Introduction
This document describes how to configure SAML authentication for Secure Web Gateway (SWG) using Active Directory Federated Services (ADFS).
Requirement for SAML Authentication
Umbrella SAML authentication requires the SAML response to include the end user’s userPrincipalName (for example, user@domain.local) as the Name ID claim. This requirement applies to all Identity Providers. Some, such as ADFS, require manual configuration to include this attribute.
Configuration Steps in ADFS
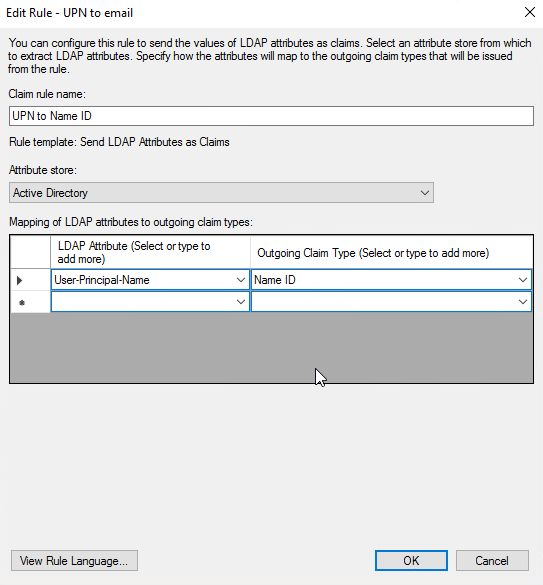
- In ADFS, select theRelying Party Trustcreated for Umbrella underADFS > Relying Party Trusts.
- ClickEdit Claim Issuance Policy.
- Add a new rule using the claim templateSend LDAP Attribute as claims.
- Configure the rule to map the LDAP attributeuserPrincipalNameto the SAML outgoing claim typeName ID.
 Screenshot_2021-10-20_at_12.33.50.png
Screenshot_2021-10-20_at_12.33.50.png
- Save the configuration.
UPN Versus E-Mail Address
A user’s UPN (for example, user@domain.local) often matches the user’s e-mail address. In some environments, the e-mail address (for example, user@externaldomain.tld) differs from the UPN.
- Umbrella requires the Identity Provider to send theName IDclaim with the UPN value.
- This must match the username provisioned inDeployments > Users and Groupsin Umbrella.
- Umbrella user provisioning tools (such as the AD Connector) identify users by their UPN.


 Feedback
Feedback