Cisco User and Breach Protection Suite At a GlanceA stronger security posture: proactive prevention and accelerated detection and response.
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Security teams today face a mix of challenges— from sophisticated adversaries to simple, persistent attacks that exploit organizations with lower security maturity. Attackers often target users as the weakest link, using techniques like phishing and credential theft to gain initial access. Identity-based attacks accounted for 60% of incidents in 2024, according to Cisco Talos. Disparate security tools further burden defenders, leading to alert overload, slower response times, and weaker security outcomes.
To help organizations overcome these threats, the Cisco User and Breach Protection Suite delivers a unified, end-to-end approach. It puts users at the center of your security strategy while empowering security teams to accelerate detection and response. By integrating the Cisco security portfolio across endpoint, email, network, identity, firewall, access to applications, and cloud, the suite provides comprehensive protection with simplified management. This unified approach strengthens your security posture — wherever you are in your security journey — while reducing complexity and operational overhead.
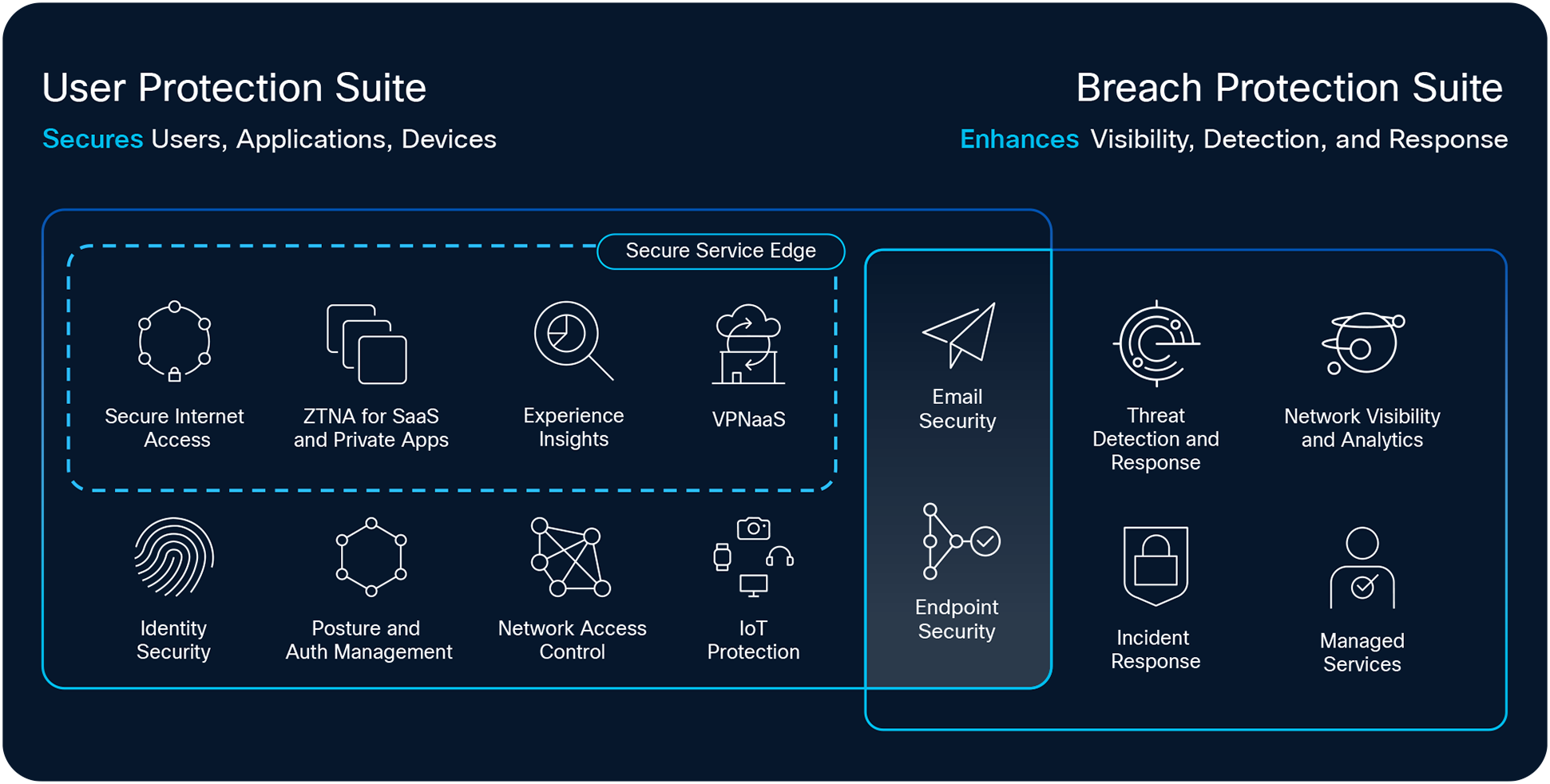
User and Breach Suite Composition
● Better Efficacy: Stop threats like ransomware and identity-based attacks like Business Email Compromise with layered protection, high-fidelity telemetry, and AI-driven insights. Integrated products work better together to defend against the evolving threat landscape and provide clear verdicts for decisive action.
● Better Experiences: Enable a seamless and secure experience for the hybrid workforce, anywhere. Reduce user friction by simplifying authentication and access. For security teams, streamline investigations, prioritize threats, and simplify management with unified capabilities.
● Better Economics: Ease operational burdens and support vendor consolidation by leveraging integrated protection. Combat increasing security complexity and reduce breach risk with a unified approach. Elevate analyst skills through response guidance and automation to enhance efficiency and effectiveness.
● Unified, Intelligent Protection: A cloud-based platform that leverages AI, cross-domain telemetry (including native network visibility), and Cisco Talos threat intelligence for intelligent, integrated protection across your environment.
● Simplified Security Operations: Solutions are designed to reduce the burden on your security team by simplifying operations while providing world-class protection. Centralized management and a single agent reduce complexity.
● Strategic Value and Comprehensive Coverage: Cisco Security Suites bring together the right tools for comprehensive protection and vendor consolidation, delivering exceptional value for your evolving security needs.
How it works together (Example: Phishing attack)
Attackers frequently target users as the weakest link, often through phishing campaigns. Once an attacker gains access to a valid account, it can take an average of 210 days to detect a breach, providing ample time for them to escalate privileges, move laterally, and significantly increase the cost and damage of the breach.
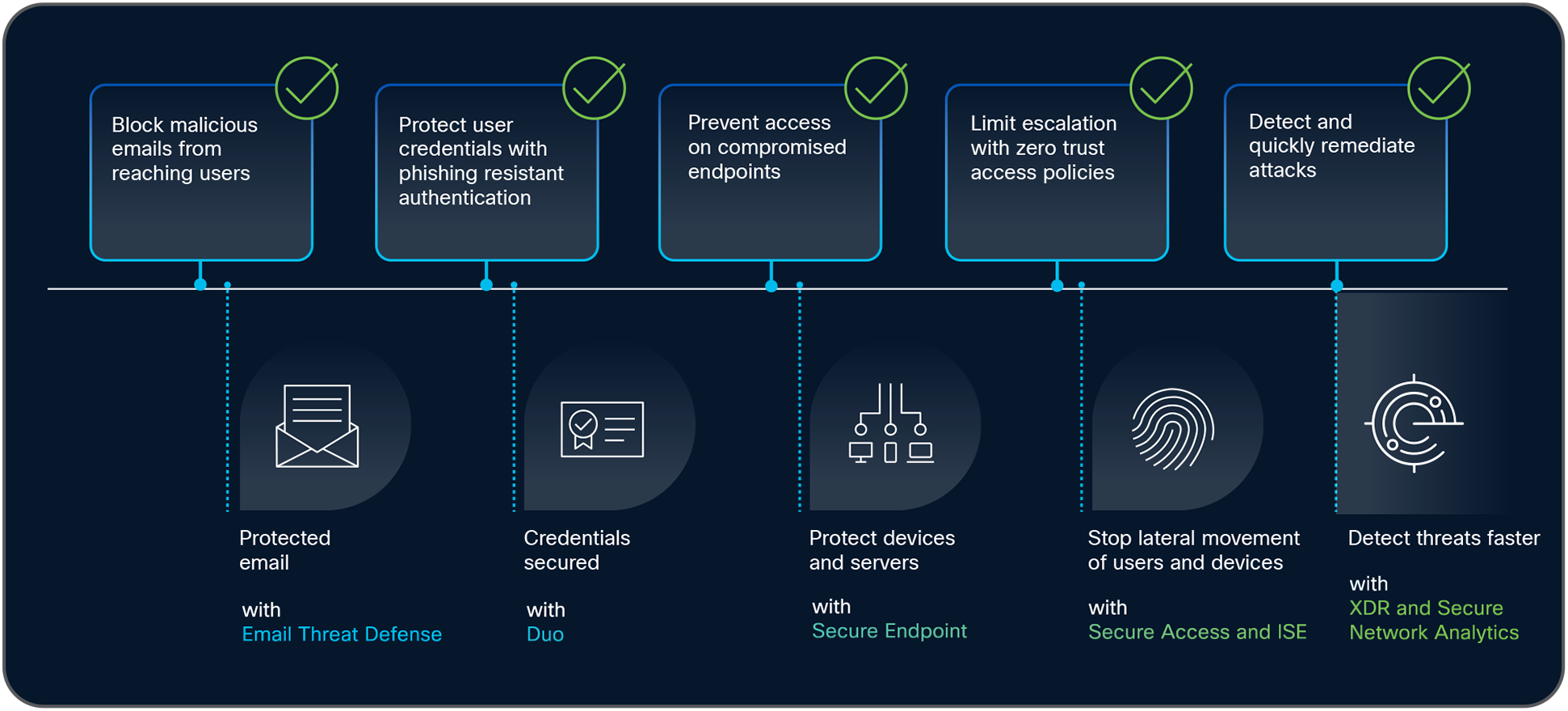
Layered Approach to Security
Consider a common phishing scenario: A user receives a fraudulent email, perhaps disguised as an urgent request from HR to fix an expense report. If they click a malicious link, log into a fake website, and even accept a push notification, an attacker could gain access to their account and begin to move laterally across the network.
Here’s how Cisco’s User and Breach Protection Suite provides a layered, integrated defense:
● Secure Email Threat Defense: Proactively blocks malicious emails (like phishing attempts) from ever reaching the user’s inbox, stopping the attack at its first point of entry.
● Duo: Even if an email slips through, Duo provides phishing-resistant authentication, protecting user credentials and preventing attackers from logging in, even with stolen passwords.
● Secure Endpoint: Should malware be downloaded onto a device, Secure Endpoint detects and blocks it, working together with Duo to prevent fraudulent access attempts.
● Secure Access/ISE: If an attacker manages to gain a foothold, Secure Access/ISE enforce zero-trust policies, preventing damage by stopping lateral movement across the network for both users and IoT devices.
● Cisco XDR: Acting as the central intelligence hub that natively integrates and correlates data from all these solutions, Cisco XDR provide a unified view of the incident. This comprehensive telemetry allows security teams to prioritize threats, understand the full scope of an attack, and respond rapidly before significant damage occurs.
This integrated approach empowers security teams with full visibility into the attack chain, enabling proactive prevention and accelerated response for improved security outcomes and operational efficiency.
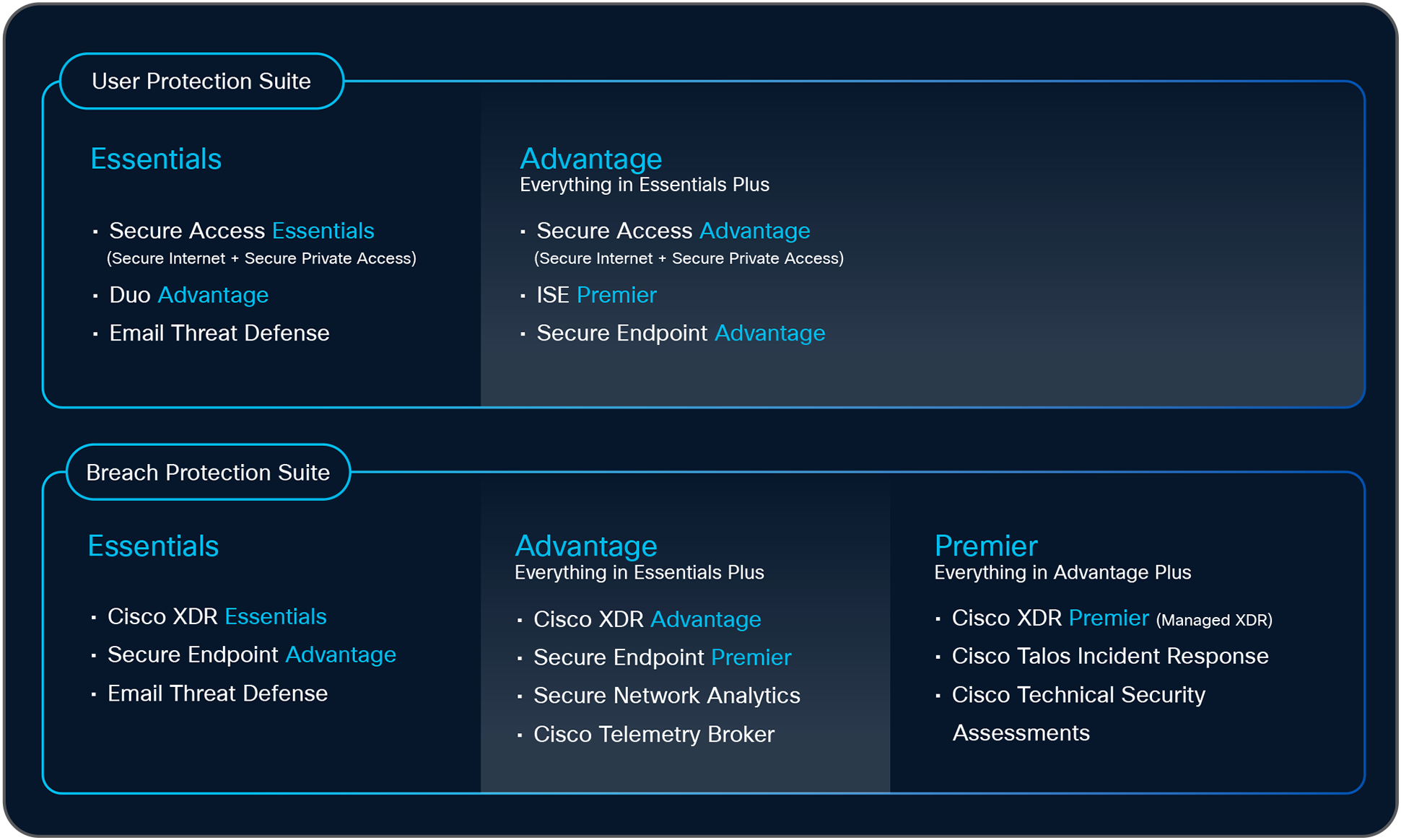
Mix and Match Tiers of User & Breach Protection Suite
Ready to learn more? Connect with a Cisco Security Suites expert today.