-
CEPM User Guide
-
Preface
-
Cisco Enterprise Policy Manager
-
Overview of the PAP Console
-
Login Page and Home Page
-
Manage Entities
-
Manage Entitlements
-
Auditing and Reporting
-
System Config
-
Delegated Administration
-
Policy Combining Algorithm and Obligation
-
PAP User Login Authentication Using LDAP and SSO
-
Open Source License Acknowledgements
-
Table Of Contents
Entitled Groups for a Resources
Auditing and Reporting
Auditing and Reporting enables the user to monitor the activities carried on the application at any point of time. It is a regular observation and recording of ongoing activities. The user can view a variety of logs generated, such as runtime log, admin log, various permitted resources and their entitlements, and also the user can review SoD roles for any particular role.
This chapter explains the various operations that you can perform on the Auditing and Reporting tab in the PAP administration console. This Chapter contains the following sections:
•
Audit Entitlements—This feature provides audit entitlements for users, groups, and roles.
•
Resources—This feature allows you to view a list of roles, users and groups that are permitted for any resource.
•
Exception Policies—This feature allows you to find out which resources are not allowed for a selected user, group, and role irrespective of the role that is associated
•
Audit Reports—This feature displays reports and logs related to the create, update, and delete operations carried out on various PAP entities, such as users, groups, roles, resources, user types, group types, role types, resource types, contexts, role bundles, user attribute sources, and application attribute sources.
•
Audit SoD Violations—This feature displays SoD violated roles.
•
Manage Log Level—This feature sets the log level to one of the following values, DEBUG, INFO, WARN, ERROR or FATAL.
•
Handler Status—This feature displays the list of active handlers.
•
Sync Failure Events—This feature displays a list of sync handler error messages.
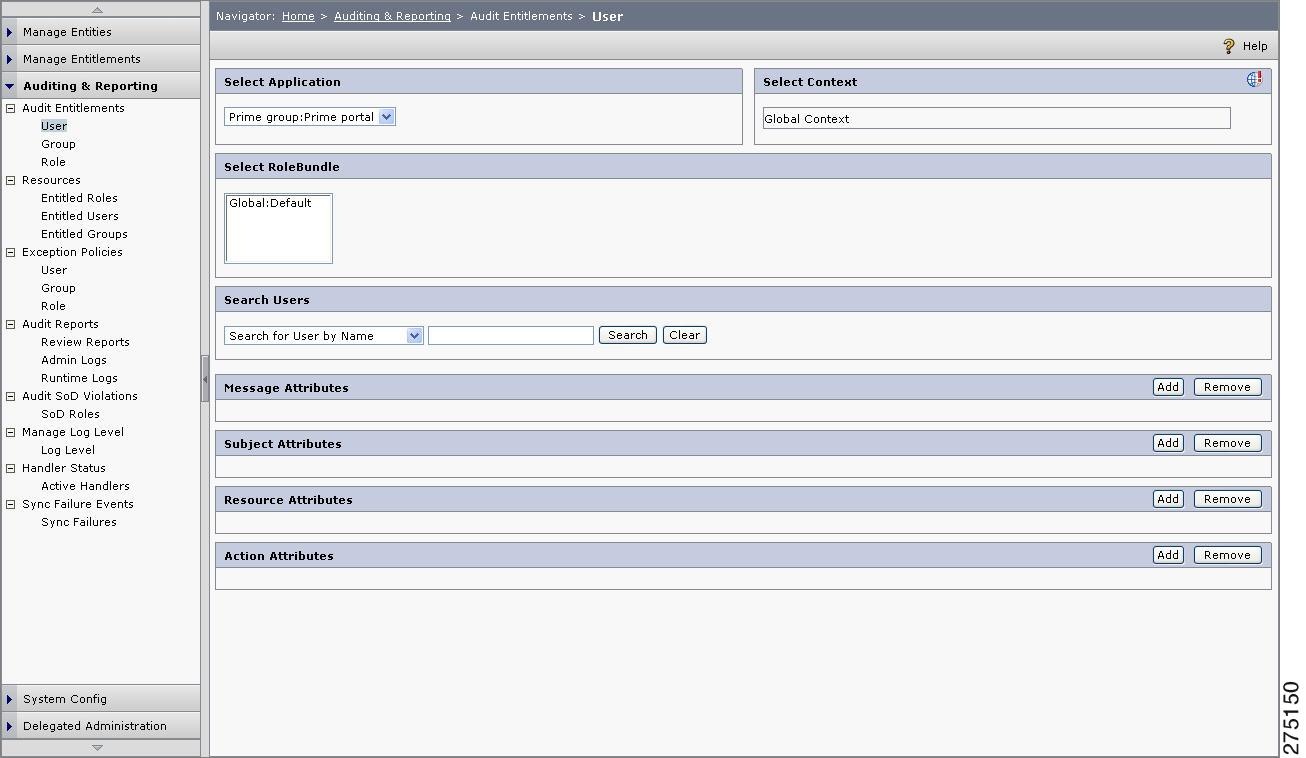
Figure 6-1 Audit Entitlement Home page
This section in the admin console allows you to view details pertaining to individual users, groups, roles, and resources. Apart from these, it also enables you to review entitlements, allow and deny policies on a selected resource. For example, in a banking organization, to know about who all are authorized to view details of Account No: xxxx009, you can use `Users entitled to a resource' feature on the Monitor Entitlements page. Search for that particular resource named Account No, xxxx009 and clickthe Account No to view all Allowed users to that resource.
Audit Entitlements
The Cisco Enterprise Policy Manager (CEPM) has extensive capabilities to review policies as well as analyze audit logs (administration and decision). The CEPM provides the users information on who has access to what and why a particular user or group of users are allowed or denied access to a resource. This allows users to quickly analyze policy settings from the administration console.
The Review Entitlements functionality illustrates what resources have been granted to a user at any point in time. It makes the user explore the details related to the user, group, role, and resource entitlement.
Note
Evaluation of rules in which $resource-id or $action-id is selected in the LHS:
In CEPM, when $resource-id is selected as the Resource Attribute in the LHS, the resource name passed in the xacmlRequest is taken as its value. Similarly, if Resource is selected in the RHS, the value is the requested resource or the child resource.
While configuring rule on an Allow policy for a resource or action, if $resource-id (or $action-id) is selected as the ResourceAttribute (or ActionAttribute) in the LHS and Resource (or Action) is selected in the RHS, a mismatch in the decision can be observed in the PAP UI in the Auditing and Reporting tab because of the AJAX tree limitation. At the same time, the right decision is rendered in the Runtime log (in the UI) and in the server log.
For example, create an 'Allow' policy for Mary for the resource Prime group:Prime portal:Send trades and configure the rule (LHS=$resourceid, Operator=EQ or In, RHS=Resource) on that policy.
In the UI, if you check the decision for Mary in a Home > Auditing and Reporting > Audit Entitlements > users tab, the resource is rendered in with a red label (denied) but at the same time the Runtime log for the same resource shows Permit for the same user.
This happens because, in the Auditing and Reporting tab, by clicking on Prime group:Prime portal, the evaluation is done based on the $resourceid=Prime group:Prime portal and RHS=Resource is replaced with Prime group:Prime portal, Prime group:Prime portal:Send Trades, Prime group:Prime portal:View Reports. Hence the resource is rendered with a red label for Prime group:Prime portal:Send Trades,View reports.
If you ask the decision for Prime group:Prime portal:Send Trades by clicking on Prime group:Prime portal:Send Trades, the evaluation happens based on the $resourceid=Prime group:Prime portal:Send Trades and RHS=Resource is replaced with Prime group:Prime portal, Prime group:Prime portal:Send Trades and Prime group:Prime portal:View Reports while evaluating each resource and again the resource is rendered in red label for Prime group:Prime portal:Send Trades,View reports.
The same scenario for rule evaluation can also be observed in the case of $Action-id.
Audit Entitlements for User
To review entitlement for a particular user to verify how the policy comes into effect, you must:
Step 1
Choose Auditing and Reporting > Audit Entitlement > User.
The User page is displayed.
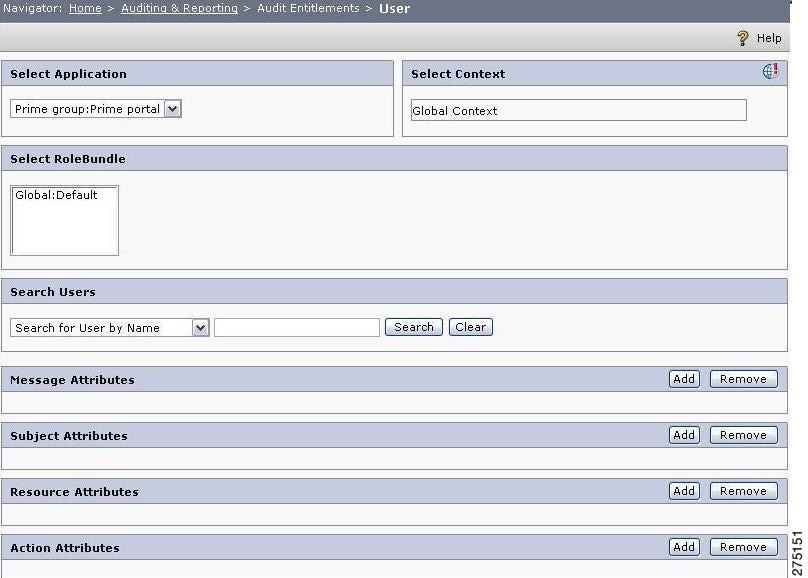
Figure 6-2 Audit Entitlement for Users
Step 2
Select the Application, Context, and RoleBundle from the drop-down list.
Step 3
To search for a particular user, enter the full name, first, or last name in the search user box. To view all users under the selected combination, leave the Search Users field blank.
Step 4
Enter the message attribute (if any). Message attributes are attributes extracted from an Xpath without giving the full path. While creating a PIP rule, you can select the message attribute as an attribute for defining a condition.
Step 5
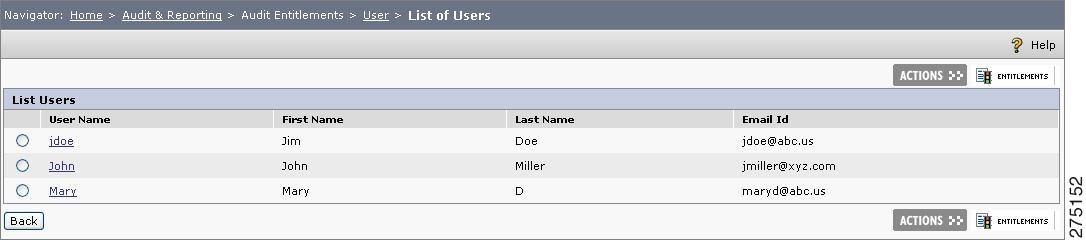
Click Search. A list of users (as per the search criteria entered in the page) is displayed for the selected application or application group.
Figure 6-3 Audit Entitlement Users search
Step 6
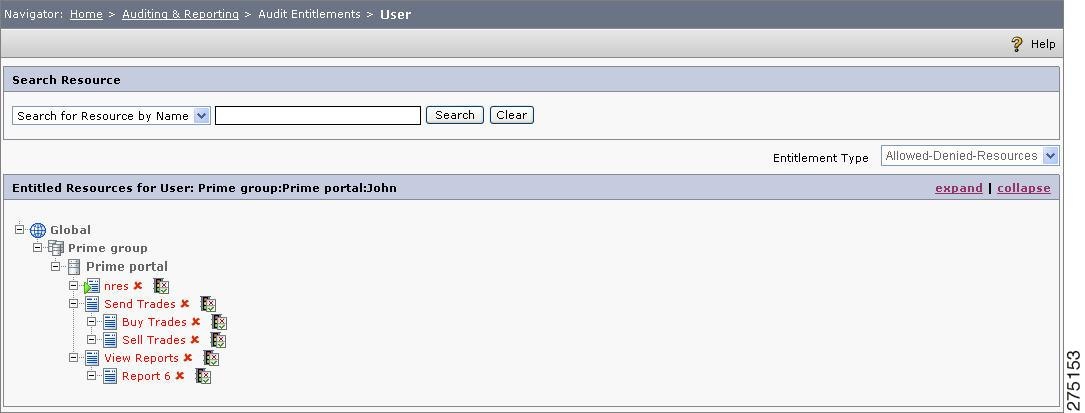
Select the user and click Entitlements to review the entitlements defined for that user. The permitted resources for the selected user are displayed.
Figure 6-4 Entitled Resource for User
Step 7
Select Entitlement Type from the drop-down list to view the filtered policies of the selected user.
You can use the following criteria for filtering the policies.
•
Allowed Denied Resources—Displays the resources with Allow and Deny permission.
•
Only Allowed Resources—Displays the resources with Allow permission
•
Only Denied Resource—Displays the resources with Deny permission
Step 8
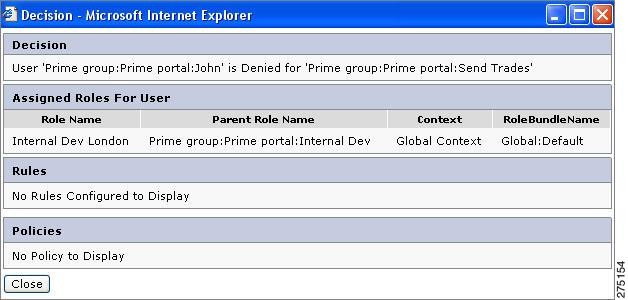
Click View Decision for any resource. A pop-up page displays the policy log, which justifies why the resource is allowed or denied. For example, in the View Decision for Users, if you click the View Decision button of Sell Trades, the window shown in View Decision for Users appears with the reason is displayed showing why the resource is allowed to the selected user.
Figure 6-5 View Decision for Users
Audit Entitlements for Group
You can view the entitlements defined on a particular group under an application group or application. The process is similar to what is followed in the case of auditing users with a few exceptions, such as viewing the decision policy is not permitted for groups.
To audit entitlement for a group, you must:
Step 1
Choose Auditing and Reporting > Audit Entitlement > Group.
The Group page is displayed which displays a list of groups created under that application.
Step 2
Select the Application, Context, and RoleBundle from the drop-down list.
Step 3
To search for a particular group, enter the group name in the search text box.
Step 4
Enter the message attribute (if any). Message attributes are attributes extracted from an Xpath without giving the full path. While creating a PIP rule, you can select message attribute as an attribute for defining a condition.
Step 5
Click Search. A list of groups (as per the search criteria entered in the page) is displayed for the selected application or application group.
Figure 6-6 Audit Entitlement Group search
Step 6
Select the group and click Entitlements to review the entitlements defined for that group. The permitted resources for the selected group are displayed.
Step 7
Select Entitlement Type from the drop-down list to view the filtered policies of the selected group. You can use the following criteria for filtering the policies:
•
Allowed Denied Resources—Displays the resources with Allow and Deny permission.
•
Only Allowed Resources—Displays the resources with Allow permission
•
Only Denied Resource—Displays the resources with Deny permission
Step 8
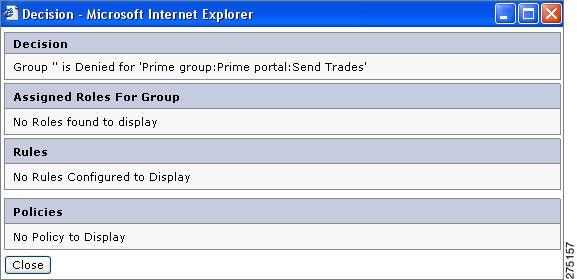
Click View Decision for any resource. A pop-up page displays the policy log, which justifies why the resource is allowed or denied. For example, in View Decision for Groups, if you click the View Decision button of Send Trades, the following window is displayed showing why the resource is denied to the selected group.
Figure 6-7 View Decision for Groups
Audit Entitlements for Role
To view the roles and policies on the resources created under a selected application group or application, you must:
Step 1
Choose Auditing and Reporting > Audit Entitlement > Role.
The Role page is displayed, which lists the roles created under that application.
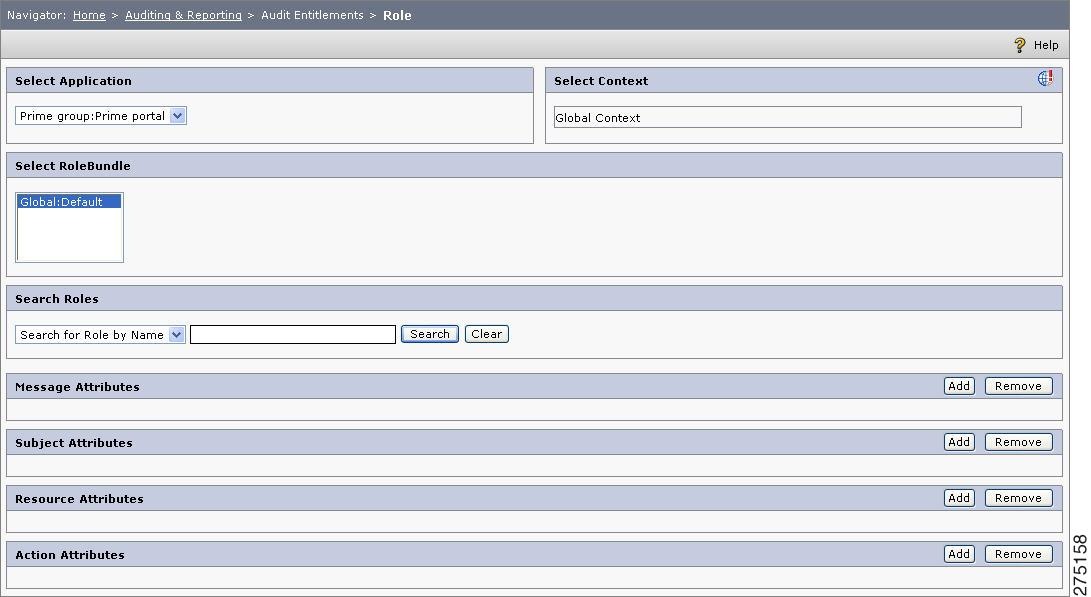
Figure 6-8 Audit Entitlement for Roles
Step 2
Select the Application, Context, and RoleBundle from the drop-down list.
Step 3
To search for a particular role, enter the role name in the search field.
Step 4
Enter the message attribute (if any). Message attributes are attributes extracted from an Xpath without giving the full path. While creating a PIP rule, you can select message attribute as an attribute for defining a condition.
Step 5
Click Search. A list of groups (as per the search criteria entered in the page) is displayed for the selected application or application group.
Figure 6-9 Audit Entitlement Role search
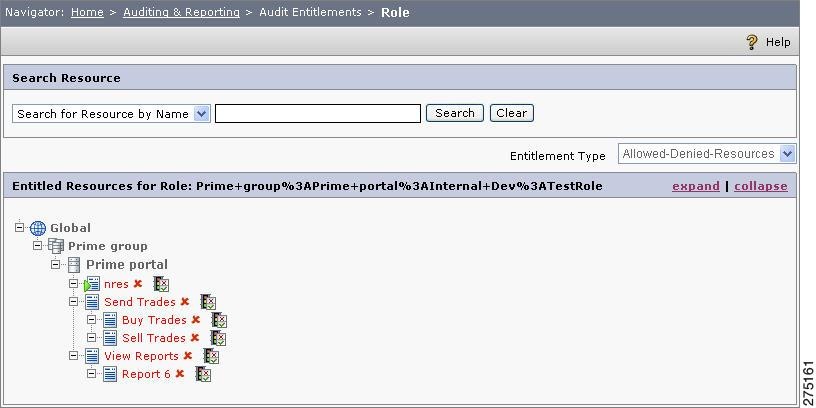
Step 6
Select the role and click Entitlements to review the entitlements defined for that role. The permitted resources for the selected role are displayed.The resources that are permitted for the selected role are displayed in green and those that are not are displayed in red.
Figure 6-10 Entitled Resources for Role
Step 7
Select Entitlement Type from the drop-down list to view the filtered policies of the selected role. You can use the following criteria for filtering the policies:
•
Allowed Denied Resources—Displays the resources with Allow and Deny permission.
•
Only Allowed Resources—Displays the resources with Allow permission.
•
Only Denied Resource—Displays the resources with Deny permission.
Step 8
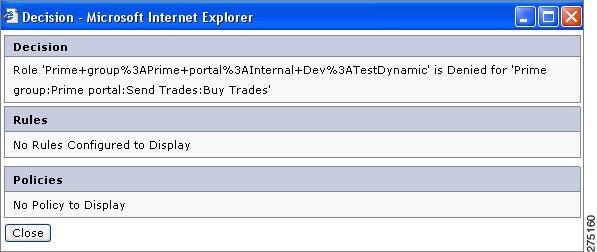
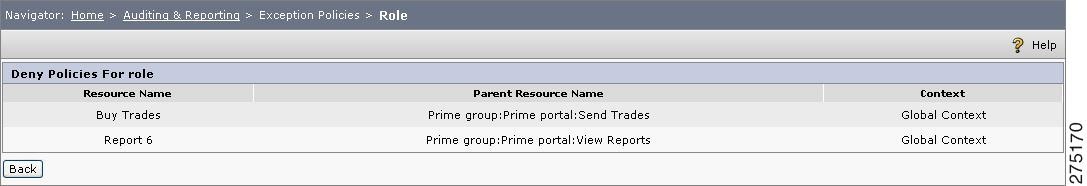
Click View Decision for any resource. A pop-up page displays the policy log, which justifies why the resource is allowed or denied. For example, in View Deciisons for Roles., if you click the View Decision button of Report6, the window is displayed showing why the resource is denied to the selected role
Figure 6-11 View Deciisons for Roles.
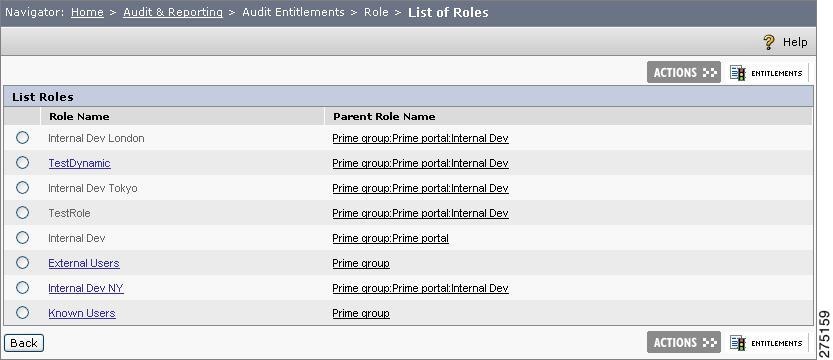
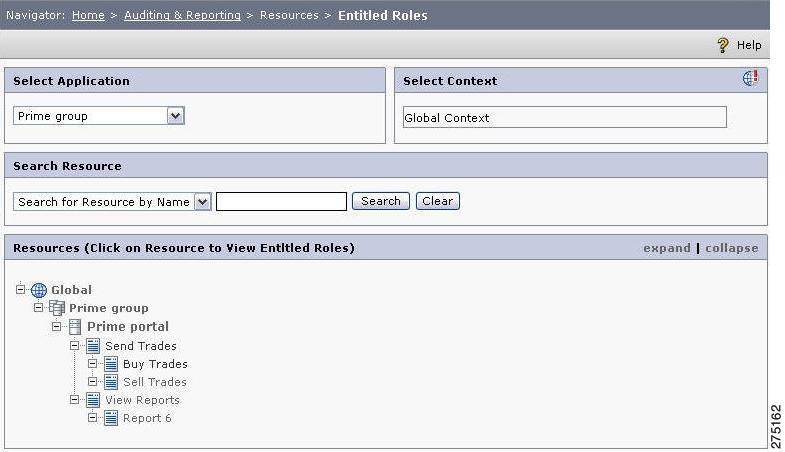
Entitled Roles for a Resource
This feature allows you to choose a resource and get back a list of roles that are permitted for the chosen resource.
After viewing a list of roles, to further enquire into which roles get permission in which application or resource, you must:
Step 1
Choose Auditing and Reporting > Resources > Entitled Roles.
Figure 6-12 Entitled Roles
Step 2
Select the application from the drop-down list.
Step 3
Select the context under which you want to view the allowed roles for a specific resource.
Step 4
Search for the required resource by entering the search criteria in the Search box. When the number of resources are high, this helps in finding the required resources without navigating the complete tree.
Step 5
Search for the resource to view the roles allowed on it. If you want to view all the resources under the selected application, expand the resource tree in the lowermost section.
Step 6
Click the application to view the entitled roles. The Entitled Roles page is displayed.
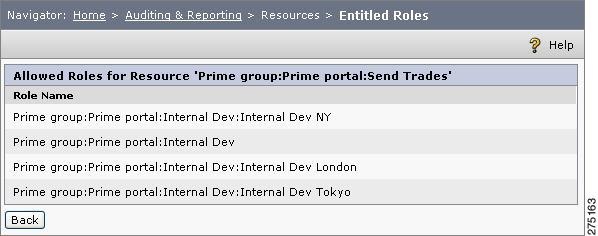
Figure 6-13 Allowed Roles for Resource
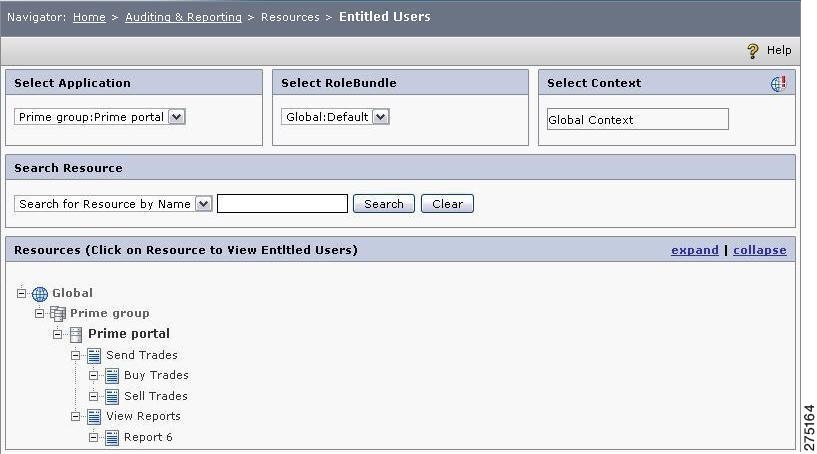
Entitled Users for a Resource
This feature allows you to choose a resource and get back a list of users who are permitted for the chosen resource. The list includes all users belonging to the roles and groups mapped to the selected resources.
To view users entitled to a resource, you must:
Step 1
Choose Auditing and Reporting > Resources > Entitled Users.
The Users Entitled to Resources page is displayed.
Figure 6-14 Entitled Users
Step 2
Select an application from the drop-down list. The resource tree is displayed from which you need to select the resource to view its entitled users.
Step 3
Select the role bundle to filter the users entitled under that particular role bundle. If you do not select the role bundle, the Global:Default is considered as the default role bundle.
Step 4
Search for the required resource by entering the search criteria in the Search field. When the number of resources are high, this helps in finding the required resources without navigating the complete tree.
Step 5
Click the resource to view the entitled users. The users list is displayed.
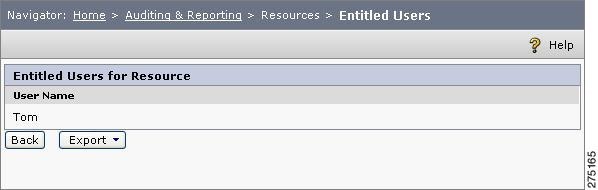
Figure 6-15 Entitled Users for Resources
The users table lists all the users that are entitled to the selected resource, irrespective of the roles and group that they belong to. You can export the list of users entitled for the selected resource into an Excel file. Click Export to save the Excel file (named EntitledUsers.xls) at an appropriate location.
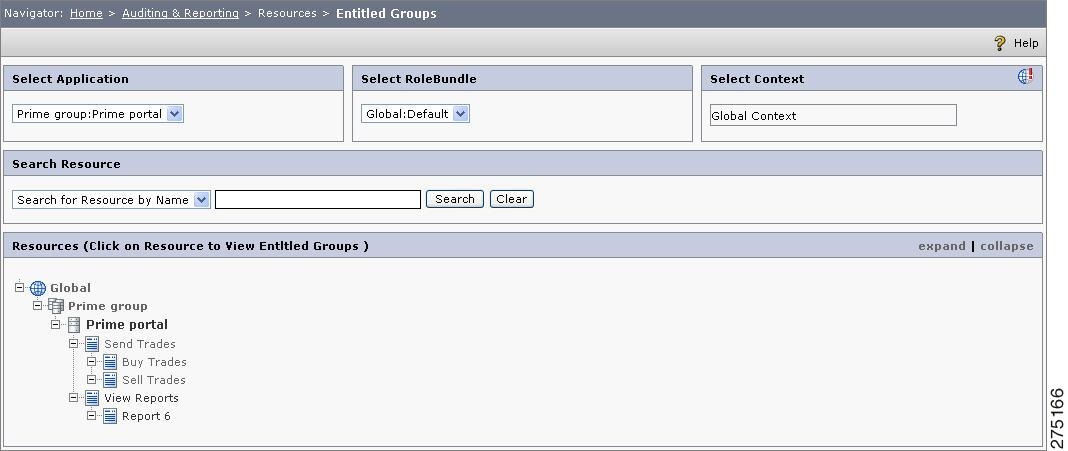
Entitled Groups for a Resources
This feature allows you to choose a resource and get back a list of groups that are permitted for the chosen resource. The list includes all the groups that belong to the roles and groups mapped to the selected resource.
To view groups entitled to a resource, you must:
Step 1
Choose Auditing and Reporting > Resources > Entitled Groups. The Entitled Groups to Resources page is displayed.
Figure 6-16 Entitled Groups to Resources
Step 2
Select an application from the drop-down list. The resource tree is displayed from which you need to select the resource to view its entitled groups.
Step 3
Select the role bundle to filter the groups entitled under that particular role bundle. If you do not select the role bundle, the Global:Default is considered as the default role bundle.
Step 4
Search for the required resource by entering the search criteria in the Search field. When the number of resources are high, this helps in finding the required resources without navigating the complete tree.
Step 5
Click the resource to view the entitled groups. The groups list is displayed.
Exception Policies
When you have a large number of users/roles/groups, it is difficult to review which user is denied what resource. Keeping track on the direct deny policies for a given user/role/group, CEPM provides the Exception Policy section in the navigation pane, which enables you to view explicitly deny policies of the selected user/role/group. This feature allows you to get a list of resources based on user/group/role for which there is a direct Deny policy associated. Given a user/group/role, this functionality does not evaluate the policies, but just displays the direct Deny policy associations. Using this list, you can analyze what resources are not allowed for which user/group/role. The same list can be viewed by clicking Permitted Resources for any user/role/group in the Audit Entitlements page, but along with the allowed resources.
The Exception Policies work well if the user/role/group are exclusively assigned Deny permission while assigning resources.
Exception Policies for User
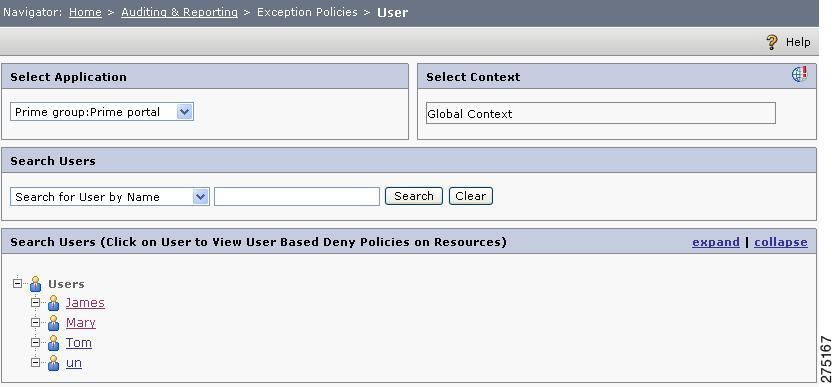
To find out which resources are not allowed for a selected user irrespective of the role associated, you must:
Step 1
Choose Home > Auditing and Reporting > Exception Policies > User. The User page is displayed, which lists all the users under the selected application.
Figure 6-17 Exception Policies User Home page
Step 2
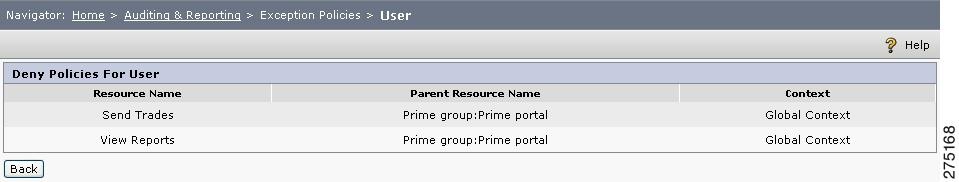
To view resources that have direct Deny policies for a particular user, click that user in the list.
The resources are displayed in a tabular format. It is important to note that this outcome is based on all types of policies involving the specified user, for example, user-based, group-based, resource-based, and role-based entitlement.
Figure 6-18 Exception Policies for User
For example a user, Mary is mapped with a role called Agent. As a part of the user-based entitlement, Mary is denied to the resource called View Reports. The role Agent has Deny policies on Send Trades and Buy Trades. While viewing explicit Deny policies of Mary, the resource table contains only View Reports.
Exception Policies for Group
To find out which resources are not allowed for a selected group irrespective of the role associated, you must:
Step 1
Choose Home > Auditing and Reporting > Exception Policies > Group.
The Group page is displayed, which displays all the groups under the selected application.
Figure 6-19 Exception Policies Group Home page
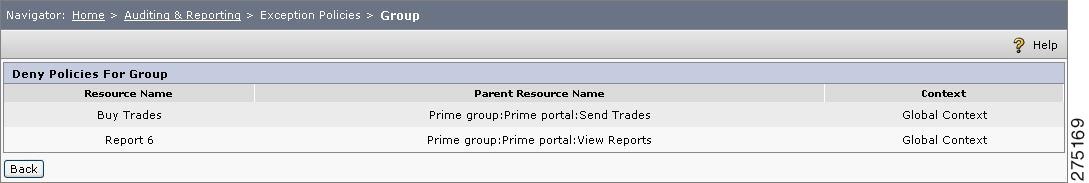
Step 2
To view resources which that have direct Deny policies for a particular group, click that group in the list.The resources are displayed in a tabular format.
Figure 6-20 Exception Policies for Group
Step 3
While listing the resources, only group-based and role-based policies are taken into consideration and not the user-based policies.
Exception Policies for Role
To find out which resources are not allowed for a selected role, you must:
Step 1
Choose Home > Auditing and Reporting > Exception Policies > Role.
The role page is displayed, which displays all the roles under the selected application
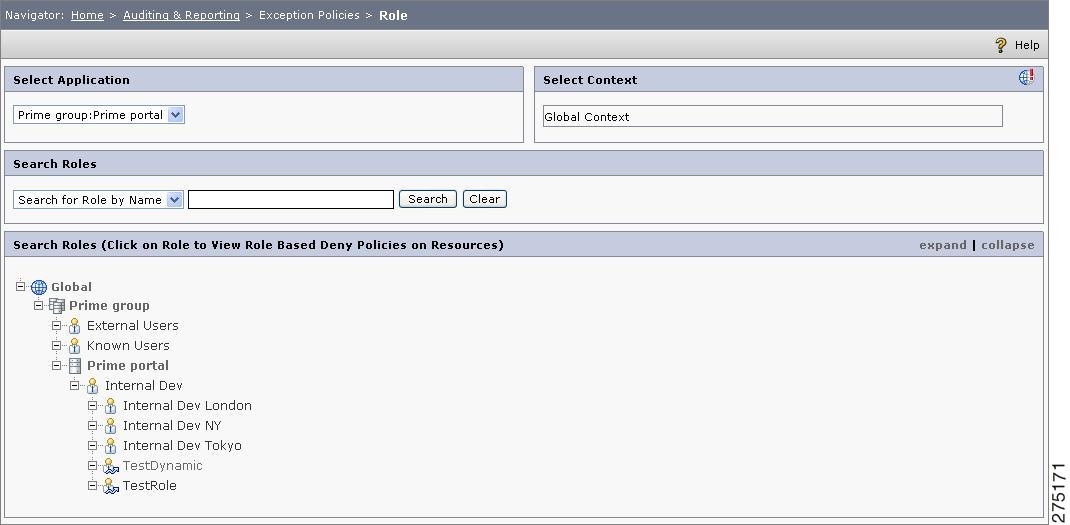
Figure 6-21 Exception Policies Role Home page
Step 2
To view the resources that have direct Deny policies for a particular role, click that role in the list.The resources are displayed in a tabular format.
This functionality narrows down the resources to only role-based Deny policies defined on these listed resources
Figure 6-22 Exception Policies for Roles
Audit Reports
Audit Reports deal with logging and reporting of the activities that take place within the administration console for a specified time period. Review Reports enables you to view the entities status. The entity status provides statistics on how many users, groups, resources, roles, policies, and mappings are created/updated/deleted in a given time frame and for a given application.
As a security measure, all the activities carried out in the PDP and PAP are recorded in the database. The superuser can view activity logs of other admin users and also the type of permission granted by the PDP to any PEP user for accessing a resource. CEPM supports two types of logs:
•
Runtime log
•
Admin log
Review Reports
Review Reports allows you to create, update, and delete entities within a specified timeframe. It generates event-based reports of the entities, such as users, groups, roles, resources, resourceTypes, userTypes, contexts, role bundles, user attribute sources, and application attribute sources. Events include creation, updation, and deletion. It also generates a report of resource-based, role-based, group-based, and user-based.
It is important to note that in order to view the deleted entities using this functionality, you must update the pap_config.xml file by setting the <eventenable> tag to true. No such settings are required for the other events.
To view the reports, you must:
Step 1
Choose Auditing and Reporting > Audit Reports > Review Reports.
Step 2
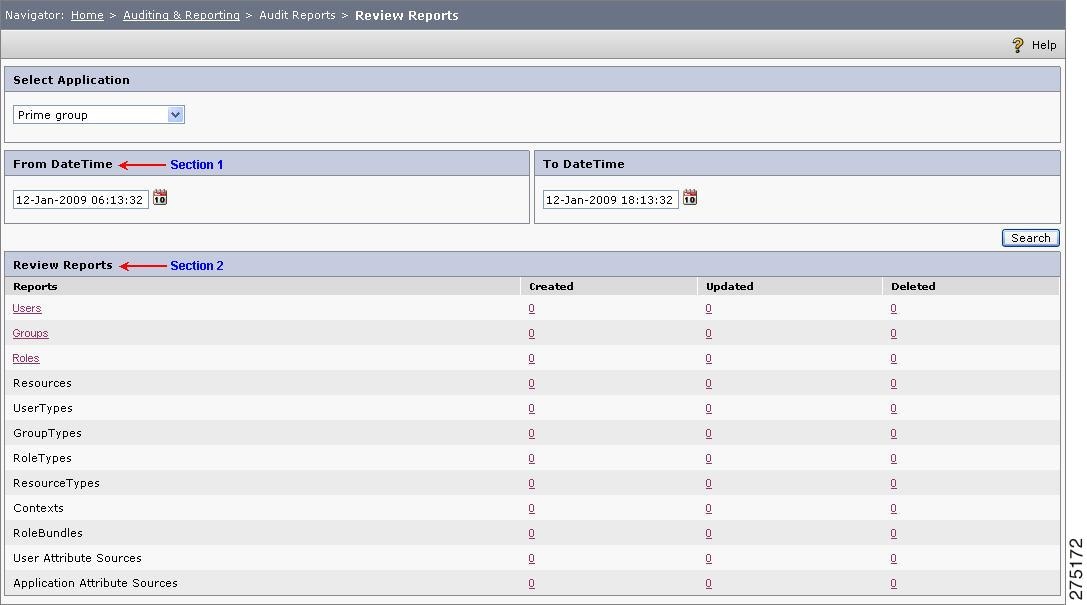
Review Reports page is displayed. This page comprises of two sections.
•
From DateTime to To DateTime—Prompts you to set the date and time frame within which you need to generate the report.
•
Review Reports—Itemized with the entities, such as, users, groups, roles, and so on with the corresponding figures of creation, updation, and deletion.
Step 3
Select the time limit and click Search. A list of entities created, updated, and deleted between the specified dates is displayed. These counts are hyperlinked dynamically.
Figure 6-23 Review Reports Home Page
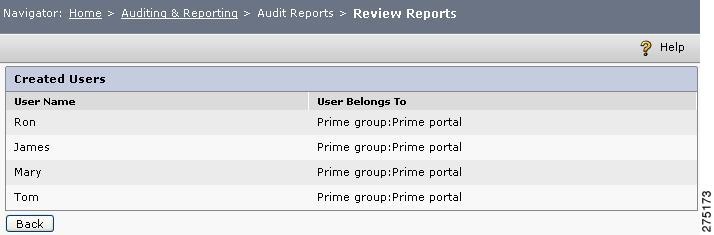
Step 4
Click the hyperlinks (counts) for more information on the entities and the corresponding operation from the table that is displayed. For example, to view all the users created within the specified time period, click the number `4' in the `created' column. A pop-up window is displayed that lists the users that have been created within the specified time period.
Figure 6-24 Review Reports-created users
Similarly, you can view the updated and deleted users, groups, roles, resources, user types, group types, role types, resource types, contexts, role bundles, user attribute sources and application attribute sources.
Step 5
To view the mappings that are done in a specified time frame, for example, related to a user (user-role mapping, user-group mapping, and user-resource mapping as done in user-based entitlement) click the Users link in the table. The Mapping report is displayed that lists the count of user-role mappings, user-group mappings, and user-based policies. The numbers that appear as counts are hyperlinked.
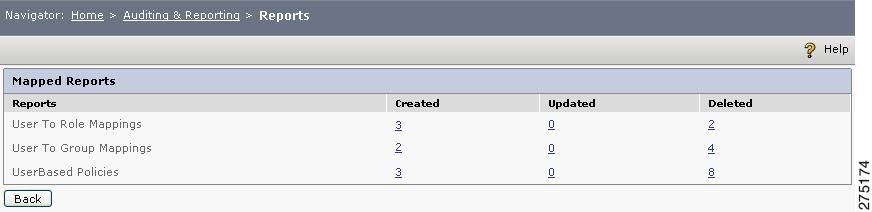
Figure 6-25 Mapped Reports
Step 6
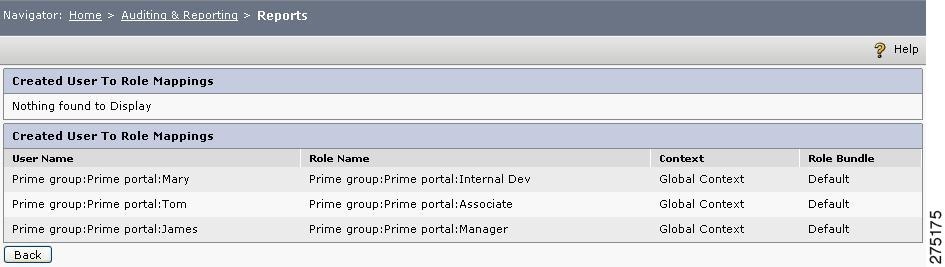
Click the hyperlinked number to view the details of each mapping. For example, when you click 3 in the User to Role Mappings row, can view the mapped users and roles.
Figure 6-26 Mapped Users and Roles
Similarly, you can click Group and Role buttons in the table to view all the related mappings along with the policies that are created.
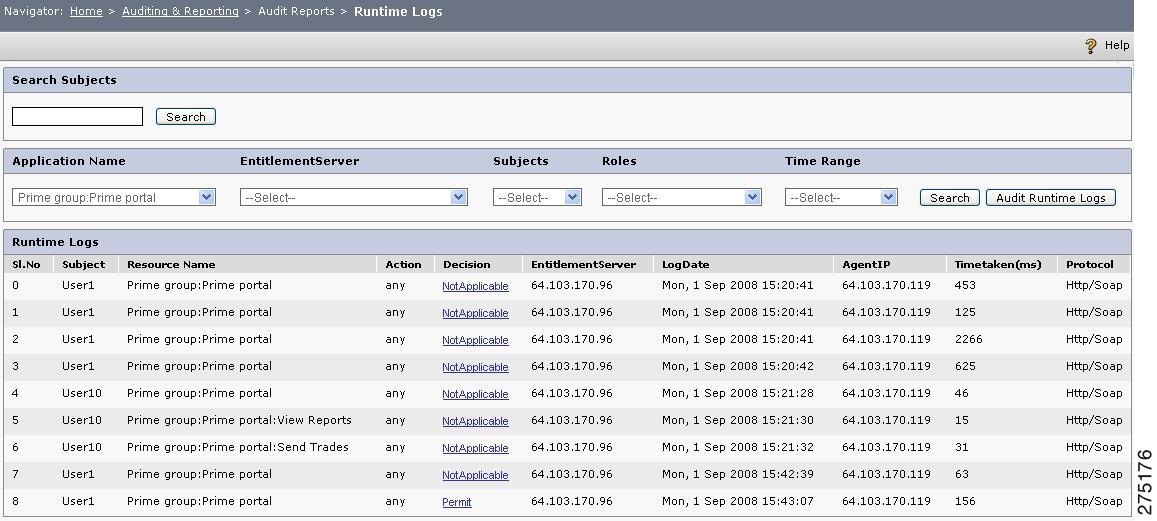
Runtime Log
This functionality enables the user to view the runtime log that is generated in accordance with the parameters that are passed. Logs can be obtained based on any application, PDP, users, roles, and time range. The following settings are mandatory to view the runtime logs:
•
The runtime logs for any application will be visible in User Interface only when `Enable XACML Logs' option is checked while creating that application.
•
To view the attributes returned as obligations, set the `attributeEnable' tag to `True' at <pdp> tag in pdp_config.xml file.
To view a runtime log, you must:
Step 1
Choose Auditing and Reporting > Audit Reports > Runtime Log.
Figure 6-27 Runtime Log
Step 2
Select all or any parameter and click Search.
All runtime logs related to the selected parameters are generated. As far as user-related logs are concerned, a search option is available that provides you that provides you the option to view logs for that particular user.
Step 3
To view logs for a particular user, enter the user name or the first letter of the user name in the Search Subjects field and click Search.
Step 4
Select other parameters, such as application name, PDP name, role, and time range from the drop-down list. Click Search to view the runtime log according to the settings done in the parameters.
The Access Log cannot display all the logs generated at any time in a single web page if the content is vast. It may contain more than one page of reports. Appropriate arrangement has been made to enable the user to view the logs when a huge number of reports are generated.
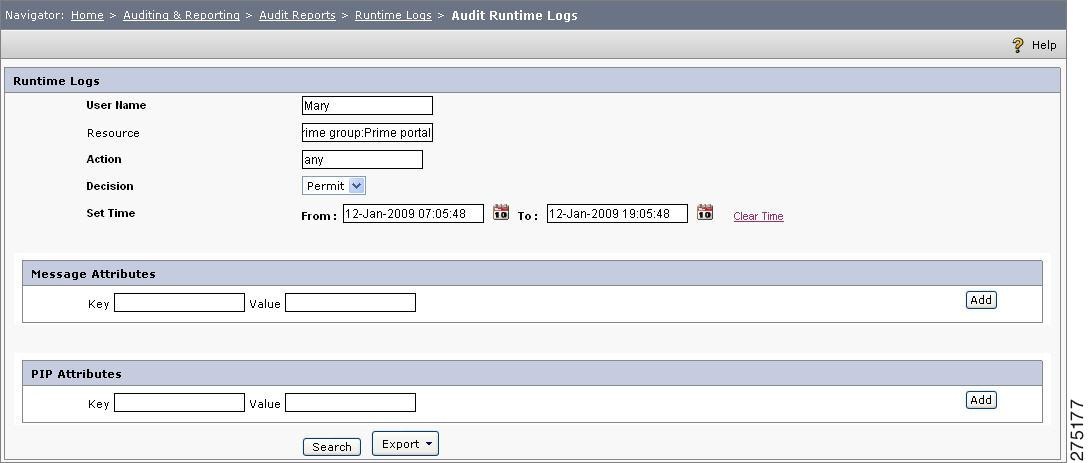
Audit Runtime Logs
This feature is applicable for new APIs only. Using this feature, you can search within the runtime log (XACML Response), for a particular user under the specific user decision (permit/deny) on any resource and action with respect to a set of environmental attributes. In the runtime log, the XacmlResponse for the given inputs is filtered on the basis of the message attributes and PIP attributes and the final outcome can be displayed.
To audit the runtime logs, you must:
Step 1
Choose Auditing and Reporting > Audit Reports > Runtime Log > Audit Runtime Logs.
Figure 6-28 Audit Runtime Logs
Step 2
Enter the Username.
Step 3
Enter the Fully qualified name of the resource (for example, Prime group:Prime portal:Send trades).
Step 4
Enter the Action name. If there is no specific action, you must specify this name as Any.
Step 5
Select the Decision type as Permit or Deny.
Step 6
Set the Time period for which the report is to be generated.
Step 7
Enter the environmental attribute details, such as key-value pair of message attributes and PIP attributes. Use the Add button if more than one attribute is to be added for the filtration.
Step 8
Click Search.
The required logs are displayed on the Access Runtime Logs section of the page. You can export these logs to your local drives using the Export button. When you click this button, you are prompted to save the AuditRuntimeLogs.xls /AuditRuntimeLogs.csv file, which contains the generated logs as per the given inputs.
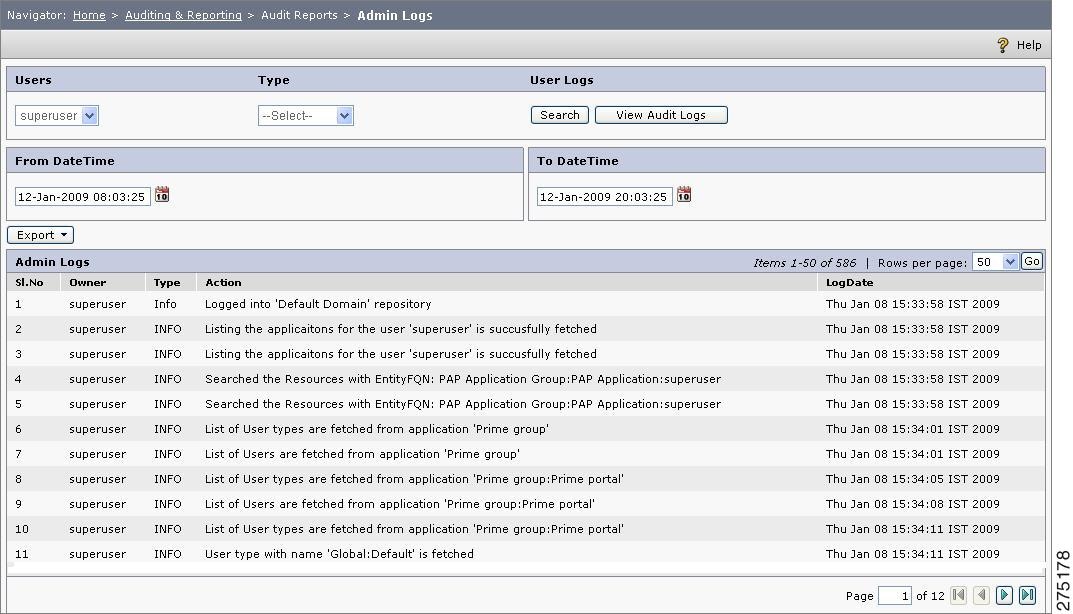
Admin Logs
The admin log works in coherence with the PAP. The admin log discloses the user activity, type, and actions taken by the user along with the time stamps.
To view the Admin logs, you must:
Step 1
Choose Auditing and Reporting > Audit Reports > Admin Log.
The Admin Log page is displayed.
Figure 6-29 Admin Logs
Step 2
To access logs of any PAP users for a specific time period, choose from the Users drop-down list, which dynamically contains the users created by the superuser. The logs are generated for a time period that can be set using the From Date time and To Date time.
Step 3
Select the Type from the drop-down list. The various types that CEPM supports are:.
Step 4
Click Search. The logs are generated.
Step 5
To save the record in Excel format, click Export, which prompts you to save the file named AdminLogs.xls.
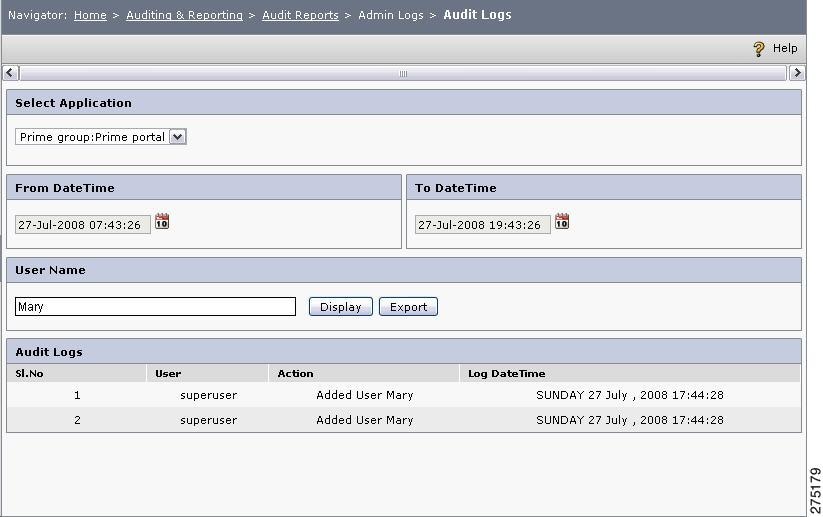
Step 6
To monitor the activities of any PAP users created under an application group or an application, click the View Audit Logs link at the top-right corner of the page. The Audit Logs page is displayed.
Figure 6-30 Audit Logs
Step 7
Enter the Username and set the From Date time and To Date time and click Display. The logs are generated.
Step 8
To export this report in Excel format, click Export. This will create a file called AuditLogs.xls, which can be saved in the desired location in your system.
Audit SoD Violation
In the CEPM, in a few instances, SoD role are configured for roles much after necessary policies are created for these roles on same resources. A similar situation might arise for users and groups, when they are mapped to the roles which are SoD to each other.
For example, Role1 has an existing policy on a Resource called MyReport. Role1 and Role2 are SoD roles. In this case, you cannot create the desired policy for Role2 in MyReport due to SoD violation, but in certain circumstances, if you have already created policies for Role1 and Role2 on the same resource (MyReport) before declaring the SoD roles, no such SoD violation is known unless and until it is detected by the PDP while giving decision to a PEP request. Similarly, if SoD roles are defined after mapping users and group to the roles, a similar situation arises.
The policy administrator can look up all the SoD violations for user, group, role. to avoid such situation by periodical verification of SoD violations listed in this page. To view what SoD roles are created after defining the policies, you must:
Step 1
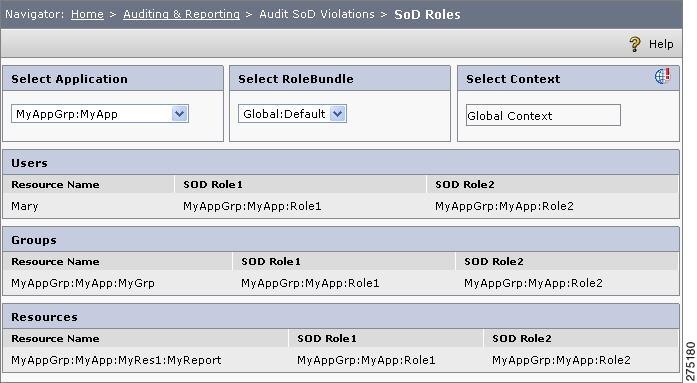
Choose Home > Auditing and Reporting > Audit SoD Violation > SoD Roles.
The SoD Violated Roles page is displayed.
Figure 6-31 SoD Roles
Step 2
Select an application from the drop-down menu.
Step 3
Select the Role Bundle.
Step 4
Select the Context.
The Users, Groups, and Resources tables list the SoD roles. For example, the User table shows a list of users and the SoD Roles to which the user (or the group to which the user belongs to) is mapped. Similarly, the Group table lists all groups and the SoD roles that are mapped with the groups. The Resource table lists all the resources where SoD role violation has occurred. ( SoD roles are defined after a policy has been created on the specified resource)
Consider a user called Mary who is mapped to two roles (Role1 and Role2) and policies are created for these two roles in the same resource. After creating policies, you set Role2 as SoD role for Role1. As you already defined the policies, this setting does not have a direct impact of SoD role violation. When you review the SoD roles using this functionality, the Users table shows Mary along with the roles that are SoD roles to each other.
Manage Log Level
A server log is automatically created and maintained for all the activities performed by the concerned PDP server. In CEPM, these logs are generated from com.cisco.epm.pdp for any application only if the xacml log is enabled when that application is created. For example, when the PEP sends a request to the PDP, the PDP server maintains a history of that requests along with the response it returns.
The logs are separated into the following distinct categories called as log levels:
•
FATAL Level—Designates very severe error events that will presumably lead the application to abort. When this level is selected, only logs that belong to fatal category are displayed in the PDP Server console.
•
ERROR level—Records all diagnostic information on all errors. When you select this level for a PDP, the PDP log shows only errors that occurred during the run time. When this level is selected, logs that belong to FATAL and ERROR categories are displayed in the PDP Server console.
•
WARN level—Shows all the warning messages generated by the PDP. In case of a situation that seems to be potentially harmful for the application, the PDP raises a warning which is logged in the server log if WARN level is selected. When this level is selected, logs that belong to FATAL, ERROR and WARN categories are displayed in the PDP Server console.
•
DEBUG level—Designates fine-grained informational events that are most useful to debug an application. This is the widely used log level as it generates all the activities irrespective of the nature of their occurrences. When this level is selected, logs that belong to FATAL, ERROR, WARN, and DEBUG categories are displayed in the PDP Server console.
•
INFO level—Designates informational messages that highlight the progress of the application at granular level. When this level is selected, logs that belong to all the categories are displayed in the PDP Server console.
After you select the log level, click the set button to generate logs in the console according to the LogLevel type that you have chosen, logs will be generated in the console according to the selected LogLevel type.
Note
Before you set the log level, ensure that the <appender-ref> tag in the logging.xml file is set to console-appender (by default it is set to file-appender).
Debug Level displays the logs when the log level is set to DEBUG level.
Figure 6-32 Debug Level
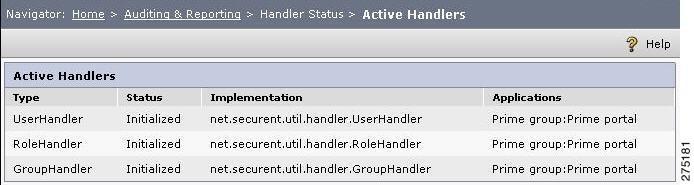
Handler Status
This feature allows checking for all the handlers that are running and also the LDAP Sync status. (For more information about the advantages of using prehook handlers in the CEPM). You can see the handlers status from Home> Auditing and Reporting > Handler status > Active Handlers. A list of handlers that are enabled in the pap_config file and their initialization status is displayed.
Figure 6-33 Active Handlers
Note
To view the handlers status, the init method of the implementation class should throw an exception called HandlerInitializationException.
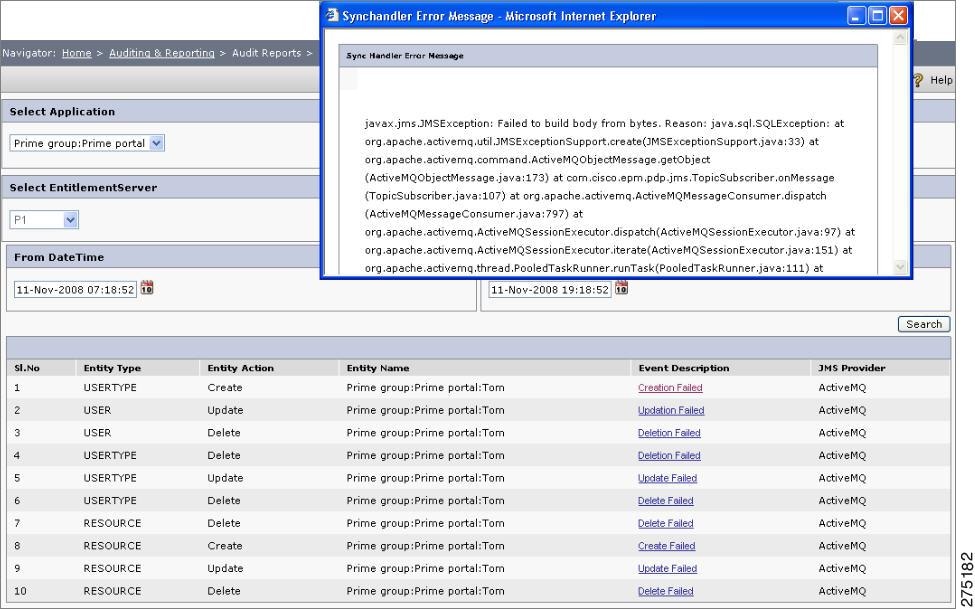
Sync Failure Events
Synchronization Failure occurs if there is a lack of harmony between events of any system in unison.
Here, in CEPM, events are Actions (Creation, Updation, and Deletion) and harmony is within PAP and the PDP.
For example, a new user named Mary is to be created. Assuming that there exist 3 instances of PDP named PDP1, PDP2, and PDP3. The user Mary is successfully created at PDP1 and PDP2, but at PDP3 due to database failure, an creation error occurred. PDP3 sends the creation failure message to PAP. As soon as PAP recieves that message, it performs a roll back operation on PDP1 and PDP2 to maintain consistency.
To view the Sync Failures, you must:
Step 1
Choose Home > Auditing and Reporting > Sync Failure Events > Sync Failures.
The Sync Failure page is displayed.
Step 2
Select the application from the drop-down list.
Step 3
Select the PDP from the drop-down list.
Step 4
Select the date and time range. Click Search. The below Sync Failure shows the Sync failure page that lists the failures that occurred during the specified time frame. To view the Sync handler error messages, click Event Description.
Figure 6-34
Sync Failure

 Feedback
Feedback