Field Notice: FN74321 - Cisco Identity Services Engine Fails to Join Microsoft Active Directory Domain Services Hosted on Windows Server 2025 - Software Upgrade Recommended
Available Languages
Notice
THIS FIELD NOTICE IS PROVIDED ON AN "AS IS" BASIS AND DOES NOT IMPLY ANY KIND OF GUARANTEE OR WARRANTY, INCLUDING THE WARRANTY OF MERCHANTABILITY. YOUR USE OF THE INFORMATION ON THE FIELD NOTICE OR MATERIALS LINKED FROM THE FIELD NOTICE IS AT YOUR OWN RISK. CISCO RESERVES THE RIGHT TO CHANGE OR UPDATE THIS FIELD NOTICE AT ANY TIME.
Products Affected
| Affected Software Product | Affected Release | Affected Release Number | Comments |
|---|---|---|---|
| Identity Services Engine System Software | 3 | 3.1.0, 3.2.0, 3.3.0, 3.4.0 | For ISE releases 3.1 P10 and earlier For ISE releases 3.2 P7 and earlier For ISE releases 3.3 P7 and earlier For ISE releases 3.4 unpatched and P1 |
Defect Information
| Defect ID | Headline |
| CSCwn62873 | Cisco Identity Services Engine (ISE) fails to join Microsoft Active Directory (AD) domains hosted on Windows Server 2025 |
Problem Description
Cisco Identity Services Engine (ISE) fails to join Microsoft Active Directory Domain Services (AD DS) that are hosted on Windows Server 2025. This prevents Cisco ISE from establishing a trusted connection with the Active Directory (AD) environment, which impacts services that rely on an AD integration, such as the following:
- Authentication using AD users
- Authorization using external AD groups
- PassiveID Agent integration
Background
Microsoft Windows Server 2025 introduces several changes to AD DS that affect password handling. One of the key changes involves the Legacy Security Account Manager (SAM) Remote Procedure Call (RPC) password change behavior.
In Windows Server 2025, secure protocols, such as Kerberos, are the preferred method for domain user password changes. On domain controllers, the latest SAM RPC password change method, SamrUnicodeChangePasswordUser4, which uses Advanced Encryption Standard (AES), is accepted by default when called remotely.
However, the following legacy SAM RPC password change methods are now blocked by default when called remotely:
- SamrChangePasswordUser
- SamrOemChangePasswordUser2
- SamrUnicodeChangePasswordUser2
Additionally, for domain users that are members of the Protected Users group and for local accounts on domain member computers, all remote password changes through the legacy SAM RPC interface are blocked by default — including SamrUnicodeChangePasswordUser4.
These changes impact the ability of Cisco ISE to join Active Directory domains hosted on Windows Server 2025, as the integration process relies on password change mechanisms that are no longer permitted by default.
For more details, see What's New in Windows Server 2025.
Problem Symptom
When Cisco ISE attempts to join Microsoft AD hosted on Windows Server 2025, the operation fails.
Steps to Reproduce Join Operation Failure
- Navigate to Administration > Identity Management > External Identity Sources > Active Directory > Add
- Configure the Join Point Name and Active Directory Domain, then click Submit
If the AD admin user has the password does not expire option enabled, the following error is observed:
- Integration Failure Message:
Join Operation Failed: ASN.1 failed call to system time library
- Error Code:
41701
- Error Name:
LW_ERROR_KRB5_ASN1_BAD_TIMEFORMAT
The following screenshot shows the error as it appears during the join attempt:
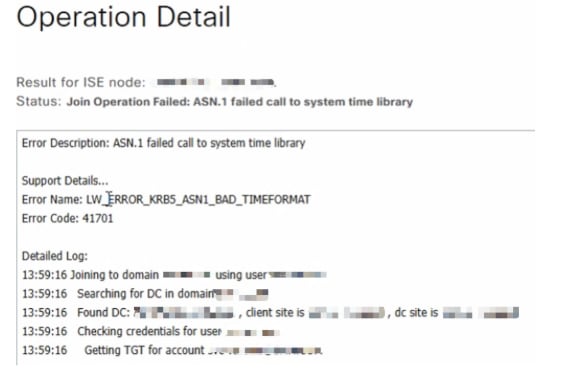
If the AD admin user has the password does not expire option disabled, the following error is observed:
- Integration Failure Message:
Join Operation Failed: Access is denied
- Error Code:
5
- Error Name:
ERROR_ACCESS_DENIED
The following screenshot shows the error as it appears during the join attempt:
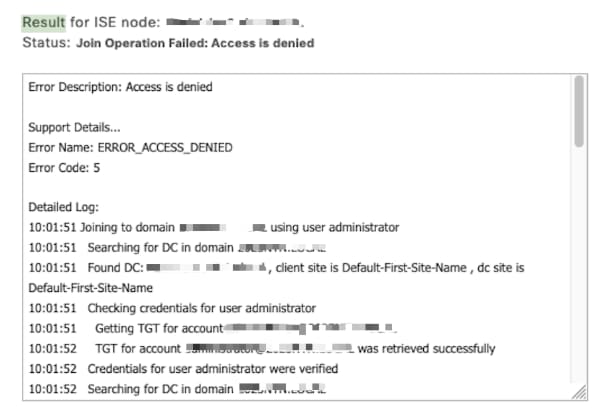
Note: This problem occurs when attempting to join Cisco ISE to AD on Windows Server 2025 for the first time. Existing Cisco ISE–AD integrations continue to function after a Windows Server upgrade until the Cisco ISE appliance account password expires and a password change is required.
Workaround/Solution
Solution
To address this issue, both a Cisco ISE software update and a Windows Server 2025 Domain Controller (DC) Group Policy configuration change are required:
1. Update the Cisco ISE software
Customers must open a TAC case to obtain the required hot patch. Hot patches are available for the following Cisco ISE releases:
- ISE 3.1 Patch 10
- ISE 3.2 Patch 7
- ISE 3.3 Patch 4, Patch 5, Patch 6, Patch 7
- ISE 3.4 Patch 1
2. Update Domain Controller Group Policy configuration
On the Windows Server 2025 Domain Controller:
- Open PowerShell as Administrator.
- Type gpedit.msc and press Enter to open the Local Group Policy Editor.
- Navigate to Computer Configuration > Administrative Templates > System > Security Account Manager > Configure SAM change password RPC methods policy
- Change the policy to Allow all change password RPC methods
Note: gpedit.msc (Group Policy Editor) modifies the local machine policy, which can be overridden by a domain-level Group Policy Object (GPO). If a domain-level change is required, use gpmc.msc (Group Policy Management Console) and apply the same steps through the domain GPO.
Revision History
| Version | Description | Section | Date |
| 1.0 | Initial Release | — | 2025-OCT-29 |
For More Information
For further assistance or for more information about this field notice, contact the Cisco Technical Assistance Center (TAC) using one of the following methods:
Receive Email Notification About New Field Notices
To receive email updates about Field Notices (reliability and safety issues), Security Advisories (network security issues), and end-of-life announcements for specific Cisco products, set up a profile in My Notifications.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
This Document Applies to These Products
Unleash the Power of TAC's Virtual Assistance
 Feedback
Feedback