-
Cisco MDS 9000 Family Fabric Manager Quick Configuration Guide
-
Index
-
Preface
-
Overview
-
Initial Switch Configuration
-
Installing Fabric Manager
-
Fabric Manager Client
-
Configuring VSANs and Interfaces
-
Configuring Zones and Zone Sets
-
Launching Fabric Manager in Cisco SAN-OS Releases Prior to 3.2(1)
-
Quick Config Wizard
-
Configuring Static Domain IDs and Persistent FC IDs
-
Configuration Files
-
Table Of Contents
Overview of VSANs, Interfaces, Zones, and Zone Sets
Overview
The primary objective of the Cisco MDS 9000 Family Fabric Manager Quick Configuration Guide is to get you started with configuring your Cisco MDS 9000 Family switch using the Cisco Fabric Manager graphical user interface (GUI).
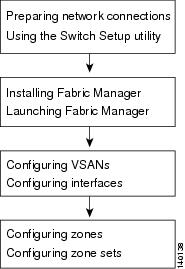
Figure 1-1 outlines the organization of the guide and it also serves as a flowchart describing the major steps used in the installation and configuration of the fabric.
Figure 1-1 Installation and Configuration Flowchart
Start the process by setting up the hardware and performing the initial switch setup using the CLI. Then install Cisco Fabric Manager, and use it to configure VSANs, interfaces, zones, and zone sets, which are the minimum requirements for creating a fabric.
Note
After setting up the switch, if you choose to perform further configuration tasks using the CLI, refer to the Cisco MDS 9000 Family Configuration Guide.
This chapter includes the following sections:
•
Overview of VSANs, Interfaces, Zones, and Zone Sets
Overview of Fabric Manager
Fabric Manager provides a graphical user interface (GUI) that displays real-time views of your network fabrics and lets you manage the configuration of Cisco MDS 9000 Family devices and third-party switches. It provides an alternative to the CLI for most switch configuration commands.
Fabric Manager includes management applications, such as Fabric Manager Client, Fabric Manager Server, Device Manager, Performance Manager, and Fabric Manager Web Server. For further details regarding the various management components of Fabric Manager, refer to the Cisco MDS 9000 Family Fabric Manager Configuration Guide.
Fabric Manager Server must be started before running Fabric Manager. On a Windows PC, Fabric Manager Server is installed as a service. This service can then be administered using the Windows Services applet in the control panel. Fabric Manager Server discovers the physical and logical fabric, and listens for SNMP traps, syslog messages, and Performance Manager threshold events.
See Chapter 3, "Installing Fabric Manager," for instructions on installing Fabric Manager. See Chapter 4, "Fabric Manager Client" for further details on using the Fabric Manager Client.
Overview of VSANs, Interfaces, Zones, and Zone Sets
VSANs, interfaces, zones, and zone sets comprise the minimum configuration required for a Cisco MDS 9000 Family switch to be up and running.
Virtual SANs can scale SANs beyond current limitations in a resilient, secure, cost-effective, and manageable fashion. Using VSANs, you can build larger consolidated fabrics and still maintain the required security and isolation between applications beyond what is currently offered through zoning. A VSAN can create separate virtual fabrics on top of the same redundant physical infrastructure.
Interfaces enable a switch to relay frames from one data link to another. You must define the characteristics of the interfaces through which the frames are sent and received. The configured interfaces can be Fibre Channel interfaces, the management interface (mgmt0), or VSAN interfaces.
The zoning service within a Fibre Channel fabric can provide security between devices sharing the same fabric. The primary goal is to prevent certain devices from accessing other devices within the fabric. With many different types of servers and storage devices on the network, the need for security is critical. For example, if a host was to gain access to a disk being used by another host, potentially with a different operating system, the data on this disk could get corrupted. To avoid any compromise of critical data within the SAN, zoning allows you to overlay a security map dictating which devices, namely hosts, can communicate with which targets, reducing the risk of data loss.
VSANs and zoning within the MDS 9000 Family of products aid the SAN designer in building secure and manageable networking environments while optimizing the use and cost of switching hardware. VSANs are used to divide a redundant physical SAN infrastructure into separate virtual SAN islands, each with its own set of Fibre Channel fabric services. By each VSAN supporting an independent set of Fibre Channel services, a VSAN-enabled infrastructure can house numerous applications without concern for fabric resource or event conflicts between these virtual environments. Once the physical fabric has been divided, zoning is then used to implement a security layout within each VSAN that is tuned to the needs of each application within each VSAN.
VSANs are first created as isolated fabrics within a common physical topology. Once VSANs have been created, individual unique zone sets can then be applied as necessary within each VSAN.
See Chapter 5, "Configuring VSANs and Interfaces," and Chapter 6, "Configuring Zones and Zone Sets," for details on configuring VSANs, interfaces, zones, and zone sets.

 Feedback
Feedback