Introduction
This document describes the configuration of MAPs in Flex and Bridge mode for local client data bridging, bypassing the RAP.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Catalyst Wireless 9800 configuration model
- Configuration of LAPs
- Control And Provision of Wireless Access Points (CAPWAP)
- Configuration of Cisco switches
Components Used
This example utilizes lightweight access points (9124AP models), which can be configured as either a Root Access Point (RAP) or a Mesh Access Point (MAP) to seamlessly integrate with the Catalyst 9800 Wireless LAN Controller (WLC).
The information in this document is based on these software and hardware versions:
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Configure
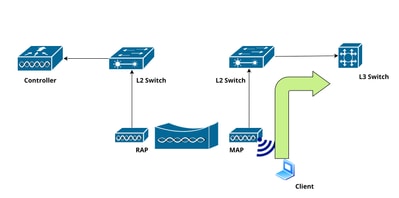
This section outlines configuration of Mesh Access Points (MAPs) operating in Mesh + Bridge mode, allowing local client data to be bridged directly to the uplink switch, bypassing the Root Access Point (RAP).
Network Diagram
Add Access Point to Controller Local Database
Step 1: Navigate to Configuration > Security > AAA > AAA Advanced.

Step 2. SelectDevice Authenticationand selectAdd.

Step 3. Type in theBase Ethernet MAC addressof the AP to join the WLC. Leave theAttribute List Nameblank, and selectApply to Device.

AAA Method List for Authentication
Step 1: Navigate to Configuration > Security > AAA > AAA Method List >Authentication and select Add.

Step 2: Define Method List Name. Select dot1x from the Type* drop-down and local for the Group Type. Select Apply to Device to save the configuration.

AAA Method List for Authorization
Step 1: Navigate to Configuration > Security > AAA > AAA Method List > Authorization and select Add.

Step 2: Define Method List Name, select credential download from the Type* dropdown and local for the Group Type. Click Apply to Device.

Mesh Profile
Step 1: Navigate to Configuration > Wireless > Mesh >Profiles and select Add.
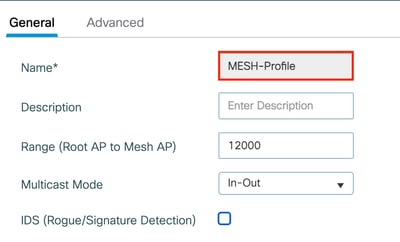
Step 2: Under the General tab, define a name and description (optional) for the Mesh profile.
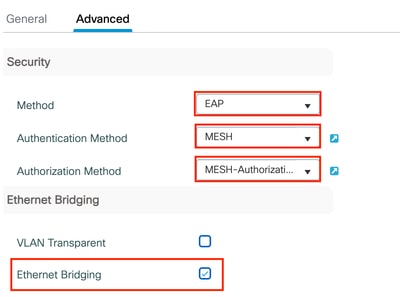
Step 3: In the Advanced tab, set the Method field to EAP, then select the previously created Authorization and Authentication profiles from the dropdown menus. Finally, enable the Ethernet Bridging checkbox and select Update and apply.
AP Join Profile
Step 1: Navigate to Configuration > Tag & Profiles > AP Join > Profile, click Add.
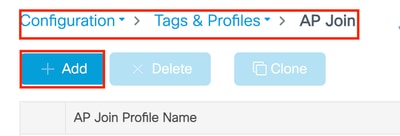
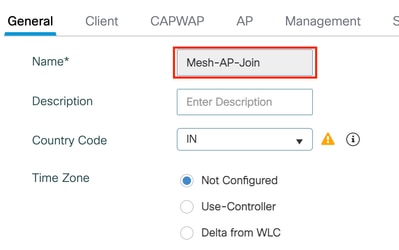
Step 2: Define profile name and description (optional).
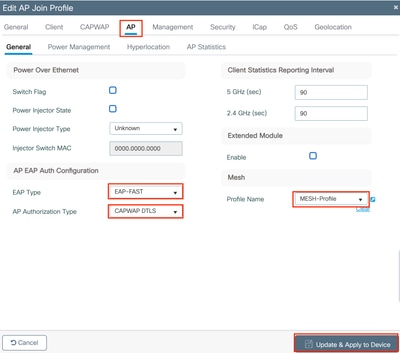
Step 3: Navigate to the AP tab, select the Mesh Profile from the Mesh Profile Name dropdown, set EAP-FAST for the EAP Type and CAPWAP DTLS for the AP Authorization Type, and click Apply to Device.
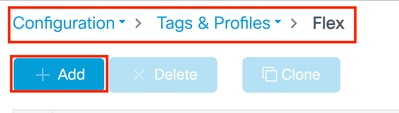
Flex Profile
Step 1: Configuration > Tags & Profiles > Flex, then click Add.
Step 2: Define a name for Flex profile.
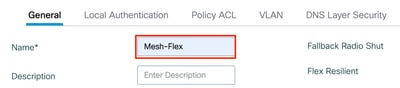
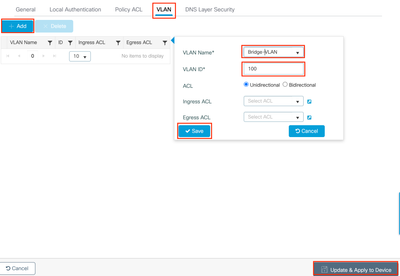
Step 3: Navigate to the vlan tab and Configure the VLAN Name and VLAN ID for Local Bridging of Wireless Client Traffic, click Save.
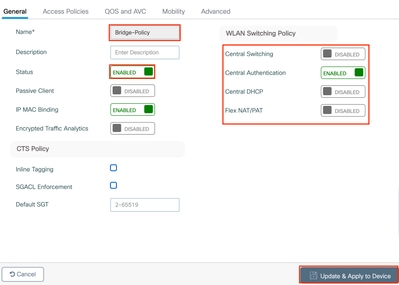
Policy Profile
Step 1: Navigate to Configuration > Tags & Profiles > Policy and click Add.

Step 2: Under the General tab, define the porifle name, set Status to Enabled, and Disable Central Switching.

Note: To enable local bridging of client traffic, Central Switching must be disabled. Based on the SSID configuration, other options can be enabled or disabled as needed.
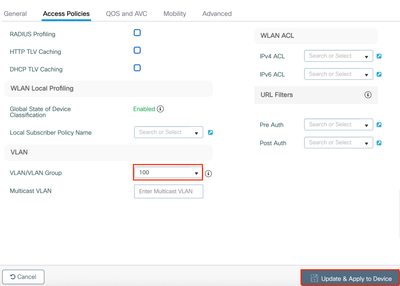
Step 3: Configure the VLANID specified under the VLAN tab of the AP Flex Profile, and click Update & Apply.
WLAN Tag
Step 1: Navigate to Configuration > Tags & Profiles > WLANs and select Add.
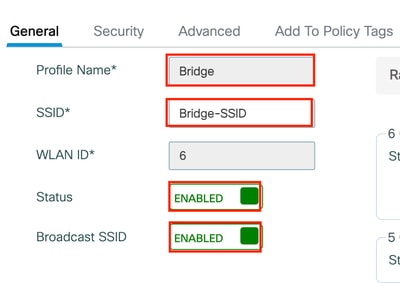
Step 2: Under the General Tab, Configure the Profile name, SSID and set the status to enabled.
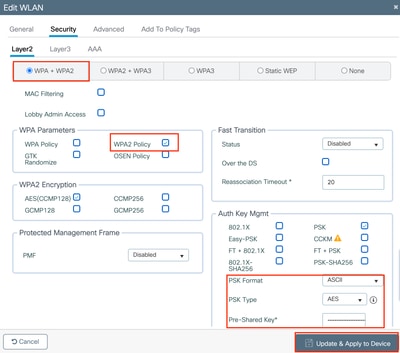
Step 3: Select the Security Tab, Enable WAP+WPA2 and configure a Pre-shared key.

Note: SSID configuration depends entirely on your requirements. For this example, a PSK-based SSID is configured.
Policy Tag
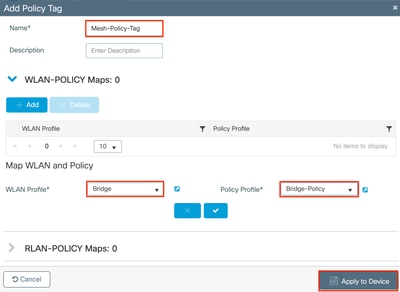
Step 1: Navigate to Configuration > Tags & Profiles > Tags > Policy Tab, click Add.
Step 2: Create a Policy Tag by defining a name and associating the WLAN and Policy Profile.
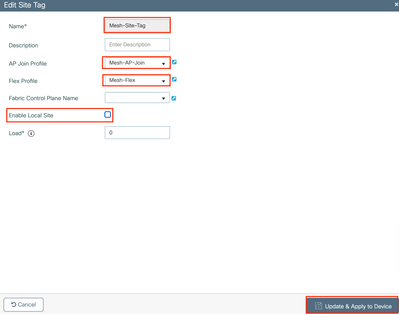
Site Tag
Step 1: Navigate to Configuration > Tags & Profiles > Tags > Site and click Add.
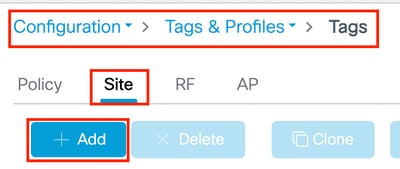
Step 2: Configure the Tag Name, disable the Enable Local Site option, and associate both the AP Join Profile and the Flex Profile.
Configuration of Access Points
This case study assumes the Access Point (AP) is first joined to the Wireless LAN Controller (WLC) in Local Mode and then transitioned to Flex+Bridge mode.
Step 1: Navigate to Configuration > Wireless > Access Points and Select the AP.
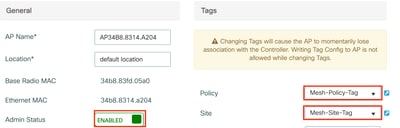
Step 2: Assign the Site Tag and Policy Tag to the Access Points (APs).

Note: The Access Point (AP) reboots, establish connection with the controller in Flex+Bridge mode, and the Mesh tab is available.
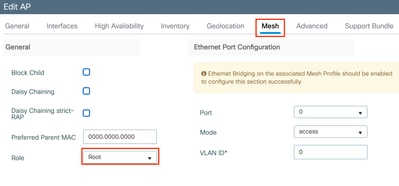
Step 3: Under the Mesh Tab, Select the Role to Root
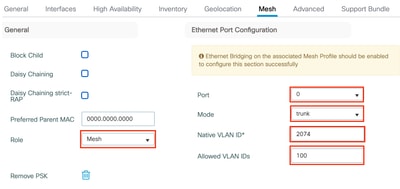
Step 4: Repeat Steps 1 and 2 for the Access Point (AP) designated to function as a Mesh AP to bring it online in Flex+Bridge mode. Navigate to the Mesh tab and configure the role as Mesh.
Step 5: The Mesh Access Point is connected to the switch on Port 0, configured in Trunk Mode, with the APs VLAN set as Native VLAN. Ensure the allowed VLANs include the client VLAN specified in the Flex profile.
Step 6: Click Update and Apply.
Switch Port Configuration
interface GigabitEthernet1/0/4
switchport trunk allowed vlan 100
switchport mode trunk
end
Verify
Mesh AP association to Root AP:
#show wireless mesh ap summary
AP Name AP Model BVI MAC BGN AP Role
------- -------------------- ------- --- -------
AP34B8.8314.A204 C9124AXI-ROW 34b8.8314.a204 Default Root AP
APC828.E536.D47C C9124AXI-ROW c828.e536.d47c Default Mesh AP
Number of Flex+Bridge APs : 2
Number of Flex+Bridge RAPs : 1
Number of Flex+Bridge MAPs : 1
#show wireless mesh ap tree
========================================================================
AP Name [Hop Ctr,Link SNR,BG Name,Channel,Pref Parent,Chan Util,Clients]
========================================================================
[Sector 1]
-----------
AP34B8.8314.A204 [0, 0, Default, (36,40), 0000.0000.0000, 5%, 0]
|-APC828.E536.D47C [1, 68, Default, (36,40), 0000.0000.0000, 6%, 0]
Number of Bridge APs : 2
Number of RAPs : 1
Number of MAPs : 1
Client association on the Mesh AP:
#show flexconnect client
Flexconnect Clients:
mac radio vap aid state encr aaa-vlan aaa-acl aaa-ipv6-acl assoc auth switching key-method roam key-progmed handshake-sent wgb SGT
52:95:C7:EE:B7:E5 0 0 1 FWD AES_CCM128 none none none Local Central Local Other regular No Yes No 0
#show controllers dot11Radio 0 client
mac radio vap aid state encr Maxrate Assoc Cap is_wgb_wired wgb_mac_addr
52:95:C7:EE:B7:E5 0 0 1 FWD AES_CCM128 MCS92SS HE HE false 00:00:00:00:00:00
#show flexconnect client aaa-override
Flexconnect Clients:
mac vlan qos acl ipv6-acl vlan-name avgdtds avgrtdtds bstdtds bstrtdtds avgdtus avgrtdtus bstdtus bstrtdtus
52:95:C7:EE:B7:E5 none none none none Bridge-VLAN 0 0 0 0 0 0 0 0
Traffic from the Mesh Access Point (MAP) is directly bridged to the uplink switch, bypassing the Root Access Point (RAP):
DHCP:
May 30 04:25:21 APC828.E536.D47C kernel: [*05/30/2025 04:25:21.2883] [ 62081:607119] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apr0v0> [U:C] DHCP_REQUEST : TransId 0x3bcb0a7b
May 30 04:25:21 APC828.E536.D47C kernel: [*05/30/2025 04:25:21.2884] chatter: dhcp_req_local_sw_nonat: 1748579121.288205428: 0.0.0.0.68 > 255.255.255.255.67: udp 308
May 30 04:25:21 APC828.E536.D47C kernel: [*05/30/2025 04:25:21.2885] [ 62081:607245] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apr0v0> [U:C] DHCP_REQUEST : TransId 0x3bcb0a7b
May 30 04:25:21 APC828.E536.D47C kernel: [*05/30/2025 04:25:21.2885] chatter: dhcp_reply_nonat: 1748579121.288205428: 0.0.0.0.68 > 255.255.255.255.67: udp 308
May 30 04:25:21 APC828.E536.D47C kernel: [*05/30/2025 04:25:21.2943] [ 62081:613080] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apbhr1> [D:C] DHCP_ACK : TransId 0x3bcb0a7b
May 30 04:25:21 APC828.E536.D47C kernel: [*05/30/2025 04:25:21.2943] [ 62081:613123] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apr0v0> [D:W] DHCP_ACK : TransId 0x3bcb0a7b
ARP:
May 30 04:31:44 APC828.E536.D47C kernel: [*05/30/2025 04:31:44.0572] [ 62464:537183] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apr0v0> [U:W] ARP_QUERY : Sender 100.0.0.2 TargIp 100.0.0.1
May 30 04:31:44 APC828.E536.D47C kernel: [*05/30/2025 04:31:44.0572] [ 62464:537219] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apr0v0> [U:C] ARP_QUERY : Sender 100.0.0.2 TargIp 100.0.0.1
May 30 04:31:44 APC828.E536.D47C kernel: [*05/30/2025 04:31:44.0573] chatter: ethertype_cl1: 1748579504.057210494: arp who-has 100.0.0.1 tell 100.0.0.2
May 30 04:31:44 APC828.E536.D47C kernel: [*05/30/2025 04:31:44.0628] [ 62464:542842] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apbhr1> [D:C] ARP_REPLY : Sender 100.0.0.1 HwAddr c4:44:a0:a2:61:d1
May 30 04:31:44 APC828.E536.D47C kernel: [*05/30/2025 04:31:44.0629] chatter: fromdevs_arp_resp: arp reply 100.0.0.1 is-at C4:44:A0:A2:61:D1
May 30 04:31:44 APC828.E536.D47C kernel: [*05/30/2025 04:31:44.0629] [ 62464:542971] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apbhr1> [D:C] ARP_REPLY : Sender 100.0.0.1 HwAddr c4:44:a0:a2:61:d1
May 30 04:31:44 APC828.E536.D47C kernel: [*05/30/2025 04:31:44.0630] [ 62464:543018] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apr0v0> [D:W] ARP_REPLY : Sender 100.0.0.1 HwAddr c4:44:a0:a2:61:d1
May 30 04:31:45 APC828.E536.D47C kernel: [*05/30/2025 04:31:45.4301] [ 62465:910100] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apr0v0> [D:A] ARP_REPLY : Sender 100.0.0.1 HwAddr c4:44:a0:a2:61:d1
ICMP:
May 30 04:32:09 APC828.E536.D47C kernel: [*05/30/2025 04:32:09.3059] [ 62489:785903] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apr0v0> [U:W] ICMP_ECHO : Id 39016 Seq 0
May 30 04:32:09 APC828.E536.D47C kernel: [*05/30/2025 04:32:09.3059] [ 62489:785938] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apr0v0> [U:C] ICMP_ECHO : Id 39016 Seq 0
May 30 04:32:09 APC828.E536.D47C kernel: [*05/30/2025 04:32:09.3104] [ 62489:790444] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apbhr1> [D:C] ICMP_ECHO_REPLY : Id 39016 Seq 0
May 30 04:32:09 APC828.E536.D47C kernel: [*05/30/2025 04:32:09.3105] [ 62489:790534] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apbhr1> [D:C] ICMP_ECHO_REPLY : Id 39016 Seq 0
May 30 04:32:09 APC828.E536.D47C kernel: [*05/30/2025 04:32:09.3105] [ 62489:790583] [APC828.E536.D47C] [52:95:c7:ee:b7:e5] <apr0v0> [D:W] ICMP_ECHO_REPLY : Id 39016 Seq 0





























 Feedback
Feedback