Introduction
This document describes how to configure Cisco Identity Services Engine(ISE) as an external authentication for Cisco Catalyst SD-WAN GUI administration.
Prerequisites
Requirements
Cisco recommends that you have the knowledge of these topics:
- TACACS+ protocol
- Cisco ISE Device Administration
- Cisco Catalyst SD-WAN Administration
- Cisco ISE Policy Evaluation
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Identity Services Engine (ISE) Version 3.4 Patch2
- Cisco Catalyst SD-WAN Version 20.15.3
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Before You Begin
Starting from Cisco vManage Release 20.9.1, new tags are used in authentication:
- Viptela-User-Group: for user group definitions instead of Viptela-Group-Name.
- Viptela-Resource-Group: for resource group definitions.
Configure - Using TACACS+
Configure Catalyst SD-WAN Using TACACS+
Procedure
Step 1. (Optional) Define Custom Roles.
Configure your custom roles that fulfils your requirement, instead, you can use the default User Roles. This can be done from the tab Catalyst SD-WAN: Administration > Users and Access > Roles.
Create two Custom Roles:
- Admin Role: super-admin
- Read Only Role: readonly
This can be done from the tab Catalyst SD-WAN: Administration > Users and Access > Roles > Click > Add Role.
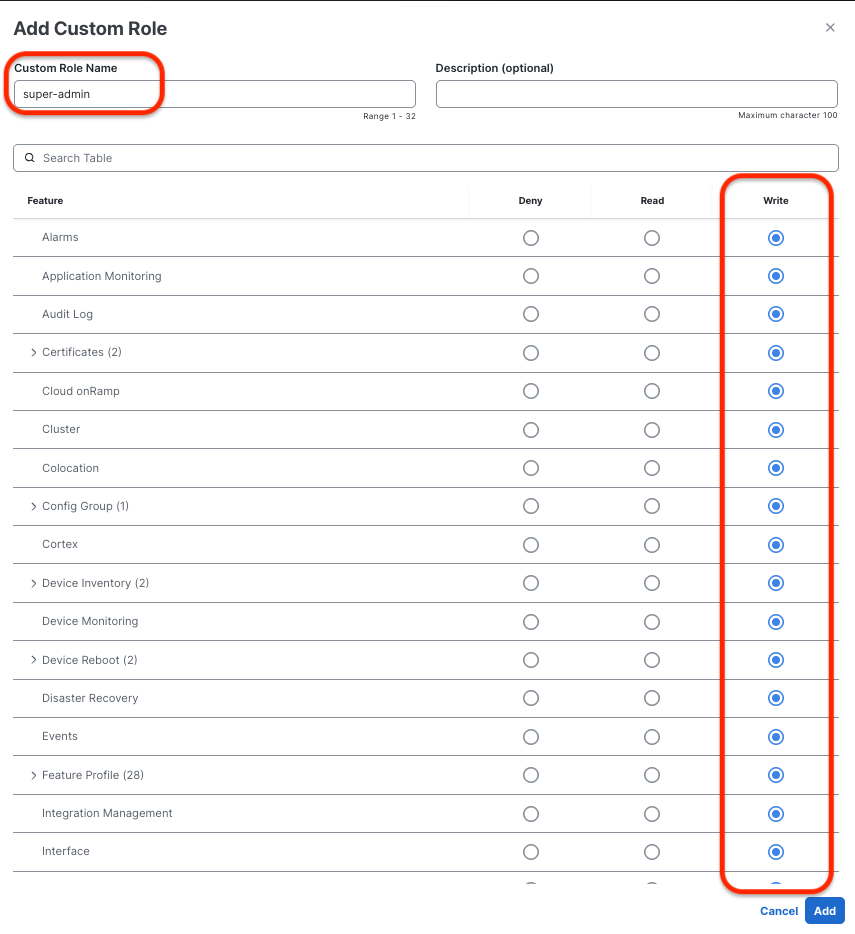 Admin Role (super-admin)
Admin Role (super-admin)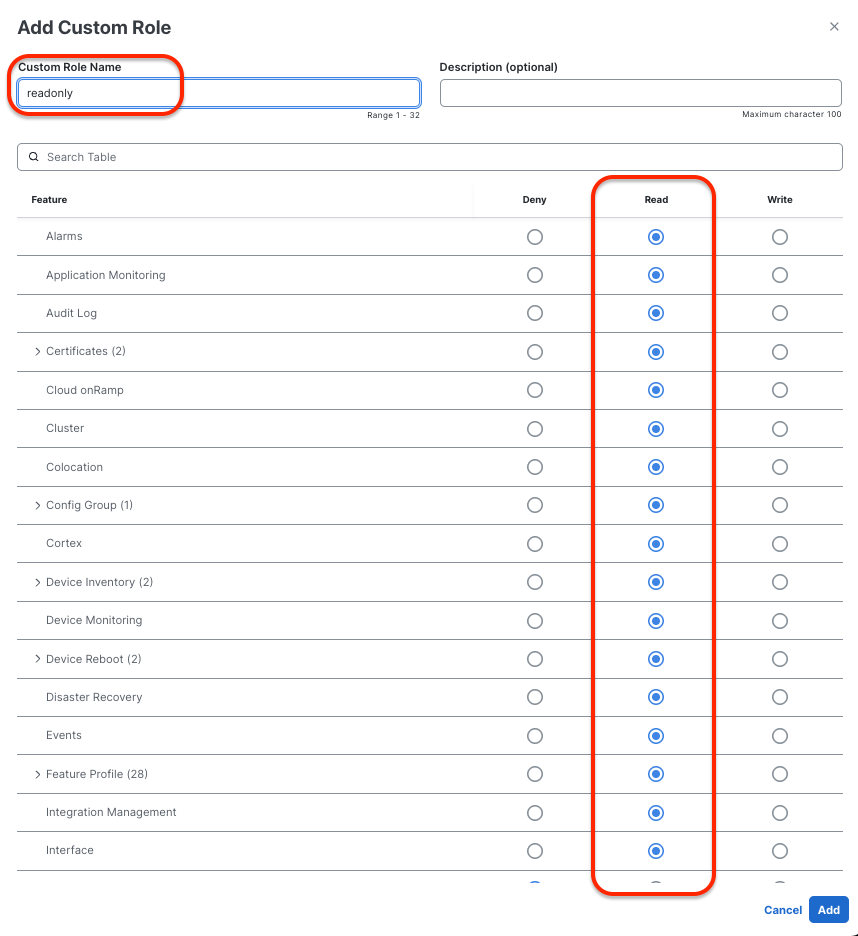 Read -Only Role (readonly)
Read -Only Role (readonly)
Step 2. Configure External Authentication using TACACS+ (CLI).
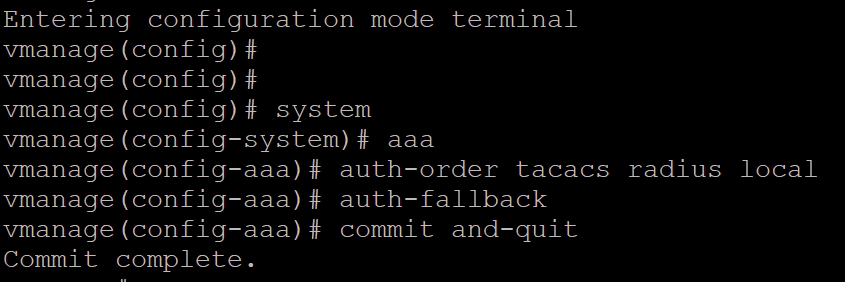 vManger CLI - TACACS+ Configuration
vManger CLI - TACACS+ Configuration
Configure ISE for TACACS+
Step 1. Enable Device Admin Service.
This can be done from the tab Administration > System > Deployment >Edit (ISE PSN Node)>Check Enable Device Admin Service.
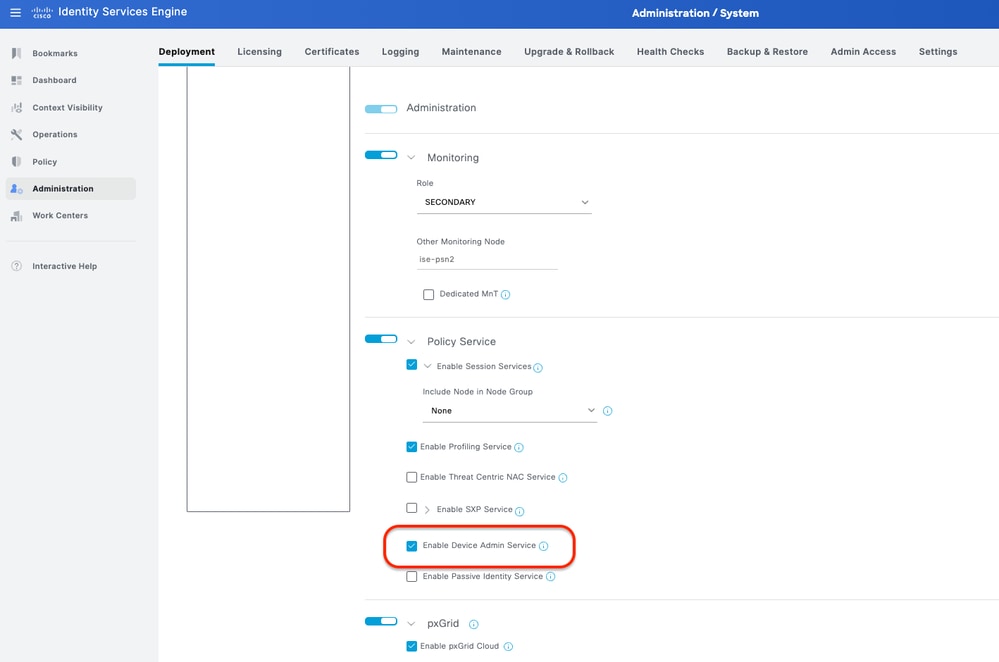 Enable Device Admin Service
Enable Device Admin Service
Step 2. Add Catalyst SD-WAN as a Network Device on ISE.
This can be done from the tab Administration > Network Resources > Network Devices.
Procedure
a. Define (Catalyst SD-WAN) Network Device name and IP.
b. (Optional) Classify Device Type for Policy Set condition.
c. Enable TACACS+ Authentication Settings.
d. Set TACACS+ Shared Secret.
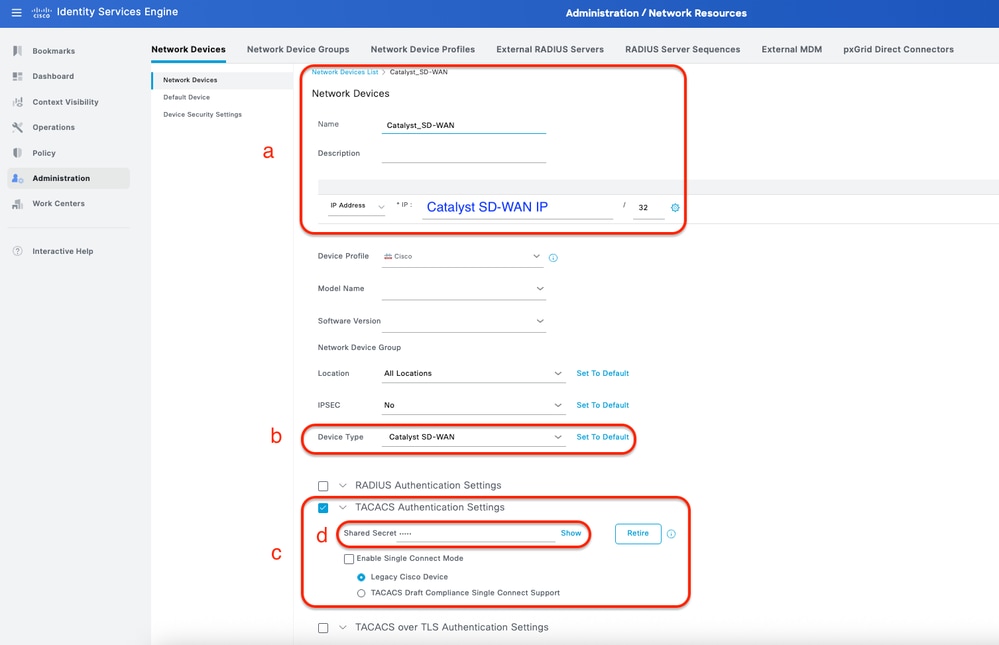 ISE Network Device (Catalyst SD-WAN) for TACACS+
ISE Network Device (Catalyst SD-WAN) for TACACS+
Step 3. Create TACACS+ Profile for each Catalyst SD-WAN role.
Create TACACS+ Profiles:
- Catalyst_SDWAN_Admin: For Super Admin Users.
- Catalyst_SDWAN_ReadOnly: For Read Only Users.
This can be done from the tab Work Centers > Device Administration > Policy Elements > Results > TACACS Profiles > Add.
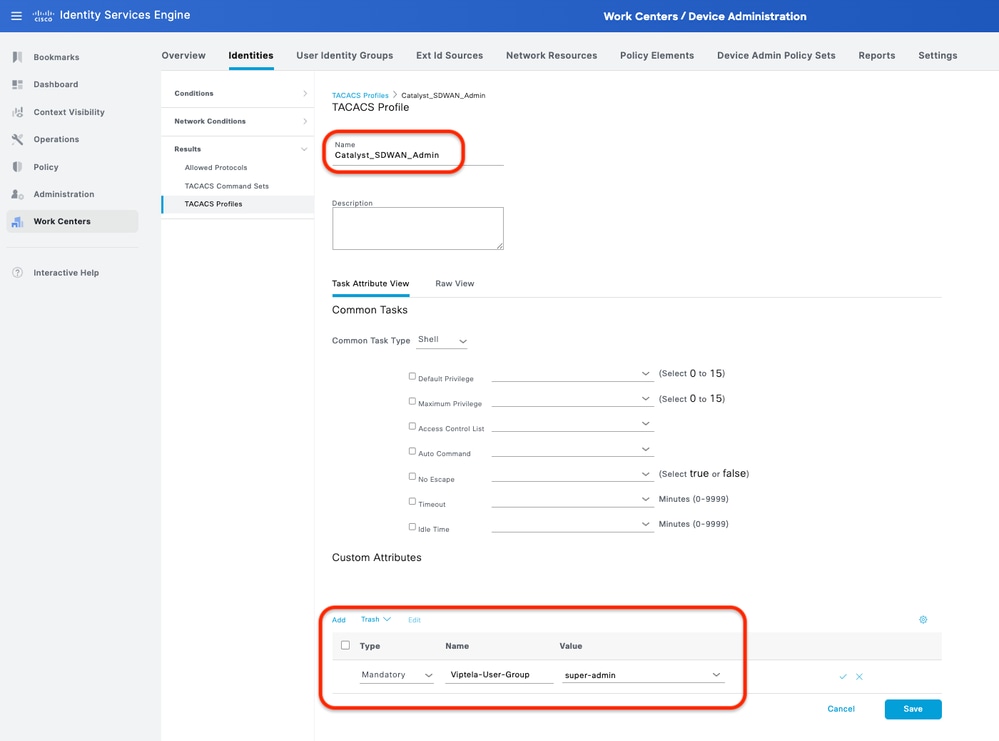 TACACS+ Profile - (Catalyst_SDWAN_Admin)
TACACS+ Profile - (Catalyst_SDWAN_Admin)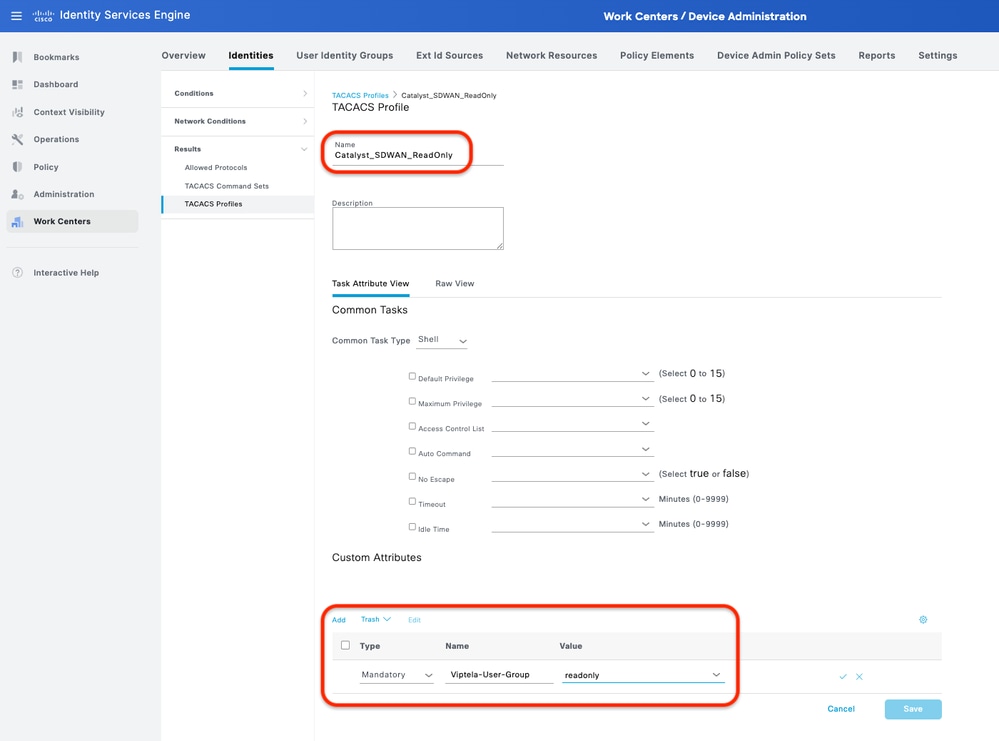 TACACS+ Profile - (Catalyst_SDWAN_ReadOnly)
TACACS+ Profile - (Catalyst_SDWAN_ReadOnly)
Step 4. Create User Group add Local Users as a member.
This can be done from the tab Work Centers > Device Administration > User Identity Groups.
Create two User Identity Groups:
- Super_Admin_Group
- ReadOnly_Group
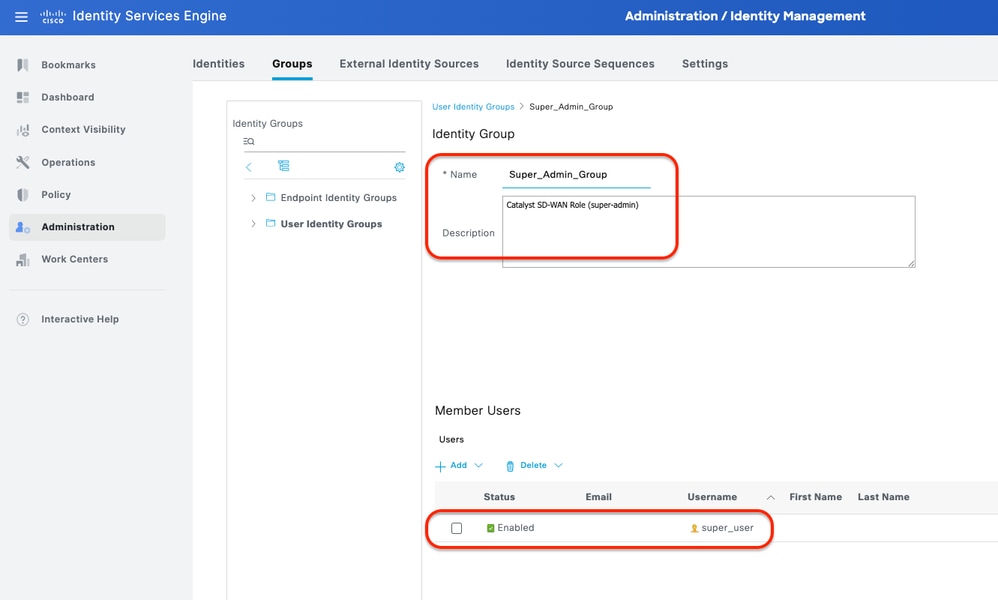 User Identity Group - (Super_Admin_Group)
User Identity Group - (Super_Admin_Group)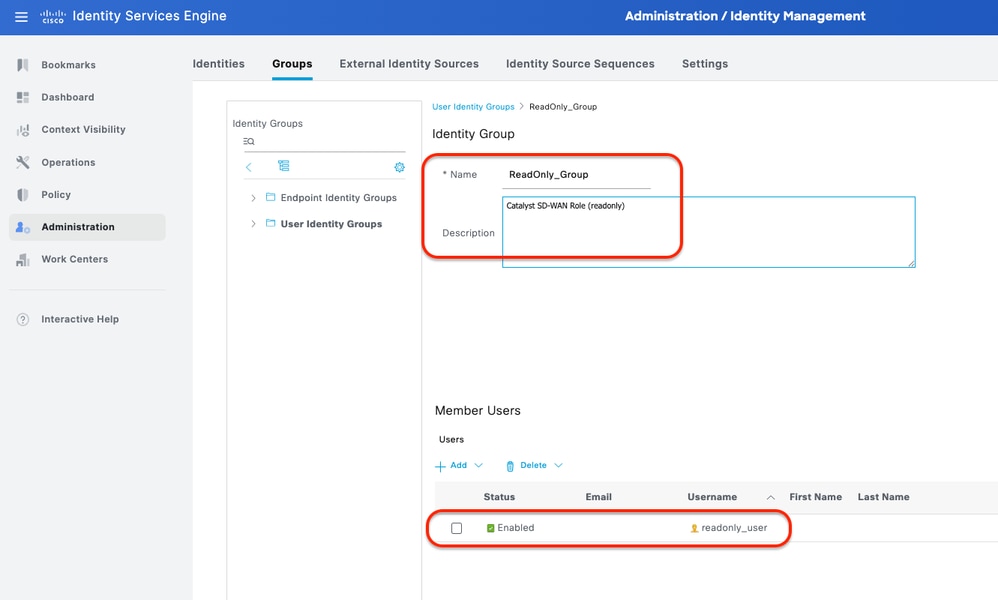 User Identity Group - (ReadOnly_Group)
User Identity Group - (ReadOnly_Group)
Step 5. (Optional) Add TACACS+ Policy Set.
This can be done from the tab Work Centers > Device Administration > Device Admin Policy Sets.
Procedure
a. Click Actions and choose (Insert new row above).
b. Define the Policy Set name.
c. Set the Policy Set Condition to Select Device Type you created previously on (Step 2 > b).
d. Set the Allowed protocols.
e. Click Save.
f. Click (>) Policy Set View to configure authentication and authorization rules.
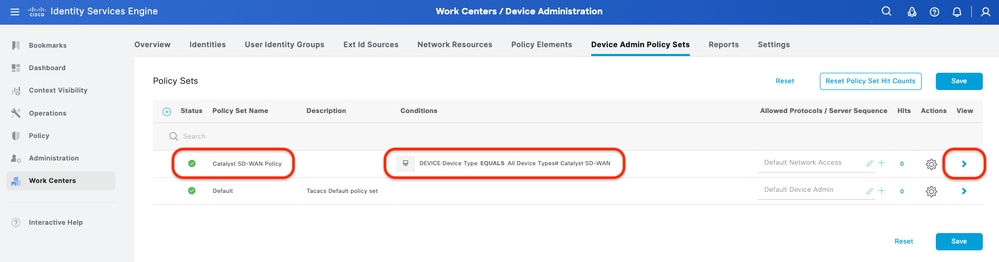 ISE Policy Set
ISE Policy Set
Step 6. Configure TACACS+ Authentication Policy.
This can be done from the tab Work Centers > Device Administration > Device Admin Policy Sets > Click (>).
Procedure
a. Click Actions and choose (Insert new row above).
b. Define the Authentication Policy name.
c. Set the Authentication Policy Condition and select Device Type you created previously on (Step 2 > b).
d. Set the Authentication Policy Use for Identity source.
e. Click Save.
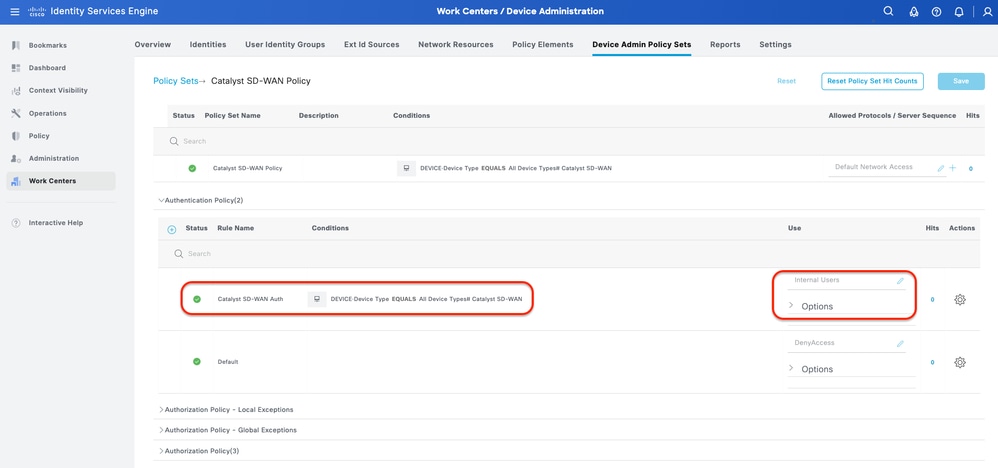 Authentication Policy
Authentication Policy
Step 7. Configure TACACS+ Authorization Policy.
This can be done from the tab Work Centers > Device Administration > Device Admin Policy Sets > Click (>).
This step to create Authorization Policy for each Catalyst SD-WAN Role:
- Catalyst SD-WAN Authz (super-admin): super-admin
- Catalyst SD-WAN Authz (readonly): readonly
Procedure
a. Click Actions and choose (Insert new row above).
b. Define the Authorization Policy name.
c. Set the Authorization Policy Condition and select User Group that you created in (Step 4).
d. Set the Authorization PolicyShell Profilesand select TACACS Profilethat you created in (Step 3).
e. Click Save.
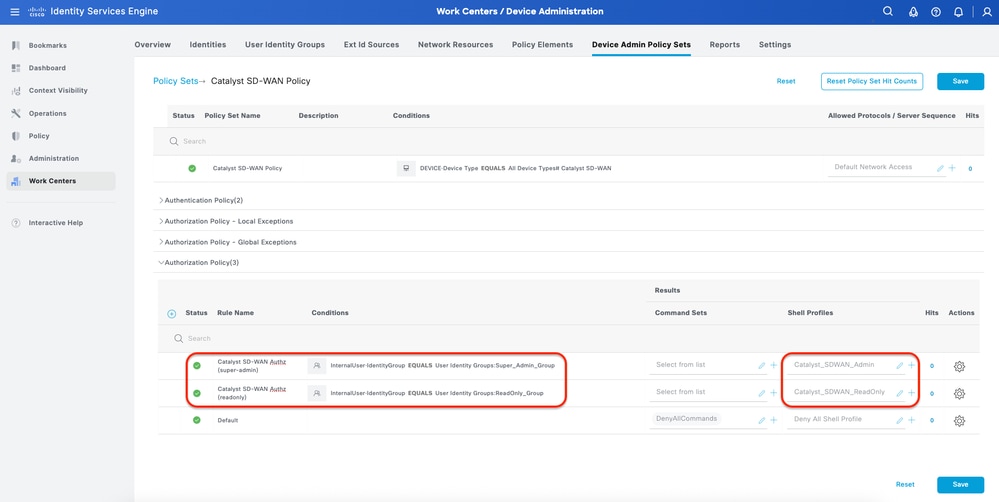 Authorization Policy
Authorization Policy
Verify TACACS+ Configuration
1- Display Catalyst SD-WAS User Sessions Catalyst SD-WAN: Administration > Users and Access > User Sessions.
You can view the list of external users who have logged in through RADIUS for the first time. The information that is displayed includes their usernames and roles.
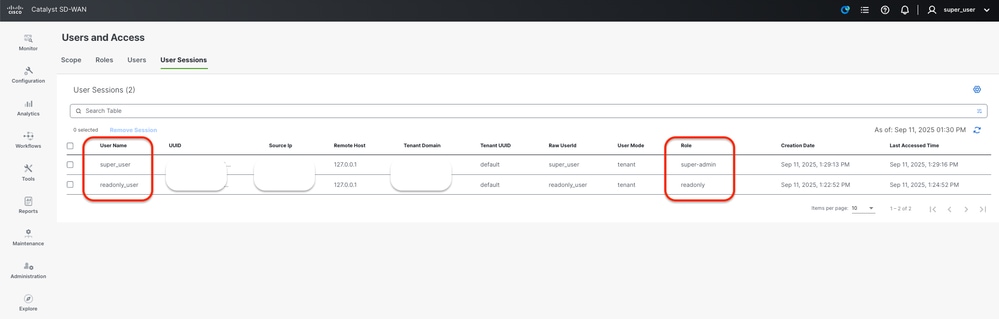 Catalyst SD-WAS User Sessions
Catalyst SD-WAS User Sessions
2- ISE - TACACS Live-Logs Operations > TACACS > Live-Logs.
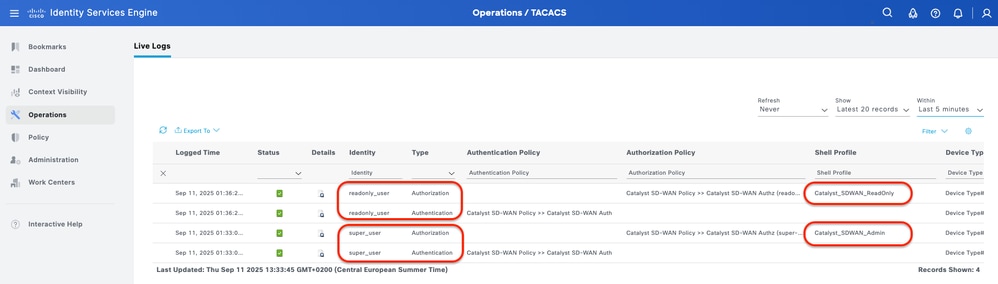 Live-Logs
Live-Logs
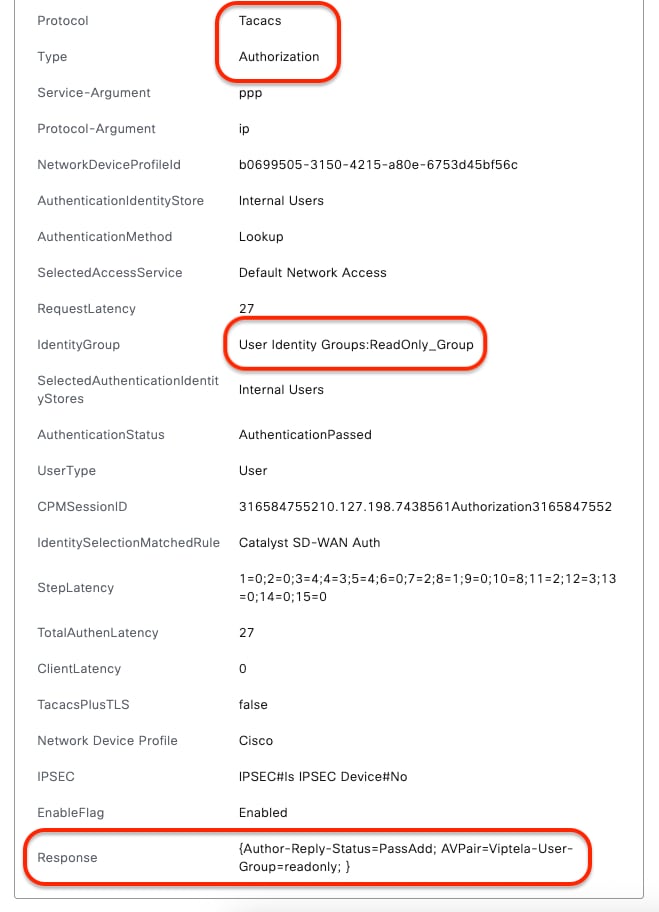 Detailed Live-Logs - (readonly)
Detailed Live-Logs - (readonly)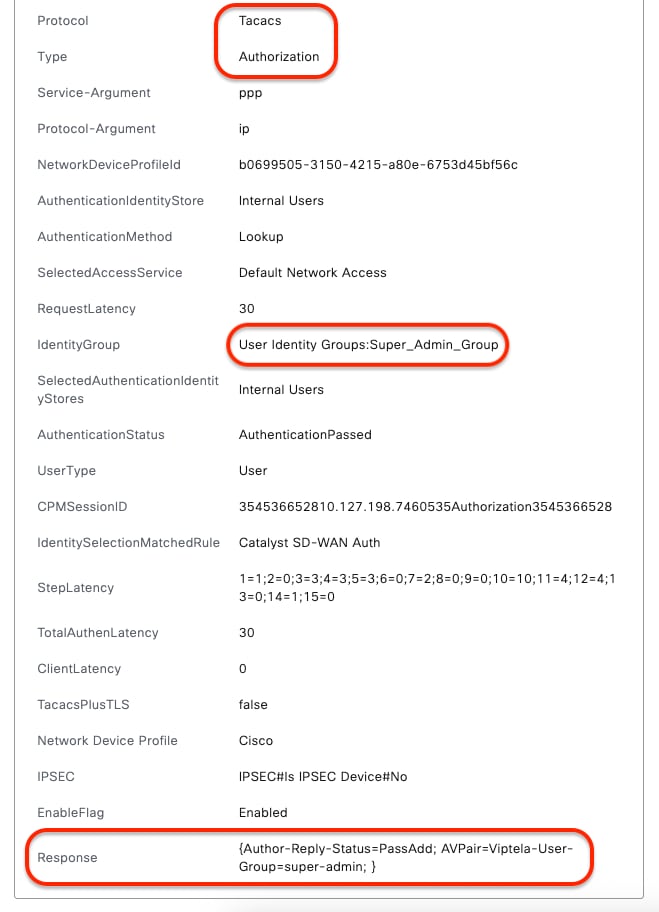 Detailed Live-Logs - (super-admin)
Detailed Live-Logs - (super-admin)
Troubleshoot
There is currently no specific diagnostic information available for this configuration.
References

















 Feedback
Feedback