Configure Cisco IOS Zone Based Firewall Interoperability with WAAS Deployment
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes a new configuration model for the Cisco IOS® Firewall feature set. This new configuration model offers intuitive policies for multiple-interface routers, increased granularity of firewall policy application, and a default deny-all policy that prohibits traffic between firewall security zones until an explicit policy is applied to allow desirable traffic.
Prerequisites
Requirements
Cisco recommends that you have knowledge of Cisco IOS® CLI.
Components Used
The information in this document is based on these software and hardware versions:
- Cisco 2900 Series Routers
- Cisco IOS® Software Release 15.2(4) M2
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
Zone-Based Policy Firewall (also known as Zone-Policy Firewall, ZFW or ZBF) changes the firewall configuration from the older interface-based model (CBAC) to a more flexible, more easily understandable zone-based model. Interfaces are assigned to zones, and inspection policy is applied to traffic that moves between the zones. Inter-zone policies offer considerable flexibility and granularity, so different inspection policies can be applied to multiple host groups connected to the same router interface. Firewall policies are configured with the Cisco® Policy Language (CPL), which employs a hierarchical structure in order to define the inspection for network protocols and the groups of hosts to which the inspection is applied.
WAAS Support with Cisco IOS® Firewall
Wide Area Application Services (WAAS) support with Cisco IOS® firewall was introduced in Cisco IOS® Release 12.4(15)T. It provides an integrated firewall that optimizes security-compliant WANs and application acceleration solutions with these benefits:
- Optimizes a WAN through full stateful inspection capabilities
- Simplifies Payment Card Industry (PCI) compliance
- Protects transparent WAN accelerated traffic
- Integrates WAAS networks transparently
- Supports the Network Management Equipment (NME) Wide Area Application Engine (WAE) modules or standalone WAAS device deployment
WAAS has an automatic discovery mechanism that uses TCP options during the initial three-way handshake used in order to identify WAE devices transparently. After automatic discovery, optimized traffic flows (paths) experience a change in the TCP sequence number in order to allow the endpoints to distinguish between optimized and non-optimized traffic flows.
The WAAS support for IOS® firewall allows for the adjustment of internal TCP state variables used for layer 4 inspection, based on the shift in the sequence number mentioned earlier. If the Cisco IOS® firewall notices that a traffic flow has successfully completed WAAS automatic discovery, it permits the initial sequence number shift for the traffic flow and maintains the Layer 4 state on the optimized traffic flow.
WAAS Traffic Flow Optimization Deployment Scenarios
The sections describe two different WAAS traffic flow optimization scenarios for branch office deployments. WAAS traffic flow optimization works with the Cisco firewall feature on a Cisco Integrated Services Router (ISR).
The figure shows an example of an end-to-end WAAS traffic flow optimization with the Cisco firewall. In this particular deployment, a NME-WAE device is on the same device as the Cisco firewall. Web Cache Communication Protocol (WCCP) is used in order to redirect the traffic for interception.
- WAAS Branch Deployment with an Off-Path Device
- WAAS Branch Deployment with an Inline Device
WAAS Branch Deployment with Off-Path Device
A WAE device can be either a standalone Cisco WAN Automation Engine (WAE) device or a Cisco WAAS Network Module (NME-WAE) that is installed on an ISR as an integrated service engine.
The figure shows a WAAS branch deployment that uses WCCP in order to redirect the traffic to an off-path, standalone WAE device for traffic interception. The configuration for this option is the same as the WAAS branch deployment with an NME-WAE.
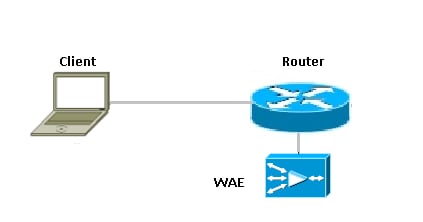
Network Diagram

Configuration and Packet Flow
This diagram depicts an example setup with WAAS optimization turned On for end-to-end traffic and Centralized Management System (CMS) that is present at the server's end. The WAAS modules present at the Branch end and the Data Center (DC) end need to register with the CMS for their operations. It is observed that the CMS uses HTTPS for it’s communication with the WAAS modules.
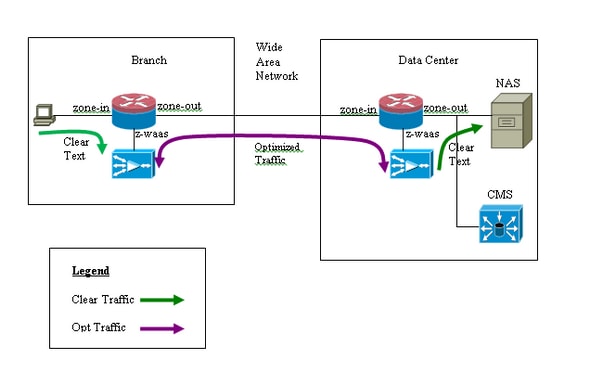
End-to-End WAAS Traffic Flow
The example here provides an end-to-end WAAS traffic flow optimization configuration for the Cisco IOS® firewall that uses WCCP in order to redirect the traffic to a WAE device for traffic interception.
Section 1. IOS-FW WCCP related configuration:
ip wccp 61 ip wccp 62 ip inspect waas enable
Section 2. IOS-FW policy configuration:
class-map type inspect most-traffic match protocol icmp match protocol ftp match protocol tcp match protocol udp ! policy—map type inspect p1 class type inspect most—traffic inspect class class—default drop
Section 3. IOS-FW Zone and Zone-pair configuration:
zone security zone-in zone security zone-out zone security z-waas zone—pair security in—out source zone-in destination zone-out service—policy type inspect p1 zone—pair security out-in source zone-out destination zone-in service—policy type inspect p1
Section 4. Interface configuration:
interface GigabitEthernet0/0 description Trusted interface ip address 172.16.11.1 255.255.255.0 ip wccp 61 redirect in zone—member security zone-in
! interface GigabitEthernet0/1 description Untrusted interface ip address 203.0.113.1 255.255.255.0 ip wccp 62 redirect in zone—member security zone-out
Note: The new configuration in Cisco IOS® Release 12.4(20)T and 12.4(22)T places the integrated-service-engine in its own zone and need not be a part of any zone-pair. The zone-pairs are configured between zone-in and zone-out.
interface Integrated—Service—Enginel/0 ip address 192.168.10.1 255.255.255.0 ip wccp redirect exclude in zone—member security z-waas
With no zone configured on the Integrated—Service—Enginel/0, traffic gets dropped with this drop message:
*Mar 9 11:52:30.647: %FW-6-DROP_PKT: Dropping tcp session 172.16.11.59:44191 172.16.10.10:80 due to One of the interfaces not being cfged for zoning with ip ident 0
CMS Traffic Flow (WAAS Device Registering with Central Manager)
The example here provides the configuration for both the scenarios listed:
- End-to-End WAAS traffic flow optimization configuration for the Cisco IOS® firewall that uses WCCP in order to redirect the traffic to a WAE device for traffic interception
- Allowing the CMS traffic (WAAS management traffic that flows to/from CMS from/to WAAS devices)
Section 1. IOS-FW WCCP related configuration:
ip wccp 61 ip wccp 62 ip inspect waas enable
Section 2. IOS-FW policy configuration:
class-map type inspect most-traffic match protocol icmp match protocol ftp match protocol tcp match protocol udp policy—map type inspect p1 class type inspect most—traffic inspect class class—default drop
Section 2.1. IOS-FW policy related to CMS traffic:
Note: The class map here is needed in order to allow the CMS traffic to go through:
class-map type inspect waas-special match access-group 123 policy-map type inspect p-waas-man class type inspect waas-special pass class class-default drop
Section 3. IOS-FW Zone and Zone-pair configuration:
zone security zone-in zone security zone-out zone security z-waas zone—pair security in—out source zone-in destination zone-out service—policy type inspect p1 zone—pair security out—in source zone-out destination zone-in service—policy type inspect p1
Section 3.1. IOS-FW CMS related Zone and Zone-pair configuration:
Note: The zone-pairs waas-out and out-waas are required in order to apply the policy created earlier for CMS traffic.
zone-pair security waas-out source z-waas destination zone-out service-policy type inspect p-waas-man zone-pair security out-waas source zone-out destination z-waas service-policy type inspect p-waas-man
Section 4. Interface configuration:
interface GigabitEthernet0/0
description Trusted interface
ipaddress 172.16.11.1 255.255.255.0
ip wccp 61 redirect in
zone—member security zone-in
!
interface GigabitEthernet0/1
description Untrusted interface
ip address 203.0.113.1 255.255.255.0
ip wccp 62 redirect in
zone—member security zone-out ! interface Integrated—Service—Enginel/0
ip address 192.168.10.1 255.255.255.0
ip wccp redirect exclude in
zone—member security z-waas
Section 5. Access-list for CMS traffic.
Note: Access-list that is used for CMS traffic. It allows HTTPS traffic in both the directions as the CMS traffic is HTTPS.
access-list 123 permit tcp any eq 443 any access-list 123 permit tcp any any eq 443
ZBF Session Information
User at 172.16.11.10 behind Router R1 accesses the file server hosted behind remote end with an IP address of 172.16.10.10, ZBF session is built from in-out zone-pair and thereafter router redirects the packet to WAAS engine for optimization.
R1#sh policy-map type inspect zone-pair in-out sess
policy exists on zp in-out
Zone-pair: in-out
Service-policy inspect : p1
Class-map: most-traffic (match-any)
Match: protocol icmp
0 packets, 0 bytes
30 second rate 0 bps
Match: protocol ftp
0 packets, 0 bytes
30 second rate 0 bps
Match: protocol tcp
2 packets, 64 bytes
30 second rate 0 bps
Match: protocol udp
0 packets, 0 bytes
30 second rate 0 bps
Inspect
Number of Established Sessions = 1
Established Sessions
Session 3D4A32A0 (172.16.11.10:49300)=>(172.16.10.10:445) tcp SIS_OPEN/TCP_ESTAB
Created 00:00:40, Last heard 00:00:10
Bytes sent (initiator:responder) [0:0]
Session built in R1-WAAS and R2-WAAS from inside host to remote server.
R1-WAAS:
R1-WAAS#show statistics connection
Current Active Optimized Flows: 1
Current Active Optimized TCP Plus Flows: 1
Current Active Optimized TCP Only Flows: 0
Current Active Optimized Single Sided Flows: 0
Current Active Optimized TCP Preposition Flows: 0
Current Active Auto-Discovery Flows: 1
Current Reserved Flows: 10
Current Active Pass-Through Flows: 0
Historical Flows: 13
D:DRE,L:LZ,T:TCP Optimization RR:Total Reduction Ratio
A:AOIM,C:CIFS,E:EPM,G:GENERIC,H:HTTP,I:ICA,M:MAPI,N:NFS,S:SSL,W:WAN SECURE,V:VID
EO, X: SMB Signed Connection
ConnID Source IP:Port Dest IP:Port PeerID Accel RR
14 172.16.11.10:49185 172.16.10.10:445 c8:9c:1d:6a:10:61 TCDL 00.0%
R2-WAAS:
R2-WAAS#show statistics connection
Current Active Optimized Flows: 1
Current Active Optimized TCP Plus Flows: 1
Current Active Optimized TCP Only Flows: 0
Current Active Optimized TCP Preposition Flows: 0
Current Active Auto-Discovery Flows: 0
Current Reserved Flows: 10
Current Active Pass-Through Flows: 0
Historical Flows: 9
D:DRE,L:LZ,T:TCP Optimization RR:Total Reduction Ratio
A:AOIM,C:CIFS,E:EPM,G:GENERIC,H:HTTP,M:MAPI,N:NFS,S:SSL,V:VIDEO
ConnID Source IP:Port Dest IP:Port PeerID Accel RR
10 172.16.11.10:49185 172.16.10.10:445 c8:9c:1d:6a:10:81 TCDL 00.0%
Working Configuration of Client Side Router (R1) with WAAS and ZBF Enabled
R1#sh run Building configuration... Current configuration : 3373 bytes ! hostname R1 ! boot-start-marker boot bootstrap tftp c2900-universalk9-mz.SPA.153-3.M4.bin 255.255.255.255 boot system flash c2900-universalk9-mz.SPA.153-3.M4.bin boot-end-marker ! ip wccp 61 ip wccp 62 no ipv6 cef ! parameter-map type inspect global WAAS enable log dropped-packets enable max-incomplete low 18000 max-incomplete high 20000 multilink bundle-name authenticated ! license udi pid CISCO2911/K9 sn FGL171410K8 license boot module c2900 technology-package securityk9 license boot module c2900 technology-package uck9 license boot module c2900 technology-package datak9 hw-module pvdm 0/1 ! hw-module sm 1 ! class-map type inspect match-any most-traffic match protocol icmp match protocol ftp match protocol tcp match protocol udp ! policy-map type inspect p1 class type inspect most-traffic inspect class class-default drop ! zone security in-zone zone security out-zone zone security waas-zone zone-pair security in-out source in-zone destination out-zone service-policy type inspect p1 zone-pair security out-in source out-zone destination in-zone service-policy type inspect p1 ! interface GigabitEthernet0/0 description Connection to IPMAN FNN N6006654R bandwidth 6000 ip address 203.0.113.1 255.255.255.0 ip wccp 62 redirect in ip flow ingress ip flow egress zone-member security out-zone duplex auto speed auto ! interface GigabitEthernet0/1 ip address 172.16.11.1 255.255.255.0 no ip redirects no ip proxy-arp ip wccp 61 redirect in zone-member security in-zone duplex auto speed auto ! interface SM1/0 description WAAS Network Module Device Name dciacbra01c07 ip address 192.168.10.1 255.255.255.0 ip wccp redirect exclude in service-module ip address 192.168.183.46 255.255.255.252 !Application: Restarted at Sat Jan 5 04:47:14 2008 service-module ip default-gateway 192.168.183.45 hold-queue 60 out ! end
WAAS Branch Deployment with Inline Device
The figure shows a WAAS branch deployment that has an inline WAE device physically in front of the ISR. Since the WAE device is in front of the device, the Cisco firewall receives WAAS optimized packets, and as a result, Layer 7 inspection on the client side is not supported.
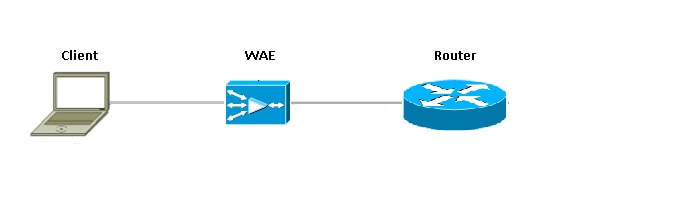
The router that runs the Cisco IOS® Firewall between WAAS devices, sees only optimized traffic. The ZBF feature watches for initial three way handshake (TCP option 33 and the sequence number shift) and it automatically adjusts expected TCP sequence window (doesn’t alter the sequence number in the packet itself). It applies full L4 stateful firewall features for the WAAS optimized sessions. WAAS transparent solution facilitates Firewall enforce per session stateful firewall and QoS Policies.
Details
- Firewall sees a normal TCP SYN packet with the 0x21 option and creates a session for it. There are no issues with the input or output interfaces since WCCP is not involved. The return SYN-ACK is not a redirected packet and firewall takes note of it.
- Firewall checks for the 0x21 option in the SYN-ACK and performs the sequence number jump, if necessary. It also turns off L7 inspection if the connection is optimized.
- It is to be observed that the only aspect which distinguishes this from the Router-1 scenario is that the return traffic is not redirected. There are no 2 half connections on this box.
Configuration
Standard ZBF configuration without any specific zone for WAAS traffic. Only Layer 7 inspection is not supported.
Restrictions for ZBF Interoperability with WAAS
- WCCP Layer 2 redirect method is not supported on Cisco IOS® firewall, it only supports Generic Routing Encapsulation (GRE) redirection.
- Cisco IOS® Firewall only supports WCCP redirection. If WAAS uses Policy Based Routing (PBR) in order to get the packets redirected, this solution does NOT ensure interoperability and hence unsupported.
- Cisco IOS® firewall do not perform L7 inspection on WAAS optimized TCP sessions.
- Cisco IOS® firewall requires ip inspect waas enable and ip wccp notify CLI commands for WCCP redirection.
- Cisco IOS® firewall with NAT and WAAS-NM interoperability is not supported at present.
- Cisco IOS® firewall WAAS redirection is only applied for TCP packets.
- Cisco IOS® firewall does not support active/active topologies.
- All the packets that belong to a session MUST flow through the Cisco IOS® firewall box.
Verify
There is currently no verification procedure available for this configuration.
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Related Information
Contributed by Cisco Engineers
- Prashant JoshiCisco TAC Engineer
- Namit AgarwalCisco TAC Engineer
- Dinkar SharmaCisco TAC Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback