Introduction
This document describes how to detect malicious connections on a Windows endpoint and block them using the Host Firewall in Cisco Secure Endpoint.
Prerequisites
Requirements
- Host Firewall is available with Secure Endpoint Advantage and Premier packages.
- Supported Connector Versions
- Windows (x64): Secure Endpoint Windows connector 8.4.2 and later.
- Windows (ARM): Secure Endpoint Windows connector 8.4.4 and later.
Components Used
This document is not restricted to specific software and hardware versions.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Troubleshoot Guide
This document provides a guide to block malicious connections with the use of Cisco Secure Endpoint Host Firewall. In order to test, you use the test page malware.wicar.org (208.94.116.246) to create a troubleshoot guide.
Steps to Identify and Block Malicious Connections
- First, you need to identify the URL or IP address you want to review and block. For this scenario consider malware.wicar.org.
- Verify if access to the URL is successful. malware.wicar.org redirects to a different URL, as show in the image.
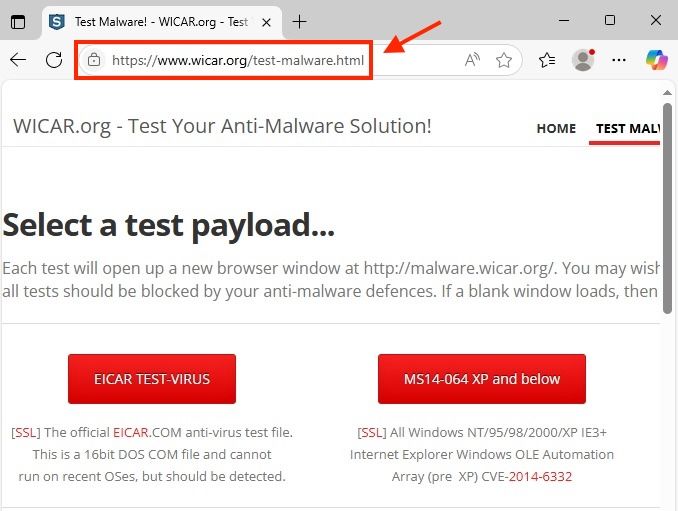 Browser Malicious URL
Browser Malicious URL
3. Use the nslookup command to retrieve the IP address associated with the URL malware.wicar.org.
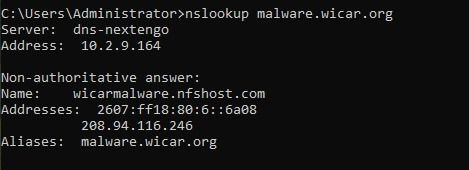 nslookup Output
nslookup Output
4. Once the malicious IP address is obtained, check the active connections on the endpoint with the command:netstat -ano.
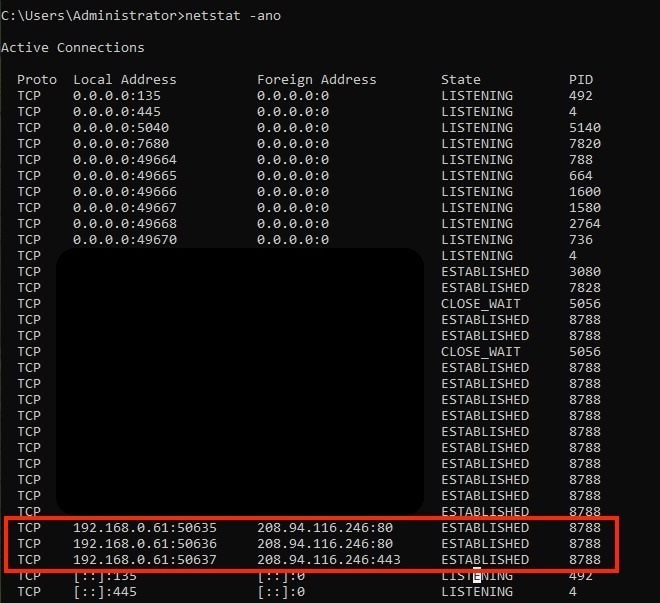 netstat for all Connections
netstat for all Connections
5. In order to isolate active connections, apply a filter to display only established connections.
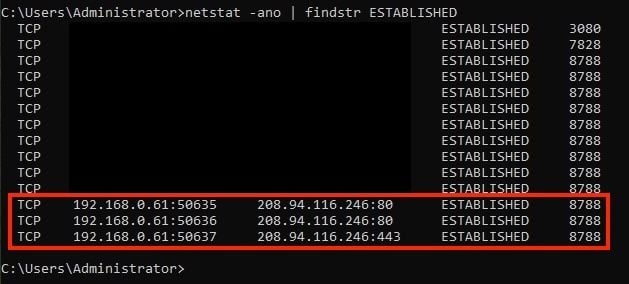 netstat for Established Connections
netstat for Established Connections
6. Look for the IP address obtained from thenslookupcommand in the previous output. Identify the source IP, destination IP, source port, and destination port.
- Local IP: 192.168.0.61
- Remote IP: 208.94.116.246
- Local Port: Not Applicable
- Destination Portto 80 and 443
7. Once you have this information, navigate to the Cisco Secure Endpoint Portal to create the Host Firewall configuration.
Host Firewall Configuration and Rule Creation
- Navigate toManagement > Host Firewalland clickNew Configuration.
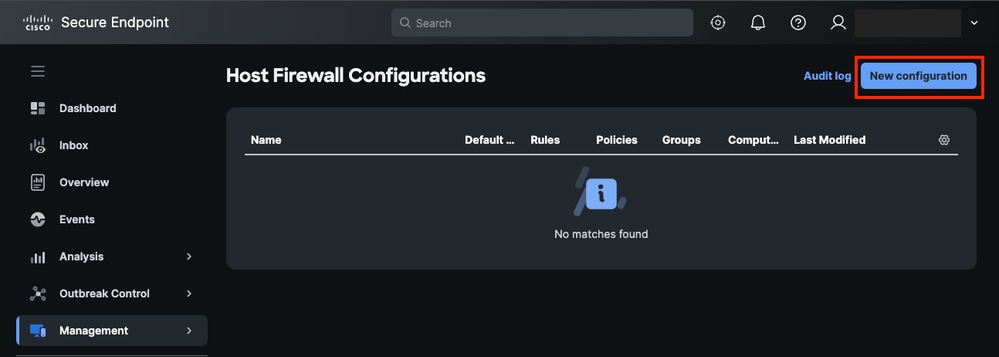 Host Firewall New Configuration
Host Firewall New Configuration
- Select a name and theDefault Action. In this case, select Allow.
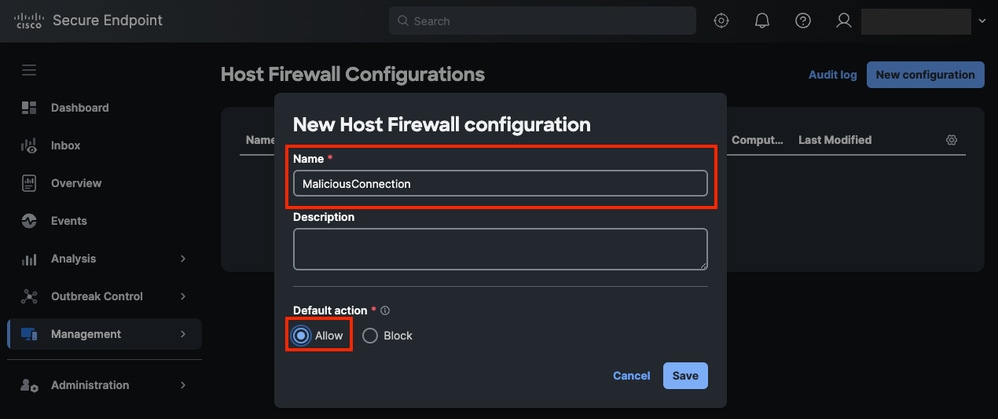 Host Firewall Configuration Name and Default Action
Host Firewall Configuration Name and Default Action

Note: Keep in mind that you create a block rule, but you must allow other traffic to avoid impact on legitimate connections.
- Verify that the default rule has been created and clickAdd Rule.
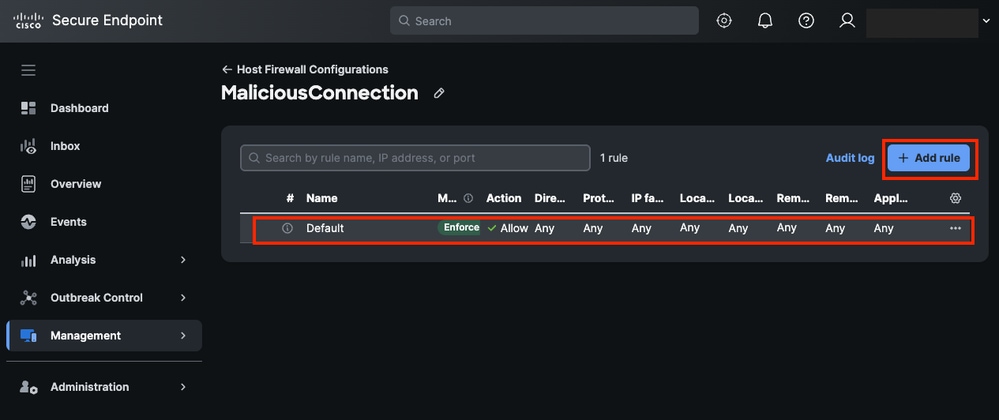 Add Rule in Host Firewall
Add Rule in Host Firewall
- Assign a name and set the next parameters:
- Position: Top
- Mode: Enforce
- Action: Block
- Direction: Out
- Protocol: TCP
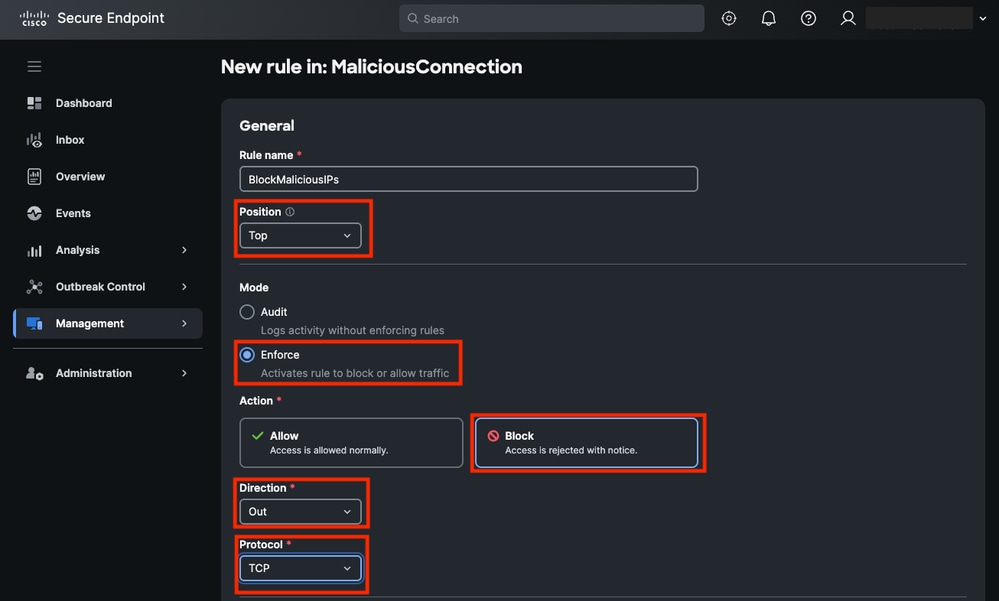 Rule General Parameters
Rule General Parameters

Note: When you address malicious connections from an internal endpoint to an external destination, typically to the internet, the direction can always be Out.
- Specify the local and destination IPs:
- Local IP: 192.168.0.61
- Remote IP: 208.94.116.246
- Leave theLocal Portfield blank.
- Set theDestination Portto 80 and 443, these correspond to HTTP and HTTPS.
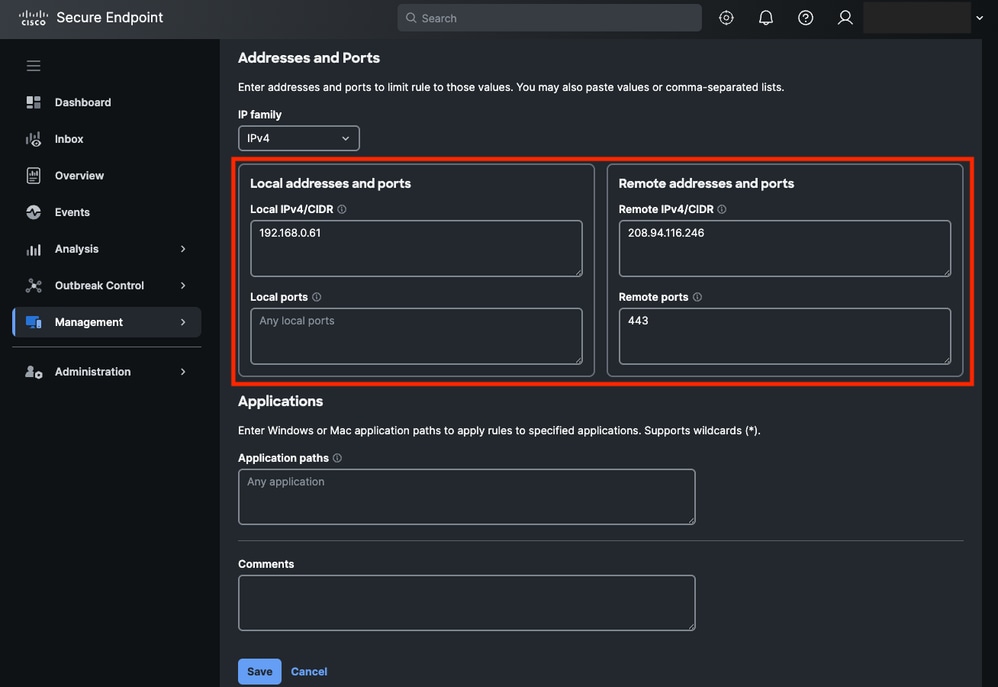 Rule Addresses and Ports
Rule Addresses and Ports
6. Finally, clickSave.
Enable Host Firewall in the Policy and Assign the New Configuration
- In the Secure Endpoint Portal, navigate toManagement > Policiesand select the policy associated with the endpoint where you want to block malicious activity.
- ClickEditand navigate to theHost Firewalltab.
- Enable the Host Firewall feature and select the recent configuration, in this case MaliciousConnection.
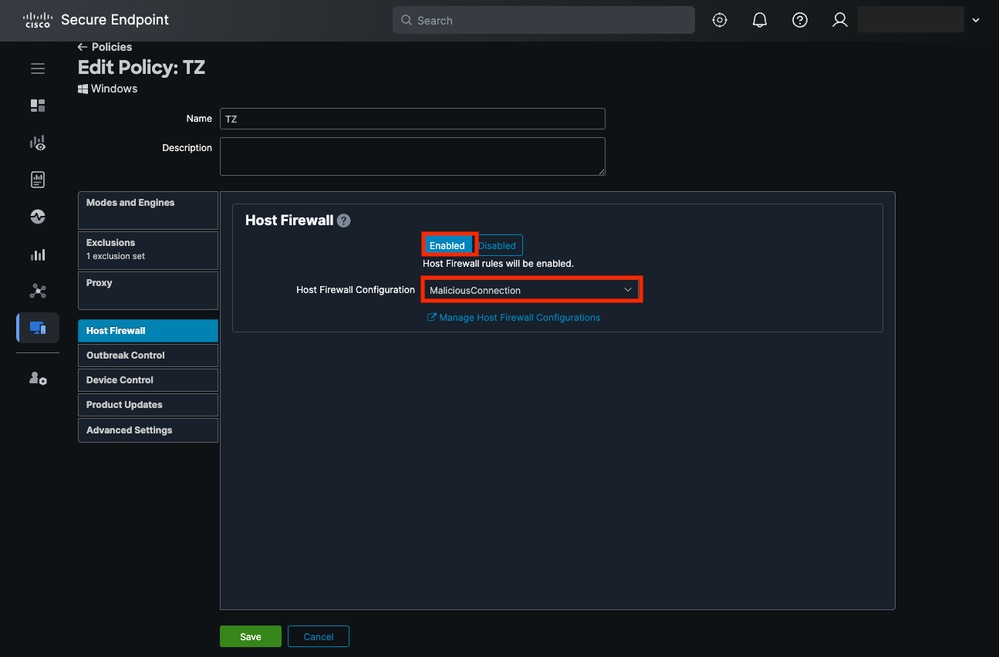 Host Firewall Enabled in Secure Endpoint Policy
Host Firewall Enabled in Secure Endpoint Policy
- Click Save.
- Finally, verify that the endpoint has applied the policy changes.
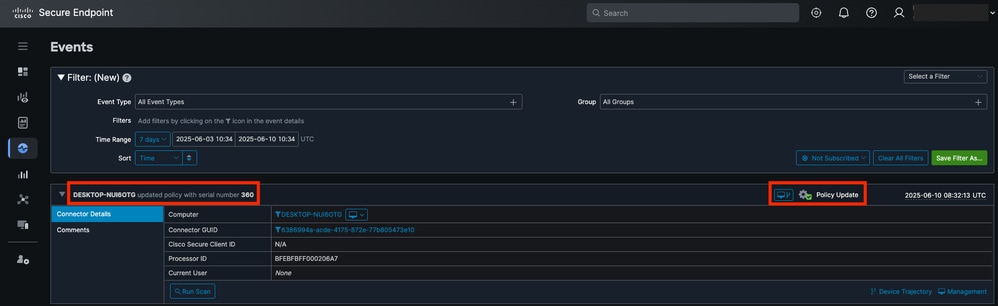 Policy Update Event
Policy Update Event
Validate the Configuration Locally
- Use the URL malware.eicar.org in a browser to confirm that it is blocked.
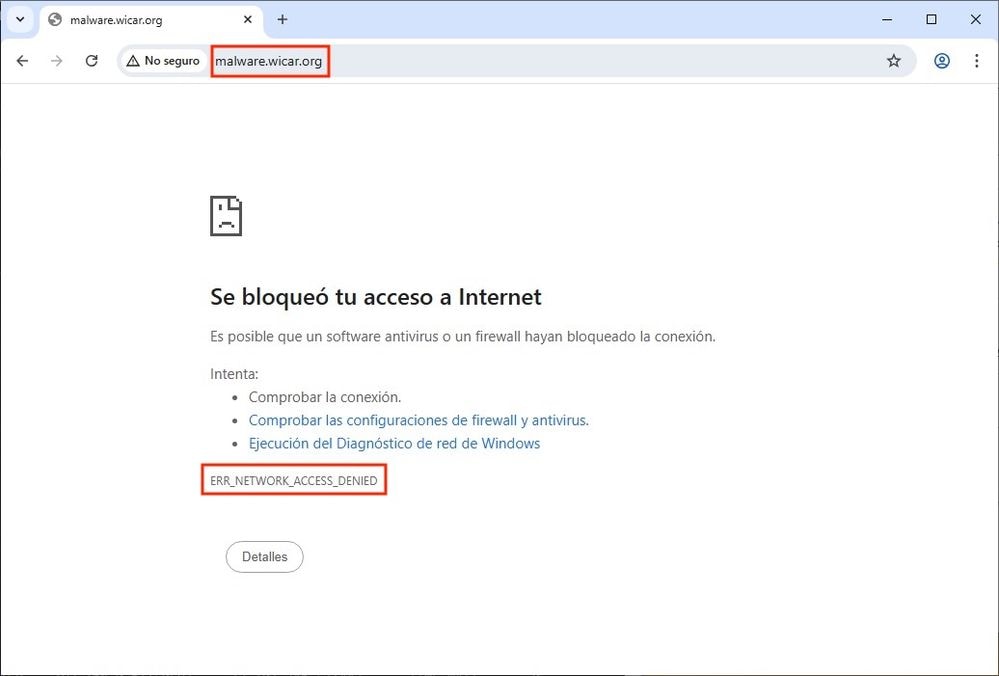 Error Network Access Denied from Browser
Error Network Access Denied from Browser
- After you confirm the block, verify that no connections are established. Use the command netstat -ano | findstr ESTABLISHED to ensure the IP associated with the malicious URL (208.94.116.246) is not visible.
Review Logs
1. On the endpoint, navigate to the folder:
C:\Program Files\Cisco\AMP\<Connector version>\FirewallLog.csv

Note: The log file is located in the folder <install directory>\Cisco\AMP\<Connector version>\FirewallLog.csv
2. Open the CSV file to validate matches for the Block action rule. Use a filter to distinguish between Allow and Block connections.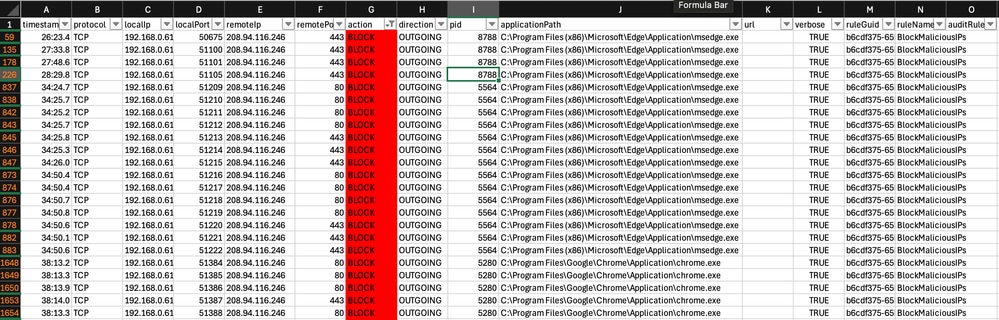 Firewall Logs in CSV File
Firewall Logs in CSV File
Use Orbital to Retrieve Firewall Logs
- In the Secure Endpoint Portal, navigate toManagement > Computers, locate the endpoint, and clickRetrieve Firewall Logs in Orbital. This action redirects you to the Orbital Portal.
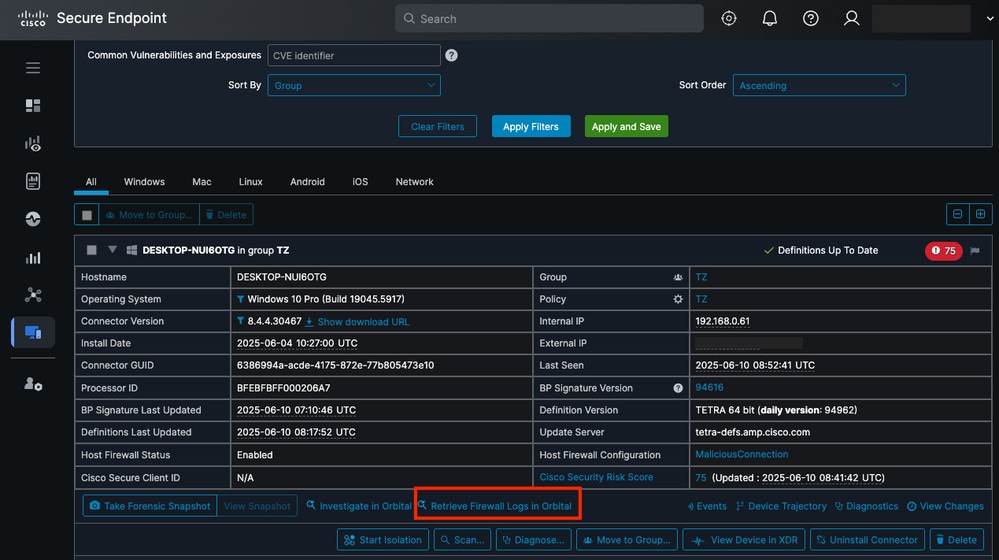 Button to Retrieve Firewall Logs in Orbital
Button to Retrieve Firewall Logs in Orbital
- In the Orbital Portal, clickRun Query. This action displays all logs recorded on the endpoint for the Host Firewall.
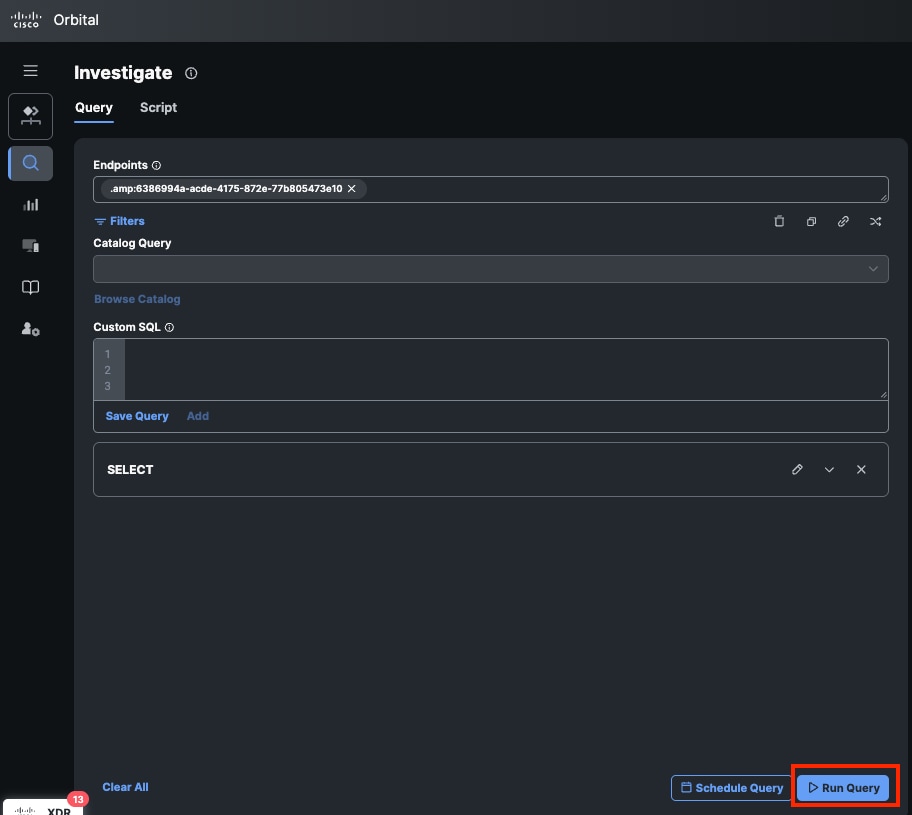 Run Query from Orbital
Run Query from Orbital
- The information is visible in theResultstab, or you can download it.
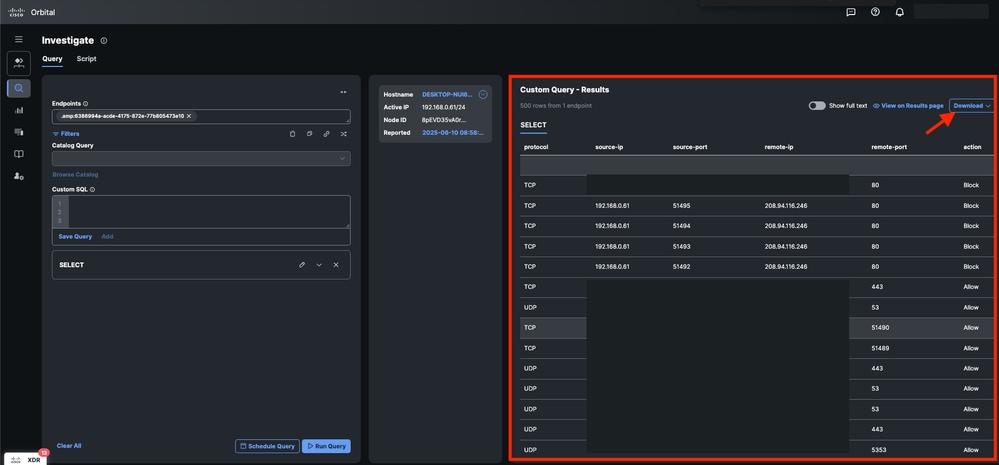 Query Results from Orbital
Query Results from Orbital


















 Feedback
Feedback