-file
Exports a subscriber template to the specified CSV file, according to the party template.
subscriber template export csv-file filename
Syntax Description
filename |
Name of the CSV file to which the subscriber template is to be exported. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to export the subscriber template to the specified file:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)# subscriber template export csv-file gold0507.csv SCE(config if)#
Related Commands
|
|
|
subscriber template import csv-file |
Imports a subscriber template from the specified CSV file, creating a party template. |
subscriber template import csv-file
Imports a subscriber template from the specified CSV file. Importing the template creates a party template.
subscriber template import csv-file filename
Syntax Description
filename |
Name of the CSV file containing the subscriber template. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to import the subscriber template from the file gold0507.csv:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)# subscriber template import csv-file gold0507.csv SCE(config if)#
Related Commands
|
|
|
subscriber template export csv-file |
Exports a subscriber template to the specified CSV file, according to the party template. |
tacacs-server host
Defines a new TACACS+ server host that is available to the SCE platform TACACS+ client. The Service Control solution supports a maximum of three TACACS+ server hosts.
To remove a TACACS+ server host, use the no form of this command.
tacacs-server host hostname [port [port-number]] [timeout [timeout-interval]] [key [key-string]]
no tacacs-server host hostname
Syntax Description
Defaults
The default port number is 49.
The default timeout interval is either 5 seconds or the user-configured global default timeout interval.
The default encryption key is either no key or the user-configured global default key.
Command Modes
Global Configuration
Usage Guidelines
You can configure a global default timeout interval that applies as the timeout to all TACACS+ server hosts. The timeout interval does not need to be configured explicitly for each server. (See tacacs-server timeout.)
Similarly, you can configure a global default key that applies to all TACACS+ server hosts. (See tacacs-server key.)
If the global default timeout interval and key string are configured, an explicitly configured value for a specific TACAS+ server overrides the global default for that server.
Authorization: admin
Examples
The following example shows how to configure a TACACS+ server host using the default port and no key:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#tacacs-server host server1 timeout 8
SCE(config)#
Related Commands
tacacs-server key
Defines the global default encryption key for the TACACS+ server hosts.
To clear the TACACS+ key, use the no form of this command.
tacacs-server key key-string
no tacacs-server key
Syntax Description
key-string |
Default encryption key that all TACACS servers and clients will use when communicating with each other. The specified key must be configured on the TACACS+ server hosts. |
Defaults
The default is no encryption.
Command Modes
Global Configuration
Usage Guidelines
This default key can be overridden for a specific TACACS+ server host by explicitly configuring a different key for that TACACS+ server host.
If no global default key is defined, each TACACS+ server host may still have a specific key defined. However, any server host that does not have a specific key defined (uses the global default key) is now configured to not use a key.
Authorization: admin
Examples
The following example shows how to configure the key string:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#tacacs-server key ABCDE SCE(config)#
Related Commands
tacacs-server timeout
Defines the global default timeout interval for the TACACS+ server hosts.
To clear the global default timeout interval, use the no form of this command.
tacacs-server timeout [interval]
no tacacs-server timeout
Syntax Description
interval |
Default time, in seconds, that the server waits for a reply from the server host before timing out. |
Defaults
The default interval is 5 seconds.
Command Modes
Global Configuration
Usage Guidelines
This default timeout interval can be overridden for a specific TACACS+ server host by explicitly configuring a different timeout interval for that TACACS+ server host.
If no global default timeout interval is defined, each TACACS+ server host may still have a specific timeout interval defined. However, any server host that does not have a timeout interval explicitly defined (uses the global default timeout interval) is now configured to a 5-second timeout interval.
Authorization: admin
Examples
The following example shows how to configure a default timeout interval of 10 seconds:
SCE>enable 10 Password:<cisco> SCE#config SCE>(config)#tacacs-server timeout 10 SCE(config)#
Related Commands
telnet
Starts a Telnet session.
telnet address [port-number]
Syntax Description
address |
Telnet access address. |
port-number |
Optional port number. |
Defaults
The default port number is 23.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to start a Telnet session:
SCE>enable 10 Password:<cisco> SCE#telnet 10.1.5.120 connecting to 10.1.5.120:23...
Related Commands
|
|
|
show telnet sessions |
Displays any active Telnet sessions. |
service telnetd |
Enables the Telnet daemon. |
timeout
Configures the timeout for the Telnet session when the Telnet session is idle. After this time, the Telnet session is disconnected.
To configure the Telnet server to work without a timeout, use the no form of this command. The system will not automatically disconnect the Telnet session, regardless of how long the session has been inactive.
timeout [time]
no timeout
Syntax Description
time |
Timeout length, in minutes. |
Defaults
The default timeout is 30 minutes.
Command Modes
Line Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to set the timeout to 45 minutes:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#line vty 0 SCE(config-line)#timeout 45 SCE(config-line)#
Related Commands
|
|
|
telnet |
Starts a Telnet session. |
tracert
Determines the route that packets take to reach a specified host.
tracert {hostname | ip-address}
Syntax Description
hostname |
Destination hostname. |
ip-address |
Destination IP address. |
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
The destination of the traceroute function can be specified as either a known hostname or an IP address.
Authorization: admin
Examples
The following example shows output from this command:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#tracert 64.103.125.118 traceroute to 10.56.217.103, 30 hops max, 40 byte packets 1 10.56.217.1 ( 10.56.217.1) 0 ms 1 ms 0 ms 2 10.56.223.9 ( 10.56.223.9) 1 ms 0 ms 1 ms 3 64.103.115.209 ( 64.103.115.209) 0 ms 1 ms 0 ms 4 64.103.125.118 ( 64.103.125.118) 0 ms 0 ms 0 ms Trace complete. SCE(config if)#
Related Commands
|
|
|
show ip route |
Displays the entire routing table and the destination of last resort (default gateway). |
traffic-counter
Defines a new traffic counter.
To delete an existing traffic counter, use the no form of this command.
traffic-counter name name {count-bytes | count-packets}
no traffic-counter {name name | all}
Syntax Description
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to create a traffic counter that counts bytes:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#traffic-counter name counter1 count-bytes SCE(config if)#
The following example shows how to delete all traffic counters:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#no traffic-counter all SCE(config if)#
Related Commands
|
|
|
show interface linecard traffic-counter |
Displays the specified traffic counter. |
clear interface linecard traffic-counter |
Clears the specified traffic counter. |
traffic-rule
Defines a new traffic rule.
To delete an existing traffic rule, use the no form of this command. To delete all existing traffic rules, use the all keyword with the no form of the command.
traffic-rule name name ip addresses ip-addresses protocol protocol [port port-id] [tunnel-id tunnel-id] direction direction traffic-counter name traffic-counter action action
traffic-rule tunnel-id-mode
no traffic-rule {name name | all | tunnel-id-mode}
no traffic-rule capture
Syntax Description
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
The following usage guidelines apply to the traffic-rule command.
IP specification
all | ([all-but] (ip-address | ip-range))
•![]() ip-address is a single IP address in dotted-decimal notation (such as 10.1.2.3).
ip-address is a single IP address in dotted-decimal notation (such as 10.1.2.3).
•![]() ip-range is an IP subnet range, in dotted-decimal notation followed by the number of significant bits (such as 10.1.2.0/24).
ip-range is an IP subnet range, in dotted-decimal notation followed by the number of significant bits (such as 10.1.2.0/24).
Port specification
all | ([all-but] [port-number] [port-range])
•![]() Specify the port or port range for both the subscriber side and the network side.
Specify the port or port range for both the subscriber side and the network side.
•![]() Specify a range of ports using the format minport:maxport.
Specify a range of ports using the format minport:maxport.
•![]() Specify ports only if the protocol is either TCP or UDP.
Specify ports only if the protocol is either TCP or UDP.
Tunnel ID specification
all | ([all-but] tunnel-id) '
•![]() tunnel-id is a hexadecimal tunnel-ID range, in the format '(HEX)tunnel-id' or '(HEX)min-tunnel-id:(HEX)max-tunnel-id
tunnel-id is a hexadecimal tunnel-ID range, in the format '(HEX)tunnel-id' or '(HEX)min-tunnel-id:(HEX)max-tunnel-id
To enable or disable defining the traffic rule according to the tunnel ID, use the tunnel-id-mode keyword.
Traffic counter name
Specify either:
•![]() Name of an existing traffic counter—Packets meeting the criteria of the rule are to be counted in the specified counter.
Name of an existing traffic counter—Packets meeting the criteria of the rule are to be counted in the specified counter.
If a counter name is defined, the "count" action is also defined implicitly.
•![]() none—An action must be explicitly defined with the action keyword.
none—An action must be explicitly defined with the action keyword.
Action
Specify one of the following options:
•![]() block—Blocks the specified traffic.
block—Blocks the specified traffic.
•![]() ignore—Bypasses the specified traffic. The traffic receives no service.
ignore—Bypasses the specified traffic. The traffic receives no service.
•![]() quick-forwarding—Quick forwards (duplicates) delay-sensitive packets with service.
quick-forwarding—Quick forwards (duplicates) delay-sensitive packets with service.
•![]() quick-forwarding-ignore—Quick forwards (duplicates) delay-sensitive packets with no service.
quick-forwarding-ignore—Quick forwards (duplicates) delay-sensitive packets with no service.
•![]() Flow-capture—Captures the flow matching the configured rule. This flow receives no service.
Flow-capture—Captures the flow matching the configured rule. This flow receives no service.
Use the no traffic-rule capture command to delete all current flow-capture rules.
Authorization: admin
Examples
The following examples show how to use this command.
Example 1
The following example shows how to create a traffic rule called rule2:
•![]() Name = rule2
Name = rule2
•![]() IP addresses: subscriber side = all IP addresses, network side = all IP addresses except the subnet address 10.10.10.0/24
IP addresses: subscriber side = all IP addresses, network side = all IP addresses except the subnet address 10.10.10.0/24
•![]() Protocol = TCP
Protocol = TCP
•![]() subscriber-side port = 100
subscriber-side port = 100
•![]() network-side ports = all-but 200
network-side ports = all-but 200
•![]() Direction = downstream
Direction = downstream
•![]() Traffic counter = counter2
Traffic counter = counter2
•![]() Action = block
Action = block
The actions performed will be counting and blocking.
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)# traffic-rule name rule2 ip-addresses subscriber-side all network-side all-but 10.10.10.0/24 protocol tcp ports subscriber-side 100 network-side all-but 200 direction downstream traffic-counter name counter2 action block SCE(config if)
Example 2
The following example shows how to create a traffic rule called rule3:
•![]() Name = rule3
Name = rule3
•![]() IP addresses: all
IP addresses: all
•![]() Protocol = IS-IS
Protocol = IS-IS
•![]() Direction = upstream
Direction = upstream
•![]() Traffic counter = none
Traffic counter = none
•![]() Action = ignore (required because traffic-counter = none)
Action = ignore (required because traffic-counter = none)
The only action performed will be ignore.
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)# traffic-rule name rule3 ip-addresses all protocol is-is direction upstream traffic-counter name none action ignore SCE(config if)
Example 3
The following example shows how to delete all traffic rules:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)# no traffic-rule all SCE(config if)
Example 4
The following example shows how to configure a traffic rule that will be used as a recording rule using the flow-capture option. All flows that match this rule will be recorded when the flow-capture process is in operation.
•![]() Name = FlowCaptureRule
Name = FlowCaptureRule
•![]() IP addresses: subscriber side = all IP addresses, network side = all IP addresses
IP addresses: subscriber side = all IP addresses, network side = all IP addresses
•![]() Direction = both
Direction = both
•![]() Protocol = 250
Protocol = 250
•![]() Traffic counter name = counter2
Traffic counter name = counter2
•![]() Action = flow-capture
Action = flow-capture
The actions performed will be counting and flow capture.
SCE>enable 10 Password:<cisco> SCE#configure SCE(config)#interface linecard 0 SCE(config if)#traffic-rule name FlowCaptureRule ip-addresses subscriber-side all network-side all protocol 250 direction both traffic-counter name counter2 action flow-capture SCE(config if)#
Related Commands
|
|
|
show interface linecard traffic-rule |
Displays the specified traffic rule configuration. |
traffic-side (SCE8000 10G platform only)
Changes the traffic direction on Link 1 of the SCE8000 10G platform.

Note ![]() This command is supported only on10 Gigabit Ethernet line interfaces 3/2/0 and 3/3/0. It is not supported on interfaces 3/0/0 and 3/1/0.
This command is supported only on10 Gigabit Ethernet line interfaces 3/2/0 and 3/3/0. It is not supported on interfaces 3/0/0 and 3/1/0.
Use the default form of the command to reset the interface to the default traffic direction.
traffic-side (subscriber | network)
default traffic-side
Syntax Description
subscriber |
Configure the interface to process subscriber traffic. |
network |
Configure the interface to process network traffic. |
Defaults
•![]() 3/2/0: subscriber
3/2/0: subscriber
•![]() 3/3/0: network
3/3/0: network
Command Modes
TenGigabitEthernet Interface Configuration
Usage Guidelines
The hardware design of the SCE8000 10G platform is such that the traffic coming in and out of SPAs 0 and 2 is limited to a total of 16Gbps in each direction, as is the traffic coming in and out of SPAs 1 and 3. Since by default, in 10GBE installations, SPAs 0 and 2 are subscriber-side ports, and SPAs 1 and 3 are network-side ports, this effectively limits total traffic in each direction (upstream and downstream) to 16Gbps. Therefore, a site that has a total of more than 16Gbps of traffic in one direction (upstream or downstream), will exceed this limit and suffer packet loss.
You can use this command to swap the roles of the ports on link 1, which will switch part of the high-volume traffic to the opposite pair of SPAs and prevent either pair of SPAs from exceeding the 16Gbps limit.
Limitations
•![]() This command is supported only Link 1 (3/2/0 and 3/3/0). It is not supported on Link 0.
This command is supported only Link 1 (3/2/0 and 3/3/0). It is not supported on Link 0.
Only one interface on the link is explicitly configured. The corresponding interface is automatically set to the opposite traffic side.
•![]() The connection mode must be either inline or receive-only. This command is not supported for cascade modes.
The connection mode must be either inline or receive-only. This command is not supported for cascade modes.
•![]() This command can only be executed when no application is loaded, or in shutdown mode.
This command can only be executed when no application is loaded, or in shutdown mode.
Authorization: admin
Examples
Example 1
The following example illustrates how to reverse the traffic direction on link 1 on the SCE8000 10G platform.
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#interface TenGigabitEthernet 3/2/0
SCE(config if)#traffic-side network
SCE(config if)#
Example 2
The following example illustrates how to reset the traffic direction to the default.
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#interface TenGigabitEthernet 3/2/0
SCE(config if)#default traffic-side
SCE(config if)#
Related Commands
|
|
|
|---|---|
show interface TenGigabitEthernet |
unzip
Extracts a zip file to the current directory.
unzip filename
Syntax Description
filename |
Zip file to be extracted. |
Defaults
None.
Command Modes
Privileged EXEC
Usage Guidelines
Authorization: admin
Examples
The following example shows how to extract the file zipfile.zip:
SCE>enable 10 Password:cisco> SCE#unzip zipfile.zip Unzipping '/system/zipfile.zip'... Zip file has 3 entries: 1.sli, 13429 bytes extracted preflut.sli, 12558 bytes extracted temp/SLI/x/IpraeLut.sli, 12929 bytes extracted Finished, Extracted 3 files.
Related Commands
|
|
|
username
Adds a new user to the local database.
To remove a user from the database, use the no form of this command.
username name {password password | nopassword | secret {0 password | 5 password }}
no username name
Syntax Description
Defaults
None.
Command Modes
Global Configuration
Usage Guidelines
Up to 100 users may be defined.
The password is defined with the username. You can use the following password options:
•![]() No password—Use the nopassword keyword.
No password—Use the nopassword keyword.
•![]() Password—Password is saved in clear-text format in the local list. Use the password keyword.
Password—Password is saved in clear-text format in the local list. Use the password keyword.
•![]() Encrypted password—Password is saved in encrypted (MD5) form in the local list. Use the secret keyword and either of the following options:
Encrypted password—Password is saved in encrypted (MD5) form in the local list. Use the secret keyword and either of the following options:
–![]() Specify a clear-text password (0), which is saved in MD5 encrypted form.
Specify a clear-text password (0), which is saved in MD5 encrypted form.
–![]() Specify an MD5 encryption string (5), which is saved as the user MD5-encrypted secret password.
Specify an MD5 encryption string (5), which is saved as the user MD5-encrypted secret password.
The following keywords are available:
•![]() nopassword—No password is associated with this user.
nopassword—No password is associated with this user.
•![]() secret—The password is saved in MD5 encrypted form. Use with either of the following keywords to indicate the format of the password as entered in the command:
secret—The password is saved in MD5 encrypted form. Use with either of the following keywords to indicate the format of the password as entered in the command:
–![]() 0 specifies a clear-text password that will be saved in MD5 encrypted form.
0 specifies a clear-text password that will be saved in MD5 encrypted form.
–![]() 5 specifies an MD5 encryption string that will be saved as the user MD5-encrypted secret password.
5 specifies an MD5 encryption string that will be saved as the user MD5-encrypted secret password.
Authorization: admin
Examples
The following example shows how to add a new user to the local database with a clear-text password:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#username johndoe password mypassword
SCE(config)#
The following example shows how to add a new user to the local database with no password:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#username johndoe nopassword
SCE(config)#
The following example shows how to add a new user to the local database with an MD5 encrypted password entered in clear text:
SCE>enable 10
Password:<cisco>
SCE#config
SCE(config)#username johndoe secret 0 mypassword
SCE(config)#
Related Commands
|
|
|
show users |
Displays the users in the local database. |
username privilege |
Sets the privilege level for the specified user. |
username privilege
Sets the privilege level for the specified user.
username name privilege [level]
Syntax Description
Defaults
The default level is 15.
Command Modes
Global Configuration
Usage Guidelines
When you request an authorization for a specified privilege level with the enable command, the SCE platform sends an authentication request to the TACACS+ server. The SCE platform grants the requested privilege level only after the TACACS+ server authenticates the enable command password and verifies that you have sufficient privileges to enter the requested privilege level.
Authorization: admin
Examples
The following example shows how to set the privilege level for the user to viewer:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#username johndoe privilege 5 SCE(config)#
Related Commands
|
|
|
show users |
Displays the users in the local database. |
username |
Adds a new user to the local database. |
virtual-links index direction
Adds a new virtual link. The command also optionally changes the PIR values for a specified Global Controller configured in the SCA BB application.
To remove a specified virtual link, use the no form of this command.
virtual-links index vl-index direction [upstream | downstream]
virtual-links index vl-index direction [upstream | downstream] gc relative-gc-index set-pir value [`]pir-value[, pir-value2, pir-value3, pir-value4]'
virtual-links index vl-index direction [upstream | downstream] gc relative-gc-index reset-pir
no virtual-links index vl-index direction [upstream | downstream]
Syntax Description
Defaults
None.
Command Modes
Linecard Interface Configuration
Usage Guidelines
You can configure virtual links when the physical link that the SCE platform monitors is actually composed of multiple smaller links that you want to monitor and control separately. With virtual links, instead of creating hundreds or even thousands of separate packages with the specific bandwidth configuration for each small link, you can create a policy with a limited number of basic packages, each with a standard bandwidth configuration. Any specific bandwidth configuration can be adjusted for each virtual link by reconfiguring the relevant Global Controller.
Configuring virtual links consists of three steps in three different components of the Cisco Service Control application:
•![]() Create and apply a virtual links policy with the Global Controllers template.
Create and apply a virtual links policy with the Global Controllers template.
The policy is managed and applied through the GUI or API.
•![]() Create the virtual links and optionally set any specific bandwidth configuration in the Global Controllers.
Create the virtual links and optionally set any specific bandwidth configuration in the Global Controllers.
Virtual links are created and managed in the SCE through a set of CLI commands.
•![]() Set the virtual link names in the CM.
Set the virtual link names in the CM.
The virtual link names are set using a command line utility (CLU) in the CM. These names are used in the Virtual Links Reports.
Direction
Virtual links are directional. In the CLI commands, a virtual link is always identified by both the index number assigned to the virtual link and the direction (upstream or downstream).
Always use the direction keyword and specify upstream or downstream.
Global Controller (GC) Templates
The virtual links policy created in the SCA BB console specifies Global Controllers that will be used as bandwidth templates for the virtual links. When a new virtual link is created, it receives a set of the directional template VL Global Controllers with their PIR values as configured in the SCA BB console.
In some cases, you may want to modify the PIR values of a particular GC template for use with a particular virtual link:
•![]() Use the set-pir keyword with the desired PIR value to change the PIR value of a specified GC associated with a specified virtual link.
Use the set-pir keyword with the desired PIR value to change the PIR value of a specified GC associated with a specified virtual link.
•![]() Use the reset-pir keyword with no PIR values to reset the PIR values of a specified GC to the original values, as configured through the console.
Use the reset-pir keyword with no PIR values to reset the PIR values of a specified GC to the original values, as configured through the console.
Global Controllers-Relative Index
To specify the GC, use the gc keyword and then indicate the relative GC index. This number is the relevant GC as found in the GC configuration for the specified direction.
GC numbering starts at 0 for the default BWC in each direction, so the third user-configured GC, for example, is number 3. In the GC configuration illustrated in Figure 2-3, the relative index for the P2P GC is 2 for upstream and 3 for downstream.

Note ![]() Each GC also has an absolute index. In Figure 2-3, six GCs are configured and each one is identified internally by a unique index. This absolute index is not needed to identify a particular GC in these commands.
Each GC also has an absolute index. In Figure 2-3, six GCs are configured and each one is identified internally by a unique index. This absolute index is not needed to identify a particular GC in these commands.
Figure 2-3 Sample Configuration
PIR Values
Either one or four PIR values are configured for each template GC. By default, the SCA BB calendar function contains four timeframes. You can configure a different PIR for each timeframe or only one PIR that will be applied to all timeframes.
Examples
The following example shows how to create a new virtual link for the downstream direction:
SCE>enable
password<cisco>
SCE#configure
SCE(config)#interface linecard 0
SCE(config if)#virtual-links index 10 direction downstream
The following example shows how to change the PIR values for the template GC (the third one, which is number 2) for the specified virtual link. Be sure to use the proper index number from the correct direction for the GC.
Note that the four PIR values are separated by commas and enclosed in single quotation marks.
SCE>enable
password<cisco>
SCE#configure
SCE(config)#interface linecard 0
SCE(config if)#virtual-links index 10 direction downstream gc 2 set-pir value
`10000,50000,50000,10000'
The following example shows how to remove a virtual link. Be sure to specify the direction.
SCE>enable
password<cisco>
SCE#configure
SCE(config)#interface linecard 0
SCE(config if)#no virtual-links index 10 direction downstream
Related CommandsE
|
|
|
|---|---|
show interface linecard virtual-links |
Displays the currently configured virtual links. |
vlan
Configures the VLAN environment. One VLAN tag is supported for each packet (no QinQ support).
To set the VLAN configuration to the default value, use the default form of this command.
vlan symmetric skip
vlan a-symmetric skip
vlan symmetric classify
default vlan
Syntax Description
See Usage Guidelines.
Defaults
The default mode is symmetric skip.
Command Modes
Linecard Interface Configuration
Usage Guidelines
The VLAN modes act as follows:
•![]() vlan symmetric skip—Ignores tunnel.
vlan symmetric skip—Ignores tunnel.
•![]() vlan a-symmetric skip—Ignores tunnel, asymmetric.
vlan a-symmetric skip—Ignores tunnel, asymmetric.
•![]() vlan symmetric classify—VLAN tag as subscriber.
vlan symmetric classify—VLAN tag as subscriber.
•![]() When the tunneling information is ignored, the subscriber identification is the subscriber IP of the IP packet carried inside the tunnel.
When the tunneling information is ignored, the subscriber identification is the subscriber IP of the IP packet carried inside the tunnel.
Use the symmetric skip form of the command to skip the VLAN header when flow classification does not use the VLAN tag. VLAN tags are symmetric.
Use the a-symmetric skip form of the command to skip the VLAN header when flow classification does not use the VLAN tag. VLAN tags are asymmetric. Note that this form of the command impacts performance.
Use the symmetric classify form of the command when flow classification uses the VLAN tag. VLAN tags are symmetric. Using VLAN classification is mutually exclusive with any other tunnel-based classification.
Symmetric and Asymmetric Environments
In a symmetric environment, the same VLAN tags are used for carrying a transaction in the upstream and downstream directions.
In an asymmetric environment, the upstream and downstream VLAN tags of the same flow might not be the same.
The SCE platform is configured by default to work in symmetric environments. The a-symmetric skip command is needed to allow correct operation of the SCE platform in an asymmetric environment. The command instructs the platform to take into consideration that the upstream and downstream of each flow has potentially different VLAN tags.
Examples
The following example shows how to enable VLAN-based classification:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#vlan symmetric classify SCE(config if)#
Related Commands
|
|
|
show interface linecard vlan |
Displays the VLAN tunnel configuration. |
wap
Enables or disables operating in a WAP-based environment.
To disable operating in a WAP-based environment, use the no form of this command.
wap
no wap
Syntax Description
This command has no arguments or keywords.
Defaults
Operating in a WAP environment is disabled.
Command Modes
Linecard Interface Configuration
Usage Guidelines
Authorization: admin
Examples
The following example shows how to enable operating in a WAP-based environment:
SCE>enable 10 Password:<cisco> SCE#config SCE(config)#interface linecard 0 SCE(config if)#wap SCE(config if)#
Related Commands
|
|
|
show interface linecard wap |
Displays the current WAP handling state. |
 Feedback
Feedback