Introduction
This document describes the process of transitioning from a Palo Alto firewall to a Cisco FTD system by employing the FMT version 6.0.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
-
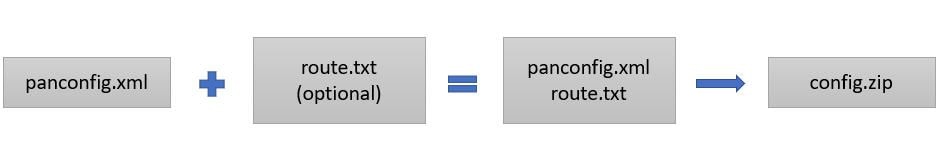
Exporting the current running configuration from the Palo Alto firewall in XML format (*.xml).
-
Accessing the Palo Alto Firewall CLI and executing the show routing route command, then saving the output as a text file (*.txt).
-
Compressing both the configuration file (*.xml) and the routing output file (*.txt) into a single ZIP archive (*.zip).
Components Used
The information in this document is based on Palo Alto Firewall version 8.4.x or later.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Firepower Migration Tool (FMT)
The FMT aids engineering teams in the transition of any existing Vendor firewalls to Ciscos Next-Generation Firewall (NGFW)/Firepower Threat Defense (FTD). Ensure to operate the latest version of FMT, downloaded from the Cisco website.
Migration Guideline
1. Pre-Migration Checklist
- Ensure the FTD has been added to the FMC before beginning the migration process.
- New user account with administrative privileges has been created on the FMC.
- Exported Palo Alto running configuration file.xml must be zipped with an extension of .zip.
- NGFW/FTD must have the same number of Physical or Sub-interface or Port-channel equals to Palo Alto Firewall interfaces.
2. Migration Tool Usage
- Download the FMT tool .exe and run as administrator.
- FMT will require CEC ID or cisco user account in order to log in.
- Post Successful login the tool will display a dashboard where you can choose firewall vendor and upload the corresponding *.zip file; refer to the next image.
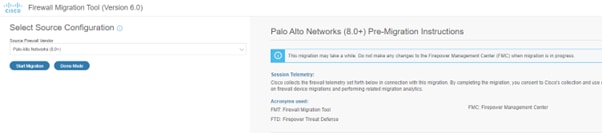
- Review the instructions provided on the right-hand side carefully before proceeding with the migration.
- Click Start Migration once you are ready to begin.
- Upload the saved *.zip file that contains the configuration settings from your Palo Alto firewall.
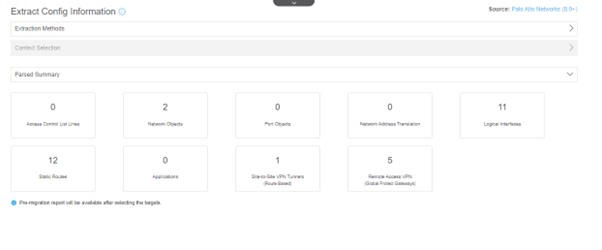
- Once the configuration file is uploaded, you will be able to see a Parsed Summary of the contents and click next; refer to the next image.
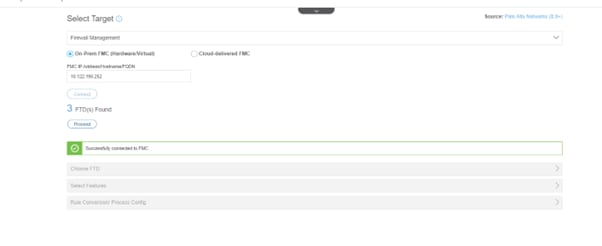
- Enter the IP address of the FMC and log in.
- The tool will search for an active FTD that has been registered with the FMC.
- Choose the FTD you like to migrate and click Proceed, as shown in the next image.
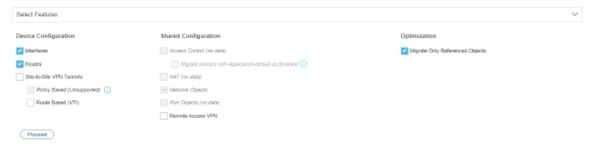
- Choose the specific features in order to migrate based on the requirements of the customer. Note that Palo Alto firewalls have a different feature set compared to FTD.
- Click Proceed and consult the next image for reference.
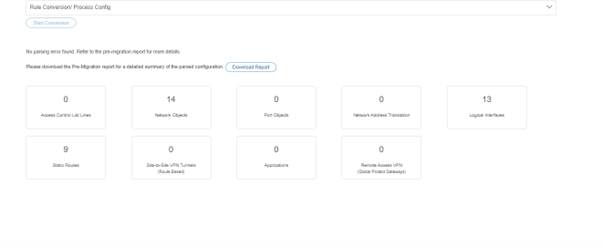
- The FMT will execute the conversion according to your selections. Review the changes in the Pre-Migration Report, then click Proceed. See the next image for guidance.
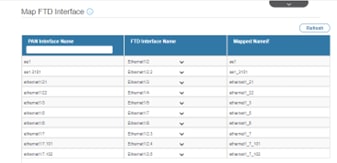
- Map the interfaces from the Palo Alto firewall to those on the FTD. Refer to the next image for details.

Note: NGFW/FTD must have same number of Physical or Sub-interface or Port-channel equals to Palo Alto Firewall interfaces including Sub-interfaces.
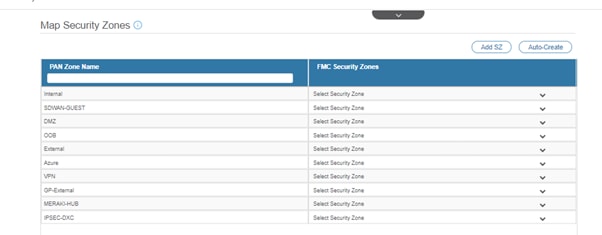
- Determine the mapping for Zones, which can either be done manually or by using the Auto-create feature. For visualization, refer to the next image.
- Assign your application blocking profile. As this is a lab device without application mapping, you can continue with the default settings can be continued. Click Next, and refer to the image provided.
- Optimize ACLs, objects, interfaces, and routes as needed. Since this is a lab setup with minimal configurations, you can proceed with the default options. Then click Validate, referencing the next image.
- Following successful validation, the configuration is ready to be deployed to the targeted FTD. See the next image for further instructions.
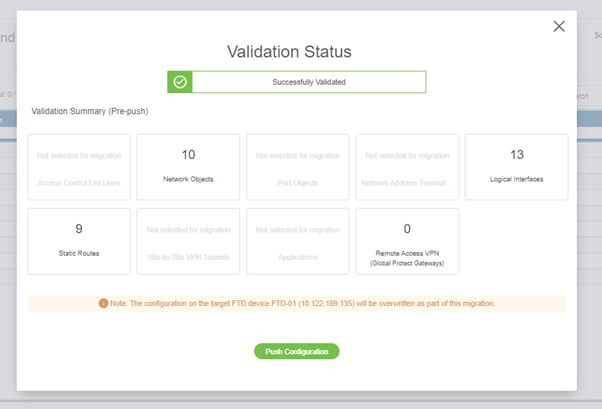
- The Push Configuration will save the migrated configurations in FMC and will be deployed to the FTD automatically.
- In case of any issue while migrating, feel free to open a TAC case for further assistance.
3. Post - Migration Validation
- Validating the configuration on the FTD and FMC.
- Testing the device ACLs, Policy, Connectivity, and other Advanced features.
- Create a rollback point before performing any changes.
- Testing the migration in the lab environment before Go-Live in the Production environment.
Known Issues
1. Missing Interfaces on FTD
- Login to Palo Alto CLI and execute the show interface all. You must have equal or more than the number of interfaces in FTD.
- Create the equal or more number of interfaces - either sub-interface, Port-channel, or Physical interface via FMC GUI.
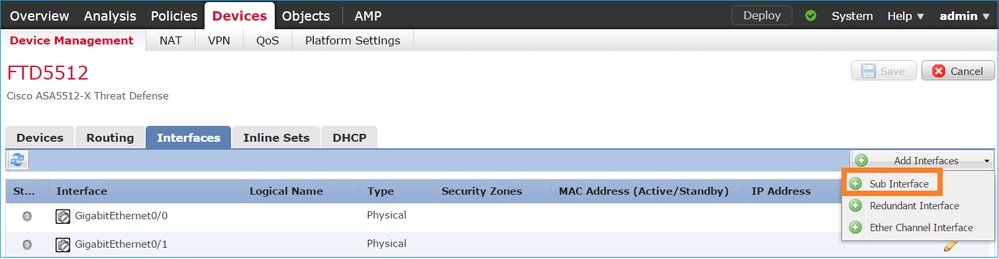
- Navigate to FMC GUI Device > Device Management, click the FTD in which the required interface is to be created. Under Interface section, from the right corner dropdown menu choose Create Sub-interface/BVI accordingly and create the interface and associate corresponding interfaces. Save the configuration and sync to the device.
- Verify that interfaces are created on FTD by executing Show interface ip brief and proceed with migration for interface mapping.
2. Routing Table
- Verify the routing table on Palo Alto firewall by executing Show routing route or Show routing route summary.
- Before migrating the routes to FTD, verify the table and choose the required routes as per the project need.
- Vaildate the same routing table in the FTD by Show route all and show route summary.
3. Optimize
- Optimizing objects panel greyed out, sometimes you must create a manual object in FMC and map it. In order to view the object in FTD, use Show Running | in objects and in Palo Alto, use Show address <object name>.
- Application Migration requires an Audit of Palo Alto firewall before the migration, FTD has dedicated IPS device or you can enable the feature in FTD so you need to plan the application migration task as per customer requirement.
- NAT Configuration of Palo Alto firewall must be verified by show running nat-policy and you must have a custom NAT policy in FTD, which can be viewed in FTD by Show Running nat.
Conclusion
The Palo Alto firewall has been successfully migrated to Cisco FTD with the help of FMT. In case of any issue post migration on FTD and for troubleshooting further open a TAC case.














 Feedback
Feedback